A Framework for Service-Oriented Architecture (SOA)-Based IoT Application Development
Abstract
:1. Introduction
2. Related Work
2.1. IoT-Driven Integration
- Adaptivity: IoT devices are often mobile, moving across wide geographical area, while still needing to continue interacting with other assets in real-time [17]. For this reason, communication devices should adjust themselves in new locations and collaborate with the local things.
- Context-awareness: Systems and their components need to understand the context of events to accurately adapt their actions to satisfy the users’ needs and requirements and thus enrich the available services.
- Autonomy: Applications/IoT devices should be able to manage spontaneous interactions when they move to new locations and get in other objects’ communication range [19]. These interactions should occur without or with minimal human involvement.
- Distributivity: IoT devices are intrinsically distributed, resource-constrained components and often require middleware to function properly [20]. The distributive approach helps reduce the overhead of centralized architectures, since IoT systems have a vast number of devices that are constantly collecting and exchanging data over the internet.
- Interoperability: In an IoT environment, heterogeneous devices, technologies and applications should operate to achieve the goal of integration, a property of utmost interest in Industry 4.0. Interoperability has the potential to make software components or systems accessible, manageable and potentially linked despite their differences in interface, execution platform and language [21].
2.2. Interoperability in IoT
- Technical Interoperability: hardware/software components, platforms and systems that allow machine-to-machine communication;
- Syntactical Interoperability: related to data formats;
- Semantic Interoperability: related to the meaning of contents.
2.3. Service-Oriented Architecture and IoT
2.4. Related Middleware Platforms
- Orion: Open-source component that allows the user to manage context information, including update context, queries context, registrations and subscriptions. Developed by the FIWARE foundation, it can be useful for providing functionalities for context management and can be useful in use cases that involve data brokers between producers (e.g., sensors) and consumers (e.g., smartphone applications). It has an NGSI interface that allows users to make several operations, such as register, update and query context information, as well as receive notifications when changes in context information take place (e.g., a sensor value has changed). This component has a Metrics API that provides a few statistical data about their services. Orion also implements a simple multitenant/multiservice model that ensures entities from one service cannot be affected by other services [50].
- ETSI M2M: Set of standards provided by ETSI defining the entities and functions to enable interoperability between M2M services. The ETSI M2M architecture is agnostic to underlying networks and includes two basic elements: Service Capability Layers and Service Capabilities. The first functionality exposes the Service Capabilities to M2M applications and should be implemented on top of devices and/or gateways [51]. The second functionality provides generic M2M functions, analogous to GEs in FIWARE, including communication management, application management, device discovery and integration, etc. It also supports both the request–response and publish–subscribe communication models [52]. According to the authors of [53], ETSI M2M has no reference implementation, compared to, for instance, FIWARE. However, the authors provide their implementation of an ETSI M2M broker and APIs and also benchmark the ETSI M2M implementation against the FIWARE-based solution. ETSI M2M enables connections between physical devices and their digital representations, called Business Applications [54]. However, there is limited information on the possibility of creating multiple instances of Business Applications.
- Ptolemy Accessor Host: Actor-based framework that relies on the notion of an actor as a central element. In the context of this component, “actor” is used to specify a software component that is triggered based on an input event and produces an output event. One specific type of actor is called an “accessor”, which wraps a device or a service in an actor interface [55]. Every accessor possesses an interface serving as a local proxy and implementation encapsulating the API of a physical device or remote service [26]. Accessors can form applications that are placed within the accessor host, providing registration and discovery functionalities. Moreover, Ptolemy provides user interface with drag-and-drop capabilities to connect actors and accessors. Ptolemy Accessor Host supports instantiation functionality, which allows the creation of multiple accessors within other accessors [56]. To the best of our knowledge, metrics are not available on the Ptolemy platform.
- DeviceHive: Middleware designed to enable message exchange between smart devices and client applications [57] that supports a wide variety of communication models, such as publish/subscribe (through MQTT), Rest and Websockets [58]. It also supports the abstraction or logical grouping of different appliances based on, for instance, their location [59]. Authentication is accomplished using a JSON Web Token. DeviceHive API is a service able to manage several resource types, for instance, the “Network”, which is an isolation entity encapsulating multiple devices. However, the solution does not provide metrics to assess API performance [60].
- NodeRED: Open-source middleware provided by IBM. The main element of the NodeRED environment is called a Node, which is the visual representation of a block of Javascript codes providing specific functionalities. Moreover, NodeRED provides a library of different nodes with different functionalities, including, for instance, MQTT nodes. The advantage of this middleware is the visual canvas that is used to drag and drop different elements/nodes and to establish connections to compose IoT applications [26]. A device or service has to posses the API as a node.js library or module accessible by NodeRED to communicate with other devices or services. While good for rapid prototyping, NodeRED does not possess service-discovery capabilities. NodeRED contains a module counts and calculates the metrics per message topic.
- Ignition: Modular server-based middleware that combines the SCADA environment and OPC UA communication [61]. Other modules that can be added on-demand include databases, connectivity gateways, industrial control system security services, charts, alarm dispatchers, etc. According to Inductive Automation—the company that developed this middleware—Ignition has the following distinguishing features: support for some SQL databases, synchronization of design and run-time, cross-platform nature and simple deployment procedure [62]. This platform also enables a wide range of metrics, including a dashboard to visualize statistics. Moreover, this component allows decoupling of physical devices from applications, which enables service isolation [63].
2.5. Security and Safety Challenges
3. Solution Description
- Generic Enablers (GE): Software components from the FIWARE project. These enablers provide base services that help applications use IoT devices and third-parties applications to process data and media in real-time on a large scale, perform Big-Data analysis or incorporate advanced features for interaction with end-users. Usually, this type of enabler must be approved by specific guidelines and public dissemination through FIWARE channels [76].
- Specific Enablers: Set of software modules developed by other researchers to help developers create applications that provide functionalities that are more specific to the system’s domain. User instructions and software testing are not standardized.
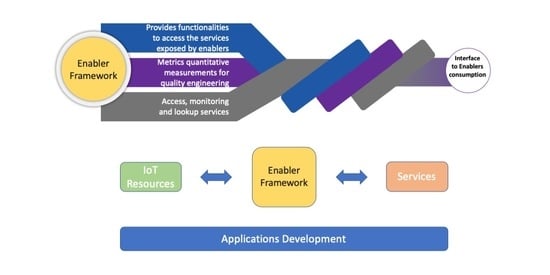
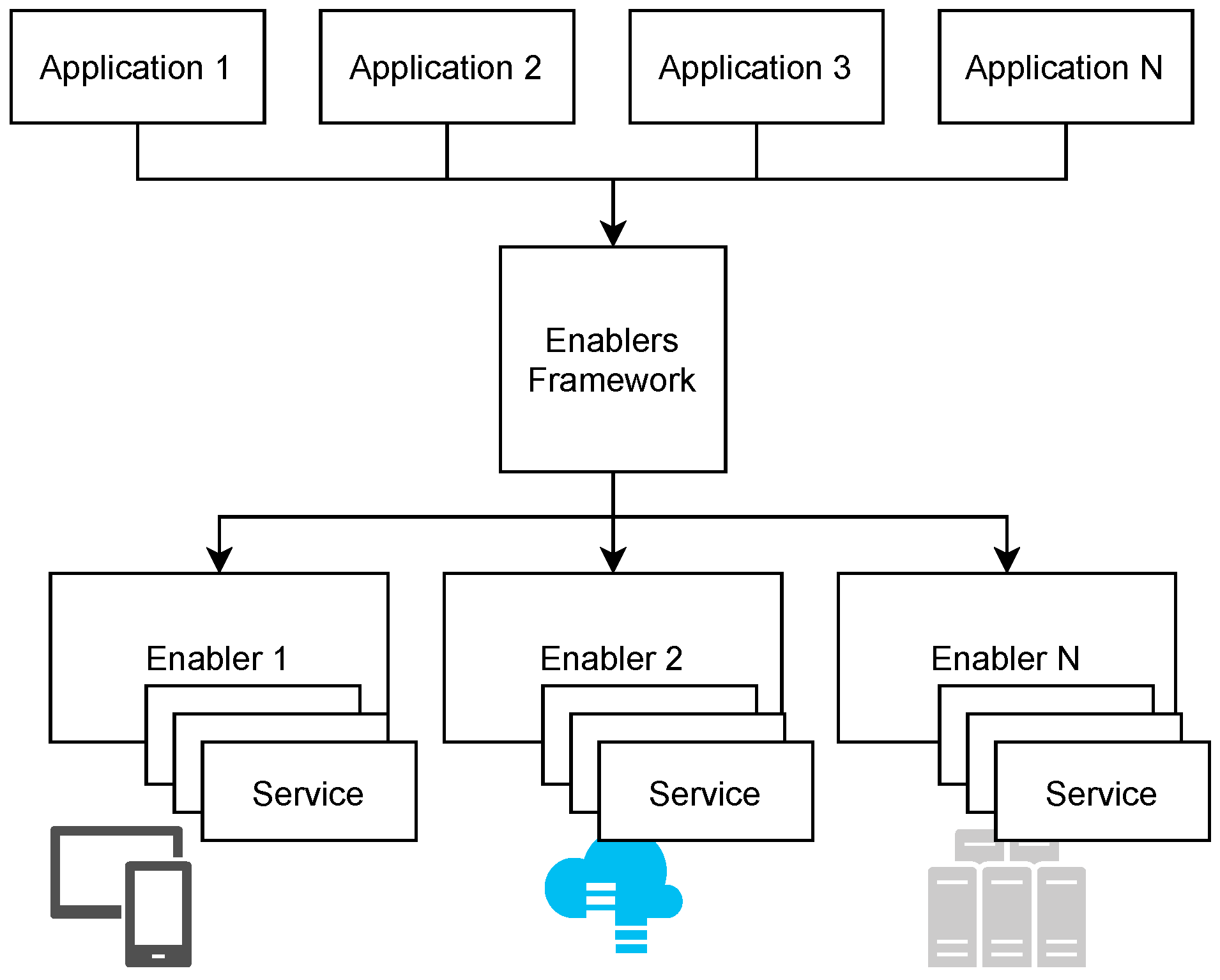
3.1. Software Architecture
- Enabler Registry: This module allows developers to register a new enabler or to search for an available enabler. Moreover, EF is responsible for providing instruments for performing CRUD (create, read, update and delete) operations. This module also contains a Docker management unit that allows the Admin to install new enabler instances and allows the configuration of various parameters for proper functioning of enablers. Enabler Registry could also use Kubernets to deploy and manage the enabler’s instances; however, this software is very complex and brings a heavy load into the system. Thus, researchers suggest Kubernets works best for deploying complex applications; otherwise other orchestration tools such as Docker management are more appropriate [77].
- Storage: Persistent storage is provided by on-premise storage that contains all enabler information and the configuration specifications of the EF. This storage is a PostgreSQL database, and all data management operations performed over EF components are based on ORM (object–relation mapping), which reduces the complexity of accessing the database [78]. ORM functionality is available through the library of static data models.
- Request Handler: This module implements all necessary functionalities for translating application requests to the enablers that are made available by the EF. The internal submodules parse the requests and create a suitable communication channel for accessing the functionalities of the enablers and build the necessary response message based on the results of function invocation. This module uses the enabler technical details from the registry and has suitable proxies to invoke the services of the enabler as requested by the application. The current module allows integration of services that use NGSIV1, NGSIV2 and REST protocols because they are the interfaces required for vf-OS. Nonetheless, other protocols can be integrated into the Request Handler module to allow interoperability of services with other interfaces.
3.2. Enabler Data Structure
- Enabler: Contains information that identifies one enabler. It contains a name that must be unique to avoid conflicts when the application is accessing the IoT software asset.
- Version: Each time a software component changes, it is a good practice to change its version number. This is due to the fact that some updates can impact service execution, such as different APIs or internal behaviour changes. To prevent interoperability problems when a software component is updated, the Enabler class is compatible with multiple versions.
- Qualification: Provides stability and trust for the associated version. Each time a new version is added, a specialized authority, e.g., security admin or software developer chief, must validate and confirm that this new version is working and can be used for future applications.
- Service: All available services from the particular version of a particular enabler’s version are instances of this class. For each service, it is possible to specify the required inputs to execute the service, thus facilitating service execution. This class contains multiple fields (e.g., input headers, required URL parameters and input body schemas) to allow the specification of a wide range of services.
- Instance: Instances are software components that have all functionalities of the corresponding enabler. This feature allows replication of software components or having multiple versions of the same enabler within the same IoT system, as examples, to have software redundancy or software compatibility, respectively, without changing any software code.
- Metric: Metrics refers to quantitative measurements for quality engineering. This SOA characteristic is important when developing applications to guarantee Quality of Service, as it provides information on the availability of a service and also allows choice between identical services that have different response times.
3.3. Instantiation of Enablers
3.4. Enhancing Security with Enablers Framework
- Secure Communication: This issue is addressed by withdrawal, renewal and issuing of digital certificates to enable secure data exchange between system components and external resources. All components within the system environment should possess a certificate for secure communication with other components. Thus, only authentic users and assets are allowed to exchange data and to be sure that data are genuine. Certificates are needed both to encrypt and authenticate communication channels and transmitted data.
- Secure Installation: Considering the potential risks third-party applications present to an IoT system, there is a necessity to use mechanisms to minimize these security risks, both for data and infrastructure. In this regard, the security measures provided are: (i) signature verification, (ii) behaviour monitoring during application run-time to detect any deviations or anomalies, and (iii) security policy management to limit accessible data to the minimum required by the service/application.
- Authorization and authentication: Authentication is the process of validation of user or asset identity, while authorization starts afterward to verify if the authenticated person/asset is allowed to access the requested resources. Authentication and authorization management is available from within the SCC, while the system assets can acquire functionality using the REST API. The authorization process relies heavily on OAuth 2.0 protocol combined with Role-Based Access Control and Attribute-Based Access Control.
- “Privacy by design”: A key principle that is applied to all activities involving the processing of personal data. This presumes the introduction of data protection from the very beginning the design of the product, service and application. This principle is applied for all the cases where ZDMP or its partners have the role of data controller, i.e., “the natural or legal person, public authority, agency, or another body which, alone or jointly with others, determines the purposes and means of the processing of personal data” [83].
- “Privacy by default”: This is applied to all activities involving the processing of personal data. This means that all the partners involved in ZDMP implement and ensure collection of only the necessary personal data for all the activities they are involved as controllers in. Thus, each process involving personal data processing is checked for the possibility of decreasing the personal data required to reach the same or a comparable result.
4. Methods for Prototypical Implementation of an IoT Scenario
4.1. Industrial Scenario
4.2. Components
- Message Queue and Data Processor: Responsible for communication and data-flow management between the connected applications and IoT sensors. They are composed of a RabbitMQ (www.rabbitmq.com, (accessed on 28 July 2022)) message broker and Data Processor grey box from Figure 6. The message queue receives all data from the enablers and redirects them to the correct receivers though the Data Processor component. The modules that use this messaging functionality have access to the software library, which provides functionalities for communication with the broker using the AMQP (www.amqp.org, (accessed on 28 July 2022)) protocol. This protocol is a middleware messaging standard, and it can be applied following publish/subscribe or point-to-point communication patterns.
- Enablers Framework: Middleware component responsible for the integration of enablers so that different enablers can be uniformly accessed and utilized.
- Orion Context Broker: GE that allows management of context information. This enabler operates with the notions of entity (e.g., house, room, or car) and a set of attributes intrinsic to the entity with the capability to query, update and subscribe established entities.
- Short-Time Historic (STH): A GE that manages (stores and retrieves) historical and aggregated time-series data. It reflects the changes in the context data, for instance, updates of attribute values.
- IoT Agent: GE used to manage connections of edge devices, such as sensors, providing corresponding APIs. The sensors are connected with a driver module, a component that is responsible for interpreting the different sensor protocols in order to connect to the message broker.
- Notification Enabler: Specific enabler component that provides a notification functionality based on predefined rules, for example, if the room temperature is higher than a specific value. If these rules are triggered, the user will be notified through an HTTP call or by email [84].
- ZDMP Security Command Center: Two specific enablers that were developed for ZDMP that address the following security concerns:
- –
- Authentication and Authorization: This enabler is used to provide authorization and authentication for users and assets (other enablers and edge devices). The enabler can: (i) store authentication credentials, (ii) issue, after successful authentication, and store access tokens, (iii) store logs of all authentication attempts, (iv) manage the access policy for the registered assets, and (v) detect suspicious activity while monitoring communication among users and assets.
- –
- Secure Communication: This enabler addresses the issuing and revoking of digital certificates for secure communication among users and assets, both internal and external. The enabler includes a Certification Authority and a Registration Authority. The secure communication enabler is tightly coupled with the authentication and authorisation enabler, so that authenticated users or assets can get corresponding digital certificates to collaborate with each other.
4.3. Applications
- SupplyAnalytic: All sensors from the environment generate large amounts of data, which are useless unless analysed and interpreted. This application uses the data gathered from the sensors deployed in the physical environment to know the past and current supply chain context. With this information, it is possible to determine how the product evolves over time and, in case of success or failure, repeat or avoid past production methodologies accordingly. The enabler responsible for context information management receives data from sensors to simplify interpretation. Moreover, another enabler stores historic data. When actuators are involved, the IoT agent component is used to automatically trigger the control output.
- ProductAlarm: The real-time size of each product from a factory production line is used as an input for this application. Data preprocessing (filtering, compression and aggregation) is then performed to examine the status of the production line. According to the factory’s current context values, if the product has not reached a predefined size threshold, an email is sent to the responsible parties. This product-monitor application can be used to detect and prevent faulty products in a production line when machinery calibration is required. Many factory machines require calibration when specific problems occur, and if it is not done quickly, the output might be incorrect. In a factory, the late detection of these problems can lead to severe economic losses.
5. Results
6. Discussion
- Programming abstraction: The API for application developers must be easy and intuitive to use. When developing the middleware, programming paradigms and interface types must be well-defined. The abstraction level specifies how the user views the system (e.g., individual node/device level). The appropriate programming paradigm simplifies the processes of modelling and programming, and the interface type defines the communication style and must be similar to the services to be more intuitive.
- Service-based: The process of adding new functions to IoT middleware has to be flexible and easy. To have the seamless integration of different components, the interfaces of those components must be standardized to facilitate interoperability [87]. It is also mandatory that each IoT module is uniquely defined, enabling discoverability within the object’s network [17].
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Abbreviations
| API | Application Programming Interface |
| GE | Generic Enablers |
| IIoT | Industrial IoT |
| IoT | Internet of Things |
| MSA | Microservice Architecture |
| ORM | Object-relation Mapping |
| SOA | Service-Oriented Architecture |
| SCC | Security Command Centre |
| TLS | Transport Layer Security |
| VPN | Virtual Private Networks |
| ZDMP | Zero-Defects Manufacturing Platform |
References
- Blackstock, M.; Lea, R. IoT interoperability: A hub-based approach. In Proceedings of the 2014 International Conference on the Internet of Things (IOT), Cambridge, MA, USA, 6–8 October 2014. [Google Scholar] [CrossRef]
- Khan, F.; Tarimer, I.; Taekeun, W. Factor Model for Online Education during the COVID-19 Pandemic Using the IoT. Processes 2022, 10, 1419. [Google Scholar] [CrossRef]
- Li, S.; Xu, L.D.; Zhao, S. The internet of things: A survey. Inf. Syst. Front. 2015, 17, 243–259. [Google Scholar] [CrossRef]
- Saidu, C.; Usman, A.; Ogedebe, P. Internet of Things: Impact on Economy. Br. J. Math. Comput. Sci. 2015, 7, 241–251. [Google Scholar] [CrossRef]
- Manyika, J.; Dobbs, R.; Chui, M.; Bughin, J.; Bisson, P.; Woetzel, J. The Internet of Things: Mapping the Value Beyond the Hype; Technical Report; McKinsey Global Institute, McKinsey & Company: Hong Kong, China, 2015. [Google Scholar]
- Xie, J.; Chen, C. Supply chain and logistics optimization management for international trading enterprises using IoT-based economic logistics model. Oper. Manag. Res. 2022. [Google Scholar] [CrossRef]
- Jiang, Z.; Chang, Y.; Liu, X. Design of software-defined gateway for industrial interconnection. J. Ind. Inf. Integr. 2020, 18, 100130. [Google Scholar] [CrossRef]
- Fortino, G.; Savaglio, C.; Palau, C.E.; de Puga, J.S.; Ganzha, M.; Paprzycki, M.; Montesinos, M.; Liotta, A.; Llop, M. Towards Multi-layer Interoperability of Heterogeneous IoT Platforms: The INTER-IoT Approach. In Integration, Interconnection, and Interoperability of IoT Systems; Internet of Things (Technology, Communications and Computing); Springer International Publishing: Berlin/Heidelberg, Germany, 2018; pp. 199–232. [Google Scholar] [CrossRef]
- Noura, M.; Atiquzzaman, M.; Gaedke, M. Interoperability in Internet of Things: Taxonomies and Open Challenges. Mob. Netw. Appl. 2019, 24, 796–809. [Google Scholar] [CrossRef]
- Costa, B.; Pires, P.F.; Delicato, F.C. Towards the adoption of OMG standards in the development of SOA-based IoT systems. J. Syst. Softw. 2020, 169, 110720. [Google Scholar] [CrossRef]
- Marks, E.A.; Bell, M. Service-Oriented Architecture; John Wiley & Sons, Inc.: Hoboken, NJ, USA, 2012. [Google Scholar] [CrossRef]
- Kosanke, K. ISO Standards for Interoperability: A Comparison. In Interoperability of Enterprise Software and Applications; Konstantas, D., Bourrières, J.P., Léonard, M., Boudjlida, N., Eds.; Springer: London, UK, 2006; pp. 55–64. [Google Scholar] [CrossRef]
- Razzaque, M.A.; Milojevic-Jevric, M.; Palade, A.; Clarke, S. Middleware for Internet of Things: A Survey. IEEE Internet Things J. 2016, 3, 70–95. [Google Scholar] [CrossRef]
- Lu, Y. Industry 4.0: A survey on technologies, applications and open research issues. J. Ind. Inf. Integr. 2017, 6, 1–10. [Google Scholar] [CrossRef]
- Tran, K.P. Artificial Intelligence for Smart Manufacturing: Methods and Applications. Sensors 2021, 21, 5584. [Google Scholar] [CrossRef]
- Chen, Y. A Survey on Industrial Information Integration 2016–2019. J. Ind. Integr. Manag. 2020, 5, 33–163. [Google Scholar] [CrossRef]
- Hejazi, H.; Rajab, H.; Cinkler, T.; Lengyel, L. Survey of platforms for massive IoT. In Proceedings of the 2018 IEEE International Conference on Future IoT Technologies (Future IoT), Eger, Hungary, 18–19 January 2018; pp. 1–8. [Google Scholar] [CrossRef]
- Schneider, M.; Hippchen, B.; Abeck, S.; Jacoby, M.; Herzog, R. Enabling IoT Platform Interoperability Using a Systematic Development Approach by Example. In Proceedings of the 2018 Global Internet of Things Summit (GIoTS), Bilbao, Spain, 4–7 June 2018; pp. 1–6. [Google Scholar] [CrossRef]
- Sill, A. Standards at the Edge of the Cloud. IEEE Cloud Comput. 2017, 4, 63–67. [Google Scholar] [CrossRef]
- Alsboui, T.; Qin, Y.; Hill, R.; Al-Aqrabi, H. Distributed Intelligence in the Internet of Things: Challenges and Opportunities. SN Comput. Sci. 2021, 2, 277. [Google Scholar] [CrossRef]
- López, E.J.; Jiménez, F.C.; Sandoval, G.L.; Estrella, F.J.O.; Monteón, M.A.M.; Muñoz, F.; Leyva, P.A.L. Technical Considerations for the Conformation of Specific Competences in Mechatronic Engineers in the Context of Industry 4.0 and 5.0. Processes 2022, 10, 1445. [Google Scholar] [CrossRef]
- Tayur, V.M.; Suchithra, R. Review of interoperability approaches in application layer of Internet of Things. In Proceedings of the 2017 International Conference on Innovative Mechanisms for Industry Applications (ICIMIA), Bengaluru, India, 21–23 February 2017; pp. 322–326. [Google Scholar] [CrossRef]
- European Commission. The Future Internet Platform FIWARE. Available online: https://ec.europa.eu/digital-single-market/en/future-internet-public-private-partnership (accessed on 23 August 2018).
- FIWARE. FIWARE Catalogue. Available online: https://github.com/FIWARE/catalogue (accessed on 25 November 2021).
- Abid, M.A.; Afaqui, N.; Khan, M.A.; Akhtar, M.W.; Malik, A.W.; Munir, A.; Ahmad, J.; Shabir, B. Evolution towards Smart and Software-Defined Internet of Things. AI 2022, 3, 100–123. [Google Scholar] [CrossRef]
- Ngu, A.H.H.; Gutierrez, M.; Metsis, V.; Nepal, S.; Sheng, M.Z. IoT Middleware: A Survey on Issues and Enabling technologies. IEEE Internet Things J. 2016, 4, 1–20. [Google Scholar] [CrossRef]
- Zhang, J.; Ma, M.; Wang, P.; dong Sun, X. Middleware for the Internet of Things: A survey on requirements, enabling technologies, and solutions. J. Syst. Archit. 2021, 117, 02098. [Google Scholar] [CrossRef]
- Xia, F. QoS Challenges and Opportunities in Wireless Sensor/Actuator Networks. Sensors 2008, 8, 1099–1110. [Google Scholar] [CrossRef]
- Kuehnel, K.; Au-Yong-Oliveira, M. The Development of an Information Technology Architecture for Automated, Agile and Versatile Companies with Ecological and Ethical Guidelines. Informatics 2022, 9, 37. [Google Scholar] [CrossRef]
- Shaikh, A.; Reshan, M.S.A.; Sulaiman, A.; Alshahrani, H.; Asiri, Y. Secure Telemedicine System Design for COVID-19 Patients Treatment Using Service Oriented Architecture. Sensors 2022, 22, 952. [Google Scholar] [CrossRef]
- Avila, K.; Sanmartin, P.; Jabba, D.; Jimeno, M. Applications Based on Service-Oriented Architecture (SOA) in the Field of Home Healthcare. Sensors 2017, 17, 1703. [Google Scholar] [CrossRef]
- Chen, I.R.; Guo, J.; Bao, F. Trust Management for SOA-Based IoT and Its Application to Service Composition. IEEE Trans. Serv. Comput. 2016, 9, 482–495. [Google Scholar] [CrossRef]
- Ochs, J.; Biermann, F.; Piotrowski, T.; Erkens, F.; Nießing, B.; Herbst, L.; König, N.; Schmitt, R.H. Fully Automated Cultivation of Adipose-Derived Stem Cells in the StemCellDiscovery—A Robotic Laboratory for Small-Scale, High-Throughput Cell Production Including Deep Learning-Based Confluence Estimation. Processes 2021, 9, 575. [Google Scholar] [CrossRef]
- Kyösti, P.; Lindström, J. SOA-Based Platform Use in Development and Operation of Automation Solutions: Challenges, Opportunities, and Supporting Pillars towards Emerging Trends. Appl. Sci. 2022, 12, 1074. [Google Scholar] [CrossRef]
- Niknejad, N.; Ismail, W.; Ghani, I.; Nazari, B.; Bahari, M.; Hussin, A.R.B.C. Understanding Service-Oriented Architecture (SOA): A systematic literature review and directions for further investigation. Inf. Syst. 2020, 91, 101491. [Google Scholar] [CrossRef]
- Tiburski, R.T.; Amaral, L.A.; Matos, E.D.; Hessel, F. The importance of a standard security architecture for SOA-based iot middleware. IEEE Commun. Mag. 2015, 53, 20–26. [Google Scholar] [CrossRef]
- Suljkanović, A.; Milosavljević, B.; Inđić, V.; Dejanović, I. Developing Microservice-Based Applications Using the Silvera Domain-Specific Language. Appl. Sci. 2022, 12, 6679. [Google Scholar] [CrossRef]
- Raj, V.; Sadam, R. Performance and complexity comparison of service oriented architecture and microservices architecture. Int. J. Commun. Netw. Distrib. Syst. 2021, 27, 100–117. [Google Scholar] [CrossRef]
- Zhu, W.; Zhou, G.; Yen, I.L.; Bastani, F. A PT-SOA Model for CPS/IoT Services. In Proceedings of the 2015 IEEE International Conference on Web Services, New York, NY, USA, 27 June–2 July 2015. [Google Scholar] [CrossRef]
- Uviase, O.; Kotonya, G. IoT Architectural Framework: Connection and Integration Framework for IoT Systems. Electron. Proc. Theor. Comput. Sci. 2018, 264, 1–17. [Google Scholar] [CrossRef]
- W3C Semantic Sensor Network Incubator Group. Semantic Sensor Network Ontology. Available online: https://www.w3.org/2005/Incubator/ssn/ssnx/ssn (accessed on 25 November 2021).
- W3C. Web of Things (WoT) Architecture. Available online: https://www.w3.org/TR/wot-architecture/ (accessed on 25 November 2021).
- ISO. ISO/IEC 30161:2020-Internet of Things (IoT) — Requirements of IoT Data Exchange Platform for Various IoT Services. Available online: https://www.iso.org/standard/53281.html (accessed on 25 November 2021).
- ETSI. Smart Appliances and SAREF. Available online: https://www.etsi.org/technologies/smart-appliances (accessed on 25 November 2021).
- Balaji, S.; Salih, A.; Al-Atroshi, C. Adaptability of SOA in IoT Services—An Empirical Survey. Int. J. Comput. Appl. 2018, 182, 25–28. [Google Scholar] [CrossRef]
- Bandyopadhyay, S.; Sengupta, M.; Maiti, S.; Dutta, S. Role Of Middleware For Internet Of Things: A Study. Int. J. Comput. Sci. Eng. Surv. 2011, 2, 94–105. [Google Scholar] [CrossRef]
- Alfalouji, Q.; Schranz, T.; Kümpel, A.; Schraven, M.; Storek, T.; Gross, S.; Monti, A.; Müller, D.; Schweiger, G. IoT Middleware Platforms for Smart Energy Systems: An Empirical Expert Survey. Buildings 2022, 12, 526. [Google Scholar] [CrossRef]
- Palade, A.; Cabrera, C.; Li, F.; White, G.; Razzaque, M.A.; Clarke, S. Middleware for internet of things: An evaluation in a small-scale IoT environment. J. Reliab. Intell. Environ. 2018, 4, 3–23. [Google Scholar] [CrossRef]
- da Cruz, M.A.A.; Rodrigues, J.J.P.C.; Sangaiah, A.K.; Al-Muhtadi, J.; Korotaev, V. Performance evaluation of IoT middleware. J. Netw. Comput. Appl. 2018, 109, 53–65. [Google Scholar] [CrossRef]
- FIWARE. Orion Context Broker. Available online: https://fiware-orion.readthedocs.io/ (accessed on 14 August 2022).
- Martigne, P. Overview of ETSI machine-to-machine and oneM2M architectures. In Machine-to-Machine (M2M) Communications; Elsevier: Amsterdam, The Netherlands, 2015; pp. 27–46. [Google Scholar] [CrossRef]
- Pereira, C.; Pinto, A.; Aguiar, A.; Rocha, P.; Santiago, F.; Sousa, J. IoT interoperability for actuating applications through standardised M2M communications. In Proceedings of the 2016 IEEE 17th International Symposium on A World of Wireless, Mobile and Multimedia Networks (WoWMoM), Coimbra, Portugal, 21–24 June 2016; pp. 1–6. [Google Scholar] [CrossRef]
- Cardoso, J.; Pereira, C.; Aguiar, A.; Morla, R. Benchmarking IoT middleware platforms. In Proceedings of the 2017 IEEE 18th International Symposium on A World of Wireless, Mobile and Multimedia Networks (WoWMoM), Macau, China, 12–15 June 2017; pp. 1–7. [Google Scholar] [CrossRef]
- Arndt, M.; Koss, J. ETSI M2M Horizontal Platform Strategy; Technical Report; ETSI: Sophia Antipolis, France, 2014. [Google Scholar]
- Lee, E.A. Accessors: What Are Accessors? Available online: https://ptolemy.berkeley.edu/accessors (accessed on 28 November 2021).
- Accessors. Available online: https://wiki.eecs.berkeley.edu/accessors/Version1/AccessorSpecification (accessed on 14 August 2022).
- Gama, K.; Touseau, L.; Donsez, D. Combining heterogeneous service technologies for building an Internet of Things middleware. Comput. Commun. 2012, 35, 405–417. [Google Scholar] [CrossRef]
- Mynzhasova, A.; Radojicic, C.; Heinz, C.; Kolsch, J.; Grimm, C.; Rico, J.; Dickerson, K.; Garcia-Castro, R.; Oravec, V. Drivers, standards and platforms for the IoT: Towards a digital VICINITY. In Proceedings of the 2017 Intelligent Systems Conference (IntelliSys), London, UK, 7–8 September 2017; pp. 170–176. [Google Scholar] [CrossRef]
- Lyaskov, M.; Spasov, G.; Petrova, G. A practical implementation of smart home energy data storage and control application based on cloud services. In Proceedings of the 2017 XXVI International Scientific Conference Electronics (ET), Sozopol, Bulgaria, 13–15 September 2017; pp. 1–4. [Google Scholar] [CrossRef]
- DeviceHive. Three Steps To IoT. Available online: https://docs.devicehive.com/docs (accessed on 14 August 2022).
- Protic, A.; Jin, Z.; Marian, R.; Abd, K.; Campbell, D.; Chahl, J. Implementation of a Bi-Directional Digital Twin for Industry 4 Labs in Academia: A Solution Based on OPC UA. In Proceedings of the 2020 IEEE International Conference on Industrial Engineering and Engineering Management (IEEM), Singapore, 14–17 December 2020; pp. 979–983. [Google Scholar] [CrossRef]
- Automation, I. Solving SCADA Pain Points: Why SCADA Is Broken & How Ignition Can Fix It. Available online: https://inductiveautomation.com/static/pdf/Solving_SCADA_Pain_Points_04-17-2018.pdf (accessed on 28 November 2021).
- Automation, I. Diagnostics-Metrics Dashboard. Available online: https://docs.inductiveautomation.com/display/DOC81/Diagnostics+-+Metrics+Dashboard (accessed on 14 August 2022).
- Balaji, S.; Nathani, K.; Santhakumar, R. IoT Technology, Applications and Challenges: A Contemporary Survey. Wirel. Pers. Commun. 2019, 108, 363–388. [Google Scholar] [CrossRef]
- Menzel, L.M. Investigating the Adoption and Management of Metrics in Large-Scale Agile Software Development at a German IT-Provider. Master’s Thesis, Technische Universitatat Munchen, Munich, Germany, 2021. [Google Scholar]
- Osório, A.L.; Camarinha-Matos, L.M.; Afsarmanesh, H.; Belloum, A. On Reliable Collaborative Mobility Services. In IFIP Advances in Information and Communication Technology; Camarinha-Matos, L.M., Afsarmanesh, H., Rezgui, Y., Eds.; Springer International Publishing: Berlin/Heidelberg, Germany, 2018; pp. 297–311. [Google Scholar] [CrossRef]
- Razzaq, M.A.; Habib, S.; Ali, M.; Ullah, S. Security Issues in the Internet of Things (IoT): A Comprehensive Study. Int. J. Adv. Comput. Sci. Appl. 2017, 8, 383–388. [Google Scholar] [CrossRef]
- Shaikh, E.; Mohiuddin, I.; Manzoor, A. Internet of Things (IoT): Security and Privacy Threats. In Proceedings of the 2019 2nd International Conference on Computer Applications & Information Security (ICCAIS), Riyadh, Saudi Arabia, 1–3 May 2019; pp. 1–6. [Google Scholar] [CrossRef]
- Gritzalis, D.A.; Pantziou, G.; Román-Castro, R. Sensors Cybersecurity. Sensors 2021, 21, 1762. [Google Scholar] [CrossRef]
- Saif, I.; Peasley, S.; Perinkolam, A. Safeguarding the Internet of Things; Technical Report 17; Deloitte Review: Chiyoda, Tokyo, 2015. [Google Scholar]
- Mai, J.; Du, J. BGP performance analysis for large scale VPN. In Proceedings of the 2013 IEEE Third International Conference on Information Science and Technology (ICIST), Yangzhou, China, 23–25 March 2013. [Google Scholar] [CrossRef]
- Lagsaiar, L.; Shahrour, I.; Aljer, A.; Soulhi, A. Modular Software Architecture for Local Smart Building Servers. Sensors 2021, 21, 5810. [Google Scholar] [CrossRef]
- Corista, P.; Ferreira, D.; Giao, J.; Sarraipa, J.; Goncalves, R.J. An IoT Agriculture System Using FIWARE. In Proceedings of the 2018 IEEE International Conference on Engineering, Technology and Innovation (ICE/ITMC), Stuttgart, Germany, 17–20 June 2018; pp. 1–6. [Google Scholar] [CrossRef]
- FIWARE. Ngsijs Documentation. Available online: https://conwetlab.github.io/ngsijs/stable/index.html (accessed on 9 March 2019).
- Information Catalyst for Enterpresi LTD. Virtual Factory Open Operating System-CORDIS. Available online: https://cordis.europa.eu/project/id/723710 (accessed on 7 October 2021).
- FIWARE. FIWARE Contribution Requirements. Available online: https://fiware-requirements.readthedocs.io/en/latest/ (accessed on 14 September 2021).
- Chan, C. Autoscaling Cloud-Native Applications using Custom Controller of Kubernetes. Master’s Thesis, National College of Ireland, Dublin, UK, 2021. [Google Scholar]
- Chen, T.; Shang, W.; Yang, J.; Hassan, A.E.; Godfrey, M.W.; Nasser, M.; Flora, P. An Empirical Study on the Practice of Maintaining Object-Relational Mapping Code in Java Systems. In Proceedings of the 2016 IEEE/ACM 13th Working Conference on Mining Software Repositories (MSR), Austin, TX, USA, 14–15 May 2016; IEEE: New York, NY, USA; Los Alamitos, CA, USA, 2016; pp. 165–176. [Google Scholar]
- Merkel, D. Docker: Lightweight Linux containers for consistent development and deployment. Linux J. 2014, 239, 2. [Google Scholar]
- Stubbs, J.; Moreira, W.; Dooley, R. Distributed Systems of Microservices Using Docker and Serfnode. In Proceedings of the 2015 7th International Workshop on Science Gateways, Budapest, Hungary, 3–5 June 2015; pp. 34–39. [Google Scholar] [CrossRef]
- Weber, R.H. Internet of Things-New security and privacy challenges. Comput. Law Secur. Rev. 2010, 26, 23–30. [Google Scholar] [CrossRef]
- Nazarenko, A.A.; Lopes, C.; Ferreira, J.; Usher, P.; Sarraipa, J. ZDMP Core Services and Middleware. In Proceedings of the Workshops of I-ESA 2020, Tarbes, France, 17–19 November 2020. [Google Scholar]
- ZDMP Consortium. WP2 Business Challenge: Vision, Market, Use Cases, and Interlinking-D2.5a: Regulation and Trustworthy System-Vs: 1.0.1. Technical Report. 2020. Available online: https://www.zdmp.eu/_files/ugd/f83381_2bc34c64f6fb4e708d8a507e94f86de7.pdf (accessed on 28 July 2022).
- vf-OS Consortium. WP3: Virtual Factory System Kernel D3.1c: WP3 Umbrella Deliverable-Vs: 1.0. Technical Report. 2018. Available online: https://ec.europa.eu/research/participants/documents/downloadPublic?documentIds=080166e5ce27dd89&appId=PPGMS (accessed on 28 July 2022).
- Giao, J.; Sarraipa, J.; Jardim-Gonçalves, R. Open Modular Components in the Industry Using vf-OS Components. In DoCEIS 2019: Technological Innovation for Industry and Service Systems; IFIP Advances in Information and Communication Technology; Springer: Cham, Switzerland, 2019; Volume 553, pp. 238–246. [Google Scholar] [CrossRef]
- Yelamarthi, K.; Aman, M.S.; Abdelgawad, A. An Application-Driven Modular IoT Architecture. Wirel. Commun. Mob. Comput. 2017, 2017, 1–16. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Baheti, R.; Gill, H. Cyber-Physical Systems. In The Impact of Control Technology; IEEE Control Systems Society: New York, NY, USA, 2011; Cross-Cutting Research Directions; pp. 161–166. [Google Scholar]









| Name | Communication Interface | Metrics | Plug-and-Play | Instantiation | Installed Service Isolation | User Interface |
|---|---|---|---|---|---|---|
| Orion | NGSI | Yes | Yes | No | Yes | No |
| ETSI M2M | REST | No | No | N/A | Yes | Option available |
| Ptolemy Accessor Host | HTTP | No | No | Yes | Yes | Yes |
| DeviceHive | EST, Websockets, MQTT | No | No | Yes | Yes | No |
| NodeRED | HTTP, MQTT, OPC UA | Yes | Yes | No | No | Yes |
| Ignition | OPA UA, related APIs | Yes | Yes | Yes | Yes | Yes |
| Proposed Solution | REST, NGSI | Yes | Yes | Yes | Yes | Yes |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Giao, J.; Nazarenko, A.A.; Luis-Ferreira, F.; Gonçalves, D.; Sarraipa, J. A Framework for Service-Oriented Architecture (SOA)-Based IoT Application Development. Processes 2022, 10, 1782. https://doi.org/10.3390/pr10091782
Giao J, Nazarenko AA, Luis-Ferreira F, Gonçalves D, Sarraipa J. A Framework for Service-Oriented Architecture (SOA)-Based IoT Application Development. Processes. 2022; 10(9):1782. https://doi.org/10.3390/pr10091782
Chicago/Turabian StyleGiao, Joao, Artem A. Nazarenko, Fernando Luis-Ferreira, Diogo Gonçalves, and Joao Sarraipa. 2022. "A Framework for Service-Oriented Architecture (SOA)-Based IoT Application Development" Processes 10, no. 9: 1782. https://doi.org/10.3390/pr10091782
APA StyleGiao, J., Nazarenko, A. A., Luis-Ferreira, F., Gonçalves, D., & Sarraipa, J. (2022). A Framework for Service-Oriented Architecture (SOA)-Based IoT Application Development. Processes, 10(9), 1782. https://doi.org/10.3390/pr10091782