Dynamic Signature Verification Technique for the Online and Offline Representation of Electronic Signatures in Biometric Systems
Abstract
:1. Introduction
2. Related Works
Motivation
3. Proposed Technique
3.1. Dynamic Signature Verification
3.2. Classification through Mutual Service
4. Discussion
4.1. Verification Instances and Authentication Lag
4.2. Mutual Time Analysis
4.3. Metric Comparisons
4.3.1. Authentication Success Rate
4.3.2. Verification Failure Ratio
4.3.3. Verification Time
4.3.4. Complexity
4.3.5. Authentication Lag
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Stylios, I.; Kokolakis, S.; Thanou, O.; Chatzis, S. Behavioral biometrics & continuous user authentication on mobile devices: A survey. Inf. Fusion 2021, 66, 76–99. [Google Scholar]
- Wang, P.; You, L.; Hu, G.; Hu, L.; Jian, Z.; Xing, C. Biometric key generation based on generated intervals and two-layer error correcting technique. Pattern Recognit. 2021, 111, 107733. [Google Scholar] [CrossRef]
- Dwivedi, R.; Dey, S.; Sharma, M.A.; Goel, A. A fingerprint based crypto-biometric system for secure communication. J. Ambient Intell. Humaniz. Comput. 2020, 11, 1495–1509. [Google Scholar] [CrossRef] [Green Version]
- Mehraj, H.; Mir, A.H. A multi-biometric system based on multi-level hybrid feature fusion. Her. Russ. Acad. Sci. 2021, 91, 176–196. [Google Scholar] [CrossRef]
- Farooq, H.; Naaz, S. Performance analysis of biometric recognition system based on palmprint. Int. J. Inf. Technol. 2020, 12, 1281–1289. [Google Scholar] [CrossRef]
- Okawa, M. Online signature verification using single-template matching with time-series averaging and gradient boosting. Pattern Recognit. 2020, 102, 107227. [Google Scholar] [CrossRef]
- Alpar, O. Signature barcodes for online verification. Pattern Recognit. 2022, 124, 108426. [Google Scholar] [CrossRef]
- Najda, D.; Saeed, K. Impact of augmentation methods in online signature verification. Innov. Syst. Softw. Eng. 2022, 1–7. [Google Scholar] [CrossRef]
- Tsourounis, D.; Theodorakopoulos, I.; Zois, E.N.; Economou, G. From text to signatures: Knowledge transfer for efficient deep feature learning in offline signature verification. Expert Syst. Appl. 2022, 189, 116136. [Google Scholar] [CrossRef]
- Batool, F.E.; Attique, M.; Sharif, M.; Javed, K.; Nazir, M.; Abbasi, A.A.; Iqbal, Z.; Riaz, N. Offline signature verification system: A novel technique of fusion of GLCM and geometric features using SVM. Multimed. Tools Appl. 2020, 1–20. [Google Scholar] [CrossRef]
- Malik, J.; Elhayek, A.; Guha, S.; Ahmed, S.; Gillani, A.; Stricker, D. Deepairsig: End-to-end deep learning based in-air signature verification. IEEE Access 2020, 8, 195832–195843. [Google Scholar] [CrossRef]
- Sadak, M.S.; Kahraman, N.; Uludağ, U. Dynamic and static feature fusion for increased accuracy in signature verification. Signal Process. Image Commun. 2022, 108, 116823. [Google Scholar] [CrossRef]
- Guerra-Segura, E.; Ortega-Pérez, A.; Travieso, C.M. In-air signature verification system using leap motion. Expert Syst. Appl. 2021, 165, 113797. [Google Scholar] [CrossRef]
- Yapıcı, M.M.; Tekerek, A.; Topaloğlu, N. Deep learning-based data augmentation method and signature verification system for offline handwritten signature. Pattern Anal. Appl. 2021, 24, 165–179. [Google Scholar] [CrossRef]
- Longjam, T.; Kisku, D.R.; Gupta, P. Multi-scripted Writer Independent Off-line Signature Verification using Convolutional Neural Network. Multimed. Tools Appl. 2022, 1–18. [Google Scholar] [CrossRef]
- Tolosana, R.; Vera-Rodriguez, R.; Fierrez, J.; Ortega-Garcia, J. DeepSign: Deep on-line signature verification. IEEE Trans. Biom. Behav. Identity Sci. 2021, 3, 229–239. [Google Scholar] [CrossRef]
- Bassit, A.; Hahn, F.; Peeters, J.; Kevenaar, T.; Veldhuis, R.; Peter, A. Fast and Accurate Likelihood Ratio-Based Biometric Verification Secure against Malicious Adversaries. IEEE Trans. Inf. Secur. 2021, 16, 5045–5060. [Google Scholar] [CrossRef]
- Ponce-Hernandez, W.; Blanco-Gonzalo, R.; Liu-Jimenez, J.; Sanchez-Reillo, R. Fuzzy vault scheme based on fixed-length templates applied to dynamic signature verification. IEEE Access 2020, 8, 11152–11164. [Google Scholar] [CrossRef]
- Yang, W.; Wang, S.; Kang, J.J.; Johnstone, M.N.; Bedari, A. A linear convolution-based cancelable fingerprint biometric authentication system. Comput. Secur. 2022, 114, 102583. [Google Scholar] [CrossRef]
- Parcham, E.; Ilbeygi, M.; Amini, M. CBCapsNet: A novel writer-independent offline signature verification model using a CNN-based architecture and capsule neural networks. Expert Syst. Appl. 2021, 185, 115649. [Google Scholar] [CrossRef]
- Okawa, M. Time-series averaging and local stability-weighted dynamic time warping for online signature verification. Pattern Recognit. 2021, 112, 107699. [Google Scholar] [CrossRef]
- Dhieb, T.; Boubaker, H.; Njah, S.; Ben Ayed, M.; Alimi, A.M. A novel biometric system for signature verification based on score level fusion approach. Multimed. Tools Appl. 2022, 81, 7817–7845. [Google Scholar] [CrossRef]
- Naz, S.; Bibi, K.; Ahmad, R. DeepSignature: Fine-tuned transfer learning based signature verification system. Multimed. Tools Appl. 2022, 81, 38113–38122. [Google Scholar] [CrossRef]
- Yang, X.; Zhu, H.; Wang, F.; Zhang, S.; Lu, R.; Li, H. MASK: Efficient and privacy-preserving m-tree based biometric identification over cloud. Peer—Peer Netw. Appl. 2021, 14, 2171–2186. [Google Scholar] [CrossRef]
- Houtinezhad, M.; Ghaffari, H.R. Off-line signature verification system using features linear mapping in the candidate points. Multimed. Tools Appl. 2022, 81, 24815–24847. [Google Scholar] [CrossRef]
- Roy, S.; Sarkar, D.; Malakar, S.; Sarkar, R. Offline signature verification system: A graph neural network based approach. J. Ambient. Intell. Humaniz. Comput. 2021, 1–11. [Google Scholar] [CrossRef]
- Tan, H.; He, L.; Huang, Z.C.; Zhan, H. Online signature verification based on dynamic features from gene expression programming. Multimed. Tools Appl. 2021, 1–27. [Google Scholar] [CrossRef]
- Saleem, M.; Kovari, B. Online signature verification using signature down-sampling and signer-dependent sampling frequency. Neural Comput. Appl. 2021, 1–13. [Google Scholar] [CrossRef]
- Available online: https://www.ncbi.nlm.nih.gov/pmc/articles/PMC7725742/ (accessed on 25 September 2022).

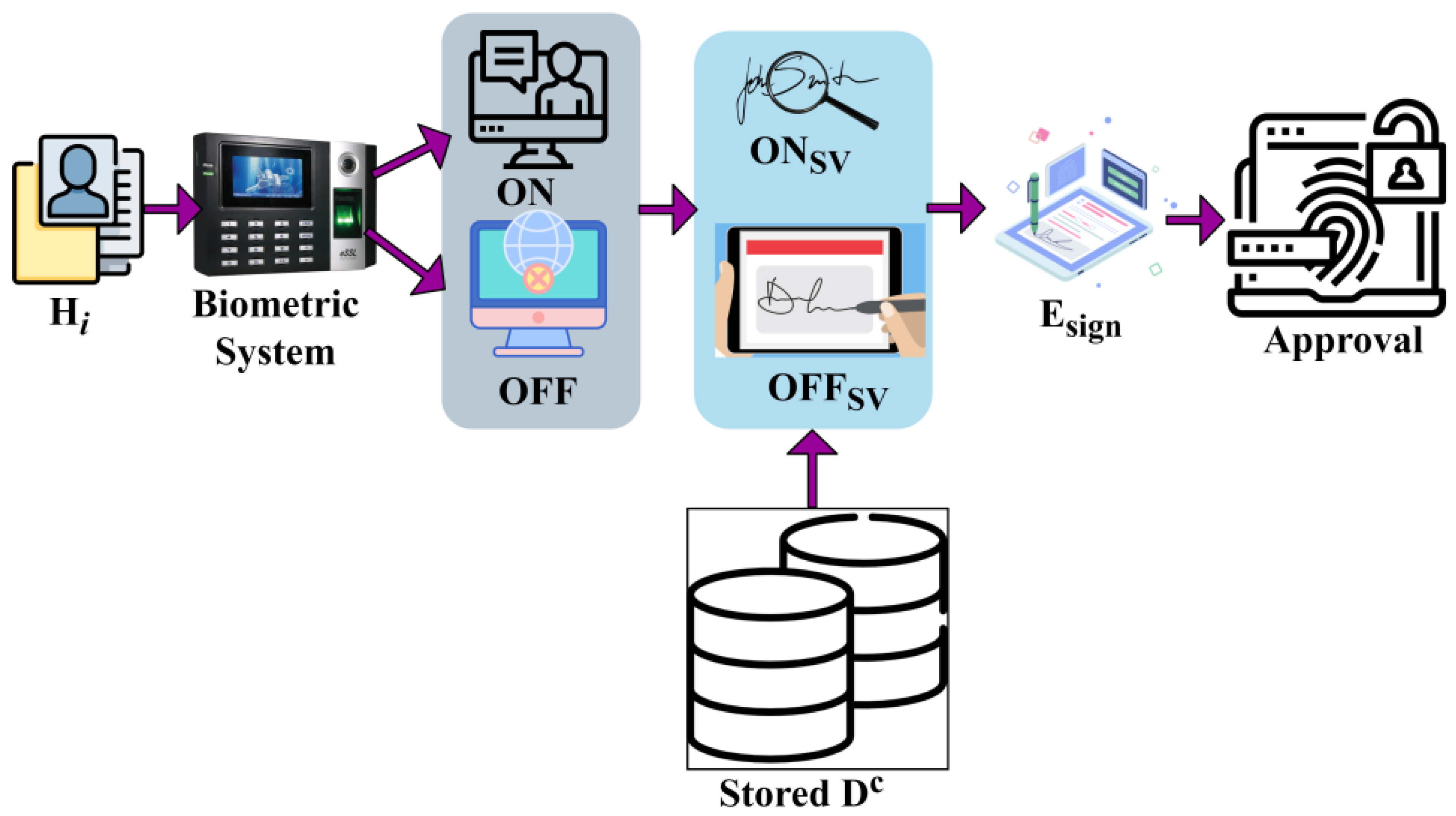












| Step 1: | Obtain inputs from users (input, biometric, and signature-type inputs) |
| Step 2: | Generate a digital signature for every user before accessing the information |
| Step 3: | Security system verifies the user’s signature both offline and online using Equation (1) |
| Step 4: | Compute the mutual authentication/verification by generating the signature using Equations (2)–(4) |
| Step 5: | Validate the generated signature using Equations (5) and (6) |
| Step 6: | Approve the signature and biometric traits using Equations (7) and (8) |
| Step 7: | After performing the mutual verification, services are classified |
| Step 8: | Then, user-given information verification is performed |
| Step 9: | Finally, permission is given to the user to access the information. |
| Metrics | FV-DSV | MASK | DeepSign | DSVT-MC |
|---|---|---|---|---|
| Success Rate | 0.882 | 0.898 | 0.921 | 0.9375 |
| Failure Ratio | 11.75 | 9.27 | 6.91 | 4.544 |
| Verification Time (s) | 4.152 | 3.124 | 2.105 | 1.2379 |
| Complexity (s) | 1.45 | 1.02 | 0.518 | 0.2299 |
| Authentication Lag | 8 | 6 | 5 | 3 |
| Metrics | FV-DSV | MASK | DeepSign | DSVT-MC |
|---|---|---|---|---|
| Success Rate | 0.893 | 0.902 | 0.919 | 0.9373 |
| Failure Ratio | 8.58 | 6.77 | 4.31 | 2.386 |
| Verification Time (s) | 4.089 | 2.996 | 1.86 | 1.0467 |
| Complexity (s) | 1.42 | 1.02 | 0.48 | 0.2513 |
| Authentication Lag | 8 | 6 | 4 | 3 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Huang, J.; Xue, Y.; Liu, L. Dynamic Signature Verification Technique for the Online and Offline Representation of Electronic Signatures in Biometric Systems. Processes 2023, 11, 190. https://doi.org/10.3390/pr11010190
Huang J, Xue Y, Liu L. Dynamic Signature Verification Technique for the Online and Offline Representation of Electronic Signatures in Biometric Systems. Processes. 2023; 11(1):190. https://doi.org/10.3390/pr11010190
Chicago/Turabian StyleHuang, Juanjuan, Yuhang Xue, and Linhui Liu. 2023. "Dynamic Signature Verification Technique for the Online and Offline Representation of Electronic Signatures in Biometric Systems" Processes 11, no. 1: 190. https://doi.org/10.3390/pr11010190




