1. Introduction
Until recently, improvements of the ICS could be categorized into two main aspects: on one hand, with integration into external networks, efficiency in production and management has been greatly enhanced; on the other hand, adopting commercial software and hardware has improved economic profiles. However, both of these aspects cause a large number of vulnerabilities and exposures to cyberattacks, which will lead to catastrophic consequences.
The past decade has witnessed a number of ICS security incidents, such as Stuxnet [
1], BlackEnergy [
2], WannaCry [
3], Triton [
4], and so on. Among them, Stuxnet was viewed as a milestone since the attackers could compromise a Programmable Logic Controller to launch a sophisticated cyberattack. Owing to its important role in controlling physical facilities, the security of PLC-based control systems is supposed to be emphasized.
No matter whether in academia or industry, work on the security of PLC-based control systems can be divided into two parts: one is to provide some detection schemes to improve security outside the PLC, such as intrusion detection and honeypots; the other is to design a security built-in PLC equipped with verified programs, trustworthy firmware, and a perfect communication protocol. The former is always for current systems or legacy ones; in contrast, the latter may be prepared for newly constructed production lines. Taking into consideration that current systems account for the majority of such instances, and that many industrial enterprises cannot afford the cost of production interruption and equipment replacement, more efforts should be made to improve the security of the PLC-based control systems in their current stage.
Besides, the current PLC itself has vulnerabilities in program verification, firmware, I/O memory, etc. Backdoors in general-purpose software and hardware, as well as flaws in communication protocols, are also introduced into the PLC-based control systems. Unfortunately, when attackers have access to certain industrial components, the aforementioned vulnerabilities could be exploited to form cyberattacks, e.g., command injection attacks, firmware modification attacks, memory corruption attacks, replay attacks, and so on. The increasing attack surfaces have the characteristics of being progress-oriented, stealthy, malicious, and sophisticated.
Based on existing vulnerabilities and attacks, research on the security detection scheme for the PLC-based control system has involved the perspectives of core-component defense and system-level defense, respectively. Compared with traditional Information Technology (IT) security schemes, keeping a balance between special industrial requirements and overall security is something that deserves to be considered. Diverse security solutions, such as code checking, firmware detection, traffic auditing, critical-state monitoring, etc., are bound to meet the industrial requirements, including real-time responses, continuous processing, frequent interactions, and high availability.
Meanwhile, the countermeasures should span the whole security lifecycle in the PLC-based systems. Differing from the solution mentioned above, digital forensic investigation of undesirable events is essential to the discovery of compromised components, internal or external attackers, malicious motivations, and skilled attack methods [
5]. Moreover, according to the results of forensic research, many suggestions can be abstracted to secure overall PLC-based control systems in the future, ranging from the core component level to the system level.
Although there are several literatures on the security of PLC-based control systems, they lack a comprehensive review on vulnerabilities, attacks, and security detection schemes, focusing on the PLC itself and its interactions with other components. We provide a survey that pays more attention to the security of current PLC-based control systems and contains four parts: vulnerability analysis, attack models, security detection schemes, and forensic research. For further research, suggestions are outlined to strengthen security in future PLC-based control systems.
The main contributions of this article are summarized as follows:
Compared with existing literature surveys on PLC-based control systems, the comprehensiveness of our work is demonstrated, containing vulnerabilities, attacks, security detection schemes, forensic research, and suggestions for the future of these systems;
We analyze the vulnerabilities from two perspectives: the PLC itself and its relevant control systems. For the PLC itself, we mainly take the program, memory, and firmware into consideration. For its relevant control systems, we focus on application software, communication protocols, and connected devices with PLC;
We provide the existing attacks on the PLC-based control systems in three categories, including attacks against availability, integrity, and confidentiality;
For current PLC-based control systems, we present security detection schemes that are classified as program detection, firmware detection, fingerprint-based detection, intrusion detection, and honeypot-based detection;
We discuss methodology, challenges, and achievements in forensic research for PLC-based control systems. For future construction of PLC-based control systems, six recommendations are outlined, concerning secure embedded systems, secure communication protocols, virtualization, open-source industrial control units, cloud-based or fog-based computing, and moving target defense (MTD).
As shown in
Figure 1,
Section 2 describes the background of the PLC and its relevant control systems, respectively. Our work is compared with existing surveys in
Section 3. Respectively,
Section 4 and
Section 5 provide vulnerabilities and attacks. Security detection schemes for current PLC-based control systems are presented in
Section 6.
Section 7 is used to discuss forensic research. We list some techniques or methods for future PLC-based control systems in
Section 8. Finally, conclusions are drawn in
Section 9. The list of acronyms used in the paper is given in
Table A2.
6. Security Detection Schemes
We discuss security detection schemes for PLC-based control systems in this section. Note that these schemes are all from the existing research articles. The classification is shown in
Figure 5. For the PLC itself, we introduced the security detection schemes, including program detection, firmware detection, and fingerprinting-based detection. Subsequently, from a system-level aspect, we provide intrusion detection as well as honeypot-based detection. It should be noted for readers that the rough classification is mainly for organizational reasons.
6.1. PLC Program Detection
Running states of PLC affect working states of the whole system, whereas the normal running of PLC depends on the inerrant operation of its logical program. Meanwhile, the PLC program is vulnerable to attacks such as the payload attack and the injection attack, which seriously violate security requirements and even cause serious physical damage. Therefore, program detection is a vital part of the PLC’s running state.
Initially, PLC program detection is more concerned with reliability, stability, and safety. As the ICS interconnected with the outside world via networks, the PLC program suffered from more network attacks, and the detection of its own security was given more attention by researchers. As a result, security problems are inseparable from safety issues. Therefore, an overview of program detection is demonstrated in this subsection. After that, we provided the detection methods for safety and security, respectively.
In general, our work is inspired by the hierarchy framework on compositional verification for PLC program detection stated in [
65]. The framework introduces program detection in three aspects, including code, model, and statute. Code-level verification focuses on the coding analysis. Mode-level verification focuses on dynamic behaviors. Statue-level verification focuses on static properties. Regarding the verification methodologies at the three levels, we discussed the impact of program detection on safety and security for the PLC program in the following sections.
6.1.1. Program Detection on Safety
Code-level detection: With the help of an Aachen Rigorous Code Analysis and Debugging Environment (ARCADE). PLC verification platform, Stattelmann et al. [
66] applied static code analysis to an industrial software development environment in engineering. Recently, Zhang et al. [
67] presented a static program analysis approach, named VETPLC, which built timed event causality graphs for causal relations among events in PLC code. Hence, it could be applied to automatically detect hidden safety violations;
Model-level detection: At this level, model checking is widely used in IT fields, where it constructs a formal model for the system and then explores the whole set of states in a brute-force manner in order to verify the property [
68]. We focus on the application of the methods in specific PLC programming languages and the application of some model checking tools in PLC-based control systems in the next subsection;
Statue-level detection: For statue-level detection, theorem proof is applied to the verification of the correctness of PLC programs in each scanning cycle. Coq is a theorem-proving tool based on the calculus of inductive constructions and excellent mathematical models. Xiao et al. [
69] defined the formal semantics of typical PLC programs with an extended
-calculus definition and provided a Coq-based verification.
From a practical point of view, the following three aspects deserve equal attention for PLC safe program detection: (1) Modular code makes it easier to test and track the integrity of code modules. For example, if the code within a module has been thoroughly tested, any copies of those modules will be checked against the hash of the source code. Verification will be useful if the integrity of the code is in question after an incident; (2) PLCs are not in “RUN” mode, and then the code can be changed. Some PLCs have a checksum to notify code changes. However, some legacy PLCs lack such a safety mechanism. For example, an alarm signal should be configured to warn operators at the end of a shift; (3) During code development, engineers need to test and validate their software modules by substituting data outside of expected boundaries. Assign different locked memory segments for firmware, logic, and the protocol stack in order to detect abuse.
6.1.2. Program Detection on Security
In our review, we found that researchers began to shift their interest from safety to security for PLC program detection after the year 2014. Combined with the symbol execution method, model checking could be applied to detecting attacks with the malicious PLC code. McLaughlin et al. [
70] proposed a trusted safety verifier, which is a trusted computing base for the verification of the PLC critical logic. The symbolic execution combined with the model checking algorithm provided a last-step verification of commands before reacting to actual controlled devices. In the same year, Zonouz et al. [
71] presented a similar method to detect malicious code bound to PLCs that did not violate the security requirements of the underlying physical factory. A temporal execution graph was built with symbolic execution outputs for modeling the PLC’s subsequent I/O.
Chang et al. [
72] presented a detection method of malicious behaviors by the state verification, which considered the sequence of input vectors. On the other hand, they removed duplicate executable paths in the same scan cycle to tackle the state space explosion problem. Moreover, the aforementioned tools were applied by researchers for PLC program detection as well. Modeling with NuSMV, Kottler et al. [
73] focused on verifying PLC programs in LD and ST languages to identify certain security vulnerabilities. Hailesellasie and Hasan [
74] proposed a scheme based on differences in the attributed graph between potentially compromised PLC programs and trusted ones. The graphs were generated from UPPAAL-based formal modeling.
Model checking cannot handle binary code directly. As a result, the reverse engineering techniques for the binary PLC codes deserve to be researched. Lv et al. [
75] proposed a decompiling framework that was suitable for the PLC program based on templates in the form of instructions or operands. Likewise, Keliris and Maniatakos [
76] developed an industrial control systems reverse engineering framework for reversing PLC binaries compiled with CODESYS, taking into consideration their unique domain-specific characteristics. Chang et al. [
77] disassembled the program into STL and then built a Control Flow Graph (CFG) to get a mapping between outputs and inputs. On the other hand, due to the fact that PLCs are vulnerable to control-flow hijacking attacks, the CFG, which is extracted from the binaries, is bound to be of great importance. Abbasi et al. [
78] introduced an embedded a Control Flow Integrity (CFI) mechanism named ECFI. In their work, they considered both real-time and runtime operations for real-world industrial PLCs.
6.2. PLC Firmware Detection
PLC firmware provides a link between the hardware and software. It has been proven that PLCs lack firmware auditing capabilities. Once the firmware is manipulated by attackers or malware, it can control other physical system components via the compromised PLCs. Therefore, firmware modification detection is extremely important for PLC-based control systems.
McMinn and Butts [
79] designed a firmware verification tool for the serial data while uploading. The tool could be applied to a variety of platforms without requiring any modifications to the existing PLC-based control systems. Furthermore, an approach to inferring the firmware update validation was proposed by Basnight et al. [
32] by using reverse engineering techniques. To detect stealthy firmware modifications like HARVEY, Garcia et al. [
33] gave suggestions: (1) allowing to check the PLC firmware integrity; (2) monitoring data from sensors to PLCs; (3) monitoring data from PLCs to actuators.
6.3. PLC Side-Channel Detection
Research has shown much unintentional information leakage from PLCs, such as radio frequency (RF) emissions, power consumption, electromagnetic (EM) emanations, and operation time. Such leakage information is usually obtained by a series of physical measurements from a side channel. Thus, side-channel analysis is a common method to detect malicious attacks or unintended operations in PLCs. We discuss four techniques for side-channel detection.
6.3.1. Radio-Frequency-Based Detection
In 2012, Stone and Temple [
80] proposed a RF-based methodology to detect anomalous operations of PLCs. After that, their research group improved the anomaly detection capability on the basis of the previous research by adopting Hilbert transformed sequences of unintentional time domain emissions of PLCs [
81]. Moreover, an additional advantage was that the standalone RF-based analysis system only depended on physical layer information from PLCs, which was isolated from network-based cyberattacks.
6.3.2. Power Fingerprinting Detection
Leveraging the power of fingerprinting, Gonzalez and Hinton [
82] presented a method to monitor PLCs and detect malicious software execution. However, it is not feasible for real-time monitoring because power fingerprinting was collected from a sensor that closely interacted with the CPU of PLCs. In other words, the exposure of CPUs to sensors and high-frequency data acquisition means burdens for PLCs. To overcome these limitations, Xiao et al. [
83] demonstrated a real-time detection method in a non-invasive way, relying on a resistor to collect power consumption traces.
6.3.3. Time-Based Detection
The above-mentioned techniques depended on the additional hardware to be added to PLC-based control systems, which made the approach complex. Using timing-based side channels, Dunlap et al. [
84] presented an approach to detect unauthorized modifications of PLCs by execution time measurements.
6.3.4. EM Emanation-Based Detection
Boggs et al. [
85] demonstrated the feasibility of EM emanation-based detection for code execution on PLC-based control systems. They separately monitored normal and abnormal activities via a signal cliff detection method. Likewise, Van Aubel et al. [
86] leveraged EM side-channel measurements for detecting behavior changes in an executing industrial software. Particularly, they suggested two layers of verification. The first layer checked the user program runtime, while its EM trace was compared with a baseline version in the second layer.
6.4. Intrusion Detection
With the existence of commercial general-purpose components and current communication protocols, PLC-based control systems are threatened by cyberattacks. Fortunately, intrusion detection is a solution to the cybersecurity threats. Depending on data sources, intrusion detection can be classified into network-based and host-based detection. In this subsection, we discuss the ongoing methods targeting ICS in the respective categories. Main findings is featured in
Table 3.
6.4.1. Network-Based Intrusion Detection
Network-based intrusion detection is necessary since cyberattack vectors are always hidden in the flow of network commands. There exists a kind of attack that contains multiple control commands, which are seemingly licit when viewed separately per packet, while they possibly breach the running states of the control systems. To detect the attacks, a critical-state analysis is presented to track a chain of packets changing the system states.
Furthermore, Deterministic Finite Automata (DFA) is a common method to provide a detailed traffic model for intrusion detection. For highly periodic Modbus/TCP traffic between HMIs and PLCs, Goldenberg and Wool developed DFA for each communication channel to detect anomalies sensitively [
87]. Based on the previous work, Faisal et al. [
89] proposed a complementary approach that combined the DFA with configuration-level specifications to monitor the communication. It effectively solved the problem that an appropriate amount of training data was required when retraining the model after the configuration changed. Interestingly, Markman et al. [
90] found that the HMI-PLC channel was filled with bursts of packets relating to semantic meaning. Thus, they suggested a new burst-DFA model to detect anomalies in the traffic, which fitted the data much better compared with previous work.
Researchers studied the targeting control process in the PLC-based control system through the detection of semantic attacks. The attacks were divided into three sub-types: reconnaissance, direct control, and indirect control [
88]. As a result, a semantic, network-based intrusion detection was presented by building a behavior model including constant, attribute, and continuous series. Deriving a set of expected values was used to model constant and attribute data. Modeling the continuous data leveraged techniques of autoregression and control limits.
6.4.2. Host-Based Intrusion Detection
Researchers model state values for intrusion detection, including the values of relevant PLC memory addresses or state transitions of the control system. Supervised and semi-supervised machine learning methodologies were used separately to identify exceptions or abnormal behavior [
91,
92]. Leveraging the values of relevant memory addresses along with timestamps, the model could be used to distinguish abnormal PLC operations. Introducing the concept of controller behavior whitelisting, two Petri Net (PN)-based anomaly detection approaches were proposed from the perspective of experimental validation. Firstly, they manually constructed a white list, which was modeled on the field devices by the PN, and then converted it to the LD with a constraint condition of the PN, which allowed the PLC to detect abnormal behaviors [
93]. However, there is a limitation to whitelisting in a manual way when the PLC-based control system is complex. To cope with the problem, they further presented an automatic generation method in which the representation of the whitelist used the SFC instead of the LD [
94].
In addition, self-parameters can be applied to detect malicious attacks. Hardware performance counters are a series of registers to maintain low-level hardware events, e.g., the number of instructions retired, cache operations and exceptions, and the number of branches taken. Krishnamurthy et al. [
95] modeled baseline behavior and then detected anomalies. It was suitable for the typical multi-threaded and interrupt-driven processes of PLCs. Combined with more parameters, a (k, l)-threshold signature scheme was developed by Chatterjee et al. [
96] by using a finite state machine. What stood out was that it could detect both corrupted PLCs and compromised states within their proposed protocol, especially for legacy PLCs.
From the perspective of engineering practice, the following four aspects need to be considered in terms of safety-reliability metrics while performing intrusion detection: (1) It is better to use a local data archive to analyze the process data. By comparing aggregated values (per period, per process cycle) with the overall aggregated values from the archive, the significant difference in values is a potential feature for detection; (2) The allowable range for setting a timer or counter must be limited to meet operational requirements. If a remote tool such as an HMI writes values to a timer or counter, it is feasible to detect the presets and timeout values in the PLC before the writing action; (3) Similarly, a default value in an acceptable operating range is configured for each input variable that does not adversely affect the process and can be used as a flag for warnings. If a PLC variable receives an out-of-bounds value, the last valid value is entered for this variable, and an event is logged for further detection analysis; (4) Paired inputs or outputs are signals that cannot physically turn on at the same time; they exclude each other. Direct validation of the status of the paired inputs in the PLC is effective in detecting fault or malicious activity.
6.5. Honeypot-Based Detection
Different from the passive methods described in the previous subsections, honeypot-based detection is a technique that is employed to monitor network state, collect data, and analyze threats. In relation to the security of PLC-based control systems, there are various honeypot features such as obfuscation, high-fidelity emulation, secure malware storage, and traffic redirection. Thanks to the results from honeypots, malicious intrusions and potential exploitations can be revealed before fatal attacks are launched. Hence, some researchers’ interest in security gradually shifts to honeypots for the PLC and its networks.
According to the interaction ability, the existing honeypots for PLCs could be mainly classified into two categories: low-interactive honeypots such as Conpot [
97], as well as high-interactive honeypots such as CryPLH [
98,
99], XPOT [
100], and S7COMMTrace [
101]. When honeypots are applied for ICS, researchers take into account the following key characteristics: performance, authenticity, scalability, cost, and risk. Although the Conpot supports seven kinds of protocols and limited function codes, it is easy for attackers to discover its fingerprint. To enhance the authenticity, CryPLH improved the interaction and added more original PLC implements. It was proven that the CryPLH was effectively deployed in real control networks to collect data. Compared with the CryPLH, S7COMMTrace had more sub-function codes in the protocol and higher fidelity simulation of PLCs, which reduced the risk of being discovered by cyberspace search engines like Shodan. Moreover, to achieve the further improvement of interactive capabilities, the PLC honeypot should support program compilation and interpretation. XPOT made it possible for the honeypot to be programmed with standard Integrated Development Environments (IDEs).
In short, we have discussed mainstream security detection schemes in the ongoing literature. Objectively speaking, there are also other security schemes to protect the ICS. For example, it is universally recognized that common PLC-based control systems are vulnerable to some types of access control attacks [
102]. Scholars might suggest the introduction of an entropy algorithm in the data transmission message part [
103] or a challenge-response authentication mechanism [
104]. However, the defense resources are ultimately limited, especially for the current control systems. The impacts of traffic entropy on the current ICS were also discussed, including high cost, undesirable performance, and so on [
105]. Besides, prevention capabilities against new threats or new attacks are weak because there are not enough security assessments. To some extent, some detection schemes have a more critical role than others [
106]. That is the reason why we emphasize security detection schemes in this subsection. We believe that the advanced defense techniques could be applied to future PLC-based control systems, which will be discussed in
Section 8.
8. Future Work
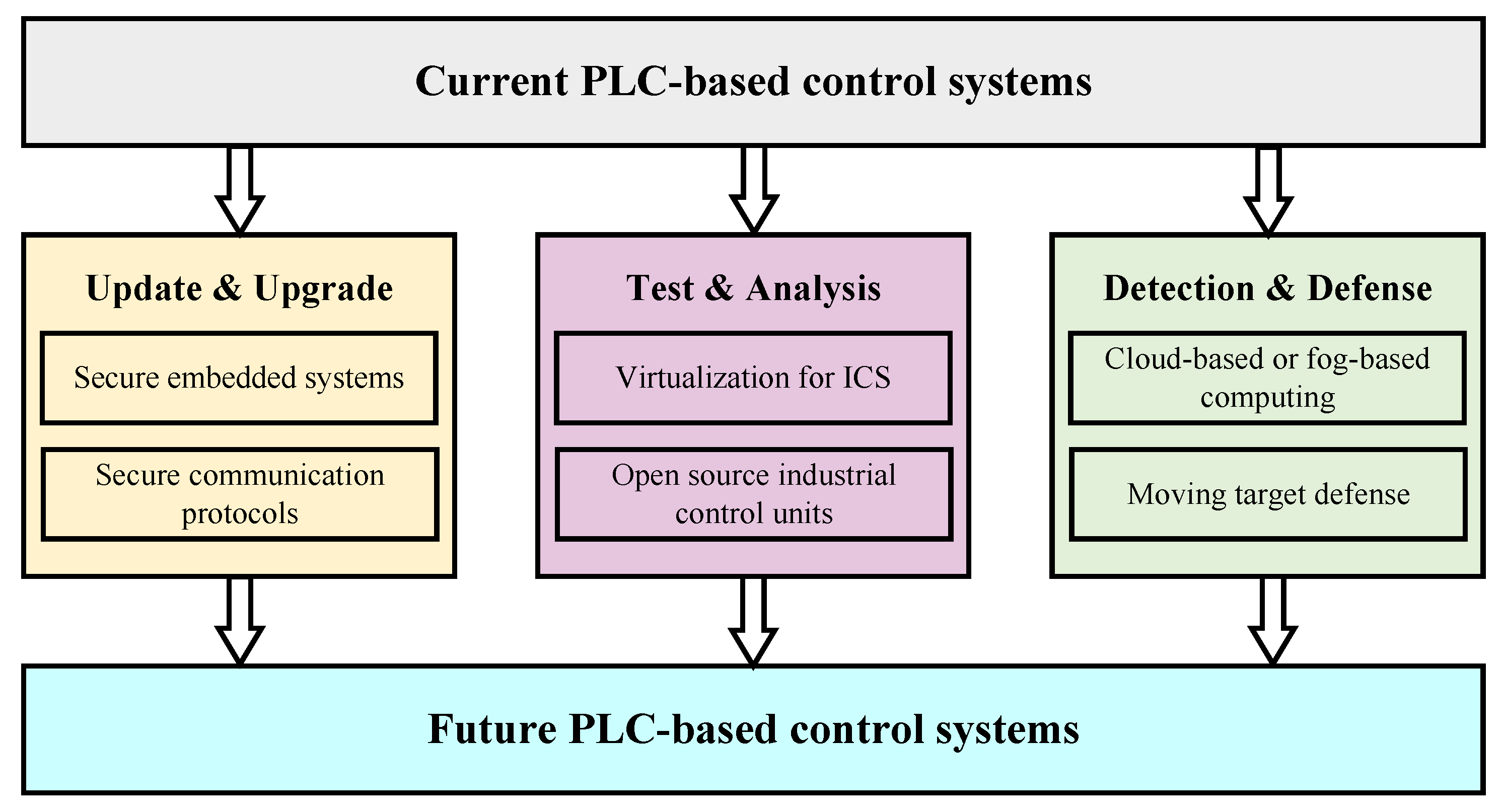
Note that we listed considerable detection schemes and digital forensics methodologies in order to improve the cyber security of the current PLC-based control system. However, they were not enough to meet increasing demands to construct a robust, reliable, and advanced PLC-based control system. In this section, we highlight six main directions on security oriented toward future PLC-based control systems, which may differ from the current ones in several dimensions, including constituent parts, computing resources, core technologies, and application strategies.
Figure 6 illustrates our outlined relationship among each part of the future work. One of the most straightforward ideas is to upgrade or update the control systems, such as through the utilization of secure embedded systems and communication protocols. Due to the need for testing and analysis, the control systems require validation capabilities with a high degree of fidelity, which can be realized by virtualization and open-source industrial control units. Furthermore, the integration of cloud-based, fog-based, and dynamic network techniques into the systems gives more opportunities for detection and defense against a series of ongoing security challenges.
8.1. Secure Embedded Systems
The embedded system-based devices, which are autonomous, intelligent, and highly connected, have a principal role in the PLC-based control system. Nevertheless, the more powerful capabilities these systems obtain, the more sophisticated cyberattacks they will suffer from. Just like the safety PLC, a pre-defined reaction on failure was designed in the PLC to fulfill reliable and safe requirements for industrial processes. In the future, more built-in security features should be supported for embedded systems, so-called “secure embedded systems”. The vulnerabilities of current PLCs themselves mostly lie in their firmware or control logic programs, as mentioned in
Section 4. For that reason, new advanced secure PLCs need to consider security properties such as secure boot, secure program update, and embedded management. The novel proof of concept of controllers with embedded hypervisors, CPUs with security processors, a secure firmware update framework, and even a software- or hardware-based secure boot mechanism will be realized in the next-generation PLC-based control systems where the Design Lifecycle of Secure Embedded Devices System approach is applied. However, it simultaneously means that it will cost more computational power. An open issue is how to ensure security while maintaining normal functionality.
8.2. Secure Communication Protocols
Obviously, the security of existing PLC-based control systems is subject to the defects of legacy communication protocols, including plaintext transmission and the lack of user authentication mechanisms as well as integrity checking. As mentioned in
Section 4, the systems are prone to being violated by attacks such as DoS, injection, replay, and MITM. As a result, extensive industrial communication protocol update versions emerged in diverse research fields, i.e., S7COMM-Plus and Modbus/TCP Security. To a large extent, these variant versions are not suitable for current resource-constrained control systems to achieve satisfactory real-time or stable performance, even if targeted adjustments are made in relevant software or hardware. What is worse, some secure-version protocols can still be exploited by sophisticated attackers. For instance, S7COMMPlus uses private algorithms to encrypt connection packets and function packets, which can effectively protect the communication between PLCs and the TIA portal from replay attack. Whereas, by means of reverse engineering the cryptographic protocol, adversaries also have a chance to launch a protocol-oriented attack. Therefore, a hot-spot research topic may be the favorable improvements of corresponding industrial communication protocols or innovatively designed secure ones.
8.3. Virtualization for ICS
Considering the cost and industry practices, it is impossible to analyze experiments or validate security solutions in real plants. Hence, there is an urgent demand for test environments, namely testbeds. The testbeds probably can be divided into four categories, including implementation-based ones, simulations with actual devices, single-simulations, and federated simulations. Due to the rise of virtualization techniques, virtual federated simulations for ICS have cost-efficient and scalable advantages over other kinds. Main research interest focuses on the virtualization of industry devices, such as virtual PLCs, as well as the construction honeypot with virtual hosts in the industrial control network. However, issues related to the fidelity of virtual devices should be taken into further consideration. For example, once attackers find out that the fingerprints of virtual devices in the honeypot differ from the real ones, they may not conduct the next violation steps in the virtual environment. In other words, the honeypot loses its value in some deceptive ways because of the failure in virtual device fingerprint emulation. In a broad sense, the future virtualization of ICS is not only for constructing a preferable performance testbed but also for pursuing an outstanding and manageable substitution for the current industrial devices.
8.4. Open-Source Industrial Control Units
A challenge of emulating PLCs in virtual environments could be missing information about their internal behaviors, especially by simply porting the PLC source codes to runtime on general-purpose operating systems. To obtain the actual response value while conducting a simulated attack experiment and exploring weaknesses in the system, researchers have to use PLCs as “hardware-in-the-loop”. Unfortunately, the proprietary software and hardware that vendors offer hinder further security research on the surrounding parts of the embedded systems, such as the operational logic and internal mechanisms. To get rid of the above dilemma, the OpenPLC project was proposed to build a functional, standardized open-source paradigm that provides the entire source code, the IDE, and the available hardware configurations on the Raspberry Pi, Arduino, and ESP8266. The modular framework in the OpenPLC project allows the researchers to construct self-defined testbeds with a combination of virtualization according to their needs, like designing an encryption layer built-in to PLCs to directly secure communication channels. In the future, apart from open-source PLCs, increasing approaches to open-source industrial control units ought to be developed for the research community to accomplish more targeted cybersecurity analysis for each key component of PLC-based control systems.
8.5. Cloud-Based or Fog-Based Computing
Within the structure of the Industrial Internet of Things, cloud-based or fog-based computing has enabled the migration of the classical PLC-based control systems to the cloud. It demonstrates an adaptable and agile solution to treating PLCs as a service. Meanwhile, attack surfaces are expanding owing to new vulnerabilities in complex and large-scale frameworks and initial access from multiple sources. Future concerns about protecting such control systems will be implemented by security platforms on the cloud. Take the following innovatively creative platforms as examples: A prototype, called PLC-Cloud, performed heavy security analysis leveraging cloud computing resources to offer a last-step verification of commands before reacting to actual controlled devices. For Service-Oriented Architecture systems, a security cloud platform was built to assure data integrity and avoid the risk of failures and attacks by providing a “toolbox” with the functions of service planning, end-to-end security, and monitoring and policing. Subsequently, the toolbox was applied to strengthen the security and privacy at the fog layer to counter cyberattacks like the compromised fog node attack. In brief, these future security platforms have common features such as low resource consumption in the local industrial control context, which reduces the extra performance effect such as latency delay. To that end, more advanced mechanisms could be deployed on the cloud to enhance the global security of the next-generation systems.
8.6. Moving Target Defense
In terms of the requirements for ICS given in
Section 2, it is impossible to update or patch the systems frequently, especially the highly-continuous processing ones. MTD is another potential active defense technique to allow a portion of unpatched vulnerabilities to exist in the underlying systems and looks forward to providing extra mechanisms that add difficulties for adversaries while launching attacks. So far, there have been two representative MTD researches for the control systems, consisting of dynamic IP and random configure parameters. By using dynamic IP techniques, peer hosts could not be easily recognized at the reconnaissance stage, and communication between them was also difficult. The random configuration parameters make the systems time-varying and stochastic, so that the specific knowledge that attackers collect beforehand about the control process is limited. Note that MTD is not an independent and complete scheme but a redundant and coordinated security one. Therefore, MTD may be an effective way to secure the future of PLC-based control systems by improving their resiliency.
9. Conclusions
The comprehensive literature review focused on the security of PLC-based control systems; it surveyed vulnerabilities, attacks, security detection schemes, digital forensic research, and future works from two aspects: the core component level and the system level. We did not only take consideration of current control system security but also offer recommendations for future control systems. Compared with the existing surveys, our work proposed specific classifications for vulnerabilities, attacks, and security detection schemes. Our analysis of PLCs’ vulnerabilities contained program, memory, and firmware. In addition, application software, communication protocols, and connected devices related to relevant control systems were researched too. Subsequently, the existing attacks are classified into three categories, including attacks against availability, integrity, and confidentiality. Then, we presented security detection schemes with detection functions, which are classified as program detection, firmware detection, device-fingerprinting-based detection, intrusion detection, and honeypot-based detection. Furthermore, we discussed methodology, challenges, and achievements in forensic research. With an eye toward further research, suggestions were outlined to strengthen security in future PLC-based control systems. In the light of mitigating cyber threats to ICS targets, sound mechanisms are needed for overall secure control systems due to the fact that single security appliances and technologies are somewhat limited.