Continuous-Variable Measurement-Device-Independent Quantum Key Distribution in the Terahertz Band
Abstract
1. Introduction
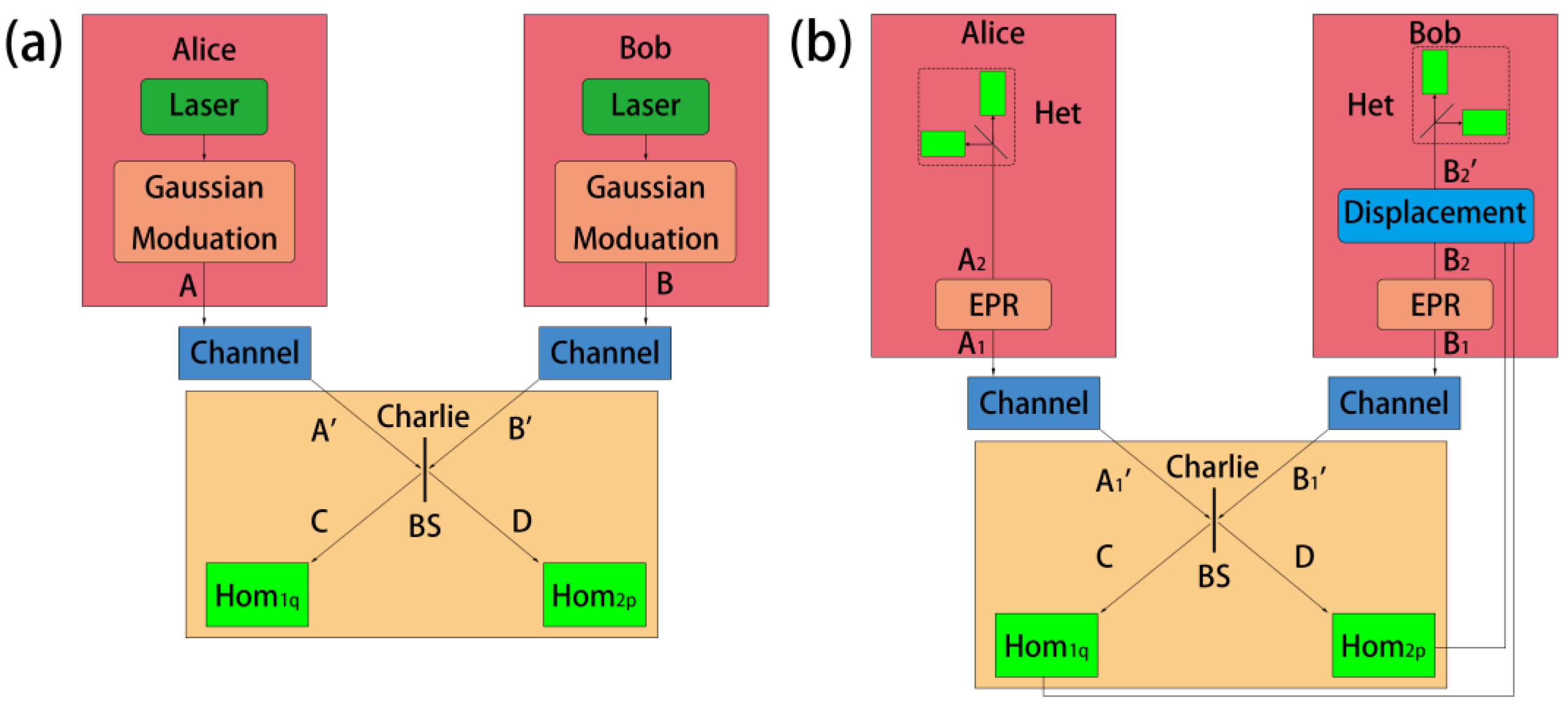
2. THz Continuous-Variable Measurement-Device-Independent QKD Protocol
2.1. Basic Principles of THz CV-MDI-QKD
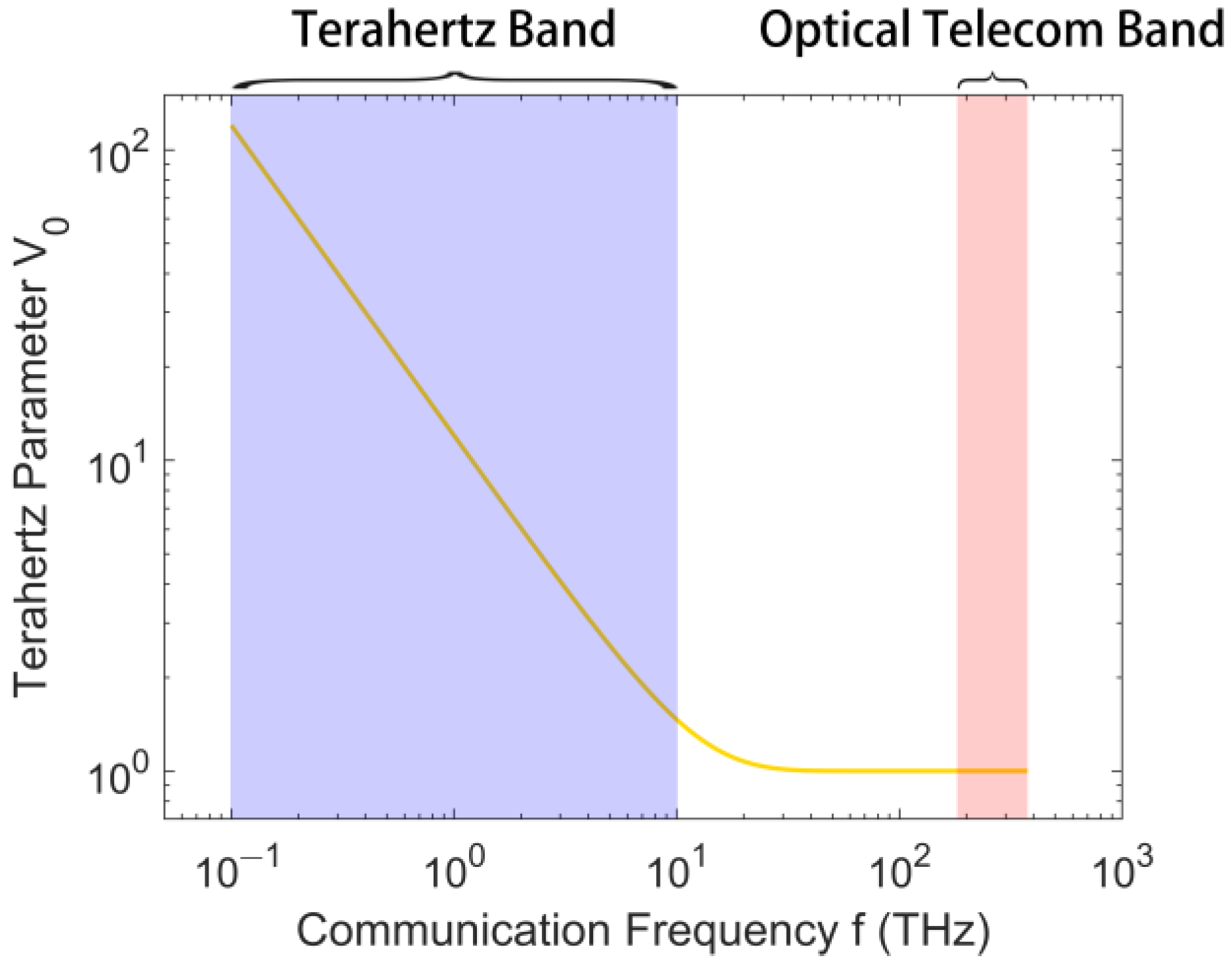
2.2. Terahertz Parameter
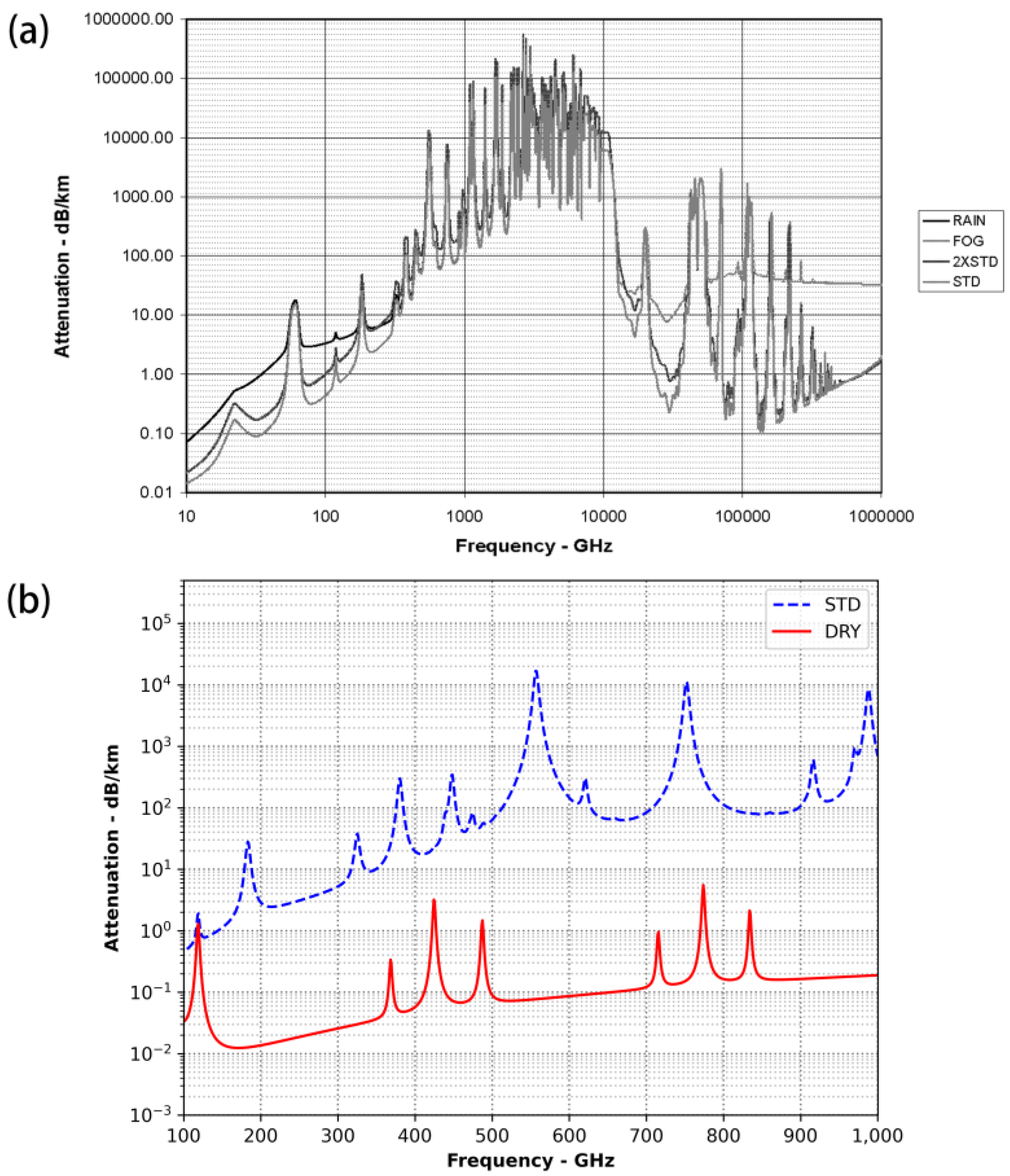
2.3. Channel Analysis for THz CV-MDI-QKD
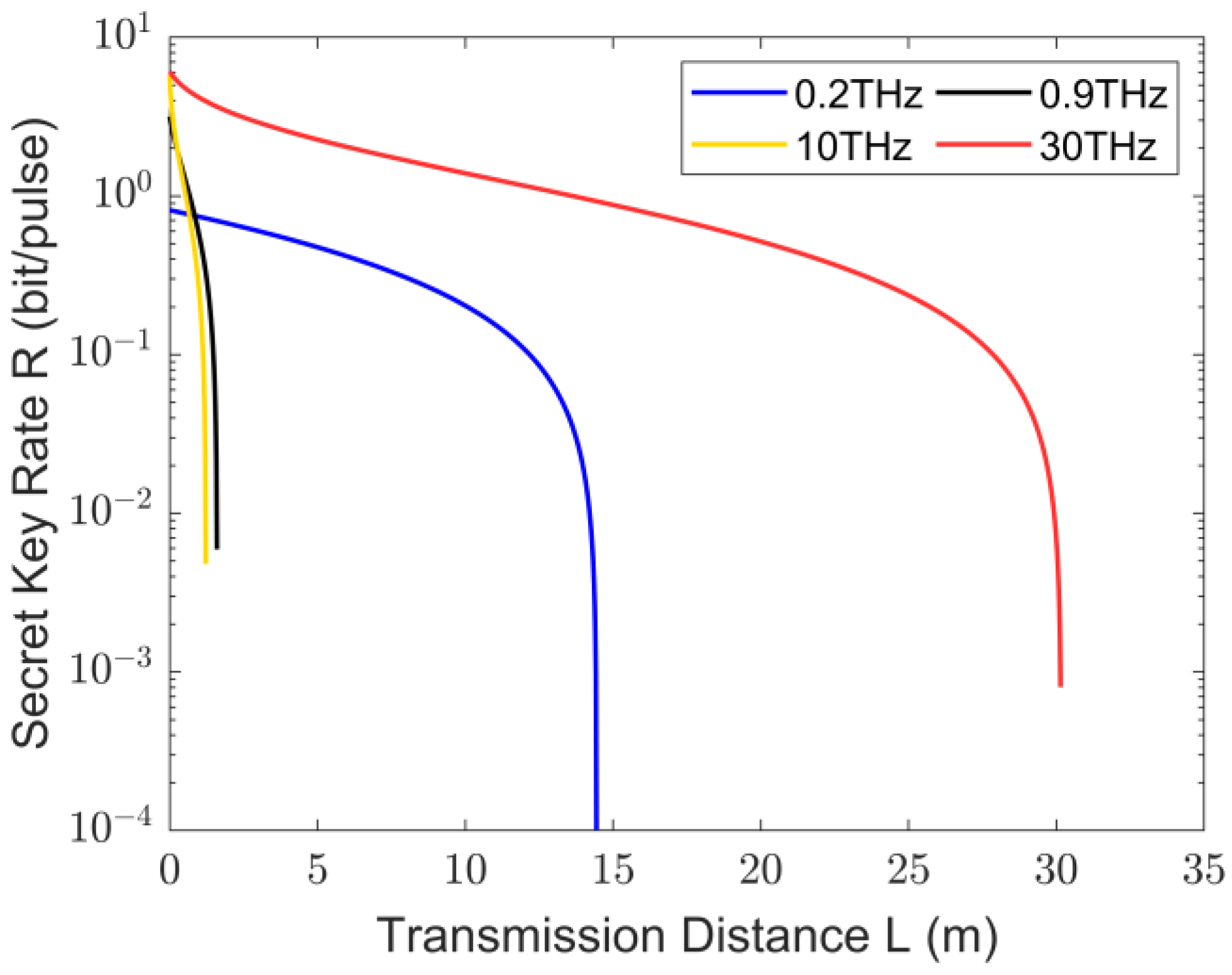
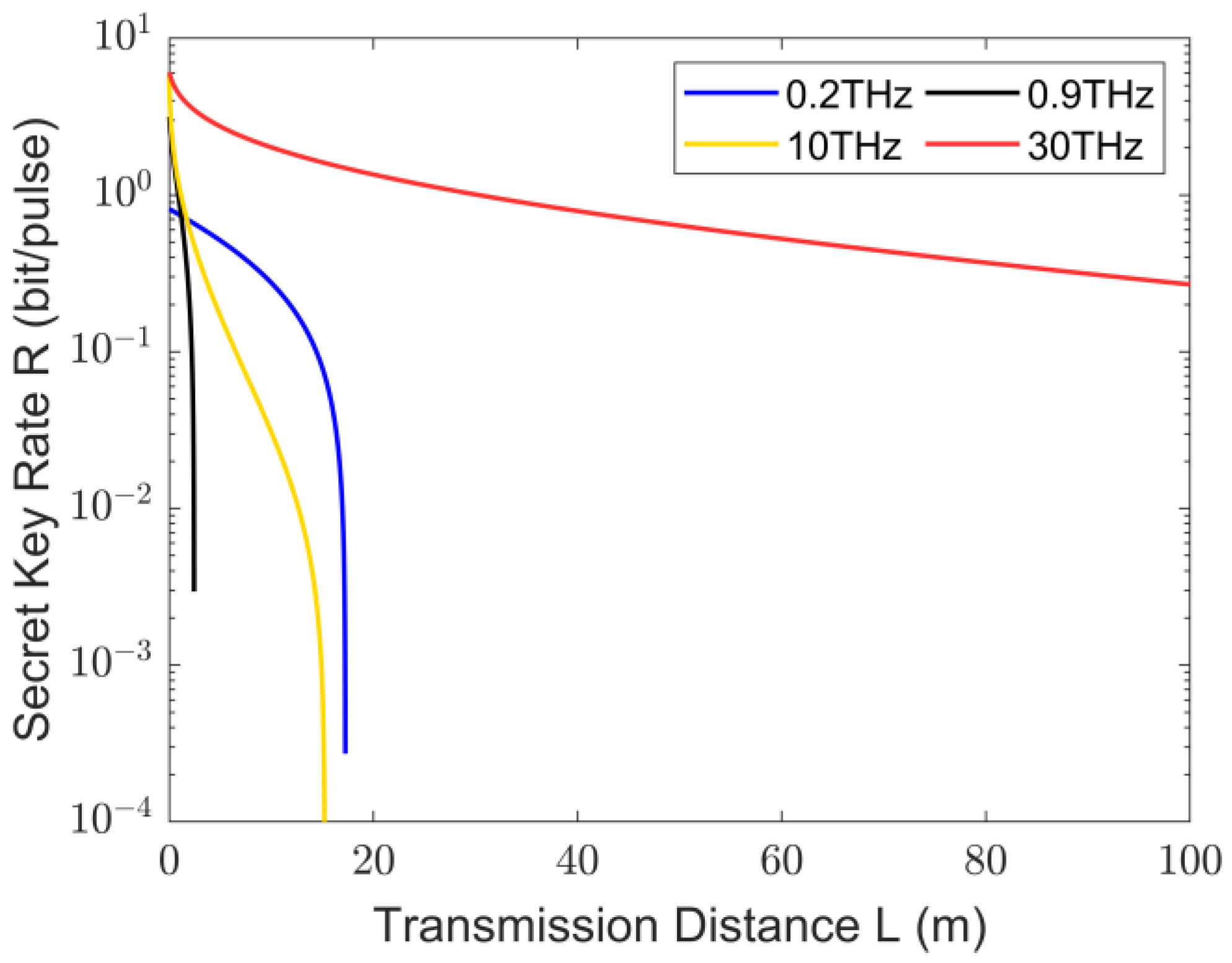
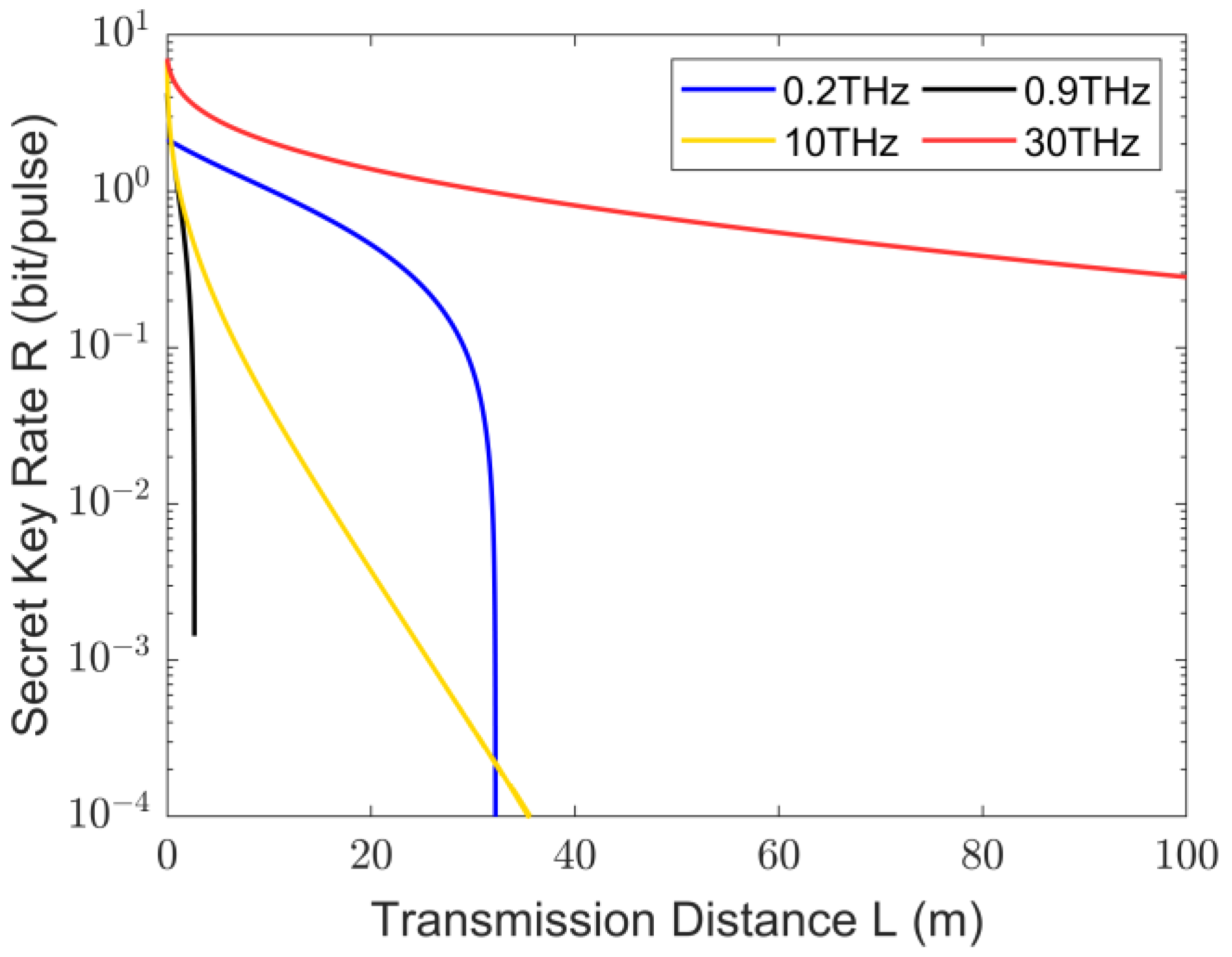
3. Analysis of Secure Key Rates for THz CV-MDI-QKD
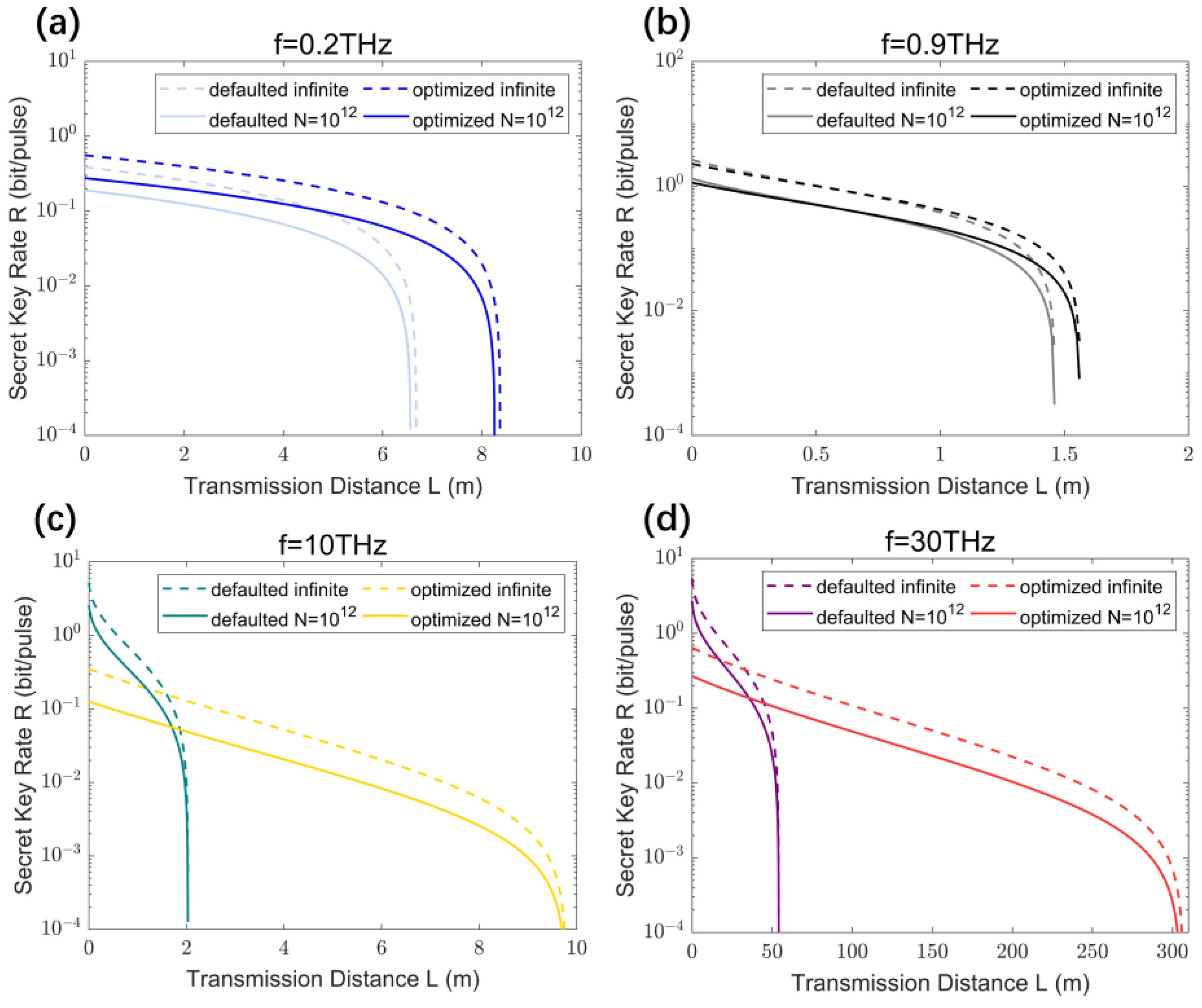
4. The Finite-Size Effect and Suboptimal Reconciliation Efficiency for THz CV-MDI-QKD
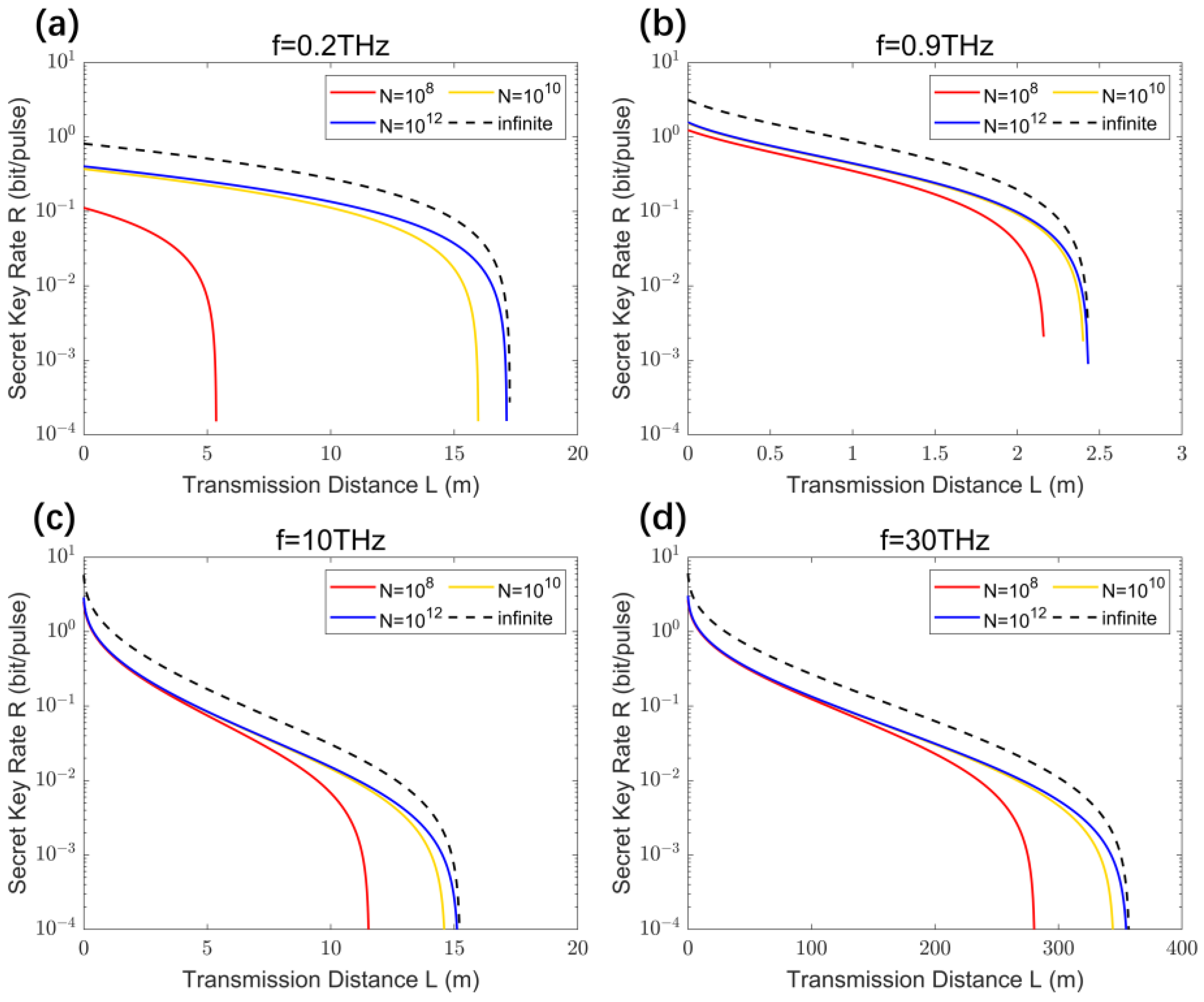
4.1. Impact of the Finite-Size Effect
4.2. Impacts of the Reconciliation Efficiency
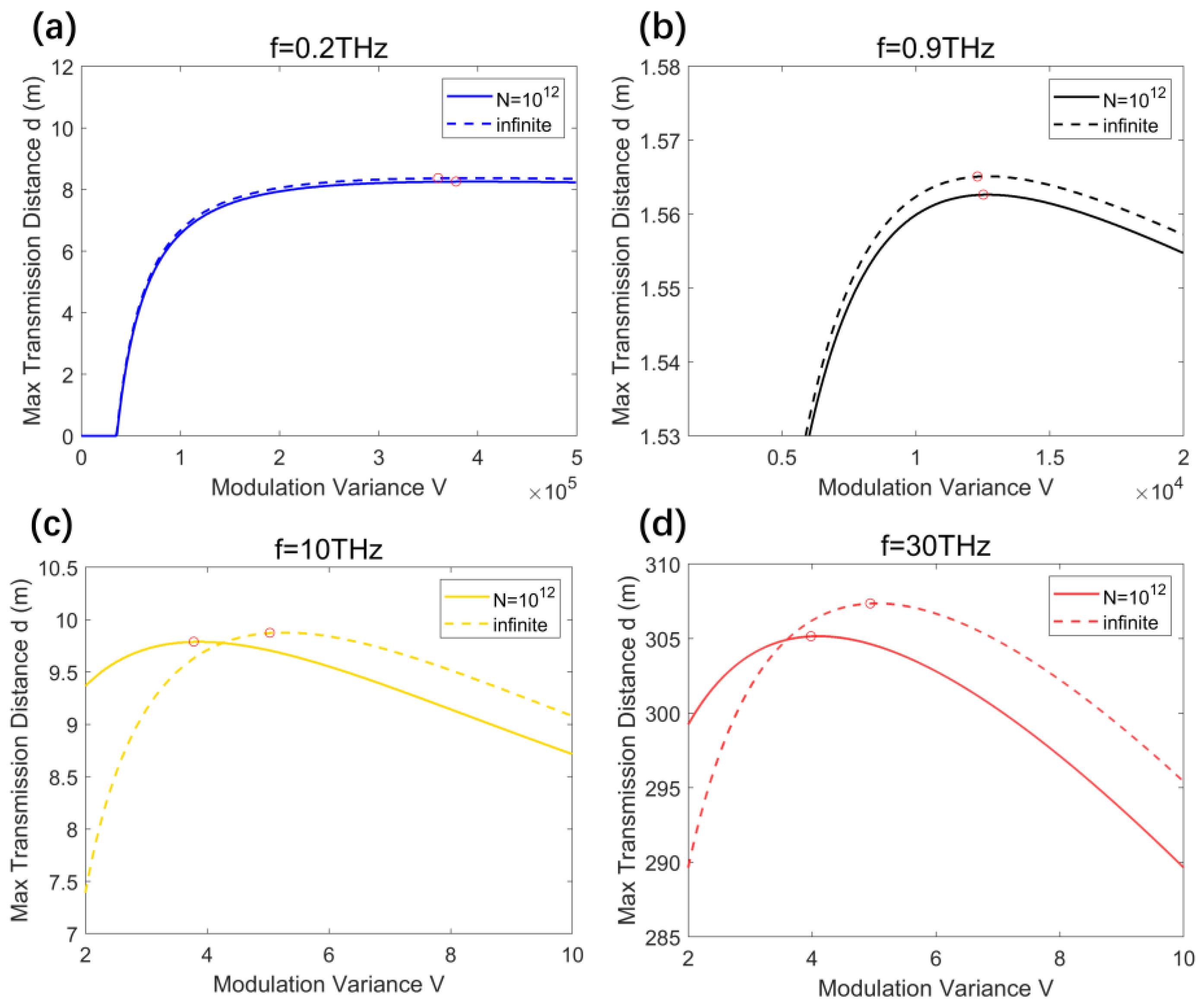
4.3. Optimal Modulation Variances
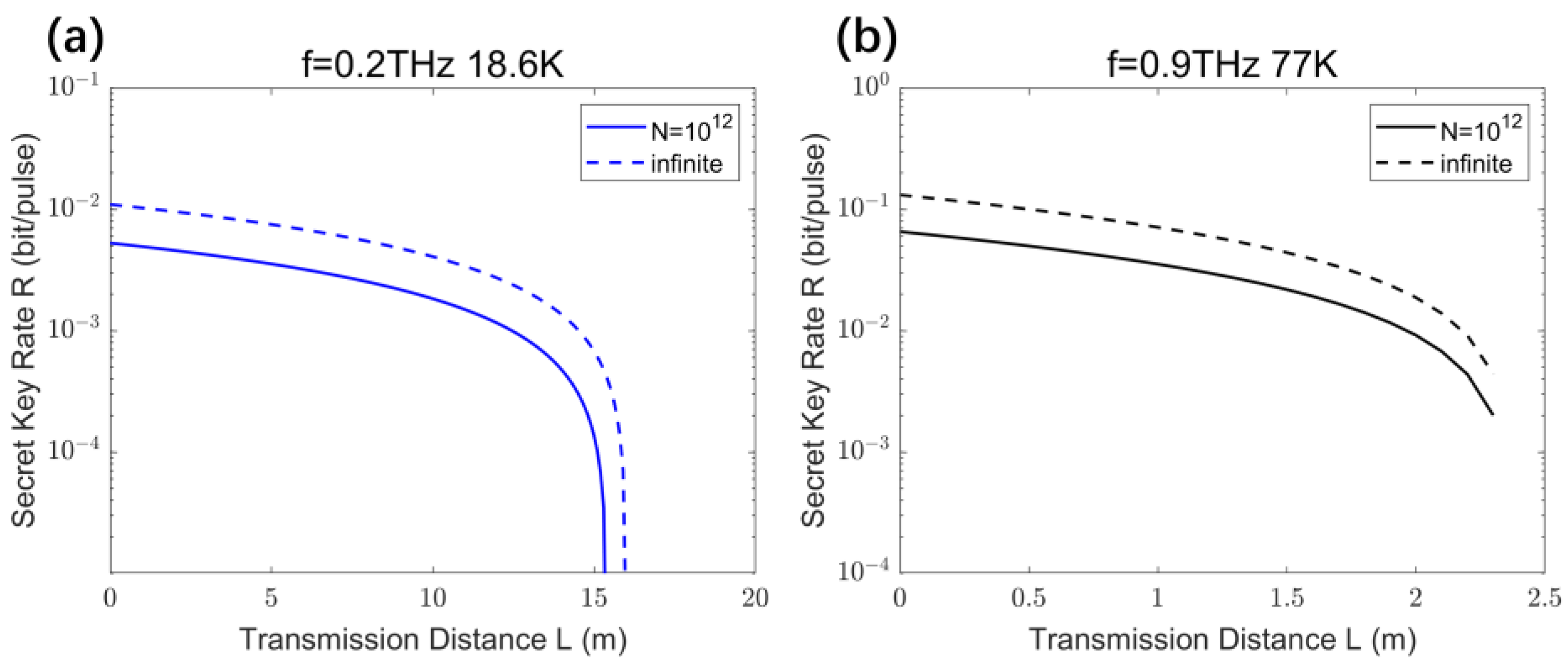
4.4. Low-Temperature THz CV-MDI-QKD
5. Discussion
5.1. Compared with Optical QKD
5.2. Experimental Implementation of THz CV-MDI-QKD
- Advances in the main components of THz QKD, which encompass THz light sources, THz detectors, and THz intensity and phase modulators, are expected to significantly promote the development of THz QKD technology.
- The maturity of THz single-photon detectors will greatly advance THz DVQKD, as the majority of current research, including our work, has been focused on THz CVQKD.
- Developments in THz optical waveguides, akin to how optical fiber advancements have greatly promoted optical QKD, can lead to significant improvements in THz wired channel QKD by reducing losses. This can help circumvent issues associated with wireless channel attenuation and obstacles.
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Bennett, C.H.; Brassard, G. Quantum cryptography: Public key distribution and coin tossing. In Proceedings of the International Conference on Computers, Systems and Signal Processing, Bangalore, India, 10–12 December 1984; pp. 175–179. [Google Scholar]
- Bennett, C.H.; Brassard, G. Experimental quantum cryptography: The dawn of a new era for quantum cryptography: The experimental prototype is working. ACM Sigact News 1989, 20, 78–80. [Google Scholar] [CrossRef]
- Wang, S.; Yin, Z.; He, D.; Chen, W.; Wang, R.; Ye, P.; Zhou, Y.; Fan-Yuan, G.; Wang, F.; Chen, W.; et al. Twin-field quantum key distribution over 830-km fibre. Nat. Photonics 2022, 16, 154–161. [Google Scholar] [CrossRef]
- Liu, Y.; Zhang, W.; Jiang, C.; Chen, J.; Zhang, C.; Pan, W.; Ma, D.; Dong, H.; Xiong, J.; Zhang, C.; et al. Experimental Twin-Field Quantum Key Distribution Over 1000 km Fiber Distance. Phys. Rev. Lett. 2023, 130, 210801. [Google Scholar] [CrossRef]
- Ralph, T.C. Security of continuous-variable quantum cryptography. Phys. Rev. A 2000, 62, 062306. [Google Scholar] [CrossRef]
- Huang, D.; Liu, S.; Zhang, L. Secure Continuous-Variable Quantum Key Distribution with Machine Learning. Photonics 2021, 8, 511. [Google Scholar] [CrossRef]
- Li, D.D.; Tang, Y.L.; Zhao, Y.K.; Zhou, L.; Zhao, Y.; Tang, S.B. Security of Optical Beam Splitter in Quantum Key Distribution. Photonics 2022, 9, 527. [Google Scholar] [CrossRef]
- Zhou, L.; Lin, J.; Xie, Y.M.; Lu, Y.S.; Jing, Y.; Yin, H.L.; Yuan, Z. Experimental quantum communication overcomes the rate-loss limit without global phase tracking. Phys. Rev. Lett. 2023, 130, 250801. [Google Scholar] [CrossRef]
- Grosshans, F.; Grangier, P. Continuous Variable Quantum Cryptography Using Coherent States. Phys. Rev. Lett. 2002, 88, 057902. [Google Scholar] [CrossRef]
- Williams, B.P.; Qi, B.; Alshowkan, M.; Evans, P.G.; Peters, N.A. Continuous-variable quantum key distribution with true local oscillator. In Proceedings of the Conference on Lasers and Electro-Optics (CLEO) 2023, San Jose, CA, USA, 7–12 May 2023; p. FF1A.2. [Google Scholar]
- Ghorai, S.; Grangier, P.; Diamanti, E.; Leverrier, A. Asymptotic security of continuous-variable quantum key distribution with a discrete modulation. Phys. Rev. X 2019, 9, 021059. [Google Scholar] [CrossRef]
- Lin, J.; Upadhyaya, T.; Lütkenhaus, N. Asymptotic security analysis of discrete-modulated continuous-variable quantum key distribution. Phys. Rev. X 2019, 9, 041064. [Google Scholar] [CrossRef]
- Liu, W.B.; Li, C.L.; Xie, Y.M.; Weng, C.X.; Gu, J.; Cao, X.Y.; Lu, Y.S.; Li, B.H.; Yin, H.L.; Chen, Z.B. Homodyne detection quadrature phase shift keying continuous-variable quantum key distribution with high excess noise tolerance. PRX Quantum 2021, 2, 040334. [Google Scholar] [CrossRef]
- Kanitschar, F.; George, I.; Lin, J.; Upadhyaya, T.; Lütkenhaus, N. Finite-Size Security for Discrete-Modulated Continuous-Variable Quantum Key Distribution Protocols. PRX Quantum 2023, 4, 040306. [Google Scholar] [CrossRef]
- Zhang, Y.; Li, Z.; Chen, Z.; Weedbrook, C.; Zhao, Y.; Wang, X.; Huang, Y.; Xu, C.; Zhang, X.; Wang, Z. Continuous-variable QKD over 50 km commercial fiber. Quantum Sci. Technol. 2019, 4, 035006. [Google Scholar] [CrossRef]
- Zhang, Y.; Chen, Z.; Pirandola, S.; Wang, X.; Zhou, C.; Chu, B.; Zhao, Y.; Xu, B.; Yu, S.; Guo, H. Long-Distance Continuous-Variable Quantum Key Distribution over 202.81 km of Fiber. Phys. Rev. Lett. 2020, 125, 010502. [Google Scholar] [CrossRef] [PubMed]
- Sakda, N.; Chitaree, R.; Rahman, B.M.A. Reflective Terahertz Metasurfaces Based on Non-Volatile Phase Change Material for Switchable Manipulation. Photonics 2022, 9, 508. [Google Scholar] [CrossRef]
- Kiwa, T.; Tonouchi, M. Special Issue “Terahertz (THz) Science in Advanced Materials, Devices and Systems”. Photonics 2023, 10, 1024. [Google Scholar] [CrossRef]
- Shiramizu, T.; Seiki, N.; Matsumoto, R.; Masutomi, N.; Mikami, Y.; Ueda, Y.; Kato, K. Feasibility Demonstration of THz Wave Generation/Modulation Based on Photomixing Using a Single Wavelength-Tunable Laser. Photonics 2023, 10, 369. [Google Scholar] [CrossRef]
- Ma, J.; Vorrius, F.; Lamb, L.; Moeller, L.; Federici, J.F. Comparison of experimental and theoretical determined terahertz attenuation in controlled rain. J. Infrared Millim. Terahertz Waves 2015, 36, 1195–1202. [Google Scholar] [CrossRef]
- Ma, J.; Vorrius, F.; Lamb, L.; Moeller, L.; Federici, J.F. Experimental comparison of terahertz and infrared signaling in laboratory-controlled rain. J. Infrared Millim. Terahertz Waves 2015, 36, 8856–8865. [Google Scholar] [CrossRef]
- Su, K.; Moeller, L.; Barat, R.B.; Federici, J.F. Experimental comparison of terahertz and infrared data signal attenuation in dust clouds. J. Opt. Soc. Am. A 2012, 29, 2360–2366. [Google Scholar] [CrossRef]
- Su, K.; Moeller, L.; Barat, R.B.; Federici, J.F. Experimental comparison of performance degradation from terahertz and infrared wireless links in fog. J. Opt. Soc. Am. A 2012, 29, 179–184. [Google Scholar] [CrossRef] [PubMed]
- Ma, J.; Lamb, L.; Moeller, L.; Federici, J.F. Experimental comparison of terahertz and infrared signaling in controlled atmospheric turbulence. J. Infrared Millim. Terahertz Waves 2015, 36, 130–143. [Google Scholar] [CrossRef]
- Ramos, R.V. A Proposal for Single-Photon Detection in Millimeter-Wave and THz Regions. In Proceedings of the 2021 SBMO/IEEE MTT-S International Microwave and Optoelectronics Conference (IMOC), Fortaleza, Brazil, 24–27 October 2021; pp. 1–3. [Google Scholar]
- Guedes, V.F.; Mendonca, F.A.; Silva, J.B.R.; Ramos, R.V. Discrete Variable Quantum Key Distribution in Millimeter-Wave and THz Regions. TechRxiv 2021, preprint. [Google Scholar] [CrossRef]
- Weedbrook, C.; Pirandola, S.; Lloyd, S.; Ralph, T.C. Quantum cryptography approaching the classical limit. Phys. Rev. Lett. 2010, 105, 110501. [Google Scholar] [CrossRef] [PubMed]
- Weedbrook, C.; Pirandola, S.; Ralph, T.C. Continuous-variable quantum key distribution using thermal states. Phys. Rev. A 2012, 86, 022318. [Google Scholar] [CrossRef]
- Weedbrook, C.; Ottaviani, C.; Pirandola, S. Two-way quantum cryptography at different wavelengths. Phys. Rev. A 2014, 89, 219–228. [Google Scholar] [CrossRef]
- Liu, X.; Zhu, C.; Chen, N.; Pei, C. Practical aspects of terahertz wireless quantum key distribution in indoor environments. Quantum Inf. Process. 2018, 17, 1–20. [Google Scholar] [CrossRef]
- Liu, C.; Zhu, C.; Nie, M.; Yang, H.; Pei, C. FL-QKD based on optical-THz biphotons generated by spontaneous parametric downconversion in inter-satellite wireless communication. Appl. Opt. 2021, 60, 7362–7370. [Google Scholar] [CrossRef]
- Kundu, N.K.; Dash, S.P.; McKay, M.R.; Mallik, R.K. MIMO terahertz quantum key distribution. IEEE Commun. Lett. 2021, 25, 3345–3349. [Google Scholar] [CrossRef]
- Liu, C.; Zhu, C.; Liu, X.; Nie, M.; Yang, H.; Pei, C. Multicarrier multiplexing continuous-variable quantum key distribution at terahertz bands under indoor environment and in inter-satellite links communication. IEEE Photonics J. 2021, 13, 1–13. [Google Scholar]
- Liu, C.; Zhu, C.; Li, Z.; Nie, M.; Yang, H.; Pei, C. Continuous-variable quantum secret sharing based on thermal terahertz sources in inter-satellite wireless links. Entropy 2021, 23, 1223. [Google Scholar] [CrossRef] [PubMed]
- Echternach, P.M.; Pepper, B.J.; Reck, T.; Bradford, C.M. Single photon detection of 1.5 THz radiation with the quantum capacitance detector. Nat. Astron. 2018, 2, 90–97. [Google Scholar] [CrossRef]
- He, Y.; Mao, Y.; Huang, D.; Liao, Q.; Guo, Y. Indoor channel modeling for continuous variable quantum key distribution in the terahertz band. Opt. Express 2020, 28, 32386–32402. [Google Scholar] [CrossRef] [PubMed]
- Wang, Z.; Malaney, R.; Green, J. Inter-Satellite Quantum Key Distribution at Terahertz Frequencies. In Proceedings of the 2019 IEEE International Conference on Communications (ICC), Shanghai, China, 20–24 May 2019; pp. 1–7. [Google Scholar]
- Ottaviani, C.; Woolley, M.J.; Erementchouk, M.; Federici, J.F.; Mazumder, P.; Pirandola, S.; Weedbrook, C. Terahertz Quantum Cryptography. IEEE J. Sel. Areas Commun. 2020, 38, 483–495. [Google Scholar] [CrossRef]
- Liu, C.; Zhu, C.; Nie, M.; Yang, H.; Pei, C. Composable security for inter-satellite continuous-variable quantum key distribution in the terahertz band. Opt. Express 2022, 30, 14798–14816. [Google Scholar] [CrossRef] [PubMed]
- Curty, M.; Xu, F.; Cui, W.; Lim, C.; Tamaki, K.; Lo, H.K. Finite-key analysis for measurement-device-independent quantum key distribution. Nat. Commun. 2014, 5, 3732. [Google Scholar] [CrossRef]
- Zhang, X.; Zhang, Y.; Zhao, Y.; Wang, X.; Yu, S.; Guo, H. Finite-size analysis of continuous-variable measurement-device-independent quantum key distribution. Phys. Rev. A 2017, 96, 042334. [Google Scholar] [CrossRef]
- Zhao, Y.; Fung, C.; Qi, B.; Chen, C.; Lo, H.K. Quantum hacking: Experimental demonstration of time-shift attack against practical quantum key distribution systems. Phys. Rev. A 2008, 78, 042333. [Google Scholar] [CrossRef]
- Makarov, V.; Hjelme, D. Faked states attack on quantum cryptosystems. J. Mod. Opt. 2005, 52, 691–705. [Google Scholar] [CrossRef]
- Makarov, V. Controlling passively quenched single photon detectors by bright light. New J. Phys. 2009, 11, 065003. [Google Scholar] [CrossRef]
- Lo, H.K.; Curty, M.; Qi, B. Measurement-device-independent quantum key distribution. Phys. Rev. Lett. 2012, 108, 130503. [Google Scholar] [CrossRef] [PubMed]
- Vorontsova, I.O.; Goncharov, R.K.; Tarabrina, A.D.; Tupyakov, D.V.; Bolychev, E.A.; Smirnov, S.V.; Kiselev, F.D.; Egorov, V.I. Theoretical analysis of measurement-device-independent quantum key distribution systems integrated into fiber-optic communication lines using dense wavelength division multiplexing. J. Opt. Technol. 2022, 89, 424–429. [Google Scholar] [CrossRef]
- Sun, Z.; Pan, D.; Ruan, D.; Long, G. One-Sided Measurement-Device-Independent Practical Quantum Secure Direct Communication. J. Light. Technol. 2023, 41, 4680–4690. [Google Scholar] [CrossRef]
- Li, Z.; Zhang, Y.; Xu, F.; Peng, X.; Guo, H. Continuous-variable measurement-device-independent quantum key distribution. Phys. Rev. A 2014, 89, 052301. [Google Scholar] [CrossRef]
- Peng, Q.; Guo, Y.; Liao, Q.; Ruan, X. Satellite-to-submarine quantum communication based on measurement-device-independent continuous-variable quantum key distribution. Quantum Inf. Process. 2022, 21, 61. [Google Scholar] [CrossRef]
- Leverrier, A.; Grosshans, F.; Grangier, P. Finite-size analysis of a continuous-variable quantum key distribution. Phys. Rev. A 2010, 81, 062343. [Google Scholar] [CrossRef]
- Wang, P.; Wang, X.; Li, J.; Li, Y. Finite-size analysis of unidimensional continuous-variable quantum key distribution under realistic conditions. Opt. Express 2017, 25, 27995–28009. [Google Scholar] [CrossRef]
- Papanastasiou, P.; Ottaviani, C.; Pirandola, S. Finite-size analysis of measurement-device-independent quantum cryptography with continuous variables. Phys. Rev. A 2017, 96, 042332. [Google Scholar] [CrossRef]
- Weedbrook, C.; Lance, A.M.; Bowen, W.P.; Symul, T.; Ralph, T.C.; Lam, P.K. Quantum Cryptography Without Switching. Phys. Rev. Lett. 2004, 93, 170504. [Google Scholar] [CrossRef]
- Devetak, I.; Winter, A. Distillation of secret key and entanglement from quantum states. Proc. R. Soc. A Math. Phys. Eng. Sci. 2005, 461, 207–235. [Google Scholar] [CrossRef]
- Sheikh, F.; Zarifeh, N.; Kaiser, T. Terahertz band: Channel modelling for short-range wireless communications in the spectral windows. IET Microw. Antennas Propag. 2016, 10, 1435–1444. [Google Scholar] [CrossRef]
- Schneider, T.; Wiatrek, A.; Preussler, S.; Grigat, M.; Braun, R.P. Link budget analysis for terahertz fixed wireless links. IEEE Trans. Terahertz Sci. Technol. 2012, 2, 250–256. [Google Scholar] [CrossRef]
- Han, C.; Wang, Y.; Li, Y.; Chen, Y.; Abbasi, N.A.; Kürner, T.; Molisch, A.F. Terahertz wireless channels: A holistic survey on measurement, modeling, and analysis. IEEE Commun. Surv. Tutor. 2022, 24, 1670–1707. [Google Scholar] [CrossRef]
- Rosker, M.J.; Wallace, H.B. Imaging through the atmosphere at terahertz frequencies. In Proceedings of the 2007 IEEE/MTT-S International Microwave Symposium, Honolulu, HI, USA, 3–8 June 2007; pp. 773–776. [Google Scholar]
- Sector, I.R. Recommendation ITU-R p. 676–12, Attenuation by Atmospheric Gases; International Telecommunications Union: Geneva, Switzerland, 2019. [Google Scholar]
- Portillo, I. ITU-Rpy: A python Implementation of the ITU-R P. Recommendations to Compute Atmospheric Attenuation in Slant and Horizontal Paths. GitHub, 2017. Available online: https://github.com/inigodelportillo/ITU-Rpy (accessed on 5 October 2023).
- Navascués, M.; Grosshans, F.; Acín, A. Optimality of Gaussian attacks in continuous-variable quantum cryptography. Phys. Rev. Lett. 2006, 97, 190502. [Google Scholar] [CrossRef]
- García-Patrón, R.; Cerf, N.J. Unconditional optimality of Gaussian attacks against continuous-variable quantum key distribution. Phys. Rev. Lett. 2006, 97, 190503. [Google Scholar] [CrossRef]
- Renner, R.; Cirac, J.I. De Finetti representation theorem for infinite-dimensional quantum systems and applications to quantum cryptography. Phys. Rev. Lett. 2009, 102, 110504. [Google Scholar] [CrossRef]
- Weedbrook, C.; Pirandola, S.; García-Patrón, R.; Cerf, N.J.; Ralph, T.C.; Shapiro, J.H.; Lloyd, S. Gaussian quantum information. Rev. Mod. Phys. 2012, 84, 621. [Google Scholar] [CrossRef]
- Wang, H.; Li, Y.; Pi, Y.; Pan, Y.; Shao, Y.; Ma, L.; Zhang, Y.; Yang, J.; Zhang, T.; Huang, W.; et al. Sub-Gbps key rate four-state continuous-variable quantum key distribution within metropolitan area. Commun. Phys. 2022, 5, 162. [Google Scholar] [CrossRef]
- Jain, N.; Chin, H.; Mani, H.; Lupo, C.; Nikolic, D.S.; Kordts, A.; Pirandola, S.; Pedersen, T.B.; Kolb, M.; Ömer, B.; et al. Practical continuous-variable quantum key distribution with composable security. Nat. Commun. 2022, 13, 4740. [Google Scholar] [CrossRef]
- Grosshans, F.; Assche, V.G.; Wenger, J.; Brouri, R.; Cerf, N.J.; Grangier, P. Quantum key distribution using gaussian-modulated coherent states. Nature 2003, 421, 238–241. [Google Scholar] [CrossRef]
- Jouguet, P.; Kunz-Jacques, S.; Leverrier, A.; Grangier, P.; Diamanti, E. Experimental demonstration of long-distance continuous-variable quantum key distribution. Nat. Photonics 2013, 7, 378–381. [Google Scholar] [CrossRef]
- Soh, D.B.S.; Brif, C.; Coles, P.J.; Lütkenhaus, N.; Camacho, R.M.; Urayama, J.; Sarovar, M. Self-referenced continuous-variable quantum key distribution protocol. Phys. Rev. X 2015, 5, 041010. [Google Scholar] [CrossRef]
- Zhang, Y.; Chen, Z.; Weedbrook, C.; Yu, S.; Guo, H. Continuous-variable source-device-independent quantum key distribution against general attacks. Sci. Rep. 2020, 10, 6673. [Google Scholar] [CrossRef] [PubMed]

Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Liu, H.; Yang, Z.; Yang, S.; Sun, D.; Zhang, C. Continuous-Variable Measurement-Device-Independent Quantum Key Distribution in the Terahertz Band. Photonics 2024, 11, 367. https://doi.org/10.3390/photonics11040367
Liu H, Yang Z, Yang S, Sun D, Zhang C. Continuous-Variable Measurement-Device-Independent Quantum Key Distribution in the Terahertz Band. Photonics. 2024; 11(4):367. https://doi.org/10.3390/photonics11040367
Chicago/Turabian StyleLiu, Haoxin, Zhe Yang, Shuoyu Yang, Dongyun Sun, and Cunlin Zhang. 2024. "Continuous-Variable Measurement-Device-Independent Quantum Key Distribution in the Terahertz Band" Photonics 11, no. 4: 367. https://doi.org/10.3390/photonics11040367
APA StyleLiu, H., Yang, Z., Yang, S., Sun, D., & Zhang, C. (2024). Continuous-Variable Measurement-Device-Independent Quantum Key Distribution in the Terahertz Band. Photonics, 11(4), 367. https://doi.org/10.3390/photonics11040367




