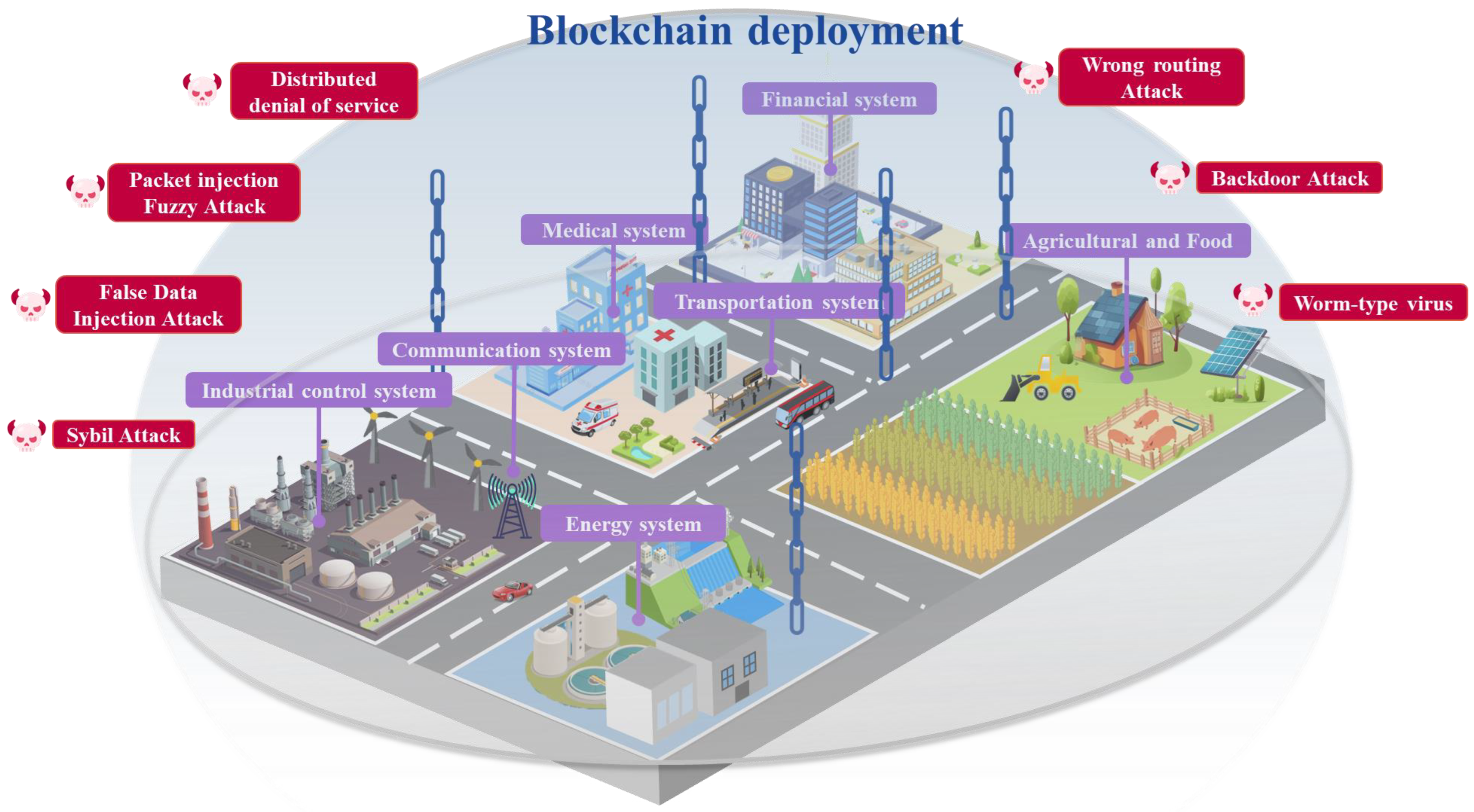
A Review on Blockchain Applications in Operational Technology for Food and Agriculture Critical Infrastructure
Abstract
1. Introduction
- What is the current research status of BT in the OTCI field?
- What are the application challenges of BT in the OTCI field?
- What is the trend of BT in the OTCI field?
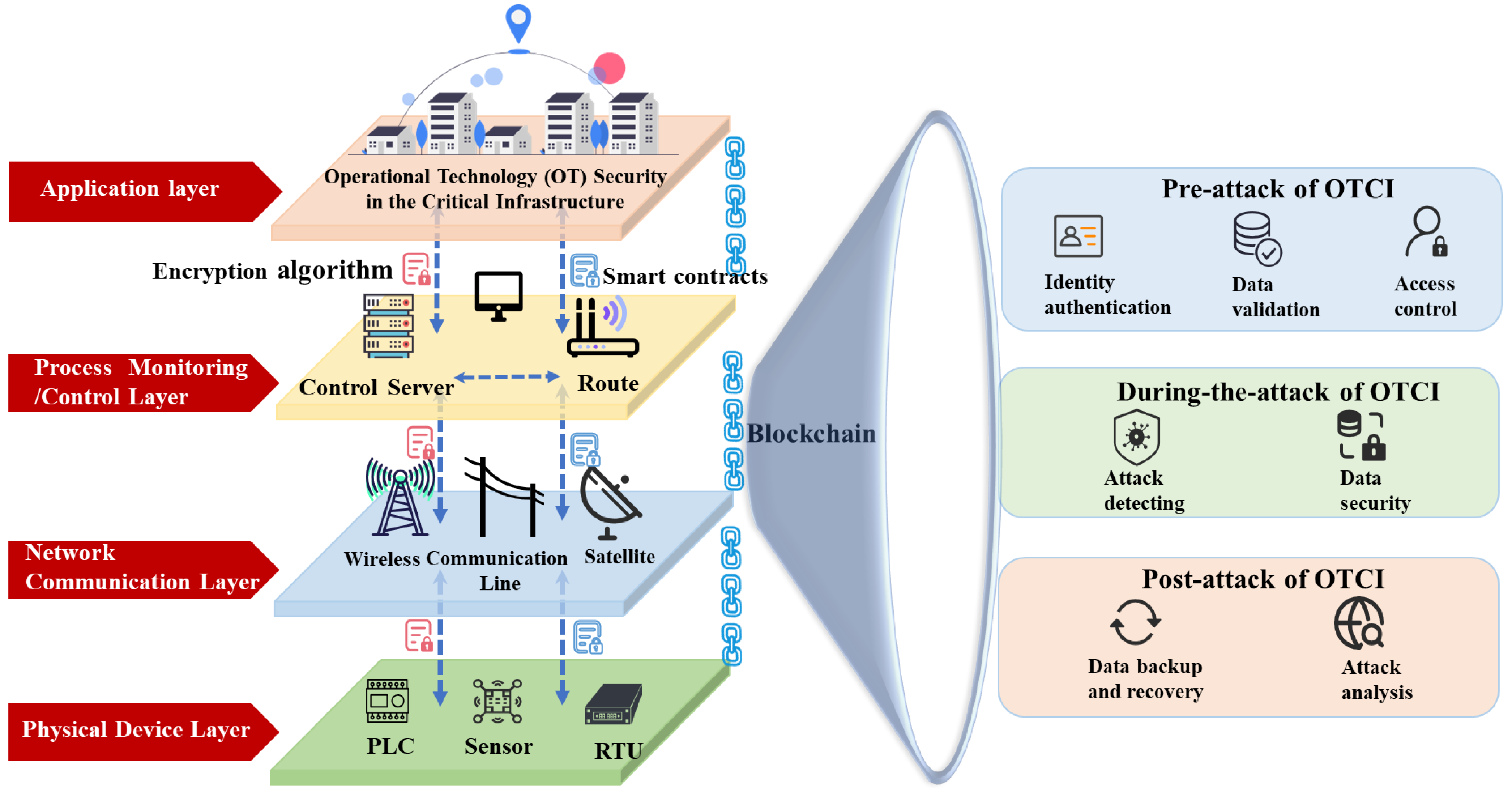
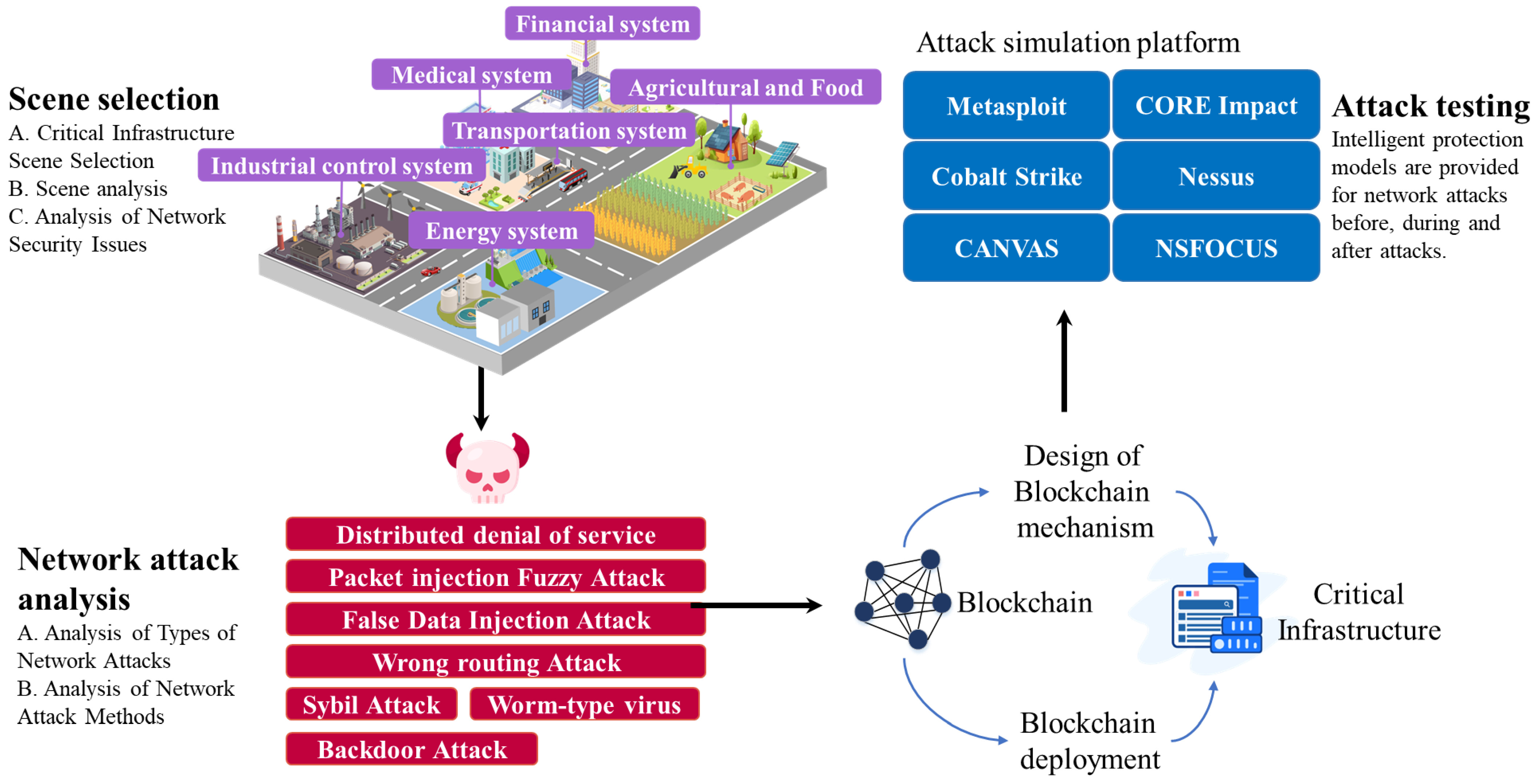
2. Defining Blockchain in Operational Technology Security of the Critical Infrastructure
3. Material and Methods
3.1. Search Method
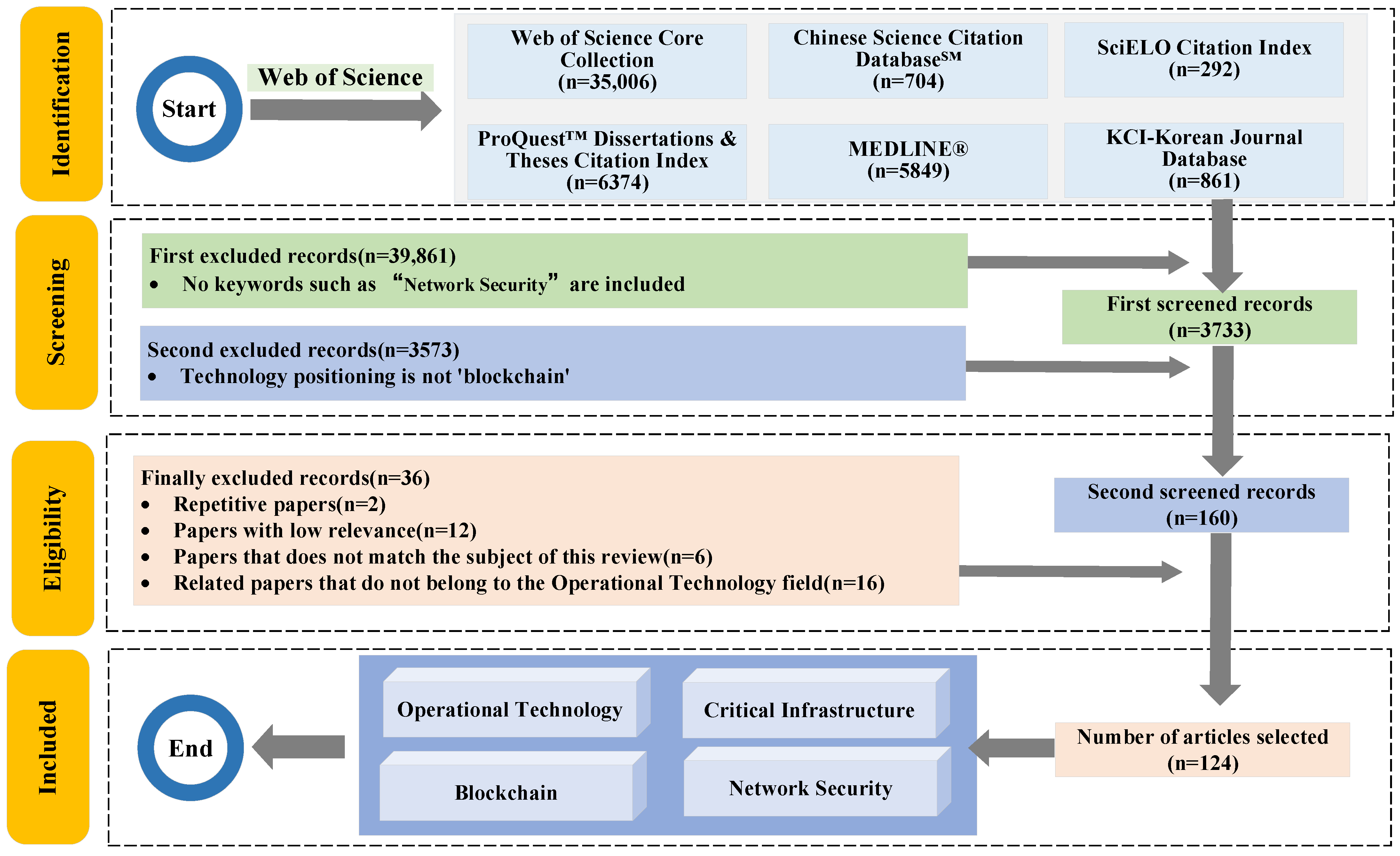
- Web of Science was utilized as a search tool. Initially, the keyword “Operational Technology” was used to search the “topic” field (which includes title, abstract, author keywords, and keywords plus) with a publication time cutoff of September 2023, resulting in 76,871 documents. Due to the lack of peer review in preprint databases, the authenticity and reliability of such studies could not be ensured; therefore, preprint documents were excluded. Subsequently, the keyword “Critical Infrastructure” was employed, narrowing the selection to 739 documents. As a distributed ledger technology, BT plays a significant role in safeguarding data within CI. For this review, “Network Security” was used as the third keyword for a refined search, resulting in 106 documents. Finally, “Blockchain” was applied as the fourth keyword for targeted searches, identifying a total of 5 documents, which were included in the Web of Science Core Collection database, covering the period from 2018 to 2023;
- To ensure the quality of paper retrieval, the preprint database was excluded due to the lack of peer-reviewed validation. The keyword “Critical Infrastructure” was then applied, resulting in 43,594 documents, among which 35,006 were included in the Web of Science Core Collection. Additional papers were distributed across other databases, including 704 in the Chinese Science Citation DatabaseSM, 292 in the SciELO Citation Index, 6374 in the ProQuest™ Dissertations & Theses Citation Index, 5849 in MEDLINE®, and 861 in the KCI-Korean Journal Database. The keyword “Network Security” was subsequently utilized for a refined search, narrowing the selection to 3733 documents. Finally, “Blockchain” was used for targeted searches, identifying a total of 160 documents spanning the years 2017 to 2023.
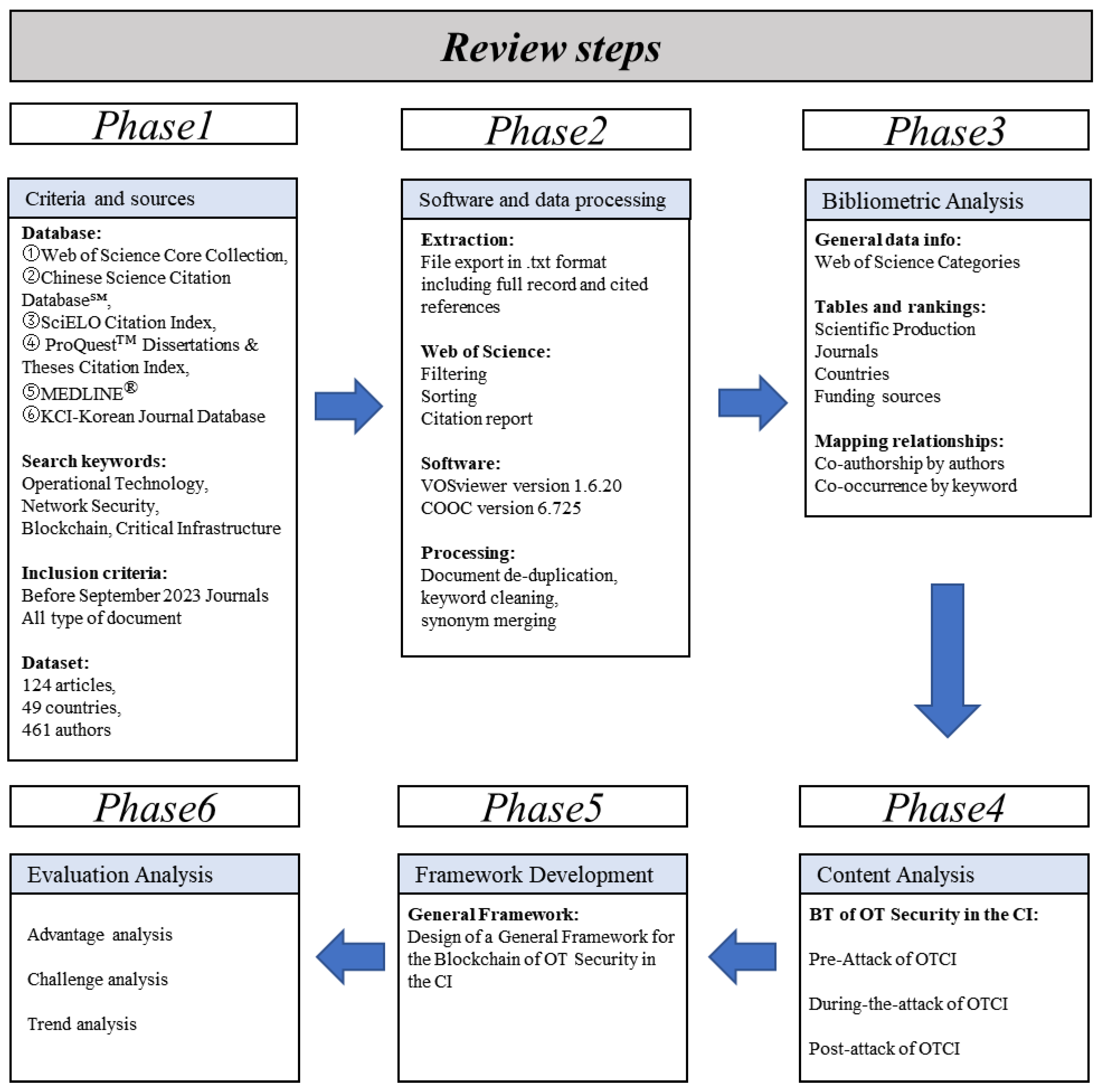
3.2. Review Steps
3.3. Bibliometric Analysis
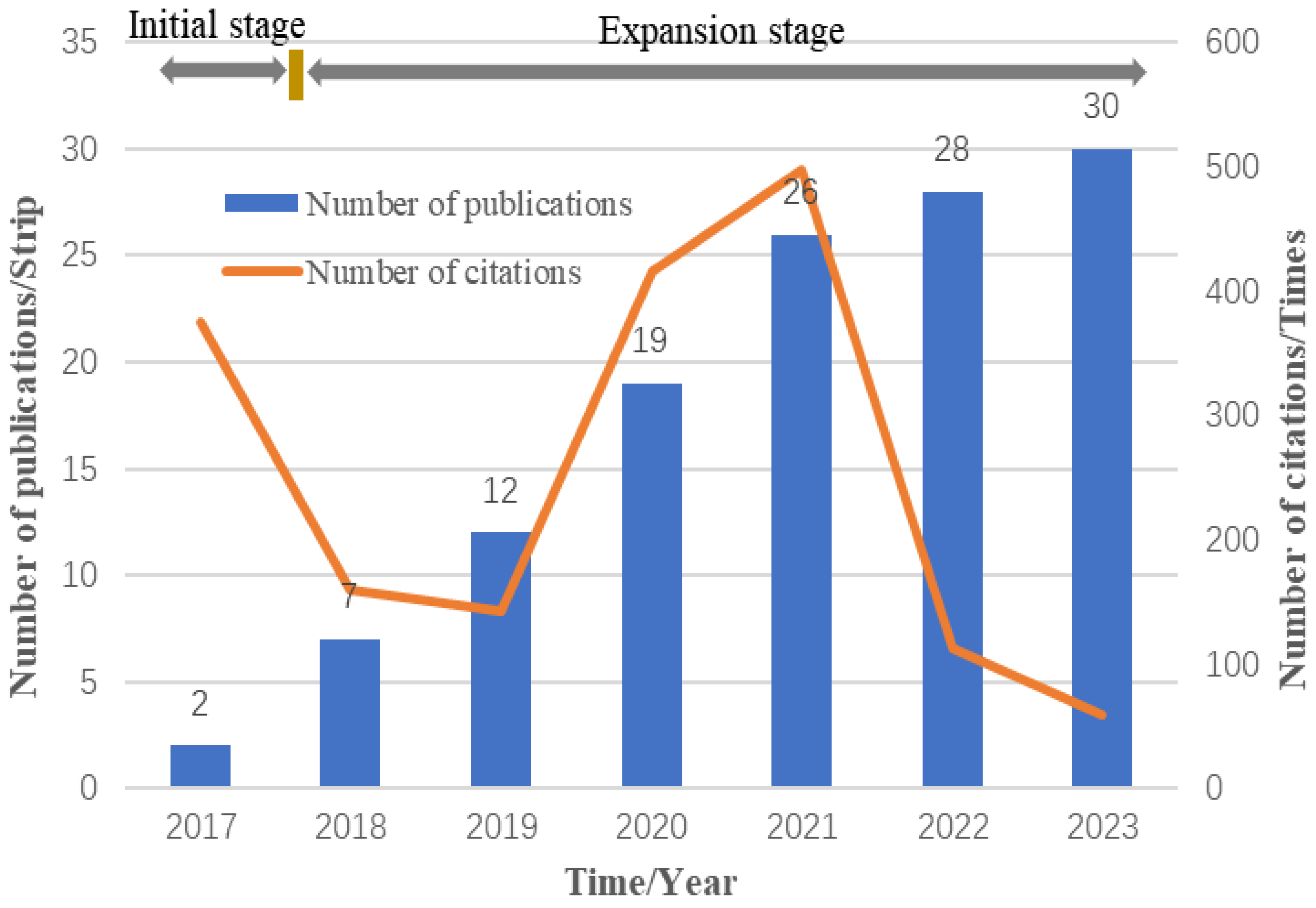
3.3.1. Year of Publication
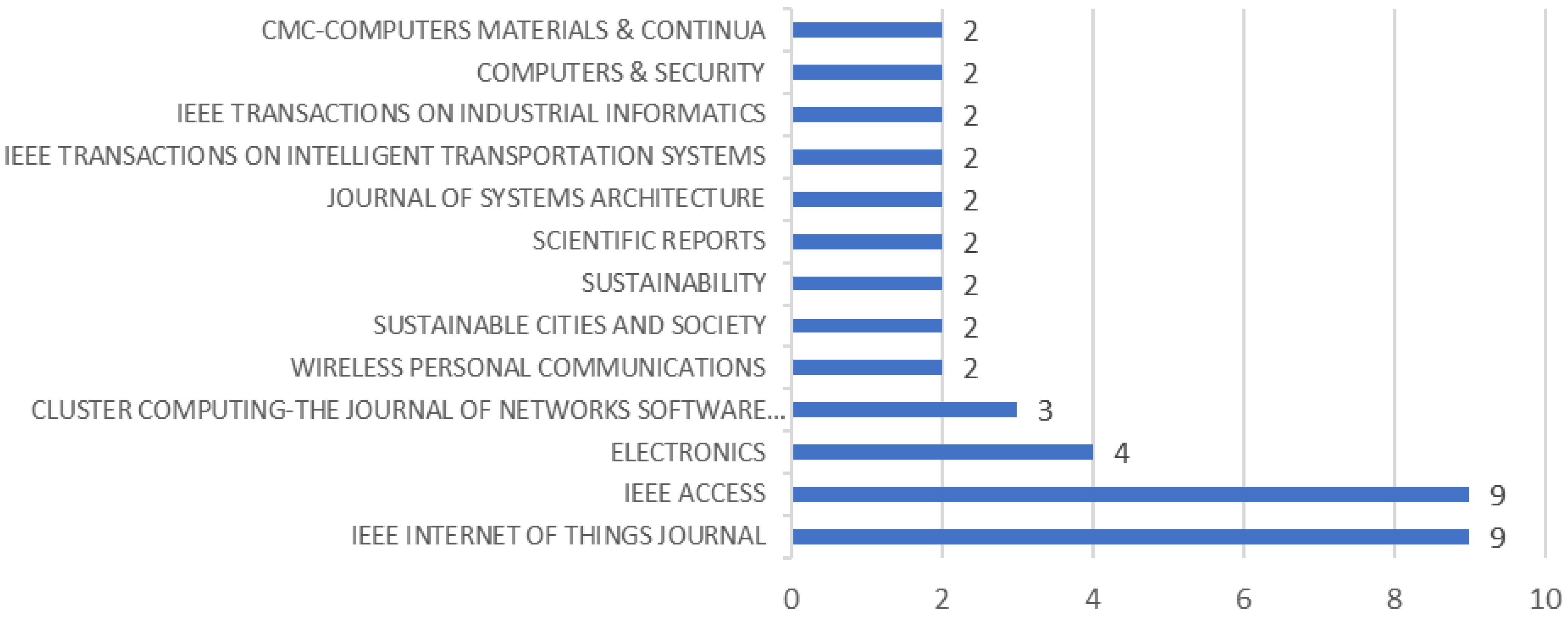
3.3.2. Literature Type and Publication Journal
3.3.3. Country
3.3.4. Author
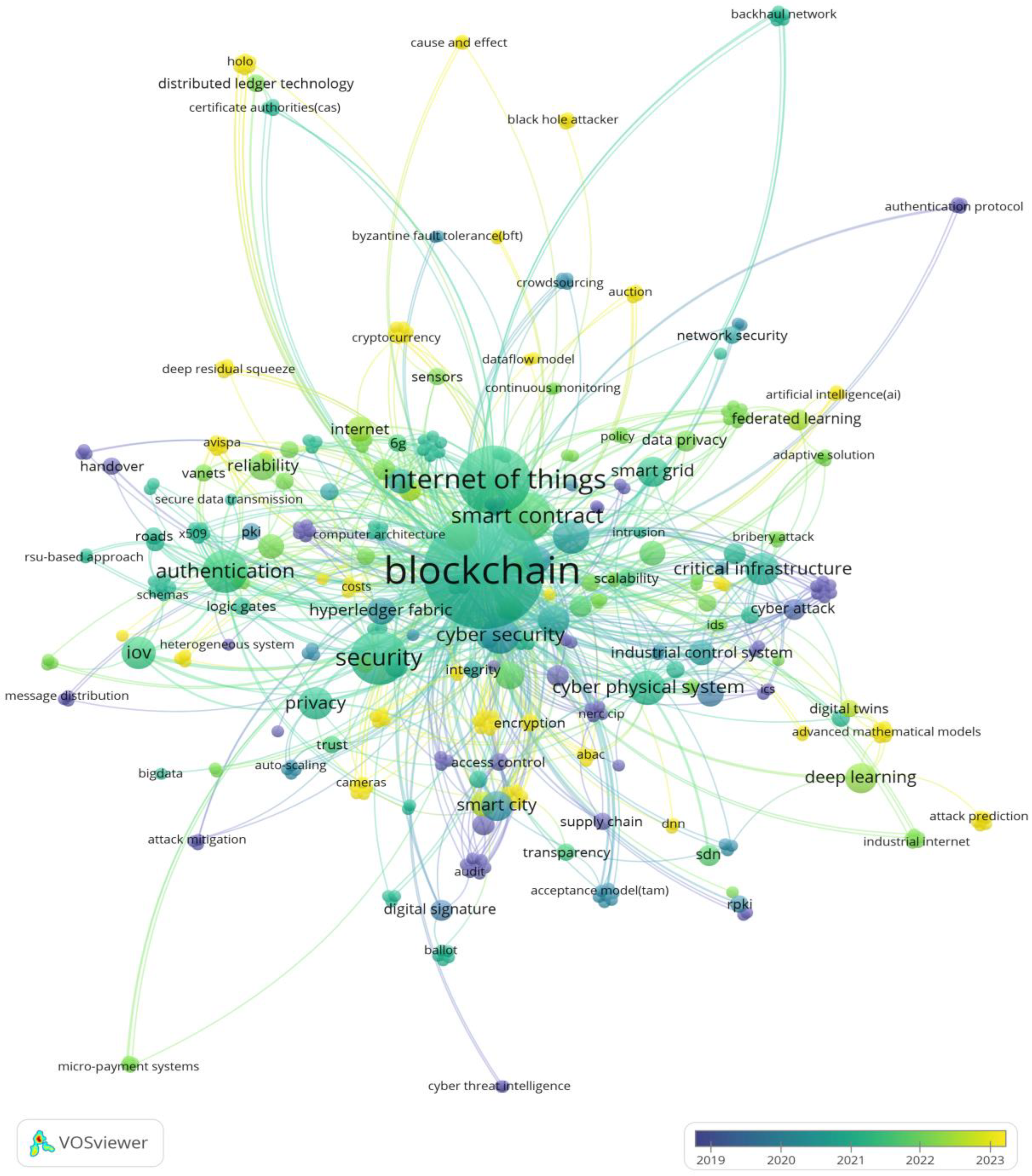
3.3.5. Keywords
4. Blockchain of Operational Technology Security in the Critical Infrastructure Topic Analysis
4.1. Pre-Attack of OTCI
4.1.1. Identity Authentication and Data Validation
- i.
- Identity Authentication
- ii.
- Data Validation
4.1.2. Security Access Control
4.2. During-the-Attack of OTCI
4.2.1. Attack Detection and Perception
4.2.2. Data Security and Protection
- i.
- Data Transit Protection
- ii.
- Data Storage Protection
4.3. Post-Attack of OTCI
4.3.1. Data Backup and Recovery
4.3.2. Attack Assessment and Accountability
5. Design of a General Framework for the Blockchain of Operational Technology Security in the Critical Infrastructure
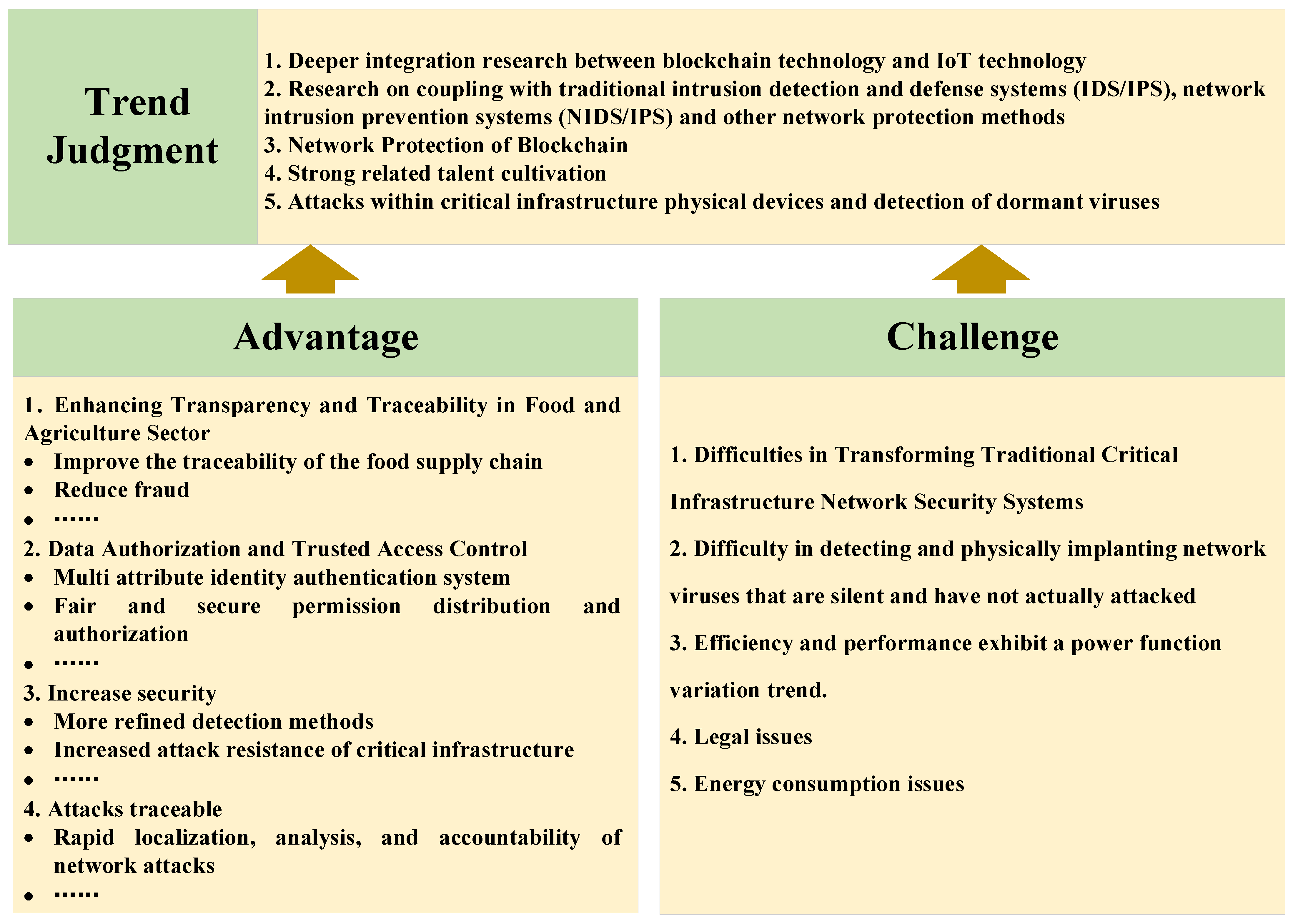
6. Discussion
6.1. Advantage Analysis
6.1.1. Enhancing Transparency and Traceability in Food and Agriculture Sector
6.1.2. Data Validation and Trusted Access Control
6.1.3. Increase Security
6.1.4. Attack Traceability
6.2. Challenge Analysis
6.3. Trend Analysis
7. Conclusions
- The research on BT in OTCI has been reviewed; however, there is a limitation in conducting an in-depth analysis of BT research from a computer science perspective;
- Research on BT in the OTCI is a dynamically evolving field. It is important to note that this study focuses on literature up until September 2023, which means it may not cover the most recent developments in this area;
- This review primarily provides an overview of BT research within OTCI. The defined six topics have a limited scope, and there is a possibility that some relevant and significant topics may not have been included in the analysis.
Author Contributions
Funding
Institutional Review Board Statement
Data Availability Statement
Conflicts of Interest
Appendix A
| No. | Journal Name | TP | IF | H | WQ | Subject Area |
| 1 | IEEE INTERNET OF THINGS JOURNAL | 9 | 8.2 | 47 | Q1 | COMPUTER SCIENCE |
| 2 | IEEE ACCESS | 9 | 3.4 | 56 | Q2 | COMPUTER SCIENCE |
| 3 | ELECTRONICS | 4 | 2.6 | 21 | Q2 | ENGINEERING |
| 4 | CLUSTER COMPUTING-THE JOURNAL OF NETWORKS SOFTWARE TOOLS AND APPLICATIONS | 3 | 3.6 | 35 | Q1 | COMPUTER SCIENCE |
| 5 | WIRELESS PERSONAL COMMUNICATIONS | 2 | 1.9 | 48 | Q3 | COMPUTER SCIENCE |
| 6 | SUSTAINABLE CITIES AND SOCIETY | 2 | 10.5 | 25 | Q1 | ENGINEERING |
| 7 | SUSTAINABILITY | 2 | 3.6 | 53 | Q2 | ENVIRONMENTAL SCIENCES |
| 8 | SCIENTIFIC REPORTS | 2 | 3.8 | 149 | Q1 | MULTIDISCIPLINARY SCIENCES |
| 9 | JOURNAL OF SYSTEMS ARCHITECTURE | 2 | 3.7 | 42 | Q1 | COMPUTER SCIENCE |
| 10 | IEEE TRANSACTIONS ON INTELLIGENT TRANSPORTATION SYSTEMS | 2 | 7.9 | 112 | Q1 | ENGINEERING |
| 11 | IEEE TRANSACTIONS ON INDUSTRIAL INFORMATICS | 2 | 11.7 | 100 | Q1 | ENGINEERING |
| 12 | COMPUTERS & SECURITY | 2 | 4.8 | 77 | Q1 | COMPUTER SCIENCE |
| 13 | CMC-COMPUTERS MATERIALS & CONTINUA | 2 | 2 | 27 | Q3 | COMPUTER SCIENCE |
| 14 | WORLD ELECTRIC VEHICLE JOURNAL | 1 | 2.6 | None | Q2 | ENGINEERING |
| 15 | TRANSACTIONS ON EMERGING TELECOMMUNICATIONS TECHNOLOGIES | 1 | 2.5 | 18 | Q3 | TELECOMMUNICATIONS |
| 16 | SYMMETRY-BASEL | 1 | 2.2 | 24 | Q2 | MATHEMATICS |
| 17 | SENSORS | 1 | 3.4 | 132 | Q2 | MULTIDISCIPLINARY SCIENCES |
| 18 | PERVASIVE AND MOBILE COMPUTING | 1 | 3 | 53 | Q2 | COMPUTER SCIENCE |
| 19 | NEURAL COMPUTING & APPLICATIONS | 1 | 4.5 | 57 | Q2 | COMPUTER SCIENCE |
| 20 | KUWAIT JOURNAL OF SCIENCE | 1 | 1.2 | 9 | Q3 | MULTIDISCIPLINARY SCIENCES |
| 21 | JOURNAL OF THE BRITISH BLOCKCHAIN ASSOCIATION | 1 | 1.4 | None | Q3 | ECONOMICS |
| 22 | JOURNAL OF SUPERCOMPUTING | 1 | 2.5 | 49 | Q2 | COMPUTER SCIENCE |
| 23 | JOURNAL OF NETWORK AND SYSTEMS MANAGEMENT | 1 | 4.1 | 30 | Q1 | COMPUTER SCIENCE |
| 24 | JOURNAL OF MEDICAL INTERNET RESEARCH | 1 | 5.8 | 116 | Q1 | MEDICAL |
| 25 | JOURNAL OF INTELLIGENT & FUZZY SYSTEMS | 1 | 1.7 | 46 | Q3 | COMPUTER SCIENCE |
| 26 | JOURNAL OF INFORMATION SECURITY AND APPLICATIONS | 1 | 3.8 | None | Q2 | COMPUTER SCIENCE |
| 27 | JOURNAL OF ENTERPRISE INFORMATION MANAGEMENT | 1 | 7.4 | None | Q1 | MANAGEMENT |
| 28 | Journal of Applied Sciences | 1 | None | None | None | COMPUTER SCIENCE |
| 29 | INTERNATIONAL JOURNAL OF DISTRIBUTED SENSOR NETWORKS | 1 | 1.9 | 38 | Q3 | COMPUTER SCIENCE |
| 30 | INTERNATIONAL JOURNAL OF ADVANCED COMPUTER SCIENCE AND APPLICATIONS | 1 | 0.7 | None | Q3 | COMPUTER SCIENCE, THEORY & METHODS |
| 31 | INTELLIGENT COMPUTING | 1 | None | None | None | COMPUTER SCIENCE |
| 32 | INFORMATION PROCESSING & MANAGEMENT | 1 | 7.4 | 88 | Q1 | MANAGEMENT, COMPUTER SCIENCE |
| 33 | INFORMATION | 1 | 2.4 | None | Q3 | COMPUTER SCIENCE, INFORMATION SYSTEMS |
| 34 | IEEE WIRELESS COMMUNICATIONS | 1 | 10.9 | 139 | Q1 | COMPUTER SCIENCE |
| 35 | IEEE TRANSACTIONS ON SERVICES COMPUTING | 1 | 5.5 | 56 | Q1 | COMPUTER SCIENCE |
| 36 | IEEE TRANSACTIONS ON NETWORK AND SERVICE MANAGEMENT | 1 | 4.7 | 31 | Q1 | COMPUTER SCIENCE |
| 37 | IEEE TRANSACTIONS ON EMERGING TOPICS IN COMPUTING | 1 | 5.1 | 31 | Q1 | COMPUTER SCIENCE |
| 38 | IEEE TRANSACTIONS ON DEPENDABLE AND SECURE COMPUTING | 1 | 7 | 59 | Q1 | COMPUTER SCIENCE |
| 39 | IEEE NETWORK | 1 | 6.8 | 111 | Q1 | COMPUTER SCIENCE |
| 40 | IEEE COMMUNICATIONS MAGAZINE | 1 | 8.3 | 213 | Q1 | COMPUTER SCIENCE |
| 41 | FUTURE GENERATION COMPUTER SYSTEMS-THE INTERNATIONAL JOURNAL OF ESCIENCE | 1 | 6.2 | 93 | Q1 | COMPUTER SCIENCE |
| 42 | DRONES | 1 | 4.4 | None | Q1 | REMOTE SENSING |
| 43 | DIAGNOSTICS | 1 | 3 | None | Q1 | MEDICINE |
| 44 | CONCURRENCY AND COMPUTATION-PRACTICE & EXPERIENCE | 1 | 1.5 | 60 | Q2 | COMPUTER SCIENCE |
| 45 | COMPUTERS IN INDUSTRY | 1 | 8.2 | 87 | Q1 | COMPUTER SCIENCE |
| 46 | COMPUTERS & ELECTRICAL ENGINEERING | 1 | 4 | 49 | Q1 | COMPUTER SCIENCE |
| 47 | COMPUTER-AIDED CIVIL AND INFRASTRUCTURE ENGINEERING | 1 | 8.5 | 68 | Q1 | CONSTRUCTION & BUILDING TECHNOLOGY |
| 48 | COMPUTER NETWORKS | 1 | 4.4 | 119 | Q1 | COMPUTER SCIENCE |
| 49 | COMPUTER COMMUNICATIONS | 1 | 4.5 | 91 | Q1 | COMPUTER SCIENCE |
| 50 | COMPUTATIONAL INTELLIGENCE AND NEUROSCIENCE | 1 | None | 42 | None | MATHEMATICAL & COMPUTATIONAL BIOLOGY-NEUROSCIENCES |
| 51 | APPLIED ARTIFICIAL INTELLIGENCE | 1 | 2.9 | 52 | Q2 | COMPUTER SCIENCE |
| 52 | ALEXANDRIA ENGINEERING JOURNAL | 1 | 6.2 | None | Q1 | ENGINEERING, MULTIDISCIPLINARY |
| 53 | AD HOC NETWORKS | 1 | 4.4 | 79 | Q1 | COMPUTER SCIENCE |
| TP = total publications; H = h-index; IF = impact factor; WQ = WoS quartile. | ||||||
References
- CISA Food and Agriculture Sector. Available online: https://www.cisa.gov/topics/critical-infrastructure-security-and-resilience/critical-infrastructure-sectors/food-and-agriculture-sector (accessed on 28 November 2024).
- Zahedi, R.; Yousefi, H.; Aslani, A.; Ahmadi, R. Water, energy, food and environment nexus (WEFEN): Sustainable transition, gaps and Covering approaches. Energy Strategy Rev. 2024, 54, 101496. [Google Scholar] [CrossRef]
- Beckman, J.; Countryman, A.M. The importance of agriculture in the economy: Impacts from COVID-19. Am. J. Agric. Econ. 2021, 103, 1595–1611. [Google Scholar] [CrossRef] [PubMed]
- Ghadge, A.; Wurtmann, H.; Seuring, S. Managing climate change risks in global supply chains: A review and research agenda. Int. J. Prod. Res. 2020, 58, 44–64. [Google Scholar] [CrossRef]
- Sung, T.K. Industry 4.0: A Korea perspective. Technol. Forecast. Soc. Change 2018, 132, 40–45. [Google Scholar] [CrossRef]
- Firoozjaei, M.D.; Mahmoudyar, N.; Baseri, Y.; Ghorbani, A.A. An evaluation framework for industrial control system cyber incidents. Int. J. Crit. Infrastruct. Prot. 2022, 36, 100487. [Google Scholar] [CrossRef]
- Hajda, J.; Jakuszewski, R.; Ogonowski, S. Security challenges in industry 4.0 plc systems. Appl. Sci. 2021, 11, 9785. [Google Scholar] [CrossRef]
- Lei, A.; Cruickshank, H.; Cao, Y.; Asuquo, P.; Ogah, C.P.A.; Sun, Z. Blockchain-based dynamic key management for heter-ogeneous intelligent transportation systems. IEEE Internet Things J. 2017, 4, 1832–1843. [Google Scholar] [CrossRef]
- Wang, C.; Shen, J.; Lai, J.-F.; Liu, J. B-TSCA: Blockchain assisted trustworthiness scalable computation for V2I authentication in VANETs. IEEE Trans. Emerg. Top. Comput. 2020, 9, 1386–1396. [Google Scholar] [CrossRef]
- Reilly, E.; Maloney, M.; Siegel, M.; Falco, G. An iot integrity-first communication protocol via an ethereum blockchain light client. In Proceedings of the 2019 IEEE/ACM 1st International Workshop on Software Engineering Research & Practices for the Internet of Things (SERP4IoT), Montreal, QC, Canada, 27 May 2019; pp. 53–56. [Google Scholar]
- Wu, Y.; Dai, H.-N.; Wang, H. Convergence of blockchain and edge computing for secure and scalable IIoT critical infra-structures in industry 4.0. IEEE Internet Things J. 2020, 8, 2300–2317. [Google Scholar] [CrossRef]
- Kendzierskyj, S.; Jahankhani, H. The role of blockchain in supporting critical national infrastructure. In Proceedings of the 2019 IEEE 12th International Conference on Global Security, Safety and Sustainability (ICGS3), London, UK, 16–18 January 2019; pp. 208–212. [Google Scholar]
- Kumar, A.; Sharma, S.; Singh, A.; Alwadain, A.; Choi, B.-J.; Manual-Brenosa, J.; Ortega-Mansilla, A.; Goyal, N. Revolutionary strategies analysis and proposed system for future infrastructure in internet of things. Sustainability 2021, 14, 71. [Google Scholar] [CrossRef]
- Abir, S.A.A.; Anwar, A.; Choi, J.; Kayes, A. Iot-enabled smart energy grid: Applications and challenges. IEEE Access 2021, 9, 50961–50981. [Google Scholar] [CrossRef]
- Alfandi, O.; Khanji, S.; Ahmad, L.; Khattak, A. A survey on boosting IoT security and privacy through blockchain: Exploration, requirements, and open issues. Clust. Comput. 2021, 24, 37–55. [Google Scholar] [CrossRef]
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. 2008. Available online: https://assets.pubpub.org/d8wct41f/31611263538139.pdf (accessed on 9 January 2025).
- Peng, X.; Zhang, X.; Wang, X.; Li, H.; Xu, J.; Zhao, Z.; Wang, Y. Research on the cross-chain model of rice supply chain su-pervision based on parallel blockchain and smart contracts. Foods 2022, 11, 1269. [Google Scholar] [CrossRef] [PubMed]
- Puente, L.; Char, C.; Patel, D.; Thilakarathna, M.S.; Roopesh, M. Research Trends and Development Patterns in Microgreens Publications: A Bibliometric Study from 2004 to 2023. Sustainability 2024, 16, 6645. [Google Scholar] [CrossRef]
- Singh, S.K.; Jeong, Y.-S.; Park, J.H. A deep learning-based IoT-oriented infrastructure for secure smart city. Sustain. Cities Soc. 2020, 60, 102252. [Google Scholar] [CrossRef]
- Noble, M.; Wang, Z. Securing critical infrastructures with location based authentication blockchain. In Proceedings of the Sensors and Smart Structures Technologies for Civil, Mechanical, and Aerospace Systems, Denver, CO, USA, 27 March 2019; pp. 217–224. [Google Scholar]
- Prodan, R.; Saurabh, N.; Zhao, Z.; Orton-Johnson, K.; Chakravorty, A.; Karadimce, A.; Ulisses, A. ARTICONF: Towards a smart social media ecosystem in a blockchain federated environment. In Proceedings of the European Conference on Parallel Processing, Göttingen, Germany, 26–30 August 2019; pp. 417–428. [Google Scholar]
- Rivera, A.O.G.; Tosh, D.K. Towards security and privacy of SCADA systems through decentralized architecture. In Proceedings of the 2019 International Conference on Computational Science and Computational Intelligence (CSCI), Las Vegas, NV, USA, 5–7 December 2019; pp. 1224–1229. [Google Scholar]
- Singh, P.; Masud, M.; Hossain, M.S.; Kaur, A.; Muhammad, G.; Ghoneim, A. Privacy-preserving serverless computing using federated learning for smart grids. IEEE Trans. Ind. Inform. 2021, 18, 7843–7852. [Google Scholar] [CrossRef]
- Samy, S.; Azab, M.; Rizk, M. Towards a secured blockchain-based smart grid. In Proceedings of the 2021 IEEE 11th Annual Computing and Communication Workshop and Conference (CCWC), Virtual, 27–30 January 2021; pp. 1066–1069. [Google Scholar]
- Namane, S.; Ahmim, M.; Kondoro, A.; Dhaou, I.B. Blockchain-based authentication scheme for collaborative traffic light systems using fog computing. Electronics 2023, 12, 431. [Google Scholar] [CrossRef]
- Aman, M.N.; Javaid, U.; Sikdar, B. A privacy-preserving and scalable authentication protocol for the internet of vehicles. IEEE Internet Things J. 2020, 8, 1123–1139. [Google Scholar] [CrossRef]
- Gomez Rivera, A.O.; Tosh, D.K.; Ghosh, U. Resilient sensor authentication in SCADA by integrating physical unclonable function and blockchain. Clust. Comput. 2022, 25, 1869–1883. [Google Scholar] [CrossRef]
- Stephen, S.M.; Jaekel, A. Blockchain based vehicle authentication scheme for vehicular ad-hoc networks. In Proceedings of the 2021 IEEE Intelligent Vehicles Symposium Workshops (IV Workshops), Nagoya, Japan, 11–17 July 2021; pp. 1–6. [Google Scholar]
- Reyneke, M.; Mullins, B.; Reith, M. LoRaWAN & The Helium Blockchain: A Study on Military IoT Deployment. In Proceedings of the International Conference on Cyber Warfare and Security, Baltimore, MD, USA, 9–10 March 2023; pp. 327–337. [Google Scholar]
- Karim, S.M.; Habbal, A.; Chaudhry, S.A.; Irshad, A. BSDCE-IoV: Blockchain-based secure data collection and exchange scheme for IoV in 5G environment. IEEE Access 2023, 11, 36158–36175. [Google Scholar] [CrossRef]
- Sukumaran, R.P.; Benedict, S. Survey on blockchain enabled authentication for industrial Internet of Things. In Proceedings of the 2021 Fifth International Conference on I-SMAC (IoT in Social, Mobile, Analytics and Cloud) (I-SMAC), Palladam, India, 11–13 November 2021; pp. 1510–1516. [Google Scholar]
- Fu, X.; Wang, H.; Shi, P.; Zhang, X. Teegraph: A Blockchain consensus algorithm based on TEE and DAG for data sharing in IoT. J. Syst. Archit. 2022, 122, 102344. [Google Scholar] [CrossRef]
- Yeasmin, S.; Baig, A. Permissioned blockchain: Securing industrial IoT environments. Int. J. Adv. Com-Puter Sci. Appl. 2021, 12, 715–725. [Google Scholar] [CrossRef]
- Hu, N.; Yin, S.; Su, S.; Jia, X.; Xiang, Q.; Liu, H. Blockzone: A decentralized and trustworthy data plane for DNS. Comput. Mater. Contin. 2020, 65, 1531–1557. [Google Scholar] [CrossRef]
- Nyangaresi, V.O.; Abduljabbar, Z.A.; Ma, J.; Al Sibahee, M.A. Verifiable security and privacy provisioning protocol for high reliability in smart healthcare communication environment. In Proceedings of the 2022 4th Global Power, Energy and Communication Conference (GPECOM), Nevsehir, Turkey, 14–17 June 2022; pp. 569–574. [Google Scholar]
- Fang, H. Intelligent Security Provisioning and Trust Management for Future Wireless Communications. Ph.D. Thesis, The University of Western Ontario, London, ON, Canada, August 2020. [Google Scholar]
- Adja, Y.C.E.; Hammi, B.; Serhrouchni, A.; Zeadally, S. A blockchain-based certificate revocation management and status verification system. Comput. Secur. 2021, 104, 102209. [Google Scholar] [CrossRef]
- Burra, M.S.; Maity, S. A Distributed and Decentralized Certificateless Framework for Reliable Shared Data Auditing for FOG-CPS Networks. IEEE Access 2023, 11, 42595–42618. [Google Scholar] [CrossRef]
- Elia, N.; Barchi, F.; Parisi, E.; Pompianu, L.; Carta, S.; Bartolini, A.; Acquaviva, A. Smart contracts for certified and sustainable safety-critical continuous monitoring applications. In Proceedings of the European Conference on Advances in Databases and Information Systems, Turin, Italy, 5–8 September 2022; pp. 377–391. [Google Scholar]
- Aldweesh, A. A Blockchain-Based Data Authentication Algorithm for Secure Information Sharing in Internet of Vehicles. World Electr. Veh. J. 2023, 14, 223. [Google Scholar] [CrossRef]
- Youssef, S.B.H.; Boudriga, N. A resilient micro-payment infrastructure: An approach based on blockchain technology. Kuwait J. Sci. 2022, 49, 1–27. [Google Scholar] [CrossRef]
- Vashistha, M.; Barbhuiya, F.A. Blockchain in Smart Power Grid Infrastructure. In Proceedings of the 2019 ACM International Symposium on Blockchain and Secure Critical Infrastructure, Auckland, New Zealand, 8 July 2019; pp. 89–96. [Google Scholar]
- Yi, H. A secure blockchain system for Internet of Vehicles based on 6G-enabled Network in Box. Comput. Commun. 2022, 186, 45–50. [Google Scholar] [CrossRef]
- Otoum, S.; Al Ridhawi, I.; Mouftah, H. A federated learning and blockchain-enabled sustainable energy trade at the edge: A framework for industry 4.0. IEEE Internet Things J. 2022, 10, 3018–3026. [Google Scholar] [CrossRef]
- Kaur, K.; Garg, S.; Kaddoum, G.; Gagnon, F.; Ahmed, S.H. Blockchain-based lightweight authentication mechanism for vehicular fog infrastructure. In Proceedings of the 2019 IEEE International Conference on Communications Workshops (ICC Workshops), Shanghai, China, 20–24 May 2019; pp. 1–6. [Google Scholar]
- Rendon, C.M.; González-Compeán, J.; Sánchez-Gallegos, D.D.; Carretero, J. Blockchain-based schemes for continuous verifiability and traceability of IoT data. In Proceedings of the 2023 31st Euromicro International Conference on Parallel, Distributed and Network-Based Processing (PDP), Naples, Italy, 1–3 March 2023; pp. 169–172. [Google Scholar]
- Monfared, S.K.; Shokrollahi, S. DARVAN: A fully decentralized anonymous and reliable routing for VANets. Comput. Netw. 2023, 223, 109561. [Google Scholar] [CrossRef]
- Kamalov, F.; Gheisari, M.; Liu, Y.; Feylizadeh, M.R.; Moussa, S. Critical controlling for the network security and privacy based on blockchain technology: A fuzzy dematel approach. Sustainability 2023, 15, 10068. [Google Scholar] [CrossRef]
- Su, L.; Cheng, Y.; Meng, H.; Thing, V.; Wang, Z.; Kong, L.; Cheng, L. Securing Intelligent Transportation System: A Block-chain-Based Approach with Attack Mitigation. In Proceedings of the Smart Blockchain: Second International Conference, SmartBlock 2019, Birmingham, UK, 11–13 October 2019; pp. 109–119. [Google Scholar]
- George, S.A.; Stephen, S.M.; Jaekel, A. Blockchain-based pseudonym management scheme for vehicular communication. Electronics 2021, 10, 1584. [Google Scholar] [CrossRef]
- Jain, G.; Singh, H.; Chaturvedi, K.R.; Rakesh, S. Blockchain in logistics industry: In fizz customer trust or not. J. En-Terprise Inf. Manag. 2020, 33, 541–558. [Google Scholar] [CrossRef]
- Li, X.; Zeng, J.; Chen, C.; Chi, H.L.; Shen, G.Q. Smart work package learning for decentralized fatigue monitoring through facial images. Comput. -Aided Civ. Infrastruct. Eng. 2023, 38, 799–817. [Google Scholar] [CrossRef]
- Putra, G.D.; Dedeoglu, V.; Kanhere, S.S.; Jurdak, R. Toward blockchain-based trust and reputation management for trust-worthy 6G networks. IEEE Netw. 2022, 36, 112–119. [Google Scholar] [CrossRef]
- Lalouani, W. AI Cyber Threat in Cyber Physical Systems. Ph.D. Thesis, University of Maryland, Baltimore, MD, USA, 2022. [Google Scholar]
- Suciu, G.; Farao, A.; Bernardinetti, G.; Palamà, I.; Sachian, M.-A.; Vulpe, A.; Vochin, M.-C.; Muresan, P.; Bampatsikos, M.; Muñoz, A. SAMGRID: Security authorization and monitoring module based on SealedGRID platform. Sensors 2022, 22, 6527. [Google Scholar] [CrossRef] [PubMed]
- Gaba, S.; Khan, H.; Almalki, K.J.; Jabbari, A.; Budhiraja, I.; Kumar, V.; Singh, A.; Singh, K.K.; Askar, S.S.; Abouhawwash, M. Holochain: An agent-centric distributed hash table security in smart IoT applications. IEEE Access 2023, 11, 81205–81223. [Google Scholar] [CrossRef]
- Halgamuge, M.N. Latency estimation of blockchain-based distributed access control for cyber infrastructure in the IoT environment. In Proceedings of the 2021 IEEE 16th Conference on Industrial Electronics and Applications (ICIEA), Chengdu, China, 1–4 August 2021; pp. 510–515. [Google Scholar]
- Ivanov, N.; Yan, Q. AutoThing: A Secure Transaction Framework for Self-Service Things. IEEE Trans. Serv. Com-Puting 2022, 16, 983–995. [Google Scholar] [CrossRef]
- Kong, L.; Chen, C.; Zhao, R.; Chen, Z.; Wu, L.; Yang, Z.; Li, X.; Lu, W.; Xue, F. When permissioned blockchain meets IoT oracles: An on-chain quality assurance system for off-shore modular construction manufacture. In Proceedings of the 2022 IEEE 1st Global Emerging Technology Blockchain Forum: Blockchain & Beyond (iGETblockchain), Irvine, CA, USA, 7–11 November 2022; pp. 1–6. [Google Scholar]
- Lei, K.; Huang, S.; Huang, J.; Liu, H.; Liu, J. Intelligent eco networking (ien) ii: A knowledge-driven future internet infrastructure for value-oriented ecosystem. In Proceedings of the 2019 2nd International Conference on Hot Information-Centric Networking (HotICN), Chongqing, China, 13–15 December 2019; pp. 31–36. [Google Scholar]
- Mhaisen, N.; Fetais, N.; Massoud, A. Secure smart contract-enabled control of battery energy storage systems against cyber-attacks. Alex. Eng. J. 2019, 58, 1291–1300. [Google Scholar] [CrossRef]
- Won, J.; Singla, A.; Bertino, E.; Bollella, G. Decentralized public key infrastructure for internet-of-things. In Proceedings of the MILCOM 2018-2018 IEEE Military Communications Conference (MILCOM), Los Angeles, CA, USA, 29–31 October 2018; pp. 907–913. [Google Scholar]
- Xing, Q.; Wang, B.; Wang, X. Bgpcoin: Blockchain-based internet number resource authority and bgp security solution. Symmetry 2018, 10, 408. [Google Scholar] [CrossRef]
- Lazrag, H.; Chehri, A.; Saadane, R.; Rahmani, M.D. Efficient and secure routing protocol based on Blockchain approach for wireless sensor networks. Concurr. Comput. Pract. Exp. 2021, 33, e6144. [Google Scholar] [CrossRef]
- Xenakis, D.; Tsiota, A.; Koulis, C.-T.; Xenakis, C.; Passas, N. Contract-less mobile data access beyond 5G: Fully-decentralized, high-throughput and anonymous asset trading over the blockchain. IEEE Access 2021, 9, 73963–74016. [Google Scholar] [CrossRef]
- Awais Hassan, M.; Habiba, U.; Ghani, U.; Shoaib, M. A secure message-passing framework for inter-vehicular communication using blockchain. Int. J. Distrib. Sens. Netw. 2019, 15, 1550147719829677. [Google Scholar] [CrossRef]
- Haddaji, A.; Ayed, S.; Chaari, L. Federated learning with blockchain approach for trust management in IoV. In Proceedings of the International Conference on Advanced Information Networking and Applications, Sydney, NSW, Australia, 13–15 April 2022; pp. 411–423. [Google Scholar]
- Hassan, M.; Gregory, M.; Li, S. Blockchain enhanced BGP4 Security for an SDN based Federation. In Proceedings of the 2022 32nd International Telecommunication Networks and Applications Conference (ITNAC), Wellington, New Zealand, 30 November–2 December 2022; pp. 1–7. [Google Scholar]
- Khan, A.A.; Laghari, A.A.; Li, P.; Dootio, M.A.; Karim, S. The collaborative role of blockchain, artificial intelligence, and industrial internet of things in digitalization of small and medium-size enterprises. Sci. Rep. 2023, 13, 1656. [Google Scholar] [CrossRef]
- Dubovitskaya, A.; Baig, F.; Xu, Z.; Shukla, R.; Zambani, P.S.; Swaminathan, A.; Jahangir, M.M.; Chowdhry, K.; Lachhani, R.; Idnani, N. ACTION-EHR: Patient-centric blockchain-based electronic health record data management for cancer care. J. Med. Internet Res. 2020, 22, e13598. [Google Scholar] [CrossRef]
- Sharma, S.; Ghanshala, K.K.; Mohan, S. Blockchain-based internet of vehicles (IoV): An efficient secure ad hoc vehicular networking architecture. In Proceedings of the 2019 IEEE 2nd 5G World Forum (5GWF), Dresden, Germany, 30 September–2 October 2019; pp. 452–457. [Google Scholar]
- Cheema, M.A.; Shehzad, M.K.; Qureshi, H.K.; Hassan, S.A.; Jung, H. A drone-aided blockchain-based smart vehicular network. IEEE Trans. Intell. Transp. Syst. 2020, 22, 4160–4170. [Google Scholar] [CrossRef]
- Ragab, M.; Altalbe, A. A Blockchain-based architecture for enabling cybersecurity in the internet-of-critical infrastructures. Comput. Mater. Contin. 2022, 72, 1579–1592. [Google Scholar] [CrossRef]
- Sai Ganesh, S.; Surya Siddharthan, S.; Rajakumar, B.R.; Neelavathy Pari, S.; Padmanabhan, J.; Priya, V. Hybrid-AI blockchain supported protection framework for smart grids. In Proceedings of the Science and Information Conference, London, UK, 14–15 July 2022; pp. 646–659. [Google Scholar]
- Nasir, M.H.; Arshad, J.; Khan, M.M. Collaborative device-level botnet detection for internet of things. Comput. Secur. 2023, 129, 103172. [Google Scholar] [CrossRef]
- Graf, R.; King, R. Neural network and blockchain based technique for cyber threat intelligence and situational awareness. In Proceedings of the 2018 10th International Conference on Cyber Conflict (CyCon), Tallinn, Estonia, 29 May–1 June 2018; pp. 409–426. [Google Scholar]
- Mylrea, M.; Gourisetti, S.N.G. Blockchain for supply chain cybersecurity, optimization and compliance. In Proceedings of the 2018 resilience week (RWS), Denver, CO, USA, 20–23 August 2018; pp. 70–76. [Google Scholar]
- Demertzis, K.; Iliadis, L.; Tziritas, N.; Kikiras, P. Anomaly detection via blockchained deep learning smart contracts in in-dustry 4.0. Neural Comput. Appl. 2020, 32, 17361–17378. [Google Scholar] [CrossRef]
- Liang, X.; Konstantinou, C.; Shetty, S.; Bandara, E.; Sun, R. Decentralizing cyber physical systems for resilience: An innovative case study from a cybersecurity perspective. Comput. Secur. 2023, 124, 102953. [Google Scholar] [CrossRef]
- Vargas, H.; Lozano-Garzon, C.; Montoya, G.A.; Donoso, Y. Detection of security attacks in industrial IoT networks: A blockchain and machine learning approach. Electronics 2021, 10, 2662. [Google Scholar] [CrossRef]
- Finogeev, A.; Deev, M.; Parygin, D.; Finogeev, A. Intelligent SDN Architecture with Fuzzy Neural Network and Blockchain for Monitoring Critical Events. Appl. Artif. Intell. 2022, 36, 2145634. [Google Scholar] [CrossRef]
- Eisenbarth, J.-P.; Cholez, T.; Perrin, O. Ethereum’s peer-to-peer network monitoring and sybil attack prevention. J. Netw. Syst. Manag. 2022, 30, 65. [Google Scholar] [CrossRef]
- Zhang, H.; Zhang, W.; Feng, Y.; Liu, Y. SVScanner: Detecting smart contract vulnerabilities via deep semantic extraction. J. Inf. Secur. Appl. 2023, 75, 103484. [Google Scholar] [CrossRef]
- Zhang, X.; Zhu, H.; Zhou, J. Shoreline: Data-Driven Threshold Estimation of Online Reserves of Cryptocurrency Trading Platforms. In Proceedings of the AAAI Conference on Artificial Intelligence, New York, NY, USA, 7–12 February 2020; pp. 1194–1201. [Google Scholar]
- Awan, S.M.; Azad, M.A.; Arshad, J.; Waheed, U.; Sharif, T. A blockchain-inspired attribute-based zero-trust access control model for IoT. Information 2023, 14, 129. [Google Scholar] [CrossRef]
- Alangot, B.; Reijsbergen, D.; Venugopalan, S.; Szalachowski, P.; Yeo, K.S. Decentralized and lightweight approach to detect eclipse attacks on proof of work blockchains. IEEE Trans. Netw. Serv. Manag. 2021, 18, 1659–1672. [Google Scholar] [CrossRef]
- Alsulami, F.N. A Comprehensive Analysis of the Environmental Impact on ROPUFs employed in Hardware Security, and Techniques for Trojan Detection. Ph.D. Thesis, The University of Toledo, Toledo, OH, USA, December 2022. [Google Scholar]
- Bernieri, G.; Conti, M.; Sovilla, M.; Turrin, F. ALISI: A lightweight identification system based on Iroha. In Proceedings of the 35th Annual ACM Symposium on Applied Computing, Brno, Czech Republic, 30 March–3 April 2020; pp. 271–273. [Google Scholar]
- Kumar, P.; Kumar, R.; Gupta, G.P.; Tripathi, R. A Distributed framework for detecting DDoS attacks in smart contract-based Blockchain-IoT Systems by leveraging Fog computing. Trans. Emerg. Telecommun. Technol. 2021, 32, e4112. [Google Scholar] [CrossRef]
- He, S.; Ren, W.; Zhu, T.; Choo, K.-K.R. BoSMoS: A blockchain-based status monitoring system for defending against unau-thorized software updating in industrial Internet of Things. IEEE Internet Things J. 2019, 7, 948–959. [Google Scholar] [CrossRef]
- Kumar, R.; Kumar, P.; Kumar, A.; Franklin, A.A.; Jolfaei, A. Blockchain and deep learning for cyber threat-hunting in soft-ware-defined industrial IoT. In Proceedings of the 2022 IEEE International Conference on Communications Workshops (ICC Workshops), Seoul, Republic of Korea, 16 May–20 May 2022; pp. 776–781. [Google Scholar]
- Kravitz, D.W. Transaction immutability and reputation traceability: Blockchain as a platform for access controlled IoT and human interactivity. In Proceedings of the 2017 15th Annual Conference on Privacy, Security and Trust (PST), Calgary, AB, Canada, 28–30 August 2017; pp. 3–309. [Google Scholar]
- Mansour, R.F. Artificial intelligence based optimization with deep learning model for blockchain enabled intrusion detection in CPS environment. Sci. Rep. 2022, 12, 12937. [Google Scholar] [CrossRef] [PubMed]
- Chauhdary, S.H.; Alkatheiri, M.S.; Alqarni, M.A.; Saleem, S. An efficient evolutionary deep learning-based attack prediction in supply chain management systems. Comput. Electr. Eng. 2023, 109, 108768. [Google Scholar] [CrossRef]
- Shaikh, J.A.; Wang, C.; Khan, M.A.; Mohsan, S.A.H.; Ullah, S.; Chelloug, S.A.; Muthanna, M.S.A.; Muthanna, A. A uav-assisted stackelberg game model for securing lomt healthcare networks. Drones 2023, 7, 415. [Google Scholar] [CrossRef]
- Alangot, B.; Reijsbergen, D.; Venugopalan, S.; Szalachowski, P. Decentralized lightweight detection of eclipse attacks on bitcoin clients. In Proceedings of the 2020 IEEE international Conference on Blockchain (Blockchain), Rhodes, Greece, 2–6 November 2020; pp. 337–342. [Google Scholar]
- Zhang, M.; Liu, J.; Feng, K.; Beltran, F.; Zhang, Z. SmartAuction: A blockchain-based secure implementation of private data queries. Future Gener. Comput. Syst. 2023, 138, 198–211. [Google Scholar] [CrossRef]
- Shin, J.S.; Lee, S.; Choi, S.; Jo, M.; Lee, S.-H. A new distributed, decentralized privacy-preserving ID registration system. IEEE Commun. Mag. 2021, 59, 138–144. [Google Scholar] [CrossRef]
- Mena, D.M.M. Blockchain-Based Security Framework for the Internet of Things and Home Networks. Ph.D. Thesis, Purdue University, West Lafayette, IN, USA, May 2021. [Google Scholar]
- Campbell, R. Transitioning to a hyperledger fabric quantum-resistant classical hybrid public key infrastructure. J. Br. Blockchain Assoc. 2019, 2, 11. [Google Scholar] [CrossRef]
- Apeh, A.J.; Ayo, C.K.; Adebiyi, A. A Scalable Blockchain Implementation Model for Nation-Wide Electronic Voting System. In Proceedings of the Computational Science and Its Applications–ICCSA 2021: 21st International Conference, Cagliari, Italy, 13–16 September 2021; pp. 84–100. [Google Scholar]
- George, S.A.; Jaekel, A.; Saini, I. Secure identity management framework for vehicular ad-hoc network using blockchain. In Proceedings of the 2020 IEEE Symposium on Computers and Communications (ISCC), Rennes, France, 7–10 July 2020; pp. 1–6. [Google Scholar]
- Moges, E.; Han, T. DecOp: Decentralized Network Operations in Software Defined Networking using Blockchain. In Proceedings of the IEEE INFOCOM 2020-IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), Toronto, Canada, 6–9 July 2020; pp. 225–230. [Google Scholar]
- Shukla, P.; Patel, R.; Varma, S. A novel of congestion control architecture using edge computing and trustworthy blockchain system. J. Intell. Fuzzy Syst. 2023, 44, 6303–6326. [Google Scholar] [CrossRef]
- Wang, L.; Zheng, Y.; Zhang, Y.; Li, F. Secure spectrum sharing for satellite internet-of-things based on blockchain. Wirel. Pers. Commun. 2023, 131, 357–369. [Google Scholar] [CrossRef]
- Moztarzadeh, O.; Jamshidi, M.; Sargolzaei, S.; Keikhaee, F.; Jamshidi, A.; Shadroo, S.; Hauer, L. Metaverse and medical di-agnosis: A blockchain-based digital twinning approach based on MobileNetV2 algorithm for cervical vertebral maturation. Diagnostics 2023, 13, 1485. [Google Scholar] [CrossRef] [PubMed]
- Anglés-Tafalla, C.; Viejo, A.; Castellà-Roca, J.; Mut-Puigserver, M.; Payeras-Capellà, M.M. Security and privacy in a block-chain-powered access control system for low emission zones. IEEE Trans. Intell. Transp. Syst. 2022, 24, 580–595. [Google Scholar] [CrossRef]
- Sunny, J.; Sankaran, S.; Saraswat, V. Towards a lightweight blockchain platform for critical infrastructure protection. In Proceedings of the 2020 IEEE 40th International Conference on Distributed Computing Systems (ICDCS), Singapore, 29 November–1 December 2020; pp. 1287–1292. [Google Scholar]
- Otoum, S.; Mouftah, H.T. Enabling trustworthiness in sustainable energy infrastructure through blockchain and AI-assisted solutions. IEEE Wirel. Commun. 2021, 28, 19–25. [Google Scholar] [CrossRef]
- Khan, K.M.; Arshad, J.; Iqbal, W.; Abdullah, S.; Zaib, H. Blockchain-enabled real-time SLA monitoring for cloud-hosted services. Clust. Comput. 2022, 25, 537–559. [Google Scholar] [CrossRef]
- Dimogerontakis, E.; Navarro, L.; Selimi, M.; Mosquera, S.; Freitag, F. Contract networking for crowdsourced connectivity. In Proceedings of the 2020 IEEE International Conference on Decentralized Applications and Infrastructures (DAPPS), Oxford, UK, 3–6 August 2020; pp. 126–132. [Google Scholar]
- Laghari, A.A.; Khan, A.A.; Alkanhel, R.; Elmannai, H.; Bourouis, S. Lightweight-biov: Blockchain distributed ledger tech-nology (bdlt) for internet of vehicles (iovs). Electronics 2023, 12, 677. [Google Scholar] [CrossRef]
- Pothumani, S.; Arunachalam, A. Effective security mechanisms for big data using block chain technology. In Proceedings of the 2021 International Conference on Computer Communication and Informatics (ICCCI), Coimbatore, India, 27–29 January 2021; pp. 1–6. [Google Scholar]
- Peng, X.; Zhang, X.; Wang, X.; Xu, J.; Li, H.; Zhao, Z.; Qi, Z. A refined supervision model of rice supply chain based on multi-blockchain. Foods 2022, 11, 2785. [Google Scholar] [CrossRef]
- Mayer, A.H.; Rodrigues, V.F.; da Costa, C.A.; da Rosa Righi, R.; Roehrs, A.; Antunes, R.S. Fogchain: A fog computing ar-chitecture integrating blockchain and internet of things for personal health records. IEEE Access 2021, 9, 122723–122737. [Google Scholar] [CrossRef]
- Singh, A.; Kumar, D.; Hötzel, J. IoT Based information and communication system for enhancing underground mines safety and productivity: Genesis, taxonomy and open issues. Ad Hoc Netw. 2018, 78, 115–129. [Google Scholar] [CrossRef]
- Ebrahimpour, G.; Haghighi, M.S.; Alazab, M. Can blockchain be trusted in industry 4.0? study of a novel misleading attack on bitcoin. IEEE Trans. Ind. Inform. 2022, 18, 8307–8315. [Google Scholar] [CrossRef]
- Wang, D.; Zhu, Y.; Zhang, Y.; Liu, G. Security assessment of blockchain in Chinese classified protection of cybersecurity. IEEE Access 2020, 8, 203440–203456. [Google Scholar] [CrossRef]
- Moradpoor, N.; Barati, M.; Robles-Durazno, A.; Abah, E.; McWhinnie, J. Neutralizing Adversarial Machine Learning in Industrial Control Systems Using Blockchain. In Proceedings of the International Conference on Cybersecurity, Situational Awareness and Social Media: Cyber Science, Wales, UK, 20–21 June 2022; pp. 437–451. [Google Scholar]
- Raj, J.M.; Ranjani, S.S. A secured blockchain method for multivariate industrial IoT-oriented infrastructure based on deep residual squeeze and excitation network with single candidate optimizer. Internet Things 2023, 22, 100823. [Google Scholar]
- Otoum, S.; Al Ridhawi, I.; Mouftah, H. Securing critical IoT infrastructures with blockchain-supported federated learning. IEEE Internet Things J. 2021, 9, 2592–2601. [Google Scholar] [CrossRef]
- Ali, S.; Wang, G.; Bhuiyan, M.Z.A.; Jiang, H. Secure data provenance in cloud-centric internet of things via blockchain smart contracts. In Proceedings of the 2018 IEEE SmartWorld, Ubiquitous Intelligence & Computing, Advanced & Trusted Computing, Scalable Computing & Communications, Cloud & Big Data Computing, Internet of People and Smart City Innovation (Smart-World/SCALCOM/UIC/ATC/CBDCom/IOP/SCI), Guangzhou, China, 8–12 October 2018; pp. 991–998. [Google Scholar]
- Rahman, Z.; Khalil, I.; Yi, X.; Atiquzzaman, M. Blockchain-based security framework for a critical industry 4.0 cyber-physical system. IEEE Commun. Mag. 2021, 59, 128–134. [Google Scholar] [CrossRef]
- Tosh, D.; Shetty, S.; Foytik, P.; Kamhoua, C.; Njilla, L. CloudPoS: A proof-of-stake consensus design for blockchain integrated cloud. In Proceedings of the 2018 IEEE 11th International Conference on Cloud Computing (CLOUD), San Francisco, CA, USA, 2–7 July 2018; pp. 302–309. [Google Scholar]
- Hou, L.; Zheng, K.; Liu, Z.; Xu, X.; Wu, T. Design and prototype implementation of a blockchain-enabled LoRa system with edge computing. IEEE Internet Things J. 2020, 8, 2419–2430. [Google Scholar] [CrossRef]
- Maw, A.; Adepu, S.; Mathur, A. ICS-BlockOpS: Blockchain for operational data security in industrial control system. Pervasive Mob. Comput. 2019, 59, 101048. [Google Scholar] [CrossRef]
- Alfandi, O.; Otoum, S.; Jararweh, Y. Blockchain solution for IoT-based critical infrastructures: Byzantine fault tolerance. In Proceedings of the NOMS 2020-2020 IEEE/IFIP Network Operations and Management Symposium, Budapest, Hungary, 20–24 April 2020; pp. 1–4. [Google Scholar]
- Ahmad, I.; Abdullah, S.; Ahmed, A. IoT-fog-based healthcare 4.0 system using blockchain technology. J. Super-Comput. 2023, 79, 3999–4020. [Google Scholar] [CrossRef] [PubMed]
- Colelli, R.; Foglietta, C.; Fusacchia, R.; Panzieri, S.; Pascucci, F. Blockchain application in simulated environment for Cyber-Physical Systems Security. In Proceedings of the 2021 IEEE 19th International Conference on Industrial Informatics (INDIN), Palma de Mallorca, Spain, 21–23 July 2021; pp. 1–7. [Google Scholar]
- Faisal, T.; Dohler, M.; Mangiante, S.; Lopez, D.R. BEAT: Blockchain-Enabled Accountable and Transparent Infrastructure Sharing in 6G and Beyond. IEEE Access 2022, 10, 48660–48672. [Google Scholar] [CrossRef]
- Wu, T.; Wang, W.; Zhang, C.; Zhang, W.; Zhu, L.; Gai, K.; Wang, H. Blockchain-based anonymous data sharing with ac-countability for Internet of Things. IEEE Internet Things J. 2022, 10, 5461–5475. [Google Scholar] [CrossRef]
- Suhail, S.; Malik, S.U.R.; Jurdak, R.; Hussain, R.; Matulevičius, R.; Svetinovic, D. Towards situational aware cyber-physical systems: A security-enhancing use case of blockchain-based digital twins. Comput. Ind. 2022, 141, 103699. [Google Scholar] [CrossRef]
- Fan, Q.; Chen, J.; Deborah, L.J.; Luo, M. A secure and efficient authentication and data sharing scheme for Internet of Things based on blockchain. J. Syst. Archit. 2021, 117, 102112. [Google Scholar] [CrossRef]
- Xu, R.; Li, C.; Joshi, J. Blockchain-based transparency framework for privacy preserving third-party services. IEEE Trans. Dependable Secur. Comput. 2022, 20, 2302–2313. [Google Scholar] [CrossRef]
| Journal | Year | Field | Analytical Method | Censorship Content |
|---|---|---|---|---|
| [11] | 2020 | Internet of things | Content analysis | IoT/IIoT CI security review in Industry 4.0 |
| [12] | 2019 | Healthcare, Cyber–Physical Systems | Content analysis | An introduction to critical national infrastructure cybersecurity |
| [13] | 2022 | Internet of things | Content analysis | The current state of the art of different IoT architectures, as well as current technologies, applications, challenges, IoT protocols, and opportunities |
| [14] | 2021 | Energy system | Content analysis | Architecture and functionality of IoT-enabled smart energy grid systems |
| [15] | 2021 | Internet of things | Content analysis | Security and privacy challenges related to IoT |
| Sector | China | U.S. | Germany | Russia |
|---|---|---|---|---|
| Chemical Sector | √ | |||
| Commercial Facilities Sector | √ | |||
| Communications Sector | √ | √ | √ | √ |
| Critical Manufacturing Sector | √ | √ | ||
| Dams Sector | √ | √ | √ | |
| Defense Industrial Base Sector | √ | √ | ||
| Emergency Services Sector | √ | √ | ||
| Energy Sector | √ | √ | √ | |
| Financial Services Sector | √ | √ | √ | |
| Food and Agriculture Sector | √ | √ | ||
| Government Facilities Sector | √ | √ | √ | √ |
| Healthcare and Public Health Sector | √ | √ | √ | |
| Information Technology Sector | √ | |||
| Nuclear Reactors | √ | |||
| Materials and Waste Sector | √ | |||
| Transportation Systems Sector | √ | √ | √ | √ |
| Water and Wastewater Sector | √ | √ | √ | |
| Technology/Research Sector | √ | √ | ||
| Education Sector | √ | |||
| Social Security Sector | √ | |||
| Important Internet Applications Sector | √ | |||
| Judicial Sector | √ | |||
| Media and Culture Sector | √ |
| No. | Country | Number of Documents | Number of References | Total Citations |
|---|---|---|---|---|
| 1 | USA | 30 | 839 | 347 |
| 2 | China | 23 | 946 | 236 |
| 3 | India | 21 | 954 | 200 |
| 4 | Saudi Arabia | 12 | 538 | 31 |
| 5 | Pakistan | 11 | 534 | 108 |
| 6 | United Kingdom | 9 | 467 | 507 |
| 7 | Canada | 9 | 199 | 103 |
| 8 | Australia | 8 | 263 | 92 |
| 9 | United Arab Emirates | 7 | 290 | 87 |
| 10 | Singapore | 6 | 171 | 97 |
| Pre-Attack Stage of OTCI | Identity Authentication and Data Validation | Identity Authentication | [9,19,20,21,22,23,24,25,26,27,28,29,30,31,32,33,34,35,36,37] |
| Data Validation | [8,38,39,40,41,42,43,44,45,46,47,48,49,50,51,52,53,54] | ||
| Security Access Control | [55,56,57,58,59,60,61,62,63,64,65,66,67,68,69,70,71,72] | ||
| During-the-Attack Stageof OTCI | Attack Detection and Perception | [73,74,75,76,77,78,79,80,81,82,83,84,85,86,87,88,89,90,91,92,93,94,95,96] | |
| Data Security and Protection | Data Transit Protection | [10,97,98,99,100,101,102,103,104,105,106,107,108,109,110,111,112,113,114,115,116,117,118] | |
| Data Storage Protection | [119,120,121,122,123,124,125] | ||
| Post-Attack Stage of OTCI | Data Backup and Recovery | [126,127,128,129] | |
| Attack Assessment and Attribution | [130,131,132,133,134] | ||
| Literature | Field | Types of Attacks | Effect | Impact on the Food and Agriculture Sector | |
|---|---|---|---|---|---|
| [19,29,31,32,33,36,37] | Communication Systems | Internet of Things | Replay Attacks, Man-in-the-Middle Attacks, DNS Cache Poisoning, Distributed Denial of Service (DDoS) Attacks | Reducing authentication costs, enhancing authentication efficiency, and bolstering security | Leading to supply chain disruptions, affecting food supply and prices, as well as consumer trust in food brands |
| [34] | Internet | ||||
| [20,23,24] | Energy Systems | Data Injection | Ensuring system resilience, reducing penetration rates, and enhancing the security of smart grid operational management | Affecting the stability of energy systems, thereby impacting the operation of food processing and agricultural machinery | |
| [9,25,26,28,30] | Transportation Systems | Physical, Side-Channel, and Clone Attacks | Reducing authentication overhead and improving authentication efficiency | Impacting the logistics and distribution of food and agricultural products, leading to supply chain delays or disruptions | |
| [22,27] | Industrial Control Systems | Denial of Service Attacks, Data and Identity Deception, and Data Poisoning | By ensuring the integrity and authenticating the identities of underlying sensor data, the reliability of ICS/SCADA ecosystems is enhanced | Resulting in the tampering of sensor data in industrial control systems, affecting food safety and production efficiency | |
| [21] | Social Media and Online Communities | Identity Spoofing, Password Guessing and Cracking, and so on | Ensure the trustworthiness of user identities on proprietary social media platforms | Attacks on social media affect consumer trust in food brands and influence purchasing decisions | |
| [35] | Healthcare System | Attacks, Side-Channel Attacks, Impersonation Threats, Man-in-the-Middle Attacks, and others | Perform mutual authentication between biometric sensor units and hospital medical servers | Attacks on healthcare systems indirectly impact the food and agriculture sector, as they may affect the health and safety of food processing workers | |
| Literature | Field | Research Method | Effect | Impact on the Food and Agriculture Sector |
|---|---|---|---|---|
| [38,46,48,53,54] | Communication System | Method Design | Provides data auditing to ensure that IoT data streams offer the organization verifiable information, enabling the secure execution of critical decision-making processes | By ensuring IoT data streams provide verifiable information, the security and reliability of data in agricultural decision-making processes are enhanced, contributing to precision agriculture and food safety monitoring |
| [42,44] | Energy System | System/Framework Development | Secure sharing of energy resources among users and devices in a networked environment | Secure sharing of energy resources in a networked environment can improve the energy efficiency of agricultural mechanization and food processing, reducing costs |
| [8,40,43,45,47,49,50] | Transportation System | Method Design | Maintains and authenticates shared data to achieve trustworthy information sharing among vehicles | Ensuring the maintenance and authentication of data shared between vehicles enhances the efficiency and safety of agricultural product logistics, minimizing losses during transportation |
| [41] | Financial System | Method Design | Reduces the complexity of transaction verification, minimizes losses, and prevents various network attacks | Reducing the complexity of transaction verification, minimizing losses, and preventing cyberattacks contribute to the security and efficiency of agricultural financial services, safeguarding the funds of farmers and agricultural enterprises |
| [39,52] | Building Facility Security | Architecture/Method Design | Authenticates data and human behavior to ensure the security of building facility-related data | Authenticating data and human behavior to ensure the security of building-related data is critical for the safety of food processing and storage facilities, helping to maintain food safety |
| Literature | Field | Research Method | Effect | Impact on the Food and Agriculture Sector |
|---|---|---|---|---|
| [66,67,71,72] | Transportation Systems | Method Design | Facilitates secure communication between users in the connected vehicle network | Ensuring secure communication between users in vehicle networks improves the efficiency and safety of agricultural product logistics, reducing losses during transportation and minimizing food waste |
| [70] | Healthcare Systems | Case Study | Ensures secure sharing of electronic health records | Securing the sharing of electronic health records helps monitor the health of agricultural workers, thereby enhancing agricultural productivity and food safety |
| [60,62,63,64,65,68,69] | Communication Systems | Method Design | Achieves personnel and IoT device access management and trusted authorization, ensuring trusted data sharing | Implementing access management and trusted authorization for personnel and IoT devices ensures the trusted sharing of agricultural data, improving the decision-making quality and efficiency of precision agriculture |
| [55,61] | Energy Systems | Method Design | Implements access control for data and other resources using blockchain and smart contracts | Using blockchain and smart contracts to enforce access control for data and other resources enhances the transparency and efficiency of agricultural energy use, reducing costs |
| [58] | Financial Systems | Method Design | Replaces permissive API with multi-signature transaction tokens, enhancing network defense resilience in self-service terminal systems | Replacing APIs with multi-signature transaction tokens strengthens the cybersecurity of self-service terminal systems, safeguarding agricultural financial services |
| [57] | Industrial Control Systems | Method Design | Enables distributed access control through authentication and authorization | Achieving distributed access control through authentication and authorization improves the security and efficiency of agricultural automation systems |
| [59] | Building Facilities | Method Design | Utilizes a blockchain network to provide authentication functions, ensuring authorized access to channels related to quality inspections | Leveraging blockchain networks to provide authentication functionality ensures authorized access to quality inspection-related channels, enhancing the safety of food processing facilities and product quality |
| [56] | Food and Agriculture Systems | Case Study | Protects personal data related to agricultural land records and prevents unauthorized access | Protecting personal data related to agricultural land records prevents unauthorized access, ensuring the security of agricultural production data and safeguarding farmers’ rights |
| Literature | Field | Attack Detection/Perception Categories | Effect | Impact on the Food and Agriculture Sector |
|---|---|---|---|---|
| [73,78,91] | Industrial Control Systems | False Routing Attacks | Detect anomalies in relevant infrastructure operational parameters while ensuring anonymity and confidentiality of industrial information | Detecting abnormal operating parameters in industrial control systems protects the anonymity and confidentiality of industrial information, which is crucial for agricultural automation and food processing, preventing the tampering of critical production data |
| [74,77,79,85,87] | Energy Systems | False Data Injection Attacks (FDIAs), Distributed Denial of Service (DDoS) Attacks | Detect/perceive attacks involving data, users, and services within smart grids, energy transmission systems, and bulk power systems to enhance detection resilience | Detecting data, user, and service attacks in smart grids, energy transmission systems, and large power systems enhances detection resilience, which is vital for ensuring the energy supply for agriculture and the energy demands of food processing |
| [76,80,81] | Transportation Systems | Packet Injection (Fuzzing) and Denial of Service (DoS) Attacks | Perform real-time and automated network situational awareness and attack detection in transportation systems | Real-time and automated network situational awareness and attack detection are crucial for ensuring the security and efficiency of agricultural product logistics and distribution systems, reducing transportation disruptions and food waste |
| [75,88,89,90,92,93,94,95] | Communication Systems | Botnet Attacks, DDoS Attacks, Intrusion Attacks | Create a trusted environment and signature-based detection schemes for effective detection of known attacks | Creating trusted environments and signature-based detection schemes to effectively detect known attacks is essential for protecting agricultural communication networks and food safety communications |
| [84] | Financial Systems | Theft Attacks | Assist in attack detection through threshold estimation of hot wallets | Assisting attack detection through threshold estimation of hot wallets is crucial for safeguarding agricultural financial services and farmers’ funds |
| [82,83,86,96] | BT | Sybil Attacks, Eclipse Attacks | Detecting attacks on blockchain nodes, smart contracts, and more | Detecting attacks on blockchain nodes, smart contracts, and other components is critical for protecting agricultural supply chains and blockchain applications related to food safety |
| Literature | Field | Research Method | Effect | Impact on the Food and Agriculture Sector |
|---|---|---|---|---|
| [10,99,103,105,108,111,116] | Communication Systems | Method Design | Enhancing network communication security based on optimal resource allocation | Helps ensure the secure transmission of sensitive data in the food and agriculture sectors, safeguarding the security of agricultural supply chains and market information exchange |
| [97] | Financial Systems | Method Design | Ensuring the security and fairness of trading network infrastructure | Protects the interests of farmers and agricultural businesses in financial transactions |
| [98,109] | Energy Systems | Method/Scheme Design | Using BT in smart grids to provide integrity and anonymity | Enhances the transparency of energy usage in the food and agriculture sectors, reduces energy costs, and strengthens energy management |
| [100,106,115] | Healthcare Systems | Case Studies/Method Design | Maintaining the security and privacy of collected healthcare-sensitive data | Helps protect the health information of food and agriculture workers, improving the quality of healthcare services in agricultural communities |
| [101] | Electronic Voting | Method Design | Protecting the integrity of voting data | Contributes to the fairness and transparency of the voting process in food and agriculture policy decision-making |
| [102,104,107,112] | Transportation Systems | Method Design | Ensuring integrity, availability, reliable information exchange, and source trustworthiness of vehicle-related data | Improves the logistics efficiency and security of food and agricultural products |
| [110] | Cloud Computing | Method Design | Enabling accurate execution of service level agreements (SLAs) by all stakeholders through publicly maintained immutable ledgers in a blockchain network, without inaccuracies or delays | Increases the efficiency and reliability of cloud services in the food and agriculture sector |
| [114] | Food and Agriculture Systems | Scheme Design | Improving security, privacy, transparency, and trust among all stakeholders in agricultural supply chains | Enhances the security, privacy, transparency, and trustworthiness of all stakeholders in the agricultural supply chain |
| [113,117,118] | BT | Scheme Design | Security of data collection, data retrieval, and data processing | Protects the integrity of agricultural data, contributing to the accuracy of agricultural decision-making |
| Literature | Field | Research Method | Effect | Impact on the Food and Agriculture Sector |
|---|---|---|---|---|
| [119,123] | Industrial Control Systems | Method Design | Protecting and maintaining data in industrial control systems to provide a trustworthy data source | Providing trustworthy data sources for the food and agriculture sectors, ensuring the accuracy and reliability of data during the production process |
| [120,121,125] | Communication Systems | Scheme/Model Design | Preventing data forgery or loss during the communication phase | Protecting data in the supply chain from tampering, ensuring the transparency and security of food traceability and supply chain management |
| [122,124] | Cloud Storage | Framework Design | Safely recording data operations that occur in the cloud environment | Achieving the secure storage and management of vast agricultural data, such as crop monitoring, soil analysis, and market data, in the cloud, improving the efficiency and security of data processing |
| Literature | Field | Research Method | Effect | Impact on the Food and Agriculture Sector |
|---|---|---|---|---|
| [127] | Internet of Things | Method Design | BT-based IoT architecture enabling distributed storage | Protecting agricultural data from tampering, enhancing the transparency and traceability of the food supply chain |
| [128] | Healthcare Systems | Method Design | Data and interaction records distributed on blockchain for trusted recovery of electronic healthcare systems | Ensuring the security of agricultural workers’ health records helps increase trust in the healthcare services provided to agricultural communities |
| [126,129] | Industrial Control Systems | Method Design | Supporting data recovery after attacks through efficient replication mechanisms | Helping agricultural control systems quickly recover critical data after a cyberattack reduces the potential impact on agricultural production and the food supply chain |
| Attack Category | Description |
|---|---|
| Distributed denial of service attack | Attackers send a large number of requests to the target system, occupying its resources, causing the system to fail to run properly and thus interrupting services. |
| Ransomware attack | Attackers encrypt critical systems or data with malware and then blackmail the injured party into paying a ransom to unlock them. |
| Supply chain attack | By planting malware or tampering with hardware at key points in the supply chain, attackers can exploit vulnerabilities to attack targeted systems when products or services are delivered to end users. |
| Malware attack | Attackers can gain improper access or steal sensitive information by introducing malware, such as viruses, trojans, or spyware, into a target system. |
| Insider attack | Refers to the abuse of access rights by individuals within a business or organization to attack CI or intentionally disclose sensitive information. |
| Zero-day attack | Exploit undisclosed vulnerabilities in software or systems. These vulnerabilities are often unpatched and can be used by an attacker to break into a system before the attacker is aware of them. |
| Identity fraud | Attackers use forged identities to impersonate legitimate users and gain access to CI. |
| Social engineering attack | Attackers gain access to systems or sensitive information by communicating with people or spoofing them, such as phishing emails, phone scams, etc. |
| Phase | Model | Problem Solving |
|---|---|---|
| Pre-Attack stage of OTCI | Blockchain-based data recording model | Identity authentication and verification of equipment, personnel and data, permission distribution and access control, and data recording and leaving marks throughout the process |
| Blockchain-based identity authentication model | ||
| Blockchain-based data verification model | ||
| Blockchain-based permission distribution model | ||
| Blockchain-based access control model | ||
| During-the-attack stage of OTCI | Blockchain-based attack detection model | Detection and defense of network attack models |
| Blockchain-based data protection model | ||
| Post-attack stage of OTCI | Blockchain-based attack assessment model | Cyberattack analysis, data recovery, and location and accountability |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zheng, C.; Peng, X.; Wang, Z.; Ma, T.; Lu, J.; Chen, L.; Dong, L.; Wang, L.; Cui, X.; Shen, Z. A Review on Blockchain Applications in Operational Technology for Food and Agriculture Critical Infrastructure. Foods 2025, 14, 251. https://doi.org/10.3390/foods14020251
Zheng C, Peng X, Wang Z, Ma T, Lu J, Chen L, Dong L, Wang L, Cui X, Shen Z. A Review on Blockchain Applications in Operational Technology for Food and Agriculture Critical Infrastructure. Foods. 2025; 14(2):251. https://doi.org/10.3390/foods14020251
Chicago/Turabian StyleZheng, Chengliang, Xiangzhen Peng, Ziyue Wang, Tianyu Ma, Jiajia Lu, Leiyang Chen, Liang Dong, Long Wang, Xiaohui Cui, and Zhidong Shen. 2025. "A Review on Blockchain Applications in Operational Technology for Food and Agriculture Critical Infrastructure" Foods 14, no. 2: 251. https://doi.org/10.3390/foods14020251
APA StyleZheng, C., Peng, X., Wang, Z., Ma, T., Lu, J., Chen, L., Dong, L., Wang, L., Cui, X., & Shen, Z. (2025). A Review on Blockchain Applications in Operational Technology for Food and Agriculture Critical Infrastructure. Foods, 14(2), 251. https://doi.org/10.3390/foods14020251







