Abstract
Ring signatures are widely used in e-voting, anonymous whistle-blowing systems, and blockchain transactions. However, due to the anonymity of ring signatures, a signer can sign the same message multiple times, potentially leading to repeated voting or double spending in blockchain transactions. To address these issues in blockchain transactions, this work constructs an identity-based linkable ring signature scheme based on the hardness of the lattice-based Module Small Integer Solution (M-SIS) assumption, which is hard even for quantum attackers. The proposed scheme is proven to be anonymous, unforgeable, linkable, and nonslanderable in the random oracle model. Compared to existing identity-based linkable ring signature (IBLRS) schemes of linear size, our signature size is relatively smaller, and this advantage is more pronounced when the number of ring members is small. We provide approximate signature size data for ring members ranging from 2 to 2048. When the number of ring members is 16 (or 512. resp.), the signature size of our scheme is 11.40 KB (or 24.68 KB, respectively). Finally, a threshold extension is given as an additional scheme with specifications and security analysis.
1. Introduction
A ring signature, first proposed [] by Rivest et al. in 2001, allows the signer to create signatures in the name of a group include him or herself (called a ring). A ring signature is verified to come from a ring, without knowing the identity of the real signer, thus ensuring the anonymity. To meet the privacy and security needs of both parties in blockchain transactions, ring signatures have been introduced to ensuring the anonymity of transaction user identities and transaction security in the last decade or so [,]. The first use of ring signatures on blockchains was in the Cryptonote protocol research conducted by Saberhagen et al. [] in 2013. The Cryptonote protocol proposed two major privacy-related properties that an anonymous e-cash system needs to satisfy: untraceability and unlinkability. To meet these requirements, the protocol uses one-time public–private key pairs to protect the privacy of the recipient in transactions and, at the same time, uses one-time ring signatures to protect the privacy of the sender. This provides an important practical case and theoretical basis for the application of ring signatures in blockchain privacy protection.
However, using ring signatures to solve the privacy protection problem on blockchains also introduces the “double-spending” problem due to its anonymity. “Double spending”, also known as double payment, refers to the situation where the same digital asset is used repeatedly. The linkable ring signature first introduced by Liu et al. [] in 2004 provides a solution. By linking two legitimate ring signatures created by the same sender for a single message, the “double-spending” problem in blockchain technology can be solved.
Early linkable ring signatures were built based on Public Key Infrastructure (PKI), where certificate management issues increased computational costs. This issue can be solved by identity-based cryptography, which was proposed by Adi Shamir [] in 1984. An identity-based signature (IBS) allows users to directly generate public keys from their identities, such as email addresses or usernames, without the need for certificates. Combining identity-based cryptography with linkable ring signature technology to achieve an identity-based linkable ring signature (IBLRS) is a significant topic that addresses identity authentication and key management issues while providing linkability to prevent repeated signatures. In 2006, Chow et al. [] proposed the first IBLRS scheme based on the bilinear pairing assumption. Subsequently, numerous IBLRS schemes emerged [,,,,,].
However, many of the above schemes rely on traditional number-theoretic assumptions, including factoring and discrete logarithms, which become vulnerable to quantum attacks with the development of large-scale quantum computers [,]. So, researchers start to turn their attention to post-quantum cryptography []. Among the post-quantum candidates, lattice-based cryptography is the most promising one. This can be confirmed by the post-quantum algorithmic standards selected by NIST (National Institute of Standards and Technology) after years of analysis and argumentation []. Therefore, this work chooses to construct identity linkable ring signatures that rely on a lattice-based assumption to achieve post-quantum security, thus provide identity privacy, as well as linkability to avoid double spending in blockchain transactions.
1.1. Contributions
Based on the lattice-based hard problem, we propose an identity-based linkable dual-ring signature scheme as well as its threshold extension. Our proposal has several advantages:
- (1)
- It applies identity information directly for public key operations to remove the need for certificates and third-party certificate authorities, and fully demonstrates the flexibility of identity-based keys.
- (2)
- By adopting a dual-ring structure, it has a very short signature size, especially when the ring scale is not very large (below 2000). The “double-spending” problem in general ring signature schemes is solved by adding linkability.
- (3)
- The scheme proposed in this paper is based on the lattice-based M-SIS assumption and can resist quantum attacks. It is proved in the random oracle model that this scheme is correct, anonymous, unforgeable, linkable, and nonslanderable.
- (4)
- It presents a threshold extension with detailed explanations and security analysis.
1.2. Related Works
The first post-quantum one-time linkable ring signature was proposed by Torres et al. [] in 2018. Le et al. [] suggested IBLRS methods that rely on lattice-based SIS and ring-SIS. Tang et al. [] proposed a new lattice-based IBLRS scheme in 2020, which reduced the signature size and computational complexity, making it more suitable for practical applications. Although lattice-based ring signature schemes offer more security and are particularly suitable for future quantum computing environments, they tend to have large signature sizes and high computational complexity. To further reduce the size of ring signatures, much effort has been made in recent years. Most schemes for reducing ring signature size use two methods: accumulators [] and zero-knowledge proofs []. However, accumulators require a trusted setup. In 2021, Yuen et al. [] introduced a novel type of ring signature known as the “dual-ring signature”. This signature scheme builds upon the type-T standard signature algorithm and includes a lattice-based variant of the dual-ring signature. This new structure of ring signatures significantly reduces the signature size and speeds up the signing and verification processes compared to ordinary ring signatures. In 2024, Feng et al. [] proposed a dual-ring signature scheme based on SM2, initially converting SM2 digital signatures into Type-T, and then integrating dual-ring with a variant of SM2 digital signatures.
2. Preliminaries
2.1. Notations
Table 1 lists the related symbols. When an integer N exists for each positive integer c and, for all , , a function is said to be negligible (negl). If all probabilistic polynomial-time (PPT) algorithms cannot solve a problem with a non-negligible probability, then the problem is considered hard.

Table 1.
Symbol description.
2.2. Lattices
Definition 1.
Let be n vectors in m-dimensional space, which are linearly independent. All integer linear combinations of the vectors in constitute lattice ; that is, . We call a basis of lattice .
Definition 2
(M- assumption []). Let q, n, m be integers and β be a positive real number. Given , the Module Small Integer Solution (M-SIS) assumption aims to find a vector such that and .
The M-SIS (Module-SIS) hard problem is a modular version of the SIS (Short Integer Solution) hard problem, which transforms in the SIS problem to . Due to the increase in the modular structure, the M-SIS problem is more computationally complex, and finding short vectors is more challenging than in the SIS problem.
2.3. Important Algorithms
In 2008, Gentry et al. [] proposed the GPV lattice screening algorithm, which is used by most lattice-based signature schemes and mainly consists of the following three parts:
TrapGen(): Input the security parameter n; let , , and . The algorithm TrapGen outputs a matrix and a set of bases on , and satisfies .
SampleDom(: Input the security parameter n and the Gaussian parameter . The algorithm SampleDom selects a random vector according to the distribution , and with high probability satisfies .
SamplePre(: Input the matrix ; is a trapdoor basis of the lattice (); the parameter ; for any vector , the algorithm SamplePre() outputs a random non-zero vector , where and .
2.4. Rejection Sampling Technique
In lattice-based digital signatures, the signer wants to output a vector z that is independent of the private key s, ensuring that z cannot be used to gain any information about the signer’s secret. In the protocol, the signer computes , where s can be the private key or randomness used for the signer’s secret, is a challenge polynomial, and r is a “masking” vector. To eliminate the dependence of z on s, rejection sampling can be applied [].
As Theorem 1 shows, for any , , = = .
Theorem 1.
Given a probability distribution , determine and . The statistical distance between the input distributions of the next two algorithms is then less than , where M = is a constant:
- Distribution 1: Output with probability min; sample and ;
- Distribution 2: With a probability of , the sample and yields .
Distribution 1 has a minimum probability of producing an output of .
2.5. The Forking Lemma
In 2000, Pointcheval and Stern proposed the forking lemma []. Suppose is a digital signature scheme with security parameter n. A is a PPT algorithm whose input only consists of public data. Let Q be the maximum number of queries that A can make to the random oracle. If A generates a valid signature with probability within time T, then there exists an algorithm B that controls algorithm A and can generate two valid signatures and within expected time , where .
2.6. Dual-Ring Structure
To further shorten the ring signature size of the AOS structure [], especially the number of responses, the dual-ring structure, an efficient approach for constructing ring signatures, is suggested by []. The dual-ring signature splits the AOS single-ring signature into two separate rings: the commitments ring and the challenges ring, which are connected using a hash function. A dual-ring signature consists of N challenges and one response. We further provide a high-level description of the dual-ring structure:
In Figure 1, represents the function used by the signer. ⊙ and ⊗ are two commutative group operations. V is the verification function. The verification function is split into two parts, and , and their relationship is . Z is the response function.
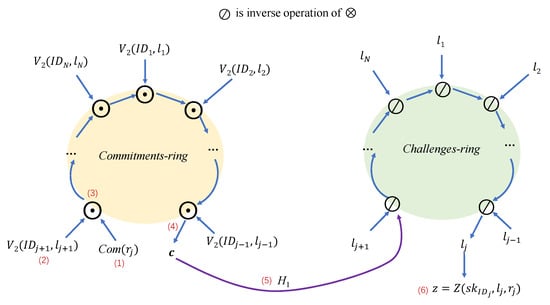
Figure 1.
Structure of dual-ring structure.
- (1)
- The signatory selects a random number and generates a commitment through the Com function.
- (2)
- Randomly select challenges , where .
- (3)
- Use the group operation ⊙ and functions and to form a commitment ring.
- (4)
- Calculate the commitment c.
- (5)
- Link the commitment ring and the challenge ring through the hash function .
- (6)
- Obtain through the hash value of and by group operation ⊘. Calculate the response z through the Z function.
3. Syntax and Security Model
As shown in the Figure 2, an identity-based linkable ring signature (IBLRS) scheme includes five PPT algorithms []:
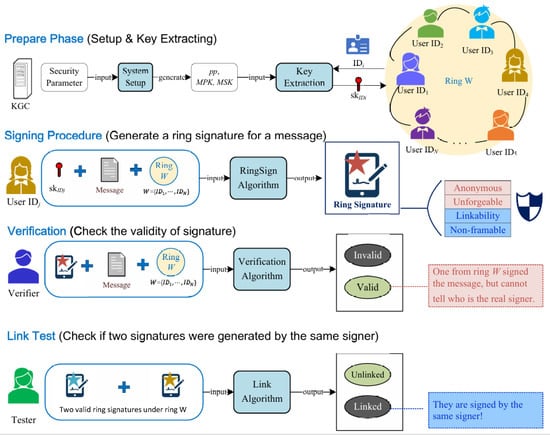
Figure 2.
Definition of identity-based linkable ring signature.
- (1)
- Setup(): The Key Generation Center (KGC) generates the public parameter and the system master private key .
- (2)
- KeyExt(): Performed by the , this process takes the user’s identity , , and as input, and produces the private key corresponding to the user’s identity .
- (3)
- Sign(): Operated by the signer. Taking , a set of ring members W = , message , and the private key corresponding to the signer’s identity as input, this algorithm outputs a linkable ring signature on under W. The signature includes a linkable tag .
- (4)
- Verify(): Carried out by the verifier, this process takes , the set of user identities W = forming the ring, , and as inputs. If the verification is successful, it outputs “1”; otherwise, it outputs “0”.
- (5)
- Link(): Taking as input two tuples, () and (), this algorithm returns “linkable” or “unlinkable”.
We illustrate the security model of IBLRS through a series of interactions between attacker and challenger . In the context of the random oracle model (ROM), attacker is granted access to the RO and can issue two distinct types of queries:
- (1)
- Key extract query: selects identity and sends it to for a private key query. generate corresponding to , and returns the result to .
- (2)
- Signing query: selects a ring signature , a user identity , and to send to for querying. returns the generated signature to .
Definition 3
(Correctness). For any PPT attacker , an IBLRS scheme is correct if
Definition 4
(Anonymity). The anonymity of IBLRS is defined by below:
- (1)
- System Setup: Challenger inputs the security parameter λ, and the KGC generates and . sends to . is allowed a polynomially bounded number of queries, each query potentially dependent on previous query results.
- (2)
- Query Stage: adaptively carries out various queries with polynomial time bounds.
- (3)
- Challenge Phase: submits the message , the ring , and randomly selects the user identity as . Note that A has not queried the private key associated to . returns a signature , then sends it to .
- (4)
- Guessing Phase: outputs his or her guess .
The advantage of in is defined as
For any PPT attacker , an IBLRS scheme is anonymous if the advantage in is negligible.
Definition 5
(Unforgeability against insider corruption). We define the unforgeability of IBLRS through the below:
- (1)
- System Setup: Challenger inputs the security parameter λ, and the KGC generates and . sends to . is allowed a polynomially bounded number of queries, each query potentially dependent on previous query results.
- (2)
- Query Stage: can access a polynomial-time oracle, and perform the aforementioned private key inquiries and signature inquiries.
- (3)
- Forgery Stage: provides (); if it satisfies the following conditions, then the attacker wins the unforgeability :
- =;
- has not queried the private key of any user in the ring ;
- has not initiated any signature queries for ().
The advantage of winning the unforgeability game is defined as follows:
For any PPT attacker , the advantage of winning is negligible.
Definition 6
(Linkability). We define the linkability of IBLRS through the below:
- (1)
- System Setup: Challenger inputs the security parameter λ, and the KGC generates and . sends to . is allowed a polynomially bounded number of queries, each query potentially dependent on previous query results.
- (2)
- Query Stage: can access a polynomial-time oracle, and perform the aforementioned private key inquiries and signature inquiries.
- (3)
- Forgery Stage: outputs two signatures and , with linking tag . If they satisfy the following conditions, then attacker wins the linkability :
- , ;
- ;
- Less than two inquiries for the private key are made by attacker (attacker can have at most one user’s private key).
The advantage of attacker winning the linkability game is defined as follows:
For any PPT attacker , the advantage of winning the following is negligible.
Definition 7
(Nonslanderability). The nonslanderability of IBLRS is defined by below:
- (1)
- System Setup: Challenger inputs the security parameter λ, and the KGC generates and . sends to . is allowed a polynomially bounded number of queries, each query potentially dependent on previous query results.
- (2)
- Query Stage I: can access a polynomial-time oracle, and perform the aforementioned private key inquiries and signature inquiries.
- (3)
- Challenge: Attacker sends a tuple to the challenger , with the not having undergone a private key query. The challenger returns a signature .
- (4)
- Query Stage II: Similar to Query Stage I, but private key queries for and signature queries for are not allowed.
- (5)
- Slander: On μ and τ, attacker produces a new signature . If the following scenarios are met, then attacker wins the nonslanderability :
- ;
- did not result from any queries made in Query Stage I or Query Stage II;
- .
The advantage of winning the nonslanderability game is defined as follows:
For any PPT attacker , the advantage of winning is negligible.
4. The Proposed Scheme
In this section, we first present the system model of privacy-preserving transactions on the blockchain, and then describe the construction of an identity-based linkable dual ring signature (IB-LDRS) in detail.
4.1. System Model
As Figure 3 shows, the signer with starts the transaction and creates a ring using his or her identity and the identity information of other users in the blockchain to protect anonymity in blockchain transactions. The signer signs the transaction data using their private key. Note that it is impossible for outsiders to identify which signer created the signature since the identities of the entire ring are used in the signature generation process. The ring signature and associated transaction details are broadcast along with the transaction to the blockchain network. The ring signature is validated by other nodes on the blockchain network, confirming that a member of the ring actually created it. Thus, the ring signature protects the identity privacy of its real signer.
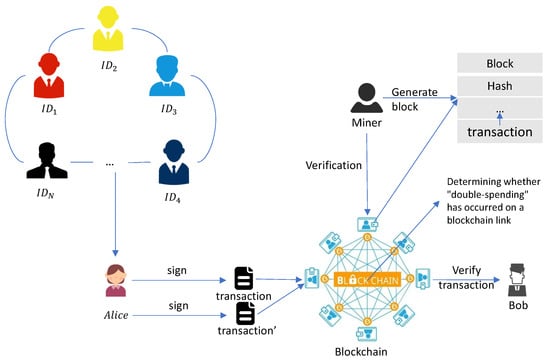
Figure 3.
System model of IB-LDRS in blockchain transactions.
4.2. Parameters and Ranges
Before giving the algorithms, we first introduce the related parameters as follows: is defined as the modulus of odd numbers, ; are real numbers such that . is a ring of dimension d. The set D is the collection of polynomials in . We define the total ring as . Define the following challenge space:
Observe that . When , we have . During the computation, the polynomial coefficients need to be modulo 3. After performing the modulo operation, the polynomial coefficients will be within the range .
4.3. Construction
The proposed construction of the IB-LDRS scheme from lattices is described as follows:
IB-LDRS.Setup: The blockchain system executes Algorithm 1; this algorithm takes the security parameter as input, and outputs the public parameter . and act as random oracles, and functions as a collision-resistant one-way function.
| Algorithm 1: IB-LDRS.Setup |
Input: . Output: .
|
IB-LDRS.KeyExt: The KGC runs Algorithm 2 to generate the user’s public and private keys; this algorithm takes the public parameters , identity , and master private key as inputs; compute using hash function and sample using the function. It outputs public key and private key.
| Algorithm 2: IB-LDRS.KeyExt |
Input: Output: .
|
IB-LDRS.Sign: The transaction initiator, Alice, runs the signature Algorithm 3 to initiate a transaction; the following algorithm generates the ring signature of message based on the dual-ring architecture, given input , , W. The signer’s index is , .
| Algorithm 3: IB-LDRS.Sign |
Input: Output: .
|
IB-LDRS.Verify: The transaction receiver, Bob, runs the verification Algorithm 4 to verify the transaction; given , W, , and , verify it by the following steps.
| Algorithm 4: IB-LDRS.Verify |
Input: Output: 0 or 1.
|
IB-LDRS.Link: The blockchain link runs the linking Algorithm 4 to conduct “double-spending” detection. Once it receives two different and valid signatures to be tested, this algorithm checks whether . If it does, it returns “linkable”; otherwise, it returns “unlinkable”. Note that this algorithm tests valid signatures only, because it can invoke Algorithm 4 to check the validity and reject the invalid signatures. If both of the signatures are accepted, go to Algorithm 5 to check whether they are generated by the same signer.
| Algorithm 5: IB-LDRS.Link |
Input: Output: linkable or unlinkable.
|
5. Security Analysis
Theorem 2
(Correctness). A linkable ring signature generated by a legitimate signature system can pass the verification of the algorithm, thereby satisfying the correctness verification.
Since it is impossible to determine whether it has been tampered with during transmission, suppose is the signature received by the IB-LDRS.Verify Algorithm 4, , and it will be accepted by the IB-LDRS.Verify Algorithm 4 as follows.
Correctness of :
Correctness of :
Therefore, holds, and the proposed scheme meets the correctness requirement.
Theorem 3
(Unforgeability). Under the assumption of , for any PPT attacker , the scheme is unforgeable under chosen message attacks and insider corruption attacks in the random oracle model, where .
Proof.
Let us assume that there is an attacker with a non-negligible advantage that can forge signatures in polynomial time. Then, there is a challenger that has a non-negligible probability of solving the M-SIS hard problem. Assume has an instance to solve, where . Finding a short vector e such that that is the aim of . first transforms into the form , and then embeds it in the reduction algorithm. The hash functions and are random oracles. establishes four lists, , and , which are used to store -oracle, -oracle, signature queries, and corruption queries, respectively. The following describes how and interact:
- IB-LDRS.Setup Stage: Generate system parameter . Send the system parameters and the ring W to .
- Query phase: During this phase, the attacker interacts with by making oracle queries to learn information about the scheme. The challenge responds to the queries as follows.
- (1)
- oracle query: When submits user to , for , checks whether exists in : if so, it returns to ; if not, randomly selects , and then computes , assigns to , and returns it to . records it in list . If , setsfor randomly chosen , and returns to ; records it in list .
- (2)
- oracle query: Upon receiving an oracle query with message , ring , and intermediate parameters R and T to from , first searches in list ; if found, it returns the corresponding hash value to ; if not, it randomly choose a vector , and returns l to . Finally, records in list . This query can be made at most times.
- (3)
- Registration query: When sends a new identity for registration, first randomly chooses and computes as for the oracle, and then returns the private key to . Finally, adds to list and tuple to list .
- (4)
- Signing oracle query: When submits an inquiry for a ring signature on identity of message under ring such that , if , chooses random with , and random , and computes and as in the verification algorithm. calculates through , and stores it in , and then returns the signature , where . If , first checks if . If not, it returns ⊥ to . If it does meet the condition, directly checks tuple in list and returns the signature to if it does exist. Otherwise, generates a new signature as in the following steps. If it does exist, researches in list . If it exists, generates a ring signature of under with by the steps in the signing algorithm. If does not exist in list , invokes the oracle to achieve the private key and then generates ring signature as before. Note that tuple should have been added to list by the query to during the generation of the ring signature, where is an intermediate value in signing procedures. Finally, returns the signature of message under ring , and then stores tuple in list .
- (5)
- Corruption query: If selects a user identity to corrupt, first checks whether exists in list . If it does, searches in list and returns the corresponding private key to ; if it does not, randomly choose and generates as for the oracle, and then returns the private key to . Finally, adds to list , and tuple to list . If selects a user identity to corrupt, fails and aborts.
- Forgery Stage: After polynomial queries to the oracles, submits a signature of message under ring as his or her forgery to challenger . The signature is considered to be a successful forgery if it satisfies the following conditions:
- (1)
- Attacker never registers or corrupts any user , that is, ;
- (2)
- Attacker has not queried the signature of under , that is, ;
- (3)
- The forgery can pass the verification algorithm, that is,IB-LDRS.Verify =“1”.
Analysis: Assume is a successful forgery with probability ; then, the verification equation
holds from the correctness property. There must be one that comes from the response of oracle , so can be found in list . From the general forking lemma [], can obtain another valid signature where with same randomness from of message under by rewinding the random oracle , with a probability at least . So, for , , ,. The verification equation
holds by the correctness property. Subtracting Equation (2) from Equation (3) yields the following equation:
Then, we multiply Equation (1) by to achieve
By subtracting Equation (7) from Equation (5), we obtain a short such that
is a non-zero vector as its last coordinate is which is not zero. Therefore, can output a valid solution to , where . Therefore, we can conclude that our signature algorithm is strongly unforgeable under the message chosen and the insider corruption attack. This completes the proof. □
Theorem 4
(Anonymity). The proposed IB-LDRS scheme satisfies unconditional anonymity.
Proof.
The challenger and the PPT attacker interact in a game to prove the scheme’s anonymity. The attacker provides with a message, two identities, and a ring, after which returns a signature. If can guess the identity of the signer with a non-negligible probability, the scheme’s anonymity is compromised.
- IB-LDRS.Setup Stage: Determine the ring . Challenger generates and W for each user. Then, sends to .
- Query Stage: Conduct various queries adaptively on with polynomial time limits.
- Challenge Stage: submits a message , ring , and user identity to . randomly selects , computes for , and performs a ring signature , then sends it to .
- Guess Stage: outputs the guess .
- Forgery Stage: To demonstrate that the probability of winning the game is negligible, we only need to prove that the signature generated by and the signature generated by are statistically indistinguishable.
When signing , results in , and results in , , according to Theorem 1, and the Gaussian distribution are statistically indistinguishable; thus, the signature is statistically indistinguishable from . Similarly, the signature is also statistically indistinguishable from . Therefore, and follow the same discrete Gaussian distribution, making them statistically indistinguishable. Consequently, the probability that can determine whether was generated by or is negligible. □
Theorem 5
(Linkability). For any polynomial-time attacker , the proposed IB-LDRS scheme is linkable in the ROM.
Proof.
The linkability of the scheme is proved by an interactive security game between challenger and a PPT adversary .
- IB-LDRS.Setup Stage: Challenger inputs the security parameter . Generate the public parameter . Send the system parameter to the attacker .
- Inquiry Stage: Same as in the scheme’s unforgeability proof.
- Challenge Stage I: The attacker provides two signatures, denoted and .
Analysis. Attacker uses a single private key to generate two ring signatures and for the same message with a non-negligible probability. These signatures can pass the verification algorithm and satisfy .
We assume that , , and are generated by the signer’s own private key, while is forged. Simplifying the operations Equations (10) and (11) yields the following:
From the above equations, through simple derivation, we can obtain , which leads to . This contradicts the assumption; thus, the signatures of the same signer on the same message can be linked.
In the event that the signer did not utilize their private key in , then the signature is legitimately faked. According to the unforgeability of Theorem 3, challenger can generate using the forking lemma based on forger ’s ability. Subtracting from yields ; thus, we obtain a solution to the M-SIS hard problem. Therefore, we can conclude that legitimate signatures generated for the same message by the same signer are linkable. This completes the proof. □
Theorem 6
(Nonslanderability). The IB-LDRS is nonslanderable in the random oracle model, if the M-SIS problem is hard.
Proof.
Challenger and polynomial-time attacker interact in a game to prove the nonslanderability of the scheme. We will explain that the nonslanderability relies on the scheme’s unforgeability.
In the security model of nonslanderability, attacker sends a tuple to challenger , with the not having undergone a private key query. Challenger obtains the private key for the by running IB-LDRS.KeyExt. Then, challenger runs IB-LDRS.Sign to obtain the signature . On the same message and tag , attacker produces a new signature .
This implies that, for any PPT attacker , if he or she knows , he or she can produce a signature with the linkability tag without knowing the private key . According to the unforgeability of Theorem 3, challenger can generate using the forking lemma based on forger ’s ability. Subtracting from yields ; thus, we obtain a solution to the M-SIS hard problem. Consequently, we can state that legitimate signatures generated by the same signer for the same message ought to be connected. □
6. Performance Analysis
In this section, we will compare our scheme with other ring signature schemes, including functionality, computational overhead, and communication overhead.
6.1. Functionality Comparison
We compare the scheme’s functionality with those of other schemes in the section below. Table 2 compares five features, including post-quantum resistant (PQR), linkability (Link), identity-based (ID-based), dual-ring (DR), and hard problem assumptions (Assumption). Unlike the Yuen et al. [] lattice-based dual-ring signature system from 2019, our scheme improves linkability and resolves the blockchain’s “double-spending” problem. The SM2-based dual-ring scheme proposed by Feng et al. [] in 2024 is similar in structure to our scheme, but it does not possess quantum-resistant properties. Tang et al. presented [], a scheme based on the NTRU lattice that satisfies the properties of PQR, Link, and ID-based. The two schemes [,] only satisfy the PQR and ID-based properties. The schemes in [,,] satisfy all properties except DR. Our scheme satisfies all the functionalities aforementioned.

Table 2.
Comparison of functionality.
6.2. Comparison of Costs
We selected three schemes with similar functionalities to our proposed scheme [,,] for a comparison of computational and communication overhead.
The time comparisons for generation, individual user generation, and generation of the three schemes are shown in Table 3. Here, represents the security parameter, N denotes the number of ring members, and represents the average time for the TrapGen algorithm. Because [] is not identity-based, there is no such time overhead. For this part, it is represented by “/”. represents the average time for the SamplePre algorithm. represents the average time for polynomial modular multiplication. represents the average time for scalar multiplication. Table 3 presents a comparative analysis of the time overhead, individual user generation time, and signature generation time for the four schemes. We ignored less time-consuming procedures like hash functions and matrix additions in favor of concentrating mostly on computationally demanding operations.

Table 3.
Comparison of time costs.
Table 4 compares the communication overhead of three schemes in terms of private key size and signature size. Our private key is generated using the SamplePre algorithm and is an m-dimensional vector multiplied by the polynomial dimension d. The private key in [] is generated using BasisDel and SamplePre, resulting in an m-dimensional vector. The scheme in [] uses the SampleDom algorithm to generate the private key, with the size being the same as in []. In our scheme, in the signature is a d-dimensional vector with values in the range {−1, 0, 1}, so its size is . The vectors and are m-dimensional and n-dimensional vectors, respectively, and, since the scheme is based on the M-SIS hard problem, they need to be multiplied by the polynomial dimension d. Although this makes our scheme appear larger in size compared to other schemes, the values of m and n in our scheme are very small, so the signature size is smaller compared to other schemes.

Table 4.
Comparison of communication costs.
We set the parameters and . In our signature scheme, , , and . Here are the estimated signature sizes for this scheme with different numbers of ring members based on the parameters in [].
In Table 5, we provide the sizes of the proposed ring signature with the increase in ring size N, as well as the sizes of responses . “Sig Size” denotes the sizes of signature, while the “Size of ” shows the sizes of the hash values in the ring signatures. Figure 4 shows the increasing trend of communication costs with the ring scale. We can observe that, although the signature size increases linearly with the number of ring members N, the size of in the signature does not change significantly. When the number of ring members , the signature size does not change much, and it is no more than 13 KB even when . The size is mainly affected by the response . Therefore, the signature size is mainly related to the number of values. Since the values are very small, the signature size does not change much as the number of ring members increases. When N reaches 128, the signature size is just under 15 KB. When N grows to 2048 and the parameters n and m are chosen to be larger, the signature size is 62.72 KB, which is still acceptable for most application scenarios.

Table 5.
Communication costs (KB).
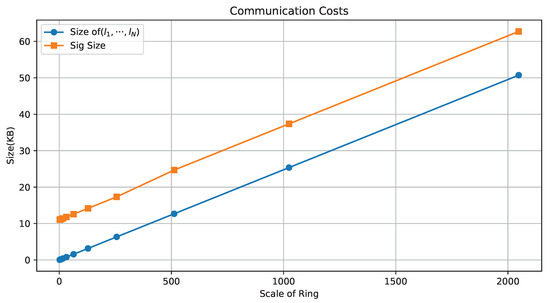
Figure 4.
Communication costs with numbers of ring members.
7. Identity-Based Threshold Linkable Dual-Ring Signature
To further enhance threshold functionality, we adapt the threshold technique from [] into our scheme, resulting in an identity-based threshold linkable dual-ring signature scheme (IB-TLDRS). Since most steps of this structure are similar to the previous scheme, we focus on the different steps.
- IB-TLDRS.Setup: Same as the setup process in Algorithm 1, except setting a threshold t.
- IB-TLDRS.KeyExt: Same as Algorithm 2.
- IB-TLDRS.Sign: Same as Algorithm 3.
- IB-TLDRS.Combine: A new algorithm required to be added in. The signer sends the generated valid signature to the IB-TLDRS.Combine algorithm, which then combines it into a set and sends it to the verification algorithm IB-TLDRS.Verify.
- IB-TLDRS.Link: Same as Algorithm 5.
- IB-TLDRS.Verify: Input ; after parsing and verifying the signature, the verifier retrieves the successfully verified signature tag in . If it is not in , the tag is added. Finally, if , the output is 1; otherwise, the output is 0.
Specifications. Through the above method, we can obtain a new scheme with threshold functionality. For the new scheme, we only need a third party to perform the IB-LDRS.Combine algorithm after the signing procedure is completed. In the Verify algorithm, it is necessary to first verify the correctness of the signature before checking whether the threshold requirement is met.
Security Analysis. Adding threshold functionality does not affect the security. The threshold functionality mainly relies on the tags in the signature. We have already proven the linkability and nonslanderability, which ensure the security of the tags. This also demonstrates that the scheme can still ensure its security after incorporating the threshold functionality.
8. Conclusions and Future Work
Based on the lattice-based M-SIS assumption, this work constructs an efficient identity-based linkable dual-ring signature scheme, with its threshold extension additionally. The proposed scheme leverages the benefits of dual-ring signatures, which can reduce signature size effectively, especially when the number of ring members is not very large compared to other logarithmic (linkable) ring signatures. Moreover, our scheme, based on identity, simplifies key management processes, reduces computational and communication costs, and offers enhanced security in linkability compared to existing linkable ring signature schemes. Our ring signature is proved to be anonymous, unforgeable, linkable, and nonslanderable in the random oracle model. The research data further show that this work achieves a smaller signature size compared to prior schemes, effectively decreasing storage costs, even though our signature size scales linearly with the number of ring members. Finally, a threshold extension is given as an additional scheme with specifications and security analysis. Although the signature size in this scheme is very small, it increases linearly with the increase in the number of ring members. Therefore, we consider research on the construction of the logarithmic ring signature from lattices as future work.
Author Contributions
Conceptualization, W.G. and H.Y.; methodology, W.G. and H.Y.; software, B.Q.; validation, B.Q., X.D. and Z.Z.; formal analysis, W.G.; investigation, J.Z.; resources, W.G. and B.Q.; writing—original draft preparation, W.G., H.Y. and J.Z.; writing—review and editing, W.G. and H.Y.; visualization, X.D.; supervision, Z.Z.; project administration, B.Q. All authors have read and agreed to the published version of the manuscript.
Funding
This work is supported by the National Natural Science Foundation of China under Grant Nos. 62002288, 62372370, and 62102299, the Key Research and Development Program of Shaanxi (No. 2023-YBGY-015), the Henan Key Laboratory of Network Cryptography Technology under No. LNCT2022-A05, and the Youth Innovation Team of Shaanxi Universities (No. 23JP160).
Data Availability Statement
The original contributions presented in the study are included in the article, further inquiries can be directed to the corresponding author.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Rivest, R.L.; Shamir, A.; Tauman, Y. How to Leak a Secret: Theory and Applications of Ring Signatures. In Essays in Memory of Shimon Even; Springer: Berlin/Heidelberg, Germany, 2001. [Google Scholar]
- Li, X.; Mei, Y.; Gong, J.; Xiang, F.; Sun, Z. A Blockchain Privacy Protection Scheme Based on Ring Signature. IEEE Access 2020, 8, 76765–76772. [Google Scholar] [CrossRef]
- Wang, L.; Peng, C.; Tan, W. Secure Ring Signature Scheme for Privacy-Preserving Blockchain. Entropy 2023, 25, 1334. [Google Scholar] [CrossRef] [PubMed]
- van Saberhagen, N. CryptoNote v 2.0. 2013. Available online: https://api.semanticscholar.org/CorpusID:2711472 (accessed on 22 October 2024).
- Liu, J.K.; Wei, V.K.; Wong, D.S. Linkable Spontaneous Anonymous Group Signature for Ad Hoc Groups (Extended Abstract). In Information Security and Privacy, Proceedings of the 9th Australasian Conference, ACISP 2004, Sydney, Australia, 13–15 July 2004; Springer: Berlin/Heidelberg, Germany, 2004. [Google Scholar]
- Shamir, A. Identity-Based Cryptosystems and Signature Schemes. In Proceedings of the Annual International Cryptology Conference, Santa Barbara, CA, USA, 19–22 August 1984; Springer: Berlin/Heidelberg, Germany, 1984. [Google Scholar]
- Chow, S.S.; Yiu, S.M.; Hui, L.C. Efficient Identity Based Ring Signature. In Applied Cryptography and Network Security, Proceedings of the Third International Conference, ACNS 2005, New York, NY, USA, 7–10 June 2005; Springer: Berlin/Heidelberg, Germany, 2005. [Google Scholar]
- Boneh, D.; Franklin, M. Identity-Based Encryption from the Weil Pairing. In Proceedings of the Annual International Cryptology Conference, Santa Barbara, CA, USA, 19–23 August 2001; Springer: Berlin/Heidelberg, Germany, 2001. [Google Scholar]
- Zhang, J. An Efficient Identity-Based Ring Signature Scheme and Its Extension. In Communication Systems and Applications; Springer: Berlin/Heidelberg, Germany, 2007. [Google Scholar]
- Deng, L.; Jiang, Y.; Ning, B. Identity-Based Linkable Ring Signature Scheme. IEEE Access 2019, 7, 153969–153976. [Google Scholar] [CrossRef]
- Nassurdine, M.; Zhang, H.; Zhang, F. Identity Based Linkable Ring Signature with Logarithmic Size. In Information Security and Cryptology, Proceedings of the 17th International Conference, Inscrypt 2021, Virtual Event, 12–14 August 2021; Springer: Berlin/Heidelberg, Germany, 2021. [Google Scholar]
- Odoom, J.; Huang, X.; Wang, L. Stateless forward-secure key-insulated linkable ring signature scheme in ID-based setting. J. Syst. Archit. 2022, 129, 102600. [Google Scholar] [CrossRef]
- Wang, S.; Zheng, S.; Zhan, T. Identity-Based Linkable and Convertible Ring Signature: Identity-Based Linkable and Convertible Ring Signature. J. Electron. Inf. Technol. 2011, 30, 995–998. [Google Scholar] [CrossRef]
- Singh, P.; Hasabnis, A.R.; Rajpoot, S.; Singh, P. Quantum Attacks on Public Cryptosystems. In Proceedings of the 2023 6th International Conference on Contemporary Computing and Informatics (IC3I), Gautam Buddha Nagar, India, 14–16 September 2023; pp. 36–41. [Google Scholar] [CrossRef]
- Zhang, Z.; Wu, W.; Sui, H.; Wang, B. Quantum Attacks on Type-3 Generalized Feistel Scheme and Unbalanced Feistel Scheme with Expanding Functions. Chin. J. Electron. 2023, 32, 209–216. [Google Scholar] [CrossRef]
- Bernstein, D.J. Introduction to Post-Quantum Cryptography. 2009. Available online: https://api.semanticscholar.org/CorpusID:61401925 (accessed on 22 October 2024).
- NIST. NIST Selects Four Post-Quantum Cryptography Algorithms for Standardization [Press Release]. Available online: https://csrc.nist.gov/Projects/post-quantum-cryptography (accessed on 22 October 2024).
- Alberto Torres, W.A.; Steinfeld, R.; Sakzad, A.; Liu, J.K.; Kuchta, V.; Bhattacharjee, N.; Au, M.H.; Cheng, J. Post-Quantum One-Time Linkable Ring Signature and Application to Ring Confidential Transactions in Blockchain (Lattice RingCT v1.0). In Information Security and Privacy, Proceedings of the 23rd Australasian Conference, ACISP 2018, Wollongong, NSW, Australia, 11–13 July 2018; Springer International Publishing: Cham, Switzerland, 2018. [Google Scholar]
- Le, H.Q.; Bay, V.; Dung, H.D.; Willy, S.; Ngoc-Thao, L.; Kazuhide, F.; Kiyomoto, S. Identity-Based Linkable Ring Signatures from Lattices. IEEE Access 2021, 9, 84739–84755. [Google Scholar] [CrossRef]
- Tang, Y.; Xia, F.; Ye, Q.; Wang, M.; Mu, R.; Zhang, X. Identity-Based Linkable Ring Signature on Lattice. J. Cryptologic Res. 2021, 8, 232–247. [Google Scholar] [CrossRef]
- Dodis, Y.; Kiayias, A.; Nicolosi, A.; Shoup, V. Anonymous Identification in Ad Hoc Groups. In Advances in Cryptology-EUROCRYPT 2004, Proceedings of the International Conference on the Theory and Applications of Cryptographic Techniques, Interlaken, Switzerland, 2–6 May 2004; Springer: Berlin/Heidelberg, Germany, 2004. [Google Scholar]
- Groth, J.; Kohlweiss, M. One-Out-of-Many Proofs: Or How to Leak a Secret and Spend a Coin. In Proceedings of the 34th Annual International Conference on the Theory and Applications of Cryptographic Techniques, Sofia, Bulgaria, 26–30 April 2015; Springer: Berlin/Heidelberg, Germany, 2015. [Google Scholar]
- Yuen, T.H.; Esgin, M.F.; Liu, J.K.; Au, M.H.; Ding, Z. DualRing: Generic Construction of Ring Signatures with Efficient Instantiations. In Proceedings of the Annual International Cryptology Conference, Virtual Event, 16–20 August 2021; Springer International Publishing: Cham, Switzerland, 2021. [Google Scholar]
- Feng, M.; Lin, C.; Wu, W.; He, D. SM2-DualRing: Efficient SM2-based ring signature schemes with logarithmic size. Comput. Stand. Interfaces 2024, 87, 103763. [Google Scholar] [CrossRef]
- Koo, Z.; No, J.S.; Kim, Y.S. Reduction From Module-SIS to Ring-SIS Under Norm Constraint of Ring-SIS. IEEE Access 2020, 8, 140998–141006. [Google Scholar] [CrossRef]
- Jeong, I.R.; Kwon, J.O.; Lee, D.H. Analysis of Revocable-iff-Linked Ring Signature Scheme. IEICE Trans. Fundam. Electron. Commun. Comput. Sci. 2009, 92, 322–325. [Google Scholar] [CrossRef]
- Lyubashevsky, V. Lattice Signatures Without Trapdoors. In Proceedings of the Annual International Conference on the Theory and Applications of Cryptographic Techniques, Cambridge, UK, 15–19 April 2012; Springer: Berlin/Heidelberg, Germany, 2012. [Google Scholar]
- Pointcheval, D.; Stern, J. Security Arguments for Digital Signatures and Blind Signatures. J. Cryptol. 2015, 13, 361–396. [Google Scholar] [CrossRef]
- Abe, M.; Ohkubo, M.; Suzuki, K. 1-out-of-n Signatures from a Variety of Keys. In IEICE Transactions on Fundamentals of Electronics Communications and Computer Sciences; Springer: Berlin/Heidelberg, Germany, 2002. [Google Scholar]
- Wang, J. Ring Signature and Identity-Based Ring Signature from Lattice Basis Delegation. IACR Cryptol. ePrint Arch. 2010, 2010, 378. [Google Scholar]
- Hu, M.; Zhang, W.; Liu, Z. An Improved Lattice-Based Ring Signature with Unclaimable Anonymity in the Standard Model. Comput. J. 2022, 66, 2542–2553. [Google Scholar] [CrossRef]
- Cao, C.; You, L.; Hu, G. A Novel Linkable Ring Signature on Ideal Lattices. Entropy 2023, 25, 237. [Google Scholar] [CrossRef] [PubMed]
- Baum, C.; Lin, H.; Oechsner, S. Towards Practical Lattice-Based One-Time Linkable Ring Signatures. In Proceedings of the International Conference on Information and Communications Security, Lille, France, 29–31 October 2018; Springer International Publishing: Cham, Switzerland, 2018. [Google Scholar]
- Aranha, D.F.; Hall-Andersen, M.; Nitulescu, A.; Pagnin, E.; Yakoubov, S. Count Me In! Extendability for Threshold Ring Signatures. In Proceedings of the 25th IACR International Conference on Practice and Theory of Public-Key Cryptography, Virtual Event, 8–11 March 2022. [Google Scholar]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).