Abstract
Intelligent precision agriculture incorporates a number of Internet of Things (IoT) devices and drones to supervise agricultural activities and surroundings. The collected data are then forwarded to processing centers to facilitate crucial decisions. This can potentially help optimize the usage of agricultural resources and thwart disasters, enhancing productivity and profitability. To facilitate monitoring and decision, the smart devices in precision agriculture must exchange massive amounts of data across the open wireless communication channels. This inadvertently introduces a number of vulnerabilities, exposing the collected data to numerous security and privacy threats. To address these issues, massive security solutions have been introduced to secure the communication process in precision agriculture. However, most of the current security solutions either fail to offer perfect protection or are inefficient. In this paper, a scheme deploying efficient cryptographic primitives such as hashing, exclusive OR and random number generators is presented. We utilize the Burrows–Abadi–Needham (BAN) logic to demonstrate the verifiable security of the negotiated session keys. In addition, we execute an extensive semantic analysis which reveals the robustness of our scheme against a myriad of threats. Moreover, comparative performance evaluations demonstrate its computation overheads and energy consumption efficiency.
1. Introduction
Precision agriculture (PA) involves the integration of technologies such as drones, Wireless Sensor Networks (WSNs), IoT, artificial intelligence, geographic information systems (GISs), geospatial technologies (GTs) and machine learning to improve agricultural outputs. In PA, a large number of different sensors are used to remotely monitor farmlands. They also collect data regarding livestock health, environmental and crop growth. For instance, real-time data regarding soil conditions, quantity and quality of yield, crops, effects of deployed chemicals on crops, weather conditions and time of yield can be remotely collected and forwarded to servers for analysis and decision making [1]. This can help reduce threats to the production process and hence improve agricultural productivity. In addition, drones have been utilized for the application of pesticide spray and management of crops (such as disease discovery and management of weeds). In IoT-based smart agriculture, several technologies such as end-user applications, radio frequency identification (RFID), cloud computing and WSNs are utilized [2]. These technologies have been shown to positively impact the agricultural sector in terms of enhanced productivity, water conservation and increased income [3]. As explained in [4], crop water usage optimization is driven by the need for sustainable agricultural practices in the face of growing global food demands and climatic changes. According to [5], PA greatly helps in resource management in terms of agronomic (improving farm inputs effectiveness and hence yields), economic (enhancing competitiveness and productivity via efficient farming practices) and environment (reduction in ecological effects of agriculture via optimization of farm inputs usage). As explained in [6], smart agronomy has been implemented to increase productivity and offer disaster protection using limited resources. Similarly, faster decision making due to the incorporation of IoT and UAVs has been noted to result in costs savings and increased yields [7,8].
It is evident that the agricultural sector has benefited from rapid and intense transformations in access methods, data acquisition and sharing technologies. This has been reflected in production quality improvements, effective usage of natural resources and environmental sustainability. However, the usage of these integrated technologies render smart farming environments vulnerable to numerous cyber-security threats. For instance, the sensed data are exchanged over the open public internet and are hence susceptible to myriad threats such as eavesdropping and unauthorized access. These threats can result in the compromise of data availability, integrity and confidentiality. It is also possible for data belonging to an agricultural partner to be tampered with or altered, reducing its trustworthiness [9]. There is therefore a need for robust data verification schemes [10,11]. Due to extensive collaboration among different PA entities from diverse domains, there is a need for device authentication so as to foster secure communication [12,13]. This ensures that sensitive agricultural data are only shared with legitimate network entities. In addition, there is need to uphold trust by protecting both data in transit and in storage against any form of misuse. In this regard, we make the following contributions:
- We timestamp all the exchanged messages and validate them at the receiver end so as to thwart any packet replays.
- Frequently refreshed random numbers are incorporated in intermediary parameters to prevent against forgery and spoofing attacks.
- Elaborate formal security substantiation is executed to demonstrate the security verifiability of the negotiated session keys.
- Extensive semantic security analyses are executed, with results showing the resilience of our protocol against myriad precision agriculture threats.
- We carry out comparative performance evaluations to demonstrate the efficiency of our scheme. Specifically, this protocol is shown to consume the lowest energy and computation overheads at relatively low communication costs.
The remainder of this paper is organized as follows: Section 2 presents the related past research works, while Section 3 presents the detailed description of our protocol. Conversely, Section 4 and Section 5 discuss the security analyses and performance evaluation of the proposed scheme, respectively. Finally, Section 6 concludes this paper and offers some future research scopes.
1.1. Motivation
The requirement for data protection in precision agricultural networks and devices has seen the development of numerous security solutions. Most of these schemes are based on cryptographic operations such as public key infrastructure (PKI), blockchain technology, elliptic curve cryptography (ECC) and identity-based cryptography (IBC). However, schemes based on PKI, such as the Rivest–Shamir–Adleman (RSA) algorithm require third-party certificate authorities (CAs) for digital certificate assignment among devices. This comes with high costs for certificate management and storage. Although IBC-based crypto-systems solves this issue by using the identity of the devices as the public key and designating private key generator (PKG) for private keys distribution, these systems have key escrow challenges. For consistency, blockchain-based schemes require that each network entity maintain identical copies of the blockchains. This is detrimental to memory-limited agriculture Internet of Things (AIoT) devices. Similarly, ECC-based schemes require operations such as scalar multiplications which results in extensive overheads. In addition, most of the security solutions for PA security are based on centralized architectures, rendering them susceptible to single point of failure. Therefore, a truly efficient but robust security solution for resource-limited PA devices is required.
1.2. Research Goals
To provide perfect security in an environment characterized by frequent security threats, the following security goals should be pursued.
Message authentication: all the exchanged messages transmitted over the public channels should be verified at the receiver end.
Confidentiality: A session key need to be negotiated to encipher all the messages exchanged across the public communication channels. This presents attackers from eavesdropping on any secret parameters from the intercepted messages.
Availability: It should be cumbersome for the attackers to launch denial of service and de-synchronization attacks that can potentially lock legitimate users from accessing the required functionality and services.
Integrity: Based on any intercepted messages, attackers should be unable to modify or insert any bogus messages to the communication channel.
Perfect key secrecy: Adversaries should be unable to deploy the captured current session keys to work out session keys for the past as well as consequent communication sessions.
Anonymity: It should be cumbersome to reveal the real identities of any network entity based on the intercepted messages.
Robustness against threats: the authentication scheme needs to be resistant against typical intelligent precision agriculture threats such as denial of service (DoS), packet replay, man-in-the-middle (MitM), de-synchronization, privileged insider, impersonation and spoofing attacks.
1.3. Threat Model
The Canetti and Krawczyk model is one of the most popular threat models, and hence, we adopt it in our proposed scheme. In this model, adversary à is assumed to have the capabilities of eavesdropping on the wireless communication channel, intercepting all exchanged messages, modifying, or deleting these messages. In addition, the attacker can insert malicious messages into the communication channels to mislead the unsuspecting receivers. Moreover, à can steal smart farm devices and sensors, after which all stored security values can be extracted via power analysis. All low-entropy passwords can also be guessed by à in polynomial time, in addition to accessing all ephemeral keying parameters.
2. Related Works
In light of the many cyber threats in the smart agriculture ecosystem, several security schemes have been presented in the literature. For instance, blockchain technology allows the independent auditing and verification of transactions. This renders it ideal for enhancing trust during data access and recording in distributed network architectures [14]. Therefore, blockchain-based security solutions have been developed in [3,12,15,16,17,18,19,20,21,22]. These schemes help mitigate the single point of failure problems [23] in centralized architecture-based protocols developed in [6,24,25,26,27]. In addition, they boost both integrity and messages source verification. However, the storage and computation requirements for the blockchains are extensive IoT devices due to their limited resources [28]. Conversely, the security techniques developed in [29] utilize only one-way hash chains and hence can address the challenges in blockchain-based solutions. However, it does not offer untraceability, anonymity and dynamic node addition. In addition, it is susceptible to privileged insider, offline password guessing, impersonation and smart card loss attacks [3]. Similarly, the three factor user authentication protocol in [30] is not resilient session hijacking and eavesdropping threats.
Hinged on IBC, authentication protocols are presented in [31,32,33,34,35,36,37]. However, IBC-based schemes are susceptible to key escrow threats [38]. Similarly, the security solutions in [3,13,20,21] face key escrow threats. Although the scheme in [32] offers data confidentiality and mitigates several attacks, the leakage of the master key can result in the compromise of all the session keys [31]. Similarly, the protocol in [33] provides identity authentication, session key security and location privacy but incurs relatively high costs [31]. On the other hand, the scheme in [34] cannot withstand MitM, impersonation, DoS, privileged insider and offline password guessing attacks [3]. Similarly, the security technique presented in [35] cannot withstand privileged insider and DoS attacks [3], while the approach in [36] does not support secure communication and cannot withstand ephemeral secret leakage (ESL) attacks [39].
Some researchers have also utilized ECC to develop security schemes to secure systems and networks; for example, ECC-based authentication protocols have been developed in [40,41,42,43,44]. Although the technique in [40] protects against attacks such as impersonation and replay, it incurs high communication costs [31]. The schemes in [41,42] have relatively lower computation and communication overheads but fail to support anonymity and untraceability. In addition, the technique in [41] is exposed to ESL, smart card loss, DoS and privileged insider attacks [3]. For their part, the protocols in [42,43,44] cannot protect against ESL, offline guessing attacks, privileged insider and DoS attacks [3]. The Rabin cryptosystem-based scheme in [45] supports both untraceability and anonymity and hence can address the issues in [41,42]. However, it is not robust against privileged insider, smart card loss, ESL and offline guessing attacks [3]. Additionally, it has extensive communication overheads. In the same breath, the protocol in [46] exhibits extensive overheads due to bilinear pairing operations [47]. On the other hand, a scheme based on fuzzy extraction is presented in [48]. However, this scheme is not evaluated against attacks such as side-channeling, de-synchronization and session hijacking. A multi-factor user authentication protocol is developed in [49], while a multi-server scheme is developed in [50]. On the other hand, a homomorphic signcryption system is presented in [51], while an ECC-based scheme for authentication in smart agriculture monitoring systems is introduced in [52]. However, the scalar point multiplications in [51,52] and the fuzzy extraction operations in [49] render these schemes computationally extensive. Similarly, the required encryptions and decryptions in [50] increase its execution time.
From the discussions above, it is evident that the achievement of low-latency authentication with minimal communication overheads presents some challenges. In addition, the majority of the works in the literature are still vulnerable and hence expose the communication process to attacks. Our scheme is demonstrated to be not only efficient but also robust against conventional attacks inherent in precision agriculture environment.
3. The Proposed Scheme
The network model of our protocol comprises the user (Ui), controller node (CNj) and smart farm sensor node (SNk). The user in this case is the farmer performing some remote monitoring of his/her farm, while the sensor nodes are the actual devices that collect data from the field.
Conversely, the controller node performs the registration of all the users and sensors before the actual data collection process, as shown in Figure 1. The symbols utilized throughout this work are detailed in Table 1.
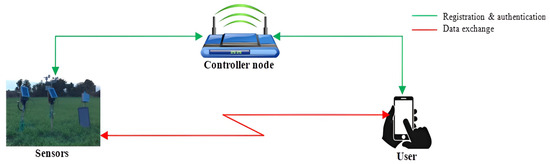
Figure 1.
Network model.

Table 1.
Symbols.
In terms of execution, our protocol executes in three major phases. The specific details of registration, authentication and parameter update phases are detailed below.
3.1. Registration
In this phase, all users and smart farm sensors are registered at the controller node prior to engaging in mutual verification, key setup and data exchange. The sub-sections that follow describe these procedures in finer detail. In addition, Algorithm 1 gives a summary of the registration process.
| Algorithm 1: Sensor node and user registration |
| Begin ** Sensor registration **
End |
3.1.1. Sensor Registration
Whenever a new sensor is introduced in the agricultural field, it must undergo registration prior to interacting with the rest of the network entities. To achieve this, the following three steps are carried out over the secure communication channels.
Step 1: The sensor node SNk selects SIDk as its unique identity, which is then forwarded to the controller node CNj, as depicted in Figure 2.
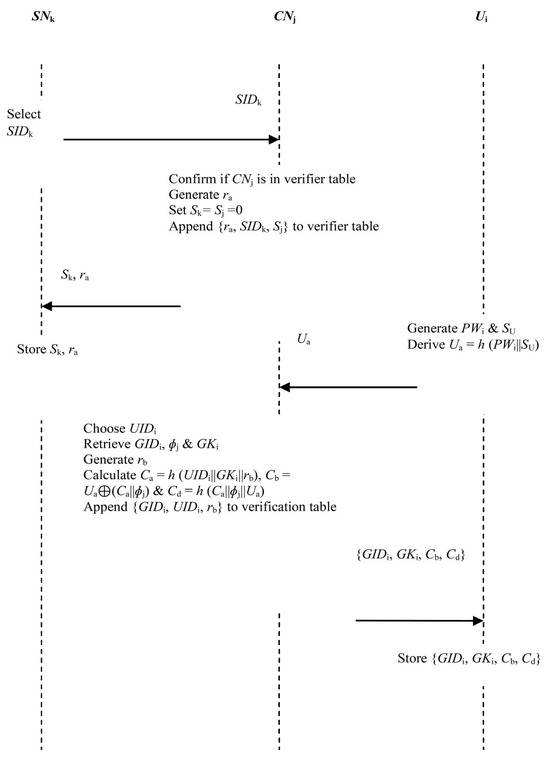
Figure 2.
Registration phase.
Step 2: After obtaining SIDk, CNj checks whether it exists in its verification table (VT). Essentially, SNk is prompted to select a different identity if SIDk already exists in the CNj verification table. Otherwise, CNj generates random number ra and initializes the sequence numbers as Sk = Sj =0. These sequence numbers ensure that SNk and CNj are always synchronized. Next, CNj appends value set {ra, SIDk, Sj} to its verification table before forwarding {Sk, ra} to the SNk.
Step 3: Upon obtaining {Sk, ra} from CNj, the SNk safely stores these parameters in its memory. These values will be used in the subsequent mutual authentication phase that is described in Section 3.2 below.
3.1.2. User Registration
The ultimate objective of this phase is to register all users at the controller node CNj before being permitted to access information in specific sensor node SNk. This is accomplished by the execution of the four steps below.
Step 1: User Ui generates password PWi and private key SU. Next, parameter Ua = h (PWi||SU) is derived before forwarding {Ua} to the controller node, as shown in Figure 2.
Step 2: Upon obtaining {Ua}, CNj randomly chooses unused UIDi P and assigns it to the current Ui, where P is a pool of generated identities (UID1, UID2,…UIDN). Essentially, CNj maintains a pool of identities from which one is picked and assigned to a new user Ui. Next, CNj utilizes this UIDi to obtain the equivalent pseudonym GIDi shared among users of the group, ɸj and GKi. Basically, each user’s unique identity UIDi is associated with a certain group whose pseudonym is GIDi and group key is GKi. After the effective retrieval of GIDi and GKi, CNj retrieves its secret key ɸj used to compute the parameters in the subsequent steps.
Step 3: CNj chooses random number rb and proceeds to derive Ca = h (UIDi||GKi||rb), Cb = Ua(Ca||ɸj) and Cd = h (Ca||ɸj||Ua). Next, CNj appends {GIDi, UIDi, rb} to its verification table and sends {GIDi, GKi, Cb, Cd} over to user Ui for subsequent login and mutual authentication. This verification table is searched every time new users and sensor nodes are registered so that a given identity is not assigned to more than one network entity.
Step 4: Upon obtaining {GIDi, GKi, Cb, Cd}, the user’s smart device SDi stores these parameters in its memory. The user will deploy these security tokens to authenticate with the controller node CNj as well as the smart farm sensor node SNk.
3.2. Login and Authentication
When the user wishes to access some particular smart farm sensor SNk, the two must mutually authenticate each other. In addition, they must negotiate a session key upon successful mutual verification. This key is then utilized to encipher all the exchanged information over the wireless public channels. This is accomplished using the seven steps described below, and summarized in Algorithm 2.
Step 1: User Ui enters password PWi into his/her smart device SDi, which then computes Ua* = h (PWi||SU), (Ca||ɸj) = CbUa* and Cd* = h (Ca||ɸj||Ua*). Next, it checks if Cd* = Cd, where Cd is the value stored in its memory. Essentially, the login request is rejected if this verification fails. Otherwise, Ui has successfully logged into his/her smart device SDi.
Step 2: The smart device SDi generates random number rc and derives Ub = ɸjh (GIDi||GKi||Tu), Uc = (rc||SIDk||)h(GIDi||ɸj||Ca||Tu) and Ud = h (rc||Ca||GIDi||Tu). At the end, the smart device SDi composes authentication message Authu = {GIDi, Ub, Uc, Ud, Tu}, which is forwarded to CNj, as shown in Figure 3.
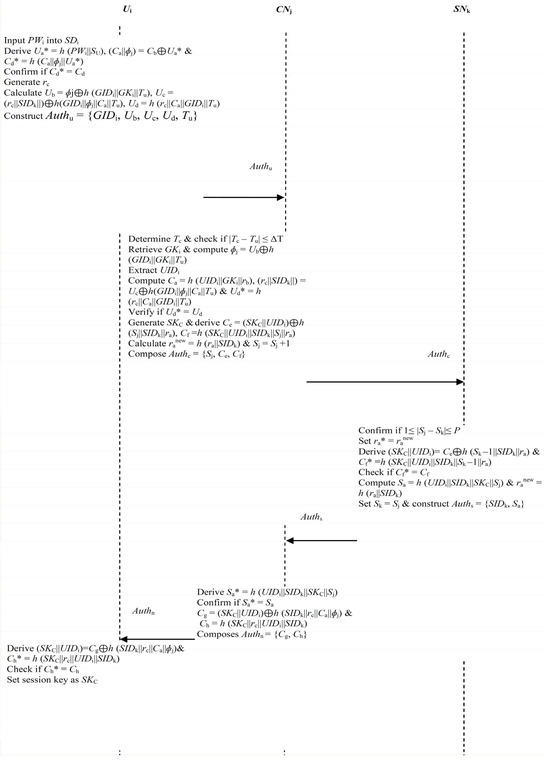
Figure 3.
Login and authentication.
Step 3: Upon obtaining Authu, CNj determines current timestamp Tc that it deploys to validate the received Tu against ΔT by checking if |Tc − Tu| ≤ ΔT. On the condition that Tu is not fresh, the session is aborted. Otherwise, CNj retrieves GKi based on the received GIDi. It then computes ɸj = Ubh (GIDi||GKi||Tu) and retrieves user identity UIDi from its verification table. Next, values Ca = h (UIDi||GKi||rb), (rc||SIDk||) = Uch(GIDi||ɸj||Ca||Tu) and Ud* = h (rc||Ca||GIDi||Tu) are derived before checking whether the derived Ud* is equivalent to Ud received in message Authu. Provided that these two values are dissimilar, the session is aborted immediately. If not, CNj randomly selects SKC as the session key, which it utilizes to calculate Ce = (SKC||UIDi)h (Sj||SIDk||ra) and Cf = h (SKC||UIDi||SIDk||Sj||ra).
Step 4: CNj updates random number ra as ranew = h (ra||SIDk). In addition, it increments the sequence number Sj by 1; that is, Sj = Sj + 1. At the end, it constructs authentication message Authc = {Sj, Ce, Cf} and sends it over to SNk.
Step 5: Having received Authc, the SNk checks if 1≤ |Sj − Sk|≤ P. In a nutshell, the authentication session is aborted when this validation fails. However, if the verification is successful, the SNk proceeds to derive (SKC||UIDi)= Ceh (Sk||SIDk||ra) and Cf* =h (SKC||UIDi||SIDk||Sk||ra). Next, it confirms whether Cf* = Cf and terminates the session if this condition is false. Otherwise, Sa = h (UIDi||SIDk||SKC||Sj) is computed. This is followed by updating ra as ranew = h (ra||SIDk) and setting Sk = Sj. At the end, the SNk composes authentication message Auths = {SIDk, Sa} which is transmitted towards CNj.
Step 6: Upon obtaining message Auths, CNj derives Sa* = h (UIDi||SIDk||SKC||Sj) and checks if Sa* is equivalent to Sa received Auths. Provided that these two parameters are dissimilar, the authentication session is aborted. However, if the verification succeeds, CNj calculates Cg = (SKC||UIDi)h (SIDk||rc||Ca||ɸj) and Ch = h (SKC||rc||UIDi||SIDk). Finally, CNj constructs message Authn = {Cg, Ch}, which is forwarded towards Ui.
Step 7: After receiving message Authn, the user’s smart device SDi computes (SKC||UIDi) = Cgh (SIDk||rc||Ca||ɸj) and Ch* = h (SKC||rc||UIDi||SIDk). Next, the smart device SDi confirms whether the derived Ch* is equivalent to Ch received in message Authn. Provided that this verification is successful, the authentication among Ui, CNj and SNk is considered complete, and SKC is set as the session key.
| Algorithm 2: Login and authentication |
Begin
|
3.3. Parameter Update Phase
The two procedures below are activated upon the compromising of user password PWi.
Step 1: Ui enters his/her password into SDi. This is followed by the calculation of Ua = h (PWi||SU), (Ca||ɸj) = UaCb and Cd* = h (Ca||ɸj||Ua). Next, it confirms whether the derived Cd* is equivalent to Cd, stored in its memory. If this verification is unsuccessful, the password change request is denied. However, if the verification is successful, the SDi inputs new password PWinew.
Step 2: SDi calculates Uanew = h (PWinew||SU), Cbnew = Uanew(Ca||ɸj) and Cdnew = h (Ca||ɸj||Uanew). At the end, the SDi substitutes parameter set {Cb, Cd} with its updated version {Cbnew, Cdnew} in its memory.
4. Security Analysis
In this part, we carry out both formal and informal security analyses of our scheme. The aim is to demonstrate its semantic robustness and resilience to typical attacks in the precision agriculture environment.
4.1. Formal Security Evaluation
In this sub-section, we utilize the Burrows–Abadi–Needham (BAN) logic to reveal the robustness of the authentication procedures as well as the session key setup between Ui and SNk. In this proof, we let A and B represent statements, while S and T denote the subjects. The symbols used during the BAN logic proofs are detailed below.
# (B): Message B is fresh;
S | ≡ A: Subject S considers statement A to be true;
S | ~ A: At some point, subject S sent message A;
S | A: S has seen message A;
S | ⇒ A: S has control over A;
: Subject S and T are sharing key k;
ST: k is the shared secret between principals S and T;
{A}k: Message A is encrypted using key k;
: Secret k is combined with A.
In addition to the above logic symbols, we deployed BAN logic rules below to demonstrate that the authentication among Ui, CNj and SNk is carried out in a secure manner.
Message-meaning rule (MMR): ;
Nonce verification rule (NVR): ;
Jurisdiction rule (JR): ;
Believe rule (BR): ;
Freshness rule (FR):.
To demonstrate that our scheme achieves perfect and protected joint validation between Ui and SNk, the goals below must be attained.
Goal 1: UiUi SNk;
Goal 2: Ui SNkUi SNk;
Goal 3: SNk Ui SNk;
Goal 4: SNk UiUi SNk.
During the login and authentication process, four messages are exchanged among Ui, CNj and SNk. For effective proofs, these messages are converted into idealized format as detailed below.
Authu (Ui → CNj): {GIDi, Ub, Uc, Ud, Tu};
Idealized form: (UiCNj, SIDk, < GIDi, SIDk, rc, Tu ;
Authc (CNj → SNk): {Sj, Ce, Cf };
Idealized form: (CNjSNk, UIDi, < UIDi, SIDk, , Sj ;
Auths (SNk → CNj): {SIDk, Sa};
Idealized form: < UIDi, SIDk, ;
Authn (CNj → Ui): {Cg, Ch};
Idealized form: (CNjUi, < UIDi, SIDk, CNj Ui .
Next, the following preliminary state assumptions (PSAi) are made regarding our proposed scheme. The freshness and legitimacy of the values in these assumptions are deployed to demonstrate the robustness of the authentication procedures and the session key setup between Ui and SNk (as seen in proofs P1 to P24 that follow).
PSA1: CNj |≡ # (Tu);
PSA2: CNj |≡ # (rc);
PSA3: SNk |≡ # (SKC);
PSA4: SNk |≡ # (SKC);
PSA5: UiUiCNj;
PSA6: CNjUiCNj;
PSA7: SNkSNk iCNj;
PSA8: CNjSNk iCNj;
PSA9: UiCNj SNk;
PSA10: SNkCNj SNk.
Using these notation, rules, initial state assumptions and idealized messages, we execute the rigorous BAN logic proofs to demonstrate the existence of robust and secured authentication among Ui, CNj and SNk.
Based on message Authu, we obtain the following proof.
P1: CNj (Ui CNj, SIDk.
According to PSA6, the MMR is applied to yield P2.
P2: CNj |≡ Ui CNj, SIDk.
On the other hand, the freshness rule is used in PSA6 to obtain P3.
P3: CNj |≡# (UIDi, SIDk, GIDi, Tu, Ui CNj).
Based on P2 and P3, we apply the NVR to obtain P4.
P4: CNj |≡ Ui (UIDi, SIDk, GIDi, Tu, Ui CNj).
According to Authc, we obtain P5 as follows.
P5: SNk (CNj SNk, UIDi.
Based on PSA7 and P5, the message-meaning rule is applied to yield P6.
P6: SNk |≡ CNj|~ (CNj SNk, UIDi).
In accordance with PSA3, the freshness rule is effected to obtain P7.
P7: SNk |≡ # (UIDi, SIDk, CNj SNk, Sj).
From P6 and P7, we utilize the nonce-verification rule to obtain P8.
P8: SNk |≡ CNj |≡ (UIDi, SIDk, CNj SNk, Sj).
Based on Auths, we obtain P9 as follows.
P9: CNj < UIDi, SIDk, .
In accordance with PSA8 and P9, the message-meaning rule is applied to yield P10.
P10: CNj |≡ SNk|~ (UIDi, SIDk, ).
The application of the freshness rule to P10 results in P11 as follows.
P11: CNj |≡ SNk|≡ (UIDi, SIDk, ).
Based on message Authn, we obtain P12.
P12: Ui (CNj Ui.
In accordance with PSA5 and P12, we utilize the message-meaning rule to obtain P13.
P13: Ui |≡ CNj |~ (CNj Ui).
The application of the freshness rule on PSA4 results in P14.
P14: Ui |≡# (UIDi, SIDk, CNj Ui).
On the other hand, NVR is applied to P13 and P14 to obtain the following.
P15: Ui |≡ CNj |≡ (UIDi, SIDk, CNj Ui).
Similarly, the belief rule is applied to P6 and P7 to obtain P16.
P16: SNk |≡ (CNj SNk).
From P8, we utilize the belief rule to obtain P17.
P17: SNk |≡ CNj |≡ (CNj Ui).
On the other hand, the belief rule is used in P11 to obtain P18.
P18: CNj |≡ SNk|≡ ( ).
Similarly, the belief rule is utilized in P13 and P14 to obtain P19.
P19: Ui |≡ (CNj Ui).
However, the application of the belief rule in P15 yields P20.
P20: Ui |≡ CNj |≡ (CNj Ui).
Based on PSA10 and P16, we obtain P21.
P21: SNk |≡ (Ui SNk); hence, Goal 3 is realized.
On the other hand, we obtain P22 from PSA10 and P17 as follows.
P22: SNk |≡ Ui |≡ (Ui SNk) and hence Goal 4 is attained.
From PSA9, P18 and P19, we obtain the following.
P23: Ui |≡ (SNk Ui), achieving Goal 1.
Finally, from PSA9, P18 and P20, we obtain P24 as follows.
P24: Ui |≡ SNk|≡ (SNk Ui), attaining Goal 2.
4.2. Informal Security Analysis
In this sub-section, we formulate and prove a number of lemmas to show that our scheme is secure under the adversarial capabilities in the Canetti–Krawczyk attack model. These capabilities are described in [53].
Lemma 1.
MitM and forgery threats are prevented.
Proof.
Let us assume that adversary à is wants to forge validation messages so as to deceive any unsuspecting receivers. To achieve this goal, messages Authu = {GIDi, Ub, Uc, Ud, Tu}, Authc = {Sj, Ce, Cf }, Auths = {SIDk, Sa} and Authn = {Cg, Ch} are captured. Next, attempts are made to modify these messages. Here, Ub = ɸj h (GIDi||GKi||Tu), Uc = (rc||SIDk||) h(GIDi||ɸj||Ca||Tu), Ud = h (rc||Ca||GIDi||Tu), Ce = (SKC||UIDi) h (Sj||SIDk||ra), Cf = h (SKC||UIDi||SIDk||Sj||ra), Sa = h (UIDi||SIDk||SKC||Sj), Cg = (SKC||UIDi) h (SIDk||rc||Ca||ɸj) and Ch = h (SKC||rc||UIDi||SIDk). Evidently, adversary à does not have access to keys such as GKi and SKC, sequence number Sj, unique identities SIDk and UIDi, and random numbers rc and ra. Since these two threats are easily mitigated in our protocol, both integrity and confidentiality are upheld. □
Lemma 2.
Robust mutual verification is executed.
Proof.
During the login and validation phase, entities Ui, SDi, CNj and SNk mutually verify each other. To gain access to his/her smart device SDi, it checks whether Cd* = Cd, where Cd is the value stored in its memory. Basically, the login request is rejected if this verification unsuccessful. On the other hand, CNj validates SDi by deriving Ud* = h (rc||Ca||GIDi||Tu) and confirming if Ud* = Ud. For its part, the SNk verifies CNj by deriving Cf* = h (SKC||UIDi||SIDk||Sk − 1||ra) and confirming whether Cf* = Cf. Similarly, CNj validates SNk through the computation of Sa* = h (UIDi||SIDk||SKC||Sj) and confirmation of whether Sa* = Sa. Finally, SDi authenticates CNj by calculating Ch* = h (SKC||rc||UIDi||SIDk) and checking if Ch* = Ch. For all these scenarios, the authentication session is halted upon verification failure. □
Lemma 3.
Our security technique prevents replay threats.
Proof.
In our scheme, we make use of timestamps, sequence numbers and random numbers to curb these threats. During the authentication procedures, messages Authu = {GIDi, Ub, Uc, Ud, Tu}, Authc = {Sj, Ce, Cf }, Auths = {SIDk, Sa} and Authn = {Cg, Ch} are exchanged. Here, Ub = ɸj h (GIDi||GKi||Tu), Uc = (rc||SIDk||) h(GIDi||ɸj||Ca||Tu), Ca = h (UIDi||GKi||rb), Ud = h (rc||Ca||GIDi||Tu), Ce = (SKC||UIDi) h (Sj||SIDk||ra), Cf =h (SKC||UIDi||SIDk||Sj||ra), Sa = h (UIDi||SIDk||SKC||Sj), Cg = (SKC||UIDi) h (SIDk||rc||Ca||ɸj) and Ch = h (SKC||rc||UIDi||SIDk). Evidently, these messages incorporate timestamp Tu, random numbers rc, rb and ra, and sequence number Sj. Therefore, any replayed message can be effortlessly decerned at the receiver end since these parameters will fail the freshness tests. □
Lemma 4.
Anonymity and untraceability are preserved.
Proof.
The objective of anonymity is to prevent adversaries from discerning the actual identity of the users hinged on the messages transferred across the public channels. On the other hand, untraceability ensures that users are not tracked based on the publicly exchanged messages. In our scheme, messages Authu = {GIDi, Ub, Uc, Ud, Tu}, Authc = {Sj, Ce, Cf }, Auths = {SIDk, Sa} and Authn = {Cg, Ch} are exchanged over the public internet. It is clear that the user’s real identity UIDi is never sent in plaintext in all these messages. In fact, it is only the GIDi (pseudonym shared among users of the group) that can be extracted from these messages. Any effort to retrieve UIDi from Ce = (SKC||UIDi) h (Sj||SIDk||ra), Cf =h (SKC||UIDi||SIDk||Sj||ra), Sa = h (UIDi||SIDk||SKC||Sj), Cg = (SKC||UIDi) h (SIDk||rc||Ca||ɸj) and Ch = h (SKC||rc||UIDi||SIDk) will fail due to its encapsulation in other parameters. In addition, there is need to reverse h (.), which is computationally cumbersome. □
Lemma 5.
Our protocol mitigates eavesdropping and sensor node spoofing threats.
Proof.
The ultimate goal of this attack is to derive verification parameter Sa = h (UIDi||SIDk||SKC||Sj) used to authenticate SNk at CNj. This requires that adversary à access identities UIDi and SIDk, session key SKC and sequence number Sj. Based on Lemma 4, adversary à does not have access to UIDi. Similarly, session key SKC and sequence number Sj are generated at the CNj and hence not available to Ã. Therefore, although SIDk can be obtained by eavesdropping on message Auths, an adversary cannot execute sensor node spoofing. □
Lemma 6.
KSSTI attacks are thwarted and forward secrecy is preserved.
Proof.
To uphold forward key secrecy, it is required that the leakage of long-term secret keys cannot result in the recovery of the previous and subsequent session keys. Let us assume that à has compromised long-term secrets such as SU and GKi. The session key in our protocol is generated at CNj and encapsulated in parameters such as Ce = (SKC||UIDi) h (Sj||SIDk||ra), Cf =h (SKC||UIDi||SIDk||Sj||ra), Sa = h (UIDi||SIDk||SKC||Sj), Cg = (SKC||UIDi) h (SIDk||rc||Ca||ɸj) and Ch = h (SKC||rc||UIDi||SIDk). Evidently, these long-term keys cannot help adversary à in deriving session key SKC. □
Lemma 7.
Our approach can withstand user impersonation attacks.
Proof.
In the proposed protocol, user Ui constructs message Authu = {GIDi, Ub, Uc, Ud, Tu}, which is transmitted towards CNj over the public internet. Let us assume that adversary à wants to construct this message so as to impersonate Ui. Here, Ub = ɸj h (GIDi||GKi||Tu), ɸj = Ub h (GIDi||GKi||Tu), Uc = (rc||SIDk||) h(GIDi||ɸj||Ca||Tu), Ca = h (UIDi||GKi||rb) and Ud = h (rc||Ca||GIDi||Tu). According to Lemma 4, adversary à cannot access UIDi. In addition, group key GKi cannot be eavesdropped on from the public Internet since it is never sent in messages Authu, Authc, Auths and Authn. For the same reason, adversary à does not have access to random numbers rb and rc. □
Lemma 8.
Our scheme can withstand physical, stolen device and side-channeling threats.
Proof.
Supposing that an adversary has stolen or captured sensor node SNk and extracted value set {Sk, ra} stored in it through power analysis. Using the extracted parameters, attempts are made to derive sensor node verification parameter Sa = h (UIDi||SIDk||SKC||Sj). It is clear that the extracted values cannot help the adversary to derive Sa. Similarly, the physical capture and extraction of value set {GIDi, GKi, Cb, Cd} cannot facilitate the computation of user verification parameter Ud = h (rc||Ca||GIDi||Tu). □
Lemma 9.
Privileged insider attacks are thwarted.
Proof.
Suppose that some entities in the control node CNj turns out to be malicious. As such, attempts may be made to capture user password PWi and use it for malicious activities. During user registration, Ui sends parameter Ua = h (PWi||SU) to CNj over secured channels. Although Ua contains PWi, it is masked in secret key SU prior to being exposed to one-way hashing operation. Therefore, it is extremely cumbersome for à to extract PWi from parameter Ua. □
Lemma 10.
Our scheme can withstand password guessing and session hijacking threats.
Proof.
Let us assume that adversary à wants to gain access to user smart device SDi and thereafter hijack the session and exchange data with other network entities. In our scheme, after entering PWià into SDi, it computes parameters Ua* = h (PWiÃ||SU), (Ca||ɸj) = Cb Ua* and Cd* = h (Ca||ɸj||Ua*). Next, it checks if Cd* = Cd, where Cd is the value stored in SDi’s memory. Since PWià PWi, the adversary à will fail the Cd* Cd check. □
Lemma 11.
Denial of service and de-synchronization attacks are mitigated.
Proof.
Supposing that adversary à is determined to de-sync the controller node CNj so that the sensor nodes are denied access to CNj. To avert this, our scheme uses sequence numbers Sk and Sj to ensure that SNk and CNj are always synchronized. During the authentication procedures, message Authc = {Sj, Ce, Cf} is sent by CNj towards the SNk. Here, Ce = (SKC||UIDi) h (Sj||SIDk||ra) and Cf =h (SKC||UIDi||SIDk||Sj||ra). Similarly, message Auths = {SIDk, Sa} is forwarded from the SNk towards CNj, where Sa = h (UIDi||SIDk||SKC||Sj). It is clear that these messages contain sequence number Sj. □
Lemma 12.
Scalability is enhanced in the proposed scheme.
Proof.
In our scheme, the network entities do not rely solely on the controller node to generate and distribute all the identities and keying parameters. For instance, during the registration phase, the sensor node SNk selects SIDk as its unique identity, which is then forwarded to the controller node CNj. Similarly, user Ui generates password PWi and private key SU, and computes value Ua = h (PWi||SU) before forwarding {Ua} to the controller node. This lack of total dependency on CNj for derivation and distribution of identities and keying parameters imply that more users and sensors can be added without overwhelming the controller node. □
5. Comparative Performance Evaluations
In the majority of the security techniques, communication costs, offered functionalities, energy consumption levels and computation overheads are frequently utilized to evaluate their performance. Therefore, we utilize these four performance measures to evaluate our scheme as described below.
5.1. Computation Overheads
The implementation details of our scheme involved a laptop with 4 GB of RAM, running on an Intel processor with 2.4 Ghz of clock frequency. On the other hand, the operating system installed in this machine is Ubuntu 22.04 LTS. Under these operational conditions, the Pairing-Based Cryptography (PBC) library is used to yield the execution time for various cryptographic primitives as follows: elliptic curve scalar multiplications (Tpm ≈ 3.53 ms), one-way hashing (Th ≈ 0.128 ms), elliptic curve point addition (Tpa ≈ 0.026 ms), fuzzy extraction (Tfe ≈ 3.53 ms), t-degree univariate polynomial evaluation (Tpe ≈ 16.28 ms), bilinear pairing (Tb ≈ 27.52 ms), modular exponentiation (Te ≈ 0.275 ms) and symmetric encryption/decryption (Ten ≈ 0.028 ms). During the login and verification procedures, SDi executes 8Th, while SNk executes 5Th.
On the other hand, the controller node CNj executes 10Th operations, and hence, the cumulative computation overhead in our scheme is 23Th. Table 2 presents the comparison of this computation overhead with other related schemes.

Table 2.
Computation overheads.
As demonstrated in Figure 4, the approach in [18] incurs the heaviest computation costs of 76.82 ms. This is followed by the security methods in [6,12,16,30,48,49,50,51,52] with computation overheads of 57.41 ms, 43.62 ms, 30.54 ms, 16.04 ms, 12.54 ms, 7.37 ms, 5.91 ms and 5.56 ms, respectively. The high execution durations of these schemes is attributed to the computationally extensive scalar multiplications, fuzzy extractions and encryptions.
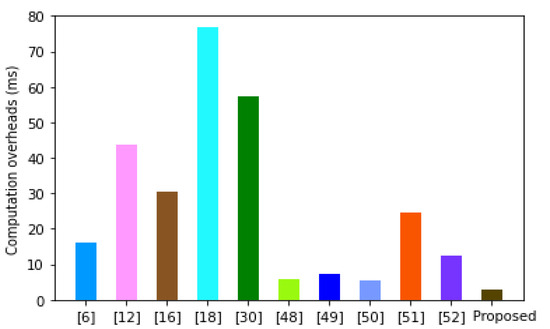
Figure 4.
Computation overheads.
However, the proposed scheme involves only efficient one-way hashing and XOR operations. This explains its low computation costs. High computation overheads translate to increased operational delays, which can result in packet drops. These frequent packet drops can potentially interfere with the proper transmission and reception of messages exchanged in precision agriculture. Since the proposed scheme yields the lowest computation overheads, it exhibits the lowest latencies and hence achieves the greatest packet delivery ratio.
5.2. Communication Overheads
In this part, we utilize the sizes of the messages transferred during the login and authentication procedures to obtain the cumulative communication overheads of the developed protocol. To accomplish this, we deploy the values in [18] in which the sizes of the passwords, timestamps and sequence numbers, identities, finite group points, hashing output, elliptic curve points and random numbers are 160 bits, 32 bits, 160 bits, 512 bits, 160 bits, 320 bits and 160 bits, correspondingly. Therefore, the sizes of Authu, Authc, Auths and Authn are (160 + 160 + 160 + 160 + 32 = 672 bits), (32 + 160 + 160 = 352 bits), (160 + 160 = 320 bits), and (160 + 160 = 320 bits), respectively. As such, our scheme has 1664 bits as its communication costs. Table 3 shows the communication costs of other related schemes, where HGWN is the home gateway node, U is the user, SN is the sensor node, DR is the drone, GSS is the ground station server, AG is the aggregator, DSP is the data service provider, CBC is the consortium blockchain, SM is the service manager and CA is the controlling authority.

Table 3.
Communication overheads.
It is apparent from Figure 5 that the protocol in [30] incurs the highest communication costs of 5792 bits. This is followed by the schemes in [6,12,16,18,48,49,50], the proposed protocol, and [51,52] with communication costs of 4256 bits, 3776 bits, 2752 bits, 2368 bits, 2304 bits, 2016 bits, 1728 bits, 1664 bits, 1312 bits and 1060 bits, respectively. Although the schemes in [51,52] incur relatively lower communication costs, they have high computation overheads and are vulnerable to numerous attacks, as shown in Table 4.
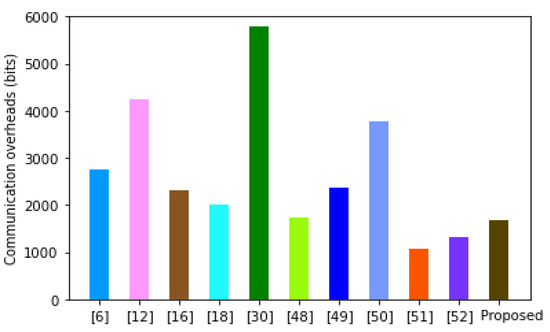
Figure 5.
Communication overheads.

Table 4.
Energy consumption levels.
Therefore, although our protocol incurs relatively high communication overheads, it offers perfect security at the lowest computation overheads. It is therefore suitable for addressing security issues in precision agriculture.
5.3. Energy Consumption
In this sub-section, we estimate the power consumed by our scheme during the login and authentication process. The power consumption (in mJ) is given by the product of voltage in volts, current (in milliamps, mA) drawn in active mode and the time in seconds. That is,
where execution time is equivalent to the computation overheads in Table 2 above.
Power consumption = supply voltage (in V) × current (in mA) × execution time (in S),
According to [54], this current is 2.2 mA, while the supply voltage is 3V. Using these values, the energy consumption of our scheme is 0.019 mJ. Table 4 presents the comparisons of energy consumption of our scheme against other related protocols.
Based on the graphs in Figure 6, the protocol in [18] exhibits the heaviest amount of energy consumption of 0.507 mJ. This is followed by the schemes in [6,12,16,30,48,49,50,51,52] with energy consumption levels of 0.379 mJ, 0.288 mJ, 0.202 mJ, 0.163 mJ, 0.106 mJ, 0.083 mJ, 0.049 mJ, 0.039 mJ and 0.037 mJ.
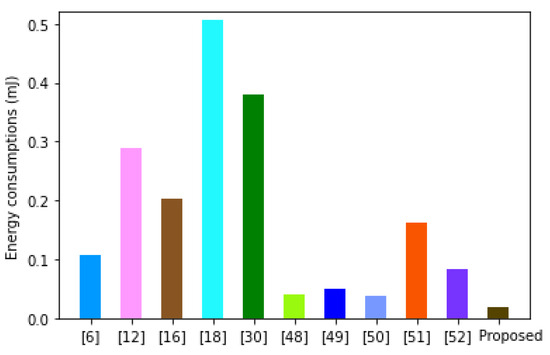
Figure 6.
Energy consumption levels.
However, the proposed scheme consumes only 0.019 mJ of energy, which is the lowest. Since most of the PA sensor devices are limited in terms of energy, our scheme is the best suited for deployment in these sensors.
5.4. Supported Functionalities
The proposed protocol supports a wide range of security and privacy characteristics which are key in precision agriculture. In addition, it has been demonstrated to be robust against numerous security threats. Table 5 presents the comparative evaluation of the features of our scheme against other related protocols.

Table 5.
Security characteristics.
It is evident from Table 5 that the security protocol in [12] supports only seven features, rendering it the most vulnerable. Conversely, the protocols in [50,51] support 11 features each, while the schemes in [16,18,48,49,52] support 12 features each. For its part, the protocol in [30] supports 13 features, while the scheme in [6] offers support for 14 features. However, our proposed scheme supports all 19 of the security features. Overall, the proposed scheme has been demonstrated to offer robust security at relatively low communication costs and the least computation costs, as well as the lowest energy consumption. Since the majority of the devices in precision agriculture are resource-constrained, our scheme is the most suitable this environment. Our scheme adopts the conventional communication framework typical in existing farming systems, where we have central controllers, users and sensor nodes. In addition, the proposed scheme deploys only one-way hashing functions, which are lightweight. As such, no additional hardware is required for extensive computations. Consequently, our protocol is easy to integrate into existing farming systems such as drones and other IoT devices.
6. Conclusions
The need to increase the food supply in the face of limited resources for the ever-growing global population has seen the incorporation of smart technologies in agriculture. Sensors in precision agriculture collect information such as water content, soil moisture, humidity and temperature, which are then analyzed to facilitate decision making. These technologies have been shown to result in increased agricultural yields at low labor and resources. In spite of these positive contributions of smart agronomy, the amalgamation of a wide range of sensors and technologies coupled with the deployment of open wireless internet for message exchange results in numerous security threats. Although many solutions have been presented in the literature, security vulnerabilities and high resource requirements in most of these schemes render them unsuitable for deployment in resource-limited PA devices. The developed scheme is demonstrated to mitigate the majority of these security threats, such as packet replay, MitM, DoS, de-synchronization, privileged insider, impersonation and spoofing attacks. From the performance perspective, our technique consumes the least energy and computational resources while incurring relatively lower communication overheads. As such, our protocol can reduce operational costs and improve the resilience of agricultural IoT networks. Future research in this area will involve further improvements in the obtained communication costs so as to make it bandwidth-friendly. In addition, real-world testing and various case studies may be carried out against this scheme.
Author Contributions
All the authors have contributed equally to this article. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Data Availability Statement
The raw data supporting the conclusions of this article will be made available by the authors upon request.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Torky, M.; Hassanein, A.E. Integrating Blockchain and the Internet of Things in Precision Agriculture: Analysis, Opportunities, and Challenges. Comput. Electron. Agric. 2020, 178, 105476. [Google Scholar] [CrossRef]
- Fathy, C.; Ali, H.M. A Secure IoT-Based Irrigation System for Precision Agriculture Using the Expeditious Cipher. Sensors 2023, 23, 2091. [Google Scholar] [CrossRef]
- Vangala, A.; Das, A.K.; Mitra, A.; Das, S.K.; Park, Y. Blockchain-Enabled Authenticated Key Agreement Scheme for Mobile Vehicles-Assisted Precision Agricultural IoT Networks. IEEE Trans. Inf. Forensics Secur. 2023, 18, 904–919. [Google Scholar] [CrossRef]
- Munaganuri, R.K.; Rao, Y.N. PAMICRM: Improving Precision Agriculture through Multimodal Image Analysis for Crop Water Requirement Estimation Using Multidomain Remote Sensing Data Samples. IEEE Access 2024, 12, 52815–52836. [Google Scholar] [CrossRef]
- Lanucara, S.; Praticò, S.; Pioggia, G.; Di Fazio, S.; Modica, G. Web-Based Spatial Decision Support System for Precision Agriculture: A Tool for Delineating Dynamic Management Unit Zones (MUZs). Smart Agric. Technol. 2024, 8, 100444. [Google Scholar] [CrossRef]
- Rangwani, D.; Sadhukhan, D.; Ray, S.; Khan, M.K.; Dasgupta, M. An Improved Privacy Preserving Remote User Authentication Scheme for Agricultural Wireless Sensor Network. Trans. Emerg. Telecommun. Technol. 2021, 32, e4218. [Google Scholar] [CrossRef]
- Abduljabbar, Z.A.; Nyangaresi, V.O.; Jasim, H.M.; Ma, J.; Hussain, M.A.; Hussien, Z.A.; Aldarwish, A.J.Y. Elliptic Curve Cryptography-Based Scheme for Secure Signaling and Data Exchanges in Precision Agriculture. Sustainability 2023, 15, 10264. [Google Scholar] [CrossRef]
- Raj, M.; Harshini; Gupta, S.; Atiquzzaman, M.; Rawlley, O.; Goel, L. Leveraging Precision Agriculture Techniques Using UAVs and Emerging Disruptive Technologies. Energy Nexus 2024, 14, 100300. [Google Scholar] [CrossRef]
- Sonavane, S.M.; Prashantha, G.R.; Nikam, P.D.; Mayuri, A.V.R.; Chauhan, J.; Sountharrajan, S.; Bavirisetti, D.P. Optimizing QoS and Security in Agriculture IoT Deployments: A Bioinspired Q-Learning Model with Customized Shards. Heliyon 2024, 10, e24224. [Google Scholar] [CrossRef] [PubMed]
- You, M.; Kim, Y.; Kim, J.; Seo, M.; Son, S.; Shin, S.; Lee, S. FuzzDocs: An Automated Security Evaluation Framework for IoT. IEEE Access 2022, 10, 102406–102420. [Google Scholar] [CrossRef]
- Bouzidi, M.; Gupta, N.; Cheikh, F.A.; Shalaginov, A.; Derawi, M. A Novel Architectural Framework on IoT Ecosystem, Security Aspects and Mechanisms: A Comprehensive Survey. IEEE Access 2022, 10, 101362–101384. [Google Scholar] [CrossRef]
- Luo, F.; Huang, R.; Xie, Y. Hybrid Blockchain-Based Many-to-Many Cross-Domain Authentication Scheme for Smart Agriculture IoT Networks. J. King Saud Univ.-Comput. Inf. Sci. 2024, 36, 101946. [Google Scholar] [CrossRef]
- Mutlaq, K.A.-A.; Nyangaresi, V.O.; Omar, M.A.; Abduljabbar, Z.A.; Abduljaleel, I.Q.; Ma, J.; Al Sibahee, M.A. Low Complexity Smart Grid Security Protocol Based on Elliptic Curve Cryptography, Biometrics and Hamming Distance. PLoS ONE 2024, 19, e0296781. [Google Scholar] [CrossRef] [PubMed]
- Huang, H.; Zhou, S.; Lin, J.; Zhang, K.; Guo, S. Bridge the Trustworthiness Gap amongst Multiple Domains: A Practical Blockchain-Based Approach. In Proceedings of the ICC 2020—2020 IEEE International Conference on Communications (ICC), Dublin, Ireland, 7–11 June 2020. [Google Scholar]
- Wu, H.-T.; Tsai, C.-W. An Intelligent Agriculture Network Security System Based on Private Blockchains. J. Commun. Netw. 2019, 21, 503–508. [Google Scholar] [CrossRef]
- Vangala, A.; Sutrala, A.K.; Das, A.K.; Jo, M. Smart Contract-Based Blockchain-Envisioned Authentication Scheme for Smart Farming. IEEE Internet Things J. 2021, 8, 10792–10806. [Google Scholar] [CrossRef]
- Wang, L.; Xu, L.; Zheng, Z.; Liu, S.; Li, X.; Cao, L.; Li, J.; Sun, C. Smart Contract-Based Agricultural Food Supply Chain Traceability. IEEE Access 2021, 9, 9296–9307. [Google Scholar] [CrossRef]
- Bera, B.; Vangala, A.; Das, A.K.; Lorenz, P.; Khan, M.K. Private Blockchain-Envisioned Drones-Assisted Authenti-Cation Scheme in IoT-Enabled Agricultural Environment. Comput. Stand. Interfaces 2022, 80, 103567. [Google Scholar] [CrossRef]
- Xue, L.; Huang, H.; Xiao, F.; Wang, W. A Cross-Domain Authentication Scheme Based on Cooperative Blockchains Functioning with Revocation for Medical Consortiums. IEEE Trans. Netw. Serv. Manag. 2022, 19, 2409–2420. [Google Scholar] [CrossRef]
- Shen, M.; Liu, H.; Zhu, L.; Xu, K.; Yu, H.; Du, X.; Guizani, M. Blockchain-Assisted Secure Device Authentication for Cross-Domain Industrial IoT. IEEE J. Sel. Areas Commun. 2020, 38, 942–954. [Google Scholar] [CrossRef]
- Yang, Y.; Wei, L.; Wu, J.; Long, C.; Li, B. A Blockchain-Based Multidomain Authentication Scheme for Conditional Privacy Preserving in Vehicular Ad-Hoc Network. IEEE Internet Things J. 2022, 9, 8078–8090. [Google Scholar] [CrossRef]
- Bagga, P.; Sutrala, A.K.; Das, A.K.; Vijayakumar, P. Blockchain-Based Batch Authentication Protocol for Internet of Vehicles. J. Syst. Arch. 2021, 113, 101877. [Google Scholar] [CrossRef]
- Nyangaresi, V.O.; Jasim, H.M.; Mutlaq, K.A.A.; Abduljabbar, Z.A.; Ma, J.; Abduljaleel, I.Q.; Honi, D.G. A Symmetric Key and Elliptic Curve Cryptography-Based Protocol for Message Encryption in Unmanned Aerial Vehicles. Electronics 2023, 12, 3688. [Google Scholar] [CrossRef]
- Ali, R.; Pal, A.K.; Kumari, S.; Karuppiah, M.; Conti, M. A Secure User Authentication and Key-Agreement Scheme Using Wireless Sensor Networks for Agriculture Monitoring. Future Gener. Comput. Syst. 2018, 84, 200–215. [Google Scholar] [CrossRef]
- Chen, M.; Lee, T.-F.; Pan, J.-I. An Enhanced Lightweight Dynamic PseudonymIdentity Based Authentication and Key AgreementScheme Using Wireless Sensor Networks for Agriculture Monitoring. Sensors 2019, 19, 1146. [Google Scholar] [CrossRef] [PubMed]
- Alyahya, S.; Khan, W.U.; Ahmed, S.; Marwat, S.N.K.; Habib, S. Cyber Secure Framework for Smart Agriculture: Robust and Tamper-Resistant Authentication Scheme for IoT Devices. Electronics 2022, 11, 963. [Google Scholar] [CrossRef]
- Bothe, A.; Bauer, J.; Aschenbruck, N. RFID-Assisted Continuous User Authentication for IoT-Based Smart Farming. In Proceedings of the 2019 IEEE International Conference on RFID Technology and Applications (RFID-TA), Pisa, Italy, 25–27 September 2019. [Google Scholar]
- Hussien, Z.A.; Abdulmalik, H.A.; Hussain, M.A.; Nyangaresi, V.O.; Ma, J.; Abduljabbar, Z.A.; Abduljaleel, I.Q. Lightweight Integrity Preserving Scheme for Secure Data Exchange in Cloud-Based IoT Systems. Appl. Sci. 2023, 13, 691. [Google Scholar] [CrossRef]
- Panda, S.S.; Jena, D.; Mohanta, B.K.; Ramasubbareddy, S.; Daneshmand, M.; Gandomi, A.H. Authentication and Key Management in Distributed IoT Using Blockchain Technology. IEEE Internet Things J. 2021, 8, 12947–12954. [Google Scholar] [CrossRef]
- Vangala, A.; Das, A.K.; Lee, J.-H. Provably Secure Signature-based Anonymous User Authentication Protocol in an Internet of Things-enabled Intelligent Precision Agricultural Environment. Concurr. Comput. 2021, 35, e6187. [Google Scholar] [CrossRef]
- Hassan, B.; Alsanad, A.A.; Ullah, I.; Amin, N.U.; Khan, M.A.; Uddin, M.I.; Wu, J.M.T. A Cost Effective Identi-Ty-Based Authentication Scheme for Internet of Things-Enabled Agriculture. Wirel. Commun. Mob. Comput. 2022, 2022, 4275243. [Google Scholar] [CrossRef]
- Harbi, Y.; Aliouat, Z.; Refoufi, A.; Harous, S.; Bentaleb, A. Enhanced Authentication and Key Management Scheme for Securing Data Transmission in the Internet of Things. Ad Hoc Netw. 2019, 94, 101948. [Google Scholar] [CrossRef]
- Yuan, E.; Wang, L.; Cheng, S.; Ao, N.; Guo, Q. A Key Management Scheme Based on Pairing-Free Identity Based Digital Signature Algorithm for Heterogeneous Wireless Sensor Networks. Sensors 2020, 20, 1543. [Google Scholar] [CrossRef]
- Mishra, D.; Dharminder, D.; Yadav, P.; Sreenivasa Rao, Y.; Vijayakumar, P.; Kumar, N. A Provably Secure Dynamic ID-Based Authenticated Key Agreement Framework for Mobile Edge Computing without a Trusted Party. J. Inf. Secur. Appl. 2020, 55, 102648. [Google Scholar] [CrossRef]
- Andola, N.; Prakash, S.; Gahlot, R.; Venkatesan, S.; Verma, S. An Enhanced Smart Card and Dynamic ID Based Remote Multi-Server User Authentication Scheme. Cluster Comput. 2022, 25, 3699–3717. [Google Scholar] [CrossRef]
- Gupta, D.S.; Islam, S.K.H.; Obaidat, M.S.; Vijayakumar, P.; Kumar, N.; Park, Y. A Provably Secure and Lightweight Identity-Based Two-Party Authenticated Key Agreement Protocol for IIoT Environments. IEEE Syst. J. 2021, 15, 1732–1741. [Google Scholar] [CrossRef]
- Liu, J.; Liu, R.; Lai, Y. Risk-Based Dynamic Identity Authentication Method Based on the UCON Model. Secur. Commun. Netw. 2022, 2022, 1–13. [Google Scholar] [CrossRef]
- Sibahee, A.; Nyangaresi, M.A.; Abduljabbar, V.O.; Luo, Z.A.; Zhang, C.; Ma, J. Two-Factor Privacy Preserving Protocol for Efficient Authentication in Internet of Vehicles Networks. IEEE Internet Things J. 2023, 11, 14253–14266. [Google Scholar] [CrossRef]
- Li, Y.; Cheng, Q.; Shi, W. Security Analysis of a Lightweight Identity-Based Two-Party Authenticated Key Agreement Protocol for IIoT Environments. Secur. Commun. Netw. 2021, 2021, 1–6. [Google Scholar] [CrossRef]
- Li, X.; Niu, J.; Bhuiyan, M.Z.A.; Wu, F.; Karuppiah, M.; Kumari, S. A Robust ECC-Based Provable Secure Authen-Tication Protocol with Privacy Preserving for Industrial Internet of Things. IEEE Trans. Ind. Inform. 2017, 14, 3599–3609. [Google Scholar] [CrossRef]
- Eddine, M.S.; Ferrag, M.A.; Friha, O.; Maglaras, L. EASBF: An Efficient Authentication Scheme over Blockchain for Fog Computing-Enabled Internet of Vehicles. J. Inf. Secur. Appl. 2021, 59, 102802. [Google Scholar] [CrossRef]
- Tomar, A.; Tripathi, S. Blockchain-Assisted Authentication and Key Agreement Scheme for Fog-Based Smart Grid. Clust. Comput. 2022, 25, 451–468. [Google Scholar] [CrossRef]
- Itoo, S.; Khan, A.A.; Kumar, V.; Alkhayyat, A.; Ahmad, M.; Srinivas, J. CKMIB: Construction of Key Agreement Protocol for Cloud Medical Infrastructure Using Blockchain. IEEE Access 2022, 10, 67787–67801. [Google Scholar] [CrossRef]
- Jia, X.; Luo, M.; Wang, H.; Shen, J.; He, D. A Blockchain-Assisted Privacy-Aware Authentication Scheme for Internet of Medical Things. IEEE Internet Things J. 2022, 9, 21838–21850. [Google Scholar] [CrossRef]
- Shuai, M.; Xiong, L.; Wang, C.; Yu, N. A Secure Authentication Scheme with Forward Secrecy for Industrial Internet of Things Using Rabin Cryptosystem. Comput. Commun. 2020, 160, 215–227. [Google Scholar] [CrossRef]
- Fan, Q.; Chen, J.; Deborah, L.J.; Luo, M. A Secure and Efficient Authentication and Data Sharing Scheme for Internet of Things Based on Blockchain. J. Syst. Arch. 2021, 117, 102112. [Google Scholar] [CrossRef]
- Mutlaq, K.A.A.; Nyangaresi, V.O.; Omar, M.A.; Abduljabbar, Z.A. Symmetric Key Based Scheme for Veri-Fication Token Generation in Internet of Things Communication Environment. In EAI International Conference on Applied Cryptography in Computer and Communications; Springer Nature: Cham, Switzerland, 2022; pp. 46–64. [Google Scholar]
- Khalid, H.; Hashim, S.J.; Ahmad, S.M.S.; Hashim, F.; Chaudhary, M.A. Robust Multi-Gateway Authentication Scheme for Agriculture Wireless Sensor Network in Society 5.0 Smart Communities. Agriculture 2021, 11, 1020. [Google Scholar] [CrossRef]
- Kumar, R.; Singh, S.; Singh, D.; Kumar, M.; Gill, S.S. A Robust and Secure User Authentication Scheme Based on Multifactor and Multi-gateway in IoT Enabled Sensor Networks. Secur. Priv. 2024, 7, e335. [Google Scholar] [CrossRef]
- Irshad, A.; Alreshoodi, M. SEMS-5G: A Secure and Efficient Multi-Server Authentication Scheme for 5G Networks. IEEE Access 2024, 12, 49062–49077. [Google Scholar] [CrossRef]
- Taji, K.; Ghanimi, F. Enhancing Security and Privacy in Smart Agriculture: A Novel Homomorphic Signcryption System. Results Eng. 2024, 22, 102310. [Google Scholar] [CrossRef]
- Itoo, S.; Khan, A.A.; Ahmad, M.; Idrisi, M.J. A Secure and Privacy-Preserving Lightweight Authentication and Key Exchange Algorithm for Smart Agriculture Monitoring System. IEEE Access 2023, 11, 56875–56890. [Google Scholar] [CrossRef]
- Nyangaresi, V.O. Provably Secure Authentication Protocol for Traffic Exchanges in Unmanned Aerial Vehicles. High-Confid. Comput. 2023, 3, 100154. [Google Scholar] [CrossRef]
- Bahache, A.N.; Chikouche, N.; Mezrag, F. Authentication Schemes for Healthcare Applications Using Wireless Medical Sensor Networks: A Survey. SN Comput. Sci. 2022, 3, 382. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).