Cybersecurity in a Scalable Smart City Framework Using Blockchain and Federated Learning for Internet of Things (IoT)
Abstract
Highlights
- Implementation of blockchain enhances the security and scalability of smart city frameworks.
- Federated Learning enables efficient and privacy-preserving data sharing among IoT devices.
- The proposed framework significantly reduces the risk of data breaches in smart city infrastructures.
- Improved data privacy and security can foster greater adoption of IoT technologies in urban environments.
Abstract
1. Introduction
- Framework Design: The BFLIoT framework represents the first comprehensive integration of blockchain and federated learning, addressing the unique security and scalability challenges of smart city IoT systems. The framework’s security is underpinned by a foundational proof based on the intractability of the Discrete Logarithm (DL) problem, which demonstrates its robustness against sophisticated cyber threats.
- Comprehensive Performance Analysis: Extensive simulations are conducted to evaluate the framework’s performance across various smart city applications, focusing on key metrics of Quality of Service (QoS) such as throughput, reliability, and energy consumption. This analysis provides valuable insights into the practical viability of the BFLIoT framework in real-world scenarios.
- Scalable and Efficient Data Processing: The method optimizes the placement and operation of EC devices, enabling efficient local data processing and reducing the reliance on central servers. This scalability is crucial for handling the large data volumes typical of smart city environments, ensuring that the system maintains real-time processing capabilities.
- Advanced Anomaly Detection Framework: The framework includes a dynamic anomaly detection system that adapts to evolving data patterns. The globally refined model from FL enhances the accuracy of detecting irregularities and potential security threats, improving the overall security and reliability of smart city operations.
- Formal Security Verification: The BFLIoT protocol’s security is thoroughly verified using ProVerif, a tool for the formal verification of cryptographic protocols. This formal analysis confirms the framework’s resilience against a wide range of cyber threats, establishing a high level of confidence in its security architecture.
2. Literature Review
2.1. Evolution of IoT Security Challenges
2.2. Blockchain and AI in IoT Security: A Review of Recent Studies
2.3. Common Challenges and Strategic Gaps Identified across Studies
3. Problem Statement
3.1. BFLIoT Framework and Segmentation
- Privacy Preservation: By keeping data local to the IoT devices, FL significantly enhances privacy. Sensitive data, such as personal or public movement patterns, is never transmitted to a central server, reducing the risk of data breaches and enhancing trust in the system.
- Scalability: With thousands of IoT devices continuously generating data, centralized systems would face significant challenges in handling this volume of information. FL decentralizes computation, minimizing the need for extensive server resources and allowing the system to scale effectively in large smart city environments.
- Real-Time Anomaly Detection: The BFLIoT framework is designed to adapt to changing conditions within the city. FL facilitates real-time updates to anomaly detection models, allowing the system to continuously improve its ability to detect cyber threats or system failures without compromising security.
- Decentralized Data Storage and Integrity: Blockchain stores encrypted data and FL model updates in an immutable, distributed ledger. Each IoT device contributes to the ledger by adding blocks containing encrypted data or model parameters. The distributed nature of Blockchain ensures that no single point of failure exists, enhancing the system’s fault tolerance and security.
- Tamper-Resistant and Transparent Transactions: By using Blockchain, the BFLIoT framework guarantees that once data or model updates are recorded, they cannot be altered or tampered with. This immutability is critical for securing sensitive data and ensuring that any malicious attempt to manipulate the system would be detectable by the decentralized network of nodes.
- Secure Data Sharing through Smart Contracts: Blockchain’s smart contracts are leveraged to manage access control and automate data sharing across IoT devices. Smart contracts allow for automated execution of predefined rules, such as determining which entities can access certain data or model updates without relying on intermediaries. This automation not only ensures security but also improves system efficiency by reducing the need for manual intervention.
- Validation of FL Updates: Blockchain serves as the validation mechanism for FL model updates. Before updates are aggregated into the global model, they are verified and added to the Blockchain ledger, ensuring that only valid, secure contributions from authenticated devices are incorporated. This guarantees the trustworthiness of the learning process, preventing malicious data injections or model poisoning attacks.
3.2. Why Blockchain over Traditional Encryption (e.g., HTTPS)?
3.3. Mathematical Formulation for QoS in BFLIoT Systems
- : Represents the throughput of the system, typically measured as the amount of data processed per unit of time.
- : represents the summation of the absolute values of data processed, from to , where indexes each data transaction or piece of data processed, and is the total number of transactions or data pieces processed in the given period.
- : Represents the total period over which the throughput is measured. This could be in seconds, minutes, hours, etc., depending on the context of the measurement.
- stands for the system’s reliability over time, indicating the probability of failure-free operation throughout a specific period t.
- represents the failure rate of the system, which quantifies the frequency of failures per unit of time. A lower failure rate corresponds to higher reliability.
- denotes the latency, measured as the total time taken for a data transaction.
- represents the distance traveled by the data packet, which can be the physical distance between devices in an IoT environment.
- is the speed of the data transmission, which can be influenced by the medium of transmission (e.g., fiber optics, wireless) and the bandwidth of the network.
- accounts for the processing time required at each node the data packet encounters, including delays introduced by routing decisions, data processing, and any queuing that may occur within the network infrastructure or the blockchain system itself.
4. Proposed Method
- The choice of a bilinear map a pairing function over cryptographic groups and , along with the choice of a prime number , underpins the robustness of our encryption scheme, enabling secure interactions within the framework. Additionally, specifying four secure hash functions for distinct aspects of the encryption process further tailors our cryptographic measures to address diverse security requirements, ensuring comprehensive data protection across the IoT infrastructure.
- The allocation of hash functions within our cryptographic framework plays an important role in enhancing data security and integrity. Four secure hash functions are defined for their specific roles in the encryption process:
- ○
- maps binary strings to integers within , facilitating secure numerical operations.
- ○
- transforms binary strings into elements of the cryptographic group , ensuring that data can be securely embedded within this group.
- ○
- performs the inverse operation, converting group elements back into binary strings, which is essential for data retrieval and processing.
- ○
- is designed to maintain data integrity, providing a reliable mechanism for verifying the unaltered state of data throughout the encryption and decryption processes.
| Algorithm 1: Proposed Method for a single node |
| Input: Collection of IoT Devices D, Set of Edge Computing Devices EC, Data Authorization Center (DAC) Output: Securely processed data with high Quality of Service (QoS) 01: > Cryptographic Setup for DAC 02: if DAC. Setup Complete () == False then 03: DAC. Initialize Cryptographic Parameters() 04: for each hash Function in (H1, H2, H3, H4) do 05: DAC. Configure (hash Function) 06: end for 07: DAC. Generate Public Key () 08: end if 09: 10: > Data Processing for Each IoT Device (Single Node) 11: for each device in D do 12: if device. HasData () then 13: Raw Data = device. Collect Data () 14: Normalized Data = Normalize Data (Raw Data) 15: Encrypted Data = Encrypt Data(Normalized Data, DAC. PublicKey) 16: Blockchain. Store(Encrypted Data) 17: else 18: Continue 19: end if 20: end for 21: 22: > Integration and Secure Operation of Edge Computing Devices (EC) 23: for each EC_device in EC do 24: if EC_device. Is Registered With(DAC) == False then 25: ECID = EC_device. Generate Unique Identifier() 26: EC_device.Register(ECID, DAC) 27: end if 28: Key Pair = DAC. Generate Secure Key For (EC_device) 29: EC.Store Key Pair(Key Pair) 30: end for 31: 32: > Federated Learning on Encrypted Data 33: GM = Initialize Global Model() 34: for Round = 1 to Number Of Rounds do 35: Local Models = [] 36: for each EC_device in EC do 37: Encrypted Data = EC_device. Fetch Encrypted Data From Blockchain() 38: if EncryptedData != None then 39: Local Model = EC_device. TrainModel On Encrypted Data() 40: Local Models. Append (Local Model) 41: end if 42: end for 43: GM = Aggregate Models (Local Models) 44: end for 45: 46: > Secure Handling of Gradients 47: for each EC_device in EC do 48: Gradients = EC_device. Compute Encrypted Gradients() 49: if Gradients. Is Valid() then 50: Secure Gradients = Encrypt(Gradients, PublicKey_FL) 51: Blockchain. Store (Secure Gradients) 52: end if 53: end for 54: Aggregated Gradients = Aggregate Encrypted Gradients From Blockchain() 55: GM = Update Global Model (GM, Aggregated Gradients) 56: 57: > Anomaly Detection Framework 58: for each EC_device in EC do 59: Encrypted Data = EC_device. Fetch Encrypted Data From Blockchain() 60: Decrypted Data = Decrypt(Encrypted Data, EC_device. Private Key) 61: Anomalies = Detect Anomalies (Decrypted Data, GM) 62: EC_device. Report Anomalies(Anomalies) 63: end for 64: 65: > Consensus on Model Updates and Blockchain Integration 66: if Reach Consensus On (GM) then 67: Blockchain. Update Global Model(GM) 68: else 69: Log Error(“Consensus not reached”) 70: end if 71: 72: > Advanced Model Deployment and Data Decryption 73: for each EC_device in EC do 74: Deploy (GlobalModel_new, EC_device) 75: Encrypted Data = EC_device. Retrieve Encrypted Data() 76: if Verify Integrity (Encrypted Data) then 77: Decrypted Data = Decrypt (Encrypted Data, EC_device. Private Key) 78: EC_device. Process Data (Decrypted Data) 79: end if 80: end for |
5. Security Proof with Enhanced Mathematical Rigor
5.1. Encryption Scheme and Security
- Eventually, outputs a guess for the encryption of or . Since can simulate the encryption oracle without knowing (only using ), any advantage has in distinguishing the encryptions directly translates into ’s ability to compute .
- If succeeds with a non-negligible advantage, uses this advantage to solve the DL problem, contradicting our assumption that the DL problem is hard.
5.2. Security Analysis
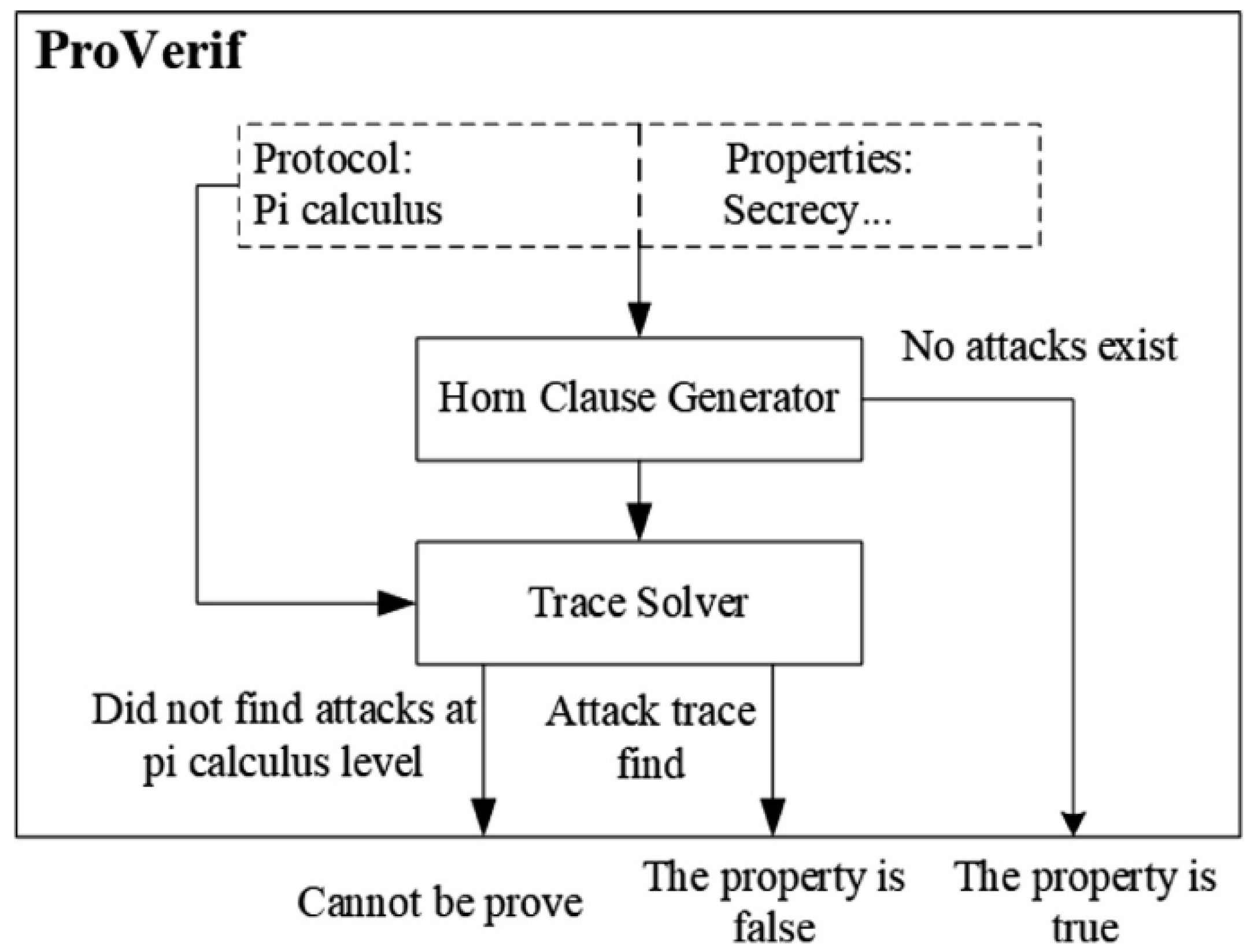
5.3. Formal Analysis Using ProVerif
- (1)
- Query not attacker(s) is true.
- (2)
- Query not attacker(lsk(i)) is true.
- (3)
- Query not attacker(lpk(i)) is true.
- (4)
- Query not attacker(ask(i)) is true.
- (5)
- Query not attacker(lsesb(i)) is true.
- (6)
- Query not attacker(lskb(i)) is true.
- (7)
- Query not attacker(m(i)) is true.
- (8)
- Non-interference RIDi is true.
- (9)
- Query inj-event(endES_Veri) ==> ==> inj-event(endSDi_Sig) is true.
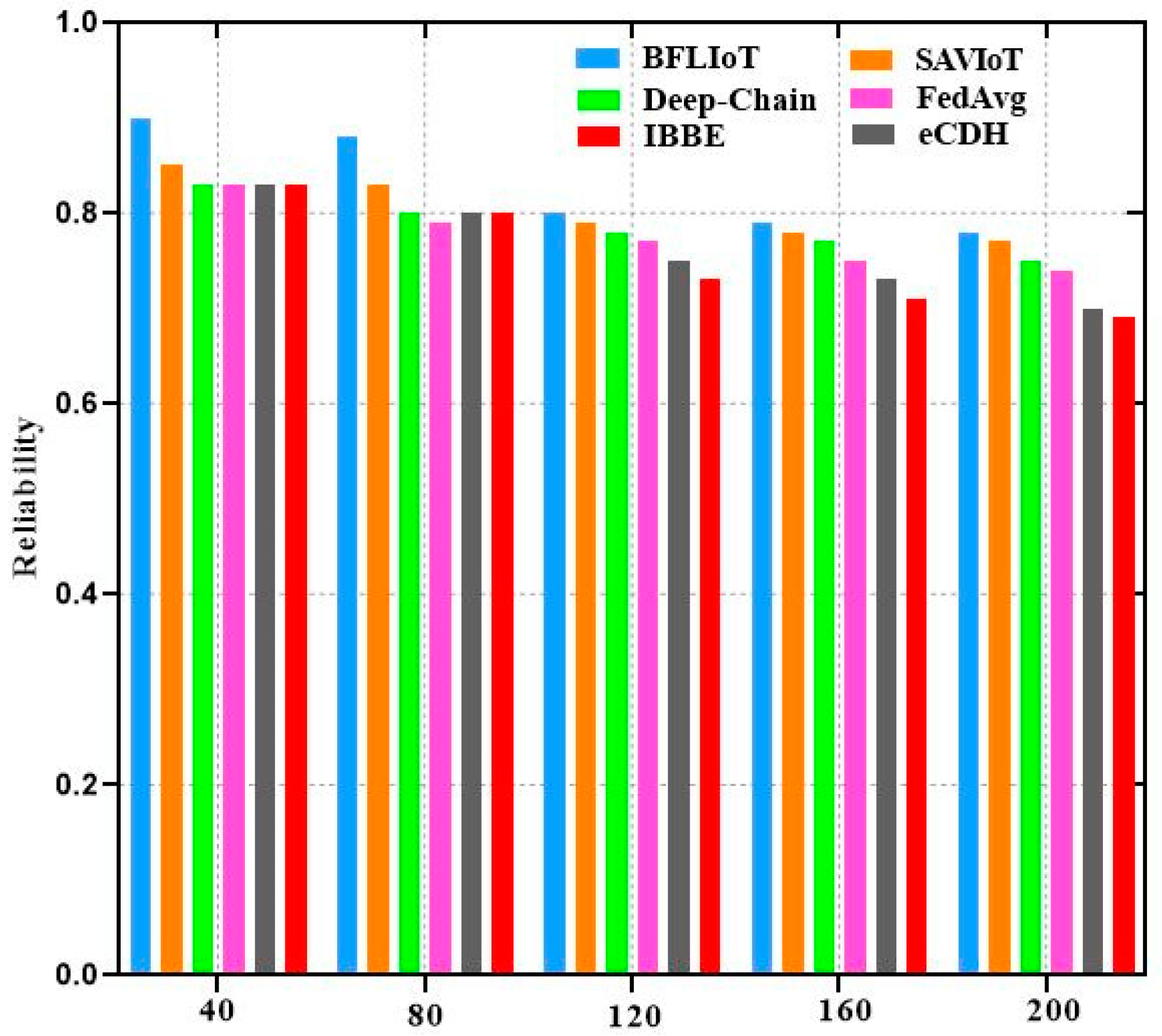
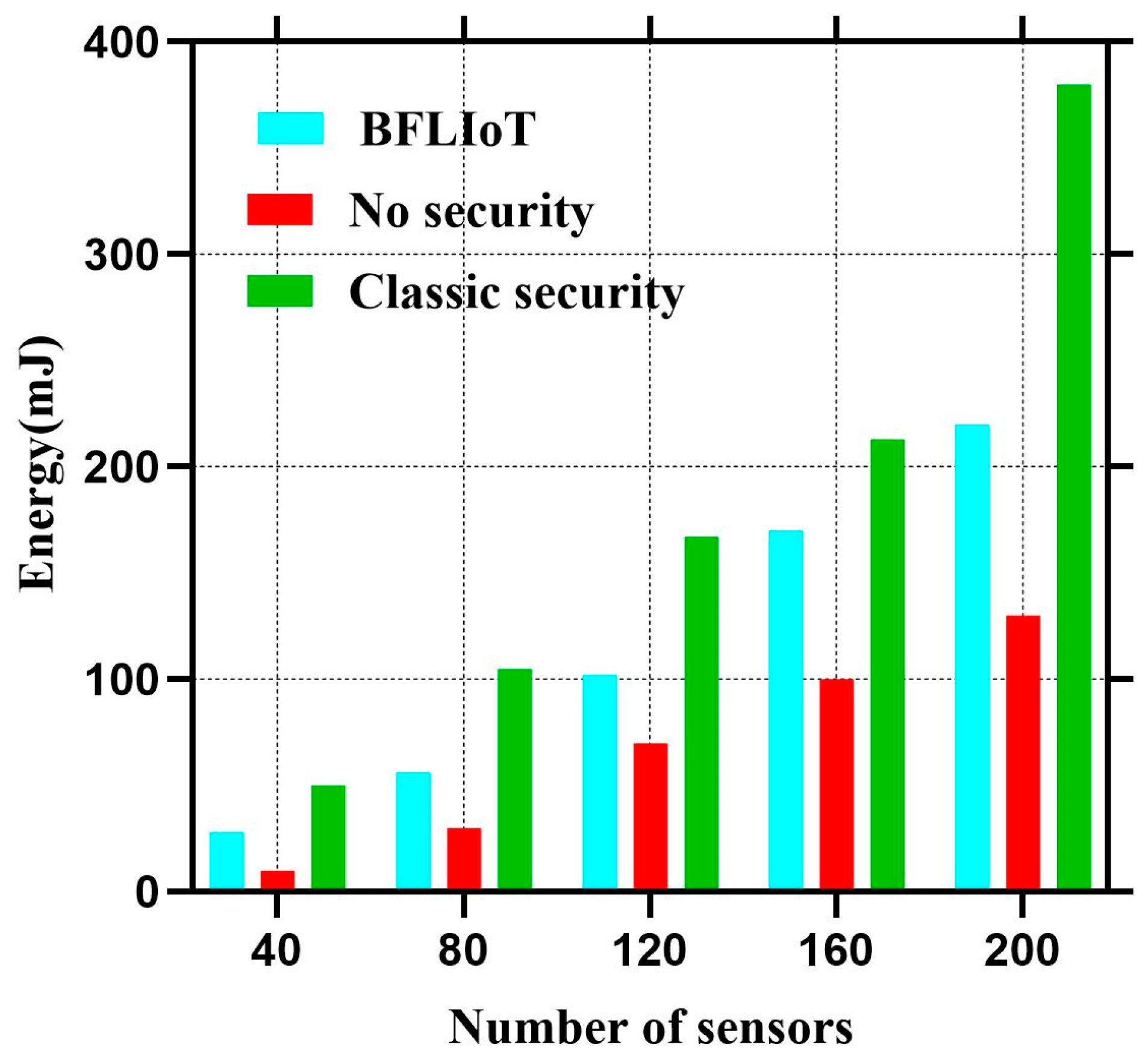
6. Performance Analysis
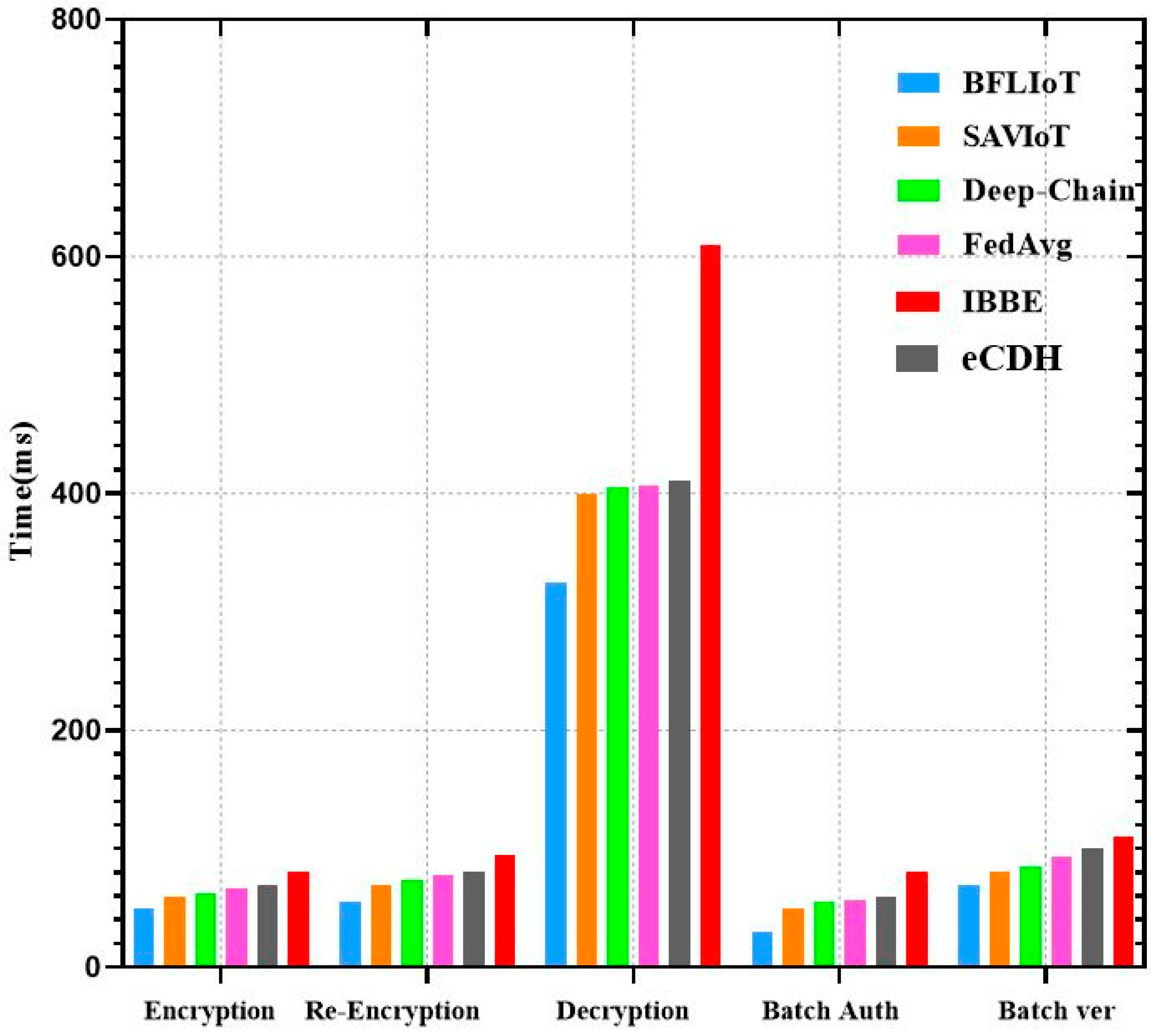
Performance Evaluation
- Encryption time is calculated as ms. This calculation includes the time to process six messages, perform basic encryption, hash six times, and authenticate twice.
- Re-encryption time = ms. Proxy re-encryption uses three base proxy operations, message processing, and two group theory-based multiplications.
- Decryption time is ms. Decryption involves multiple base proxy operations, message processing, message-to-proxy conversion, several group theory-based multiplications, hashing, and authentication steps. Here, n refers to the number of messages being decrypted, adding complexity to the process.
- Re-encryption time is ms. This process reduces the number of base proxy operations from three to two. It also adjusts encryption time and message processing to optimize the re-encryption time.
- Decryption time is ms. Decryption in this configuration is simplified, involving only two base proxy operations and one group theory-based multiplication. This results in a much faster decryption time compared to the initial configuration.
- Encryption time is ms. The encryption process is highly optimized, with minimal message processing, one hashing operation, and one group theory-based multiplication, resulting in a much faster encryption time.
- Re-encryption Time is ms. Although encryption is faster, re-encryption remains more complex, involving two base proxy operations, three message processing steps, two encryption operations, one hashing operation, one authentication step, and two group theory-based multiplications.
- Decryption time is ms.
- Encryption time = ms. Encryption becomes slower, possibly due to increased message size or processing demands.
- Re-encryption time is ms.
- Decryption time is ms.
- Re-encryption time is ms. Despite reductions in base proxy operations, re-encryption remains slow.
- Decryption time is ms.
- Encryption time is ms.
- Re-encryption time is ms,
- Decryption time is ms.
- Encryption time is calculated as ms.
- Re-encryption time is ms.
- Decryption time is ms.
7. Conclusions and Future Work
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Appendix A
| Notation | Description |
|---|---|
| Set of feature vectors from IoT devices, used to extract relevant information for security analysis. | |
| Feature vector for the i-th device, encompassing data points like device behavior and network interactions. | |
| Set of predefined categories representing various potential security statuses of the devices. | |
| Classification model mapping feature vectors X to categories Y, vital for determining security threat levels | |
| The category assigned to the i-th device’s data, indicating the security status as determined by model f | |
| Parameters of the classification model, are tuned to optimize threat detection accuracy. | |
| Cross-entropy loss function for classification, measuring the model’s performance in accurately classifying device data. | |
| A binary indicator if category j is the correct classification for observation i, is used for training accuracy. | |
| Predicted probability that i belongs to category j, indicating the likelihood of each security status. | |
| Total number of IoT devices represented in the dataset, influencing the model’s complexity and scalability | |
| Total number of security categories, which define the granularity of threat assessment. | |
| Segments of the dataset, each defined by unique criteria to enhance model learning and detection capabilities. | |
| Segmentation function that assigns data points to segments based on their characteristics, improving model efficiency. | |
| Segment containing data points categorized under security status j, used for focused analysis. | |
| The function g serves as the segmentation function, assigning each device’s feature vector to a specific segment which groups data points based on similar characteristics such as behavior, security risk levels, or operational patterns. | |
| ) | Intra-segment variance for segment indicating the consistency of data within a segment. |
| Mean of data points within segment S_j, helping in normalization and comparison of segments. | |
| p | P represents the total number of segments into which the dataset is divided. |
| The overall mean of the dataset provides a baseline for comparing segment deviations. | |
| Updated model parameters after iteration t+1, reflecting learning and adaptation to new data. | |
| Learning rate used in the optimization algorithm, balancing speed, and accuracy of convergence. | |
| at iteration t, guiding model updates. |
| Notation | Description |
|---|---|
| Normalized data ensures uniform scale across IoT device inputs, crucial for accurate traffic and environmental analysis. | |
| Represents the mean of IoT device data, essential for assessing average traffic conditions or environmental quality. | |
| Standard deviation, indicating variability in IoT data, is useful for detecting anomalies in traffic or environmental conditions. | |
| A bilinear map crucial for secure multi-party computations in traffic and environmental data sharing among IoT devices. | |
| Cryptographic groups used for secure data operations, ensuring that traffic and environmental data remain tamper-proof. | |
| Prime number defining the order of cryptographic groups, foundational for the security parameters of IoT data exchanges. | |
| . Hash function that securely maps device identifiers to cryptographic values, protecting device identity in a smart city network. | |
| refers to the set of all nonzero integers modulo q. In cryptographic terms, this represents the multiplicative group of integers modulo q excluding zero. | |
| . Hash function for securely embedding IoT data within cryptographic groups, vital for preserving data integrity. | |
| back into binary strings. Converts group elements back to strings, facilitating the secure retrieval of encrypted traffic and environmental data. | |
| Hash function used for verifying data integrity. Ensures data integrity by verifying that traffic and environmental data have not been altered post-encryption. | |
| Public key used for encryption and signature verification. Public key for encrypting IoT data, allowing secure data exchange across the smart city network. | |
| . Generator of the cryptographic group, fundamental to the creation and management of encryption keys in IoT security. | |
| , used in public key generation. Secret key component in cryptographic operations, critical for maintaining secure communication between IoT devices. | |
| Cipher text of encrypted data. | |
| Unique identifier of an IoT device, used for secure network authentication. Unique identifier for each IoT device, ensuring secure and authenticated device operations in smart city infrastructure. | |
| Long secret key generated securely for each device through a random process. Randomly generated long secret key for each IoT device, enhancing the security of device-specific operations. | |
| Long-term public key derived from the long sec ret key using generator g. Used in securing device communications within the IoT network. | |
| is securely stored in the blockchain. Ensuring immutable recording of traffic and environmental data. | |
| New blockchain block created from the hash of the previous block, a critical step for maintaining a secure, verifiable record of IoT data transactions. | |
| Method for IoT devices to securely access encrypted data from the blockchain, crucial for Edge Computing (EC). | |
| Represents the IoT data post-decryption, used for actionable insights into traffic flow and environmental conditions. | |
| by the IoT device using its long secret key. | |
| Measures the change in data flow, critical for monitoring variations in traffic density or environmental sensor outputs. | |
| Rate of change of data, important for understanding trends in traffic congestion and environmental conditions over time | |
| , used in the context of data flow integration. Integral used to ensure the completeness and integrity of data paths in the IoT network. | |
| , typically representing data flow or force fields. Represents forces or flows in vector fields, useful in simulations of traffic patterns and environmental dispersion models | |
| . | |
| Position vector of the IoT device in the network. Essential for optimizing sensor placements and ensuring effective data coverage in a smart city. | |
| Symbol indicating proportionality, used in algorithms that adjust IoT device operations based on traffic and environmental data scales. | |
| Position vector of the sensor relative to the IoT device. Sensor position vectors, key to strategically deploying environmental and traffic monitoring sensors for optimal data collection. | |
| Denotes perpendicularity between vectors, used in optimal path calculations. Indicates perpendicularity in data transmission paths, crucial for minimizing interference and maximizing the efficiency of data flow in IoT networks. | |
| Optimal direction vector for data transmission between IoT device and sensor. | |
| , ensuring confidentiality and integrity. | |
| , used in cryptographic operations. | |
| . | |
| . Encrypted communication, vital for maintaining data confidentiality in IoT interactions. | |
| during a session. | |
| t stands for timestamp. Seq: Indicates that this timestamp is part of a sequence, which could be used to order events, messages, or data packets chronologically. | |
| for enhanced security. | |
| Encrypted Data, key for protecting sensitive information in traffic and environmental monitoring systems. | |
| Represents the encryption function. The subscript k indicates that this function uses the cryptographic key k to perform the encryption. | |
| This is the batch of data that is being encrypted. In the context of IoT systems or any large-scale data processing environment like a smart city BFLIoT system, data is often processed in batches for efficiency. | |
| Hash of encrypted data, providing a unique fingerprint for verification without revealing content. Providing a checksum to verify data integrity before decryption in IoT systems. | |
| Initial commitment in cryptographic protocols, ensuring integrity and non-repudiation. | |
| , typically in a learning or optimization context. Updated model parameters in machine learning algorithms, essential for adapting traffic control and environmental prediction models to new data. | |
| Learning rate, controlling the update magnitude in optimization processes. Determining the speed and effectiveness of updates to IoT data processing models. | |
| , calculated on decrypted data. Key for refining machine learning models based on secure IoT data. | |
| . Critical for enhancing the collaborative intelligence of IoT devices in smart city applications. | |
| -th device, contributing to the overall model update. | |
| Set of all participating EC devices in the federated learning network. Central to distributed data processing and decision-making in smart cities. | |
| Encrypted version of the aggregated model parameters for secure transmission. | |
| devices, representing data aggregation while preserving privacy. Maintaining data privacy while enabling comprehensive analysis in federated learning. | |
| Optimal model parameters obtained from minimizing integrated loss across aggregated data. | |
| Integral of the loss function over the disjoint union of datasets, indicating continuous optimization. | |
| -th device, derived from local data and model parameters. | |
| . | |
| Public key used in federated learning for encrypting data, ensuring participant data confidentiality. | |
| Total number of devices participating in the federated learning network, indicative of the scale of collaborative data processing in smart city infrastructure. | |
| Used to average aggregated values across all devices, essential for balancing model updates in federated learning systems. | |
| . Securing detailed traffic and environmental data during collaborative learning processes. | |
| Aggregated encrypted gradients, averaged across all participating devices. Averaged to update global models without compromising the privacy of individual IoT data inputs. | |
| Updated global model parameters after applying aggregated gradient changes. | |
| Change to be applied to the global model, based on the decrypted aggregated gradients. | |
| Encrypted updated global model, ready for secure transmission to devices. | |
| Decrypted updated global model, ready for deployment on edge devices. | |
| Secret key of a specific EC device, used to decrypt transmitted data. | |
| Public key associated with an EC device, used for encrypting data before transmission. | |
| Hash function applied to normalized data, part of security checks for anomaly detection. | |
| . Crucial for identifying deviations in traffic patterns and environmental conditions in real-time. | |
| . | |
| Threshold for classifying data points in anomaly detection, adjusted dynamically. | |
| Updated dynamic threshold for anomaly detection based on statistical measures of detected anomalies. Recalibrated to maintain accuracy as traffic and environmental conditions evolve. | |
| Mean of detected anomalies, used in dynamic threshold calculation. | |
| Standard deviation of detected anomalies, used in dynamic threshold calculation. | |
| . | |
| Encrypted local model update of the i-th device, using public key . Ensuring secure and personalized adaptation to localized data conditions. | |
| Decryption of encrypted gradients, part of the global model update aggregation. | |
| Aggregated model updates from participating devices, prior to consensus validation. | |
| when computing an average, where K is the total number of items over which the sum is calculated. | |
| Blockchain record after consensus validation of the aggregated updates. Ensuring that all device contributions are authenticated and the model update is secure | |
| Updated blockchain record incorporating the new validated updates. | |
| Broadcasted new global model state, synchronized across all network participants. | |
| , across the entire network. | |
| Indicates that the ciphertext has been encrypted, specifying the state of the data as being securely encoded. | |
| k Represents a cryptographic key, which is used for encryption, and decryption. Indexed: Implies that the key is part of a collection or series of keys, each uniquely identified by an index. | |
| represents a specific timestamp in data communication contexts. | |
| SK Stands for “Secret Key,” which is used for decrypting data that has been encrypted with the corresponding Public Key. bi serves as an identifier and index for a particular device. | |
| t Stands for timestamp. Esb stands for a specific protocol. | |
| C Stands for ciphertext which is the data in its encrypted form. Dec Indicates that the ciphertext has been decrypted, specifying the state of the data as having been transformed from its secure, encoded format to its plaintext format. | |
| T stands for Transformation. K: Represents a Key used in the cryptographic operation. b i user b and has an identifier i. |
| Represents the adversary in the cryptographic proof, trying to compromise the system. Testing the system’s resilience against potential security breaches. | |
| The challenger in cryptographic games simulates the protocol to validate the security measures of the IoT system. | |
| A secret value selected uniformly at random from , used as the exponent in the key generation to create the public key. Used in the cryptographic key generation process to secure IoT device communications. | |
| The public key in the BFLIoT system, derived as , where is a generator of the group . | |
| Represents a message that is an element of , involved in the encryption process. | |
| A random value is chosen uniformly from for each encryption process. | |
| The ciphertext resulting from the encryption scheme combines a power of and the message masked with a hash output. | |
| A cryptographic hash function is used as a random oracle, ensuring the randomness of the hash output used in the encryption. | |
| An algorithm constructed to solve the DL problem using the adversary’s ability to break the encryption scheme. | |
| Local gradient from a device in the federated learning process. | |
| Noise-adjusted gradient ensuring -differential privacy by adding Gaussian noise . | |
| HF | The cryptographic hash function used in the PoW mechanism within the blockchain integration. |
| Nonce in the PoW, a number that miners adjust to solve the hashing challenge. | |
| Gaussian noise was added to the local gradient to ensure differential privacy. |
References
- Sefati, S.S.; Arasteh, B.; Halunga, S.; Fratu, O.; Bouyer, A. Meet User’s Service Requirements in Smart Cities Using Recurrent Neural Networks and Optimization Algorithm. IEEE Internet Things J. 2023, 10, 22256–22269. [Google Scholar] [CrossRef]
- Sefati, S.S.; Halunga, S. Ultra-reliability and low-latency communications on the internet of things based on 5G network: Literature review, classification, and future research view. Trans. Emerg. Telecommun. Technol. 2023, 34, e4770. [Google Scholar] [CrossRef]
- Ullah, A.; Ahmad, J.; Arif, M.; Javed, A.; Alazab, M.; Khan, M.S. Smart Cities: The Role of Internet of Things and Machine Learning in Realizing a Data-Centric Smart Environment. Complex Intell. Syst. 2024, 10, 1607–1637. [Google Scholar] [CrossRef]
- Miranda, R.; Filippoupolitis, A.; Oliff, W. Revolutionising the Quality of Life: The Role of Real-Time Sensing in Smart Cities. Electronics 2024, 13, 550. [Google Scholar] [CrossRef]
- Farooq, M.S.; Riaz, S.; Abid, A.; Abid, K.; Naeem, M. A Survey on the Role of IoT in Agriculture for the Implementation of Smart Farming. IEEE Access 2019, 7, 156237–156271. [Google Scholar] [CrossRef]
- Sefati, S.S.; Halunga, S. Mobile sink assisted data gathering for URLLC in IoT using a fuzzy logic system. In Proceedings of the 2022 IEEE International Black Sea Conference on Communications and Networking (BlackSeaCom), Sofia, Bulgaria, 6–9 June 2022; IEEE: Piscataway, NJ, USA, 2022; pp. 379–384. [Google Scholar]
- Javed, A.R.; Usman, M.; Raza, M.; Khan, A.A.; Noor, K.; Din, S. Future Smart Cities: Requirements, Emerging Technologies, Applications, Challenges, and Future Aspects. Cities 2022, 129, 103794. [Google Scholar] [CrossRef]
- Alfandi, O.; Patel, A.; Santos, A.; Bennett, F. A Survey on Boosting IoT Security and Privacy through Blockchain: Exploration, Requirements, and Open Issues. Clust. Comput. 2021, 24, 37–55. [Google Scholar] [CrossRef]
- Farahani, B.; Firouzi, F.; Luecking, M. The Convergence of IoT and Distributed Ledger Technologies (DLT): Opportunities, Challenges, and Solutions. J. Netw. Comput. Appl. 2021, 177, 102936. [Google Scholar] [CrossRef]
- Qu, Y.; Uddin, M.P.; Gan, C.; Xiang, Y.; Gao, L.; Yearwood, J. Blockchain-enabled federated learning: A survey. ACM Comput. Surv. 2022, 55, 1–35. [Google Scholar] [CrossRef]
- Sefati, S.S.; Haq, A.U.; Craciunescu, R.; Halunga, S.; Mihovska, A.; Fratu, O. A Comprehensive Survey on Resource Management in 6G Network Based on Internet of Things. IEEE Access 2024, 12, 113741–113784. [Google Scholar] [CrossRef]
- Henry, R.; Herzberg, A.; Kate, A. Blockchain Access Privacy: Challenges and Directions. IEEE Secur. Priv. 2018, 16, 38–45. [Google Scholar] [CrossRef]
- Sefati, S.S.; Halunga, S. Data forwarding to Fog with guaranteed fault tolerance in Internet of Things (IoT). In Proceedings of the 2022 14th International Conference on Communications (COMM), Bucharest, Romania, 16–18 June 2022; IEEE: Piscataway, NJ, USA, 2022; pp. 1–5. [Google Scholar]
- Omar, A.S.; Basir, O. Identity Management in IoT Networks Using Blockchain and Smart Contracts. In Proceedings of the 2018 IEEE International Conference on Internet of Things (iThings) and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom) and IEEE Smart Data (SmartData), Halifax, NS, Canada, 30 July–3 August 2018; IEEE: Piscataway, NJ, USA, 2018. [Google Scholar]
- Kharche, A.; Badholia, S.; Upadhyay, R.K. Implementation of Blockchain Technology in Integrated IoT Networks for Constructing Scalable ITS Systems in India. Blockchain Res. Appl. 2024, 5, 100188. [Google Scholar] [CrossRef]
- Sisi, Z.; Souri, A. Blockchain Technology for Energy-Aware Mobile Crowd Sensing Approaches in Internet of Things. Trans. Emerg. Telecommun. Technol. 2024, 35, e4217. [Google Scholar] [CrossRef]
- Jyoti, A.; Yadav, V.; Prakash, A.; Kumar Jha, S.; Rahul, M. Blockchain for Big Data: Approaches, Opportunities and Future Directions. Recent Adv. Electr. Electron. Eng. (Former. Recent Pat. Electr. Electron. Eng.) 2024, 17, 229–243. [Google Scholar] [CrossRef]
- Malik, K.R.; Samad, A.; Anjum, A.; Saeed, Y.; Han, K. A Methodology for Real-Time Data Sustainability in Smart City: Towards Inferencing and Analytics for Big-Data. Sustain. Cities Soc. 2018, 39, 548–556. [Google Scholar] [CrossRef]
- Sefati, S.; Mousavinasab, M.; Zareh Farkhady, R. Load balancing in cloud computing environment using the Grey wolf optimization algorithm based on the reliability: Performance evaluation. J. Supercomput. 2022, 78, 18–42. [Google Scholar] [CrossRef]
- Wan, S.; Chen, Z.; Lin, K.; Wang, X.; Wu, Y.; Di, Y. To Smart City: Public Safety Network Design for Emergency. IEEE Access 2017, 6, 1451–1460. [Google Scholar] [CrossRef]
- Mahesh, B. Machine Learning Algorithms-A Review. Int. J. Sci. Res. (IJSR) 2020, 9, 381–386. [Google Scholar] [CrossRef]
- Aldoseri, A.; Al-Khalifa, K.N.; Hamouda, A.M. AI-Powered Innovation in Digital Transformation: Key Pillars and Industry Impact. Sustainability 2024, 16, 1790. [Google Scholar] [CrossRef]
- He, P.; Zhou, Y.; Qin, X. A Survey on Energy-Aware Security Mechanisms for the Internet of Things. Future Internet 2024, 16, 128. [Google Scholar] [CrossRef]
- Amoo, O.O.; Shithili, S.; Ramanujan, R. Cybersecurity Threats in the Age of IoT: A Review of Protective Measures. Int. J. Sci. Res. Arch. 2024, 11, 1304–1310. [Google Scholar] [CrossRef]
- Kvak, K.; Straka, M. The Use of the Internet of Things in the Distribution Logistics of Consumables. Appl. Sci. 2024, 14, 3263. [Google Scholar] [CrossRef]
- Merlec, M.M.; In, H.P. SC-CAAC: A Smart Contract-Based Context-Aware Access Control Scheme for Blockchain-Enabled IoT Systems. IEEE Internet Things J. 2024, 11, 19866–19881. [Google Scholar] [CrossRef]
- CheSuh, L.N. Improve Quality of Service for the Internet of Things Using Blockchain & Machine Learning Algorithms. Internet Things 2024, 26, 101123. [Google Scholar]
- Kiran, M. Blockchain Based Secure Ownership Transfer Protocol for Smart Objects in the Internet of Things. Internet Things 2024, 25, 101002. [Google Scholar]
- Li, K. Privacy-Preserving Scheme with Bidirectional Option for Blockchain-Enhanced Logistics Internet of Things. IEEE Internet Things J. 2024, 11, 20562–20574. [Google Scholar] [CrossRef]
- Vishwakarma, L.; Das, D. BLISS: Blockchain-Based Integrated Security System for Internet of Things (IoT) Applications. Int. J. Inf. Secur. 2024, 23, 1649–1665. [Google Scholar] [CrossRef]
- Singh, D.; Dwivedi, R.K. Designing Blockchain Based Secure Autonomous Vehicular Internet of Things (IoT) Architecture with Efficient Smart Contracts. Int. J. Inf. Technol. 2024, 1–17. [Google Scholar] [CrossRef]
- Khan, A.A. Data Security in Healthcare Industrial Internet of Things with Blockchain. IEEE Sens. J. 2023, 23, 25144–25151. [Google Scholar] [CrossRef]
- Xiong, H.; Wu, Y.; Jin, C.; Kumari, S. Efficient and privacy-preserving authentication protocol for heterogeneous systems in IIoT. IEEE Internet Things J. 2020, 7, 11713–11724. [Google Scholar] [CrossRef]
- Zhong, H.; Zhang, S.; Cui, J.; Wei, L.; Liu, L. Broadcast encryption scheme for V2I communication in VANETs. IEEE Trans. Veh. Technol. 2021, 71, 2749–2760. [Google Scholar] [CrossRef]
- Gervais, A. On the Security and Performance of Proof of Work Blockchains. In Proceedings of the 2016 ACM SIGSAC Conference on Computer and Communications Security, Vienna, Austria, 24–28 October 2016. [Google Scholar]
- Sefati, S.S.; Fartu, O.; Nor, A.M.; Halunga, S. Enhancing Internet of Things Security and Efficiency: Anomaly Detection via Proof of Stake Blockchain Techniques. In Proceedings of the 2024 International Conference on Artificial Intelligence in Information and Communication (ICAIIC), Osaka, Japan, 19–22 February 2024; IEEE: Piscataway, NJ, USA, 2024; pp. 591–595. [Google Scholar]
- Iqbal, M.A. A Review on Internet of Things (IoT): Security and Privacy Requirements and the Solution Approaches. Glob. J. Comput. Sci. Technol. 2016, 16, 1–9. [Google Scholar]
- Datta, A.; Halpern, J.Y.; Mitchell, J.C.; Roy, A.; Sen, S. A symbolic logic with concrete bounds for cryptographic protocols. arXiv 2015, arXiv:1511.07536. [Google Scholar]
- Wang, J. Game-Based Low Complexity and Near Optimal Task Offloading for Mobile Blockchain Systems. IEEE Trans. Cloud Comput. 2024, 12, 539–549. [Google Scholar] [CrossRef]
- Benrebbouh, C.; Mansouri, H.; Cherbal, S.; Pathan AS, K. Enhanced secure and efficient mutual authentication protocol in iot-based energy internet using blockchain. Peer-to-Peer Netw. Appl. 2024, 17, 68–88. [Google Scholar] [CrossRef]

| Reference | Prior Studies | Advantages of Prior Studies | Disadvantages of Prior Studies | BFLIoT Contribution |
|---|---|---|---|---|
| [26] | SC-CAAC for Blockchain-IoT | Enhances security and privacy Promotes trust | Complex deployment Scalability and cost issues. | BFLIoT integrates federated learning for scalability and edge computing to reduce complexity. |
| [27] | Blockchain and ML for IoT QoS | Improves security and QoS Utilizes ML analytics. | Scalability issues. High computational demands. | BFLIoT optimizes energy efficiency and scalability through distributed edge computing and lightweight ML models. |
| [28] | OTP with PUF and blockchain | Secure flexible ownership transfer | PUF complexity. Scalability evolving threat challenges. | BFLIoT avoids hardware-based complexity by using cryptographic methods for secure and scalable data management. |
| [29] | PB-IoT for logistics | Enhances privacy; Supports humane services. | Integration complexity. High computational needs. | BFLIoT simplifies integration with a unified blockchain and federated learning model, reducing computational load. |
| [30] | BLISS for IoT | Improves cybersecurity; efficient mechanisms. | Scalability and latency in large network optimization are needed. | BFLIoT addresses latency by distributing processing across edge devices, ensuring real-time performance. |
| [31] | Secure AV IoT Architecture SAVIoT | Decentralized data sharing; improves safety. | Low scalability in AV networks. High resource demands. | BFLIoT’s decentralized architecture handles larger networks efficiently, improving scalability and reducing latency. |
| [32] | BHIIoT for e-healthcare | Enhances data security and scalable. | Integration complexity; needs extensive evaluation. | BFLIoT’s lightweight and scalable design simplifies deployment and supports real-time healthcare applications. |
| [33] | Computational Diffie-Hellman (eCDH) | Ensures secure communication between heterogeneous cryptosystems, low computation cost, and reduced communication overhead. | Extra computation cost due to cross-domain communication. | BFLIoT’s recommend a low cost algorithm |
| [34] | Identity-Based Broadcast Encryption (IBBE) with Proxy Server for VANETs | Reduces encryption redundancy, improves communication efficiency, lowers decryption cost for new vehicles. | Complexity added by using a proxy server, introducing extra computational overhead | BFLIoT’s reduces encryption redundancy in one-to-many communication |
| Criteria | Proposed Method | SAVIoT | eCDH | IBBE | FedAvg | DeepChain |
|---|---|---|---|---|---|---|
| Confidentiality of Data Transmission and Storage | ✓ | × | ✓ | ✓ | ✓ | ✓ |
| Robust Access Control Mechanism | ✓ | ✓ | × | ✓ | ✓ | ✓ |
| Anonymity Through Pseudonyms | ✓ | × | × | × | × | × |
| Unlinkability of Device Requests | ✓ | × | × | × | × | × |
| Replay Attack Resistance | ✓ | × | ✓ | × | ✓ | ✓ |
| Modification Attack Resistance | ✓ | ✓ | × | ✓ | × | ✓ |
| Impersonation Attack Resistance | ✓ | × | ✓ | ✓ | ✓ | ✓ |
| Parameters | Description |
|---|---|
| Deployment area | |
| Number of users | 2 |
| Number of the cloud server | 1 |
| Number of sensors | 40, 80, 120, 160, 200 |
| Communication range of cloud server | 2000 m |
| Communication range of sensors | 20 m |
| Simulation time | 2400 s |
| Cryptographic Library | VC++ 6.0 with Pairing-Based Cryptography (PBC) library |
| Security Standard | 1024-bit RSA encryption |
| Parameters | Description |
|---|---|
| Computational cost for hash functions, essential for data integrity, digital signatures, random number generation, and hash tables. | |
| The computational cost for bilinear pairing operations is used in advanced cryptographic systems like identity-based encryption and zero-knowledge proofs. | |
| , a group on a supersingular elliptic curve, crucial for frequent cryptographic operations. | |
| , another group used for various cryptographic operations in different settings. | |
| The computational cost for symmetric encryption/decryption, where the same key encrypts and decrypts data, is noted for its efficiency. |
| Metric | BFLIoT | SAVIoT | DeepChain | FedAvg | eCDH | IBBE |
|---|---|---|---|---|---|---|
| Moderate Rate Throughput | 326.2 | 208.3 | 180.2 | 170.1 | 148.7 | 98.9 |
| High-Rate Throughput | 3208.2 | 2015.4 | 1700.3 | 1600.5 | 1583.9 | 1024.1 |
| Throughput Completion Rate (Moderate, %) | 99.330 | 99.045 | 98.972 | 98.914 | 98.867 | 98.700 |
| Throughput Completion Rate (High, %) | 99.997 | 99.985 | 99.962 | 99.960 | 99.956 | 99.961 |
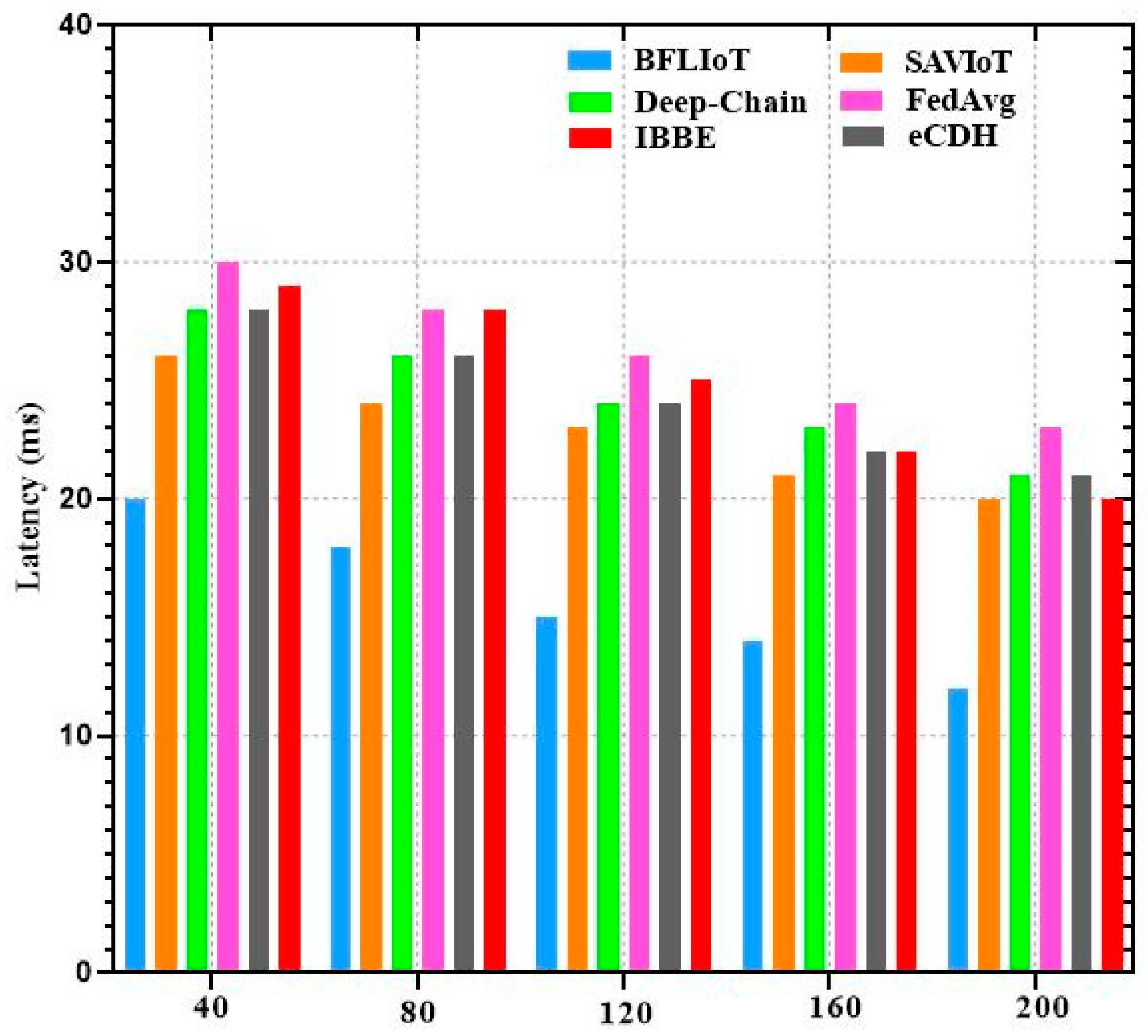
| Latency for Main Operation (Seconds) | 0.069 | 0.082 | 0.087 | 0.090 | 0.095 | 0.120 |
| Notation | Description |
|---|---|
| Encrypt a message. | |
| Re-encrypt a message using proxy re-encryption | |
| Time to process a message | |
| Basic encryption time | |
| Hashing time | |
| Authentication time | |
| Base proxy re-encryption time | |
| Message to proxy conversion time | |
| Group theory-based multiplication time |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Sefati, S.S.; Craciunescu, R.; Arasteh, B.; Halunga, S.; Fratu, O.; Tal, I. Cybersecurity in a Scalable Smart City Framework Using Blockchain and Federated Learning for Internet of Things (IoT). Smart Cities 2024, 7, 2802-2841. https://doi.org/10.3390/smartcities7050109
Sefati SS, Craciunescu R, Arasteh B, Halunga S, Fratu O, Tal I. Cybersecurity in a Scalable Smart City Framework Using Blockchain and Federated Learning for Internet of Things (IoT). Smart Cities. 2024; 7(5):2802-2841. https://doi.org/10.3390/smartcities7050109
Chicago/Turabian StyleSefati, Seyed Salar, Razvan Craciunescu, Bahman Arasteh, Simona Halunga, Octavian Fratu, and Irina Tal. 2024. "Cybersecurity in a Scalable Smart City Framework Using Blockchain and Federated Learning for Internet of Things (IoT)" Smart Cities 7, no. 5: 2802-2841. https://doi.org/10.3390/smartcities7050109
APA StyleSefati, S. S., Craciunescu, R., Arasteh, B., Halunga, S., Fratu, O., & Tal, I. (2024). Cybersecurity in a Scalable Smart City Framework Using Blockchain and Federated Learning for Internet of Things (IoT). Smart Cities, 7(5), 2802-2841. https://doi.org/10.3390/smartcities7050109











