Review of Authentication, Blockchain, Driver ID Systems, Economic Aspects, and Communication Technologies in DWC for EVs in Smart Cities Applications
Abstract
:Highlights
- Provides insights on fast, lightweight authentication and highlights how blockchain enhances security, privacy, and efficiency in IoV for DWC systems.
- Provides insights into driver identification for EV safety and comfort, and analyzes the economic viability of DWC for the EV ecosystem.
Abstract
1. Introduction
- The manuscript explores the integration of DWC technology for EV, particularly focusing on critical components like authentication techniques, blockchain applications, driver identification systems, and communication technologies.
- The study emphasizes the importance of fast and lightweight authentication systems for secure access to the DWC infrastructure, along with blockchain’s role in decentralizing and securing vehicular networks to improve privacy and efficiency within the IoV architecture.
- The economic aspects of implementing DWC are thoroughly evaluated, offering insights into its feasibility, cost implications, and potential impact on the broader EV ecosystem.
- By providing a comprehensive analysis of current technologies and challenges, the manuscript offers valuable guidance for advancing the DWC infrastructure and integrating it into smart city applications.
2. Dynamic Charging Technology
2.1. DWC System and Charging Demand Estimation of EVs
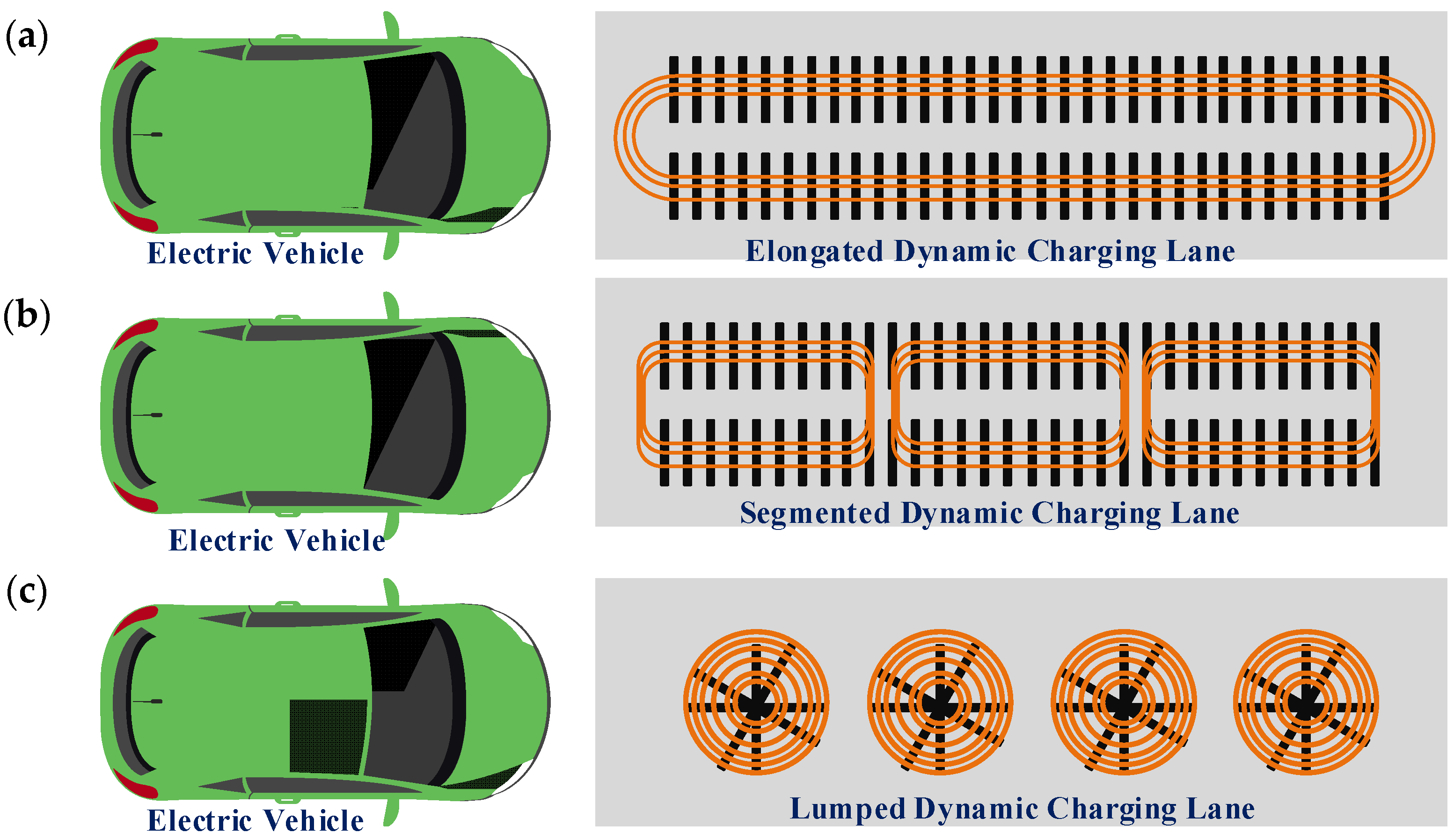
2.2. Structure of Dynamic Wireless Charging
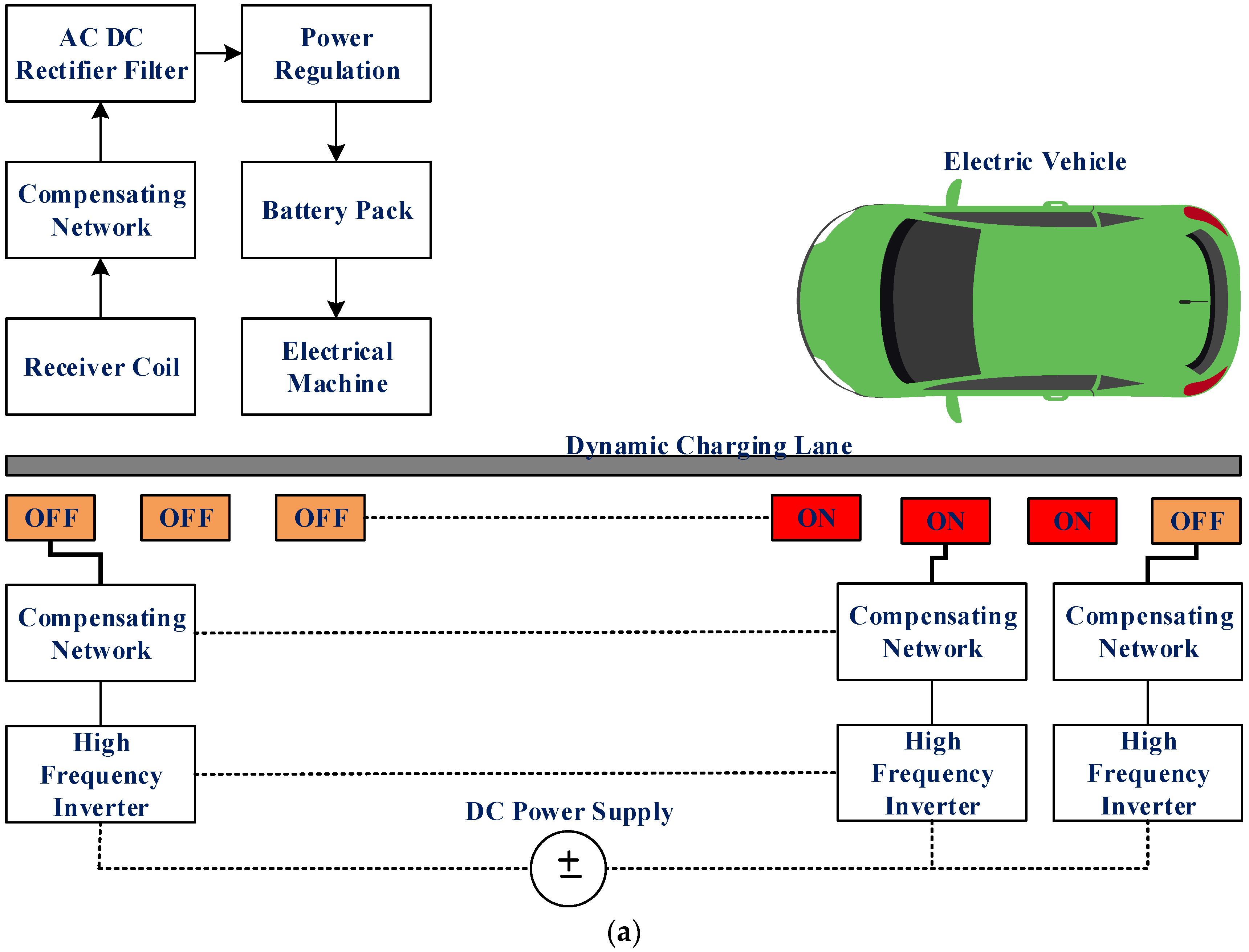
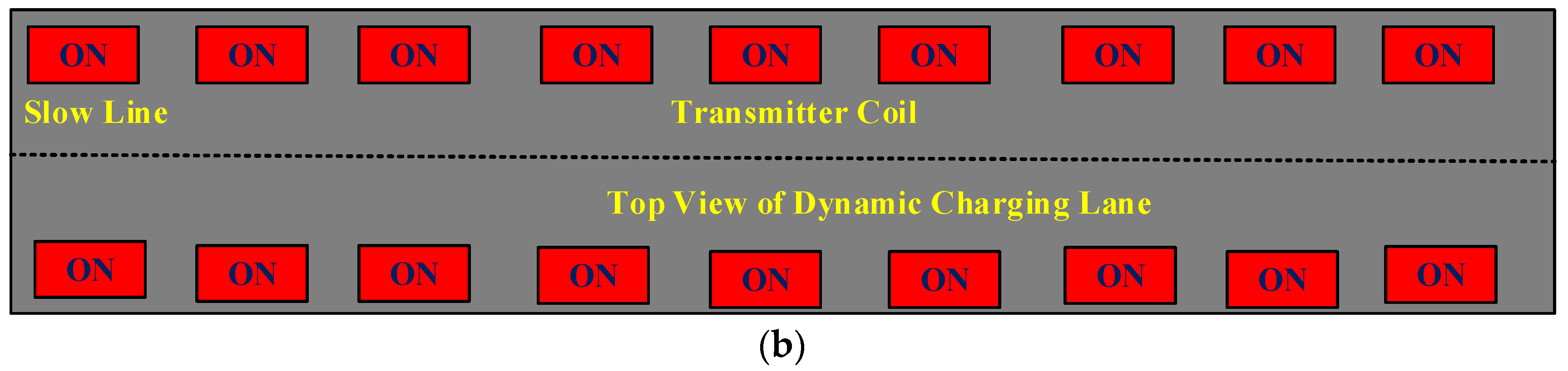
2.3. Types of Economic Analysis of DWC System
- Cost-Benefit Analysis (CBA)
- Life-Cycle Cost Analysis (LCCA)
- Net Present Value (NPV) Analysis
- Return on Investment (ROI) Analysis
- Sensitivity Analysis
- Total Cost of Ownership Equation
- Purchase cost = $35,000
- Operating costs = ($0.12/kWh × 60 kWh × 100 miles/100 miles) × 5 years = $4320
- Residual value = $15,000
- TCO = $35,000 + $4320 − $15,000 = $24,320.
- Levelized Cost of Electricity Equation
- Net Present Value (NPV) Equation
- Internal Rate of Return (IRR) Equation
- Benefit-Cost Ratio (BCR) Equation
- Benefits = $300,000 × 10 years = $3 million
- Costs = $100,000 × 10 years = $1 million
- BCR = $3 million/$1 million = 3
2.4. Challenges
- Complexity of the technology
- Interdisciplinary nature
- Limited data availability
- Difficulty in estimating costs and benefits
- Heterogeneous adoption
- Time lag
2.5. Advantage of Economic Analysis of Dynamic Charging
- Identifying cost savings: Economic analysis can help identify cost savings associated with dynamic charging, such as reduced battery size, which can result in a lower cost of ownership for EVs.
- Assessing the economic feasibility: Economic analysis can assess the economic possibility of DC by determining costs of implementing the infrastructure and the potential revenue streams that can be generated from the technology. This can help policymakers and investors determine whether dynamic charging is a worthwhile investment.
- Evaluating the influence on the power grid: Dynamic charging can have a significant influence on the power grid, as it requires a large amount of electricity to be supplied to the charging infrastructure. Economic analysis can evaluate the influence of dynamic charging on the power grid and determine the infrastructure requirements necessary to support the technology.
- Understanding the impact on consumer behavior: Economic analysis can help understand the impact of dynamic charging on consumer behavior, such as the willingness to pay for dynamic charging services and the potential increase in demand for EVs.
- Supporting policy development: Economic analysis can support the development of policies and regulations related to dynamic charging by providing insights into the costs and benefits of technology on the environment and society.
2.6. Limitations in Economic Analysis of Dynamic Charging
- Uncertainty about future technology: Economic analysis relies on assumptions about future technology, such as the cost and performance of batteries and charging infrastructure. These assumptions can be uncertain, and if the technology does not develop as expected, the economic analysis may be inaccurate.
- Lack of data: Economic analysis requires data on variables such as consumer behavior and infrastructure costs. However, data on these variables may be limited or difficult to obtain, which can limit the accuracy of the analysis.
- Difficulty in accounting for externalities: Economic analysis typically focuses on the private costs and benefits of dynamic charging, such as the cost of infrastructure and the savings from reduced battery size. However, dynamic charging can also have externalities, such as reduced air pollution, that are difficult to account for in economic analysis.
- Limited scope: Economic analysis is typically focused on specific outcomes, such as the cost-effectiveness of dynamic charging. However, there may be broader social, environmental, and equity considerations that are not fully captured in economic analysis.
- Geographical and temporal limitations: Economic analysis may not be generalizable to different geographical contexts or time periods. For example, the costs and benefits of dynamic charging may vary depending on the region or country, and economic analysis may not capture the long-term impacts of the technology.
3. Authentication Techniques
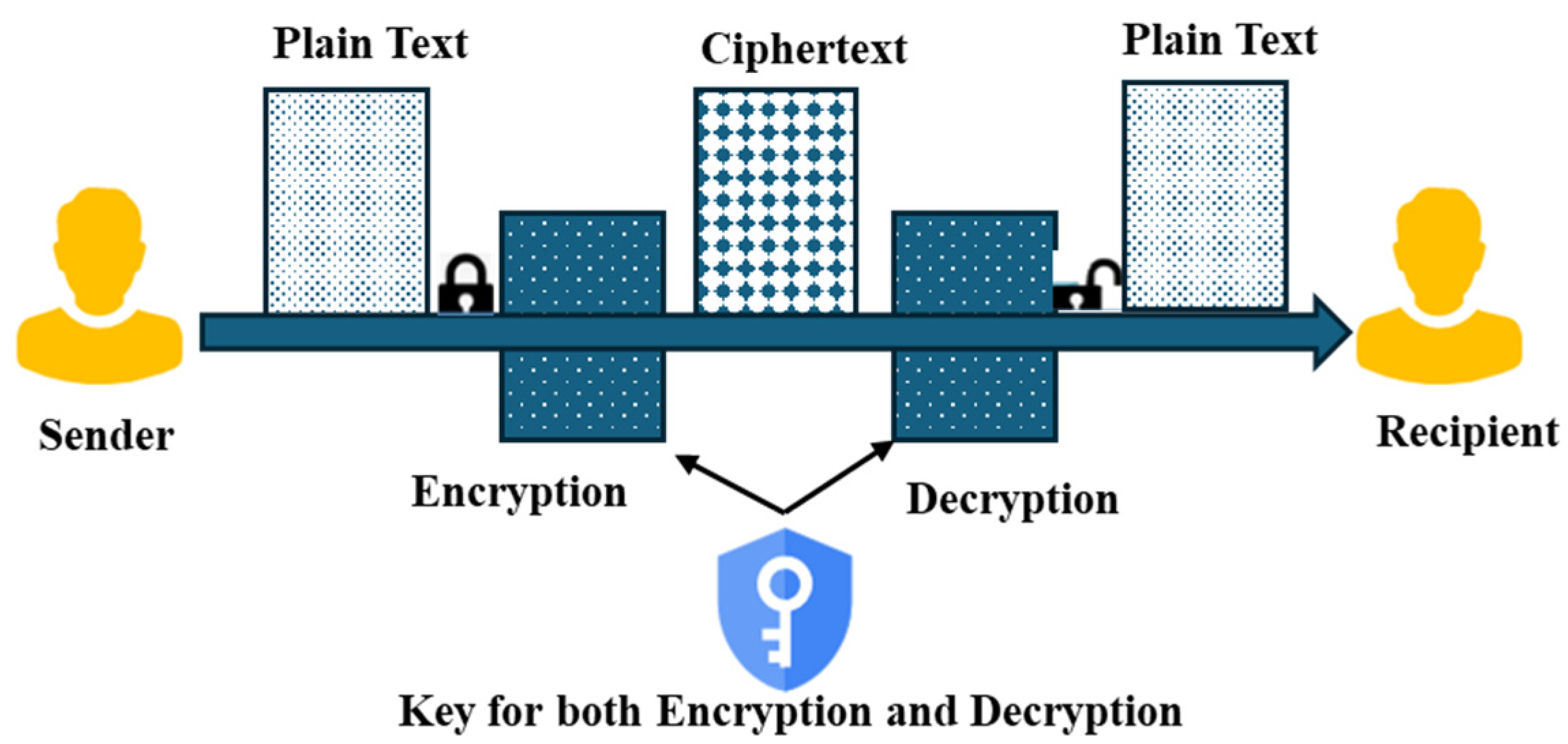
- Symmetric and Asymmetric Cryptography
- Confidentiality
- Data integrity
- Authentication
- Non-repudiation
- Digital signatures
- Hash chains
- Fast Authentication for Dynamic EV Charging
- Hash-based Message Authentication Code
- Elliptic Curve Digital Signature Algorithm
- Just Fast Keying
- Fast and Lightweight Privacy-Aware Authentication
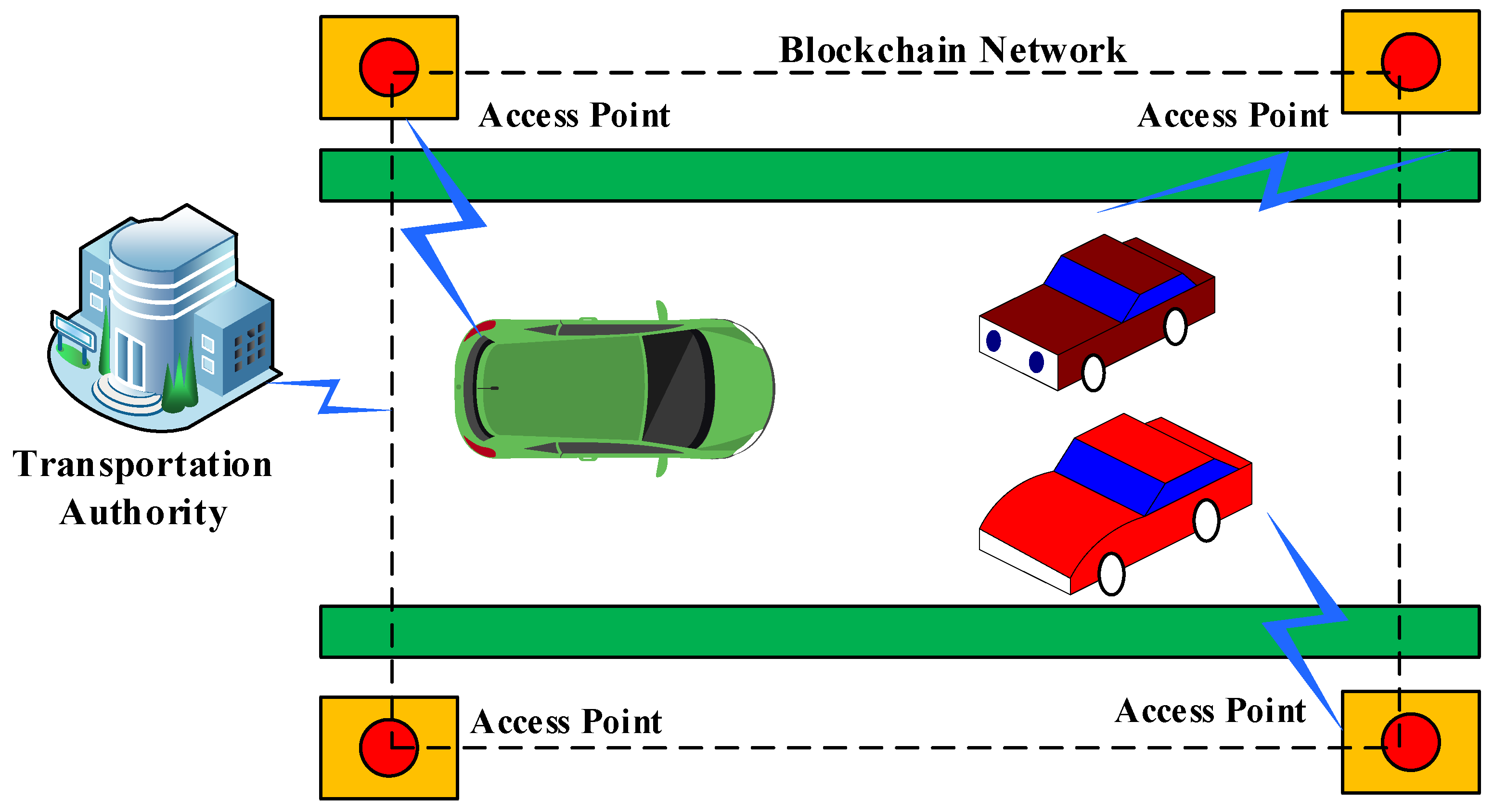
4. Blockchain Technology in DWC-EV
4.1. Layers of Blockchain
- Sensing Layer
- Communication Layer
- Application Layer
- Layer 1: All of the vehicle sensors make up the sensing layer, which gathers data and identifies specific events that are relevant such vehicle circumstances, driving patterns, weather conditions, etc.
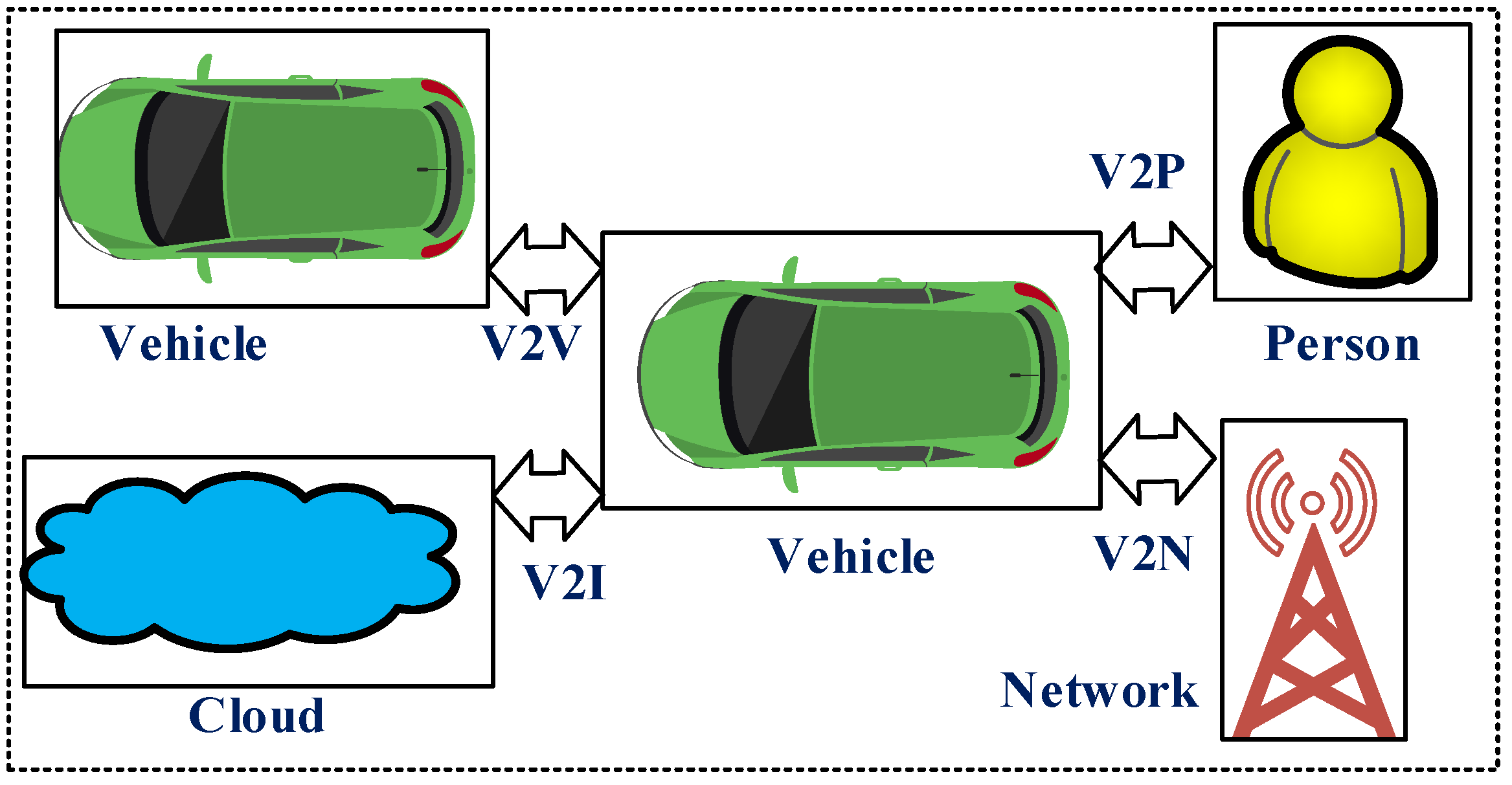
- Layer 2: Different wireless communication modes are made possible by the second layer that is the communication layer (e.g., V2I and V2V). Current and upcoming networks, including Wi-Fi, GSM, Bluetooth, and LTE, are often connected thanks to a communication layer.
- Layer 3: A gateway between the communication layer and application levels, the blockchain serves as a governance layer. This may offer blockchain built keys and group information into blocks in such a broadened IoV architecture. Furthermore, by offering a set number of tokens in exchange for sharing information resources, it may use incentive mechanisms to encourage users to do so. This would enable users to actively contribute transactional data to the system.
- Layer 4: The IoV network’s third layer, or computing, is responsible for storing, analyzing, and making choices pertaining to a variety of situations. Additionally, this layer offers data computing services.
- Layer 5: The IoV’s topmost level, the application layer, can provide customers with a variety of various vehicle services.
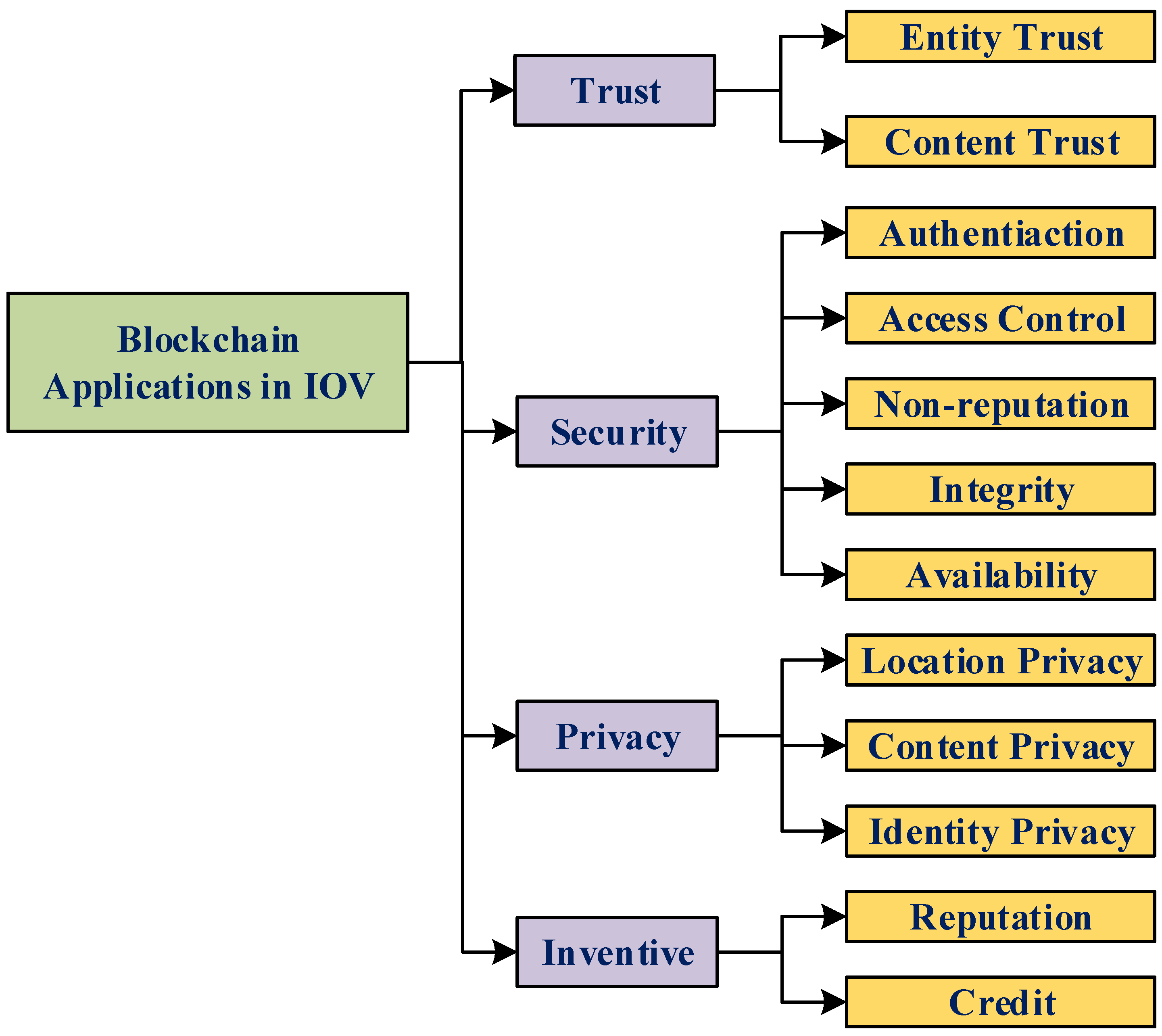
4.2. Blockchain Applications in IoV
4.3. Challenges of IoV-Assisted Smart Grid
- Scalability
- Interoperability
- Energy Consumption
- Regulation and Governance
- Security and Privacy
- Cost
- Blockchain-based IoV Security
- Identity management
- Secure communication
- Data privacy
4.4. Smart Contracts
- Immutable Record
- Distributed consensus
4.5. Blockchain Contributions in IoV-Assisted Smart Grids
- Decentralization
- Trust and transparency
- Smart contracts
- Energy Trading
- Data Privacy
- Traceability
4.6. Limitations of Using Blockchain in IoV-Assisted Smart Grids
- Scalability
- Energy Consumption
- Interoperability
- Regulatory challenges
- Security
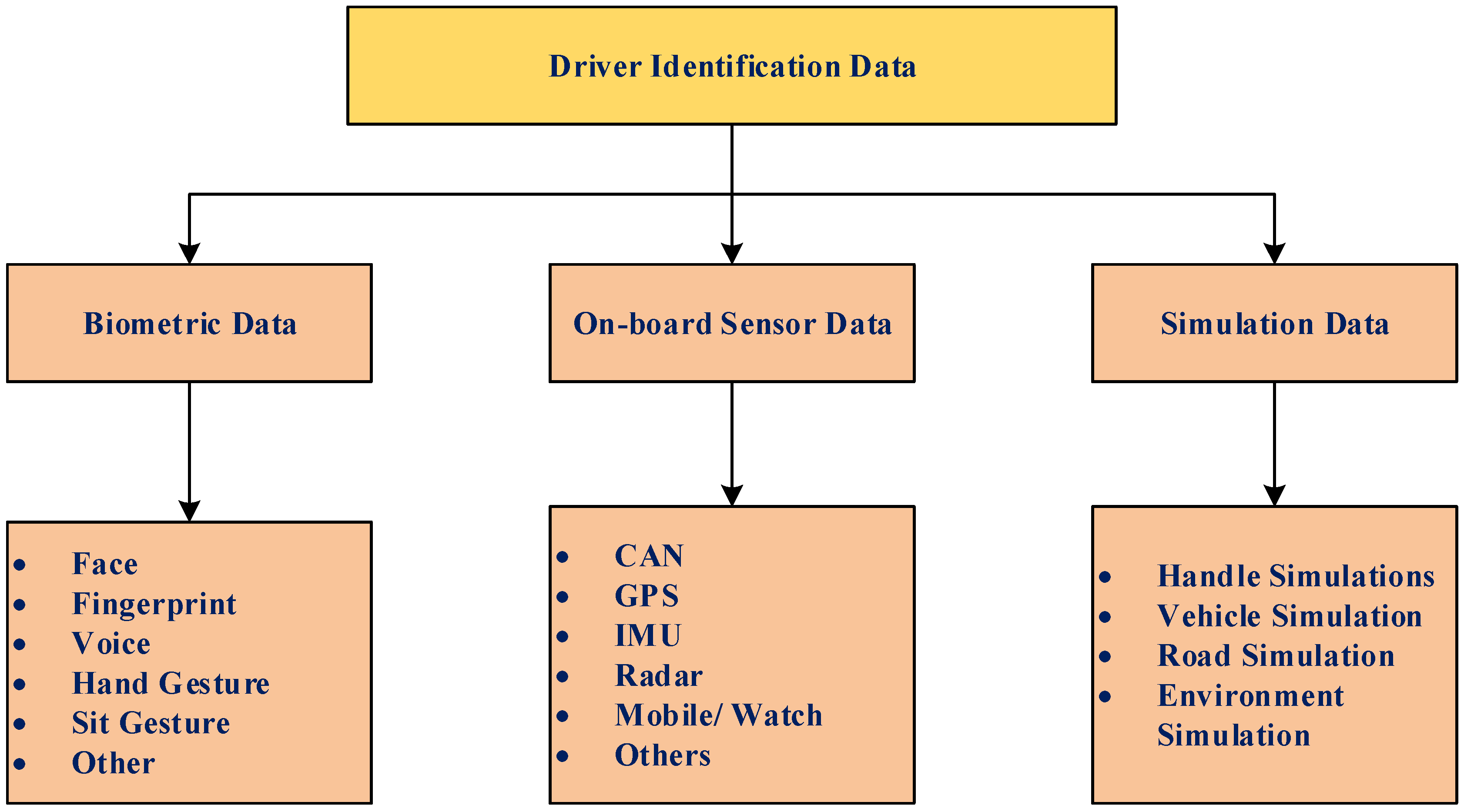
5. Driver Identification Data
- Biometric Data
- On-Board Sensor Data
- Driving Simulator Data
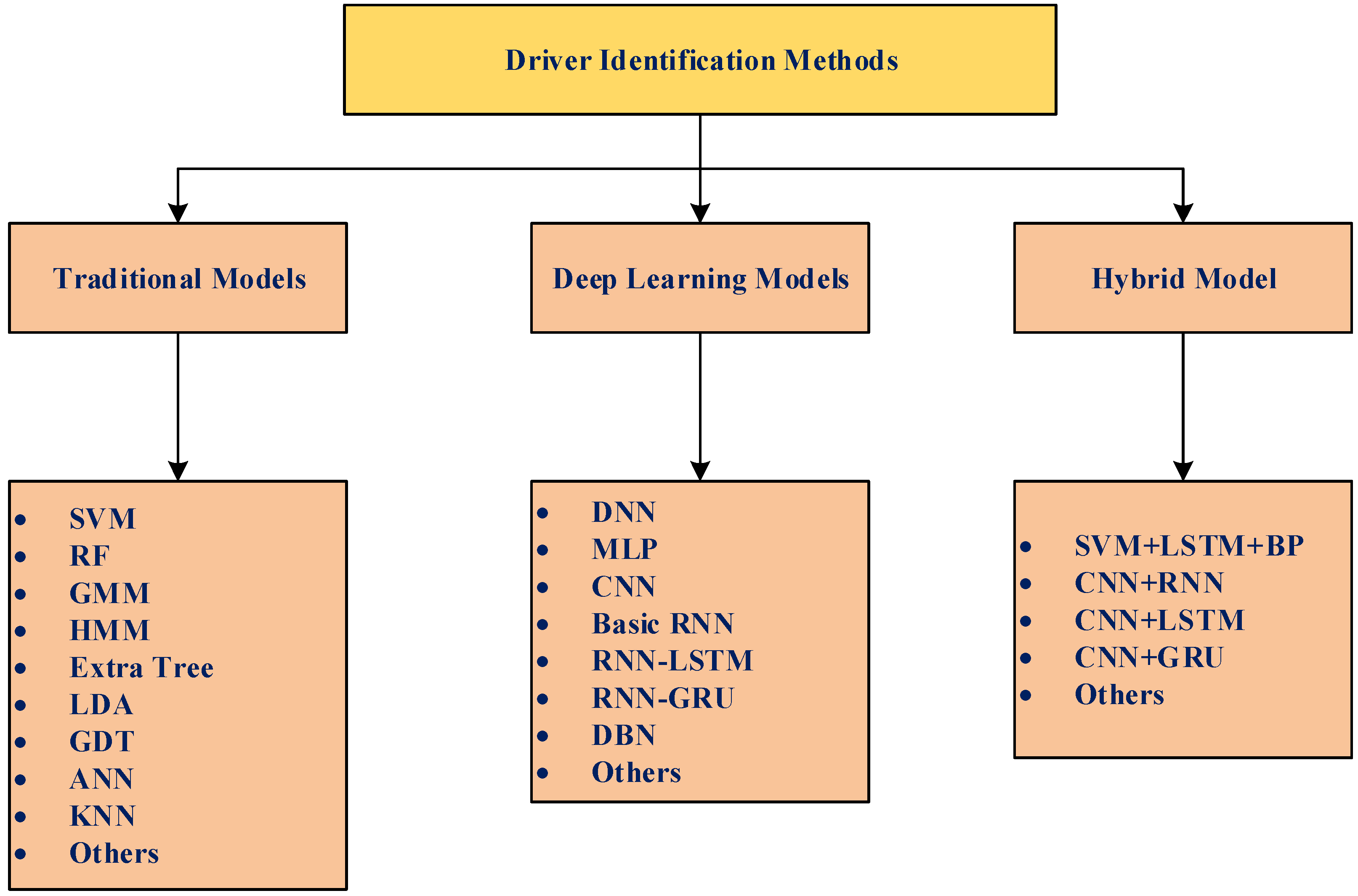
5.1. Driver Identification Models
- Traditional Model
- SVM Model
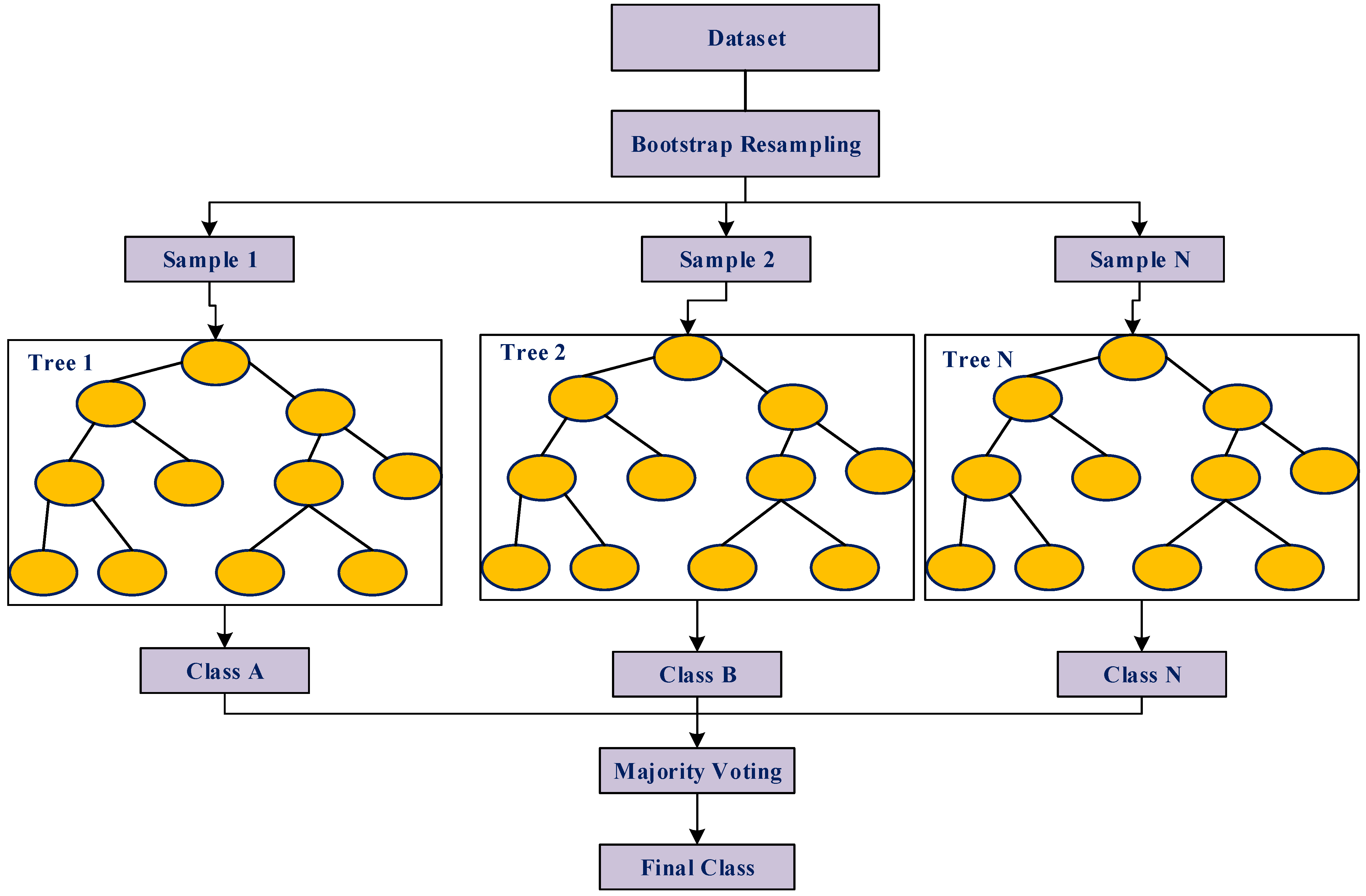
- RF Model
- Deep Learning Model
- CNN Model
- RNN Model
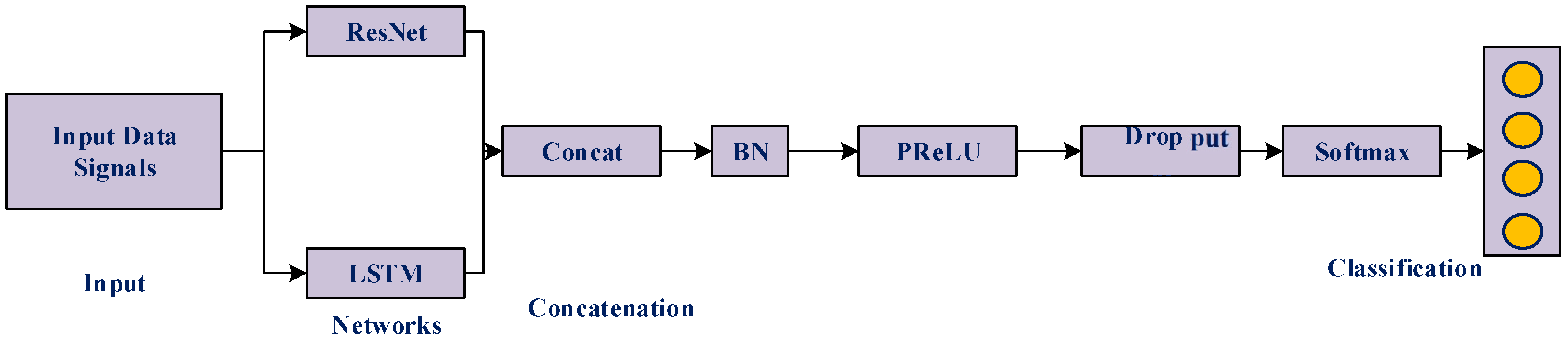
- Hybrid Model
5.2. Summary on Driver Identification Technique in EV
6. Standards, Protocols, and Emerging Technologies for EVs
6.1. New Communications Technologies for Electric Vehicles
6.2. Computational Technologies Intended for EVs
6.3. ML for Plug-In Electric Vehicles
6.4. Big Data Technologies for EVs
6.5. Blockchain Technology for Electric Vehicles
6.6. EV Security Considerations
7. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Venkatesan, R.; Savio, A.D.; Balaji, C.; Narayanamoorthi, R.; Kotb, H.; ELrashidi, A.; Nureldeen, W. A Comprehensive Review on Efficiency Enhancement of Wireless Charging System for the Electric Vehicles Applications. IEEE Access 2024, 12, 46967–46994. [Google Scholar] [CrossRef]
- ElGhanam, E.; Sharf, H.; Odeh, Y.; Hassan, M.S.; Osman, A.H. On the Coordination of Charging Demand of Electric Vehicles in a Network of Dynamic Wireless Charging Systems. IEEE Access 2022, 10, 62879–62892. [Google Scholar] [CrossRef]
- Zhang, X.; Yuan, Z.; Yang, Q.; Li, Y.; Zhu, J.; Li, Y. Coil Design and Efficiency Analysis for Dynamic Wireless Charging System for Electric Vehicles. IEEE Trans. Magn. 2016, 52, 8700404. [Google Scholar] [CrossRef]
- Hamouid, K.; Adi, K. Privacy-aware Authentication Scheme for Electric Vehicle In-motion Wireless Charging. In Proceedings of the 2020 International Symposium on Networks, Computers and Communications (ISNCC), Montreal, QC, Canada, 16–18 June 2020; pp. 1–6. [Google Scholar] [CrossRef]
- Nguyen, T.-V.; Sun, H.; Wang, H.; Hu, R.Q. Authentication and PHY-Security Schemes for Electric Vehicle Dynamic Wireless Charging. IEEE Trans. Veh. Technol. 2024, 73, 1698–1712. [Google Scholar] [CrossRef]
- Bianchi, T.; Asokraj, S.; Brighente, A.; Conti, M.; Poovendran, R. QEVSEC: Quick Electric Vehicle SEcure Charging via Dynamic Wireless Power Transfer. In Proceedings of the 2023 IEEE 97th Vehicular Technology Conference (VTC2023-Spring), Florence, Italy, 20–23 June 2023; pp. 1–6. [Google Scholar] [CrossRef]
- Sikdar, S.; Damle, M. IoT Solutions for Electric Vehicles (EV) Charging Stations: A Driving Force Towards EV Mass Adoption. In Proceedings of the 2022 International Interdisciplinary Humanitarian Conference for Sustainability (IIHC), Bengaluru, India, 18–19 November 2022; pp. 114–120. [Google Scholar] [CrossRef]
- Hongwei, M.; Meng, Z.; Xu, F.; Xia, W. Study on coordinated charging control algorithm for plug-in electric vehicle based on energy internet. In Proceedings of the 2017 China International Electrical and Energy Conference (CIEEC), Beijing, China, 25–27 October 2017; pp. 653–657. [Google Scholar] [CrossRef]
- Kadav, P.; Asher, Z.D. Improving the Range of Electric Vehicles. In Proceedings of the 2019 Electric Vehicles International Conference (EV), Bucharest, Romania, 3–4 October 2019; pp. 1–5. [Google Scholar] [CrossRef]
- Yuan, K.; Sun, C.; Song, Y.; Xue, Z.; Wu, Z.; Gao, S.; Xu, J. Electric vehicle smart charging network under the energy internet framework. In Proceedings of the 2017 IEEE Conference on Energy Internet and Energy System Integration (EI2), Beijing, China, 26–28 November 2017; pp. 1–5. [Google Scholar] [CrossRef]
- Halba, K.; Griffor, E.; Kamongi, P.; Roth, T. Using Statistical Methods and Co-Simulation to Evaluate ADS-Equipped Vehicle Trustworthiness. In Proceedings of the 2019 Electric Vehicles International Conference (EV), Bucharest, Romania, 3–4 October 2019; pp. 1–5. [Google Scholar] [CrossRef]
- Wang, D.; Shi, Q.; Kong, W.; Dai, H. Research on the Development of Electric Vehicles and Vehicle to Grid. In Proceedings of the 2023 4th International Conference on Advanced Electrical and Energy Systems (AEES), Shanghai, China, 27–29 October 2023; pp. 614–619. [Google Scholar] [CrossRef]
- Drosu, A.; Suciu, G.; Scheianu, A.; Petre, I. An Analysis of Hybrid/Electric Vehicle Monitoring Systems and Parameters. In Proceedings of the 2019 Electric Vehicles International Conference (EV), Bucharest, Romania, 3–4 October 2019; pp. 1–5. [Google Scholar] [CrossRef]
- Shaikh, P.W.; Mouftah, H.T. Connected and Autonomous Electric Vehicles Charging Reservation and Trip Planning System. In Proceedings of the 2021 International Wireless Communications and Mobile Computing (IWCMC), Harbin City, China, 28 June–2 July 2021; pp. 1135–1140. [Google Scholar] [CrossRef]
- Kaššaj, M.; Peráček, T. Synergies and Potential of Industry 4.0 and Automated Vehicles in Smart City Infrastructure. Appl. Sci. 2024, 14, 3575. [Google Scholar] [CrossRef]
- Funta, R. Automated Driving and Data Protection: Some Remarks on Fundamental Rights and Privacy. Crit. Law 2021, 13, 106–118. [Google Scholar] [CrossRef]
- Perișoară, L.A.; Dănișor, C.; Săcăleanu, D.I. Analysis of Mobile Communications Services for Internet of Things in Romania. In Proceedings of the 2022 23rd International Carpathian Control Conference (ICCC), Sinaia, Romania, 29 May–1 June 2022; pp. 198–202. [Google Scholar] [CrossRef]
- Li, G.; Liu, P.; Wang, Z.; Zhang, Z.; Yan, Z.; Wang, S. An Overview of Cloud-Based Electric Vehicle Safety Service Platform Functions and A Case Study. In Proceedings of the 2021 6th International Conference on Transportation Information and Safety (ICTIS), Wuhan, China, 22–24 October 2021; pp. 1476–1481. [Google Scholar] [CrossRef]
- Luo, L.; Feng, J.; Yu, H.; Sun, G. Blockchain-Enabled Two-Way Auction Mechanism for Electricity Trading in Internet of Electric Vehicles. IEEE Internet Things J. 2022, 9, 8105–8118. [Google Scholar] [CrossRef]
- Yu, H.; Deng, J.; Wang, Z.; Wang, S. Research on Efficiency Interval Distribution of Permanent Magnet Synchronous Motor for Electric Vehicle Based on Operation Data Statistics. In Proceedings of the 2020 IEEE 29th International Symposium on Industrial Electronics (ISIE), Delft, Netherlands, 17–19 June 2020; pp. 362–367. [Google Scholar] [CrossRef]
- Yang, Y.; Zhang, B.; Wang, W.; Wang, M.; Peng, X. Development Pathway and Practices for Integration of Electric Vehicles and Internet of Energy. In Proceedings of the 2020 IEEE Sustainable Power and Energy Conference (iSPEC), Chengdu, China, 23–25 November 2020; pp. 2128–2134. [Google Scholar] [CrossRef]
- Muralidharan, M.; Karneswaran, S.G.; Elizabeth, E. Dynamic Charging Lane for Authenticated Electric Vehicles. In Proceedings of the 2024 Second International Conference on Emerging Trends in Information Technology and Engineering (ICETITE), Vellore, India, 22–23 February 2024; pp. 1–5. [Google Scholar] [CrossRef]
- Babu, P.R.; Reddy, A.G.; Palaniswamy, B.; Kommuri, S.K. EV-Auth: Lightweight Authentication Protocol Suite for Dynamic Charging System of Electric Vehicles with Seamless Handover. IEEE Trans. Intell. Veh. 2022, 7, 734–747. [Google Scholar] [CrossRef]
- Babu, P.R.; Reddy, A.G.; Palaniswamy, B.; Das, A.K. EV-PUF: Lightweight Security Protocol for Dynamic Charging System of Electric Vehicles Using Physical Unclonable Functions. IEEE Trans. Netw. Sci. Eng. 2022, 9, 3791–3807. [Google Scholar] [CrossRef]
- Abouyoussef, M.; Ismail, M. Blockchain-Based Privacy-Preserving Networking Strategy for Dynamic Wireless Charging of EVs. IEEE Trans. Netw. Serv. Manag. 2022, 19, 1203–1215. [Google Scholar] [CrossRef]
- Massmi, K.; Hamouid, K.; Adi, K. Secure Electric Vehicle Dynamic Charging Based on Smart Contracts. In Proceedings of the 2023 International Symposium on Networks, Computers and Communications (ISNCC), Doha, Qatar, 23–26 October 2023; pp. 1–6. [Google Scholar] [CrossRef]
- Pazos-Revilla, M.; Alsharif, A.; Gunukula, S.; Guo, T.N.; Mahmoud, M.; Shen, X. Secure and Privacy-Preserving Physical-Layer-Assisted Scheme for EV Dynamic Charging System. IEEE Trans. Veh. Technol. 2018, 67, 3304–3318. [Google Scholar] [CrossRef]
- Alshaeri, A.; Younis, M. Lightweight Authentication and Authorization Protocol for Dynamic Charging of Electric Vehicles. In Proceedings of the 2022 IEEE 19th Annual Consumer Communications & Networking Conference (CCNC), Las Vegas, NV, USA, 8–11 January 2022; pp. 550–556. [Google Scholar] [CrossRef]
- Alshaeri, A.; Younis, M. A Blockchain-based Energy Trading Scheme for Dynamic Charging of Electric Vehicles. In Proceedings of the 2021 IEEE Global Communications Conference (GLOBECOM), Madrid, Spain, 7–11 December 2021; pp. 1–6. [Google Scholar] [CrossRef]
- Li, H.; Dán, G.; Nahrstedt, K. Portunes+: Privacy-Preserving Fast Authentication for Dynamic Electric Vehicle Charging. IEEE Trans. Smart Grid 2017, 8, 2305–2313. [Google Scholar] [CrossRef]
- Guo, T.; Mahmoud, M. Performance Analysis of Physical-Layer-Based Authentication for Electric Vehicle Dynamic Charging. In Proceedings of the 2018 IEEE 88th Vehicular Technology Conference (VTC-Fall), Chicago, IL, USA, 27–30 August 2018; pp. 1–7. [Google Scholar] [CrossRef]
- Li, H.; Dan, G.; Nahrstedt, K. Portunes: Privacy-preserving fast authentication for dynamic electric vehicle charging. In Proceedings of the 2014 IEEE International Conference on Smart Grid Communications (SmartGridComm), Venice, Italy, 3–6 November 2014; pp. 920–925. [Google Scholar] [CrossRef]
- Li, H.; Dán, G.; Nahrstedt, K. FADEC: Fast authentication for dynamic electric vehicle charging. In Proceedings of the 2013 IEEE Conference on Communications and Network Security (CNS), National Harbor, MD, USA, 14–16 October 2013; pp. 369–370. [Google Scholar] [CrossRef]
- Gunukula, S.; Sherif, A.B.T.; Pazos-Revilla, M.; Ausby, B.; Mahmoud, M.; Shen, X.S. Efficient scheme for secure and privacy-preserving electric vehicle dynamic charging system. In Proceedings of the 2017 IEEE International Conference on Communications (ICC), Paris, France, 21–25 May 2017; pp. 1–6. [Google Scholar] [CrossRef]
- Razmjouei, P.; Kavousi-Fard, A.; Dabbaghjamanesh, M.; Jin, T.; Su, W. DAG-Based Smart Contract for Dynamic 6G Wireless EVs Charging System. IEEE Trans. Green Commun. Netw. 2022, 6, 1459–1467. [Google Scholar] [CrossRef]
- Li, H.; Dán, G.; Nahrstedt, K. Proactive key dissemination-based fast authentication for in-motion inductive EV charging. In Proceedings of the 2015 IEEE International Conference on Communications (ICC), London, UK, 8–12 June 2015; pp. 795–801. [Google Scholar] [CrossRef]
- Almarshoodi, A.; Keenan, J.; Campbell, I.; Hassan, T.; Ibrahem, M.I.; Fouda, M.M. Security and Privacy Preservation for Future Vehicular Transportation Systems: A Survey. In Proceedings of the 2023 IEEE 12th International Conference on Communication Systems and Network Technologies (CSNT), Bhopal, India, 8–9 April 2023; pp. 728–734. [Google Scholar] [CrossRef]
- Fraiji, Y.; Azzouz, L.B.; Trojet, W.; Saidane, L.A.; Hoblos, G. Adaptive Security for the Intra-Electric Vehicular Wireless Networks. In Proceedings of the 2019 15th International Wireless Communications & Mobile Computing Conference (IWCMC), Tangier, Morocco, 24–28 June 2019; pp. 1215–1220. [Google Scholar] [CrossRef]
- Iqbal, A.; Rajasekaran, A.S.; Nikhil, G.S.; Azees, M. A Secure and Decentralized Blockchain Based EV Energy Trading Model Using Smart Contract in V2G Network. IEEE Access 2021, 9, 75761–75777. [Google Scholar] [CrossRef]
- Yi, P.; Zhu, T.; Jiang, B.; Jin, R.; Wang, B. Deploying Energy Routers in an Energy Internet Based on Electric Vehicles. IEEE Trans. Veh. Technol. 2016, 65, 4714–4725. [Google Scholar] [CrossRef]
- Qin, J.; Sun, X.; Wang, J.; Li, X.; Yin, L.; Zhang, R. Data-Driven Robust Day-Ahead Optimal Dispatch of Distribution Network Considering the Electric Vehicle. In Proceedings of the 2021 3rd International Conference on Smart Power & Internet Energy Systems (SPIES), Shanghai, China, 25–28 September 2021; pp. 322–327. [Google Scholar] [CrossRef]
- Jia, Y.; Li, X.; Sang, L.; Wang, K. Research on Constant Voltage Output Optimization Method for EV Dynamic Wireless Charging System. In Proceedings of the 2020 8th International Conference on Power Electronics Systems and Applications (PESA), Hong Kong, China, 7–10 December 2020; pp. 1–4. [Google Scholar] [CrossRef]
- Chowdary, K.V.V.S.R.; Kumar, K.; Behera, R.K.; Banerjee, S.; Kumar, R.R. Load Independent Characteristics of Dynamic Wireless Charging System Through Higher Order Compensation. In Proceedings of the 2020 IEEE International Conference on Power Electronics, Drives and Energy Systems (PEDES), Jaipur, India, 16–19 December 2020; pp. 1–6. [Google Scholar] [CrossRef]
- Prasad, K.K.; Agarwal, V. A Novel Frequency Modulation Technique to Minimize the Start-Up Transients in Dynamic Wireless Charging Systems for Electric Vehicles. In Proceedings of the 2022 Wireless Power Week (WPW), Bordeaux, France, 5–8 July 2022; pp. 834–838. [Google Scholar] [CrossRef]
- Zavrel, M.; Kindl, V.; Tyrpekl, M. Dynamic Wireless Charging Using LCC-S Compensation Topology in Low and Medium Power Applications. In Proceedings of the 2023 IEEE 32nd International Symposium on Industrial Electronics (ISIE), Helsinki, Finland, 19–21 June 2023; pp. 1–6. [Google Scholar] [CrossRef]
- Chowdary, K.V.V.S.R.; Kumar, K.; Nayak, B.; Mali, V. Decoding the Magnetic Coupler Characteristics for the Implementation of Dynamic Wireless Charging Scheme for Electric Vehicles. In Proceedings of the 2023 IEEE 3rd International Conference on Smart Technologies for Power, Energy and Control (STPEC), Bhubaneswar, India, 10–13 December 2023; pp. 1–6. [Google Scholar] [CrossRef]
- Chowdary, K.V.V.S.R.; Kumar, K. Assessment of Dynamic Wireless Charging System with the Variation in Mutual Inductance. In Proceedings of the 2022 IEEE 19th India Council International Conference (INDICON), Kochi, India, 24–26 November 2022; pp. 1–4. [Google Scholar] [CrossRef]
- Yao, Y.; Du, L. Design of Intelligent Vehicle Based on Dynamic Wireless Charging. In Proceedings of the 2020 12th International Conference on Advanced Computational Intelligence (ICACI), Dali, China, 14–16 August 2020; pp. 402–407. [Google Scholar] [CrossRef]
- Odeh, Y.S.; Elkahlout, I.S.; Naeimi, P.V.; ElGhanam, E.A.; Hassan, M.S.; Osman, A.H. Planning and Allocation of Dynamic Wireless Charging Infrastructure for Electric Vehicles. In Proceedings of the 2022 9th International Conference on Electrical and Electronics Engineering (ICEEE), Alanya, Turkey, 29–31 March 2022; pp. 306–310. [Google Scholar] [CrossRef]
- Openshaw, S.; Etta, D.; Maji, S.; Ruan, T.; Afridi, K.K. Investigation of Commercial Viability and Public Perception of Electrified Roadways with Dynamic Wireless Charging. In Proceedings of the 2023 IEEE Wireless Power Technology Conference and Expo (WPTCE), San Diego, CA, USA, 4–8 June 2023; pp. 1–6. [Google Scholar] [CrossRef]
- Jeong, S.; Jang, Y.J.; Kum, D. Economic Analysis of the Dynamic Charging Electric Vehicle. IEEE Trans. Power Electron. 2015, 30, 6368–6377. [Google Scholar] [CrossRef]
- García-Vázquez, C.A.; Llorens-Iborra, F.; Fernández-Ramírez, L.M.; Sánchez-Sainz, H.; Jurado, F. Evaluating Dynamic Wireless Charging of electric vehicles moving along a stretch of highway. In Proceedings of the 2016 International Symposium on Power Electronics, Electrical Drives, Automation and Motion (SPEEDAM), Capri, Italy, 22–24 June 2016; pp. 61–66. [Google Scholar] [CrossRef]
- Haddad, D.; Arellano, P.; Bernicke, D.; Castilho, M.; Gilley, B.; Lagpacan, Z.; Maxey, C.; Pilaszewicz, A.; Young, W.; Aliprantis, D. Economic Feasibility of Dynamic Wireless Power Transfer Lanes in Indiana Freight Corridors. In Proceedings of the 2022 IEEE Power and Energy Conference at Illinois (PECI), Champaign, IL, USA, 10–11 March 2022; pp. 1–8. [Google Scholar] [CrossRef]
- Alattab, A.A.; Irshad, R.R.; Yahya, A.A.; Al-Awady, A.A. Privacy Protected Preservation of Electric Vehicles’ Data in Cloud Computing Using Secure Data Access Control. Energies 2022, 15, 8085. [Google Scholar] [CrossRef]
- Tappeta, V.S.R.; Appasani, B.; Patnaik, S.; Ustun, T.S. A Review on Emerging Communication and Computational Technologies for Increased Use of Plug-In Electric Vehicles. Energies 2022, 15, 6580. [Google Scholar] [CrossRef]
- Piedel, E.; Lauth, E.; Grahle, A.; Göhlich, D. Review and Evaluation of Automated Charging Technologies for Heavy-Duty Vehicles. World Electr. Veh. J. 2024, 15, 235. [Google Scholar] [CrossRef]
- Kulkarni, G.A.; Joshi, R.D. Electric vehicle charging station integration with IOT enabled device. In Proceedings of the 2021 10th International Conference on Internet of Everything, Microwave Engineering, Communication and Networks (IEMECON), Jaipur, India, 1–2 December 2021; pp. 1–6. [Google Scholar] [CrossRef]
- Zhang, X.; Yang, Y.; Su, S. Study on Electric Vehicle Sharing and Leasing Business Model for Group Users based on Blockchain. In Proceedings of the 2020 IEEE Sustainable Power and Energy Conference (iSPEC), Chengdu, China, 23–25 November 2020; pp. 2628–2633. [Google Scholar] [CrossRef]
- Durga, C.R.; Karthik, J.; Dakshayani, R.; Manikanta, S. A Novel Approach for Smart Battery Monitoring System in Electric Vehicles using Internet of Things. In Proceedings of the 2023 International Conference on Intelligent Data Communication Technologies and Internet of Things (IDCIoT), Bengaluru, India, 5–7 January 2023; pp. 870–874. [Google Scholar] [CrossRef]
- Zhang, Y.; Xu, H. Reconfigurable-Intelligent-Surface-Enhanced Dynamic Resource Allocation for the Social Internet of Electric Vehicle Charging Networks with Causal-Structure-Based Reinforcement Learning. Future Internet 2024, 16, 165. [Google Scholar] [CrossRef]
- Shanmugam, Y.; Rajamanickam, N.; Alroobaea, R.; Afandi, A. Driving towards Sustainability: Wireless Charging of Low-Speed Vehicles with PDM-Based Active Bridge Rectifiers. Sustainability 2024, 16, 3810. [Google Scholar] [CrossRef]
- Ahn, S.; Jung, H.; Park, K.-W. LazyFrog: Advancing Security and Efficiency in Commercial Wireless Charging with Adaptive Frequency Hopping. Sensors 2024, 24, 2571. [Google Scholar] [CrossRef] [PubMed]
- Li, J.; Deng, Z.; Feng, Y.; Liu, N. Deep-Reinforcement-Learning-Based Joint Energy Replenishment and Data Collection Scheme for WRSN. Sensors 2024, 24, 2386. [Google Scholar] [CrossRef]
- Behnamfar, M.; Stevenson, A.; Tariq, M.; Sarwat, A. Vehicle Position Detection Based on Machine Learning Algorithms in Dynamic Wireless Charging. Sensors 2024, 24, 2346. [Google Scholar] [CrossRef]
- Jung, S. Precision Landing of Unmanned Aerial Vehicle under Wind Disturbance Using Derivative Sliding Mode Nonlinear Disturbance Observer-Based Control Method. Aerospace 2024, 11, 265. [Google Scholar] [CrossRef]
- Zhu, X.; Fan, H.; Zhang, S.; Du, J. Stochastic Optimization of an Electric Bus Dynamic Wireless Charging System. World Electr. Veh. J. 2024, 15, 137. [Google Scholar] [CrossRef]
- Rabih, M.; Takruri, M.; Al-Hattab, M.; Alnuaimi, A.A.; Bin Thaleth, M.R. Wireless Charging for Electric Vehicles: A Survey and Comprehensive Guide. World Electr. Veh. J. 2024, 15, 118. [Google Scholar] [CrossRef]
- Wang, J.; Wang, S.; Wen, K.; Weng, B.; Zhou, X.; Chen, K. An ECC-Based Authentication Protocol for Dynamic Charging System of Electric Vehicles. Electronics 2024, 13, 1109. [Google Scholar] [CrossRef]
- Iqbal, S.; Alshammari, N.F.; Shouran, M.; Massoud, J. Smart and Sustainable Wireless Electric Vehicle Charging Strategy with Renewable Energy and Internet of Things Integration. Sustainability 2024, 16, 2487. [Google Scholar] [CrossRef]
- Sabban, A. Novel Meta-Fractal Wearable Sensors and Antennas for Medical, Communication, 5G, and IoT Applications. Fractal Fract. 2024, 8, 100. [Google Scholar] [CrossRef]
- Bertoluzzo, M.; Di Barba, P.; Forzan, M.; Mognaschi, M.E.; Sieni, E. A Deep Learning Approach to Improve the Control of Dynamic Wireless Power Transfer Systems. Energies 2023, 16, 7865. [Google Scholar] [CrossRef]
- Quadir, N.; Alawar, F.S.; Albasha, L.; Mir, H. Linear-in-dB Logarithmic Signal Strength Sensor Circuit for Wireless Power Transfer Receivers. Energies 2023, 16, 7612. [Google Scholar] [CrossRef]
- Bozhi; Mohamed, M.; Gilani, V.N.M.; Amjad, A.; Majid, M.S.; Yahya, K.; Salem, M. A Review of Wireless Pavement System Based on the Inductive Power Transfer in Electric Vehicles. Sustainability 2023, 15, 14893. [Google Scholar] [CrossRef]
- Liang, M.; El Khamlichi Drissi, K.; Pasquier, C. Self- and Mutual-Inductance Cross-Validation of Multi-Turn, Multi-Layer Square Coils for Dynamic Wireless Charging of Electric Vehicles. Energies 2023, 16, 7033. [Google Scholar] [CrossRef]
- Chowdary, K.V.V.S.R.; Kumar, K.; Nayak, B.; Kumar, A.; Bertoluzzo, M. Dynamic Wireless Charging Performance Enhancement for Electric Vehicles: Mutual Inductance, Power Transfer Capability, and Efficiency. Vehicles 2023, 5, 1313–1327. [Google Scholar] [CrossRef]
- Allama, O.; Habaebi, M.H.; Khan, S.; Islam, M.R.; Alghaihab, A. Simulation and Control Design of a Midrange WPT Charging System for In-Flight Drones. Energies 2023, 16, 5746. [Google Scholar] [CrossRef]
- Bensetti, M.; Kadem, K.; Pei, Y.; Le Bihan, Y.; Labouré, E.; Pichon, L. Parametric Optimization of Ferrite Structure Used for Dynamic Wireless Power Transfer for 3 kW Electric Vehicle. Energies 2023, 16, 5439. [Google Scholar] [CrossRef]
- Zhang, B.; Gong, C.; Wang, Y.; Ma, L.; Zhang, D.; Xia, S. Research on the Collaborative Optimization of the Power Distribution Network and Traffic Network Based on Dynamic Traffic Allocation. Energies 2023, 16, 5259. [Google Scholar] [CrossRef]
- Bourzik, M.; Elbaz, H.; Bouleft, Y.; Alaoui, A.E.H. Round-Trip Wireless Charging Infrastructure for Heterogeneous Electric Vehicles on Highways: Modelling and Optimization. World Electr. Veh. J. 2023, 14, 160. [Google Scholar] [CrossRef]
- Wang, W.; Fan, S.; Wang, Z.; Yao, X.; Mu, K. Optimal Driving Model for Connected and Automated Electric Freight Vehicles in a Wireless Charging Scenario at Signalised Intersections. Appl. Sci. 2023, 13, 6286. [Google Scholar] [CrossRef]
- Xiong, W.; Liu, J.; Chen, J.; Hu, D. Detection of Secondary Side Position for Segmented Dynamic Wireless Charging Systems Based on Primary Phase Angle Sensing. Electronics 2023, 12, 2148. [Google Scholar] [CrossRef]
- Tang, Q.; Li, D.; Zhang, Y.; Chen, X. Dynamic Path-Planning and Charging Optimization for Autonomous Electric Vehicles in Transportation Networks. Appl. Sci. 2023, 13, 5476. [Google Scholar] [CrossRef]
- Xu, F.; Wei, S.; Yuan, D.; Li, J. Review on Key Technologies and Development of Magnetic Coupling Resonant-Dynamic Wireless Power Transfer for Unmanned Ground Vehicles. Electronics 2023, 12, 1506. [Google Scholar] [CrossRef]
- Dimitriadou, K.; Rigogiannis, N.; Fountoukidis, S.; Kotarela, F.; Kyritsis, A.; Papanikolaou, N. Current Trends in Electric Vehicle Charging Infrastructure; Opportunities and Challenges in Wireless Charging Integration. Energies 2023, 16, 2057. [Google Scholar] [CrossRef]
- Wang, Y.; Gong, L.; Bao, B.; Pan, J.; Feng, Q.; Xu, R. Conceptual Design and Preliminary Verification of Distributed Wireless System of Weigh-in-Motion. Appl. Sci. 2023, 13, 2467. [Google Scholar] [CrossRef]
- Hakemi, A.; Jovanovic, D.; Vilathgamuwa, M.; Walker, G.R. Robust Maximum Efficiency Tracking Control of Wirelessly Powered Directly Supplied Heart Pumps. Energies 2023, 16, 1517. [Google Scholar] [CrossRef]
- Ganchev, I.; O’Droma, M. Outsourcing Authentication, Authorization and Accounting, and Charging and Billing Services to Trusted Third Parties for Future Consumer-Oriented Wireless Communications. Electronics 2023, 12, 558. [Google Scholar] [CrossRef]
- Park, J.-H.; Joe, I.-W. Federated Learning-Based Prediction of Energy Consumption from Blockchain-Based Black Box Data for Electric Vehicles. Appl. Sci. 2024, 14, 5494. [Google Scholar] [CrossRef]
- Xu, Y.; Alderete Peralta, A.; Balta-Ozkan, N. Vehicle-to-Vehicle Energy Trading Framework: A Systematic Literature Review. Sustainability 2024, 16, 5020. [Google Scholar] [CrossRef]
- Kim, M.; Park, K.; Park, Y. A Reliable and Privacy-Preserving Vehicular Energy Trading Scheme Using Decentralized Identifiers. Mathematics 2024, 12, 1450. [Google Scholar] [CrossRef]
- Khan, S.; Amin, U.; Abu-Siada, A. P2P Energy Trading of EVs Using Blockchain Technology in Centralized and Decentralized Networks: A Review. Energies 2024, 17, 2135. [Google Scholar] [CrossRef]
- Miao, Q.; Ren, T.; Dong, J.; Chen, Y.; Xu, W. A 3C Authentication: A Cross-Domain, Certificateless, and Consortium-Blockchain-Based Authentication Method for Vehicle-to-Grid Networks in a Smart Grid. Symmetry 2024, 16, 336. [Google Scholar] [CrossRef]
- Stetter, D.; Höpfer, T.; Schmid, M.; Sturz, I.; Falkenberger, S.; Knoll, N. BANULA—A Novel DLT-Based Approach for EV Charging with High Level of User Comfort and Role-Specific Data Transparency for All Parties Involved. World Electr. Veh. J. 2024, 15, 79. [Google Scholar] [CrossRef]
- Chougule, S.B.; Chaudhari, B.S.; Ghorpade, S.N.; Zennaro, M. Exploring Computing Paradigms for Electric Vehicles: From Cloud to Edge Intelligence, Challenges and Future Directions. World Electr. Veh. J. 2024, 15, 39. [Google Scholar] [CrossRef]
- Samadi, M.; Ruj, S.; Schriemer, H.; Erol-Kantarci, M. Secure and Robust Demand Response Using Stackelberg Game Model and Energy Blockchain. Sensors 2023, 23, 8352. [Google Scholar] [CrossRef]
- Singh, M.; Ahmed, S.; Sharma, S.; Singh, S.; Yoon, B. BSEMS—A Blockchain-Based Smart Energy Measurement System. Sensors 2023, 23, 8086. [Google Scholar] [CrossRef]
- Wang, X.; Wei, J.; Wen, F.; Wang, K. A Trading Mode Based on the Management of Residual Electric Energy in Electric Vehicles. Energies 2023, 16, 6317. [Google Scholar] [CrossRef]
- Aldweesh, A. A Blockchain-Based Data Authentication Algorithm for Secure Information Sharing in Internet of Vehicles. World Electr. Veh. J. 2023, 14, 223. [Google Scholar] [CrossRef]
- Cui, D.; He, J.; Cheng, X.; Liu, Z. Electric Vehicle Charging Transaction Model Based on Alliance Blockchain. World Electr. Veh. J. 2023, 14, 192. [Google Scholar] [CrossRef]
- Naseri, F.; Kazemi, Z.; Larsen, P.G.; Arefi, M.M.; Schaltz, E. Cyber-Physical Cloud Battery Management Systems: Review of Security Aspects. Batteries 2023, 9, 382. [Google Scholar] [CrossRef]
- Mousavi, P.; Ghazizadeh, M.S.; Vahidinasab, V. A Decentralized Blockchain-Based Energy Market for Citizen Energy Communities. Inventions 2023, 8, 86. [Google Scholar] [CrossRef]
- Cabrera-Gutiérrez, A.J.; Castillo, E.; Escobar-Molero, A.; Cruz-Cozar, J.; Morales, D.P.; Parrilla, L. Blockchain-Based Services Implemented in a Microservices Architecture Using a Trusted Platform Module Applied to Electric Vehicle Charging Stations. Energies 2023, 16, 4285. [Google Scholar] [CrossRef]
- Cavalcante, I.; Júnior, J.; Manzolli, J.A.; Almeida, L.; Pungo, M.; Guzman, C.P.; Morais, H. Electric Vehicles Charging Using Photovoltaic Energy Surplus: A Framework Based on Blockchain. Energies 2023, 16, 2694. [Google Scholar] [CrossRef]
- Waseem, M.; Adnan Khan, M.; Goudarzi, A.; Fahad, S.; Sajjad, I.A.; Siano, P. Incorporation of Blockchain Technology for Different Smart Grid Applications: Architecture, Prospects, and Challenges. Energies 2023, 16, 820. [Google Scholar] [CrossRef]
- Mololoth, V.K.; Saguna, S.; Åhlund, C. Blockchain and Machine Learning for Future Smart Grids: A Review. Energies 2023, 16, 528. [Google Scholar] [CrossRef]
- Zondervan, N.A.; Tolentino-Zondervan, F.; Moeke, D. Logistics Trends and Innovations in Response to COVID-19 Pandemic: An Analysis Using Text Mining. Processes 2022, 10, 2667. [Google Scholar] [CrossRef]
- Espina-Romero, L.; Guerrero-Alcedo, J.; Noroño Sánchez, J.G.; Ochoa-Díaz, A. What Are the Topics That Business Ecosystems Navigate? Updating of Scientific Activity and Future Research Agenda. Sustainability 2022, 14, 16224. [Google Scholar] [CrossRef]
- Guo, W.; Chang, Z.; Su, Y.; Guo, X.; Hämäläinen, T.; Li, J.; Li, Y. Reputation-Based Blockchain for Spatial Crowdsourcing in Vehicular Networks. Appl. Sci. 2022, 12, 11049. [Google Scholar] [CrossRef]
- Teimoori, Z.; Yassine, A. A Review on Intelligent Energy Management Systems for Future Electric Vehicle Transportation. Sustainability 2022, 14, 14100. [Google Scholar] [CrossRef]
- Biegańska, M. IoT-Based Decentralized Energy Systems. Energies 2022, 15, 7830. [Google Scholar] [CrossRef]
- Seven, S.; Yoldas, Y.; Soran, A.; Yalcin Alkan, G.; Jung, J.; Ustun, T.S.; Onen, A. Energy Trading on a Peer-to-Peer Basis between Virtual Power Plants Using Decentralized Finance Instruments. Sustainability 2022, 14, 13286. [Google Scholar] [CrossRef]
- Enescu, F.M.; Birleanu, F.G.; Raboaca, M.S.; Bizon, N.; Thounthong, P. A Review of the Public Transport Services Based on the Blockchain Technology. Sustainability 2022, 14, 13027. [Google Scholar] [CrossRef]
- Kakkar, R.; Gupta, R.; Agrawal, S.; Tanwar, S.; Altameem, A.; Altameem, T.; Sharma, R.; Turcanu, F.-E.; Raboaca, M.S. Blockchain and IoT-Driven Optimized Consensus Mechanism for Electric Vehicle Scheduling at Charging Stations. Sustainability 2022, 14, 12800. [Google Scholar] [CrossRef]
- Trivedi, M.; Kakkar, R.; Gupta, R.; Agrawal, S.; Tanwar, S.; Niculescu, V.-C.; Raboaca, M.S.; Alqahtani, F.; Saad, A.; Tolba, A. Blockchain and Deep Learning-Based Fault Detection Framework for Electric Vehicles. Mathematics 2022, 10, 3626. [Google Scholar] [CrossRef]
- Roozbehani, M.M.; Heydarian-Forushani, E.; Hasanzadeh, S.; Elghali, S.B. Virtual Power Plant Operational Strategies: Models, Markets, Optimization, Challenges, and Opportunities. Sustainability 2022, 14, 12486. [Google Scholar] [CrossRef]
- Khan, H.; Masood, T. Impact of Blockchain Technology on Smart Grids. Energies 2022, 15, 7189. [Google Scholar] [CrossRef]
- Kaushal, R.K.; Agal, S.; Singh, N.B.R.; Singh, P.P. SVM Modeling Simulation to Evaluate the Electric Vehicle Transmitting Points. In Proceedings of the 2023 International Conference on Advances in Computing, Communication and Applied Informatics (ACCAI), Chennai, India, 25–26 May 2023; pp. 1–7. [Google Scholar] [CrossRef]
- Ashfaq, T.; Khalid, M.I.; Ali, G.; Affendi, M.E.; Iqbal, J.; Hussain, S.; Ullah, S.S.; Yahaya, A.S.; Khalid, R.; Mateen, A. An Efficient and Secure Energy Trading Approach with Machine Learning Technique and Consortium Blockchain. Sensors 2022, 22, 7263. [Google Scholar] [CrossRef]
- Xue, F.; Chang, K.; Li, W.; Wang, Q.; Zhao, H.; Zhang, H.; Ni, Y.; Xia, W. Blockchain Smart Contract-Enabled Secure Energy Trading for Electric Vehicles. Energies 2022, 15, 6733. [Google Scholar] [CrossRef]
- Wang, N.; Garg, A.; Su, S.; Mou, J.; Gao, L.; Li, W. Echelon Utilization of Retired Power Lithium-Ion Batteries: Challenges and Prospects. Batteries 2022, 8, 96. [Google Scholar] [CrossRef]
- Ghobadpour, A.; Monsalve, G.; Cardenas, A.; Mousazadeh, H. Off-Road Electric Vehicles and Autonomous Robots in Agricultural Sector: Trends, Challenges, and Opportunities. Vehicles 2022, 4, 843–864. [Google Scholar] [CrossRef]
- Kakkar, R.; Gupta, R.; Agrawal, S.; Bhattacharya, P.; Tanwar, S.; Raboaca, M.S.; Alqahtani, F.; Tolba, A. Blockchain and Double Auction-Based Trustful EVs Energy Trading Scheme for Optimum Pricing. Mathematics 2022, 10, 2748. [Google Scholar] [CrossRef]
- Appasani, B.; Mishra, S.K.; Jha, A.V.; Mishra, S.K.; Enescu, F.M.; Sorlei, I.S.; Bîrleanu, F.G.; Takorabet, N.; Thounthong, P.; Bizon, N. Blockchain-Enabled Smart Grid Applications: Architecture, Challenges, and Solutions. Sustainability 2022, 14, 8801. [Google Scholar] [CrossRef]
- Miao, J. Design of a Data Security Access Control Algorithm for the Electric Vehicle Internet of Vehicles Based on Blockchain Technology. World Electr. Veh. J. 2022, 13, 111. [Google Scholar] [CrossRef]
- Juszczyk, O.; Shahzad, K. Blockchain Technology for Renewable Energy: Principles, Applications and Prospects. Energies 2022, 15, 4603. [Google Scholar] [CrossRef]
- Xiao, J.; Hou, W. Cost Estimation Process of Green Energy Production and Consumption Using Probability Learning Approach. Sustainability 2022, 14, 7091. [Google Scholar] [CrossRef]
- Kapassa, E.; Themistocleous, M. Blockchain Technology Applied in IoV Demand Response Management: A Systematic Literature Review. Future Internet 2022, 14, 136. [Google Scholar] [CrossRef]
- Rimal, B.P.; Kong, C.; Poudel, B.; Wang, Y.; Shahi, P. Smart Electric Vehicle Charging in the Era of Internet of Vehicles, Emerging Trends, and Open Issues. Energies 2022, 15, 1908. [Google Scholar] [CrossRef]
- Kapassa, E.; Themistocleous, M.; Christodoulou, K.; Iosif, E. Blockchain Application in Internet of Vehicles: Challenges, Contributions and Current Limitations. Future Internet 2021, 13, 313. [Google Scholar] [CrossRef]
- Santos, J.B.; Francisco, A.M.B.; Cabrita, C.; Monteiro, J.; Pacheco, A.; Cardoso, P.J.S. Development and Implementation of a Smart Charging System for Electric Vehicles Based on the ISO 15118 Standard. Energies 2024, 17, 3045. [Google Scholar] [CrossRef]
- Uribe-Pérez, N.; Gonzalez-Garrido, A.; Gallarreta, A.; Justel, D.; González-Pérez, M.; González-Ramos, J.; Arrizabalaga, A.; Asensio, F.J.; Bidaguren, P. Communications and Data Science for the Success of Vehicle-to-Grid Technologies: Current State and Future Trends. Electronics 2024, 13, 1940. [Google Scholar] [CrossRef]
- Kirchner, S.R. OCPP Interoperability: A Unified Future of Charging. World Electr. Veh. J. 2024, 15, 191. [Google Scholar] [CrossRef]
- Boutsiadis, E.; Pasialis, N.; Lettas, N.; Tsiamitros, D.; Stimoniaris, D. Distributed Generation Control Using Ripple Signaling and a Multiprotocol Communication Embedded Device. Energies 2023, 16, 7604. [Google Scholar] [CrossRef]
- Zeinali, M.; Erdogan, N.; Bayram, I.S.; Thompson, J.S. Impact of Communication System Characteristics on Electric Vehicle Grid Integration: A Large-Scale Practical Assessment of the UK’s Cellular Network for the Internet of Energy. Electricity 2023, 4, 309–319. [Google Scholar] [CrossRef]
- Sánchez Díaz, C.A.; Díaz Lucio, A.S.; Salazar-Cabrera, R.; Pachón de la Cruz, Á.; Madrid Molina, J.M. Prototype of a System for Tracking Transit Service Based on IoV, ITS, and Machine Learning. World Electr. Veh. J. 2023, 14, 261. [Google Scholar] [CrossRef]
- Park, S.; Lee, E.; Noh, Y.-H.; Choi, D.-H.; Yook, J.-g. Accurate Modeling of CCS Combo Type 1 Cable and Its Communication Performance Analysis for High-Speed EV-EVSE Charging System. Energies 2023, 16, 5947. [Google Scholar] [CrossRef]
- Babangida, A.; Light Odazie, C.M.; Szemes, P.T. Optimal Control Design and Online Controller-Area-Network Bus Data Analysis for a Light Commercial Hybrid Electric Vehicle. Mathematics 2023, 11, 3436. [Google Scholar] [CrossRef]
- Jeffrey, N.; Tan, Q.; Villar, J.R. A Review of Anomaly Detection Strategies to Detect Threats to Cyber-Physical Systems. Electronics 2023, 12, 3283. [Google Scholar] [CrossRef]
- Dipon, W.; Gamboa, B.; Estrada, M.; Flynn, W.P.; Guo, R.; Bhalla, A. Self-Sustainable IoT-Based Remote Sensing Powered by Energy Harvesting Using Stacked Piezoelectric Transducer and Thermoelectric Generator. Micromachines 2023, 14, 1428. [Google Scholar] [CrossRef] [PubMed]
- Rathje, P.; Poirot, V.; Landsiedel, O. STARC: Decentralized Coordination Primitive on Low-Power IoT Devices for Autonomous Intersection Management. J. Sens. Actuator Netw. 2023, 12, 56. [Google Scholar] [CrossRef]
- Gwon, M.; Lee, K.; Park, J.; Kim, J. Establishment of Real-Time Simulation Test Environment for Electric Propulsion System of Unmanned Aerial Vehicle Using KDECAN Communication. Electronics 2023, 12, 3008. [Google Scholar] [CrossRef]
- Alden, R.E.; Gong, H.; Rooney, T.; Branecky, B.; Ionel, D.M. Electric Water Heater Modeling for Large-Scale Distribution Power Systems Studies with Energy Storage CTA-2045 Based VPP and CVR. Energies 2023, 16, 4747. [Google Scholar] [CrossRef]
- Kraemer, R.A.S.; Lodetti, P.Z.; Silva, A.C.d.; Cardoso, B.B.; Vicente, I.; Martins, M.A.I.; Simões, A.d.P.; Spader, N. Regulatory Challenges in the Electromobility Sector: An Analysis of Electric Buses in Brazil. Energies 2023, 16, 3510. [Google Scholar] [CrossRef]
- Rautenberg, P.; Weber, P.; Degel, J.P.; Hähnlein, S.; Gauterin, F.; Koch, T.; Doppelbauer, M.; Gohl, M. Electrified Powertrain Development: Distributed Co-Simulation Protocol Extension for Coupled Test Bench Operations. Appl. Sci. 2023, 13, 2657. [Google Scholar] [CrossRef]
- Alzahrani, A.; Wangikar, S.M.; Indragandhi, V.; Singh, R.R.; Subramaniyaswamy, V. Design and Implementation of SAE J1939 and Modbus Communication Protocols for Electric Vehicle. Machines 2023, 11, 201. [Google Scholar] [CrossRef]
- Anusha, T.; Pushpalatha, M. Efficient Communication Model for a Smart Parking System with Multiple Data Consumers. Smart Cities 2022, 5, 1536–1553. [Google Scholar] [CrossRef]
- Almuhaideb, A.M.; Algothami, S.S. Efficient Privacy-Preserving and Secure Authentication for Electric-Vehicle-to-Electric-Vehicle-Charging System Based on ECQV. J. Sens. Actuator Netw. 2022, 11, 28. [Google Scholar] [CrossRef]
- Basavaraj, D.; Tayeb, S. Towards a Lightweight Intrusion Detection Framework for In-Vehicle Networks. J. Sens. Actuator Netw. 2022, 11, 6. [Google Scholar] [CrossRef]
- Luciani, S.; Feraco, S.; Bonfitto, A.; Tonoli, A. Hardware-in-the-Loop Assessment of a Data-Driven State of Charge Estimation Method for Lithium-Ion Batteries in Hybrid Vehicles. Electronics 2021, 10, 2828. [Google Scholar] [CrossRef]
- Chen, T.; Li, X. (Semi-)Automatically Parsing Private Protocols for In-Vehicle ECU Communications. Entropy 2021, 23, 1495. [Google Scholar] [CrossRef]
- Habeeb, S.A.; Tostado-Véliz, M.; Hasanien, H.M.; Turky, R.A.; Meteab, W.K.; Jurado, F. DC Nanogrids for Integration of Demand Response and Electric Vehicle Charging Infrastructures: Appraisal, Optimal Scheduling and Analysis. Electronics 2021, 10, 2484. [Google Scholar] [CrossRef]
- Tramacere, E.; Luciani, S.; Feraco, S.; Bonfitto, A.; Amati, N. Processor-in-the-Loop Architecture Design and Experimental Validation for an Autonomous Racing Vehicle. Appl. Sci. 2021, 11, 7225. [Google Scholar] [CrossRef]
- Gehlot, A.; Alshamrani, S.S.; Singh, R.; Rashid, M.; Akram, S.V.; AlGhamdi, A.S.; Albogamy, F.R. Internet of Things and Long-Range-Based Smart Lampposts for Illuminating Smart Cities. Sustainability 2021, 13, 6398. [Google Scholar] [CrossRef]
- Chamberlain, K.; Al-Majeed, S. Standardisation of UK Electric Vehicle Charging Protocol, Payment and Charge Point Connection. World Electr. Veh. J. 2021, 12, 63. [Google Scholar] [CrossRef]
- Gaggero, G.B.; Marchese, M.; Moheddine, A.; Patrone, F. A Possible Smart Metering System Evolution for Rural and Remote Areas Employing Unmanned Aerial Vehicles and Internet of Things in Smart Grids. Sensors 2021, 21, 1627. [Google Scholar] [CrossRef]
- Mlýnek, P.; Rusz, M.; Benešl, L.; Sláčik, J.; Musil, P. Possibilities of Broadband Power Line Communications for Smart Home and Smart Building Applications. Sensors 2021, 21, 240. [Google Scholar] [CrossRef]
- Guerrero Alonso, J.I.; Personal, E.; García, S.; Parejo, A.; Rossi, M.; García, A.; Delfino, F.; Pérez, R.; León, C. Flexibility Services Based on OpenADR Protocol for DSO Level. Sensors 2020, 20, 6266. [Google Scholar] [CrossRef]
- Kaveh, M.; Martín, D.; Mosavi, M.R. A Lightweight Authentication Scheme for V2G Communications: A PUF-Based Approach Ensuring Cyber/Physical Security and Identity/Location Privacy. Electronics 2020, 9, 1479. [Google Scholar] [CrossRef]
- Kupzog, F.; Veichtlbauer, A.; Heinisch, A.; von Tüllenburg, F.; Langthaler, O.; Pache, U.; Jung, O.; Frank, R.; Dorfinger, P. The Impact of Virtualisation Techniques on Power System Control Networks. Electronics 2020, 9, 1433. [Google Scholar] [CrossRef]
- El Hariri, M.; Youssef, T.; Saleh, M.; Faddel, S.; Habib, H.; Mohammed, O.A. A Framework for Analyzing and Testing Cyber–Physical Interactions for Smart Grid Applications. Electronics 2019, 8, 1455. [Google Scholar] [CrossRef]
- Park, J.; Kim, H.; Choi, J.-Y. Improving TCP Performance in Vehicle-To-Grid (V2G) Communication. Electronics 2019, 8, 1206. [Google Scholar] [CrossRef]







| Data | Biometric Data | Driving Simulator Data | On-Board Sensor Data |
|---|---|---|---|
| Strengths | Simple, direct special sensor, high accuracy Easy to implement | Easy to do the test again with the ability to manually design driving situations and collect data on various working conditions. | Unbiased and realistic driving scenario and the information is reliable, accurate, and difficult to fake. Good real-time data at a reasonable price without compromising privacy. |
| Weakness | Built-in sensor surges hardware cost, and the device needs to manually activate image intrusion into personal privacy. | Distinct from actual operational circumstances, and the price of test facilities is not expensive for data accuracy. | Data gathering over the CAN bus protocol needs authorization and a significant expenditure in constructing a database. |
| Standard/Protocol | Use Cases |
|---|---|
| OCPP [129,130] | Billing, charging point operation, smart charging, charging session authorization, grid management, reservation |
| OCHP [129,130] | Reservation, charging session authorization, providing charging point data, smart charging, roaming |
| OCPI [129,130] | Reservation, charging session authorization, providing charging point data, smart charging, roaming |
| OSCP [129,130] | Distributing capacity budgets, utilizing these budgets to manage grid capacity, and smart charging by sharing capacity projections |
| OpenADR [129,130] | Smart charging, managing grid, handling registrations |
| eMIP [129,130] | Charging session authorization, roaming, facilitating smart charging features, billing |
| ISO15118 [129,130] | Schedule-based charging, charging session authorization, certificate handling |
| IEEE2030.5 [129,130] | Solutions for n-house smart grids, requesting action and load management, sharing metering information, publishing tariff details, text message sending, giving information on real consumption and invoicing, and reservation for energy flow. |
| IEC61850 [129,130] | Modeling of communication parameters, uniformity of message format, plug-and-play functionality for a variety of applications, including coordinating EV charging stations and operating virtual power plants. |
| Use Cases | OCPP [131] | OCHP [131] | OCPI [131] | OSCP [131] | Open ADR [131] | eMIP [131] | IEEE 2030.5 [131] | IEC 61851 [131] |
|---|---|---|---|---|---|---|---|---|
| Manage Grid | * | * | ||||||
| EV Charging | * | |||||||
| Handle Registration | * | * | * | |||||
| Billing | * | * | * | * | ||||
| Provide Charge Point Info | * | * | * | |||||
| Smart Charging | * | * | * | * | ||||
| Roaming | * | * | * |
| Communication Technology | Standard | Speed | Range | Frequency Spectrum |
|---|---|---|---|---|
| Zigbee | IEEE 802.15.4 [142] | 250 Kbps | 100 m | 2.4 GHz |
| LoRa/LoRaWAN | IEEE 802.15.g [142] | 27 Kbps | 10 km+ | 865–926 MHz |
| WiMAX | IEEE 802.16 [142] | 70 Mbps | 50 km+ | 2–11 GHz |
| Wi-Fi | IEEE 802.11 [142] | 100–250 Mbps | 100 mts+ | 2.4, 5 GHz |
| GSM/GPRS | ETSI | 114 Kbps | 35 km+ | 1800, 1900, 900 MHz |
| LTE | 3GPP | 0.1–1 Gbps | 28 km/10 km | 700–2600 MHz |
| Types of ML | Purpose |
|---|---|
| Supervised | Regression, Classification, Forecasting |
| Semi-supervised | Labeled as well as unlabeled data |
| Unsupervised | Clustering, Association, and Dimensionality reduction |
| Reinforcement | RNN, ANN |
| Big Data | Conventional Data | |
|---|---|---|
| Data Type | Structured, unstructured, semi-structured | Structured |
| Data Structure | Distributed | Centralized |
| Data Relationship | Complex | Uncertain |
| Data Volume | Petabytes and zettabytes | Terabytes |
| Blockchain Platforms | Industry Type | Ledger Type |
|---|---|---|
| XDC Network | Cross-Industry | Permission-less |
| Ethereum | Cross-Industry | Permission-less |
| Hyperledger Fabric | Cross-Industry | Permissioned |
| R3 Corda | Financial Services | Permissioned |
| Ripple | Financial Services | Permissioned |
| Hyperledger Fabric | Ethereum | |
|---|---|---|
| Private vs. Public | Private | Public |
| Governance | Federated | Decentralized |
| Permission | Permissioned | Permissionless |
| Smart Contract Languages | Javascript (Node.js), Java, Go | Vyper, Solidity |
| Private Transactions | Yes | No |
| Consensus Mechanism | Pluggable BFT | Proof-of-work |
| Speed | 3000 Tps | 15 Tps |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Rajamanickam, N.; Vishnuram, P.; Abraham, D.S.; Gono, M.; Kacor, P.; Mlcak, T. Review of Authentication, Blockchain, Driver ID Systems, Economic Aspects, and Communication Technologies in DWC for EVs in Smart Cities Applications. Smart Cities 2024, 7, 3121-3164. https://doi.org/10.3390/smartcities7060122
Rajamanickam N, Vishnuram P, Abraham DS, Gono M, Kacor P, Mlcak T. Review of Authentication, Blockchain, Driver ID Systems, Economic Aspects, and Communication Technologies in DWC for EVs in Smart Cities Applications. Smart Cities. 2024; 7(6):3121-3164. https://doi.org/10.3390/smartcities7060122
Chicago/Turabian StyleRajamanickam, Narayanamoorthi, Pradeep Vishnuram, Dominic Savio Abraham, Miroslava Gono, Petr Kacor, and Tomas Mlcak. 2024. "Review of Authentication, Blockchain, Driver ID Systems, Economic Aspects, and Communication Technologies in DWC for EVs in Smart Cities Applications" Smart Cities 7, no. 6: 3121-3164. https://doi.org/10.3390/smartcities7060122
APA StyleRajamanickam, N., Vishnuram, P., Abraham, D. S., Gono, M., Kacor, P., & Mlcak, T. (2024). Review of Authentication, Blockchain, Driver ID Systems, Economic Aspects, and Communication Technologies in DWC for EVs in Smart Cities Applications. Smart Cities, 7(6), 3121-3164. https://doi.org/10.3390/smartcities7060122







