Abstract
The rapid adoption of mobile banking applications has raised significant concerns about their security vulnerabilities. This study presents a comparative vulnerability analysis of mobile banking applications from Thai and non-Thai banks, utilising the OWASP Mobile Top 10 framework. Nine mobile banking applications (five Thai and four non-Thai) were assessed using three vulnerability detection tools: AndroBugs, MobSF, and QARK. The results showed that both Thai and non-Thai mobile banking applications had vulnerabilities across multiple OWASP Mobile Top 10 categories, with reverse engineering, code tampering, and insufficient cryptography being the most common. Statistical analysis revealed that Thai banking applications exhibited significantly more vulnerabilities compared to non-Thai banking applications. In the context of vulnerability detection tools, AndroBugs and QARK proved more effective in detecting vulnerabilities compared to MobSF. Additionally, the study highlights critical security challenges in mobile banking applications, particularly for Thai banks, and emphasises the need for enhanced security measures. The findings also show the importance of using multiple assessment tools for comprehensive security evaluation and suggest potential areas for improvement in mobile banking applications.
1. Introduction
Mobile banking has become increasingly popular in recent years, allowing users to conveniently perform financial transactions on their smartphones. Mobile banking applications in Thailand, like in many other countries, have gained significant popularity due to their convenience and accessibility. The Bank of Thailand reported in April 2024 that there were over 108 million active mobile banking accounts with over 2.6 billion transactions [1]. These numbers show that the use of mobile banking applications in Thailand has seen a rapid upsurge due to their convenience and accessibility. In the mobile applications and smartphone landscape, Android is the most used smartphone platform in Thailand, with a 64.73% market share as of February 2024 [2]. This is followed by Apple iOS with 34.2%. As a result of the increase in mobile application usage, especially on Android, cybersecurity is one of the major concerns among mobile users and developers. This is especially the case for mobile banking applications, which have to deal with users’ sensitive personal and financial data [3,4].
The challenges faced by mobile banking applications include the lack of security auditing and assessment, inadequate protection against cyber threats, the lack of security awareness on the users’ as well as developers’ part, and an increasing number of adversaries. It is, therefore, crucial to understand the vulnerabilities that these applications may possess [5]. Attackers can attempt to exploit these vulnerabilities to gain unauthorised access to users’ financial data, manipulate transactions, or inject malicious code into the application [3,5]. In the context of mobile application security, the Open Worldwide Application Security Project (OWASP) Foundation, formerly known as the Open Web Application Security Project, has compiled a list of the most common vulnerabilities found in mobile applications. Although the details of the vulnerabilities are provided in the subsequent section, the OWASP Mobile Top 10 vulnerabilities [6] include such issues as insecure authentication and authorisation, insecure communication, insecure data storage, and insufficient use of cryptography. While many researchers and developers analyse mobile application security using different approaches from the OWASP’s list of common vulnerabilities, they only cover some of the security concerns, not the whole list of OWASP [7].
For this reason, it is critical to conduct thorough vulnerability assessments of these mobile banking applications to identify and mitigate any potential security threats based on the list of OWASP Top 10 most common vulnerabilities in mobile applications. In contrast to prior studies [7,8,9], we aim to assess the vulnerability of Android mobile banking applications in Thailand with the highest number of users using AndroBugs, MobSF, and QARK, focusing on the OWASP Mobile Top 10. In addition, we analysed the security of four other mobile banking applications in Asian countries and compared the security level with the Thai applications. By evaluating these applications for common security weaknesses, we can gain valuable insights into the overall security posture of mobile banking applications in Thailand.
2. Background and Related Work
This section provides the foundational knowledge essential for understanding the vulnerability analysis conducted on mobile banking applications in this study. It includes an explanation of vulnerability analysis, an overview of the OWASP Mobile Top 10, and a review of the relevant literature concerning mobile application vulnerability assessment. These insights lay the groundwork for the primary objective of this research, which is to conduct vulnerability analysis on Thai mobile banking applications.
2.1. Mobile Application Vulnerability Analysis
In recent years, security threats on mobile platforms, particularly Android, have escalated, presenting a significant challenge. Not only has the frequency of attacks increased, but their severity has also intensified. As a result, mobile application users are at risk of losing sensitive data, and in some cases, they may even lose access to their smartphones entirely. This leads to a need for vulnerability analysis of mobile applications.
Vulnerability analysis in the context of cybersecurity can be defined as a test process used to identify and detect security-relevant issues that can create moderate or severe weaknesses in a system. From the attacker’s perspective, if weaknesses or vulnerabilities of a system are found, it is possible to exploit them so that damage to the system can occur. One method of vulnerability analysis is known as static application security testing (SAST) or static analysis [10], which is a method for automatically testing the security of the application without having to execute the code. On the fundamental level, this method ensures that any security issues in the application are detected. The other method of vulnerability analysis is dynamic application security testing (DAST) or dynamic analysis [10], which usually involves tracing the execution of the application to understand exactly how it operates. This approach can also involve the analysis of memory and how the application uses or accesses the memory of the system. In this research, the static analysis method was adopted to maintain consistency with other existing research [7,8].
The SAST process consists of five key steps. Initially, the information gathering phase involves analysing the application to identify its language, framework, and core functionalities. Subsequently, in the preparation step, any required reverse engineering is conducted to acquire the application’s source code for further analysis. The third stage entails scanning for vulnerabilities, during which an automated code scan is executed. Following this, the fourth step involves identifying security flaws and exploitable vulnerabilities within the code. Finally, the process finishes with the generation of a detailed report highlighting critical vulnerabilities detected.
Static and dynamic application security testing, as already mentioned, are fundamental components in the evaluation of vulnerabilities in mobile applications. Nevertheless, researchers have created specialised tools designed to suit the unique characteristics of mobile platforms. In this context, the discussion revolves around three vulnerability detection tools—AndroBugs, MobSF, and QARK—commonly utilised for the analysis of vulnerabilities in mobile applications.
AndroBugs is a Python-based open-source SAST framework designed for Android applications. It operates on Android Package Kit (APK) files and does not require root access on the device. This tool features a modular design that enables researchers to enhance its capabilities by incorporating custom vulnerability vectors. The primary advantage of AndroBugs lies in its efficiency. By utilising predefined vulnerability patterns, it can quickly examine applications, making it well-suited for large-scale assessments. Studies conducted by [11,12,13,14] utilised AndroBugs to examine a selection of popular Android applications, successfully identifying vulnerabilities such as insecure data storage and inadequate cryptography. The research highlights AndroBugs’ efficacy as an initial screening tool for identifying potential security flaws in mobile applications.
The Mobile Security Framework (MobSF), one of the most popular vulnerability scanners, is an open-source framework developed for conducting thorough security assessments of mobile applications. It features a modular design that integrates various static and dynamic analysis tools to identify vulnerabilities such as insecure data storage and weak cryptography through source code analysis. Moreover, it can scan applications to detect leaks of sensitive information and assess network security issues. Research studies, such as those conducted by [9,14,15], have demonstrated the efficacy of MobSF in uncovering a wide array of vulnerabilities in mobile applications.
The Quick Android Review Kit (QARK) is an open-source static analysis tool designed specifically for evaluating the security of Android applications. In contrast to AndroBugs, which primarily focuses on known vulnerabilities, QARK conducts a more in-depth examination by inspecting the source code of the application. By employing static code analysis methods, QARK can detect various security issues such as insecure communication channels and inadequate encryption implementations. Moreover, a study conducted by [15] applied QARK to assess a selection of banking applications, successfully identifying vulnerabilities associated with insecure data transmission and weak user authentication mechanisms. This research highlights QARK’s efficacy in identifying security flaws that could be exploited by potential adversaries. While QARK provides a more thorough analysis compared to AndroBugs and MobSF, it is not suitable for users who are unfamiliar with Android application development to interpret the findings.
These tools, in conjunction with SAST and DAST, offer a valuable collection of resources for researchers and cybersecurity experts to detect and mitigate vulnerabilities that could be present in mobile banking applications. The choice of the most suitable toolset depends on variables such as the unique features of the application, the proficiency of the analyst, and the extent of thoroughness required in the evaluation process.
2.2. Mobile Security Threats
In today’s digital landscape, ensuring the security of mobile applications has gained significant importance, especially in the context of financial transactions. Given that mobile banking applications manage confidential user data and financial details, they are highly susceptible to cyber threats. In response to these security challenges, the Open Worldwide Application Security Project (OWASP) introduced the OWASP Mobile Top 10, which is a valuable reference point for developers and cybersecurity experts.
This well-regarded framework identifies and classifies the ten most common security risks associated with mobile applications. It plays a vital role in shaping our research endeavours by directing our focus towards the vulnerabilities that are most prone to exploitation within mobile banking applications.
The list of common cyber threats of mobile applications and their descriptions as compiled by OWASP Mobile Top 10 [6] is provided in Table 1.

Table 1.
OWASP Mobile Top 10.
Our research aims to enhance the security of mobile banking applications by identifying and mitigating the cybersecurity risks provided by the OWASP Mobile Top 10 in Table 1. This effort is intended to strengthen user confidence and trust in utilising mobile platforms for financial transactions. By systematically evaluating the security weaknesses of mobile banking applications using the OWASP Mobile Top 10, this research not only highlights common vulnerabilities but also uncovers potential regional differences that may influence security practices. Understanding these trends is crucial for stakeholders, including developers, customers, and financial institutions, as it enables them to tailor their security measures to address specific vulnerabilities prevalent in their respective markets.
2.3. Related Work
The vulnerability analysis of mobile banking applications is a crucial aspect of ensuring the security of financial transactions. Several studies have focused on identifying vulnerabilities in mobile banking applications across different regions and countries. This section provides an overview of the existing research on vulnerability analysis in mobile banking applications.
In the global perspective of mobile banking applications, a study analysed the vulnerability of mobile banking and payment applications on Android in African countries [7]. The researchers used AndroBugs, a vulnerability scanner, to identify vulnerabilities in six digital banks’ Android applications. The results showed that all the scanned applications had vulnerabilities, with Revolut’s application having the highest number of identified vulnerabilities. Another study assessed the security and privacy features of mobile banking applications across multiple countries using the MobSF tool [16]. The results revealed various vulnerabilities, including insecure data storage, weak encryption, and the presence of sensitive information hardcoded in the application’s code. The researchers also stressed the need for comprehensive vulnerability assessment, including both static and dynamic analysis, to ensure the security of mobile banking applications.
Moreover, research focused on the vulnerability analysis of digital banks’ mobile applications in the United Kingdom (UK) [13]. The study also used AndroBugs to scan the applications. The results indicated that all the scanned applications had vulnerabilities. However, the study was limited to only six digital banks in the UK, and the findings may not be generalisable to other regions or a broader set of mobile banking applications. Apart from the UK, there was also a study that carried out a security analysis of mobile banking applications in Qatar [15]. This research used a combination of mobile testing frameworks to assess the security posture of two mobile banking applications. The results highlighted various security weaknesses, such as insecure data storage and the failure in hiding sensitive information in the application’s code, suggesting the need for a more robust security evaluation of mobile banking applications in the region. In addition, Chen et al. [4] explored the use of automated security vulnerability detection tools, such as AUSERA, to assess the security of mobile banking applications. The results demonstrated the effectiveness of these tools in identifying a wide range of vulnerabilities stated in the OWASP Mobile Top 10.
In the context of threat modelling and security analysis, Chattopadhyay and Sripada [17] provided a review of a threat modelling framework to detect and mitigate threats in mobile banking applications. The study highlighted the major threats to banking applications, including malware and serious crimes, and proposed strategies to address these threats. While the review was thorough, it did not provide empirical evidence or case studies to validate the proposed threat modelling framework.
Overall, the existing research illustrates the importance of vulnerability analysis in mobile banking applications. The studies demonstrate that mobile banking applications across different regions and countries have vulnerabilities that need to be addressed. The reviewed studies have used various vulnerability analysis tools, such as AndroBugs, MobSF, and QARK, to identify vulnerabilities in mobile banking applications. However, the studies have some limitations, such as focusing on a specific region or a limited set of mobile banking applications. This research aims to contribute to the existing body of knowledge by conducting a comprehensive vulnerability analysis of mobile banking applications in Thailand, focusing on identifying vulnerabilities so that the owners and developers of these applications can be aware, and the security of these applications can be improved. Additionally, while the existing literature has addressed various aspects of mobile banking security, there remains a notable gap in comparative studies that specifically analyse vulnerabilities of mobile banking applications from across different Asian countries. This makes our work different from the existing work in such a way that most research tends to focus on individual applications or localised studies. This study aims to fill this gap by examining the vulnerabilities of mobile banking applications from Thailand and other Asian countries, thereby contributing to a deeper understanding of the security landscape in this rapidly evolving sector.
3. Materials and Methods
This research adopts a quantitative approach to assess and compare vulnerabilities in mobile banking applications. Through the use of a systematic approach, the goal is to recognise and classify security flaws existing within these mobile banking applications. The research focuses on quantifiable data, including the number and types of vulnerabilities detected using an established framework, namely the OWASP Mobile Top 10. Additionally, statistical methods will be applied to compare the frequency and seriousness of vulnerabilities in Thai mobile banking applications with those from other countries. This approach allows for objective assessment and facilitates the generation of generalisable insights into the security status of mobile banking applications across different regions.
3.1. Sample Selection
This research focuses on identifying and comparing vulnerabilities in mobile banking applications. To achieve this, a purposive sampling strategy was employed. The target population for this study is defined as Thai mobile banking applications available for download on the Google Play Store.
Within this target population, five popular Thai mobile banking applications, whose true identities are not disclosed in this study and are hereby called Bank A, B, C, D, and E, were chosen for in-depth analysis. All of them have achieved more than ten million downloads each on the Google Play Store. This selection was based on download numbers retrieved from the Google Play Store. By focusing on these widely downloaded applications, the research aims to gain insights into the vulnerabilities present in mobile banking applications commonly used by Thai users. All of these banks are also classified as national-level banks since they operate and have customers from all over the country. Moreover, the selected banks are similar in terms of total assets. Analysing these applications allows for a more practical understanding of the security risks faced by a significant portion of the Thai mobile banking population. Table 2 provides details of Thai mobile banking applications chosen for the analysis in this research.

Table 2.
Thai Mobile Banking Applications Used in this Research.
For comparative purposes, a group of mobile banking applications from other Asian countries was also included in the study. Although these banks’ real names are not disclosed, we provide some details as a Chinese Bank, an Indian Bank, a Singaporean Bank, and a Korean Bank. The selection of these specific banks considered factors like regional representation and similar functionalities. They are also among the largest and most influential in their respective countries, and their mobile banking applications serve a significant portion of each country’s mobile banking users. Including applications from geographically diverse locations allows for a broader understanding of potential vulnerabilities across the Asia-Pacific region. Additionally, choosing banks with functionalities comparable to the Thai applications helps to ensure a more controlled comparison, minimising the influence of variations in features on the types of vulnerabilities identified. This comparative study offers an initial analysis among the studied mobile banking applications and assesses whether Thai applications exhibit unique vulnerability patterns compared to their counterparts in other countries.
Overall, our study aimed to compare the security vulnerabilities of mobile banking applications in Thailand and different Asian countries. Purposive sampling allowed us to deliberately select banks that would provide rich information relevant to our research questions. We selected banks with significant market presence in their respective countries. This criterion ensured that our study focused on applications used by a large number of customers, thereby increasing the relevance and potential impact of our findings. To enable cross-country comparisons, we purposefully included banks from different Asian countries. While we realised that this approach does not allow for generalisation to all banks in these countries, it should still provide valuable insights into potential differences in security practices across different markets. In addition, given the in-depth nature of our security analysis, purposive sampling allowed us to focus our resources on a manageable number of applications while still addressing our research objectives.
3.2. Vulnerability Analysis and Data Collection
This research employed a comprehensive approach to identify vulnerabilities within the selected mobile banking applications. The methodology involved integrating automated vulnerability assessment tools with a manual examination of the applications’ code.
Three primary SAST tools were used: AndroBugs version 1.0.0, MobSF version 3.7.9 Beta, and QARK version 4.0.0. AndroBugs, a Python-based SAST tool, was employed for its efficiency in rapid vulnerability detection. Its focus on predefined vulnerability patterns allowed for identification of common security weaknesses within the applications. MobSF provided a comprehensive suite of functionalities, including static code analysis, network traffic inspection, and API scanning capabilities. This allowed for a broad initial screening of potential vulnerabilities across various security threats. Finally, QARK, specifically designed for Android applications, offered a deeper analysis of the application’s source code, focusing on identifying vulnerabilities related to insecure components, communication channels, and cryptographic implementations.
The rationale behind using a combination of these SAST tools lies in their complementary functionalities. MobSF’s broad scope provided a starting point, while QARK’s specialisation in Android applications offered a more targeted analysis. AndroBugs’ efficiency helped ensure a more comprehensive assessment. Moreover, by integrating these tools, we enhance the robustness of our findings, ensuring a thorough examination of the vulnerabilities present in the selected mobile banking applications. This multi-faceted approach not only increases the likelihood of identifying critical security weaknesses but also provides a better understanding of the vulnerabilities specific to each application. Consequently, our findings are not only more reliable but also offer actionable insights for developers and financial institutions seeking to improve the security of their mobile banking platforms. This methodological thoroughness highlights the originality and significance of our research in the context of mobile banking security.
The next step was the data collection process, which involved a systematic analysis of each mobile banking application using the chosen SAST tools. Each application was uploaded to each of the SAST tools’ platforms, and the automated analysis features were executed. The generated reports were then reviewed, identifying potential vulnerabilities and their corresponding details. Moreover, the tools provided functionalities for exporting the application’s code in a more human-readable format (e.g., Smali code for QARK). This made the subsequent manual code review stage possible.
3.3. Data Analysis and Vulnerability Classification
Following the vulnerability identification process mentioned above, a systematic approach to data analysis was performed. This analysis involved two key steps: vulnerability classification and data comparison.
First, we aimed to classify the found vulnerabilities in mobile banking applications using the OWASP Mobile Top 10 framework. This industry-standard framework categorises the ten most commonly found mobile application security risks. Utilising the OWASP Mobile Top 10, we believe, provided a standardised reference point for classifying the identified vulnerabilities. Each vulnerability was carefully examined and mapped to the most relevant category within the OWASP framework. The vulnerability mapping process involved the following steps. First, we independently reviewed the vulnerability reports from the assessment tools. Second, group discussions were held to compare our individual interpretations and reach a consensus on the appropriate OWASP Mobile Top 10 category for each vulnerability. This categorisation process ensured consistency and facilitated meaningful comparisons between the vulnerabilities discovered in the Thai and non-Thai mobile banking applications. By applying this established framework, the research aimed to contribute to a broader understanding of the frequently found security weaknesses within mobile banking applications and to identify any potential trends in our sample.
Once the vulnerabilities were classified using the OWASP Mobile Top 10, statistical methods were applied to analyse the collected data. This analysis focused on comparing the occurrence and types of vulnerabilities between the Thai and non-Thai mobile banking applications. Statistical metrics such as frequency counts were used to determine the distribution of vulnerabilities across the OWASP Mobile Top 10 categories within the chosen applications. This comparative analysis aimed to identify potential regional variations in the security landscape of mobile banking applications. By analysing these trends, the research could explore potential explanations for observed differences and contribute to a more comprehensive understanding of the mobile banking security landscape across different regions.
Figure 1 summarises the research methodology. In other words, the process began with mobile banking application selection. Next, SAST analyses were performed using MobSF, QARK, and AndroBugs, which output initial vulnerability reports. All identified vulnerabilities were then classified by the OWASP Mobile Top 10. Finally, data analysis and comparison between Thai and non-Thai mobile banking applications were conducted.
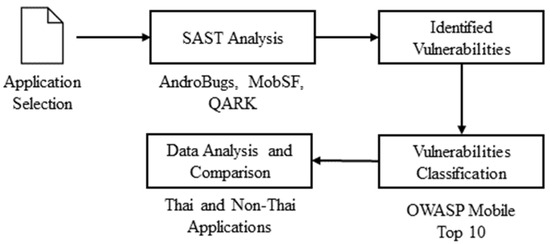
Figure 1.
Research Methodology.
4. Results and Discussion
This study conducted a comprehensive vulnerability analysis of five Thai mobile banking Android applications (Bank A, Bank B, Bank C, Bank D, and Bank E) and four international mobile banking applications (Chinese Bank, Indian Bank, Singaporean Bank, and Korean Bank). The analysis was performed using a combination of tools, including AndroBugs, MobSF, and QARK, to identify vulnerabilities according to the OWASP Mobile Top 10 framework.
The results of the vulnerability analysis provide valuable insights into the security posture of the selected mobile banking applications. By comparing the vulnerabilities identified in the Thai mobile banking applications with those of the international counterparts, this study offers a comparative perspective on the security landscape of mobile banking in Thailand and other regions. Furthermore, the effectiveness of the employed vulnerability analysis tools is discussed, highlighting their strengths and limitations in identifying security weaknesses in mobile banking applications.
4.1. Overall Vulnerability Assessment
Table 3 provides an overall assessment of the vulnerabilities found in each of the mobile banking applications using the three analysis tools, namely AndroBugs, MobSF, and QARK.

Table 3.
Results of Mobile Banking Application Vulnerability Assessment.
Our analysis of mobile banking applications from Thai and non-Thai banks revealed a concerning occurrence of security vulnerabilities across all examined applications. Using three different vulnerability assessment tools (AndroBugs, MobSF, and QARK), we evaluated the presence of the OWASP Mobile Top 10 vulnerabilities (M1–M10), which can be described as follows.
The most frequently found vulnerabilities across all examined applications were M9 (reverse engineering), detected in 85.2% of cases, followed by M8 (code tampering) at 77.8%, and M5 (insufficient cryptography) at 74.1%. Conversely, M2 (insecure data storage) was the least common, present in only 14.8% of cases. This suggests that while banks have made efforts to ensure that third-party libraries are secure, they may be neglecting other critical areas of mobile application security. To quantify the occurrence of vulnerabilities, we conducted a statistical analysis across all nine applications. The analysis is shown in Table 4 in the order of occurrence, together with the precision of our estimate based on the 95% confidence interval.

Table 4.
Overall Vulnerability Occurrence.
4.2. Comparison between Thai and Non-Thai Banks
A comparative analysis between Thai and non-Thai banks revealed a notable inconsistency in security measures. On average, Thai banks exhibited a higher number of vulnerabilities across all categories compared to their non-Thai counterparts. This difference was particularly pronounced in categories such as M9 (reverse engineering), M10 (extraneous functionality), and M5 (insufficient cryptography).
Among Thai banks, Bank A and Bank C showed the highest number of vulnerabilities (25 out of 30 possible detections), while Bank E demonstrated the best security posture with 18 out of 30 possible vulnerabilities detected. For non-Thai banks, the Indian Bank exhibited the highest number of vulnerabilities (20 out of 30 possible detections), whereas the Chinese Bank showed remarkably fewer vulnerabilities (just 5 out of 30 possible vulnerabilities).
Table 5 presents a comparative analysis of the overall security posture between Thai and non-Thai banks, using the mean total vulnerabilities as the key metric. This value represents the average number of vulnerabilities detected across all OWASP Mobile Top 10 categories and all three assessment tools (AndroBug, MobSF, and QARK) for each group of banks.

Table 5.
Comparison between Thai and Non-Thai Banks.
The results show a notable difference in the security posture between Thai and non-Thai banking applications, which can be explained as follows. The mean total number of vulnerabilities for Thai banks is 22.80 (S.D. = 3.42). This indicates that, on average, between 22 and 23 vulnerabilities were detected across all categories and tools in Thai banking applications. In contrast, non-Thai banks demonstrated a lower mean total vulnerability value of 14.25 (S.D. = 10.21), suggesting that fewer vulnerabilities were detected in these applications. For statistical significance, an independent samples t-test was conducted to compare these values. The analysis yielded a t-value of 2.35 with a p-value of 0.041. As this p-value is less than the conventional significance level of 0.05, we can conclude that the difference in total vulnerabilities between Thai and non-Thai banks is statistically significant.
For further analysis, we compared the average number of vulnerabilities detected per bank type (Thai versus non-Thai) for each vulnerability category. The results are shown in Table 6.

Table 6.
Comparison of Vulnerability Detected in Thai and Non-Thai Banking Applications.
Table 6 presents a detailed comparison of the average number of vulnerabilities detected for Thai and non-Thai banks across each of the OWASP Mobile Top 10 vulnerability categories (M1–M10). This granular analysis provides insights into the specific security challenges faced by each group of banks.
The first key finding is the consistent trend shown by Thai banking applications across all vulnerability categories. Thai banking applications show a higher average number of detected vulnerabilities compared to non-Thai banking applications. This aligns with the overall findings presented in Table 5, reinforcing the observation that Thai banks’ mobile applications generally exhibit more security vulnerabilities. Moreover, in terms of most prevalent vulnerabilities, M9 (reverse engineering) shows the highest average (5.0), followed closely by M10 (extraneous functionality) and M5 (insufficient cryptography), which showed the average of 4.6 and 4.4, respectively. For non-Thai banking applications, however, M8 (code tampering) has the highest average (3.25), followed by M9 (2.75) and M5 (2.5).
The most substantial differences between Thai and non-Thai banks can be observed in M10, whose average number of detected vulnerabilities is 4.6 for the Thai banking applications and only 2.0 for the non-Thai banking applications. The vulnerabilities M9 (5.0 and 2.75) and M4 (4.0 and 2.25) also exhibit the largest differences between the Thai and non-Thai banks. In contrast, the vulnerabilities M8 and M2 show the smallest differences between the Thai and non-Thai banking applications. That is, the Thai banking applications have the average value of 4.2 compared with the value of 3.25 for the non-Thai applications in the M8 vulnerability. At the same time, the values of 1.2 and 0.5 in the M2 vulnerability are the averages of the Thai banking applications and non-Thai banking applications, respectively.
As analysed above, both groups of banks show the lowest average vulnerabilities in M2 (insecure data storage), suggesting this might be an area of relative strength in mobile banking security across the board. However, the high averages for M9, M8, and M5 across both groups indicate that reverse engineering, code tampering, and insufficient cryptography are the real challenges for mobile banking applications, regardless of the bank’s country of origin.
4.3. Effectiveness of Vulnerability Assessment Tools
Our study employed three distinct vulnerability assessment tools, namely AndroBugs, MobSF, and QARK. The results indicate varying levels of effectiveness among these tools. AndroBugs and QARK demonstrated similar performance, detecting 66 and 64 vulnerabilities, respectively, across all applications. In contrast, MobSF detected notably fewer vulnerabilities (39 in total). Table 7 presents a comparison of the effectiveness of the three vulnerability assessment tools used in this study. The effectiveness is measured by the mean number of vulnerabilities each tool detected across all analysed mobile banking applications.

Table 7.
Tool Effectiveness Comparison.
The key findings from Table 7 can be explained as follows. AndroBugs detected, on average, 7.33 vulnerabilities per application (S.D. = 3.20). This tool showed the highest mean detection rate among the three tools evaluated. QARK demonstrated similar performance to AndroBugs, identifying an average of 7.11 vulnerabilities per application (S.D. = 3.06). The closeness of these mean values suggests that AndroBugs and QARK have comparable effectiveness in detecting vulnerabilities in mobile banking applications. Finally, MobSF detected an average of 4.33 vulnerabilities per application (S.D. = 2.65), which is notably lower than both AndroBugs and QARK. This suggests that MobSF could be less effective in identifying vulnerabilities compared to the other two tools.
In addition, the standard deviations (S.D.) provide insight into the consistency of each tool’s performance across different applications. AndroBugs shows the highest variability (S.D. = 3.20), followed closely by QARK (S.D. = 3.06), while MobSF demonstrates the least variability (S.D. = 2.65). This suggests that while MobSF detects fewer vulnerabilities on average, its performance appears to be more consistent across different applications.
It is worth noting that each tool showed strengths in detecting specific types of vulnerabilities. For example, QARK consistently detected M1 (improper platform usage) vulnerabilities across all banks, while AndroBugs appeared more effective in identifying M2 (insecure data storage) issues. MobSF, despite detecting fewer vulnerabilities overall, was particularly effective in identifying M8 (code tampering) and M9 (reverse engineering) vulnerabilities.
These findings emphasise the importance of using multiple assessment tools to gain a comprehensive view of an application’s security posture, as each tool may have its own strengths and limitations. This observation is also aligned with that of Bassolé et al. [7] and Basavala et al. [16], who recognised that to achieve comprehensive vulnerability assessment, multiple tools would be required.
The security vulnerabilities identified in this study also have several important implications for mobile banking customers. First of all, the existence of vulnerabilities, such as reverse engineering and insufficient cryptography, suggests that customer data and financial information could be at risk. Customers using mobile banking applications with these vulnerabilities could potentially be exposed to data breaches, unauthorised access, and even financial fraud. Secondly, the difference in the number of vulnerabilities found in Thai and non-Thai mobile banking applications could impact customer trust and confidence. Customers may become hesitant to use banking applications if they believe them to be insecure. This leads to the third implication, where the awareness of security issues could influence how customers use mobile banking applications. In other words, they may limit their usage to basic functions and avoid conducting high-value transactions through these applications. This, in turn, would impact the utility of mobile banking services.
5. Conclusions
This study conducted a comprehensive vulnerability analysis of five Thai mobile banking Android applications and four international mobile banking applications. The analysis was performed using three vulnerability assessment tools, including AndroBugs, MobSF, and QARK, to identify vulnerabilities according to the OWASP Mobile Top 10 framework.
The results of the study revealed a high occurrence of certain vulnerabilities across all the examined applications, particularly the reverse engineering, code tampering, and insufficient cryptography vulnerabilities. The comparison between Thai and non-Thai banking applications demonstrated that Thai banking applications had a higher number of vulnerabilities across all vulnerability categories. On average, Thai banks exhibited 22.80 vulnerabilities per application, while non-Thai banks showed 14.25 vulnerabilities, a statistically significant difference of p = 0.041.
Furthermore, the comparison of the vulnerability assessment tools revealed that AndroBugs was the most effective in identifying vulnerabilities, followed by QARK and MobSF. This highlights the importance of using a multi-tool approach to conduct a thorough vulnerability analysis and ensure that a wide range of security issues are detected.
Overall, these findings emphasise the urgent need for enhanced security measures in mobile banking applications, particularly among Thai banks. The high number of detected vulnerabilities related to reverse engineering, code tampering, and insufficient cryptography suggests that these areas should be prioritised in security improvement efforts. Moreover, the difference between Thai and non-Thai banking applications indicates a potential need for stricter regulations or improved security practices in the Thai banking sector.
It is important to note that this study was limited to a specific set of banks and assessment tools. The sample size, while providing valuable insights, may not be representative of all mobile banking applications globally, including those from Europe and the U.S. Additionally, the rapid evolution of both mobile technologies and cyber threats means that the security landscape is continually changing. Therefore, future research could include a larger and more diverse sample of banks from various countries. The main reasons for the identified vulnerabilities, such as coding practices, development processes, and security awareness among mobile banking application developers, could also be explored and investigated. Finally, the correlation between the presence of these vulnerabilities and actual security breaches or financial losses could be examined.
Author Contributions
Conceptualisation, C.T. and S.B.; methodology, C.T. and S.B.; validation, S.B.; formal analysis, S.B.; experiments, S.T., J.R. and K.D.; writing—original draft preparation, S.B.; writing—review and editing, C.T. and S.B.; visualisation, S.B.; supervision, C.T. and S.B. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Data Availability Statement
The original contributions presented in the study are included in the article; further inquiries can be directed to the corresponding author.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Bank of Thailand Use of Mobile Banking and Internet Banking. Available online: https://app.bot.or.th/BTWS_STAT/statistics/BOTWEBSTAT.aspx?reportID=949&language=ENG (accessed on 20 July 2024).
- StatCounter Global Stats Mobile Operating System Market Share Thailand. Available online: https://gs.statcounter.com/os-market-share/mobile/thailand (accessed on 20 July 2024).
- Bhatnagar, S.; Malik, Y.; Butakov, S. Analysing Data Security Requirements of Android Mobile Banking Application. In Proceedings of the Intelligent, Secure, and Dependable Systems in Distributed and Cloud Environments, Vancouver, BC, Canada, 28–30 November 2018; Traore, I., Woungang, I., Ahmed, S.S., Malik, Y., Eds.; Springer International Publishing: Cham, Switzerland, 2018; pp. 30–37. [Google Scholar]
- Chen, S.; Fan, L.; Meng, G.; Su, T.; Xue, M.; Xue, Y.; Liu, Y.; Xu, L. An Empirical Assessment of Security Risks of Global Android Banking Apps. In Proceedings of the ACM/IEEE 42nd International Conference on Software Engineering, Seoul, Republic of Korea, 27 June–19 July 2020; Association for Computing Machinery: New York, NY, USA, 2020; pp. 1310–1322. [Google Scholar]
- Kouraogo, Y.; Zkik, K.; Idrissi, N.E.J.E.; Orhanou, G. Security Model on Mobile Banking Application: Attack Simulation and Countermeasures. Int. J. Intell. Enterp. 2017, 4, 155. [Google Scholar] [CrossRef]
- OWASP. OWASP Mobile Top 10|OWASP Foundation. Available online: https://owasp.org/www-project-mobile-top-10/ (accessed on 20 July 2024).
- Bassolé, D.; Koala, G.; Traoré, Y.; Sié, O. Vulnerability Analysis in Mobile Banking and Payment Applications on Android in African Countries. In Innovations and Interdisciplinary Solutions for Underserved Areas; Thorn, J.P.R., Gueye, A., Hejnowicz, A.P., Eds.; Lecture Notes of the Institute for Computer Sciences, Social Informatics and Telecommunications Engineering; Springer International Publishing: Cham, Switzerland, 2020; Volume 321, pp. 164–175. ISBN 978-3-030-51050-3. [Google Scholar]
- Tangari, G.; Ikram, M.; Sentana, I.W.B.; Ijaz, K.; Kaafar, M.A.; Berkovsky, S. Analyzing Security Issues of Android Mobile Health and Medical Applications. J. Am. Med. Inform. Assoc. 2021, 28, 2074–2084. [Google Scholar] [CrossRef] [PubMed]
- Kouliaridis, V.; Karopoulos, G.; Kambourakis, G. Assessing the Security and Privacy of Android Official ID Wallet Apps. Information 2023, 14, 457. [Google Scholar] [CrossRef]
- Li, J. Vulnerabilities Mapping Based on OWASP-SANS: A Survey for Static Application Security Testing (SAST). Ann. Emerg. Technol. Comput. (AETiC) 2020, 4, 1–8. [Google Scholar] [CrossRef]
- Darvish, H.; Husain, M. Security Analysis of Mobile Money Applications on Android. In Proceedings of the 2018 IEEE International Conference on Big Data (Big Data), Seattle, WA, USA, 10–13 December 2018; pp. 3072–3078. [Google Scholar]
- Montealegre, C.; Njuguna, C.R.; Malik, M.I.; Hannay, P.; McAteer, I.N. Security Vulnerabilities in Android Applications. In Proceedings of the Australian Information Security Management Conference, Perth, Australia, 5–6 December 2018. [Google Scholar] [CrossRef]
- Falade, P.; Ogundele, G. Vulnerability Analysis of Digital Banks’ Mobile Applications. arXiv 2023, arXiv:2302.07586. [Google Scholar] [CrossRef]
- Kishnani, U.; Noah, N.; Das, S.; Dewri, R. Assessing Security, Privacy, User Interaction, and Accessibility Features in Popular E-Payment Applications. In Proceedings of the 2023 European Symposium on Usable Security, Copenhagen, Denmark, 16–17 October 2023; Association for Computing Machinery: New York, NY, USA, 2023; pp. 143–157. [Google Scholar]
- Al-Delayel, S.A. Security Analysis of Mobile Banking Application in Qatar. arXiv 2023, arXiv:2202.00582. [Google Scholar] [CrossRef]
- Basavala, S.R.; Kumar, N.; Aggarwal, A. Mobile Applications—Vulnerability Assessment Through the Static and Dynamic Analysis; Atlantis Press: Amsterdam, The Netherlands, 2013; pp. 673–679. [Google Scholar]
- Chattopadhyay, A.; Sripada, D. Security Analysis and Threat Modelling of Mobile Banking Applications. In Proceedings of the 2023 14th International Conference on Computing Communication and Networking Technologies (ICCCNT), Delhi, India, 6–8 July 2023; pp. 1–6. [Google Scholar]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).