An Evaluation Survey of Knowledge-Based Approaches in Telecommunication Applications
Abstract
:1. Introduction
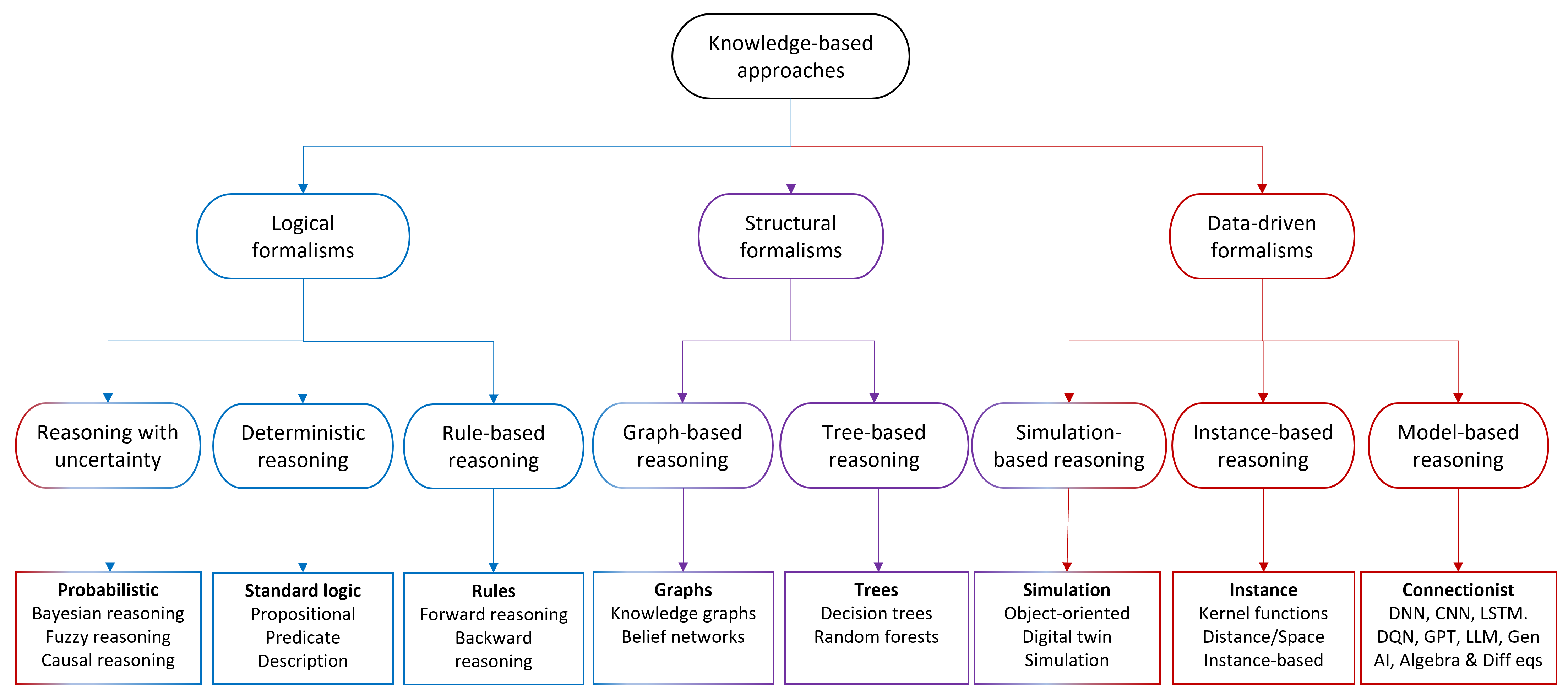
2. Knowledge-Based Approaches
2.1. Categories of Knowledge Representation and Reasoning Approaches
2.1.1. Probabilistic Formalisms
2.1.2. Standard Logic-Based Formalisms
2.1.3. Rule-Based Formalisms
2.1.4. Graph-Based Formalisms
2.1.5. Tree-Based Formalisms
2.1.6. Simulation-Based Formalisms
2.1.7. Instance-Based Formalisms
2.1.8. Neural Network-Based Formalisms
2.1.9. Generative AI-Based Formalisms
2.2. Knowledge-Based Applications
- Network operation—Different use cases may require different forms of knowledge representation and reasoning approaches. Network operation and management use cases that provide operation support based on human interaction greatly benefit from Generative AI. In Section 4.1, a description of such use cases is provided.
- Network automation—The are different approaches to realize automation in networks. One promising approach is intent-based networking automation. In Section 4.2, a description of a knowledge-assisted solution for intent-based automation is provided.
- Network optimization—Improving network performance for different use cases requires different network optimization approaches. For optimization in RAN, which is an inherently distributed network, one promising approach is distributed learning. In Section 4.3, a description of such approaches is provided.
3. Evaluation of Different Knowledge-Based Approaches
3.1. Assessment Criteria
- Knowledge formalism—Knowledge formalism refers to the specific language, representation framework, or set of rules used to express and structure knowledge within a knowledge representation system. It defines how information is encoded, stored, and manipulated to enable reasoning and inference.
- Knowledge accuracy—Accuracy refers to how well the knowledge representation reflects the true state of the world or domain it is intended to model. It manifests the degree to which the information encoded in the knowledge representation is correct and free from errors. High accuracy indicates that the knowledge representation provides a faithful reflection of reality, while low accuracy implies that it may contain inaccuracies or inaccurately represent aspects of the domain.
- Knowledge precision—Precision relates to the level of detail and specificity in the knowledge representation. It manifests how well the representation captures fine-grained distinctions, nuances, or specific aspects of the domain. High precision implies that the knowledge representation provides detailed and specific information, while low precision may result in a more abstract or generalized representation.
- Knowledge coverage—Coverage refers to the extent to which the knowledge representation includes relevant information about the domain. It manifests the comprehensiveness of the representation, indicating whether it covers all the necessary concepts, relationships, or facts related to the domain. High coverage implies that the representation includes a broad range of domain knowledge, while low coverage may result in gaps or missing information.
- Knowledge generalizability—Generalizability considers how well the knowledge or conclusions derived from the representation can apply to broader contexts or domains beyond the specific use case. It manifests the extent to which results can be generalized or adapted to different scenarios.
- Knowledge explainability—Explainability gauges how transparent and understandable the reasoning process and the conclusions drawn from the knowledge base are. It manifests the degree to which the representation facilitates mechanisms for generating explanations, justifications, or evidence to support the derived conclusions.
- Knowledge certainty—Certainty refers to the degree of confidence or trustworthiness associated with the knowledge encoded in the representation. It manifests how certain or reliable the information is in the reasoning process. High certainty implies a high degree of confidence in the knowledge, while low certainty indicates uncertainty or ambiguity.
- Knowledge consistency—Consistency pertains to the ability of the knowledge representation to handle conflicting or contradictory information and ensure coherence. It manifests how well the representation deals with conflicting facts or conclusions and resolves inconsistencies within the knowledge base.
- Knowledge confidence—Confidence assesses the levels of trust or belief in the conclusions drawn from the knowledge base. It manifests how confident one can be in the validity of the results obtained through reasoning with the represented knowledge.
- Knowledge expandability—Expandability refers to the capability of the knowledge representation to accommodate the derivation of new knowledge from existing facts or rules. It also manifests how easily new knowledge can be added to the representation.
- Knowledge scalability—Scalability relates to how well the knowledge representation can handle increasing complexity and size, particularly when dealing with large amounts of knowledge, complex relationships, or diverse domains. It manifests the ability to efficiently store, retrieve, and reason with knowledge.
3.2. Assessment Analysis Measurements
- Knowledge formalism—The choice of knowledge formalism can be assessed based on its expressive power, syntactic and semantic clarity, and adherence to the established standards. Evaluation involves considering how well the formalism captures the complexities of the domain, supports precise representation, and aligns with the requirements of the application. An indication of the level of knowledge formalism would be given by the percentage of relevant standards, like expressiveness, clarity, etc., met by the knowledge formalism.
- Knowledge accuracy—Accuracy in a formalism is measured by assessing the correspondence between the represented knowledge and the actual state of affairs. This can be performed via continued evaluations of the formalism’s performance in making correct inferences or predictions within the domain. An indication of knowledge accuracy would be given by the percentage of predictions or inferences that align with real-world data or expert assessments.
- Knowledge precision—Precision can be evaluated by examining the level of detail in the representation, such as the granularity of concepts, relationships, or constraints. A highly precise representation contains specific rules, attributes, or axioms that leave little room for ambiguity. An indication of knowledge precision would be given by the proportion of highly detailed rules or attributes in the knowledge base.
- Knowledge coverage—Coverage can be evaluated by comparing the knowledge representation to a comprehensive domain ontology or by assessing whether it includes all relevant concepts, entities, and relationships needed to address specific use cases or queries within the domain. An indication of knowledge coverage would be given by the extent to which the knowledge base covers the domain ontology’s concepts.
- Knowledge generalizability— Generalizability can be assessed by examining the performance and applicability of the knowledge representation across a range of related domains or use cases. It involves testing whether the knowledge and reasoning methods can be extended to diverse contexts effectively. An indication of knowledge generalizability would be given by the representation’s effectiveness when applied to different domains.
- Knowledge explainability—Explainability is measured by examining the degree to which formalism facilitates methods for generating human-readable explanations of the reasoning process, making it comprehensible to users or stakeholders. An indication of knowledge explainability would be given by the normalized length of the path from premises to conclusions of the reasoning processes.
- Knowledge certainty—Certainty can be quantified using probabilistic measures or certainty factors that assign degrees of belief or confidence to individual pieces of knowledge within the representation. An indication of knowledge certainty would be given by the probability of correct/incorrect individual knowledge pieces over the total of knowledge pieces.
- Knowledge consistency—Consistency can be assessed by checking whether the representation provides mechanisms to detect and resolve conflicts or contradictions, ensuring that the knowledge remains internally coherent. An indication of knowledge consistency would be given by the consistency of knowledge when comparing coherent pieces, i.e., non-conflicting knowledge pieces against the total.
- Knowledge confidence—Confidence in a formalism can be evaluated by examining its provisions for attaching confidence scores or measures to conclusions and assessing the mechanisms for assessing the reliability of knowledge sources. An indication of knowledge confidence would be given by statistical confidence or the confidence ratings given by users or experts.
- Knowledge expandability—Expandability can be evaluated by examining whether the representation supports mechanisms for inference, induction, or the incorporation of new facts, rules, or domain-specific knowledge over time. An indication of knowledge expandability would be given by the efficiency of deriving new insights relative to the addition of new knowledge.
- Knowledge scalability—Scalability can be assessed by evaluating the performance of the knowledge representation as the size and complexity of the knowledge base grow. It involves examining factors such as response times, resource utilization, and efficiency of storage. An indication of knowledge scalability would be given by the system’s performance under maximum load over its baseline performance.
3.3. Assessment Results
3.3.1. Bayesian/Causal Networks
3.3.2. Standard Logic-Based Formalisms
3.3.3. Rule-Based Formalisms
3.3.4. Graph-Based Formalisms
3.3.5. Tree-Based Formalisms
3.3.6. Simulation-Based Formalisms
3.3.7. Instance-Based Regression Formalisms
3.3.8. Neural Network-Based Formalisms
3.3.9. Generative AI-Based Formalisms
4. Knowledge-Driven Applications in Telecommunications
- -
- Efficient resource management—Knowledge-based systems aid in optimizing resource allocation, such as spectrum utilization, by intelligently predicting and adapting to network demands based on historical data and patterns. This improves overall network efficiency.
- -
- Enhanced network intelligence—By leveraging knowledge bases, wireless networks can make informed decisions in real time. This intelligence enables networks to adapt to changing conditions, predict potential issues, and proactively address them, leading to improved performance and reliability.
- -
- Dynamic network configuration—Knowledge-based applications facilitate dynamic reconfiguration of network parameters based on learned patterns, allowing networks to self-optimize and adapt to varying conditions, such as changes in user behavior or environmental factors.
- -
- Context-aware services—Knowledge-based systems enable the provision of context-aware services. By understanding user preferences, locations, and behaviors, wireless networks can deliver personalized and location-specific services, enhancing user experience.
- -
- Optimized quality of service (QoS)—Knowledge-based applications can predict network performance based on historical data and adjust parameters to ensure consistent QoS. This ensures that critical services receive adequate resources and prioritization.
- -
- Predictive Maintenance—Knowledge-based systems can predict potential failures or maintenance needs within wireless network components by analyzing historical performance data. This predictive capability minimizes downtime and prevents unexpected failures.
- -
- Improved security and anomaly detection—Knowledge-based approaches help in identifying abnormal network behavior by recognizing patterns that deviate from the norm. This aids in detecting anomalies and potential security threats, allowing for quicker responses to security breaches.
- -
- Resource optimization in dedicated networks—In dedicated environments, such as Internet-of-Things (IoT) and factory environments, knowledge-based systems can optimize device connectivity, manage data flows, and coordinate communication among devices, while ensuring efficient utilization of resources and minimizing energy consumption and communication delays.
4.1. Network Operations
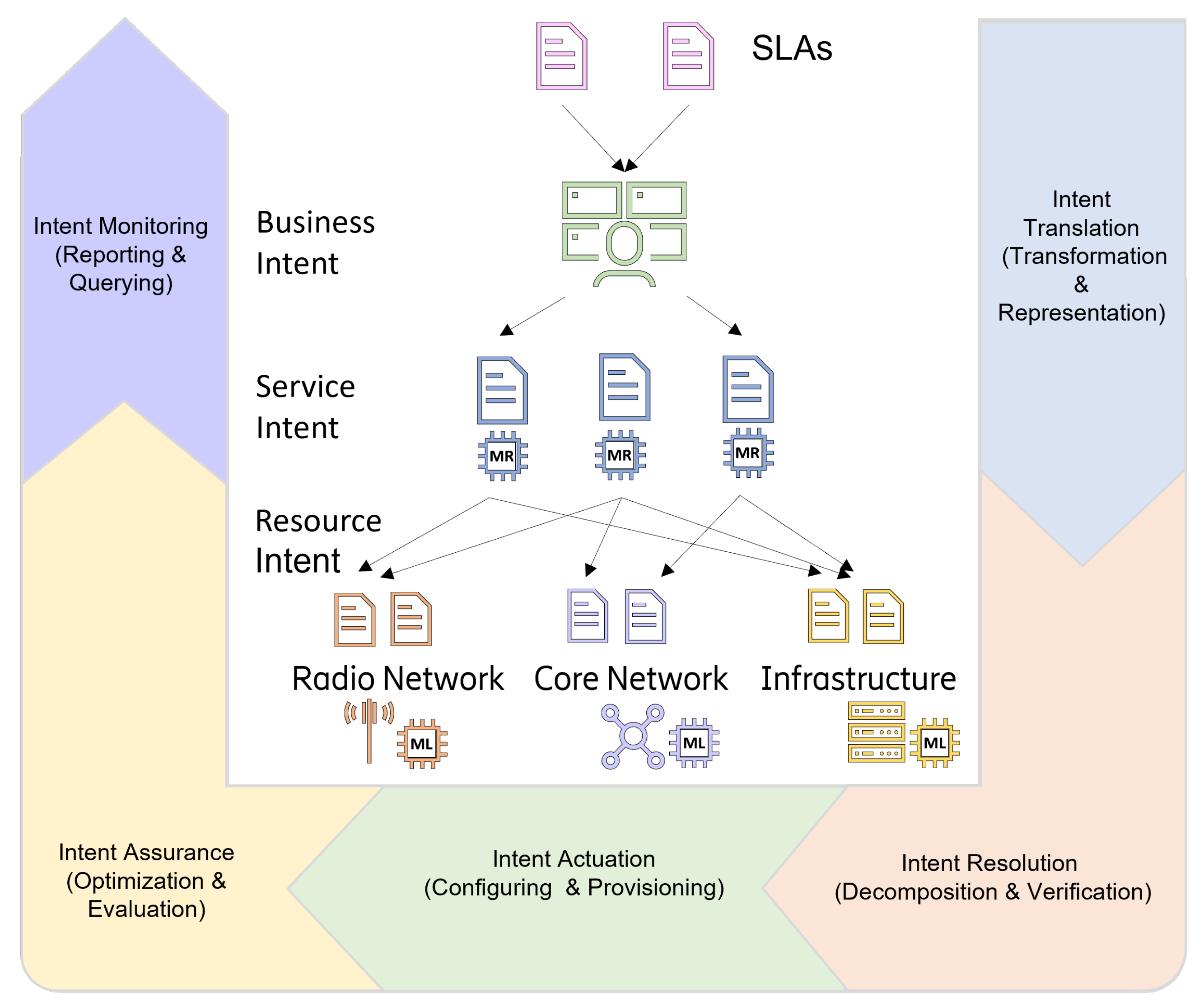
4.2. Network Automation
4.3. Network Optimization
- Federated learning—In federated learning (FL), multiple (possibly large numbers of) clients participate in the training of a shared global model by exchanging model updates with a central parameter server (PS) [43]. This is performed by using an iterative process where each global iteration, often referred to as communication round, is divided into three phases:
- The PS sends the current model parameter vector (an M-dimensional vector) to all participating clients. Either the model is sent directly, or a differential compared to the previous round is transmitted.
- The clients, the total number of which is N, perform one or more steps of stochastic gradient descent on their own (private) training data and obtain a model update. Specifically, the nth client computes a gradient update (M-dimensional vector).
- The M-dimensional model updates from the N clients are then sent back to the PS. The PS aggregates these updates by adding them together to obtain the updated model . A typical aggregation rule is to compute a weighted sum of the updates, that is, compute the M-dimensional total update for some weights . Other non-linear aggregation rules are also possible, for example, to safeguard against malicious or malfunctioning agents [44].
The above procedure is repeated until a termination criterion is met. The termination can, for example, be when a desirable training accuracy is achieved, when a predefined number of iteration rounds have been reached, or when a global loss function meets the minimum requirements. The loss function depends on the computational problem intended to be solved using the FL system, and typically, it represents a prediction error on a test dataset. The above procedures are depicted in Figure 5a. - Split learning—Split learning (SL) is another cooperative ML technique used to train a neural network model between a client and a central server by splitting the model at a cut layer into a client-side model and a server-side model [45]. The existing SL approach conducts the training process sequentially across clients, where each client calculates the intermediate results and transmits them to the next client in order. Each client passes the intermediate gradient in backward order when casting backward propagation. Furthermore, relevant features from the data are then transmitted to the central server which processes these features, performs the necessary computations, and sends back the updated parameters. This approach allows the sensitive data to remain on the client’s side, ensuring privacy, while still benefiting from the centralized server’s computational power. Split learning maintains a partition between data and computations, safeguarding user privacy during model training [46]. A depiction of SL is illustrated in Figure 5b;
- Fully distributed learning—In fully distributed learning setups, clients collaboratively perform learning without transmitting model updates to a central parameter server [47]. Instead, all clients have their own instance of the learning model. Each client has its own private training data. The clients are connected according to a connectivity graph such that each client has one or more neighbors. This scenario is illustrated in Figure 5c. The training proceeds by exchanging updates between the clients and their neighbors using, for instance, gossip-based averaging, where nodes iteratively share and merge information to collectively refine their local models. Fully distributed learning operates in a decentralized manner, promoting data locality and fostering collaboration among neighboring nodes while avoiding a central server’s reliance [48].
4.4. Limitations, Challenges, and Future Research
- -
- Data quality—Knowledge-based applications heavily rely on historical and real-time data and data quality. If data is inaccurate in case of data poisoning and harmful content or is incomplete or outdated, it can lead to incorrect decisions and predictions.
- -
- Initial training—Training certain knowledge-based models such as LLMs initially requires a substantial amount of data and computational resources. This can be a barrier to adoption, especially for smaller networks.
- -
- Data privacy—The collection and analysis of user data or exposure/training on a company’s proprietary data for knowledge-based applications raise privacy concerns. Striking a balance between data-driven insights and user privacy is a significant challenge in the case of private information exfiltration. There is a chance that the data being used for training is exposed in the output in the case of Generative AI type of use cases; therefore, data source and proper curating of data is very important.
- -
- Security—Protecting the knowledge base from intervention threats and ensuring the security of data used for training and decision-making is a significant challenge.
- -
- Trustworthiness—resilience, fairness/biases, and hallucinations are important challenges in Generative AI-based formalisms, where the research in this area is still fairly new.
- -
- Scalability—As wireless networks grow in size and complexity, managing and analyzing vast amounts of data can become challenging in wireless communication, and optimizing spectrum allocation and management in real-time is complex. Knowledge-based systems must adapt to changing spectrum conditions and demands. Complexity and scalability issues may arise in knowledge-based systems.
- -
- Resource consumption—Knowledge-based applications can be computationally intensive and costly, requiring significant processing power and memory. This can strain network resources, especially in resource-constrained environments.
- -
- Interoperability—Integrating knowledge-based systems with existing network infrastructure can be complex. Modern wireless networks encompass various technologies (e.g., 5G, IoT, and mobile edge computing) and require handling diverse types of data. Ensuring compatibility and smooth integration is a challenge.
- -
- Real-time decision making—Wireless networks are inherently dynamic, and adapting knowledge-based models to rapidly changing conditions can be difficult. Ensuring that knowledge-based systems can make timely decisions in dynamic environments is challenging.
- -
- Ethical considerations—The use of user data and AI algorithms in wireless networks raises ethical concerns, including bias in decision-making and the responsible use of AI technology.
- -
- Regulatory compliance—Compliance with data protection and privacy regulations, e.g., General Data Protection Regulation (GDPR), poses challenges for knowledge-based applications that involve user data.
- -
- Human–machine interaction—Ensuring that knowledge-based systems can effectively interact with human operators and users is a challenge, particularly in critical applications.
- -
- Cyber-security threats—In the age of digitization, protecting the knowledge base from cyber threats is a significant challenge for the protection of telecommunications businesses. Access to knowledge base contents implies access to critical business processes and technology know-how. Cyber attacks may enable the infection of knowledge bases with malicious knowledge and misbehaving models.
- i.
- Optimization of network operation including advanced self-optimized, self-configured, and self-healed networks where resource allocation is performed intelligently and in real-time based on context awareness and accurate data;
- ii.
- Security of knowledge utilization to improve privacy-preserving techniques and enhance security protocols in wireless networks. The former should aim at using knowledge representation to understand data sensitivity and reasoning to enforce data protection policies, while the latter should aim to understand complex attack patterns and to implement proactive defense mechanisms;
- iii.
- Automation where KRR and emerging technologies like 5G/6G, IoT, and edge computing are integrated to develop cross-domain applications enabling network automation;
- iv.
- User experience where KRR is utilized to model user preferences or behavior and to adapt network services accordingly for enhanced user experience. In addition, KRR can be also utilized to implement QoS-aware protocols that can dynamically adjust to meet the varying service quality requirements of different applications;
- v.
- Sustainability where KRR is applied to reduce the carbon footprint of wireless infrastructure and improve the energy-efficient operation of the network, as well as to model renewable energy sources while integrating them into the network’s energy management strategies;
- vi.
- Interoperability that require working towards standardizing KRR approaches for wireless networks to ensure interoperability between different systems and vendors, as well as collaborating with international bodies to develop guidelines and best practices for the introduction of KRR in telecommunications.
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Creswell, A.; White, T.; Dumoulin, V.; Arulkumaran, K.; Sengupta, B.; Bharath, A.A. Generative adversarial networks: An overview. IEEE Signal Process. Mag. 2018, 35, 53–65. [Google Scholar] [CrossRef]
- Gozalo-Brizuela, R.; Garrido-Merchan, E.C. A survey of Generative AI Applications. arXiv 2023, arXiv:2306.02781. [Google Scholar]
- Niemöller, J.; Sarmonikas, G.; Washington, N. Generating actionable insights from customer experience awareness. Ericsson Technol. Rev. 2016, 2020, 2–11. [Google Scholar]
- Niemöller, J.; Mokrushin, L. Cognitive technologies in network and business automation. Ericsson Technol. Rev. 2018, 6, 5. [Google Scholar]
- Inam, R.; Karapantelakis, A.; Vandikas, K.; Mokrushin, L.; Feljan, A.V.; Fersman, E. Towards automated service-oriented lifecycle management for 5G networks. In Proceedings of the 2015 IEEE 20th Conference on Emerging Technologies &Factory Automation(ETFA), Luxembourg, 8–11 September 2015; pp. 1–8. [Google Scholar]
- Conine, R. The data warehouse in the telecommunications industry. In Proceedings of the NOMS 98 1998 IEEE Network Operations and Management Symposium, New Orleans, LA, USA, 15–20 February 1998; Volume 1, pp. 205–209. [Google Scholar]
- Hossain, M.M.; Azim, T.; Karim, M.Y.; Hoque, A.S.M.L. Integrated data warehousing for telecommunication industries. In Proceedings of the 2009 12th International Conference on Computers and Information Technology, Dhaka, Bangladesh, 21–23 December 2009; pp. 657–662. [Google Scholar]
- Chaudhuri, B.G.; Rani, S. Future’s Backbone Network Monitoring With Metadata in Data Warehouse for Telecom Industry. In Proceedings of the 2023 International Conference on Computational Intelligence and Sustainable Engineering Solutions (CISES), Greater Noida, India, 28–30 April 2023; pp. 949–954. [Google Scholar]
- Haddad, M.; Altman, Z.; Elayoubi, S.E.; Altman, E. A Nash-Stackelberg Fuzzy Q-Learning Decision Approach in Heterogeneous Cognitive Networks. In Proceedings of the 2010 IEEE Global Telecommunications Conference GLOBECOM, Miami, FL, USA, 6–10 December 2010; pp. 1–6. [Google Scholar]
- Dirani, M.; Altman, Z. A cooperative Reinforcement Learning approach for Inter-Cell Interference Coordination in OFDMA cellular networks. In Proceedings of the 8th International Symposium on Modeling and Optimization in Mobile, Ad Hoc, and Wireless Networks, Avignon, France, 31 May–4 June 2010; pp. 170–176. [Google Scholar]
- Zhang, Z.; Lin, H.; Liu, K.; Wu, D. A hybrid fuzzy-based personalized recommender system for telecom products/services. Inf. Sci. 2013, 235, 117–129. [Google Scholar] [CrossRef]
- Abdallah, A.; Maarof, M.A.; Zainal, A. Fraud detection system: A survey. J. Netw. Comput. Appl. 2016, 68, 90–113. [Google Scholar] [CrossRef]
- Hilas, C.S. Designing an expert system for fraud detection in private telecommunications networks. Expert Syst. Appl. 2009, 36, 11559–11569. [Google Scholar] [CrossRef]
- Yoshinov, R.; Kulikov, I.; Zhukova, N. Methods of Composing Hierarchical Knowledge Graphs of Telecommunication Networks. Probl. Eng. Cybern. Robot. 2020, 72, 69–78. [Google Scholar] [CrossRef]
- Kulikov, I.; Vodyaho, A.; Stankova, E.; Zhukova, N. Ontology for Knowledge Graphs of Telecommunication Network Monitoring Systems. Comput. Sci. Appl. 2021, 21, 432–446. [Google Scholar]
- Quinlan, J.R. C4.5: Induction of decision trees. Mach. Learn. 1986, 1, 81–106. [Google Scholar] [CrossRef]
- Imtiaz, S.; Schiessl, S.; Koudouridis, G.P.; Gross, J. Coordinates-Based Resource Allocation Through Supervised Machine Learning. IEEE Trans. Cogn. Commun. Netw. 2021, 7, 1347–1362. [Google Scholar] [CrossRef]
- Öhlen, P.; Johnston, C.; Olofsson, H.; Terrill, S.; Chernogorov, F. Network digital twins—Outlook and opportunities. Ericsson Technol. Rev. 2023, 1, 11. [Google Scholar]
- Koudouridis, G.P.; Qvarfordt, C. A Method for the Generation of Radio Signal Coverage Maps for Dense Networks. In Proceedings of the 2018 IEEE International Conference on Communications (ICC), Kansas City, MO, USA, 20–24 May 2018; pp. 1–6. [Google Scholar]
- Zhou, Y.; Zhang, X.; Xing, Y.; Xie, Z. GAN-based Signal-to-Noise Ratio Prediction for Wireless Communication Systems. In Proceedings of the IEEE 91st Vehicular Technology Conference (VTC Spring), Antwerp, Belgium, 25–28 May 2020. [Google Scholar]
- Lin, F.; Zhang, Y.; Liu, X.; Dai, B.; Zhang, L.; Chen, X. GAN-based Channel Estimation for Wireless Communication Systems with Large-Scale Antenna Arrays. arXiv 2021, arXiv:2108.03881. [Google Scholar]
- Koudouridis, G.P.; He, Q.; Dán, G. An architecture and performance evaluation framework for artificial intelligence solutions in beyond 5G radio access networks. Wirel. Commun. Netw. 2022, 2022, 94. [Google Scholar] [CrossRef]
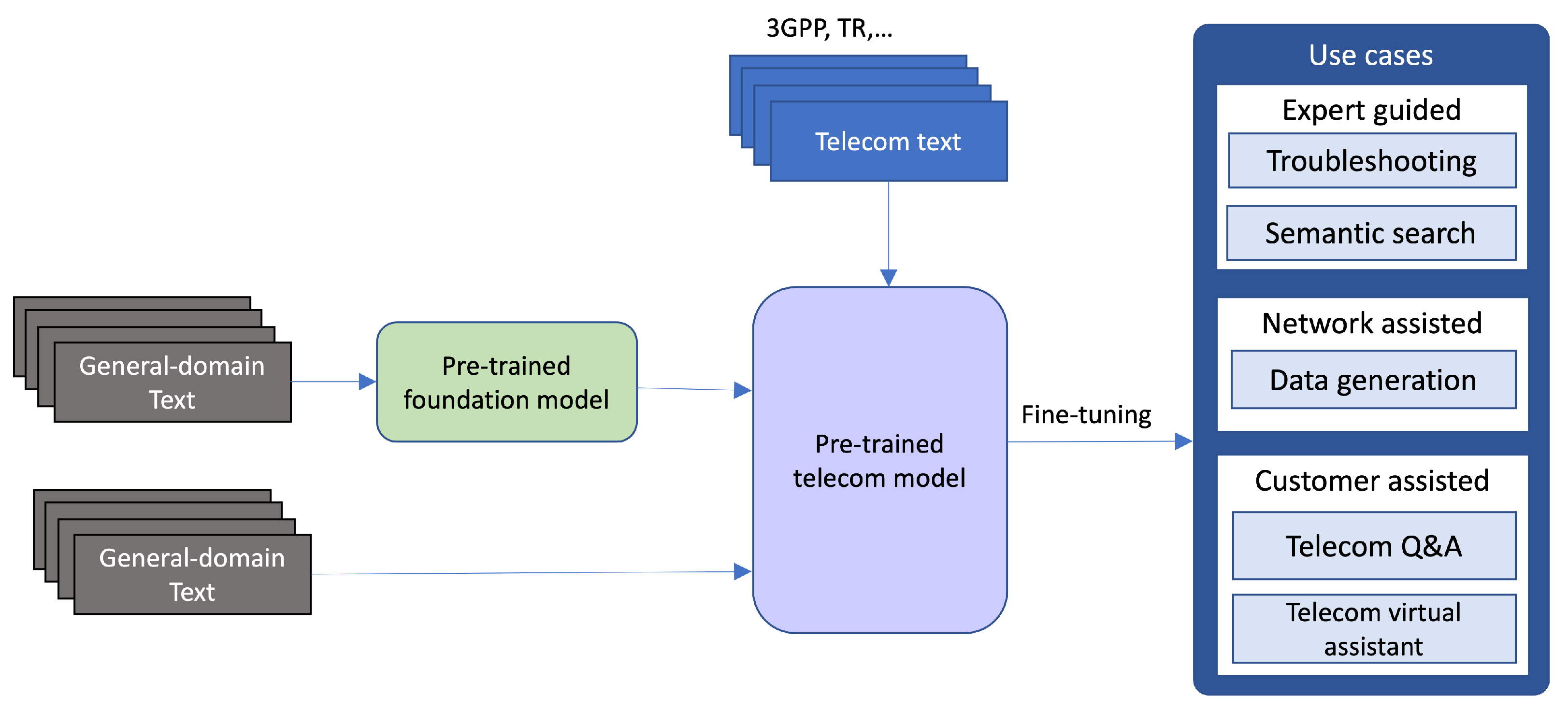
- Maatouk, A.; Piovesan, N.; Ayed, F.; Domenico, A.D.; Debbah, M. Large Language Models for Telecom: Forthcoming Impact on the Industry. arXiv 2023, arXiv:2308.06013. [Google Scholar]
- Zou, H.; Zhao, Q.; Bariah, L.; Bennis, M.; Debbah, M. Wireless Multi-Agent Generative AI: From Connected Intelligence to Collective Intelligence. arXiv 2023, arXiv:2307.02757. [Google Scholar]
- Bariah, L.; Zhao, Q.; Zou, H.; Tian, Y.; Bader, F.; Debbah, M. Large Language Models for Telecom: The Next Big Thing? arXiv 2023, arXiv:2306.10249. [Google Scholar]
- Ericsson Blog. 2021. Available online: https://www.ericsson.com/en/blog/2022/1/neural-language-models-telecom-domain (accessed on 17 January 2024).
- Holm, H. Bidirectional Encoder Representations from Transformers (BERT) for Question Answering in the Telecom Domain: Adapting a BERT-like Language Model to the Telecom Domain Using the ELECTRA Pre-Training Approach. Ph.D. Thesis, Royal Institute of Technology (KTH), Stockholm, Sweden, 2021. [Google Scholar]
- Grimalt, N.M.I.; Shalmashi, S.; Yaghoubi, F.; Jonsson, L.; Payberah, A.H. BERTicsson: A Recommender System For Troubleshooting. In Proceedings of the SDU@AAAI, Virtual, 1 March 2022. [Google Scholar]
- Bosch, N.; Shalmashi, S.; Yaghoubi, F.; Holm, H.; Gaim, F.; Payberah, A.H. Fine-Tuning BERT-based Language Models for Duplicate Trouble Report Retrieval. In Proceedings of the 2022 IEEE International Conference on Big Data, Osaka, Japan, 17–20 December 2022; pp. 4737–4745. [Google Scholar]
- Sun, X.; Holm, H.; Molavipour, S.; Gebre, F.G.; Pawar, K.R.Y.; Shalmashi, S. Recommendation System for Product Test Failures Using BERT. In Proceedings of the International Conference on Knowledge Discovery and Information Retrieval, KDIR, Rome, Italy, 13–15 November 2023. [Google Scholar]
- Bissessar, D.; Bois, A. Evaluation of Methods for Question Answering Data Generation: Using Large Language Models; Linköping University, Department of Computer: Linköping, Sweden, 2022. [Google Scholar]
- Gunnarsson, M. Multi-Hop Neural Question Answering in the Telecom Domain; LTH, Lund University: Lund, Sweden, 2021. [Google Scholar]
- ETSI. Zero Touch Network and Service Management (ZSM) Means of Automation; ETSI: Sophia Antipolis, France, 2018. [Google Scholar]
- Saha, B.K.; Tandur, D.; Haab, L.; Podleski, L. Intent-based networks: An industrial perspective. In Proceedings of the 1st International Workshop on Future Industrial Communication Networks, New Delhi, India, 2 November 2018; pp. 35–40. [Google Scholar]
- Clemm, A.; Ciavaglia, L.; Granville, L.; Tantsura, J. Intent-Based Networking—Concepts and Definitions; ITU: Geneva, Switzerland, 2021. [Google Scholar]
- Wei, Y.; Peng, M.; Liu, Y. Intent-based networks for 6G: Insights and challenges. Digit. Commun. Netw. 2020, 6, 270–280. [Google Scholar] [CrossRef]
- Du, Z.; Jiang, S.; Nobre, J.; Ciavaglia, L.; Behringer, M. ANIMA Intent Policy and Format, ANIMA WG; IETF: Fremont, CA, USA, 2016. [Google Scholar]
- Leivadeas, A.; Falkner, M. A Survey on Intent-Based Networking. IEEE Commun. Surv. Tutor. 2023, 25, 625–655. [Google Scholar] [CrossRef]
- Niemöller, J.; Silvander, J.; Stjernholm, P.; Angelin, L.; Eriksson, U. Autonomous networks with multi-layer intent-based operation. Ericsson Technol. Rev. 2023, 2023, 2–13. [Google Scholar] [CrossRef]
- Niemöller, J.; Szabó, R.; Zahemszky, A.; Roeland, D. Creating autonomous networks with intent-based closed loops. Ericsson Technol. Rev. 2022, 2022, 2–11. [Google Scholar] [CrossRef]
- Niemöller, J.; Mokrushin, L.; Mohalik, S.K.; Vlachou-Konchylaki, M.; Sarmonikas, G. Cognitive processes for adaptive intent-based networking. Ericsson Technol. Rev. 2020, 2020, 2–11. [Google Scholar] [CrossRef]
- Chen, M.; Gunduz, D.; Huang, K.; Saad, W.; Bennis, M.; Feljan, A.V.; Poor, H.V. Distributed learning in wireless networks: Recent progress and future challenges. IEEE J. Sel. Areas Commun. 2021, 39, 3579–3605. [Google Scholar] [CrossRef]
- Amiri, M.M.; G¨und¨uz, D. Federated learning over wireless fading channels. IEEE Trans. Wirel. Commun. 2020, 19, 3546–3557. [Google Scholar] [CrossRef]
- Blanchard, P.; Mhamdi, E.E.; Guerraoui, R.; Stainer, J. Machine learning with adversaries: Byzantine tolerant gradient descent. In Advances in Neural Information Processing Systems; Springer: Berlin/Heidelberg, Germany, 2017; Volume 30. [Google Scholar]
- Thapa, C.; Chamikara, M.A.P.; Camtepe, S. Splitfed: When federated learning meets split learning. arXiv 2020, arXiv:2004.12088. [Google Scholar] [CrossRef]
- Wu, W.; Li, M.; Qu, K.; Zhou, C.; Shen, X.; Zhuang, W.; Li, X.; Shi, W. Split Learning over Wireless Networks: Parallel Design and Resource Management. arXiv 2022, arXiv:2204.08119v2. [Google Scholar] [CrossRef]
- Liang, L.; Ye, H.; Li, G.Y. Spectrum sharing in vehicular networks based on multi-agent reinforcement learning. IEEE J. Sel. Areas Commun. 2019, 37, 2282–2292. [Google Scholar] [CrossRef]
- Assran, M.; Loizou, N.; Ballas, N.; Rabbat, M. Stochastic gradient push for distributed deep learning. In Proceedings of the 36th International Conference on Machine Learning, PMLR, Long Beach, CA, USA, 9–15 June 2019; Volume 97, pp. 344–353. [Google Scholar]


| Criteria | Relevant Assessment Defining Questions |
|---|---|
| Formalism | What formal language or representation framework is used to express knowledge? What is its expressive power and semantic clarity? Is knowledge represented in a clear, unambiguous, and straightforward manner? |
| Accuracy | How accurate is the representation of knowledge in reflecting the true state of the world? Can the knowledge base be evaluated for its overall correctness or accuracy? How many times is the knowledge overall correct? |
| Precision | Does the representation allow for precise and detailed domain descriptions? Does the same input give the same output? Can it capture fine-grained distinctions and nuances? Does it support the representation of explicit constraints to enforce precision? |
| Coverage | Is everything covered? How comprehensive is the representation in covering the relevant aspects of the domain? Does it handle missing or incomplete knowledge gracefully? Are there mechanisms to handle uncertainty or partial knowledge gaps? |
| Generalizability | Does it generalize properly or stand for a specialized objective? To what degree results can apply to a broader context? |
| Explainability | How transparent and explainable is the reasoning process and the conclusions drawn from the knowledge base? Does the representation provide mechanisms for generating explanations, justification, or evidence to support the derived conclusions? |
| Certainty | Does the representation support the encoding of uncertainty or degrees of belief? How certain is the representation of knowledge in the reasoning process? Is there a mechanism to quantify and reason with uncertain or probabilistic knowledge? |
| Consistency | Does the representation allow for the detection and resolution of conflicts between facts/conclusions? How sufficient are conflicting facts/conclusions resolved? Is there a mechanism to handle inconsistencies and ensure coherence in the knowledge base? |
| Confidence | Can the representation assign confidence levels to the conclusions drawn from the knowledge base? What are the levels of confidence? Are there mechanisms to assess the reliability or trustworthiness of the knowledge sources and inference results? |
| Expandability | Does the representation support the derivation of new knowledge from existing facts or rules? Are there mechanisms for logical inference or induction to generate new knowledge? Can the representation accommodate the evolution of knowledge over time? |
| Scalability | Can the representation handle complexity and scalability in time and space? Can it effectively handle large amounts of knowledge, complex relationships, or domains? Does it provide mechanisms for efficient storage, retrieval, and reasoning with knowledge? |
| Criteria Category | Quality Criteria 1 | Bayesian/ Causal 2 | Standard Logic | Rules | Graphs 3 | Trees 3 | Simulation | Instance | Neural Networks | LLMs/ Generative |
|---|---|---|---|---|---|---|---|---|---|---|
| Declarative | Formalism | High | High | High | High | Medium | Medium | Low | Low | Low |
| Accuracy | High | High | High | High | High | High | High | High | Medium | |
| Precision | High | High | High | High | Medium | High | Medium | Medium | Medium | |
| Coverage | Medium | Medium | Medium | High | Medium | High | Medium | Medium | Medium | |
| Generalizability | Medium | Medium | Medium | Medium | Medium | Medium | Low | Medium | High | |
| Explainability | Medium | High | High | High | High | Medium | Medium | Low | Low | |
| Procedural | Certainty | High | Medium | Medium | Medium | Low | Medium | Low | Low | Medium |
| Consistency | High | Medium | Medium | High | High | High | Medium | Medium | Medium | |
| Confidence | High | Low | Medium | Medium | Low | Medium | Low | Medium | Medium | |
| Expandability | High | High | High | High | Medium | Low | Low | Low | Low | |
| Scalability | Medium | Low | Low | High | Medium | Medium | High | Medium | Medium |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Koudouridis, G.P.; Shalmashi, S.; Moosavi, R. An Evaluation Survey of Knowledge-Based Approaches in Telecommunication Applications. Telecom 2024, 5, 98-121. https://doi.org/10.3390/telecom5010006
Koudouridis GP, Shalmashi S, Moosavi R. An Evaluation Survey of Knowledge-Based Approaches in Telecommunication Applications. Telecom. 2024; 5(1):98-121. https://doi.org/10.3390/telecom5010006
Chicago/Turabian StyleKoudouridis, Georgios P., Serveh Shalmashi, and Reza Moosavi. 2024. "An Evaluation Survey of Knowledge-Based Approaches in Telecommunication Applications" Telecom 5, no. 1: 98-121. https://doi.org/10.3390/telecom5010006








