The Impact of Spoofing Attacks in Connected Autonomous Vehicles under Traffic Congestion Conditions
Abstract
:1. Introduction
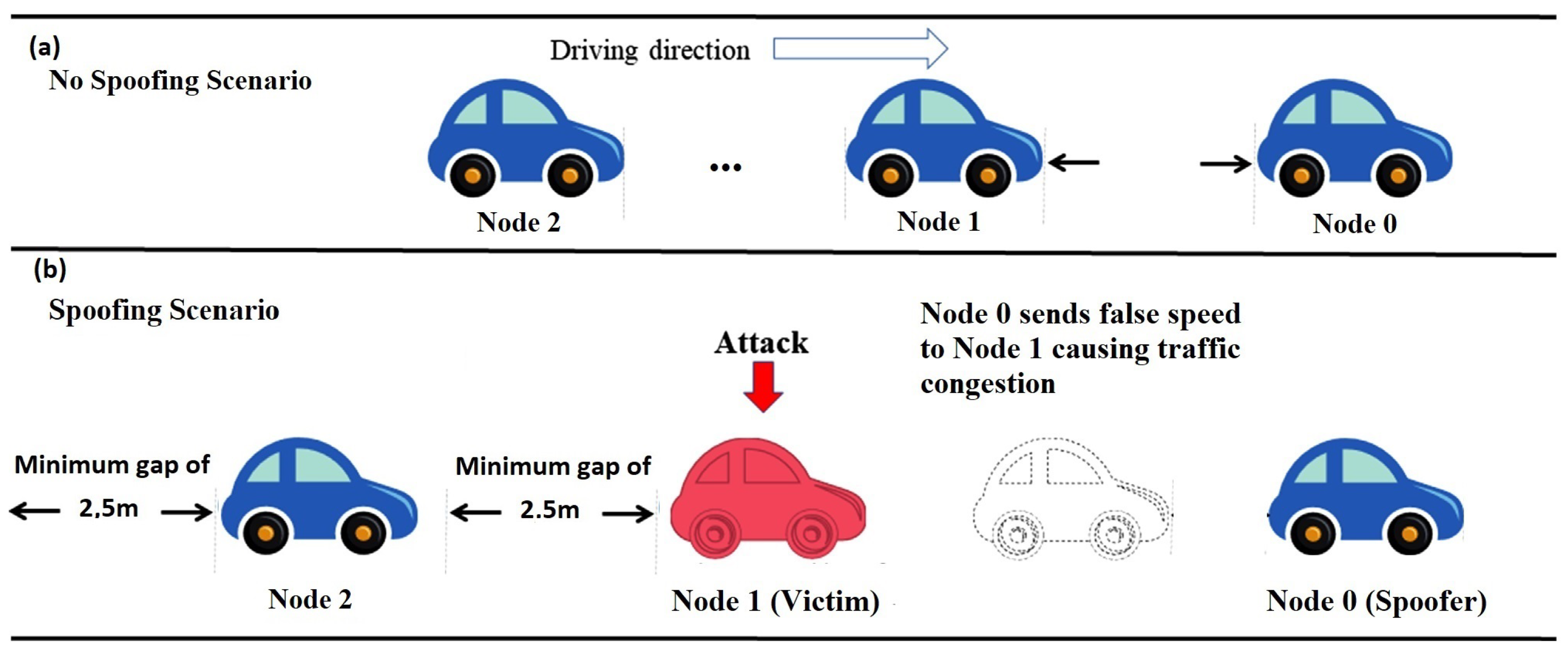
- We investigate the effects of a basic spoofing attack on a range of CAVs, that is generated in an ad-hoc fashion on the road and has some minimal security guarantees (i.e., minimum safety gap distance of 2.5 m and any member of the platoon is running a highly protected piece of code, whereby if it stops for a reasonable 10 s threshold, it alerts the following vehicles to change routes to reach their destination).
- We estimate the statistical measure of CoV and we prove that its absolute value increases under spoofing attack conditions. Moreover, without any cyber-attack, CoV remains at high levels, at about 23 for the speed parameter, under realistic traffic conditions for an urban environment, in contrast to theoretical studies, which indicate a value close to zero [8].
- Finally, we investigate how cross-layer parameters, such as PDR, impact the attack’s detection in a future detection system, and we observed how the attack causes a high volume of traffic in the wireless V2X network. This indicates higher vulnerability, a fact to be easily detected.
2. Related Work
3. System Model
3.1. Topology
3.2. Spoofing Attack
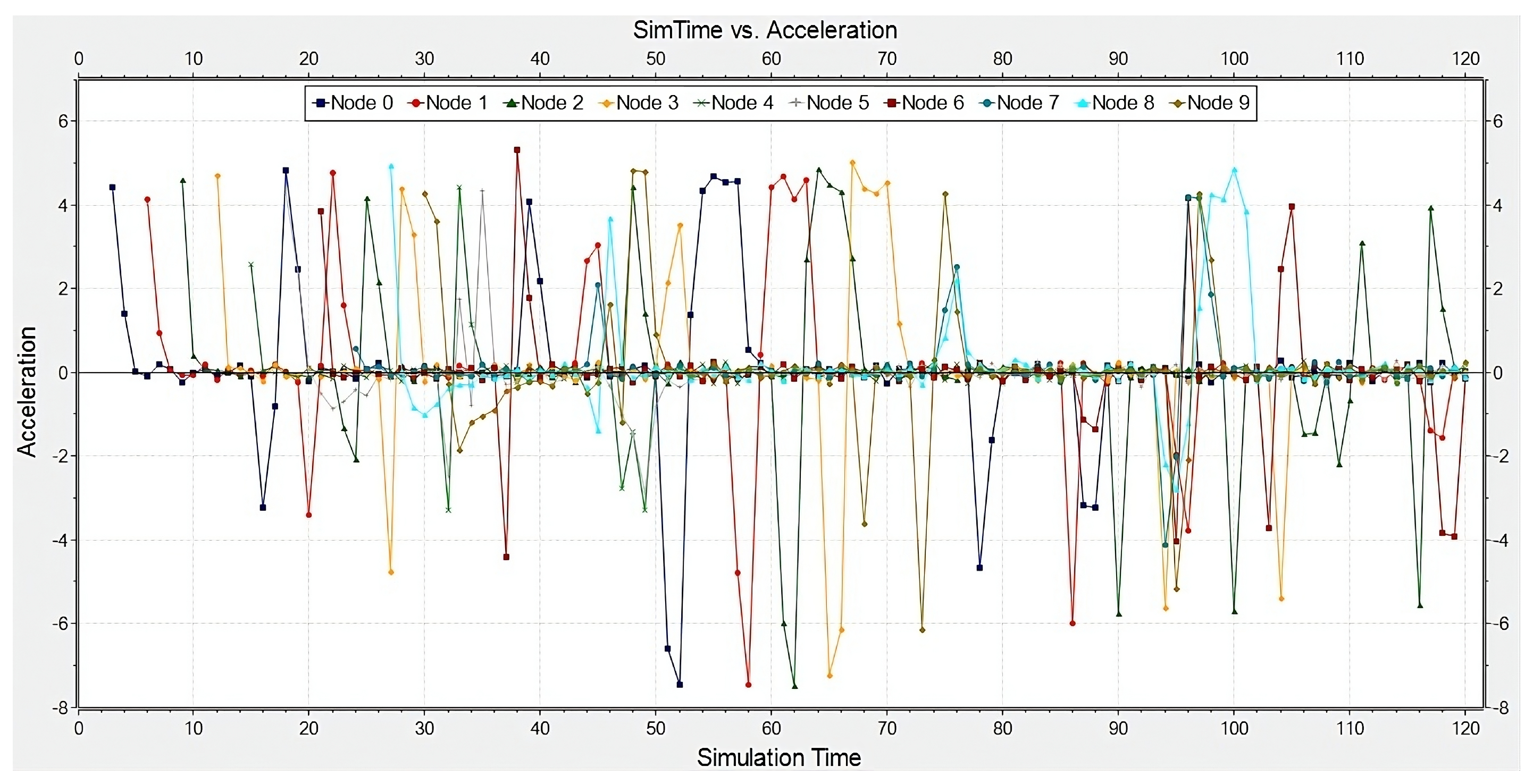
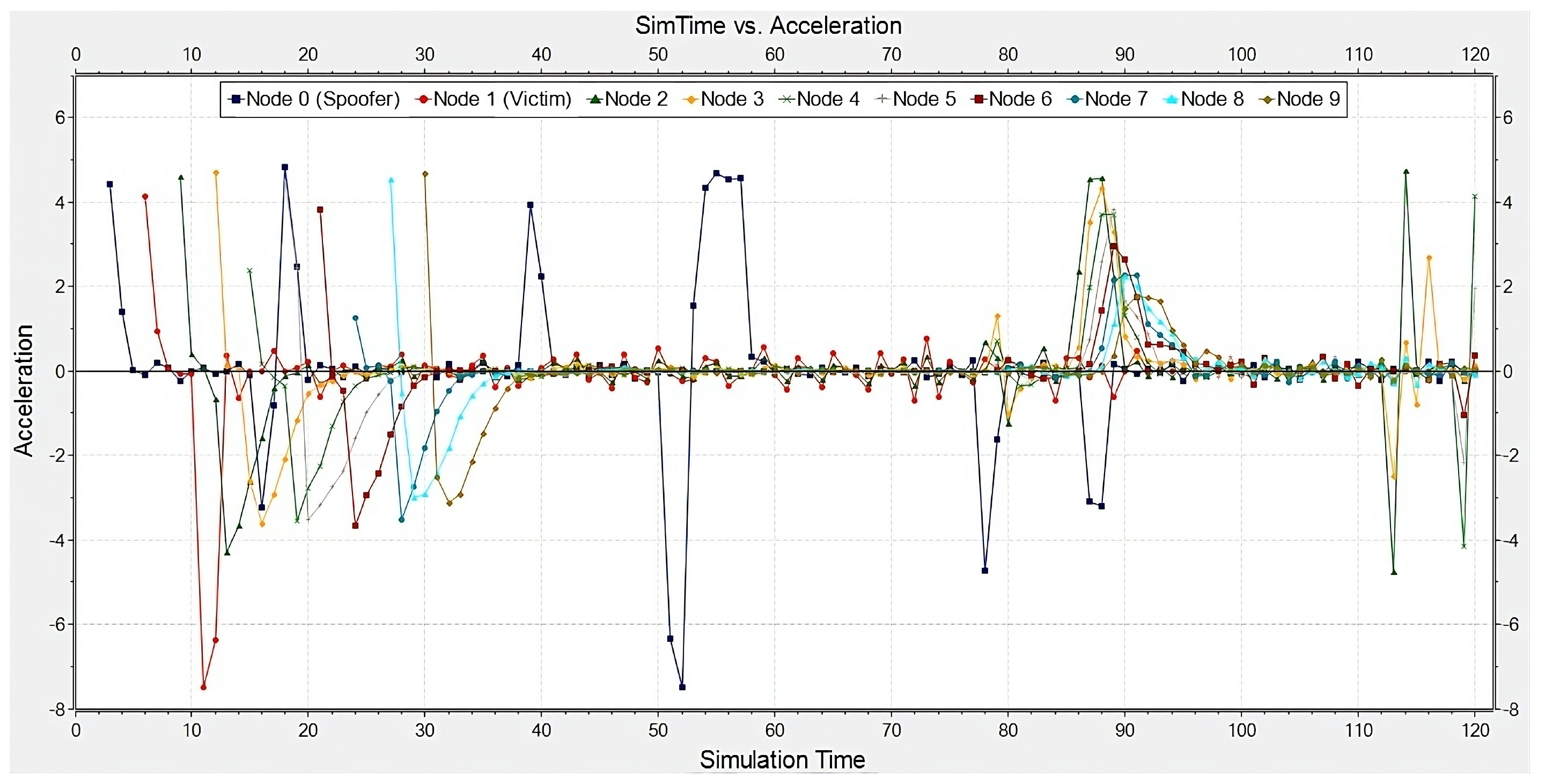
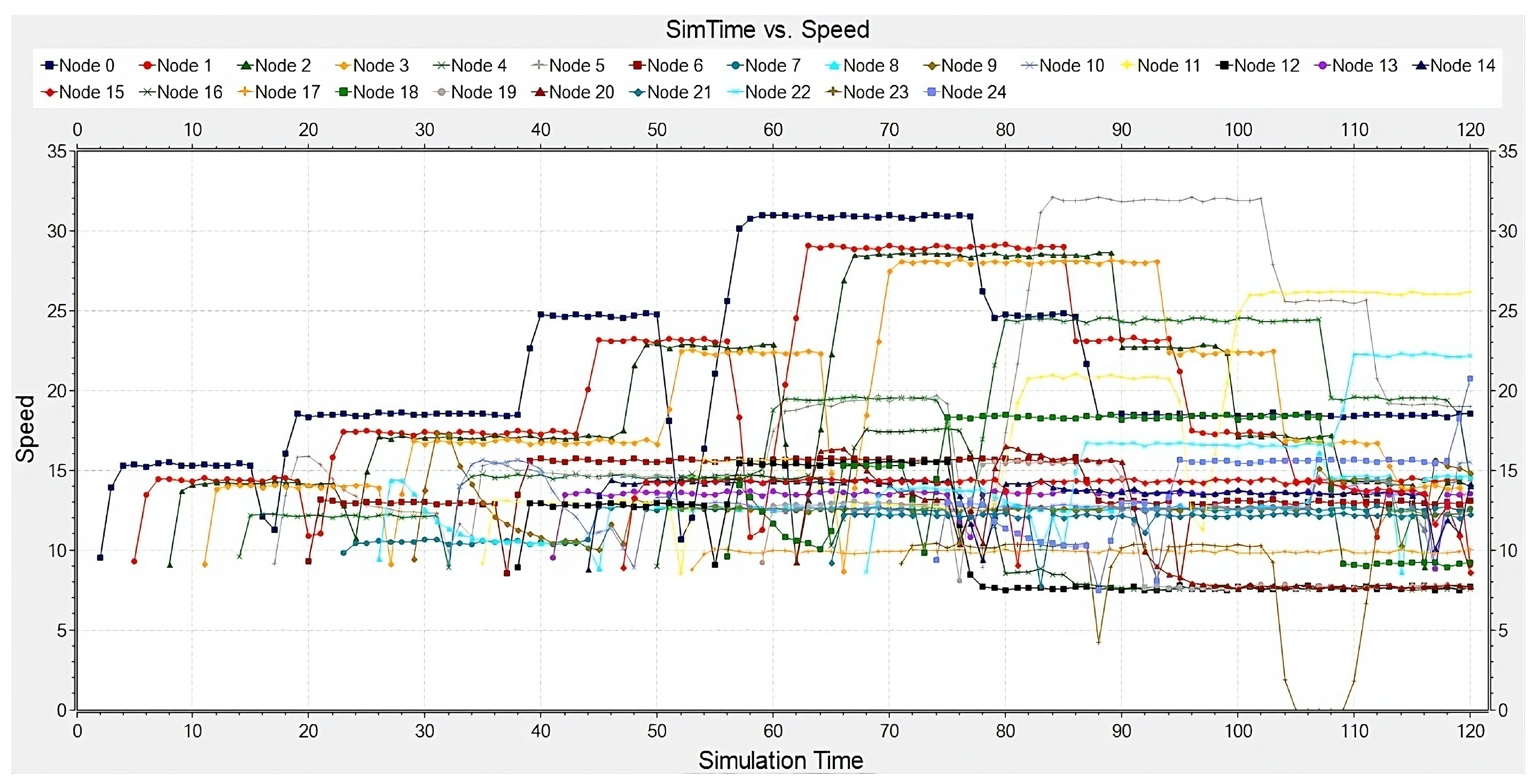
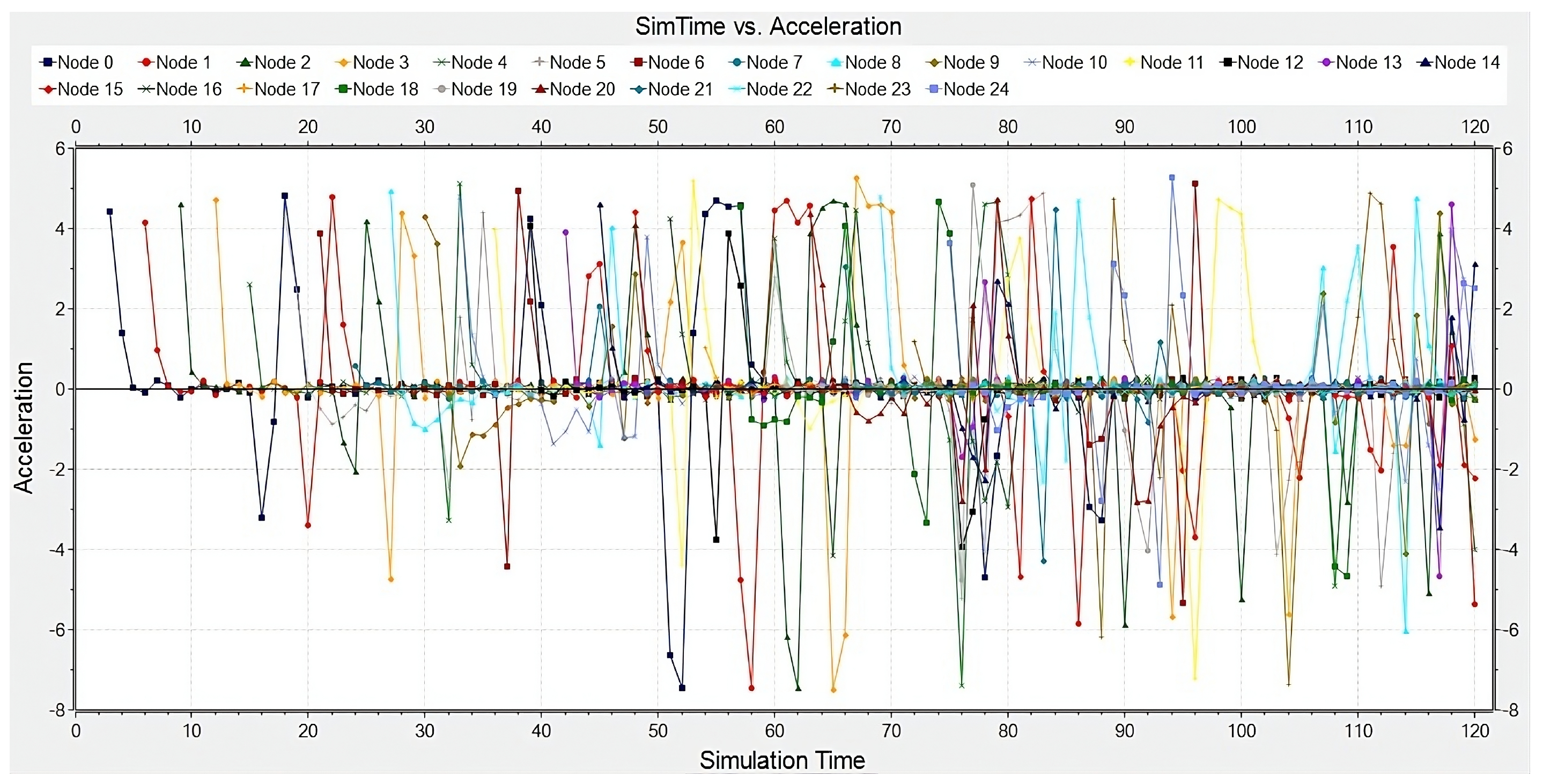
4. Evaluation
Effects of Spoofing Attack
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Sharma, N.; Chauhan, N.; Chand, N. Security challenges in Internet of Vehicles (IoV) environment. In Proceedings of the 2018 First International Conference on Secure Cyber Computing and Communication (ICSCCC), Jalandhar, India, 15–17 December 2018; pp. 203–207. [Google Scholar] [CrossRef]
- Nanda, A.; Puthal, D.; Rodrigues, J.J.P.C.; Kozlov, S.A. Internet of Autonomous Vehicles Communications Security: Overview, Issues, and Directions. IEEE Wirel. Commun. 2019, 26, 60–65. [Google Scholar] [CrossRef]
- Kosmanos, D.; Pappas, A.; Maglaras, L.; Moschoyiannis, S.; Aparicio-Navarro, F.J.; Argyriou, A.; Janicke, H. A novel Intrusion Detection System against spoofing attacks in connected Electric Vehicles. Array 2020, 5, 100013. [Google Scholar] [CrossRef]
- Kosmanos, D.; Pappas, A.; Aparicio-Navarro, F.J.; Maglaras, L.; Janicke, H.; Boiten, E.; Argyriou, A. Intrusion Detection System for Platooning Connected Autonomous Vehicles. In Proceedings of the 2019 4th South-East Europe Design Automation, Computer Engineering, Computer Networks and Social Media Conference (SEEDA-CECNSM), Piraeus, Greece, 20–22 September 2019; pp. 1–9. [Google Scholar] [CrossRef]
- Kim, K.; Kim, J.S.; Jeong, S.; Park, J.H.; Kim, H.K. Cybersecurity for autonomous vehicles: Review of attacks and defense. Comput. Secur. 2021, 103, 102150. [Google Scholar] [CrossRef]
- Nahri, M.; Boulmakoul, A.; Karim, L.; Lbath, A. IoV distributed architecture for real-time traffic data analytics. Procedia Comput. Sci. 2018, 130, 480–487. [Google Scholar] [CrossRef]
- Wang, Z.; Wei, H.; Wang, J.; Zeng, X.; Chang, Y. Security Issues and Solutions for Connected and Autonomous Vehicles in a Sustainable City: A Survey. Sustainability 2022, 14, 12409. [Google Scholar] [CrossRef]
- Khattak, Z.H.; Smith, B.L.; Fontaine, M.D. Impact of cyberattacks on safety and stability of connected and automated vehicle platoons under lane changes. Accid. Anal. Prev. 2021, 150, 105861. [Google Scholar] [CrossRef] [PubMed]
- Yadav, S.; Redhu, P. Self-stabilization control on traffic flow of connected and automated vehicles under cyberattacks. Eur. Phys. J. Plus 2023, 138, 203–207. [Google Scholar] [CrossRef]
- Giannaros, A.; Karras, A.; Theodorakopoulos, L.; Karras, C.; Kranias, P.; Schizas, N.; Kalogeratos, G.; Tsolis, D. Autonomous Vehicles: Sophisticated Attacks, Safety Issues, Challenges, Open Topics, Blockchain, and Future Directions. J. Cybersecur. Priv. 2023, 3, 493–543. [Google Scholar] [CrossRef]
- Sun, Z.; Liu, R.; Hu, H.; Liu, D.; Yan, Z. Cyberattacks on connected automated vehicles: A traffic impact analysis. IET Intell. Transp. Syst. 2023, 17, 295–311. [Google Scholar] [CrossRef]
- Vamshi Krishna, K.; Ganesh Reddy, K. Classification of Distributed Denial of Service Attacks in VANET: A Survey. Wirel. Pers. Commun. 2023, 132, 933–964. [Google Scholar] [CrossRef]
- Qurashi, J.M.; Jambi, K.M.; Eassa, F.E.; Khemakhem, M.; Alsolami, F.; Basuhail, A.A. Toward Attack Modeling Technique Addressing Resilience in Self-Driving Car. IEEE Access 2023, 11, 2652–2673. [Google Scholar] [CrossRef]
- Chowdhury, A.; Karmakar, G.; Kamruzzaman, J.; Jolfaei, A.; Das, R. Attacks on Self-Driving Cars and Their Countermeasures: A Survey. IEEE Access 2020, 8, 207308–207342. [Google Scholar] [CrossRef]
- Treiber, M.; Kesting, A. Chapter 16: Calibration and Validation. In Traffic Flow Dynamics: Data, Models and Simulation; Springer: Berlin/Heidelberg, Germany, 2013; pp. 303–337. [Google Scholar] [CrossRef]
- Gipps, P.G. A behavioural car-following model for computer simulation. Transp. Res. Part B Methodol. 1981, 15, 105–111. [Google Scholar] [CrossRef]
- Kloukiniotis, A.; Papandreou, A.; Lalos, A.; Kapsalas, P.; Nguyen, D.V.; Moustakas, K. Countering Adversarial Attacks on Autonomous Vehicles Using Denoising Techniques: A Review. IEEE Open J. Intell. Transp. Syst. 2022, 3, 61–80. [Google Scholar] [CrossRef]
- IEEE. IEEE Draft Standard for Information Technology—Telecommunications and Information Exchange Between Systems Local and Metropolitan Area Networks—Specific Requirements Part 11: Wireless LAN Medium Access Control (MAC) and Physical Layer (PHY) Specifications—Enhancements for Positioning; IEEE: Piscataway, NJ, USA, 2019; pp. 1–187. [Google Scholar]
- Sommer, C.; German, R.; Dressler, F. Bidirectionally Coupled Network and Road Traffic Simulation for Improved IVC Analysis. IEEE Trans. Mob. Comput. 2011, 10, 3–15. [Google Scholar] [CrossRef]
- Wang, X.; Khattak, A.J.; Liu, J.; Masghati-Amoli, G.; Son, S. What is the level of volatility in instantaneous driving decisions? Transp. Res. Part C Emerg. Technol. 2015, 58, 413–427. [Google Scholar] [CrossRef]
- Kosmanos, D.; Argyriou, A.; Maglaras, L. Estimating the Relative Speed of RF Jammers in VANETs. Secur. Commun. Netw. 2019, 2019, 18. [Google Scholar] [CrossRef]
- Adhikari, M.; Munusamy, A.; Hazra, A.; Menon, V.G.; Anavangot, V.; Puthal, D. Security in Edge-Centric Intelligent Internet of Vehicles: Issues and Remedies. IEEE Consum. Electron. Mag. 2022, 11, 24–31. [Google Scholar] [CrossRef]









| Evaluation Parameters in Veins Simulator | Normal Scenario | Spoofing Attack Scenario |
|---|---|---|
| Number of Lanes | one per direction | one per direction |
| Row | 1 | 1 |
| RSU | 1 | 1 |
| Total Simulation Time | 120 s | 120 s |
| Duration of Attack | 0 s | 110 s |
| Range of Vehicles (vehicles/km) | 10, 15, 20, 25 | 10, 15, 20, 25 |
| Desired Speed | 50 m/s | |
| Maximum Acceleration | ||
| Maximum Deceleration | ||
| Reaction Time | to s | to s |
| Vehicle Length | 2 | 2 |
| Minimum Gap | 2.5 m | 2.5 m |
| Victim | 0 | 1 (Node 1) |
| Spoofing Attackers | 0 | 1 |
| Kind of Attack | Density of 10 vehicles/km | Density of 15 vehicles/km | Density of 20 vehicles/km | Density of 25 vehicles/km |
|---|---|---|---|---|
| Normal Scenario | 664.9341 | 678.5202 | 679.1850 | 679.1850 |
| Spoofing Attack Scenario | −682.9962 | −678.0775 | −680.5207 | −694.6582 |
| Kind of Attack | Density of 10 vehicles/km | Density of 15 vehicles/km | Density of 20 vehicles/km | Density of 25 vehicles/km |
|---|---|---|---|---|
| Normal Scenario | 23.4126 | 23.5272 | 23.5172 | 23.5172 |
| Spoofing Attack Scenario | 190.6639 | 191.2707 | 190.8419 | 190.8157 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Tzoannos, Z.-R.; Kosmanos, D.; Xenakis, A.; Chaikalis, C. The Impact of Spoofing Attacks in Connected Autonomous Vehicles under Traffic Congestion Conditions. Telecom 2024, 5, 747-759. https://doi.org/10.3390/telecom5030037
Tzoannos Z-R, Kosmanos D, Xenakis A, Chaikalis C. The Impact of Spoofing Attacks in Connected Autonomous Vehicles under Traffic Congestion Conditions. Telecom. 2024; 5(3):747-759. https://doi.org/10.3390/telecom5030037
Chicago/Turabian StyleTzoannos, Zisis-Rafail, Dimitrios Kosmanos, Apostolos Xenakis, and Costas Chaikalis. 2024. "The Impact of Spoofing Attacks in Connected Autonomous Vehicles under Traffic Congestion Conditions" Telecom 5, no. 3: 747-759. https://doi.org/10.3390/telecom5030037







