Visual State Estimation for False Data Injection Detection of Solar Power Generation †
Abstract
:1. Introduction
- A novel deep learning architecture that can detect FDIA in solar power generation measurements based on sky images,
- A detailed step-by-step process to perform transfer learning from an object classification domain to the FDIA detection domain in solar power generation.
2. Proposed Approach
2.1. Transfer Learning Procedure
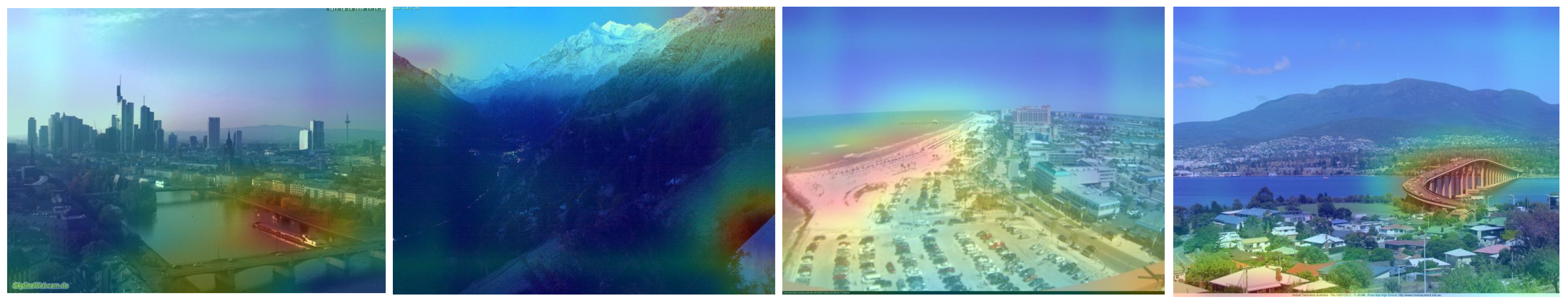
2.2. Intermediate Representation
2.3. Binary Hypothesis Test
- If , false data injection attacks are suspected;
- If , false data injection attacks are not suspected.
3. Experimental Setup
- Rotation range: This is the degree range for random rotations. In this study, a range between −5 and +5 degrees was used;
- Width shift range: The original image is randomly shifted by a proportional percentage of the original image width. In this study, this parameter was set at 0.2, i.e., ;
- Height shift range: This is similar to the previous transformation, but it uses the height of the image to perform the shift. In all the experiments, this parameter was set to 0.2, i.e., ;
- Zoom range: This transformation generates a random zoom. In this work, a range between 90% and 110% of the original image was used;
- Horizontal flip: This randomly flips the image horizontally;
- Vertical flip: This randomly flips the image vertically;
- Brightness range: This increases or decreases the brightness of the image. Hence, this parameter was set in a range between 0.9 and 1.1;
- Fill mode: In all the experiments, the nearest approach fill mode was used, which fills points outside the boundaries of the image with similar information to that of the boundaries,
Svr Training Details
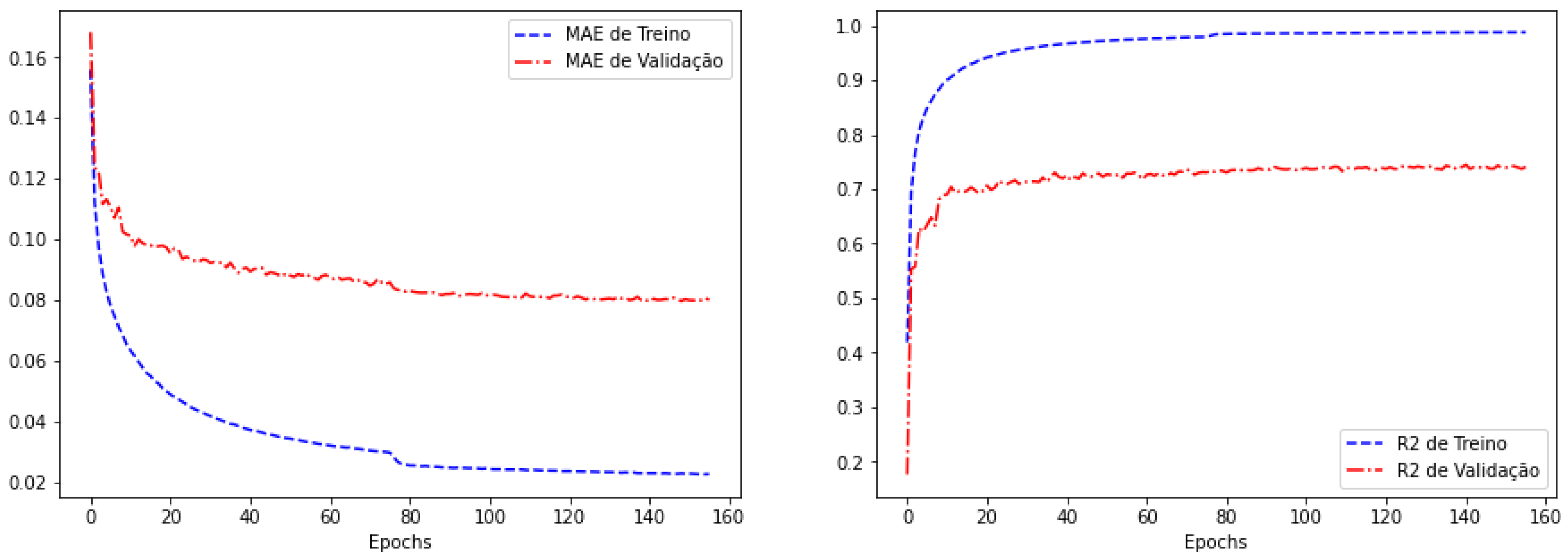
4. Results and Discussion
5. Conclusions
6. Future Works
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Musleh, A.S.; Chen, G.; Dong, Z.Y. A survey on the detection algorithms for false data injection attacks in smart grids. IEEE Trans. Smart Grid 2019, 11, 2218–2234. [Google Scholar] [CrossRef]
- Tan, R.; Nguyen, H.H.; Foo, E.Y.; Yau, D.K.; Kalbarczyk, Z.; Iyer, R.K.; Gooi, H.B. Modeling and mitigating impact of false data injection attacks on automatic generation control. IEEE Trans. Inf. Forensics Secur. 2017, 12, 1609–1624. [Google Scholar] [CrossRef]
- Acurio, B.A.A.; Barragán, D.E.C.; Amezquita, J.C.L.; Rider, M.J.; Da Silva, L.C.P. Design and Implementation of a Machine Learning State Estimation Model for Unobservable Microgrids. IEEE Access 2022, 10, 123387–123398. [Google Scholar] [CrossRef]
- Ameli, A.; Hooshyar, A.; El-Saadany, E.F.; Youssef, A.M. Attack detection and identification for automatic generation control systems. IEEE Trans. Power Syst. 2018, 33, 4760–4774. [Google Scholar] [CrossRef]
- Chaojun, G.; Jirutitijaroen, P.; Motani, M. Detecting false data injection attacks in AC state estimation. IEEE Trans. Smart Grid 2015, 6, 2476–2483. [Google Scholar] [CrossRef]
- Yang, Q.; Yang, J.; Yu, W.; An, D.; Zhang, N.; Zhao, W. On false data-injection attacks against power system state estimation: Modeling and countermeasures. IEEE Trans. Parallel Distrib. Syst. 2013, 25, 717–729. [Google Scholar] [CrossRef]
- Wang, Z.; He, H.; Wan, Z.; Sun, Y. Detection of false data injection attacks in ac state estimation using phasor measurements. IEEE Trans. Smart Grid 2020. [Google Scholar] [CrossRef]
- Manandhar, K.; Cao, X.; Hu, F.; Liu, Y. Detection of faults and attacks including false data injection attack in smart grid using Kalman filter. IEEE Trans. Control Netw. Syst. 2014, 1, 370–379. [Google Scholar] [CrossRef]
- Tan, S.; Xie, P.; Guerrero, J.M.; Vasquez, J.C. False data injection cyber-attacks detection for multiple dc microgrid clusters. Appl. Energy 2022, 310, 118425. [Google Scholar] [CrossRef]
- Husnoo, M.A.; Anwar, A.; Hosseinzadeh, N.; Islam, S.N.; Mahmood, A.N.; Doss, R. False data injection threats in active distribution systems: A comprehensive survey. arXiv 2022, arXiv:2111.14251v2. [Google Scholar] [CrossRef]
- Simonyan, K.; Zisserman, A. Very deep convolutional networks for large-scale image recognition. arXiv 2014, arXiv:1409.1556. [Google Scholar]
- Laffont, P.Y.; Ren, Z.; Tao, X.; Qian, C.; Hays, J. Transient Attributes for High-Level Understanding and Editing of Outdoor Scenes. ACM Trans. Graph. 2014, 33, 4. [Google Scholar] [CrossRef]
- Goodfellow, I.; Bengio, Y.; Courville, A. Deep Learning; MIT Press: Cambridge, MA, USA, 2016. [Google Scholar]
- Nie, Y.; Li, X.; Scott, A.; Sun, Y.; Venugopal, V.; Brandt, A. SKIPP’D: A SKy Images and Photovoltaic Power Generation Dataset for short-term solar forecasting. Sol. Energy 2023, 255, 171–179. [Google Scholar] [CrossRef]



Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Acuña Acurio, B.A.; Chérrez Barragán, D.E.; López, J.C.; Grijalva, F.; Rodríguez, J.C.; da Silva, L.C.P. Visual State Estimation for False Data Injection Detection of Solar Power Generation. Eng. Proc. 2023, 47, 5. https://doi.org/10.3390/engproc2023047005
Acuña Acurio BA, Chérrez Barragán DE, López JC, Grijalva F, Rodríguez JC, da Silva LCP. Visual State Estimation for False Data Injection Detection of Solar Power Generation. Engineering Proceedings. 2023; 47(1):5. https://doi.org/10.3390/engproc2023047005
Chicago/Turabian StyleAcuña Acurio, Byron Alejandro, Diana Estefanía Chérrez Barragán, Juan Camilo López, Felipe Grijalva, Juan Carlos Rodríguez, and Luiz Carlos Pereira da Silva. 2023. "Visual State Estimation for False Data Injection Detection of Solar Power Generation" Engineering Proceedings 47, no. 1: 5. https://doi.org/10.3390/engproc2023047005
APA StyleAcuña Acurio, B. A., Chérrez Barragán, D. E., López, J. C., Grijalva, F., Rodríguez, J. C., & da Silva, L. C. P. (2023). Visual State Estimation for False Data Injection Detection of Solar Power Generation. Engineering Proceedings, 47(1), 5. https://doi.org/10.3390/engproc2023047005







