Data-Throughput Enhancement Using Data Mining-Informed Cognitive Radio
Abstract
:1. Introduction
1.1. Scarce Spectrum Problem
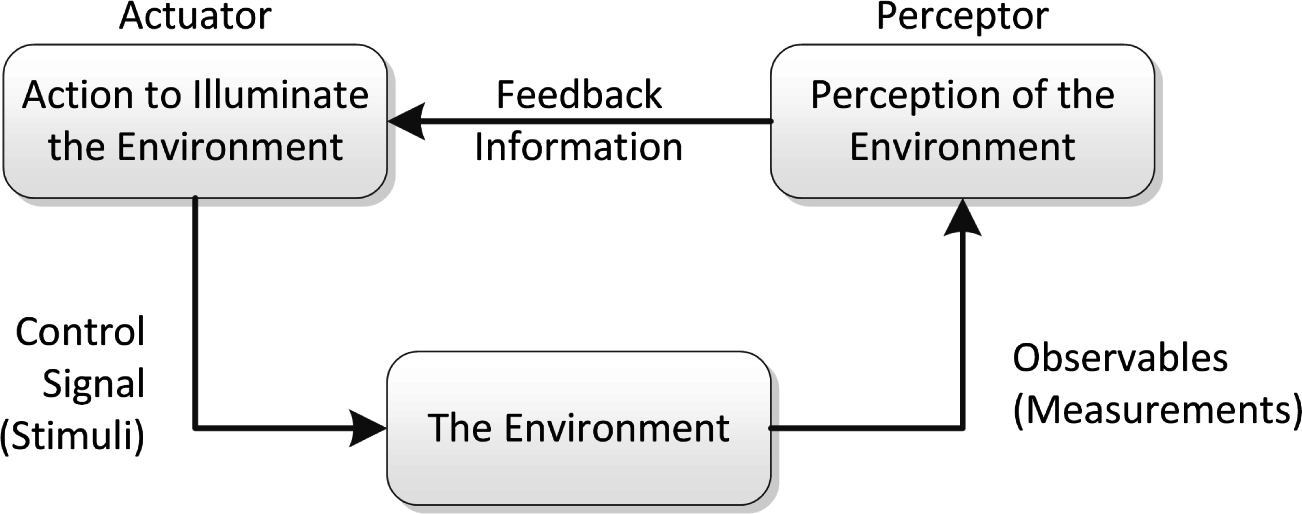
1.2. Background on Cognitive Radio
- Frequency bands that are predominantly unoccupied;
- Frequency bands that are moderately occupied; and
- Frequency bands that are heavily occupied.
1.3. Big Data Framework
1.4. Main Contributions
1.5. Proposed Cognitive Radio
1.6. Paper Organization
2. Problem Definition
2.1. Big Data Framework for Wireless Communication
2.2. Problem Definition
2.3. Wireless Channel Modeling
3. Proposed Algorithms
3.1. Data Transmission Algorithms
| for each t in {1, 2, …, M} do Find all capacity in {1, 2, …, t} |
| if Capacity(t) < Demand(t) then |
| Data(t) = 0 |
| for each t in {1, 2, …, M} do Find all capacity in {1, 2, …, t} |
| if Capacity(t) < Demand(t) then |
| Data(t) = DataReal |
| if Capacity(t) < Data(t) then |
| Data(t) = DataReal |
3.2. Incorporating Network Burstiness
| for each t in {1, 2, …, M} do Find all capacity in {1, 2, …, t} |
| if Capacity(t) < Demand(t) then |
| Data(t) = DataReal + Capacity(t − 1) − Demand(t − 1) + Capacity(t − 2) − Demand(t − 2) + … + Capacity(t − N) − Demand(t − N) − Demand(t − N) |
| if Capacity(t) < Data(t) then |
| Data(t) = DataReal |
| for each t in {1, 2, …, M} do Find all capacity in {1, 2, …, t} |
| if Data(t) > AverageData then |
| burstStart = t |
| burstData = Data(t) |
| for each tPrime in {t, t + 1, t + 2, …, M} do |
| if Data(tPrime) < AverageData then |
| if Data(tPrime − t) > ToleranceFactor then |
| burstEnd = tPrime – 1 |
| burstsPerTime[t] = Burst(burstStart, burstEnd, burstData) |
| else |
| burstData = burstData + Data(tPrime) |
| Continue |
| for each t in {1, 2, …, M} do Find all capacity in {1, 2, …, t} |
| if Capacity(t) < Demand(t) then |
| PredictiveCapacity = DataReal + Capacity(t − 1) − Demand(t − 1) + Capacity(t − 2) −Demand(t −2) + Capacity(t − 3) − Demand(t − 3) |
| BurstProportionCapacity = DataReal + (BurstLength(t)/TimePeriod) × Demand(t) |
| NonBurstProportionCapacity = DataReal + (TimePeriod − (BurstLength(t)/TimePeriod)) ×Demand(t) |
| MaximumPrediction = DataReal |
| for Prediction in PredictiveCapacity, BurstProportionCapacity, NonBurstProportionCapacity do |
| if Prediction > MaximumPrediction and Prediction < Capacity(t) then |
| MaximumPrediction = Prediction |
| Data(t) = MaximumPrediction |
4. Results and Discussion
4.1. Simulation Setup
4.2. Throughput
4.3. Simulation Methods
4.4. Simulation Supplementary Materials
5. Summary and Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Sodagari, S.; Attar, A.; Bilén, S.G. Strategies to achieve truthful spectrum auctions for cognitive radio networks based on mechanism design, Proceedings of the 2010 IEEE Symposium on New Frontiers in Dynamic Spectrum, Singapore, 6–9 April 2010; pp. 1–6.
- Sodagari, S.; Attar, A.; Leung, V.C.M.; Bilén, S.G. Time-optimized and truthful dynamic spectrum rental mechanism, Proceedings of the 72nd IEEE Vehicular Technology Conference Fall (VTC 2010-Fall), Ottawa, ON, Canada, 6–9 September 2010; pp. 1–5.
- Jana, S.; Zeng, K.; Cheng, W.; Mohapatra, P. Trusted Collaborative Spectrum Sensing for Mobile Cognitive Radio Networks. Inf. Forensics Secur. 2013, 8, 1497–1507. [Google Scholar]
- Fatemieh, O.; Chandra, R.; Gunter, C.A. Secure collaborative sensing for crowdsourcing spectrum data in white space networks, Proceedings of the 2010 IEEE Symposium on New Frontiers in Dynamic Spectrum, Singapore, 6–9 April 2010; pp. 1–12.
- Akyildiz, I.F.; Altunbasak, Y.; Fekri, F.; Sivakumar, R. AdaptNet: Adaptive protocol suite for next generation wireless internet. IEEE Commun. Mag. 2004, 42, 128–138. [Google Scholar]
- Giannoulis, A.; Patras, P.; Knightly, E.W. Mobile Access of Wide-Spectrum Networks: Design, Deployment and Experimental Evaluation. 2012. arXiv:1204.4847. arXiv.org e-Print archive. Available online: http://arxiv.org/abs/physics/0402096 accessed on 21 April 2012.
- Wang, B.; Wu, Y.; Liu, K.J. Game theory for cognitive radio networks: An overview. Comput. Netw. 2010, 54, 2537–2561. [Google Scholar]
- FCC. Notice of proposed rule making and order. ET Docket No 03-222; December 2003; pp. 1–21. [Google Scholar]
- Mitola, J.; Maguire, G.Q., Jr. Cognitive radio: Making software radios more personal. IEEE Personal Commun. 1999, 6, 13–18. [Google Scholar]
- Akyildiz, I.F.; Lee, W.; Vuran, M.C.; Mohanty, S. Next generation dynamic spectrum access cognitive radio wireless networks: A survey. Comput. Netw. 2006, 50, 2127–2159. [Google Scholar]
- Haykin, S. Cognitive radio: Brain-empowered wireless communications. IEEE J. Sel. Areas Commun. 2005, 23, 201–220. [Google Scholar]
- Gyucek, T.; Huseyin, A. A survey of spectrum sensing algorithms for cognitive radio applications. Commun. Surv. Tutor. IEEE 2009, 11, 116–130. [Google Scholar]
- Haykin, S. Cognitive Dynamic Systems Perception Action Cycle, Radar, and Radio; Cambridge University Press: New York, NY, USA, 2012. [Google Scholar]
- Jondral, F.K. Software-defined radio basics and evolution to cognitive radio. EURASIP J. Wirel. Commun. Netw. 2005, 3, 275–283. [Google Scholar]
- Hu, S.; Yao, Y.; Yang, Z. MAC protocol identification using support vector machines for cognitive radio networks. IEEE Wirel. Commun. 2014, 21, 52–60. [Google Scholar]
- Bodnar, T.; Tucker, C.S.; Hopkinson, K.; Bilén, S.G. Increasing the veracity of event detection on social media networks through user trust modeling, Proceedings of the 2014 IEEE International Conference on Big Data, Washington, DC, USA, 27–30 October 2014.
- Yin, P.; Ram, N.; Lee, W.; Tucker, C.S.; Khandelwal, S.; Salathe, M. Two sides of a coin: Separating personal communication and public dissemination accounts in Twitter, Proceedings of the 2014 Pacific-Asia Conference on Knowledge Discovery and Data Mining (PAKDD), Tainan, Taiwan, 13–16 May 2014.
- Qiu, R.; Wicks, M. Cognitive Networked Sensing and Big Data; Springer: New York, NY, USA, 2014. [Google Scholar]
- Bilén, S.G.; Kotobi, K.; Tucker, C.S. Data mining–informed cognitive radio networks, Proceedings of the 2014 New England Workshop on Software Defined Radio (NEWSDR 14), Boston, MA, USA, 6 June 2014.
- Li, Y.; Zhou, G.; Ruddy, G.; Cutler, B. A measurement-based prioritization scheme for smartphone applications. Wirel. Personal Commun. 2014, 78, 333–346. [Google Scholar]
- Das, A.K.; Pathak, P.H.; Chuah, C.N.; Mohapatra, P. Contextual localization through network traffic analysis, Proceedings of the IEEE INFOCOM, Toronto, ON, Canada, 27 April–2 May 2014.
- Basgeet, D.R.; Irvine, J.; Munro, A.; Dugenie, P.; Kaleshi, D.; Lazaro, O. Impact of mobility on aggregate traffic in mobile multimedia system, Proceedings of the 5th International Symposium on Wireless Personal Multimedia Communications, Honolulu, HI, USA, 27–30 October 2002.
- Leland, W.E.; Taqqu, M.S.; Willinger, W.; Wilson, D.V. On the self-similar nature of Ethernet traffic. ACM SIGCOMM Comput. Commun. Rev. 1993, 23, 183–193. [Google Scholar]
- Zhou, B.; He, D.; Sun, Z.; Ng, W.H. Network traffic modeling and prediction with ARIMA/GARCH, Proceeding of HET-NETs Conference, Ilkley, West Yorkshire, UK, 18–20 July 2005.
- Sang, A.; San-qi, L. A predictability analysis of network traffic. INFOCOM 2000, Proceedings of the Nineteenth Annual Joint Conference of the IEEE Computer and Communications Societies, Tel Aviv, Israel, 26–30 March 2000.
- Ge, X.; Shaokai, Y.; Won-Sik, Y.; Yong-Deak, K. A new prediction method of alpha-stable processes for self- imilar traffic, Proceedings of the 2004 Global Telecommunications Conference GLOBECOM ’04 IEEE, Dallas, TX, USA, 29 November–3 December 2004.
- Krzanowski, R. Burst of packets and burstiness, Proceedings of the 66th IETF meeting, Quebec, QC, Canada, 9–14 July 2006.
- Russell, M.A. Mining the Social Web: Data Mining Facebook, Twitter, LinkedIn, Google+, GitHub, and More; O’Reilly Media, Inc.: Sebastopol, CA, USA, 2013. [Google Scholar]









© 2015 by the authors; licensee MDPI, Basel, Switzerland This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kotobi, K.; Mainwaring, P.B.; Tucker, C.S.; Bilén, S.G. Data-Throughput Enhancement Using Data Mining-Informed Cognitive Radio. Electronics 2015, 4, 221-238. https://doi.org/10.3390/electronics4020221
Kotobi K, Mainwaring PB, Tucker CS, Bilén SG. Data-Throughput Enhancement Using Data Mining-Informed Cognitive Radio. Electronics. 2015; 4(2):221-238. https://doi.org/10.3390/electronics4020221
Chicago/Turabian StyleKotobi, Khashayar, Philip B. Mainwaring, Conrad S. Tucker, and Sven G. Bilén. 2015. "Data-Throughput Enhancement Using Data Mining-Informed Cognitive Radio" Electronics 4, no. 2: 221-238. https://doi.org/10.3390/electronics4020221
APA StyleKotobi, K., Mainwaring, P. B., Tucker, C. S., & Bilén, S. G. (2015). Data-Throughput Enhancement Using Data Mining-Informed Cognitive Radio. Electronics, 4(2), 221-238. https://doi.org/10.3390/electronics4020221





