A Novel Epidemic Model for Wireless Rechargeable Sensor Network Security
Abstract
:1. Introduction
1.1. Research Background
1.2. Related Work
1.3. Contributions
- An epidemic model suitable for WRSNs is designed.
- Based on the next-generation matrix method, the basic reproductive number of the system is obtained.Subsequently, by applying the Routh Criterion, Lyapunov function, and the other analytical methods, the local and global stabilities of the disease-free equilibrium solution and the epidemic equilibrium solution are proved and simulated. Moreover, the linear relationship between the state variables when the system tends to be stabilized, and the positive relationship between and the charging rate is disclosed in the simulation section.
- Applying the Protryagin Maximum Principle, the optimal game strategy between malware and WRSNs is given. Moreover, by comparing the evolution of sensor nodes in various states and overall cost with the control group, the validity of the strategies is verified in the case of and .
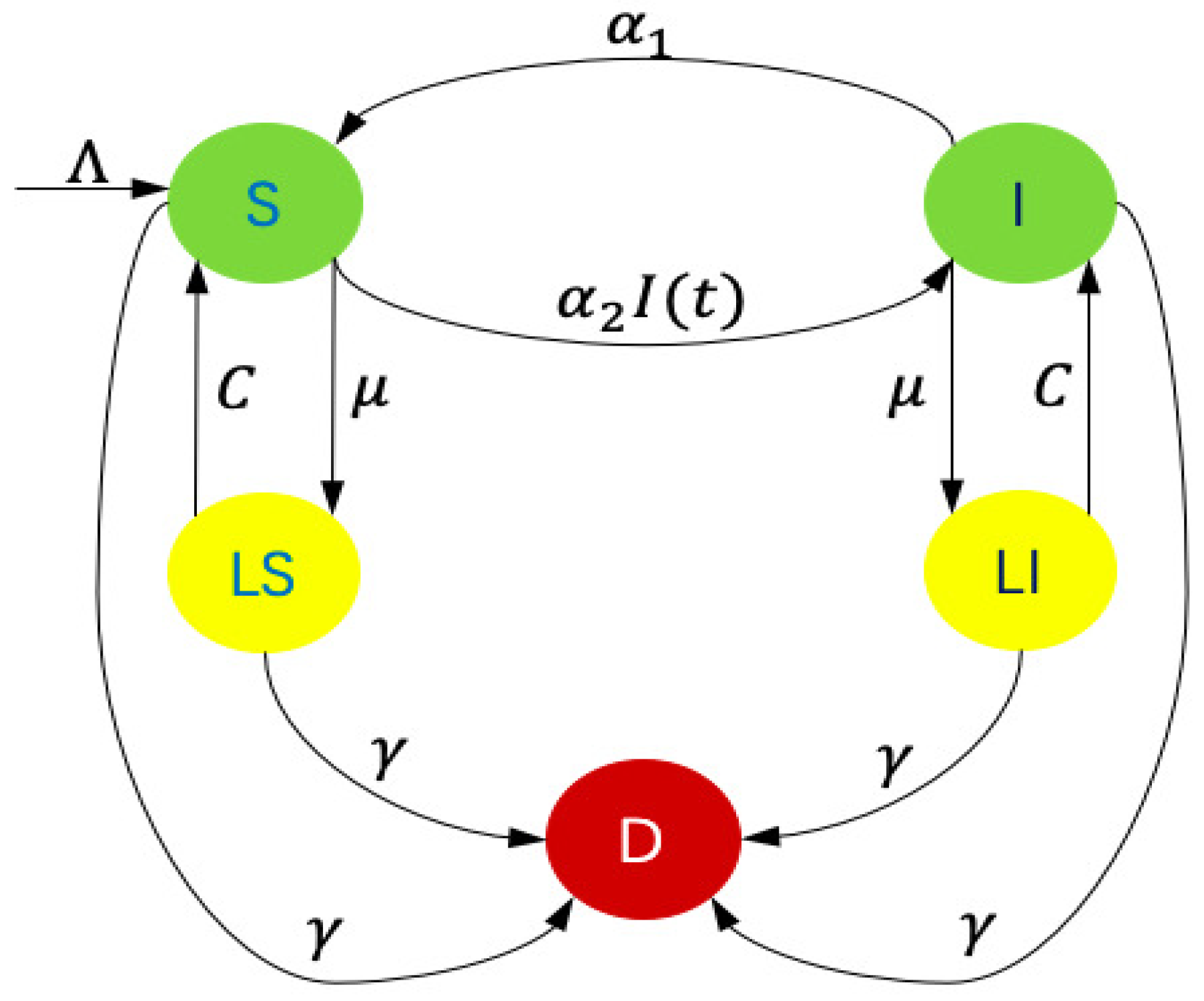
2. Modeling
2.1. Epidemic Modeling on WRSNs
2.2. Computation of the Steady States and the Basic Reproductive Number
- The disease-free steady states , where
- The endemic steady state , whereand
3. Dynamic Analysis
3.1. Local Stability Analysis
3.2. Global Stability Analysis
3.3. Optimal Control Strategies
- (a)
- The game in this paper consists of two parties, i.e., malware and WRSN.
- (b)
- (c)
- Define as a set of state variables.
- (d)
- The attacker (i.e., malware) aims at maximizing and the defender (i.e., WRSNs) aims at minimizing , andwhere indicates the cost incurred by I nodes at time t, indicates the terminal cost of corresponding state, and indicates the number of corresponding state at the terminal moment.
4. Simulation
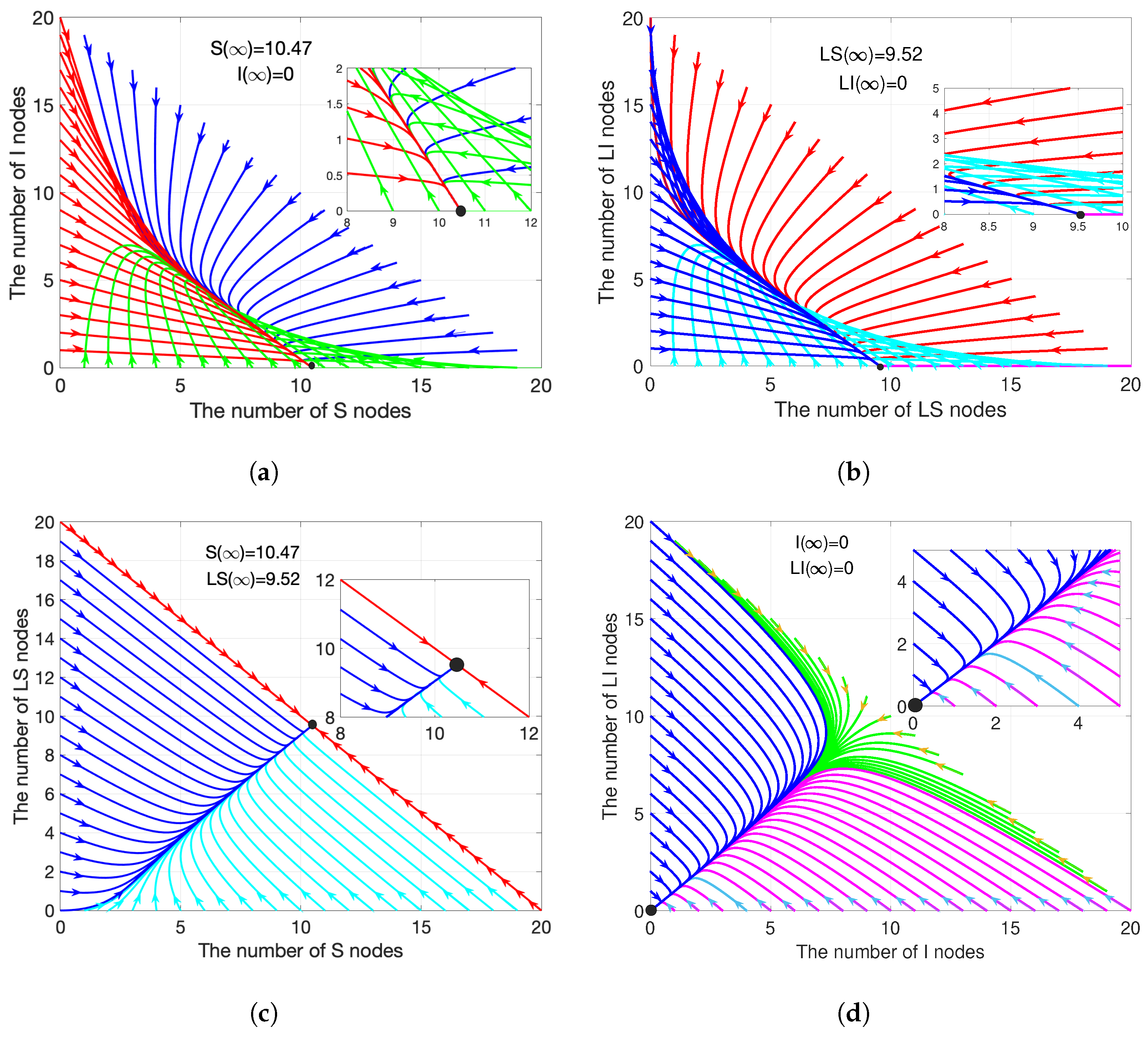
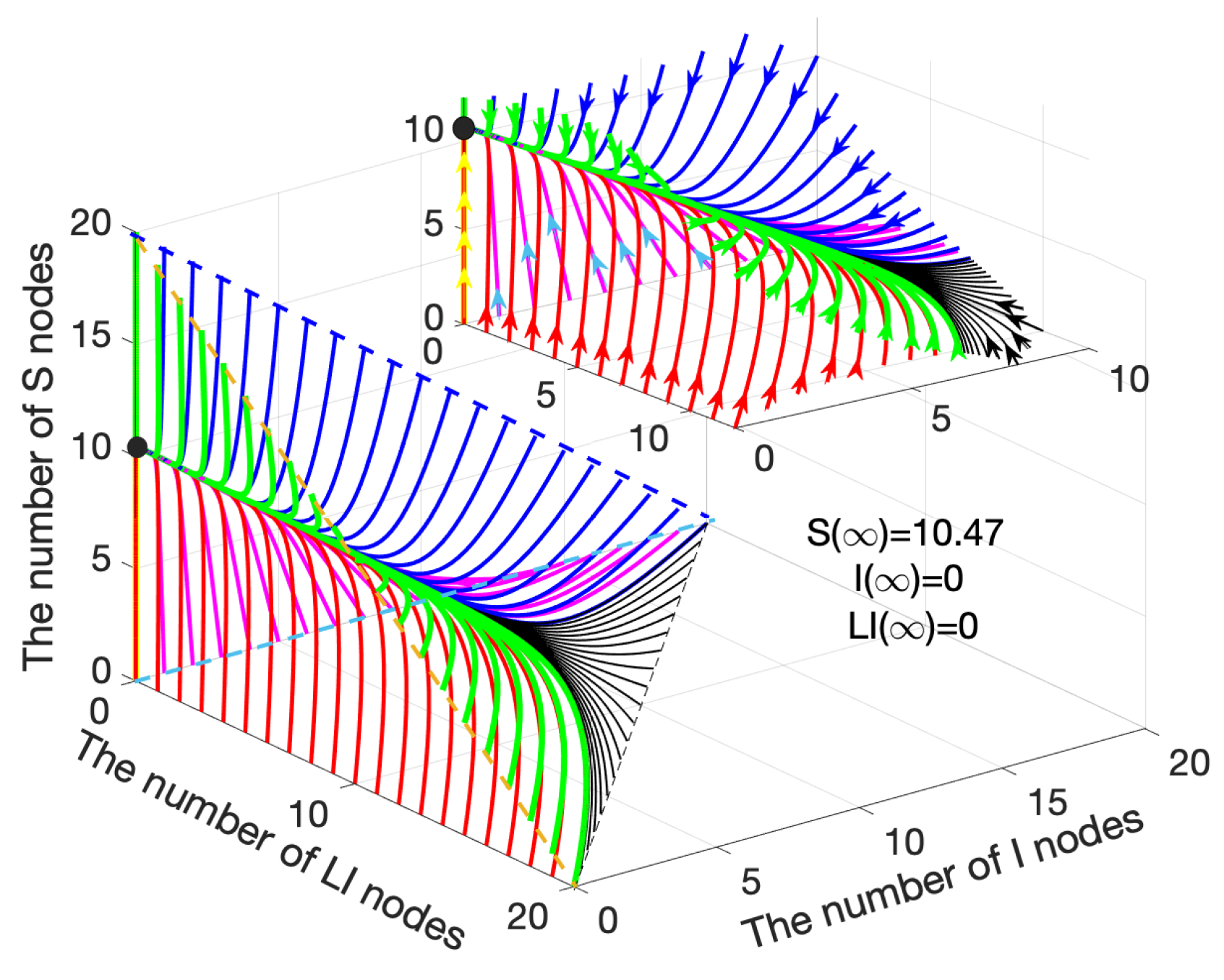
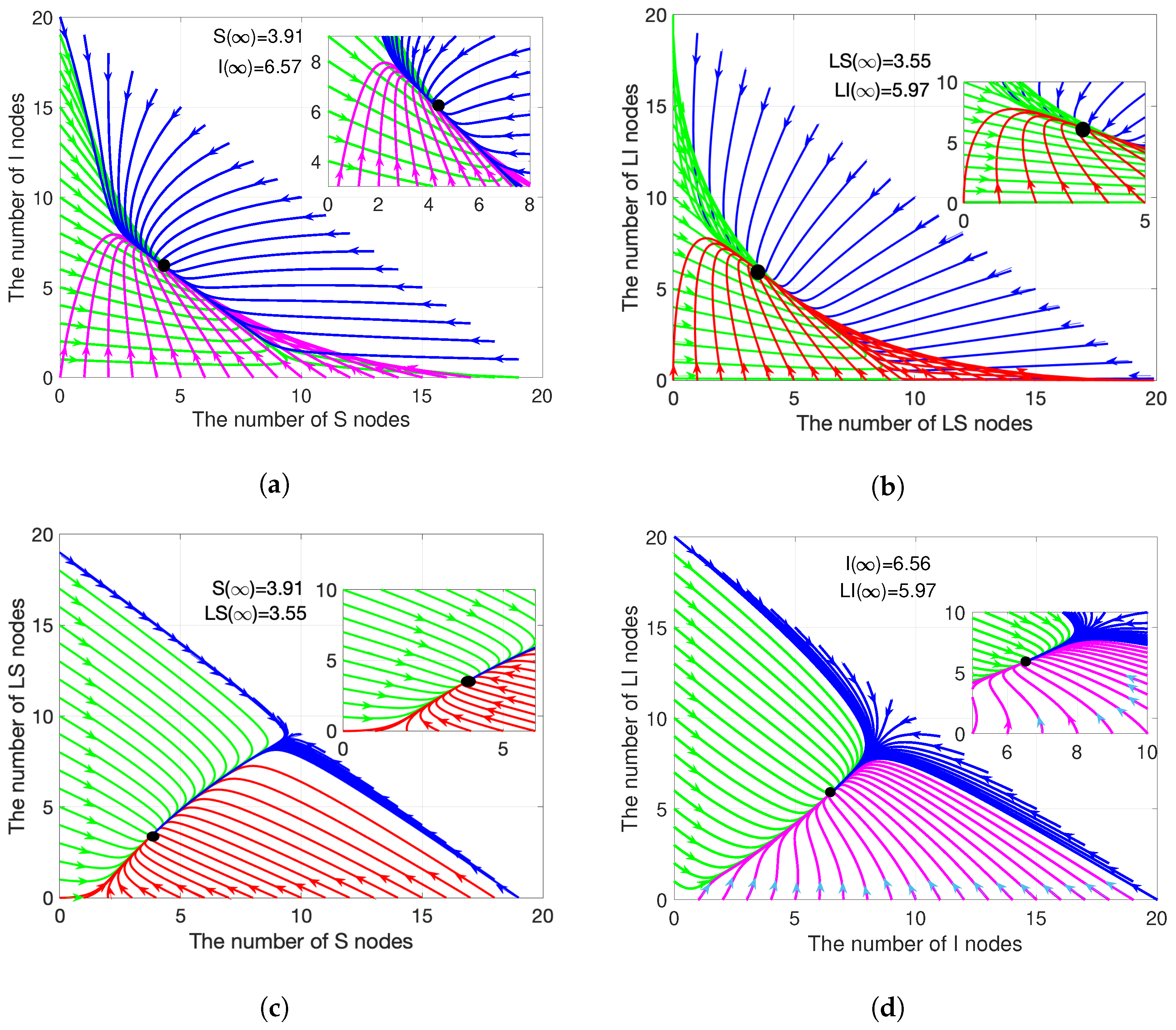
4.1. Stability Analysis
4.1.1. Disease-Free Equilibrium Stability
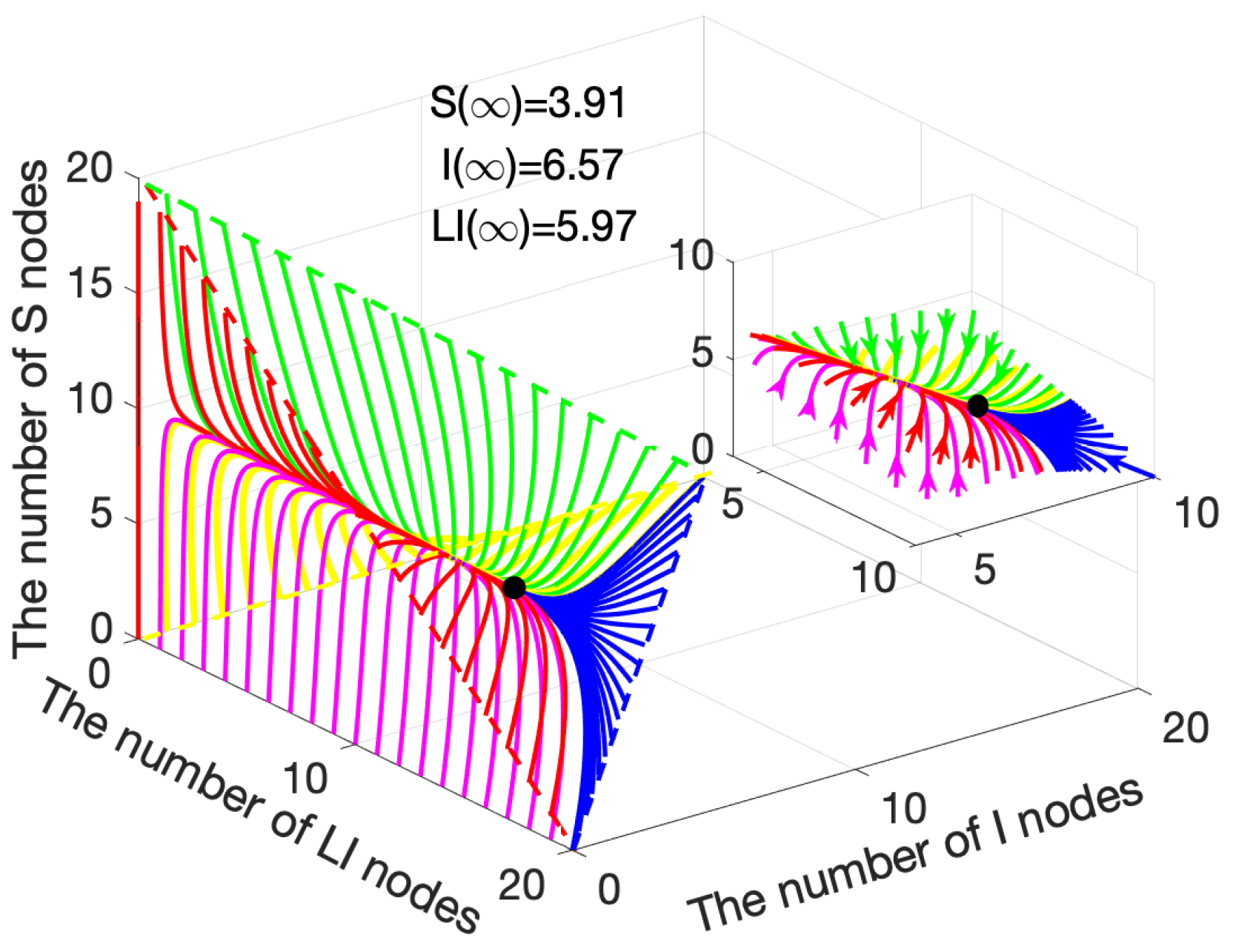
4.1.2. Epidemic Equilibrium Stability
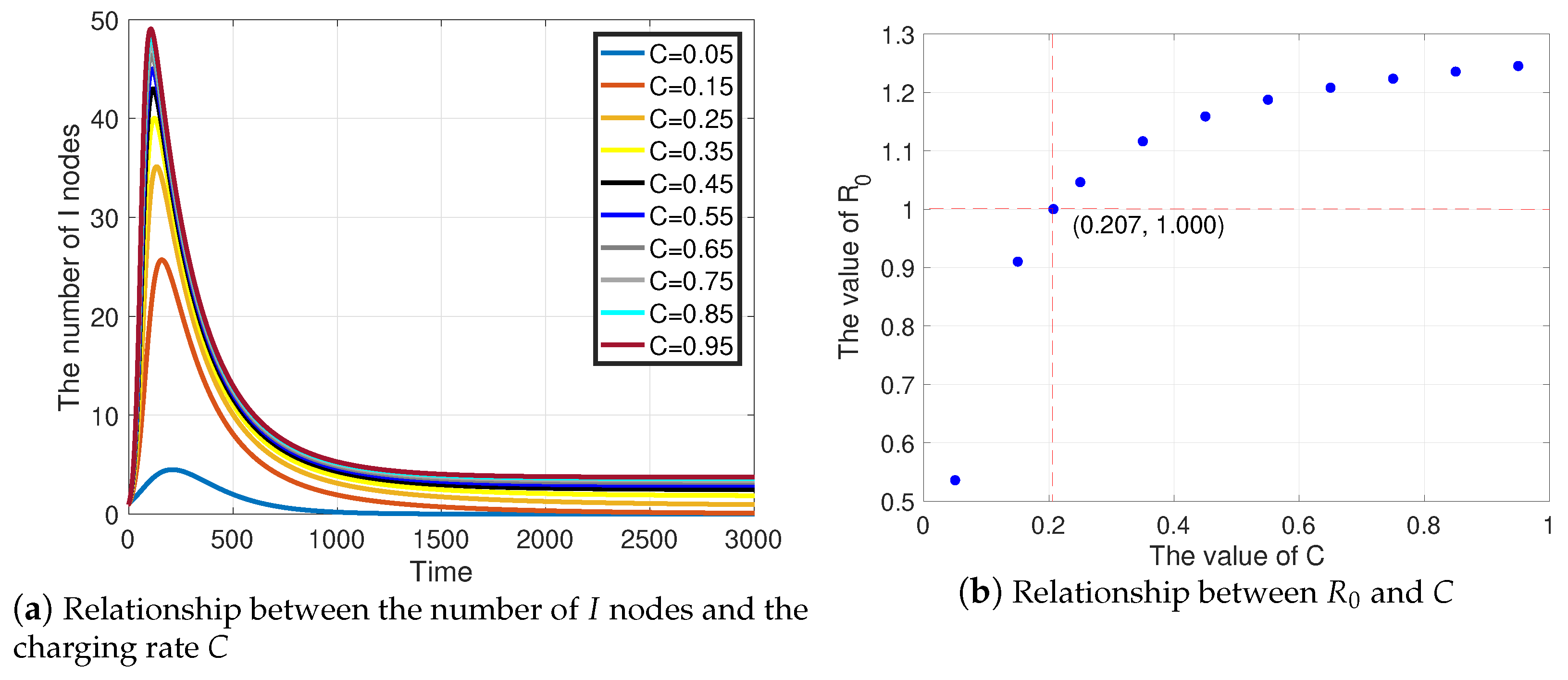
4.1.3. Influence of the Charging Rate C
4.2. Optimal Control
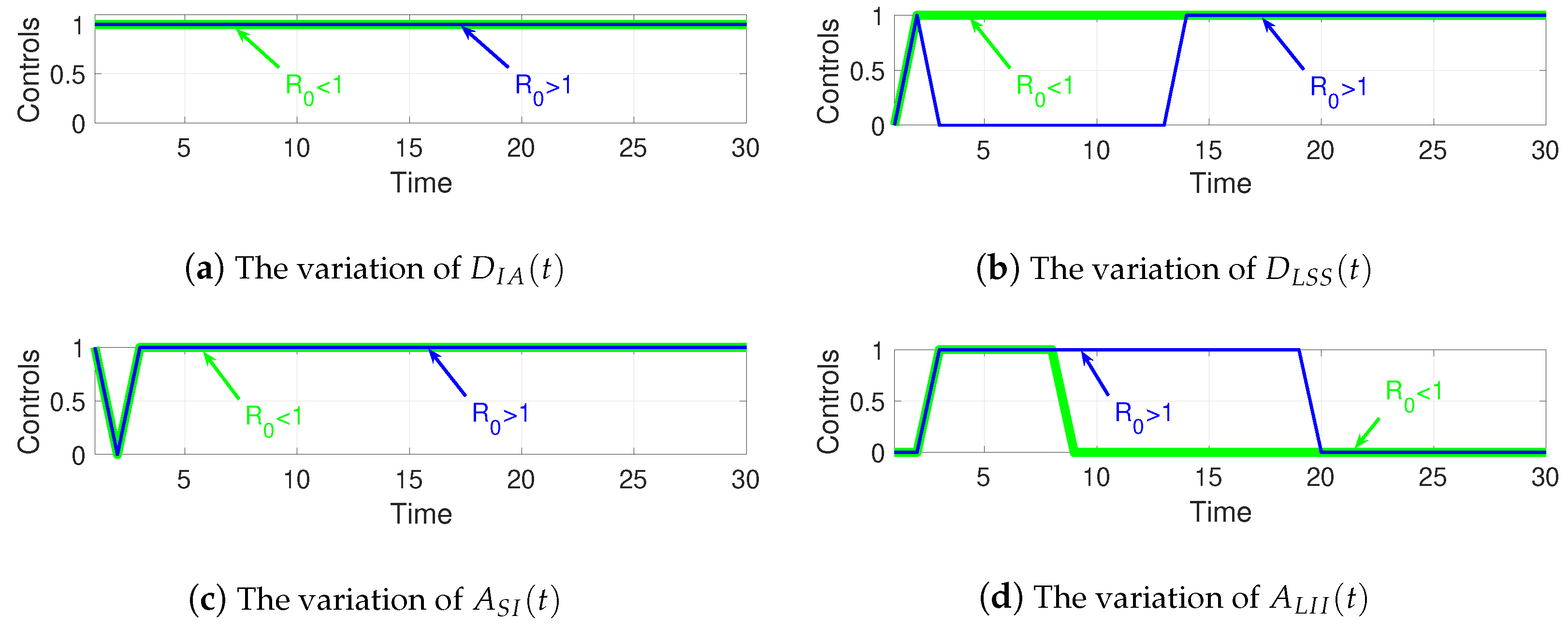
Evolution of State Variables
4.3. Overall Cost and Optimal Controls
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Abbreviations
| Symbol | Description |
| Birth rate | |
| Death rate | |
| Depletion rate | |
| Removal rate | |
| C | Charging rate |
| Transmission rate |
References
- Rashid, B.; Rehmani, M.H. Applications of wireless sensor networks for urban areas: A survey. J. Netw. Comput. Appl. 2016, 60. [Google Scholar] [CrossRef]
- Yetgin, H.; Cheung, K.T.K.; El-Hajjar, M.; Hanzo, L. A Survey of Network Lifetime Maximization Techniques in Wireless Sensor Networks. IEEE Commun. Surv. Tutor. 2017, 19, 828–854. [Google Scholar] [CrossRef] [Green Version]
- Zhang, F.; Zhang, J.; Qian, Y.J. A Survey on Wireless Power Transfer based Charging Scheduling Schemes in Wireless Rechargeable Sensor Networks. In Proceedings of the ICCSSE 2018, Wuhan, China, 21–23 August 2018. [Google Scholar]
- Shu, Y.C.; Yousefi, H.; Cheng, P.; Chen, J.M.; Gu, Y.; He, T.; Shin, K.G. Near-Optimal Velocity Control for Mobile Charging in Wireless Rechargeable Sensor Networks. IEEE. Trans. Mob. Comput. 2016, 15, 1699–1713. [Google Scholar] [CrossRef] [Green Version]
- Wu, P.F.; Xiao, F.; Sha, C.; Huang, H.P.; Sun, L.J. Trajectory Optimization for UAVs’ Efficient Charging in Wireless Rechargeable Sensor Networks. IEEE Trans. Veh. Technol. 2020, 69, 4207–4220. [Google Scholar] [CrossRef]
- Mo, L.; Kritikakou, A.; He, S.B. Energy-Aware Multiple Mobile Chargers Coordination for Wireless Rechargeable Sensor Networks. IEEE Internet Things J. 2019, 6, 8202–8214. [Google Scholar] [CrossRef] [Green Version]
- Lin, C.; Shang, Z.; Du, W.; Ren, J.K.; Wang, L.; Wu, G.W. CoDoC: A Novel Attack for Wireless Rechargeable Sensor Networks through Denial of Charge. In Proceedings of the IEEE INFOCOM 2019, Paris, France, 29 April–2 May 2019. [Google Scholar]
- Lin, C.; Zhou, J.Z.; Guo, C.Y.; Song, H.B.; Wu, G.W.; Mohammad, S.O. TSCA: A temporal-spatial real-time charging scheduling algorithm for on-demand architecture in wireless rechargeable sensor networks. IEEE. Trans. Mob. Comput. 2018, 17, 211–224. [Google Scholar] [CrossRef]
- Han, G.J.; Miao, X.; Wang, H.; Guizani, M.; Zhang, W.B. CPSLP: A Cloud-Based Scheme for Protecting Source Location Privacy in Wireless Sensor Networks Using Multi-Sinks. IEEE Trans. Veh. Technol. 2019, 68, 2739–2750. [Google Scholar] [CrossRef]
- EI Shafie, A.; Niyato, D.; AI-Dhahir, N. Security of Rechargeable Energy-Harvesting Transmitters in Wireless Networks. IEEE Wirel. Commun. Lett. 2016, 5, 384–387. [Google Scholar] [CrossRef] [Green Version]
- Bhushan, B.; Sahoo, G. E2SR2: An acknowledgement-based mobile sink routing protocol with rechargeable sensors for wireless sensor networks. Wirel. Netw 2019, 25, 2697–2721. [Google Scholar] [CrossRef]
- Saidi, A.; Benahmed, K.; Seddiki, N. Secure cluster head election algorithm and misbehavior detection approach based on trust management technique for clustered wireless sensor networks. Ad Hoc Netw. 2020, 106, 102215. [Google Scholar] [CrossRef]
- Wang, G.; Lee, B.; Ahn, J.; Cho, G. A UAV-assisted CH election framework for secure data collection in wireless sensor networks. Futur. Gener. Comp. Syst. 2020, 102, 152–162. [Google Scholar] [CrossRef]
- Karyotis, V.; Khouzani, M.H.R. Malware Diffusion Models for Modern Complex Networks: Theory and Applications; Morgan Kaufmann: Burlington, MA, USA, 2016. [Google Scholar]
- Cui, B.J.; Jin, H.F.; Carullo, G.; Liu, Z.L. Service-oriented mobile malware detection system based on mining strategies. Pervasive Mob. Comput. 2015, 2015, 101–116. [Google Scholar] [CrossRef]
- Jaint, B.; Indu, S.; Pandey, N.; Pahwa, K. Malicious Node Detection in Wireless Sensor Networks Using Support Vector Machine. In Proceedings of the International Conference on Recent Developments in Control, Automation & Power Engineering, Noida, India, 10–11 October 2019; pp. 247–252. [Google Scholar]
- Thaile, M.; Ramanaiah, O.B.V. Node Compromise Detection Based on NodeTrust in Wireless Sensor Networks. In Proceedings of the International Conference on Computer Communication and Informatics, Coimbatore, India, 7–9 January 2016. [Google Scholar]
- Butun, I.; Osterberg, P.; Song, H.B. Security of the Internet of Things: Vulnerabilities, Attacks, and Countermeasures. IEEE Commun. Sur. Tutor. 2020, 22, 616–644. [Google Scholar] [CrossRef] [Green Version]
- Ai, J.J.; Chen, H.C.; Guo, Z.H.; Cheng, G.Z.; Baker, T. Mitigating malicious packets attack via vulnerability-aware heterogeneous network devices assignment. Futur. Gener. Comp. Syst. 2020, 111, 841–852. [Google Scholar] [CrossRef]
- Hernández Guillén, J.D.; Martín del Rey, A. A mathematical model for malware spread on WSNs with population dynamics. Phys. A 2020, 545, 123609. [Google Scholar]
- Huang, D.W.; Yang, L.X.; Yang, X.F.; Wu, Y.B.; Tang, Y.Y. Towards understanding the effectiveness of patch injection. Phys. A 2019, 526, 120956. [Google Scholar] [CrossRef]
- Zhu, L.H.; Zhou, M.T.; Zhang, Z.D. Dynamical Analysis and Control Strategies of Rumor Spreading Models in Both Homogeneous and Heterogeneous Networks. J. Nonlinear Sci. 2020, 30, 2545–2576. [Google Scholar] [CrossRef]
- Shen, S.G.; Zhou, H.P.; Feng, S.; Liu, J.H.; Zhang, H.; Cao, Q.Y. An Epidemiology-Based Model for Disclosing Dynamics of Malware Propagation in Heterogeneous and Mobile WSNs. IEEE Access 2020, 8, 43876–43887. [Google Scholar] [CrossRef]
- Zhu, L.H.; Guan, G. Dynamical analysis of a rumor spreading model with self-discrimination and time delay in complex networks. Phys. A 2019, 533, 121953. [Google Scholar] [CrossRef]
- Srivastava, P.K.; Pandey, S.P.; Gupta, N.; Singh, S.P.; Ojha, R.P. Modeling and Analysis of Antimalware Effect on Wireless Sensor Network. In Proceedings of the ICCCS 2019, Singapore, 23–25 February 2019. [Google Scholar]
- Hosseini, S.; Azgomi, M.A. The dynamics of an SEIRS-QV malware propagation model in heterogeneous networks. Phys. A 2018, 512, 803–817. [Google Scholar] [CrossRef]
- Ojha, R.P.; Srivastava, P.K.; Sanyal, G.; Gupta, N. Improved Model for the Stability Analysis of Wireless Sensor Network Against Malware Attacks. Wirel. Pers. Commun. 2020. [Google Scholar] [CrossRef]
- Biswal, S.R.; Swain, S.K. Model for Study of Malware Propagation Dynamics in Wireless Sensor Network. In Proceedings of the ICOEI 2019, Tirunelveli, India, 23–25 April 2019. [Google Scholar]
- Al-Tous, H.; Barhumi, I. Differential Game for Resource Allocation in Energy Harvesting Sensor Networks. In Proceedings of the IEEE ICC 2018, Kansas City, MO, USA, 20–24 May 2018. [Google Scholar]
- Huang, Y.H.; Zhu, Q.Y. A Differential Game Approach to Decentralized Virus-Resistant Weight Adaptation Policy Over Complex Networks. IEEE Trans. Control Netw. Syst. 2020, 7, 944–955. [Google Scholar] [CrossRef] [Green Version]
- Zhang, L.T.; Xu, J. Differential Security Game in Heterogeneous Device-to-Device Offloading Network Under Epidemic Risks. IEEE Trans. Netw. Sci. Eng. 2020, 7, 1852–1861. [Google Scholar] [CrossRef]
- Shen, S.G.; Li, H.J.; Han, R.S.; Vasilakos, A.V.; Wang, Y.H.; Cao, Q.Y. Differential Game-Based Strategies for Preventing Malware Propagation in Wireless Sensor Networks. IEEE Trans. Inf. Forensics Secur. 2014, 9, 1962–1973. [Google Scholar] [CrossRef]
- Liu, G.Y.; Peng, B.H.; Zhong, X.J.; Cheng, L.F.; Li, Z.F. Attack-Defense Game between Malicious Programs and Energy-Harvesting Wireless Sensor Networks Based on Epidemic Modeling. Complexity 2020, 2020, 3680518. [Google Scholar] [CrossRef]
- Miao, L.; Li, S. A Differential Game-Theoretic Approach for the Intrusion Prevention Systems and Attackers in Wireless Networks. Wirel. Pers. Commun. 2018, 103, 1993–2003. [Google Scholar] [CrossRef]
- Zhang, H.W.; Jiang, L.; Huang, S.R.; Wang, J.D.; Zhang, Y.C. Attack-Defense Differential Game Model for Network Defense Strategy Selection. IEEE Access 2019, 7, 50618–50629. [Google Scholar] [CrossRef]
- Hu, J.H.; Qian, Q.; Fang, A.; Fang, S.Z.; Xie, Y. Optimal Data Transmission Strategy for Healthcare- Based Wireless Sensor Networks: A Stochastic Differential Game Approach. Wirel. Pers. Commun. 2016, 89, 1295–1313. [Google Scholar] [CrossRef]
- Sun, Y.; Li, Y.B.; Chen, X.H.; Li, J. Optimal defense strategy model based on differential game in edge computing. J. Intell. Fuzzy Syst. 2020, 39, 1449–1459. [Google Scholar] [CrossRef]
- Eshghi, S.; Khouzani, M.H.R.; Sarkar, S. Optimal Patching in Clustered Malware Epidemics. IEEE-ACM Trans. Netw. 2016, 24, 283–298. [Google Scholar] [CrossRef] [Green Version]
- Khouzani, M.H.R.; Sarkar, S.; Altman, E. Optimal Dissemination of Security Patches in Mobile Wireless Networks. IEEE Trans. Inf. Theory 2012, 58, 4714–4732. [Google Scholar] [CrossRef]
- Sarkar, S.; Khouzani, M.H.R.; Kar, K. Optimal Routing and Scheduling in Multihop Wireless Renewable Energy Networks. IEEE Trans. Autom. Control 2013, 58. [Google Scholar] [CrossRef] [Green Version]
- Wang, K.; Wang, L.; Lin, C.; Obaidat, M.S.; Alam, M. Prolonging lifetime for wireless rechargeable sensor networks through sleeping and charging scheduling. Int. J. Commun. Syst. 2020, 33, e4355. [Google Scholar] [CrossRef]
- Yorke, J.A. Invariance for ordinary differential equations. Math. Syst. Theory 1967, 1, 353–372. [Google Scholar] [CrossRef]
- Wiggins, S. Introduction to Applied Nonlinear Dynamical Systems and Chaos; Springer: New York, NY, USA, 2003; Volume 2. [Google Scholar]
- Diekmann, O.; Heesterbeek, H.; Britton, T. Mathematical Tools for Understanding Infectious Disease Dynamics; Princeton University Press: Princeton, NJ, USA, 2013. [Google Scholar]
- van den Diressche, P.; Watmough, J. Further notes on the basic reproduction number. In Mathematical Epidemiology; Brauer, F., van den Driessche, P., Wu, J., Eds.; Springer: Berlin/Heisenberg, Germany, 2008; pp. 159–178. [Google Scholar]
- Merkin, D.R. Introduction to the Theory of the Stability; Springer: New York, NY, USA, 2012; Volume 24. [Google Scholar]
- Lyapunov, A.M. The general problem of the stability of motion. Int. J. Control 1992, 55, 531–534. [Google Scholar] [CrossRef]
- Lasalle, J.P. The Stability of Dynamical Systems; SIAM: Philadelphia, PA, USA, 1976. [Google Scholar]
- Freedman, H.; Ruan, S.; Tang, M. Uniform persistence and flows near a closed positively invariant set. J. Dyn. Differ. Equ. 1994, 6, 583–600. [Google Scholar] [CrossRef] [Green Version]
- Hutson, V.; Schmitt, K. Permanence and the dynamics of biological systems. Math. Biosci. 1992, 111, 1–71. [Google Scholar] [CrossRef]
- Li, M.L.; Muldowney, J.S. A geometric approach to the global-stability problems. J. Math. Anal. 1996, 27, 1070–1083. [Google Scholar] [CrossRef]
- Cushing, J.M. Nonlinear matrix models and population dynamics. Nat. Resour. Model. 1988, 2, 539–580. [Google Scholar] [CrossRef]
- Avner, F. Differential games. In Handbook of Game Theory; Aumann, R.J., Hart, S., Eds.; Elsevier: Amsterdam, The Netherlands, 1994; Volume 2. [Google Scholar]
- Bressan, A. Noncooperative differential games. Milan J. Math. 2011, 79, 357–427. [Google Scholar] [CrossRef]
- Isaacs, R. Differential Game; Wiley: New York, NY, USA, 1965. [Google Scholar]


| Authors | Model | Characteristics | Stability |
|---|---|---|---|
| J.D. HernándezGuillén et al. [20] | SCIRS | Considering the carrier state, population dynamics, and vaccination and reinfection processes | Local and global stability in malware-free and epidemic points |
| S.G. Shen et al. [23] | VCQPS | Considering both the heterogeneity and mobility of heterogeneous and mobile sensor nodes | Local and global stability in malware-free point |
| Linhe Zhu et al. [24] | SBD | Considering the nonlinear incidence rate and time delay in complex networks | Local and global stability in rumor-free point |
| P.K. Srivastava et al. [25] | SEIAR | Considering the anti-malware process | Local and global stability in worm-free point |
| S. Hosseini et al. [26] | SEIRS-QV | Considering the impacts of user awareness, network delay and diverse configuration of nodes | Local and global stability in malware-free point |
| D.W. Huang et al. [21] | SIPS | Considering the patch injection mechanism | Local and global stability in epidemic point |
| L.H. Zhu et al. [22] | I2S2R | Considering the effect of time delay both in homogeneous networks and heterogeneous networks | Local and global stability in malware-free and epidemic points |
| R.P. Ojha et al. [27] | SEIQRV | Considering both quarantine and vaccination techniques | Local and global stability in worm-free point |
| S.R. Biswal et al. [28] | SEIRD | Considering the early detection and removal process | Local and global stability in worm-free point |
| Authors | Participants | Goal |
|---|---|---|
| H. Al-Tous et al. [29] | An energy-harvesting (EH) multi-hop wireless sensor network (WSN) | Adaptively changing the transmitted data and power, efficiently utilizing the available harvested energy and balancing the buffer of all sensor nodes. |
| Y.H. Huang et al. [30] | Virus and nodes with various weights | Minimizing the total cost of the whole network |
| L.T. Zhang, et al. [31] | Device to Device (D2D) offloading enabled mobile network and malware | D2D offloading enabled mobile network aims to maximize the cost |
| S.G. Shen et al. [32] | WSNs and malware | The systems aims to minimize the cost; the malware aims to maximize the cost (the same cost function) |
| G.Y. Liu et al. [33] | WRSNs and malware | WRSNs aims to minimize the cost; malware aims to maximize the cost (the same cost) |
| L. Miao et al. [34] | Intrusion prevention systems(IPS) and the malicious attackers | IPS aims to minimize the cost A; attacker aims to maximize the cost B (two different cost functions ) |
| H.W. Zhang et al. [35] | Attacker and defender | Attacker aims to maximize the cost A; Defender aims to minimize the cost B (two different cost functions) |
| J.H. Hu et al. [36] | Healthcare-based wireless sensor network (HWSN) | HWSN aims to minimizing the transmission cost |
| Y. Sun et al. [37] | Edge nodes (ENs) | ENs aims to minimize the resource consumption |
| S. Eshghi et al. [38] | Mobile WSNs and malware | Mobile WNSs aims to minimize the cost by using optimal patching policies |
| M.H.R. Khouzani et al. [39] | Mobile WSNs and malware | By obtaining the optimal dissemination of patches, the tradeoff between security risks and bandwidth is minimized |
| S. Sarkar et al. [40] | Multi-hop wireless networks | By using the optimal routing and scheduling, the throughput of the networks is optimized |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Liu, G.; Peng, B.; Zhong, X. A Novel Epidemic Model for Wireless Rechargeable Sensor Network Security. Sensors 2021, 21, 123. https://doi.org/10.3390/s21010123
Liu G, Peng B, Zhong X. A Novel Epidemic Model for Wireless Rechargeable Sensor Network Security. Sensors. 2021; 21(1):123. https://doi.org/10.3390/s21010123
Chicago/Turabian StyleLiu, Guiyun, Baihao Peng, and Xiaojing Zhong. 2021. "A Novel Epidemic Model for Wireless Rechargeable Sensor Network Security" Sensors 21, no. 1: 123. https://doi.org/10.3390/s21010123
APA StyleLiu, G., Peng, B., & Zhong, X. (2021). A Novel Epidemic Model for Wireless Rechargeable Sensor Network Security. Sensors, 21(1), 123. https://doi.org/10.3390/s21010123







