Introduction to Reconfiguration
Abstract
1. Introduction
2. Specifying and Analyzing Reconfiguration Graphs
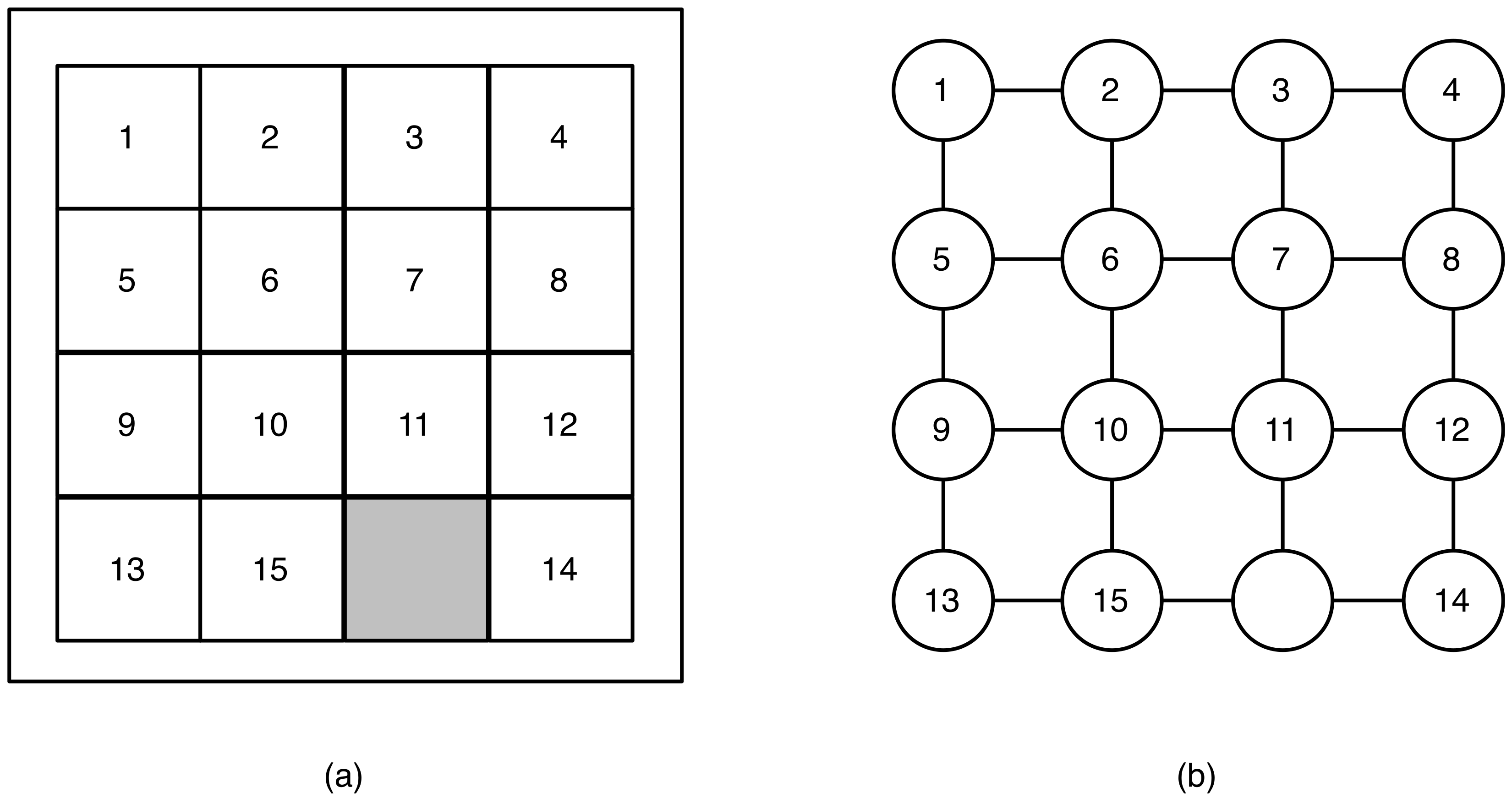
2.1. Defining Feasible Solutions and Adjacency
2.2. Defining Problems
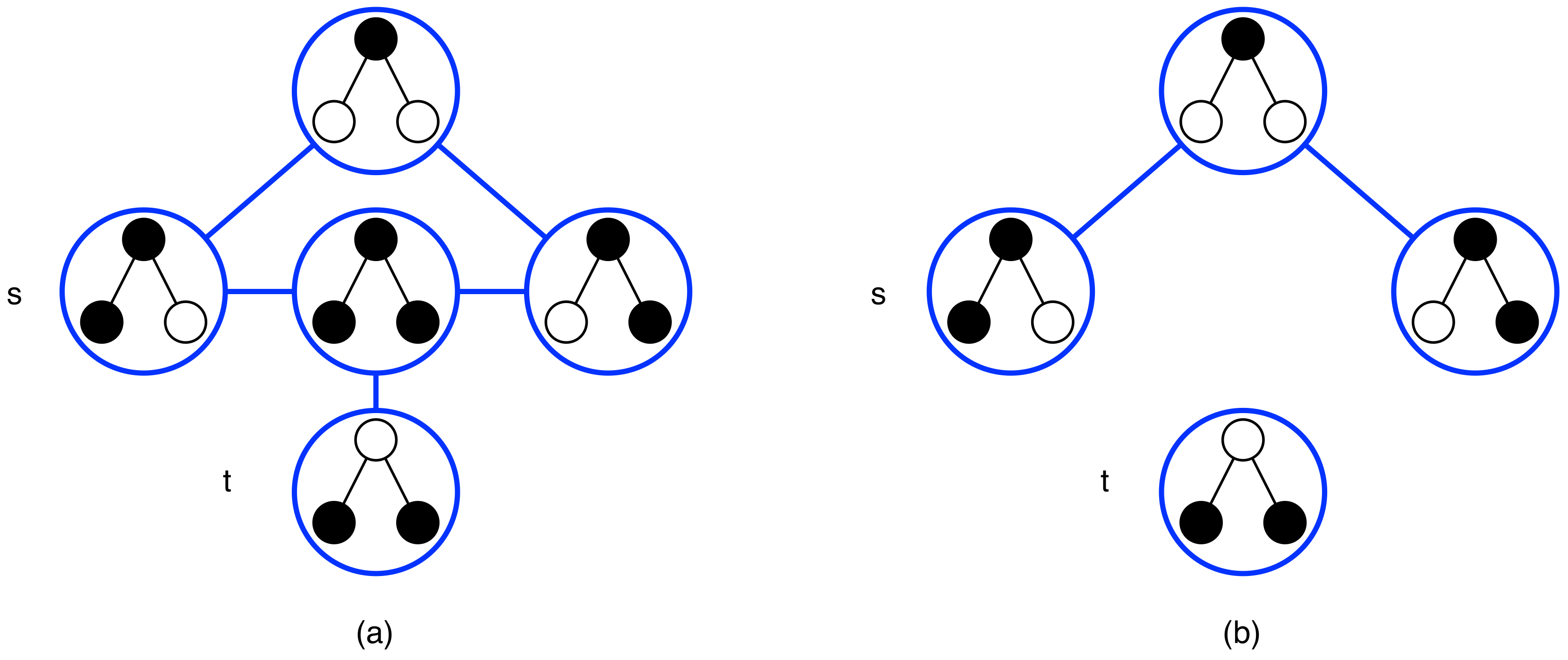
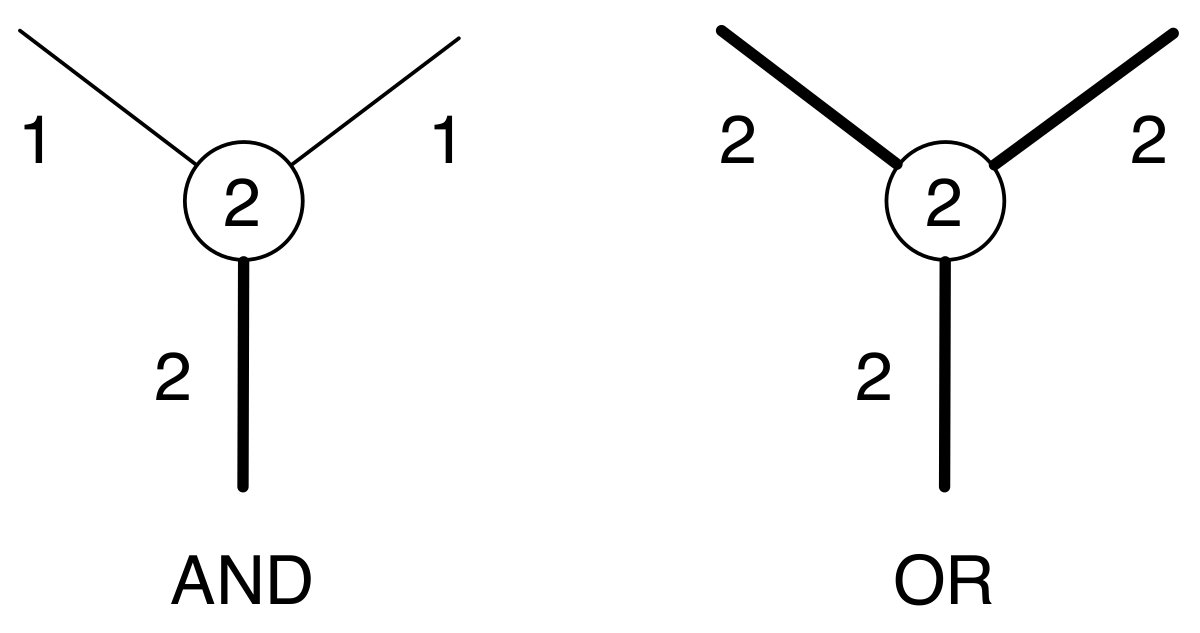
3. Tools for Proving the Complexity of Reachability
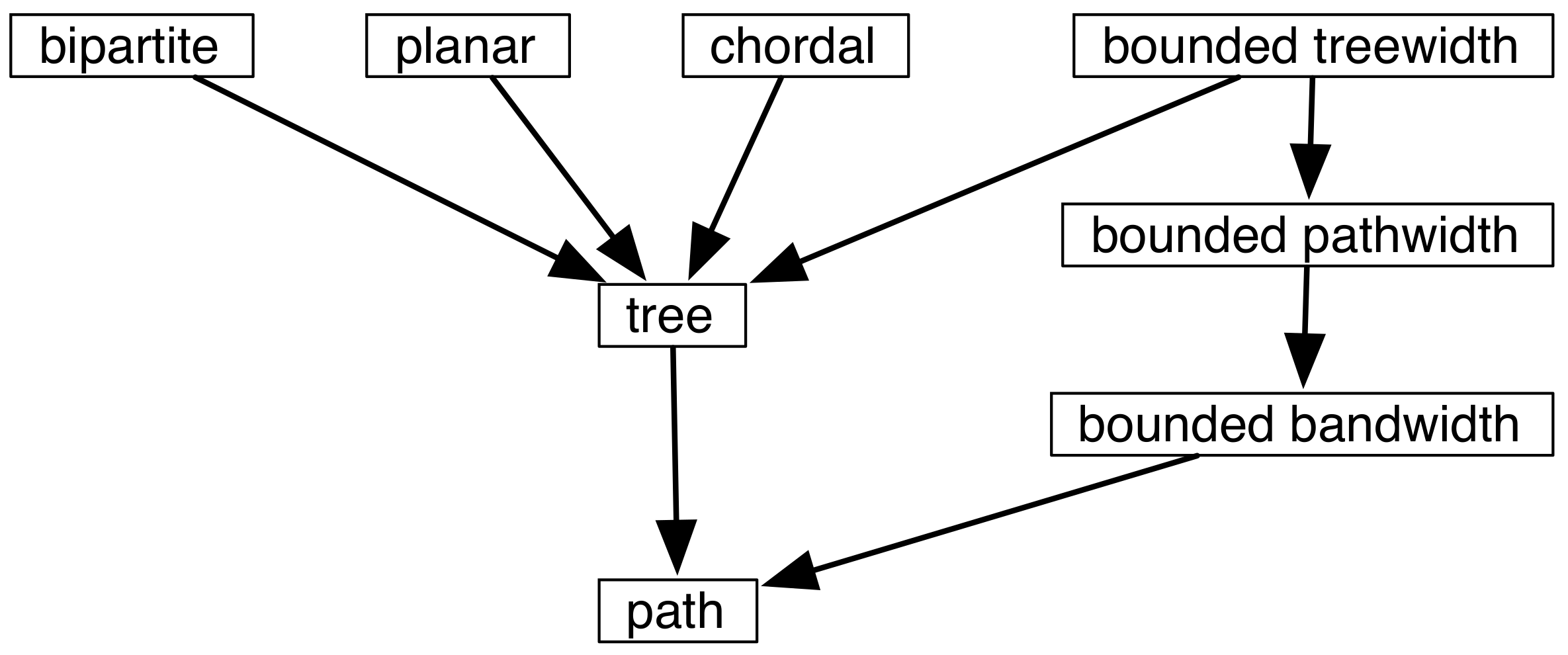
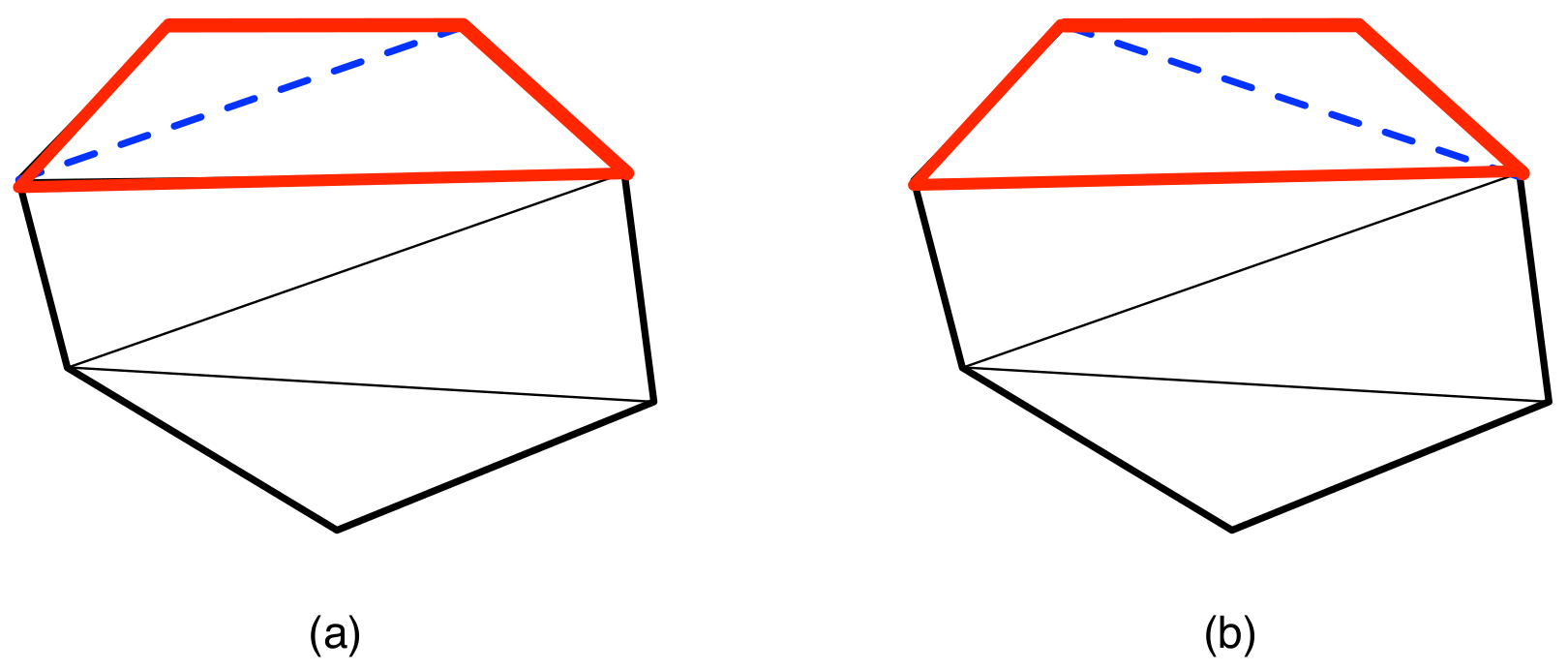
4. Analysis Using Graph Classes for Independent Set
5. Parameterized Complexity (Independent Set and Vertex Cover)
6. Connectivity and Diameter for -Coloring
6.1. k-Coloring Reconfiguration
6.2. Variants of Coloring
7. Other Structural Problems
8. Shortest Transformation
9. Labels and Colors on Tokens
9.1. Generalizing the 15-Puzzle
9.2. Placing Tokens on All Vertices
10. Further Research Directions
Acknowledgments
Conflicts of Interest
References
- Alamdari, S.; Angelini, P.; Barrera-Cruz, F.; Chan, T.M.; Da Lozzo, G.; Di Battista, G.; Frati, F.; Haxell, P.; Lubiw, A.; Patrignani, M.; et al. How to Morph Planar Graph Drawings. SIAM J. Comput. 2017, 46, 824–852. [Google Scholar] [CrossRef]
- Connelly, R.; Demaine, E.D.; Rote, G. Blowing Up Polygonal Linkages. Discret. Comput. Geom. 2003, 30, 205–239. [Google Scholar] [CrossRef]
- Johnson, W.W.; Story, W.E. Notes on the “15” Puzzle. Am. J. Math. 1879, 2, 397–404. [Google Scholar] [CrossRef]
- Ito, T.; Demaine, E.D.; Harvey, N.J.A.; Papadimitriou, C.H.; Sideri, M.; Uehara, R.; Uno, Y. On the complexity of reconfiguration problems. Theor. Comput. Sci. 2011, 412, 1054–1065. [Google Scholar] [CrossRef]
- Ahuja, R.K.; Ergun, O.; Orlin, J.B.; Punnen, A.P. A survey of very large-scale neighborhood search techniques. Discret. Appl. Math. 2002, 123, 75–102. [Google Scholar] [CrossRef]
- Fellows, M.R.; Fomin, F.V.; Lokshtanov, D.; Rosamond, F.; Saurabh, S.; Villanger, Y. Local Search: Is Brute-force Avoidable? J. Comput. Syst. Sci. 2012, 78, 707–719. [Google Scholar] [CrossRef]
- Gaspers, S.; Kim, E.J.; Ordyniak, S.; Saurabh, S.; Szeider, S. Don’t Be Strict in Local Search! In Proceedings of the Twenty-Sixth AAAI Conference on Artificial Intelligence, Toronto, ON, Canada, 22–26 July 2012; pp. 486–492. [Google Scholar]
- Gutin, G.; Punnen, A.P. (Eds.) The Traveling Salesman Problem and Its Variations; Combinatorial Optimization, Kluwer Academic: Dordrecht, UK, 2002. [Google Scholar]
- Archetti, C.; Bertazzi, L.; Speranza, M.G. Reoptimizing the traveling salesman problem. Networks 2003, 42, 154–159. [Google Scholar] [CrossRef]
- Shachnai, H.; Tamir, G.; Tamir, T. A Theory and Algorithms for Combinatorial Reoptimization. In Proceedings of the 10th Latin American Symposium on LATIN 2012: Theoretical Informatics, Arequipa, Peru, 16–20 April 2012; pp. 618–630. [Google Scholar]
- Mans, B.; Mathieson, L. Incremental Problems in the Parameterized Complexity Setting. Theory Comput. Syst. 2017, 60, 3–19. [Google Scholar] [CrossRef]
- Garey, M.R.; Johnson, D.S. Computers and Intractability: A Guide to the Theory of NP-Completeness; W. H. Freeman & Co.: New York, NY, USA, 1990. [Google Scholar]
- Cormen, T.H.; Leiserson, C.E.; Rivest, R.L.; Stein, C. Introduction to Algorithms, 3rd ed.; MIT Press: Cambridge, MA, USA, 2009. [Google Scholar]
- Van den Heuvel, J. The complexity of change. In Surveys in Combinatorics 2013; Cambridge University Press: Cambridge, UK, 2013; Volume 409, pp. 127–160. [Google Scholar]
- Mouawad, A.E. On Reconfiguration Problems: Structure and Tractability. Ph.D. Thesis, University of Waterloo, Waterloo, ON, Canada, 2015. [Google Scholar]
- Hearn, R.A.; Demaine, E.D. PSPACE-completeness of sliding-block puzzles and other problems through the nondeterministic constraint logic model of computation. Theor. Comput. Sci. 2005, 343, 72–96. [Google Scholar] [CrossRef]
- Kamiński, M.; Medvedev, P.; Milanič, M. Complexity of independent set reconfigurability problems. Theor. Comput. Sci. 2012, 439, 9–15. [Google Scholar] [CrossRef]
- Kamiński, M.; Medvedev, P.; Milanič, M. Shortest paths between shortest paths. Theor. Comput. Sci. 2011, 412, 5205–5210. [Google Scholar] [CrossRef]
- De Berg, M.; Jansen, B.M.P.; Mukherjee, D. Independent-Set Reconfiguration Thresholds of Hereditary Graph Classes. In Proceedings of the 36th IARCS Annual Conference on Foundations of Software Technology and Theoretical Computer Science, FSTTCS 2016, Chennai, India, 13–15 December 2016. [Google Scholar]
- McDonald, D.C. Connectedness and Hamiltonicity of graphs on vertex colorings. arXiv, 2015; arXiv:1507.05344. [Google Scholar]
- Fernau, H.; Haas, R.; Nishimura, N.; Seyffarth, K. Private Discussion, 2017.
- Hanaka, T.; Ito, T.; Mizuta, H.; Moore, B.; Nishimura, N.; Subramanya, V.; Suzuki, A.; Vaidyanathan, K. Reconfiguring spanning and induced subgraphs. arXiv, 2018; arXiv:1803.06074. [Google Scholar]
- Mühlenthaler, M. Degree-contrained Subgraph Reconfiguration is in P. In Proceedings of the 40th International Symposium on Mathematical Foundations of Computer Science, Milan, Italy, 24–28 August 2015; pp. 505–516. [Google Scholar]
- Hatanaka, T. Private Communication, 2017.
- Felsner, S.; Huemer, C.; Saumell, M. Recoloring Directed Graphs. In Proceedings of the XIII Encuentros de Geometría Computacional, Zaragoza, Spain, 29 June–1 July 2009; pp. 91–97. [Google Scholar]
- Garnero, V.; Junosza-Szaniawski, K.; Liedloff, M.; Montealegre, P.; Rzążewski, P. Fixing improper colorings of graphs. Theor. Comput. Sci. 2018, 711, 66–78. [Google Scholar] [CrossRef]
- Ito, T.; Ono, H.; Otachi, Y. Reconfiguration of Cliques in a Graph. In Proceedings of the 12th Annual Conference on Theory and Applications of Models of Computation, Singapore, 18–20 May 2015; pp. 212–223. [Google Scholar]
- Ito, T.; Nooka, H.; Zhou, X. Reconfiguration of Vertex Covers in a Graph. IEICE Trans. 2016, 99-D, 598–606. [Google Scholar] [CrossRef]
- Ausiello, G. Complexity and Approximation: Combinatorial Optimization Problems and Their Approximability Properties; Springer: Berlin, Germany, 1999. [Google Scholar]
- Ito, T.; Demaine, E.D. Approximability of the subset sum reconfiguration problem. J. Comb. Optim. 2014, 28, 639–654. [Google Scholar] [CrossRef]
- Cereceda, L.; van den Heuvel, J.; Johnson, M. Connectedness of the graph of vertex-colourings. Discret. Math. 2008, 308, 913–919. [Google Scholar] [CrossRef]
- Cereceda, L.; van den Heuvel, J.; Johnson, M. Finding paths between 3-colorings. J. Graph Theory 2011, 67, 69–82. [Google Scholar] [CrossRef]
- Johnson, M.; Kratsch, D.; Kratsch, S.; Patel, V.; Paulusma, D. Finding Shortest Paths Between Graph Colourings. In Proceedings of the 9th International Symposium on Parameterized and Exact Computation, IPEC 2014, Wroclaw, Poland, 10–12 September 2014; pp. 221–233. [Google Scholar]
- Gopalan, P.; Kolaitis, P.G.; Maneva, E.N.; Papadimitriou, C.H. The connectivity of Boolean satisfiability: Computational and structural dichotomies. SIAM J. Comput. 2009, 38, 2330–2355. [Google Scholar] [CrossRef]
- Bonsma, P.S.; Cereceda, L. Finding Paths between graph colourings: PSPACE-completeness and superpolynomial distances. Theor. Comput. Sci. 2009, 410, 5215–5226. [Google Scholar] [CrossRef]
- Ito, T.; Kamiński, M.; Demaine, E.D. Reconfiguration of list edge-colorings in a graph. Discret. Appl. Math. 2012, 160, 2199–2207. [Google Scholar] [CrossRef]
- Ito, T.; Kawamura, K.; Ono, H.; Zhou, X. Reconfiguration of list L(2,1)-labelings in a graph. Theor. Comput. Sci. 2014, 544, 84–97. [Google Scholar] [CrossRef]
- Mizuta, H.; Ito, T.; Zhou, X. Reconfiguration of Steiner Trees in an Unweighted Graph. In Proceedings of the 27th International Workshop on Combinatorial Algorithms, IWOCA 2016, Helsinki, Finland, 17–19 August 2016; pp. 163–175. [Google Scholar]
- Bonsma, P.S. The complexity of rerouting shortest paths. In Proceedings of the 37th International Symposium on Mathematical Foundations of Computer Science, Bratislava, Slovakia, 27–31 August 2012; pp. 222–233. [Google Scholar]
- Osawa, H.; Suzuki, A.; Ito, T.; Zhou, X. The complexity of (list) edge-coloring reconfiguration problem. In Proceedings of the 11th International Conference and Workshops on Algorithms and Computation, Limerick, Ireland, 16–20 January 2017. [Google Scholar]
- Diestel, R. Graph Theory; Electronic Edition; Springer: Berlin, Germany, 2005. [Google Scholar]
- Bonsma, P.S. Independent Set Reconfiguration in Cographs and their Generalizations. J. Graph Theory 2016, 83, 164–195. [Google Scholar] [CrossRef]
- Bonsma, P.S. Rerouting shortest paths in planar graphs. In Proceedings of the IARCS Annual Conference on Foundations of Software Technology and Theoretical Computer Science, FSTTCS 2012, Hyderabad, India, 15–17 December 2012; pp. 337–349. [Google Scholar]
- Hatanaka, T.; Ito, T.; Zhou, X. The List Coloring Reconfiguration Problem for Bounded Pathwidth Graphs. IEICE Trans. 2015, 98-A, 1168–1178. [Google Scholar] [CrossRef]
- Bonsma, P.S.; Paulusma, D. Using Contracted Solution Graphs for Solving Reconfiguration Problems. In Proceedings of the 41st International Symposium on Mathematical Foundations of Computer Science, MFCS 2016, Kraków, Poland, 22–26 August 2016. [Google Scholar]
- Schiex, T. A Note on CSP Graph Parameters; Technical Report 1999/03; French National Institute for Agricultural Research (INRA): Paris, France, 1999. [Google Scholar]
- Wrochna, M. Reconfiguration in bounded bandwidth and tree-depth. J. Comput. Syst. Sci. 2018, 93, 1–10. [Google Scholar] [CrossRef]
- Post, E.L. Recursive unsolvability of a problem of Thue. J. Symb. Log. 1947, 12, 1–11. [Google Scholar] [CrossRef]
- Mouawad, A.E.; Nishimura, N.; Raman, V.; Wrochna, M. Reconfiguration over Tree Decompositions. In Proceedings of the 9th International Symposium on Parameterized and Exact Computation, IPEC 2014, Wroclaw, Poland, 10–12 September 2014; pp. 246–257. [Google Scholar]
- Haddadan, A.; Ito, T.; Mouawad, A.E.; Nishimura, N.; Ono, H.; Suzuki, A.; Tebbal, Y. The complexity of dominating set reconfiguration. Theor. Comput. Sci. 2016, 651, 37–49. [Google Scholar] [CrossRef]
- Van der Zanden, T.C. Parameterized Complexity of Graph Constraint Logic. In Proceedings of the 10th International Symposium on Parameterized and Exact Computation, IPEC 2015, Patras, Greece, 16–18 September 2015; pp. 282–293. [Google Scholar]
- Lokshtanov, D.; Mouawad, A.E. The complexity of independent set reconfiguration on biparite graphs. In Proceedings of the 29th Annual ACM-SIAM Symposium on Discrete Algorithms, San Francisco, CA, USA, 20–22 January 2008. [Google Scholar]
- Tebbal, Y. On the Complexity of Reconfiguration of Clique, Cluster Vertex Deletion, and Dominating Set. Master’s Thesis, University of Waterloo, Waterloo, ON, Canada, 2015. [Google Scholar]
- Mouawad, A.E.; Nishimura, N.; Raman, V. Vertex Cover Reconfiguration and Beyond. In Proceedings of the 25th International Symposium on Algorithms and Computation, ISAAC 2014, Jeonju, Korea, 15–17 December 2014; pp. 452–463. [Google Scholar]
- Bonamy, M.; Bousquet, N. Reconfiguring Independent Sets in Cographs. CoRR, 2014; arXiv:1406.1433v1. [Google Scholar]
- Bonamy, M.; Bousquet, N. Token Sliding on Chordal Graphs. In Proceedings of the 43rd International Workshop on Graph-Theoretic Concepts in Computer Science (WG 2017), Eindhoven, The Netherlands, 21–23 June 2017; pp. 127–139. [Google Scholar]
- Bonsma, P.S.; Kaminski, M.; Wrochna, M. Reconfiguring Independent Sets in Claw-Free Graphs. In Proceedings of the 14th Scandinavian Symposium and Workshops on Algorithm Theory—SWAT 2014, Copenhagen, Denmark, 2–4 July 2014; pp. 86–97. [Google Scholar]
- Yamada, T.; Uehara, R. Shortest Reconfiguration of Sliding Tokens on a Caterpillar. In Proceedings of the 10th International Workshop on WALCOM: Algorithms and Computation, WALCOM 2016, Kathmandu, Nepal, 29–31 March 2016; pp. 236–248. [Google Scholar]
- Demaine, E.D.; Demaine, M.L.; Fox-Epstein, E.; Hoang, D.A.; Ito, T.; Ono, H.; Otachi, Y.; Uehara, R.; Yamada, T. Linear-time algorithm for sliding tokens on trees. Theor. Comput. Sci. 2015, 600, 132–142. [Google Scholar] [CrossRef]
- Fox-Epstein, E.; Hoang, D.A.; Otachi, Y.; Uehara, R. Sliding Token on Bipartite Permutation Graphs. In Proceedings of the 26th International Symposium on Algorithms and Computation, ISAAC 2015, Nagoya, Japan, 9–11 December 2015; pp. 237–247. [Google Scholar]
- Hoang, D.A.; Uehara, R. Polynomial-Time Algorithms for Sliding Tokens on Cactus Graphs and Block Graphs. CoRR, 2017; arXiv:1705.00429v1. [Google Scholar]
- Hoang, D.A.; Fox-Epstein, E.; Uehara, R. Sliding Tokens on Block Graphs. In Proceedings of the 11th International Conference and Workshops on WALCOM: Algorithms and Computation, WALCOM 2017, Hsinchu, Taiwan, 29–31 March 2017; pp. 460–471. [Google Scholar]
- Hoang, D.A.; Uehara, R. Sliding Tokens on a Cactus. In Proceedings of the 27th International Symposium on Algorithms and Computation, ISAAC 2016, Sydney, Australia, 12–14 December 2016. [Google Scholar]
- Mühlenthaler, M. st-Connectivity of Common Independent Sets of Partition Matroids. unpublished. 2017. [Google Scholar]
- Downey, R.G.; Fellows, M.R. Parameterized Complexity; Springer: New York, NY, USA, 1997. [Google Scholar]
- Fernau, H.; Hagerup, T.; Nishimura, N.; Ragde, P.; Reinhardt, K. On the parameterized complexity of the generalized Rush Hour puzzle. In Proceedings of the 15th Canadian Conference on Computational Geometry, Halifax, Nova Scotia, 11–13 August 2003; pp. 6–9. [Google Scholar]
- Niedermeier, R. Invitation to Fixed-Parameter Algorithms; Oxford University Press: Oxford, UK, 2006. [Google Scholar]
- Mouawad, A.E.; Nishimura, N.; Raman, V.; Simjour, N.; Suzuki, A. On the parameterized complexity of reconfiguration problems. In Proceedings of the 8th International Symposium on Parameterized and Exact Computation, Sophia Antipolis, France, 4–6 September 2013. [Google Scholar]
- Wasa, K.; Yamanaka, K.; Arimura, H. The Complexity of Induced Tree Reconfiguration Problems. In Proceedings of the 10th International Conference on Language and Automata Theory and Applications, LATA 2016, Prague, Czech Republic, 14–18 March 2016; pp. 330–342. [Google Scholar]
- Mouawad, A.E.; Nishimura, N.; Raman, V.; Simjour, N.; Suzuki, A. On the Parameterized Complexity of Reconfiguration Problems. Algorithmica 2017, 78, 274–297. [Google Scholar] [CrossRef]
- Ito, T.; Kaminski, M.; Ono, H.; Suzuki, A.; Uehara, R.; Yamanaka, K. On the Parameterized Complexity for Token Jumping on Graphs. In Proceedings of the 11th Annual Conference on Theory and Applications of Models of Computation, TAMC 2014, Chennai, India, 11–13 April 2014; pp. 341–351. [Google Scholar]
- Ito, T.; Kaminski, M.J.; Ono, H. Fixed-Parameter Tractability of Token Jumping on Planar Graphs. In Proceedings of the 25th International Symposium on Algorithms and Computation, ISAAC 2014, Jeonju, Korea, 15–17 December 2014; pp. 208–219. [Google Scholar]
- Bousquet, N.; Mary, A.; Parreau, A. Token Jumping in Minor-Closed Classes. In Proceedings of the 21st International Symposium on Fundamentals in Computation Theory (FCT 2017), Bordeaux, France, 11–13 September 2017; pp. 136–149. [Google Scholar]
- Lokshtanov, D.; Mouawad, A.E.; Panolan, F.; Ramanujan, M.S.; Saurabh, S. Reconfiguration on Sparse Graphs. In Proceedings of the 14th International Symposium on Algorithms and Data Structures, WADS 2015, Victoria, BC, Canada, 5–7 August 2015; pp. 506–517. [Google Scholar]
- Hatanaka, T.; Ito, T.; Zhou, X. Parameterized Complexity of the List Coloring Reconfiguration Problem with Graph Parameters. In Proceedings of the 42nd International Symposium on Mathematical Foundations of Computer Science (MFCS 2017), Liverpool, UK, 27–31 August 2017; pp. 51:1–51:13. [Google Scholar]
- Siebertz, S. Reconfiguration on nowhere dense graphs. CoRR, 2017; arXiv:1707.06775. [Google Scholar]
- Cereceda, L. Mixing Graph Colourings. Ph.D. Thesis, London School of Economics and Political Science, London, UK, 2007. [Google Scholar]
- Cereceda, L.; van den Heuvel, J.; Johnson, M. Mixing 3-colourings in bipartite graphs. Eur. J. Comb. 2009, 30, 1593–1606. [Google Scholar] [CrossRef]
- Bonsma, P.S.; Mouawad, A.E.; Nishimura, N.; Raman, V. The Complexity of Bounded Length Graph Recoloring and CSP Reconfiguration. In Proceedings of the 9th International Symposium on Parameterized and Exact Computation, IPEC 2014, Wroclaw, Poland, 10–12 September 2014; pp. 110–121. [Google Scholar]
- Brooks, R.L. On colouring the nodes of a network. Math. Proc. Camb. Philos. Soc. 1941, 37, 194–197. [Google Scholar] [CrossRef]
- Feghali, C.; Johnson, M.; Paulusma, D. A Reconfigurations Analogue of Brooks’ Theorem and Its Consequences. J. Graph Theory 2016, 83, 340–358. [Google Scholar] [CrossRef]
- Jerrum, M. A Very Simple Algorithm for Estimating the Number of k-Colorings of a Low-Degree Graph. Random Struct. Algorithms 1995, 7, 157–166. [Google Scholar] [CrossRef]
- Dyer, M.E.; Flaxman, A.D.; Frieze, A.M.; Vigoda, E. Randomly coloring sparse random graphs with fewer colors than the maximum degree. Random Struct. Algorithms 2006, 29, 450–465. [Google Scholar] [CrossRef]
- Bonamy, M.; Johnson, M.; Lignos, I.; Patel, V.; Paulusma, D. Reconfiguration graphs for vertex colourings of chordal and chordal bipartite graphs. J. Comb. Optim. 2014, 27, 132–143. [Google Scholar] [CrossRef]
- Bonamy, M.; Bousquet, N. Recoloring bounded treewidth graphs. Electron. Notes Discret. Math. 2013, 44, 257–262. [Google Scholar] [CrossRef]
- Bousquet, N.; Perarnau, G. Fast recoloring of sparse graphs. Eur. J. Comb. 2016, 52, 1–11. [Google Scholar] [CrossRef]
- Johnson, M.; Kratsch, D.; Kratsch, S.; Patel, V.; Paulusma, D. Finding Shortest Paths Between Graph Colourings. Algorithmica 2016, 75, 295–321. [Google Scholar] [CrossRef]
- Bonamy, M.; Dabrowski, K.K.; Feghali, C.; Johnson, M.; Paulusma, D. Recognizing Graphs Close to Bipartite Graphs with an Application to Colouring Reconfiguration. CoRR, 2017; arXiv:1707.09817v1. [Google Scholar]
- Kempe, A.B. On the geographical problem of the four colours. Am. J. Math. 1879, 2, 193–200. [Google Scholar] [CrossRef]
- Mühlenthaler, M.; Wanka, R. On the Connectedness of Clash-free Timetables. CoRR, 2015; arXiv:1507.02805. [Google Scholar]
- Fisk, S. Geometric coloring theory. Adv. Math. 1977, 24, 298–340. [Google Scholar] [CrossRef]
- Meyniel, H. Les 5-colorations d’un graphe planaire forment une classe de commutation unique. J. Comb. Theory Ser. B 1978, 24, 251–257. [Google Scholar] [CrossRef]
- Mohar, B. Kempe equivalence of colorings. In Graph Theory in Paris; Trends in Mathematics; Birkhauser: Basel, Switzerland, 2007; pp. 287–297. [Google Scholar]
- Vergnas, M.L.; Meyniel, H. Kempe classes and the Hadwiger Conjecture. J. Comb. Theory Ser. B 1981, 31, 95–104. [Google Scholar] [CrossRef]
- Bertschi, M.E. Perfectly contractile graphs. J. Comb. Theory Ser. B 1990, 50, 222–230. [Google Scholar] [CrossRef]
- McDonald, J.; Mohar, B.; Scheide, D. Kempe Equivalence of Edge-Colorings in Subcubic and Subquartic Graphs. J. Graph Theory 2012, 70, 226–239. [Google Scholar] [CrossRef]
- Belcastro, S.; Haas, R. Counting edge-Kempe-equivalence classes for 3-edge-colored cubic graphs. Discret. Math. 2014, 325, 77–84. [Google Scholar] [CrossRef]
- Bonamy, M.; Bousquet, N.; Feghali, C.; Johnson, M. On a conjecture of Mohar concerning Kempe equivalence of regular graphs. CoRR, 2015; arXiv:1510.06964. [Google Scholar]
- Feghali, C.; Johnson, M.; Paulusma, D. Kempe equivalence of colourings of cubic graphs. Eur. J. Comb. 2017, 59, 1–10. [Google Scholar] [CrossRef]
- Ito, T.; Kawamura, K.; Zhou, X. An Improved Sufficient Condition for Reconfiguration of List Edge-Colorings in a Tree. IEICE Trans. 2012, 95-D, 737–745. [Google Scholar] [CrossRef]
- Brewster, R.C.; Noel, J.A. Mixing Homomorphisms, Recolorings, and Extending Circular Precolorings. J. Graph Theory 2015, 80, 173–198. [Google Scholar] [CrossRef]
- Brewster, R.C.; McGuinness, S.; Moore, B.; Noel, J.A. A dichotomy theorem for circular colouring reconfiguration. Theor. Comput. Sci. 2016, 639, 1–13. [Google Scholar] [CrossRef]
- Vaidyanathan, K. Refiguring Graph Colorings. Master’s Thesis, University of Waterloo, Waterloo, ON, Canada, 2017. [Google Scholar]
- Wrochna, M. Homomorphism Reconfiguration via Homotopy. In Proceedings of the 32nd International Symposium on Theoretical Aspects of Computer Science, STACS 2015, Garching, Germany, 4–7 March 2015; pp. 730–742. [Google Scholar]
- Brewster, R.C.; Lee, J.B.; Moore, B.; Noel, J.A.; Siggers, M. Graph Homomorphism Reconfiguration and Frozen H-Colourings. arXiv, 2017; arXiv:1712.00200. [Google Scholar]
- Haas, R. The canonical coloring graph of trees and cycles. Ars Math. Contemp. 2012, 5, 149–157. [Google Scholar]
- Asplund, J.; Edoh, K.; Haas, R.; Hristova, Y.; Novick, B.; Werner, B. Reconfiguration graphs of shortest paths. CoRR, 2017; arXiv:1705.09385. [Google Scholar]
- Fatehi, D.; Alikhani, S.; Khalaf, A.J.M. The k-independent graph of a graph. Adv. Appl. Discret. Math. 2017, 18, 45–56. [Google Scholar] [CrossRef]
- Monroy, R.F.; Flores-Peñaloza, D.; Huemer, C.; Hurtado, F.; Urrutia, J.; Wood, D.R. Token Graphs. Graphs Comb. 2012, 28, 365–380. [Google Scholar] [CrossRef]
- Choo, K.; MacGillivray, G. Gray code numbers for graphs. Ars Math. Contemp. 2011, 4, 125–139. [Google Scholar]
- Celaya, M.; Choo, K.; MacGillivray, G.; Seyffarth, K. Reconfiguring k-colourings of complete bipartite graphs. Kyungpook Math. J. 2016, 56, 647–655. [Google Scholar] [CrossRef]
- Bard, S. Gray Code Numbers of Complete Multipartite Graphs. Master’s Thesis, University of Victoria, Victoria, BC, Canada, 2012. [Google Scholar]
- Beier, J.; Fierson, J.; Haas, R.; Russell, H.M.; Shavo, K. Classifying coloring graphs. Discret. Math. 2016, 339, 2100–2112. [Google Scholar] [CrossRef]
- Haas, R.; Seyffarth, K. The k-Dominating Graph. Graphs Comb. 2014, 30, 609–617. [Google Scholar] [CrossRef]
- Alikhani, S.; Fatehi, D.; Klavzar, S. On the Structure of Dominating Graphs. Graphs Comb. 2017, 33, 665–672. [Google Scholar] [CrossRef]
- Subramanian, K.; Sridharan, N. γ-graph of a graph. Bull. Kerala Math. Assoc. 2008, 5, 17–34. [Google Scholar]
- Fricke, G.; Hedetniemi, S.M.; Hedetniemi, S.T.; Hutson, K.R. γ-graphs of graphs. Discuss. Math. Graph Theory 2011, 31, 517–531. [Google Scholar] [CrossRef]
- Mynhardt, C.M.; Teshima, L.E. A note on some variations of the γ-graph. CoRR, 2017; arXiv:1707.02039. [Google Scholar]
- Edwards, M. Vertex-Criticality and Bicriticality for Independent Domination and Total Domination in Graphs. Ph.D. Thesis, University of Victoria, Victoria, BC, Canada, 2015. [Google Scholar]
- Lakshmanan, S.A.; Vijayakumar, A. The gamma graph of a graph. AKCE Int. J. Graphs Comb. 2010, 7, 53–59. [Google Scholar]
- Sridharan, N.; Subramanian, K. Trees and unicyclic graphs are γ-graphs. J. Comb. Math. Comb. Comput. 2009, 69, 231–236. [Google Scholar]
- Sridharan, N.; Amutha, S.; Rao, S.B. Induced subgraphs of gamma graphs. Discret. Math. Algorithms Appl. 2013, 5. [Google Scholar] [CrossRef]
- Dyck, A.; Jedwab, J.; DeVos, M.; Simon, S. The realisability of γ-graphs. unpublished. 2017. [Google Scholar]
- Dyck, A. The Realisability of γ-Graphs. Master’s Thesis, Simon Fraser University, Burnaby, BC, Canda, 2017. [Google Scholar]
- Bień, A. Gamma graphs of some special classes of trees. Ann. Math. Sil. 2015, 29, 25–34. [Google Scholar] [CrossRef]
- Connelly, E.; Hedetniemi, S.T.; Hutson, K. A note on γ-Graphs. AKCE Int. J. Graphs Comb. 2010, 8, 23–31. [Google Scholar]
- Suzuki, A.; Mouawad, A.E.; Nishimura, N. Reconfiguration of dominating sets. J. Comb. Optim. 2016, 32, 1182–1195. [Google Scholar] [CrossRef]
- Haas, R.; Seyffarth, K. Reconfiguring dominating sets in some well-covered and other classes of graphs. Discret. Math. 2017, 340, 1802–1817. [Google Scholar] [CrossRef]
- Schaefer, T.J. The Complexity of Satisfiability Problems. In Proceedings of the 10th Annual ACM Symposium on Theory of Computing, San Diego, CA, USA, 1–3 May 1978; pp. 216–226. [Google Scholar]
- Schwerdtfeger, K.W. A Computational Trichotomy for Connectivity of Boolean Satisfiability. J. Satisf. Boolean Model. Comput. 2014, 8, 173–195. [Google Scholar]
- Makino, K.; Tamaki, S.; Yamamoto, M. On the Boolean connectivity problem for Horn relations. Discret. Appl. Math. 2010, 158, 2024–2030. [Google Scholar] [CrossRef]
- Makino, K.; Tamaki, S.; Yamamoto, M. An exact algorithm for the Boolean connectivity problem for k-CNF. Theor. Comput. Sci. 2011, 412, 4613–4618. [Google Scholar] [CrossRef]
- Mouawad, A.E.; Nishimura, N.; Pathak, V.; Raman, V. Shortest Reconfiguration Paths in the Solution Space of Boolean Formulas. In Proceedings of the 42nd International Colloquium on Automata, Languages, and Programming, ICALP 2015, Kyoto, Japan, 6–10 July 2015; Part I. pp. 985–996. [Google Scholar]
- Gharibian, S.; Sikora, J. Ground State Connectivity of Local Hamiltonians. In Proceedings of the 42nd International Colloquium on Automata, Languages, and Programming, ICALP 2015, Kyoto, Japan, 6–10 July 2015; Part I. 2015; pp. 617–628. [Google Scholar]
- Lawson, C. Software for c1 surface interpolation. In Mathematical Software III; Academic Press: Cambridge, MA, USA, 1977; pp. 161–194. [Google Scholar]
- Lubiw, A.; Pathak, V. Flip distance between two triangulations of a point set is NP-complete. Comput. Geom. 2015, 49, 17–23. [Google Scholar] [CrossRef]
- Pilz, A. Flip distance between triangulations of a planar point set is APX-hard. Comput. Geom. 2014, 47, 589–604. [Google Scholar] [CrossRef]
- Kanj, I.A.; Xia, G. Flip Distance is in FPT time O(n + k · ck). In Proceedings of the 32nd International Symposium on Theoretical Aspects of Computer Science, STACS 2015, Garching, Germany, 4–7 March 2015; pp. 500–512. [Google Scholar]
- Yamanaka, K.; Demaine, E.D.; Ito, T.; Kawahara, J.; Kiyomi, M.; Okamoto, Y.; Saitoh, T.; Suzuki, A.; Uchizawa, K.; Uno, T. Swapping labeled tokens on graphs. Theor. Comput. Sci. 2015, 586, 81–94. [Google Scholar] [CrossRef]
- Papadimitriou, C.H.; Raghavan, P.; Sudan, M.; Tamaki, H. Motion Planning on a Graph (Extended Abstract). In Proceedings of the 35th Annual Symposium on Foundations of Computer Science, Santa Fe, NM, USA, 20–22 November 1994; pp. 511–520. [Google Scholar]
- Wu, Z.; Grumbach, S. Feasibility of motion planning on acyclic and strongly connected directed graphs. Discret. Appl. Math. 2010, 158, 1017–1028. [Google Scholar] [CrossRef]
- Călinescu, G.; Dumitrescu, A.; Pach, J. Reconfigurations in Graphs and Grids. SIAM J. Discret. Math. 2008, 22, 124–138. [Google Scholar] [CrossRef]
- Yamanaka, K.; Demaine, E.D.; Horiyama, T.; Kawamura, A.; Nakano, S.; Okamoto, Y.; Saitoh, T.; Suzuki, A.; Uehara, R.; Uno, T. Sequentially Swapping Colored Tokens on Graphs. In Proceedings of the 11th International Conference and Workshops on WALCOM: Algorithms and Computation (WALCOM 2017), Hsinchu, Taiwan, 29–31 March 2017; pp. 435–447. [Google Scholar]
- Dumitrescu, A.; Pach, J. Pushing Squares Around. Graphs Comb. 2006, 22, 37–50. [Google Scholar] [CrossRef]
- Lubiw, A.; Masárová, Z.; Wagner, U. Proof of the Orbit Conjecture for Flipping Edge-Labelled Triangulations. In Proceedings of the 33rd International Symposium on Computational Geometry, Brisbane, Australia, 4–7 July 2017. [Google Scholar]
- Moore, B.; Nishimura, N.; Subramanya, V. Reconfiguring minors. unpublished. 2018. [Google Scholar]
- Wilson, R.M. Graph puzzles, homotopy, and the alternating group. J. Comb. Theory Ser. B 1974, 16, 86–96. [Google Scholar] [CrossRef]
- Parberry, I. Solving the (n2 - 1)-Puzzle with 8/3 n3 Expected Moves. Algorithms 2015, 8, 459–465. [Google Scholar] [CrossRef]
- Ratner, D.; Warmuth, M.K. Finding a Shortest Solution for the N × N Extension of the 15-PUZZLE Is Intractable. In Proceedings of the 5th National Conference on Artificial Intelligence, Philadelphia, PA, USA, 11–15 August 1986; Volume 1, pp. 168–172. [Google Scholar]
- Goldreich, O. Finding the Shortest Move-Sequence in the Graph-Generalized 15-Puzzle Is NP-Hard. In Studies in Complexity and Cryptography. Miscellanea on the Interplay between Randomness and Computation—In Collaboration with Lidor Avigad, Mihir Bellare, Zvika Brakerski, Shafi Goldwasser, Shai Halevi, Tali Kaufman, Leonid Levin, Noam Nisan, Dana Ron, Madhu Sudan, Luca Trevisan, Salil Vadhan, Avi Wigderson, David Zuckerman; Springer: Berlin/Heidelberg, Gernamy, 2011; pp. 1–5. [Google Scholar]
- Kornhauser, D.; Miller, G.L.; Spirakis, P.G. Coordinating Pebble Motion on Graphs, the Diameter of Permutation Groups, and Applications. In Proceedings of the 25th Annual Symposium on Foundations of Computer Science, West Palm Beach, FL, USA, 24–26 October 1984; pp. 241–250. [Google Scholar]
- Auletta, V.; Monti, A.; Parente, M.; Persiano, P. A Linear-Time Algorithm for the Feasibility of Pebble Motion on Trees. Algorithmica 1999, 23, 223–245. [Google Scholar] [CrossRef]
- Goraly, G.; Hassin, R. Multi-Color Pebble Motion on Graphs. Algorithmica 2010, 58, 610–636. [Google Scholar] [CrossRef]
- Trakultraipruk, S. Connectivity Properties of Some Transformation Graphs. Ph.D. Thesis, London School of Economics and Political Science, London, UK, 2013. [Google Scholar]
- Akers, S.B.; Krishnamurthy, B. A Group-Theoretic Model for Symmetric Interconnection Networks. IEEE Trans. Comput. 1989, 38, 555–566. [Google Scholar] [CrossRef]
- Miltzow, T.; Narins, L.; Okamoto, Y.; Rote, G.; Thomas, A.; Uno, T. Approximation and Hardness of Token Swapping. In Proceedings of the 24th Annual European Symposium on Algorithms, ESA 2016, Aarhus, Denmark, 22–24 August 2016. [Google Scholar]
- Bonnet, É.; Miltzow, T.; Rzążewski, P. Complexity of Token Swapping and its Variants. In Proceedings of the 34th Symposium on Theoretical Aspects of Computer Science, STACS 2017, Hannover, Germany, 8–11 March 2017. [Google Scholar]
- Cayley, A. LXXVII. Note on the theory of permutations. Philos. Mag. 1849, 34, 527–529. [Google Scholar] [CrossRef]
- Pak, I. Reduced decompositions of permutations in terms of star transpositions, generalized Catalan numbers and k-ARY trees. Discret. Math. 1999, 204, 329–335. [Google Scholar] [CrossRef]
- Yasui, G.; Abe, K.; Yamanaka, K.; Hirayama, T. Swapping Labeled Tokens on Complete Split Graphs. Inf. Process. Soc. Jpn. SIG Tech. Rep. 2015, 2015-AL-153, 1–4. [Google Scholar]
- Heath, L.S.; Vergara, J.P.C. Sorting by Short Swaps. J. Comput. Biol. 2003, 10, 775–789. [Google Scholar] [CrossRef] [PubMed]
- Yamanaka, K.; Horiyama, T.; Kirkpatrick, D.G.; Otachi, Y.; Saitoh, T.; Uehara, R.; Uno, Y. Swapping Colored Tokens on Graphs. In Proceedings of the 14th International Symposium on Algorithms and Data Structures, WADS 2015, Victoria, BC, Canada, 5–7 August 2015; pp. 619–628. [Google Scholar]
- Fujita, S.; Nakamigawa, T.; Sakuma, T. Colored pebble motion on graphs. Eur. J. Comb. 2012, 33, 884–892. [Google Scholar] [CrossRef]
- Kawahara, J.; Saitoh, T.; Yoshinaka, R. The Time Complexity of the Token Swapping Problem and Its Parallel Variants. In Proceedings of the 11th International Conference and Workshops on WALCOM: Algorithms and Computation (WALCOM 2017), Hsinchu, Taiwan, 29–31 March 2017; pp. 448–459. [Google Scholar]
- Ito, T.; Kakimura, N.; Kamiyama, N.; Kobayashi, Y.; Okamoto, Y. Reconfiguration of Maximum-Weight b-Matchings in a Graph. In Proceedings of the 23rd International Conference on Computing and Combinatorics, COCOON 2017, Hong Kong, China, 3–5 August 2017; pp. 287–296. [Google Scholar]
- Lubiw, A.; Pathak, V. Reconfiguring Ordered Bases of a Matroid. CoRR, 2016; arXiv:1612.00958. [Google Scholar]
- Nishimura, N.; Subramanya, V. Graph Editing to a Given Neighbourhood Degree List is Fixed-Parameter Tractable. In Proceedings of the 11th Annual International Conference on International Conference on Combinatorial Optimization and Applications (COCOA 2017), Shanghai, China, 16–18 December 2017. [Google Scholar]
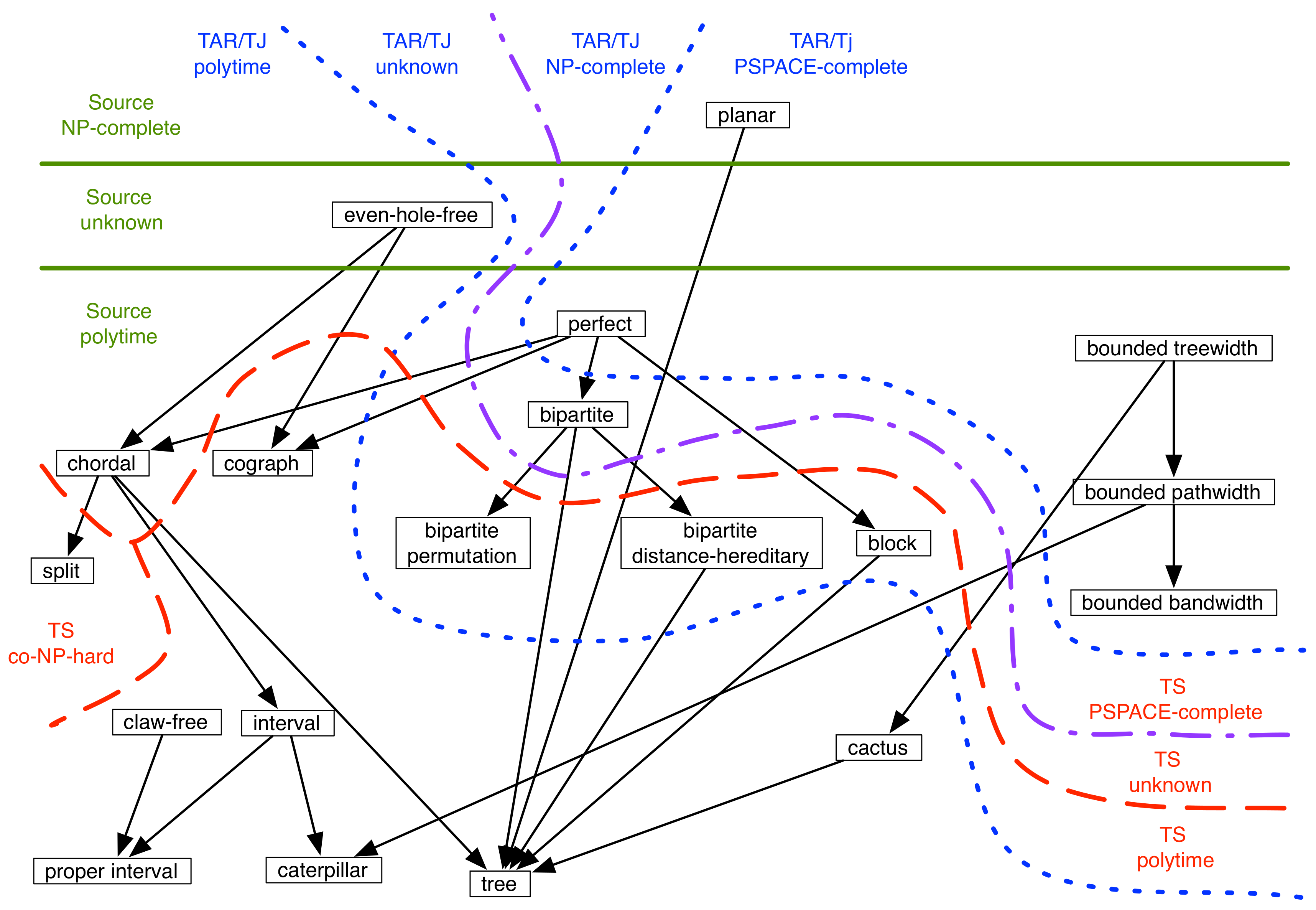
| Class | Source | TS | TAR/TJ |
|---|---|---|---|
| planar (of degree 3) | NP-complete | PSPACE-complete [17] | PSPACE-complete [17] |
| even-hole-free | ? | ? | P [17,28,54] |
| perfect | P | PSPACE-complete [17] | PSPACE-complete [17] |
| cograph | P | P [17] | P [42,55] |
| chordal | P | ? | P (since even-hole-free) |
| split | P | co-NP-hard [56] | P (since even-hole-free) |
| interval | P | P [56] | P (since even-hole-free) |
| claw-free | P | P [57] | P [57] |
| proper interval | P | P [58] | P (since even-hole-free) |
| caterpillar | P | P [58] | P (since even-hole-free) |
| tree | P | P [59] | P (since even-hole-free) |
| bipartite | P | PSPACE-complete [52] | NP-complete [52] |
| bipartite permutation | P | P [60] | ? |
| bipartite distance hereditary | P | P [60] | ? |
| block | P | P [61,62] | ? |
| bounded treewidth | P | PSPACE-complete [47] | PSPACE-complete [47] |
| bounded pathwidth | P | PSPACE-complete [47] | PSPACE-complete [47] |
| bounded bandwidth | P | PSPACE-complete [47] | PSPACE-complete [47] |
| cactus | P | P [61,63] | P [54] |
| Class | Holes | Type | Problem | Result | Citation |
|---|---|---|---|---|---|
| grid | 1 | distinct | connectivity | not connected | [3] |
| grid | 1 | distinct | connectivity | characterized | [147] |
| grid | 1 | distinct | diameter | [148] | |
| grid | 1 | distinct | shortest | NP-complete | [149] |
| any | 1 | distinct | connectivity | characterized | [147] |
| any | 1 | distinct | shortest | NP-complete | [150] |
| any | any | distinct | reachability | [151] | |
| tree | any | distinct | reachability | [152] | |
| any | any | distinct | diameter | [151] | |
| tree | any | robot | shortest | P | [140] |
| any | any | robot | shortest | NP-complete | [140] |
| any | any | colors | reachability | [153] | |
| any | any | same | shortest | P | [154] |
| any | any | colors | connectivity | characterized | [154] |
© 2018 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Nishimura, N. Introduction to Reconfiguration. Algorithms 2018, 11, 52. https://doi.org/10.3390/a11040052
Nishimura N. Introduction to Reconfiguration. Algorithms. 2018; 11(4):52. https://doi.org/10.3390/a11040052
Chicago/Turabian StyleNishimura, Naomi. 2018. "Introduction to Reconfiguration" Algorithms 11, no. 4: 52. https://doi.org/10.3390/a11040052
APA StyleNishimura, N. (2018). Introduction to Reconfiguration. Algorithms, 11(4), 52. https://doi.org/10.3390/a11040052




