Studying Semi-TCP and Its Application in Marine Internet
Abstract
:1. Introduction
2. Overview of Related Algorithms
2.1. Semi-TCP Congestion Control Algorithm Based on RTS/CTS
2.1.1. Overview of the RTS/CTS Handshake Protocol
2.2. Introduction to the Basic Idea of the Algorithm
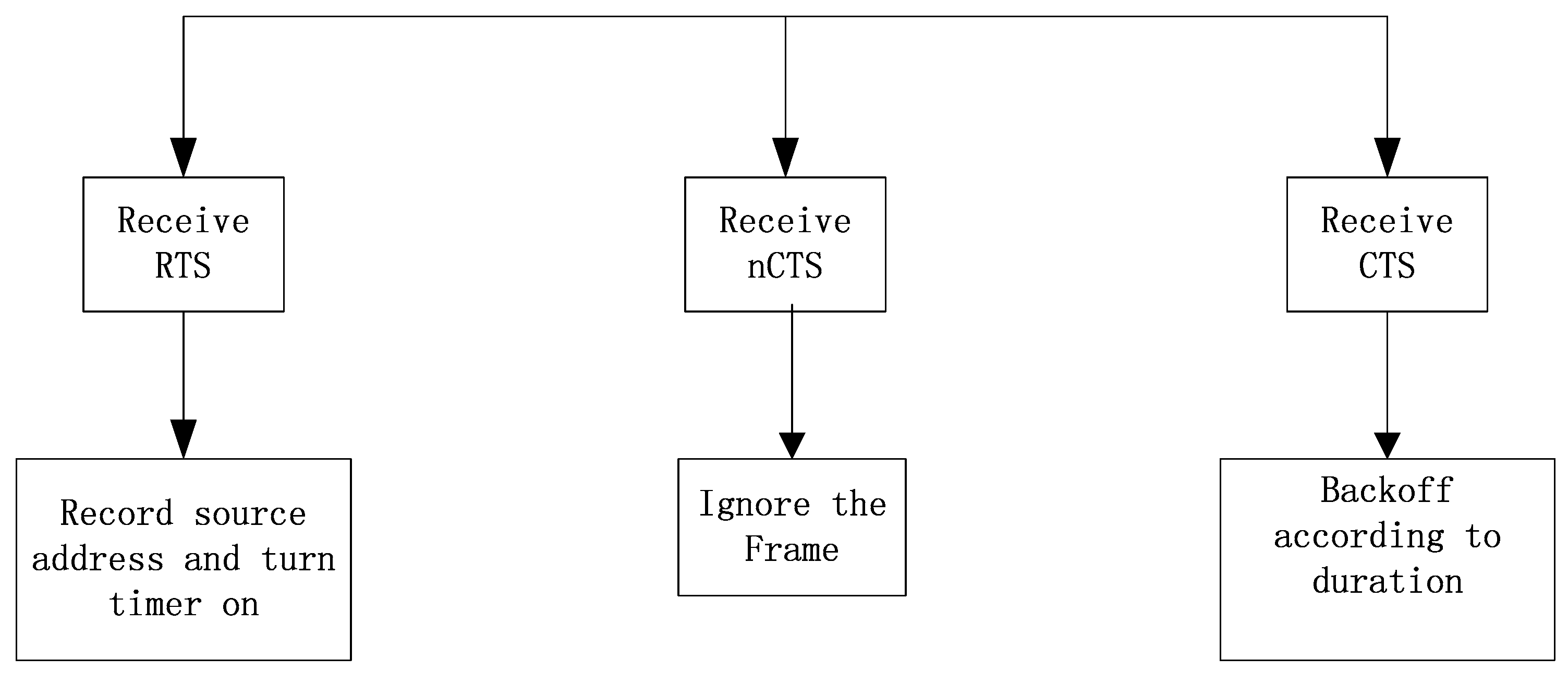
- RTSC: The sending node A sends data to node B. If A is in congestion, RTSC will be sent; otherwise, RTS will be sent.
- nCTS: After receiving the RTS frame, the receiving node B judges its own congestion status. If it is congested, it returns an nCTS frame and refuses to receive data; otherwise, it returns a CTS frame. If node A receives an nCTS, it cannot send packets to node B.
- CTSC: The introduction of CTSC frames is mainly to solve the deadlock situation. A deadlock means that two congestion nodes, say A and B, need to send data to each other to relieve their own congestion, but they are in a state of mutually rejecting each other. If both node A and node B are in a congested status, node A and B send head-data in cache to each other. The sending node A will send the RTSC frame first, and node B will reply an nCTS to reject the data. Due to node B’s rejection, nodes A and B will be in a dead-end state until they exceed the upper limit of retransmission to drop the packet. Therefore, when node B receives the RTSC, if it is determined that a deadlock may occur, the CTSC frames are returned to each other to help relieve the congestion.
3. Improvement Measures of the Algorithm
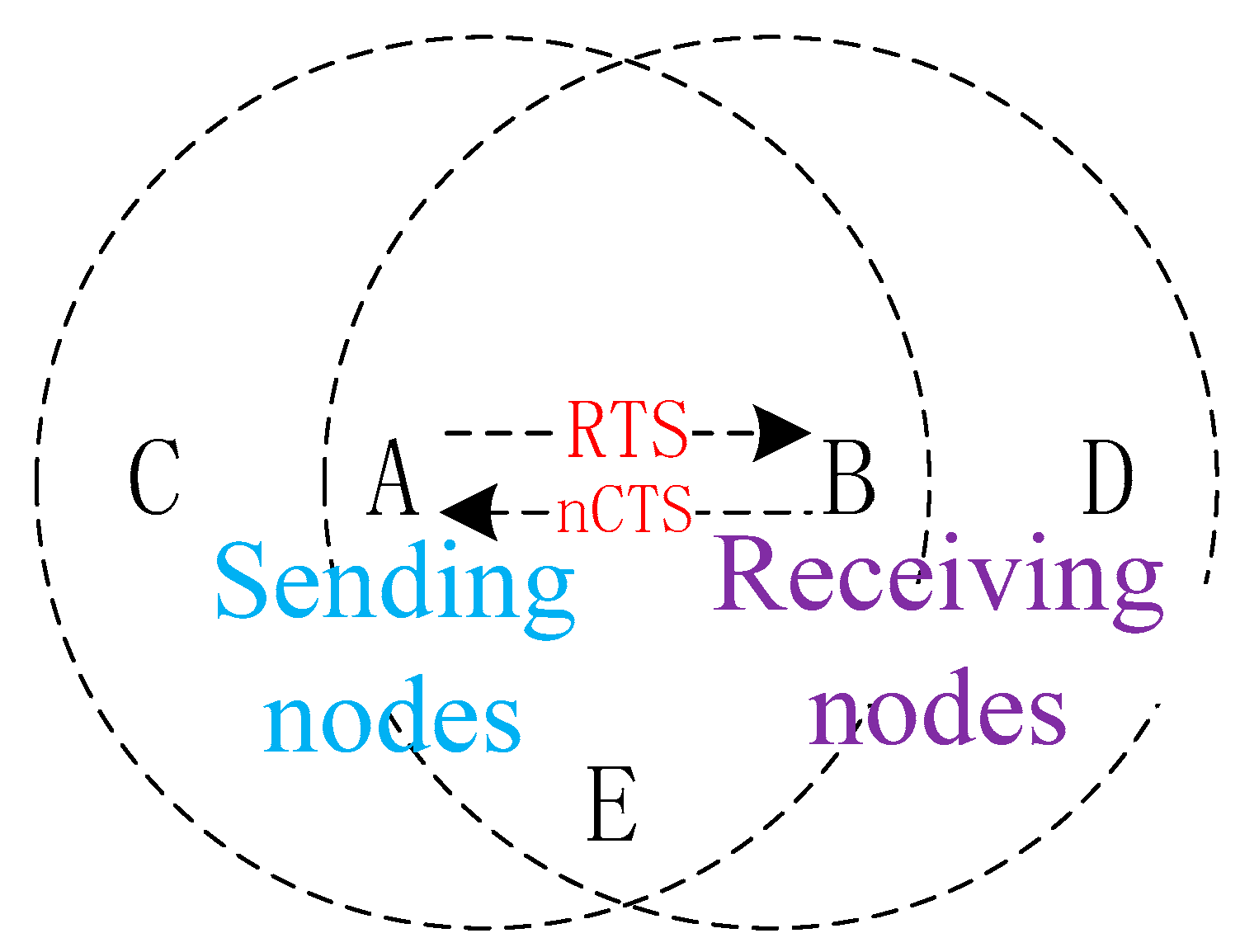
- Set the duration of an nCTS to 0 to solve the backoff problem of the hidden terminal in Figure 2.
- After the node receives an RTS frame that is not destined to itself, the node records the sending address of the frame, and at the same time initiates a Timer-for-Exposed-Terminal (TET). If no CTS or retransmitted RTS to this address is received within the certain time interval, it is determined that there is an exposed terminal and the backoff can be cancelled.
- If an nCTS is received before the Timer-for-Exposed-Terminal (TET) times out, cancel the backoff.
- When the node receives an RTS frame that is not sent to itself before the TET times out: (i) if it receives an RTS frame from another node that is not for itself, it records a new address and resets the timer; (ii) if receiving a CTS frame that is not addressed to itself, it unconditionally backs off according to Duration.
- If the node receives any control frame sent to itself when the TET is on, it will be treated as a backoff state.
4. Experimental Simulation and Analysis
4.1. Simulation Scene and Parameters
4.2. Simulation Results Analysis
5. Conclusions
Author Contributions
Acknowledgments
Conflicts of Interest
References
- Jiang, S. On the marine internet and its potential applications for underwater inter-networking. In Proceedings of the 8th ACM International Conference on Underwater Networks and Systems, Kaohsiung, Taiwan, 11–13 November 2013. [Google Scholar]
- Jiang, S.M. A Possible Development of Marine Internet: A Large Scale Heterogeneous Wireless Network. In Proceedings of the International Conference Next Generation Wired/Wireless Networking NEW2AN, Saint-Petersburg, Russia, 26–28 August 2015. [Google Scholar]
- Jiang, S.M. Fostering Marine Internet with Advanced Maritime Radio System Using Spectrums of Cellular Networks. In Proceedings of the IEEE International Conference on Communication Systems (ICCS), Shenzhen, China, 14–16 December 2016. [Google Scholar]
- Afanasyev, A.; Tilley, N.; Reiher, P.; Kleinrock, L. Host-to-host Congestion Control for TCP. IEEE Commun. Surv. Tutor. 2010, 12, 304–342. [Google Scholar] [CrossRef]
- Hanbali, A.A.; Altman, E.; Nain, P. A Survey of TCP over Ad Hoc Networks. IEEE Commun. Surv. Tutor. 2005, 7, 23–36. [Google Scholar] [CrossRef]
- Sardar, B.; Saha, D. Survey of TCP Enhancements for Last-hop Wireless Networks. IEEE Commun. Surv. Tutor. 2006, 8, 20–34. [Google Scholar] [CrossRef]
- Sundaresan, K.; Anantharaman, V.; Hsieh, H.Y.; Sivakumar, R. ATP: A reliable transport protocol for ad hoc networks. IEEE Trans. Mob. Comput. 2003, 4, 64–75. [Google Scholar]
- Christian, L.; Bjorn, S.; Martin, M. A Survey on Congestion Control or Mobile Ad Hoc Networks. Wiley Wirel. Commun. Mob. Comput. 2007, 7, 655–676. [Google Scholar]
- Fu, Z.; Greenstein, B.; Meng, X. Design and Implementation of a TCP-friendly Transport Protocol for Ad Hoc Wireless Networks. In Proceedings of the 10th IEEE International Conference on Network Protocols, Paris, France, 12–15 November 2002. [Google Scholar]
- Monzer, H.A.M.; Suhaidi, H. Loss Detection and Recovery Techniques for TCP in Mobile Ad Hoc Network. In Proceedings of the International Conference on Network Applications, Protocols and Services, Kedah, Malaysia, 22–23 September 2010; IEEE Press: Washington, DC, USA, 2010. [Google Scholar]
- Cai, Y. Semi-TCP Congestion Control Algorithm Based on RTS/CTS in Multi Hop Wireless Network; South China University of Technology: Guangzhou, China, 2010. [Google Scholar]
- Jiang, S.M.; Zuo, Q.; Wei, G. Decoupling congestion control from TCP for multi-hop wireless networks: Semi-TCP. In Proceedings of the ACM MobiCom Workshop on Challenged Networks (CHANTS), Beijing, China, 20–25 September 2009. [Google Scholar]
- Liu, M.; Jiang, S.; Lu, Y. Realization of. Semi-TCP protocol in wireless multi hop networks. Comput. Eng. 2012, 5, 79–82. [Google Scholar]
- Zhang, W. Violation analysis of wireless mobile Ad Hoc network. China Sci. Technol. 2012, 13, 62–64. [Google Scholar] [CrossRef]
- Liu, Z.; Xu, F. Research on hidden and exposed terminal problems in mobile. Ad Hoc Netw. 2010, 6, 30–37. [Google Scholar]
- Liu, S.S. ATCPL TCP for mobile ad hoc networks. IEEE J. Sel. Areas Commun. 2001, 19, 1300–1315. [Google Scholar] [CrossRef]
- Aloizio, P.; Silva, S.B.; Celso, M.; Hirata, K.O. A survey on congestion control for delay and disruption tolerant networks. Ad Hoc Netw. 2015, 25 Pt B, 480–494. [Google Scholar]
- Tassiulas, L. Adaptive back-pressure congestion control based on local Information. IEEE Trans. Autom. Control 1995, 40, 236–250. [Google Scholar] [CrossRef]
- Silva, A.P.; Obraczka, K.; Burleigh, S.; Hirata, C.M. Smart Congestion Control for Delay- and Disruption Tolerant Networks. In Proceedings of the 13th Annual IEEE International Conference on Sensing, Communication, and Networking (SECON), London, UK, 27–30 June 2016; pp. 1–9. [Google Scholar]
- Exata Network Emulator Software. Available online: https://web.scalable-networks.com/exata-network-emulator-software (accessed on 1 May 2017).
- Wu, S.; Zeng, Q.; Zhao, J. Long-distance Wireless Data Acquisition System Based on Wi-Fi. Nucl. Electron. Detect. Technol. 2012, 32, 960–964. [Google Scholar]
- Wang, Z.; Fan, W.; Zheng, L. Study and Simulation of Wave Propagation Loss Model of Sea Surface. J. Radio Wave Sci. 2008, 236, 1095–1099. [Google Scholar]







| Simulation Parameters | Values |
|---|---|
| Nodes’ moving speed | 7~10 m/s |
| Channel model | TwoRayGround |
| Attenuation model | Ricean, K = 5 |
| Frequency channel | 2.4 G |
| MAC rate | 11 Mbps |
| Sending queue | FIFO, Length 150 Kb |
| Transmission power | 33 dBm |
| Routing protocol | AODV |
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhou, L.; Jiang, S.-M.; Xiong, C.-L. Studying Semi-TCP and Its Application in Marine Internet. Future Internet 2018, 10, 44. https://doi.org/10.3390/fi10060044
Zhou L, Jiang S-M, Xiong C-L. Studying Semi-TCP and Its Application in Marine Internet. Future Internet. 2018; 10(6):44. https://doi.org/10.3390/fi10060044
Chicago/Turabian StyleZhou, Liang, Sheng-Ming Jiang, and Chen-Lin Xiong. 2018. "Studying Semi-TCP and Its Application in Marine Internet" Future Internet 10, no. 6: 44. https://doi.org/10.3390/fi10060044
APA StyleZhou, L., Jiang, S.-M., & Xiong, C.-L. (2018). Studying Semi-TCP and Its Application in Marine Internet. Future Internet, 10(6), 44. https://doi.org/10.3390/fi10060044






