Managing the Tension between Trust and Confidentiality in Mobile Supply Chains
Abstract
:1. Introduction
- RQ1:
- What is the tension between trust and confidentiality in MSCs when various information sharing scenarios are involved?
- RQ2:
- What are the applicable strategies for balancing the tension between trust and confidentiality in MSCs?
2. Theoretical Background
2.1. Trust
2.2. Confidentiality and Information Privacy
2.3. Tension between Trust and Confidentiality
2.4. Mobile Supply Chains
3. Methodology
3.1. Data Collection
3.2. Interview Protocol
3.3. Code Segments and Data Analysis
4. Results and Discussion
4.1. Decision-Making Criteria for Integration Scenarios
4.2. Integration Scenarios
4.2.1. Low-Quality Scenario
4.2.2. Conservative
4.2.3. Grey-Box Scenario
4.2.4. Innovation
4.3. Strategies for Managing the Tension between Trust and Confidentiality
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Appendix A
- 1
- Could you please explain the implementation and current status of MSCs projects in the industry and your organization?
- 2
- What would be the next steps and future of this project?
- 3
- In your opinion, how many partners need to collaborate to run MSC projects? and what is the role of each?
- 4
- What can help partners to keep trustworthy relationships in MSCs? What are the elements and factors?Questions 5 to 11 are based on the presented information scenarios: If we consider a scale for information sharing, with one side representing intensive information sharing and the other side a low level of information sharing.
- 5
- In your opinion, what is the framework of information sharing between partners in MSCs?
- 6
- How can you decide to share information or do not share? What are the criteria or situations used to make a decision?
- 7
- Let us focus on a scenario where you need to share a high level of information. Do you think there is a risk of information disclosure? In this case, how would you guarantee confidentiality regarding the information and equipment?
- 8
- Let us imagine you anticipated that your partner could produce a certain amount of information, but it turns out that they cannot. What would be your approach if your partner cannot continue the production or research without the information?
- 9
- (depends on the answers to previous questions) According to the contract, you are obliged to share a certain amount of information with you partner, and they are aware that some amount of information is not shared with them. How will it affect their relationship with you ( in terms of uncertainty/ lack of trust/ having a bad experience)? Do you think it could affect your mutual trust level?
- 10
- What can help you keep a trustworthy relationship in both situations (high information exchange/low information exchange)?
- 11
- From your experience, what is the interplay between confidentiality and trust in mobile supply chains?
- 12
- In which applications is it possible to run a mobile asset but share a low level of information?
- 13
- In your opinion, what are the challenges of information exchange in MSCs compared to traditional supply chains?
References
- Aßmann, U.; Buscher, U.; Engesser, S.; Schönberger, J.; Urbas, L. Software-Defined Mobile Supply Chains. In International Conference on Dynamics in Logistics; Springer: Cham, Switzerland, 2020; pp. 420–430. [Google Scholar]
- UN. The 17 Goals. Transforming Our World: The 2030 Agenda for Sustainable Development. 2022. Available online: https://sdgs.un.org/goals (accessed on 15 January 2022).
- Smith, G.E.; Watson, K.J.; Baker, W.H.; Pokorski, J.A. A critical balance: Collaboration and security in the IT-enabled supply chain. Int. J. Prod. Res. 2007, 45, 2595–2613. [Google Scholar] [CrossRef]
- Bertino, E.; Khan, L.R.; Sandhu, R.; Thuraisingham, B. Secure knowledge management: Confidentiality, trust, and privacy. IEEE Trans. Syst. Man Cybern. Part A Syst. Hum. 2006, 36, 429–438. [Google Scholar] [CrossRef]
- Harwood, I.; Ashleigh, M. The impact of trust and confidentiality on strategic organizational change programmes: A case study of post-acquisition integration. Strateg. Chang. 2005, 14, 63–75. [Google Scholar] [CrossRef]
- Goldfield, E.D.; Turner, A.G.; Cowan, C.D.; Scott, J.C. Privacy and confidentiality as factors in survey responce. Rev. Public Data Use 1979, 6, 219–229. [Google Scholar]
- Deason, E.E. The Need for Trust As a Justification for Confidentiality in Mediation: A Cross-Disciplinary Approach. Kans. Law Rev. 2005, 54, 1–25. [Google Scholar]
- Sahay, B.S. Understanding trust in supply chain relationships. Ind. Manag. Data Syst. 2003, 103, 553–563. [Google Scholar] [CrossRef]
- Colicchia, C.; Creazza, A.; Noè, C.; Strozzi, F. Information sharing in supply chains: A review of risks and opportunities using the systematic literature network analysis (SLNA). Supply Chain. Manag. 2019, 24, 5–21. [Google Scholar] [CrossRef]
- Hong, Y.; Vaidya, J.; Wang, S. A survey of privacy-aware supply chain collaboration: From theory to applications. J. Inf. Syst. 2014, 28, 243–268. [Google Scholar] [CrossRef] [Green Version]
- Tejpal, G.; Garg, R.K.; Sachdeva, A. Trust among supply chain partners: A review. Meas. Bus. Excell. 2013, 17, 51–71. [Google Scholar] [CrossRef]
- Flowerday, S.; von Solms, R. Trust: An element of information security. IFIP Int. Fed. Inf. Process. 2006, 201, 87–98. [Google Scholar] [CrossRef] [Green Version]
- Mayer, R.C.; Davis, J.H.; Schoorman, F.D. An Integrative Model of Organizational Trust. Acad. Manag. Rev. 1995, 20, 709–734. [Google Scholar] [CrossRef]
- Cheng, J.H.; Yeh, C.H.; Tu, C.W. Trust and knowledge sharing in green supply chains. Supply Chain. Manag. 2008, 13, 283–295. [Google Scholar] [CrossRef]
- Massimino, B.; Gray, J.V.; Boyer, K.K. The Effects of Agglomeration and National Property Rights on Digital Confidentiality Performance. Prod. Oper. Manag. 2017, 26, 162–179. [Google Scholar] [CrossRef]
- Stjepandić, J.; Liese, H.; Trappey, A.J.C. Intellectual Property Protection. In Concurrent Engineering in the 21st Century: Foundations, Developments and Challenges. In Concurrent Engineering in the 21st Century: Foundations, Developments and Challenges; Springer International Publishing: Cham, Switzerland, 2015; pp. 521–551. [Google Scholar] [CrossRef]
- Duncan, G.T.; Keller-McNulty, S.A.; Stokes, S.L. Database Security and Confidentiality: Examining Disclosure Risk vs. Data Utility through the R-U Confidentiality Map; Technical Report; National Institute of Statistical Sciences: Research Triangle Park, NC, USA, 2004. [Google Scholar] [CrossRef]
- Shackelford, S.J. Protecting Intellectual Property and Privacy in the Digital Age: The Use of National Cybersecurity Strategies to Mitigate Cyber Risk. Chapman Law Rev. 2016, 19, 1–13. [Google Scholar]
- Panahifar, F.; Byrne, P.J.; Salam, M.A.; Heavey, C. Supply chain collaboration and firm’s performance: The critical role of information sharing and trust. J. Enterp. Inf. Manag. 2018, 31, 358–379. [Google Scholar] [CrossRef]
- Doney, P.M.; Cannon, J.P. An examination of the nature of trust in buyer-seller relationships. J. Mark. 1997, 61, 35–51. [Google Scholar] [CrossRef]
- Zhao, X.; Huo, B.; Flynn, B.B.; Yeung, J.H.Y. The impact of power and relationship commitment on the integration between manufacturers and customers in a supply chain. J. Oper. Manag. 2008, 26, 368–388. [Google Scholar] [CrossRef]
- Butler, J.K. Trust Expectations, Information Sharing, Climate of Trust, and Negotiation Effectiveness and Efficiency. Group Organ. Manag. 1999, 24, 217–238. [Google Scholar] [CrossRef]
- Ebrahim-Khanjari, N.; Hopp, W.; Iravani, S.M. Trust and information sharing in supply chains. Prod. Oper. Manag. 2012, 21, 444–464. [Google Scholar] [CrossRef] [Green Version]
- Li, T.; Tong, S.; Zhang, H. Transparency of information acquisition in a supply chain. Manuf. Serv. Oper. Manag. 2014, 16, 412–424. [Google Scholar] [CrossRef] [Green Version]
- Chen, F. Information Sharing and Supply Chain Coordination. Handb. Oper. Res. Manag. Sci. 2003, 11, 341–421. [Google Scholar] [CrossRef]
- Lee, H.L.; Whang, S. Information sharing in a supply chain. Int. J. Manuf. Technol. Manag. 2000, 1, 79–93. [Google Scholar] [CrossRef]
- Fawcett, S.E.; Jin, Y.H.; Fawcett, A.M.; Magnan, G. I know it when I see it: The nature of trust, trustworthiness signals, and strategic trust construction. Int. J. Logist. Manag. 2017, 28, 914–938. [Google Scholar] [CrossRef]
- Agarwal, U.A.; Narayana, S.A. Impact of relational communication on buyer–supplier relationship satisfaction: Role of trust and commitment. Benchmark. Int. J. 2020, 27, 2459–2496. [Google Scholar] [CrossRef]
- Barrane, F.Z.; Ndubisi, N.O.; Kamble, S.; Karuranga, G.E.; Poulin, D. Building trust in multi-stakeholder collaborations for new product development in the digital transformation era. Benchmarking 2020, 28, 205–228. [Google Scholar] [CrossRef]
- Morgan, R.M.; Hunt, S.D. The Commitment-Trust Theory of Relationship Marketing. J. Mark. 1994, 58, 20–38. [Google Scholar] [CrossRef]
- Kumar, N.; Scheer, L.K.; Steenkamp, J.B.E.M. The Effects of Perceived Interdependence on Dealer Attitudes. J. Mark. Res. 1995, 32, 348–356. [Google Scholar] [CrossRef]
- Nyaga, G.N.; Whipple, J.M.; Lynch, D.F. Examining supply chain relationships: Do buyer and supplier perspectives on collaborative relationships differ? J. Oper. Manag. 2010, 28, 101–114. [Google Scholar] [CrossRef]
- Lee, L.S.; Zhong, W. Dependence Structure, Trust Dimensions, and Governance Choices in Asian Marketing Channels: Evidence in China. Asian J. Bus. Res. 2020, 10, 48. [Google Scholar] [CrossRef]
- Wu, G.; Zhao, X.; Zuo, J. Relationship between Project’s Added Value and the Trust–Conflict Interaction among Project Teams. J. Manag. Eng. 2017, 33, 04017011. [Google Scholar] [CrossRef]
- Akrout, H.; Diallo, M.F. Fundamental transformations of trust and its drivers: A multi-stage approach of business-to-business relationships. Ind. Mark. Manag. 2017, 66, 159–171. [Google Scholar] [CrossRef]
- Salam, M.A. The mediating role of supply chain collaboration on the relationship between technology, trust and operational performance: An empirical investigation. Benchmarking 2017, 24, 298–317. [Google Scholar] [CrossRef]
- Ryciuk, U. Identification of Factors Related to Trust Formation in Construction Supply Chains. Procedia Eng. 2017, 182, 627–634. [Google Scholar] [CrossRef]
- Kwon, I.W.G.; Suh, T. Factors Affecting the Level of Trust and Commitment in Supply Chain Relationships. J. Supply Chain. Manag. 2004, 40, 4–14. [Google Scholar] [CrossRef]
- Ford, J.K.; Riley, S.J.; Lauricella, T.K.; van Fossen, J.A. Factors Affecting Trust Among Natural Resources Stakeholders, Partners, and Strategic Alliance Members: A Meta-Analytic Investigation. Front. Commun. 2020, 5, 9. [Google Scholar] [CrossRef]
- Pech, W.; Swicegood, P. Trust And Trustworthiness: A Game Theory Transcontinental Experiment. Int. Bus. Econ. Res. J. (IBER) 2013, 12, 311. [Google Scholar] [CrossRef]
- Ghondaghsaz, N.; Engesser, S. Identification of factors and outcomes of trust in mobile supply chains. Eur. J. Manag. Bus. Econ. 2021. ahead-of-print. [Google Scholar] [CrossRef]
- Chen, J.V.; Yen, D.C.; Rajkumar, T.M.; Tomochko, N.A. The antecedent factors on trust and commitment in supply chain relationships. Comput. Stand. Interfaces 2011, 33, 262–270. [Google Scholar] [CrossRef]
- Myrelid, P.; Jonsson, P. Determinants of information quality in dyadic supply chain relationships. Int. J. Logist. Manag. 2019, 30, 356–380. [Google Scholar] [CrossRef]
- Kelton, K.; Fleischmann, K.R.; Wallace, W.A. Trust in Digital Information. J. Am. Soc. Inf. Sci. Technol. 2007, 59, 363–374. [Google Scholar] [CrossRef]
- Nicolaou, A.I.; Ibrahim, M.; Van Heck, E. Information quality, trust, and risk perceptions in electronic data exchanges. Decis. Support Syst. 2013, 54, 986–996. [Google Scholar] [CrossRef]
- Opolski, K.; Modzelewski, P.; Kocia, A. Interorganizational trust and effectiveness perception in a collaborative service delivery network. Sustainability 2019, 11, 5217. [Google Scholar] [CrossRef] [Green Version]
- Zhong, W.; Su, C.; Peng, J.; Yang, Z. Trust in Interorganizational Relationships: A Meta-Analytic Integration. J. Manag. 2017, 43, 1050–1075. [Google Scholar] [CrossRef]
- Chen, K.; Shing, M.; Lee, H.; Shing, C. Modeling in confidentiality and integrity for a supply chain network. Commun. IIMA 2007, 7, 41–48. [Google Scholar]
- Cezar, A.; Cavusoglu, H.; Raghunathan, S. Outsourcing information security: Contracting issues and security implications. Manag. Sci. 2014, 60, 638–657. [Google Scholar] [CrossRef] [Green Version]
- Chen, K.L.; Lee, H.; Yang, J. Security Considerations on the Design of Supply Chain Networks. Proc. Southwest Div. Decis. Sci. Inst. (SWDSI) 2006, 14, 275–277. [Google Scholar]
- Atluri, V.; Chun, S.A.; Mazzoleni, P. A Chinese wall security model for decentralized workflow systems. In Proceedings of the ACM Conference on Computer and Communications Security, Philadelphia, PA, USA, 6–8 November 2001; pp. 48–57. [Google Scholar] [CrossRef]
- Li, L.; Zhang, H. Confidentiality and information sharing in supply chain coordination. Manag. Sci. 2008, 54, 1467–1481. [Google Scholar] [CrossRef]
- Kerschbaum, F.; Schröpfer, A.; Zilli, A.; Pibernik, R.; Catrina, O.; de Hoog, S.; Schoenmakers, B.; Cimato, S.; Damiani, E. Secure Collaborative Supply-Chain Management. IEEE Comput. Soc. 2011, 44, 38–43. [Google Scholar] [CrossRef] [Green Version]
- Information Commissioner’s Office. Confidentiality of Commercial or Industrial Information (Regulation 12(5)(e)). Available online: https://ico.org.uk (accessed on 6 December 2021).
- Rizvi, S.; Cover, K.; Gates, C. A trusted third-party (TTP) based encryption scheme for ensuring data confidentiality in cloud environment. Procedia Comput. Sci. 2014, 36, 381–386. [Google Scholar] [CrossRef] [Green Version]
- Yuan, H.; Qiu, H.; Bi, Y.; Chang, S.H.; Lam, A. Analysis of coordination mechanism of supply chain management information system from the perspective of block chain. Inf. Syst. e-Bus. Manag. 2020, 18, 681–703. [Google Scholar] [CrossRef]
- Zhao, C.; Zhao, S.; Zhao, M.; Chen, Z.; Gao, C.Z.; Li, H.; Tan, Y. Secure Multi-Party Computation: Theory, practice and applications. Inf. Sci. 2019, 476, 357–372. [Google Scholar] [CrossRef]
- Nakasumi, M. Information sharing for supply chain management based on block chain technology. In Proceedings of the 2017 IEEE 19th Conference on Business Informatics, CBI 2017, Thessaloniki, Greece, 24–27 July 2017; Volume 1, pp. 140–149. [Google Scholar] [CrossRef]
- Shi, X.; Li, D.; Zhu, H.; Zhang, W. Research on Supply Chain Information Classification Based on Information Value and Information Sensitivity. In Proceedings of the International Conference on Service Systems and Service Management, Chengdu, China, 9–11 June 2007; pp. 1–7. [Google Scholar] [CrossRef]
- Birkel, H.S.; Veile, J.W.; Müller, J.M.; Hartmann, E.; Voigt, K.I. Development of a risk framework for Industry 4.0 in the context of sustainability for established manufacturers. Sustainability 2019, 11, 384. [Google Scholar] [CrossRef] [Green Version]
- Ali, M.M.; Babai, M.Z.; Boylan, J.E.; Syntetos, A.A. Supply chain forecasting when information is not shared. Eur. J. Oper. Res. 2017, 260, 984–994. [Google Scholar] [CrossRef]
- Zheng, X.; Cai, Z. Privacy-Preserved Data Sharing towards Multiple Parties in Industrial IoTs. IEEE J. Sel. Areas Commun. 2020, 38, 968–979. [Google Scholar] [CrossRef]
- Sindhuja, P.N. Impact of information security initiatives on supply chain performance an empirical investigation. Inf. Manag. Comput. Secur. 2014, 22, 450–473. [Google Scholar] [CrossRef]
- Kong, G.; Rajagopalan, S.; Zhang, H. Information Leakage in Supply Chains. Springer Ser. Supply Chain. Manag. 2017, 5, 313–341. [Google Scholar] [CrossRef]
- Baihaqi, I.; Sohal, A.S. The impact of information sharing in supply chains on organisational performance: An empirical study. Prod. Plan. Control 2013, 24, 743–758. [Google Scholar] [CrossRef]
- Butler, J.K. Behaviors, Trust, and Goal Achievement in a Win-Win Negotiating Role Play. Group Organ. Manag. 1995, 20, 486–501. [Google Scholar] [CrossRef]
- Mentzer, J.T.; Keebler, J.S.; Nix, N.W.; Smith, C.D.; Zacharia, Z.G. Defining supply chain management. J. Bus. Logist. 2001, 22, 1–25. [Google Scholar] [CrossRef]
- Fox, S. Moveable production systems for sustainable development and trade: Limitations, opportunities and barriers. Sustainability 2019, 11, 5154. [Google Scholar] [CrossRef] [Green Version]
- Ask, A.; Stillström, C. Mobile Manufacturing Systems: Market Requirements and Opportunities. In Proceedings of the 2006 IJME-Intertech International Conference, Union, NJ, USA, 19–21 October 2006. [Google Scholar]
- Alix, T.; Benama, Y.; Perry, N. Reconfigurable Manufacturing System Design: The Case of Mobile Manufacturing System. In Advances in Production Management Systems. Innovative and Knowledge-Based Production Management in a Global-Local World. APMS 2014; IFIP Advances in Information and Communication Technology; Grabot, B., Vallespir, B., Gomes, S., Bouras, A., Kiritsis, D., Eds.; Springer: Berlin/Heidelberg, Germany, 2014; Volume 440. [Google Scholar]
- Bengtsson, M.; Elfving, S.; Jackson, M. The factory-in-a-box concept and its maintenance application. In Proceedings of the 19th International Congress on Condition Monitoring and Diagnostic Engineering Management, Luleå, Sweden, 12–15 June 2006. [Google Scholar]
- Peltokoski, M.; Lohtander, M.; Volotinen, J. Location Independent Manufacturing–Manufacturing Company Competitiveness in a Changing Business Environment. Procedia Manuf. 2017, 11, 863–870. [Google Scholar] [CrossRef]
- Baldea, M.; Edgar, T.; Stanley, B.; Kiss, A. Modular Manufacturing Processes: Status, Challenges, and Opportunities. AICHE J. 2015, 61, 857–866. [Google Scholar] [CrossRef] [Green Version]
- Wörsdörfer, D.; Lier, S.; Crasselt, N. Real options-based evaluation model for transformable plant designs in the process industry. J. Manuf. Syst. 2016, 42, 29–43. [Google Scholar] [CrossRef]
- Wörsdörfer, D.; Lier, S.; Grünewald, M. Potential analysis model for case specific quantification of the degree of eligibility of innovative production concepts in the process industry. Chem. Eng. Process. Process Intensif. 2015, 98, 123–136. [Google Scholar] [CrossRef]
- Lier, S.; Wörsdörfer, D.; Gesing, J. Business Models and Product Service Systems for Transformable, Modular Plants in the Chemical Process. In Product-Service Integration for Sustainable Solutions; Lecture Notes in Production Engineering; Meier, H., Ed.; Springer: Berlin/Heidelberg, Germany, 2013; pp. 227–238. [Google Scholar] [CrossRef]
- Klose, A.; Merkelbach, S.; Menschner, A.; Hensel, S.; Heinze, S.; Bittorf, L.; Kockmann, N.; Schäfer, C.; Szmais, S.; Eckert, M.; et al. Orchestration Requirements for Modular Process Plants in Chemical and Pharmaceutical Industries. Chem. Eng. Technol. 2019, 42, 2282–2291. [Google Scholar] [CrossRef] [Green Version]
- Chokparova, Z.; Urbas, L. Utilization of Homomorphic Cryptosystems for Information Exchange in Value Chains. In Proceedings of the 26th IEEE International Conference on Emerging Technologies and Factory Automation (ETFA), Västerås, Sweden, 7–10 September 2021; pp. 1–7. [Google Scholar] [CrossRef]
- Wang, Y.; Wang, N.; Jiang, L.; Yang, Z.; Cui, V. Managing relationships with power advantage buyers: The role of supplier initiated bonding tactics in long-term buyer–supplier collaborations. J. Bus. Res. 2016, 69, 5587–5596. [Google Scholar] [CrossRef]
- Bedwell, W.L.; Wildman, J.L.; DiazGranados, D.; Salazar, M.; Kramer, W.S.; Salas, E. Collaboration at work: An integrative multilevel conceptualization. Hum. Resour. Manag. Rev. 2012, 22, 128–145. [Google Scholar] [CrossRef]
- Mayring, P. Qualitative Content Analysis: Theoretical Foundation, Basic Procedures and Software Solution; GESIS—Leibniz Institute for the Social Sciences: Klagenfurt, Austria, 2014. [Google Scholar]
- Khakhar, P.; Rammal, H.G. Culture and business networks: International business negotiations with Arab managers. Int. Bus. Rev. 2013, 22, 578–590. [Google Scholar] [CrossRef]
- Goworek, H.; Oxborrow, L.; Claxton, S.; McLaren, A.; Cooper, T.; Hill, H. Managing sustainability in the fashion business: Challenges in product development for clothing longevity in the UK. J. Bus. Res. 2020, 117, 629–641. [Google Scholar] [CrossRef] [Green Version]
- Zafari, K.; Biggemann, S.; Garry, T. Mindful management of relationships during periods of crises: A model of trust, doubt and relational adjustments. Ind. Mark. Manag. 2020, 88, 278–286. [Google Scholar] [CrossRef]
- Maxwell, J.A. Qualitative Research Design: An Interactive Approach, 3rd ed.; Sage Publication: Thousand Oaks, CA, USA, 2012. [Google Scholar]
- Bhattacherjee, A. Social Science Research: Principles, Methods, and Practices; Textbooks Collection; University of South Florida: Tampa, FL, USA, 2012. [Google Scholar]
- Crescentini, A.; Mainardi, G. Qualitative research articles: Guidelines, suggestions and needs. J. Workplace Learn. 2009, 21, 431–439. [Google Scholar] [CrossRef] [Green Version]
- Almeida, F.; Superior, I.; Gaya, P.; Queirós, A.; Faria, D. Strengths and Limitations of Qualitative and Quantitative Research Methods. Eur. J. Edu. Stu. 2017, 3, 369–387. [Google Scholar] [CrossRef]
- Tunio, M.N.; Jariko, M.A.; Børsen, T.; Shaikh, S.; Mushtaque, T.; Brahmi, M. How Entrepreneurship Sustains Barriers in the Entrepreneurial Process—A Lesson from a Developing Nation. Sustainability 2021, 13, 11419. [Google Scholar] [CrossRef]
- Van Rijnsoever, F.J. (I Can’t Get No) Saturation: A simulation and guidelines for sample sizes in qualitative research. PLoS ONE 2017, 12, e0181689. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Vasileiou, K.; Barnett, J.; Thorpe, S.; Young, T. Characterising and justifying sample size sufficiency in interview-based studies: Systematic analysis of qualitative health research over a 15-year period. BMC Med. Res. Methodol. 2018, 18, 148. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Kuckartz, U.; Rädiker, S. Working with Coded Segments and Memos; Springer: Cham, Switzerland, 2019. [Google Scholar] [CrossRef]
- Rudman, A.; Garbutt, M.; Seymour, L.F. Towards a Framework of Process Owner Competencies and Tasks. In Proceedings of the Annual Conference of the South African Institute of Computer Scientists and Information Technologists, Association for Computing Machinery, Johannesburg, South Africa, 26–28 September 2016; pp. 1–7. [Google Scholar] [CrossRef]
- Shahmoradi-Moghadam, H.; Schönberger, J. Joint optimization of production and routing master planning in mobile supply chains. Oper. Res. Perspect. 2021, 8, 100187. [Google Scholar] [CrossRef]
- Becker, T.; Lier, S.; Werners, B. Value of modular production concepts in future chemical industry production networks. Eur. J. Oper. Res. 2019, 276, 957–970. [Google Scholar] [CrossRef]
- Allman, A.; Zhang, Q. Dynamic location of modular manufacturing facilities with relocation of individual modules. Eur. J. Oper. Res. 2020, 286, 494–507. [Google Scholar] [CrossRef]
- Fawcett, S.E.; Jones, S.L.; Fawcett, A.M. Supply chain trust: The catalyst for collaborative innovation. Bus. Horiz. 2012, 55, 163–178. [Google Scholar] [CrossRef]
- Handfield, R.B.; Bechtel, C. The role of trust and relationship structure in improving supply chain responsiveness. Ind. Mark. Manag. 2002, 31, 367–382. [Google Scholar] [CrossRef]
- The Economist. Germany’s Conservative Economic Model Is Being Put to the Test. 2018. Available online: https://www.economist.com/special-report/2018/04/12/germanys-conservative-economic-model-is-being-put-to-the-test (accessed on 20 January 2022).
- Mourtzis, D.; Doukas, M.; Psarommatis, F. A multi-criteria evaluation of centralized and decentralized production networks in a highly customer-driven environment. CIRP Ann. 2012, 61, 427–430. [Google Scholar] [CrossRef]
- Shahmoradi-Moghadam, H.; Schönberger, J. Coordinated allocation production routing problem for mobile supply chains with shared factories. Comput. Chem. Eng. 2021, 155, 107501. [Google Scholar] [CrossRef]
- Armbruster, D.; De Beer, C.; Freitag, M.; Jagalski, T.; Ringhofer, C. Autonomous control of production networks using a pheromone approach. Phys. A Stat. Mech. Its Appl. 2006, 363, 104–114. [Google Scholar] [CrossRef]
- Ghosh, A.; Fedorowicz, J. The role of trust in supply chain governance. Bus. Process Manag. J. 2008, 14, 453–470. [Google Scholar] [CrossRef]
- Pooe, D.; Mafini, C.; Loury-Okoumba, V.W. The influence of information sharing, supplier trust and supplier synergy on supplier performance: The case of small and medium enterprises. J. Transp. Supply Chain. Manag. 2015, 9, 1–11. [Google Scholar] [CrossRef] [Green Version]
- Seppänen, R.; Blomqvist, K.; Sundqvist, S. Towards measuring inter-organizational trust-a review and analysis of the empirical research in 1990–2003. Retrieved August 2003, 13, 2009. [Google Scholar]
- Rauch, E.; Matt, D.T.; Dallasega, P. Mobile On-site Factories-Scalable and distributed manufacturing systems for the construction industry. In Proceedings of the IEOM 2015-5th International Conference on Industrial Engineering and Operations Management, Dubai, United Arab Emerites, 3–5 March 2015. [Google Scholar] [CrossRef]
- Manzini, R.; Lazzarotti, V. Intellectual Property Protection Mechanisms in Collaborative New Product Development. R&D Manag. 2016, 46, 579–595. [Google Scholar] [CrossRef]
- Rauschecker, U.; Meier, M.; Muckenhirn, R.; Yip, A.L.K.; Jagadeesan, A.P.; Corney, J. Cloud-Based Manufacturing-as-a-Service Environment for Customized Products. In Proceedings of the eChallenges e-2011 Conference, Florence, Italy, 26–28 October 2011. [Google Scholar]
- Bonatti, P.; De Coi, J.; Olmedilla, D.; Sauro, L. A Rule-Based Trust Negotiation System. IEEE Trans. Knowl. Data Eng. 2010, 22, 1507–1520. [Google Scholar] [CrossRef]


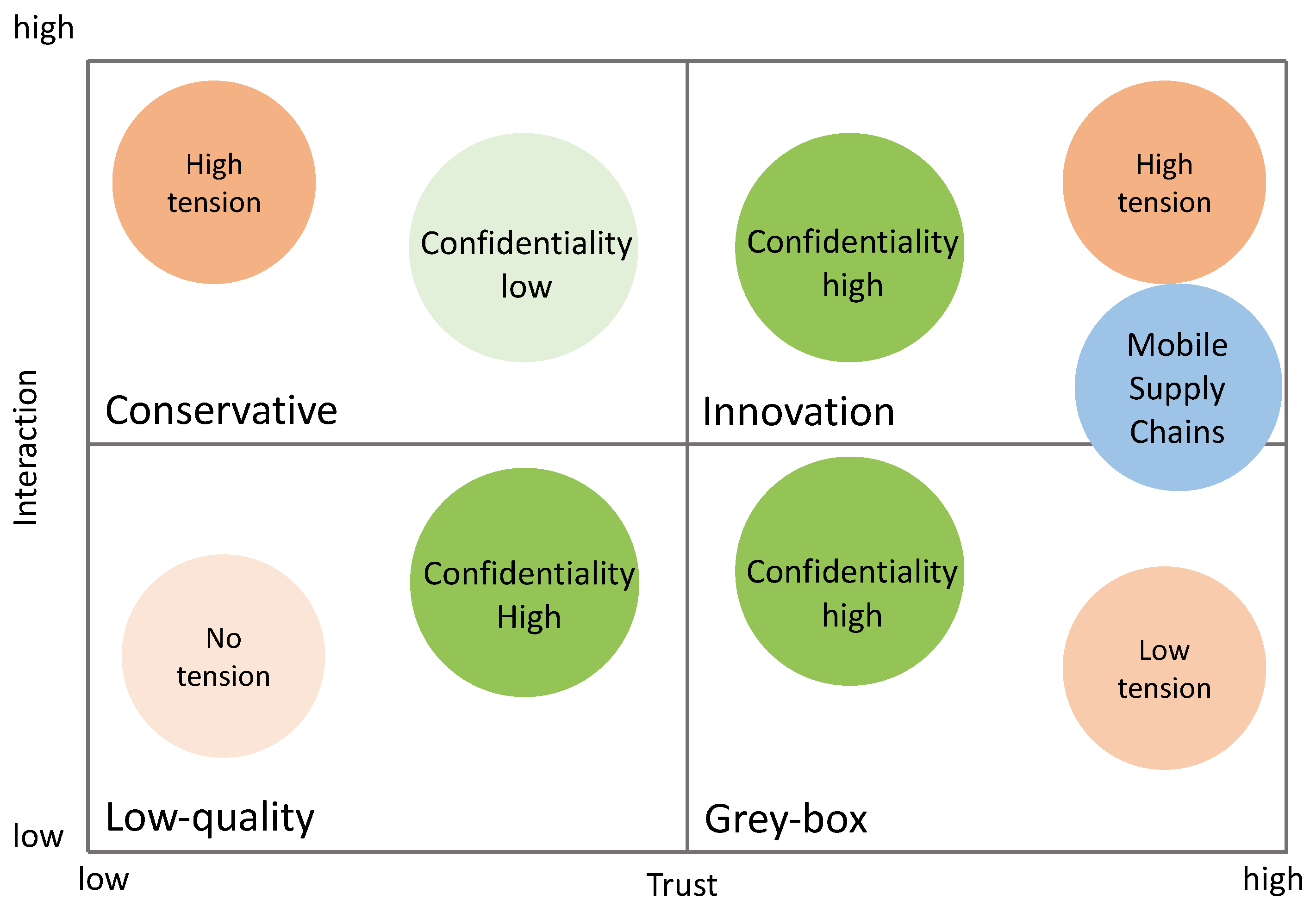

| Integration Scenarios | T–C Relationship | Characteristics |
|---|---|---|
| Low-quality (rather rare) | Trust: low Confidentiality: high Information sharing: low Tension: insignificant | Product types: poorly specified products |
| Conservative (rather rare) | Trust: low Confidentiality: low Information sharing: high Tension: high; one party does not accept low level of confidentiality, results in low level of trust | Partners: conservative partners Product types: customized products Modular plant types: individual modular plants Market threat: high threat from competitors Service period: long-term |
| Grey-box (more frequent) | Trust: high Confidentiality: high Information sharing: low Tension: low; one party accepts low exchange of sensitive information due to the importance of trust for product quality | Partner’s role: process owner and module owner are one in the same; low integration Product types: standard products; modular capacity Modular plant types: small modular units, Module-as-a-service Market threat: low threat from competitors Service period: short-term leasing |
| Innovation (most frequent) | Trust: high Confidentiality: high Information sharing: high Tension: high; three major strategies and confidentiality preserving-techniques are used to manage tension between trust and confidentiality | Partner’s role: different process owner and module owner; high integration Product types: new product development; raw material; customized products Modular plant types: Shared mobile facilities; Factory-in-a-box [71]; Manufacturing-as-a-Service [108] Market threat: high threat from competitors Service period: either short- or long-term |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ghondaghsaz, N.; Chokparova, Z.; Engesser, S.; Urbas, L. Managing the Tension between Trust and Confidentiality in Mobile Supply Chains. Sustainability 2022, 14, 2347. https://doi.org/10.3390/su14042347
Ghondaghsaz N, Chokparova Z, Engesser S, Urbas L. Managing the Tension between Trust and Confidentiality in Mobile Supply Chains. Sustainability. 2022; 14(4):2347. https://doi.org/10.3390/su14042347
Chicago/Turabian StyleGhondaghsaz, Nassim, Zarina Chokparova, Sven Engesser, and Leon Urbas. 2022. "Managing the Tension between Trust and Confidentiality in Mobile Supply Chains" Sustainability 14, no. 4: 2347. https://doi.org/10.3390/su14042347







