Integrating Lorenz Hyperchaotic Encryption with Ring Oscillator Physically Unclonable Functions (RO-PUFs) for High-Throughput Internet of Things (IoT) Applications
Abstract
:1. Introduction
- Processing power: The power of on-board processing within IoT devices is often reduced to save power. Many IoT devices do not have a constant power source and instead rely on a battery to increase the mobility of the device. In fact, many IoT devices do not have a central CPU at all and instead rely on a Field-Programmable Gate Array (FPGA) or Application-Specific Integrated-Circuit (ASIC).
- Power consumption: Increased complexity in cryptographic algorithms will draw more power. For example, the use of Digital Signal Processors (DSPs) for complex mathematical functions on ASICs or FPGAs, such as ordinary differential equations or transforms, will require additional power.
- Easy access: With the wide range of IoT applications and the growing array of connected devices, it has become easier than ever for an attacker to get inside a network. A single device’s vulnerability can expose the entire network that is otherwise secure [2]. Further, with the mobility of IoT devices such as wearables and remote sensing units, new vulnerabilities are constantly being discovered outside the security of traditional, local networks.
- Providing a secure, hyperchaotic method for high-speed image encryption.
- Securing the private key from hardware-replication methods and side-channel attacks.
- Allowing for a configurable key refresh rate.
- Providing a small power and resource footprint for resource-constrained devices.
2. Research Background
2.1. Building a True Random Number Generator
2.2. Physically Unclonable Functions
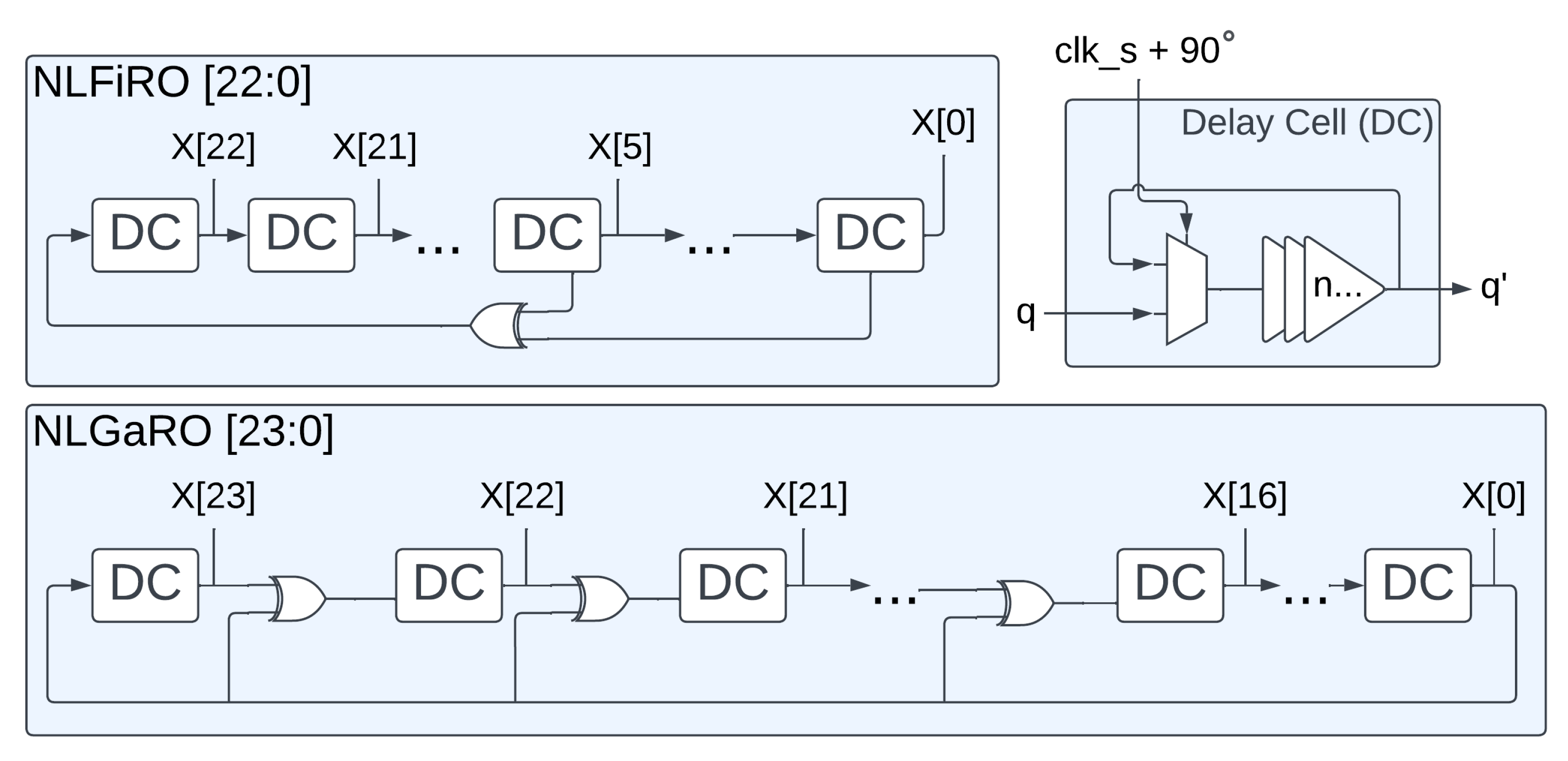
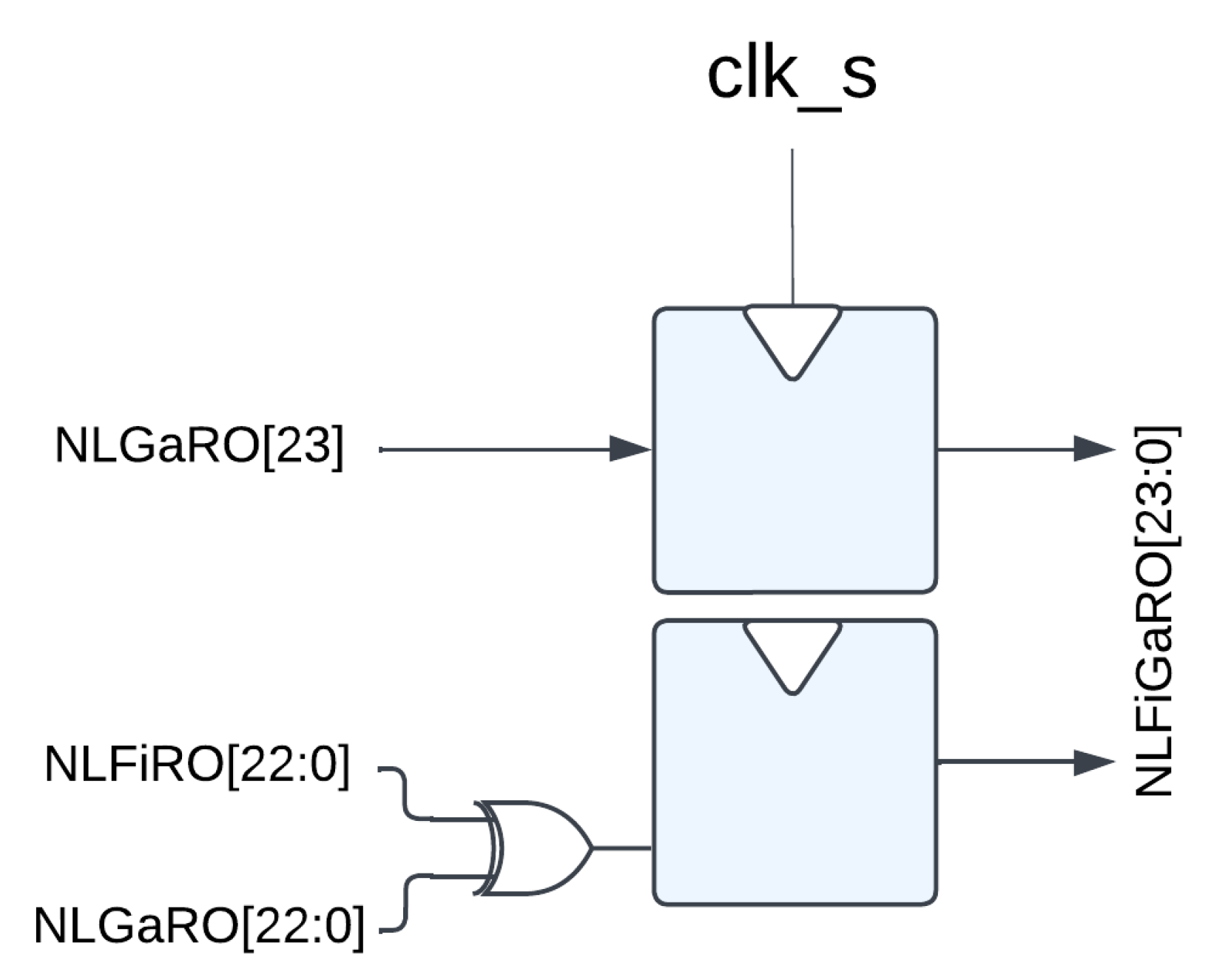
- Silicon: These rely on the uncontrollable differences in manufacturing between devices and do not require extra components outside of an FPGA. This category can further be broken up into delay-based PUFs, such as Arbiter PUFs [19,20] and RO PUFs [21,22,23,24], and memory-based PUFs, which utilize the entropy from volatile memory cells [25,26].
2.3. Lorenz Hyperchaotic Systems
3. System Design
3.1. Lorenz Hyperchaotic System
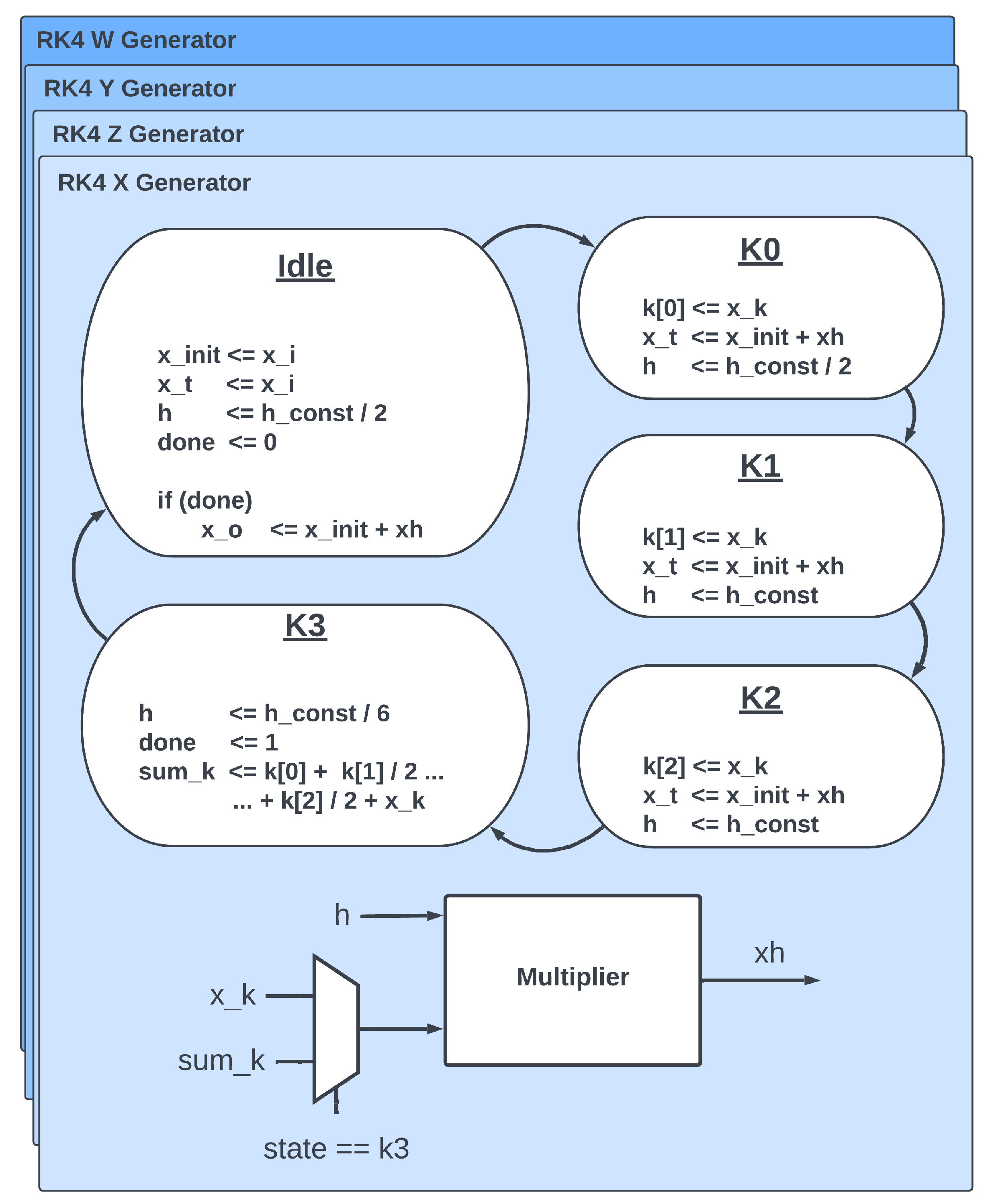
3.2. Runge–Kutta 4 Method
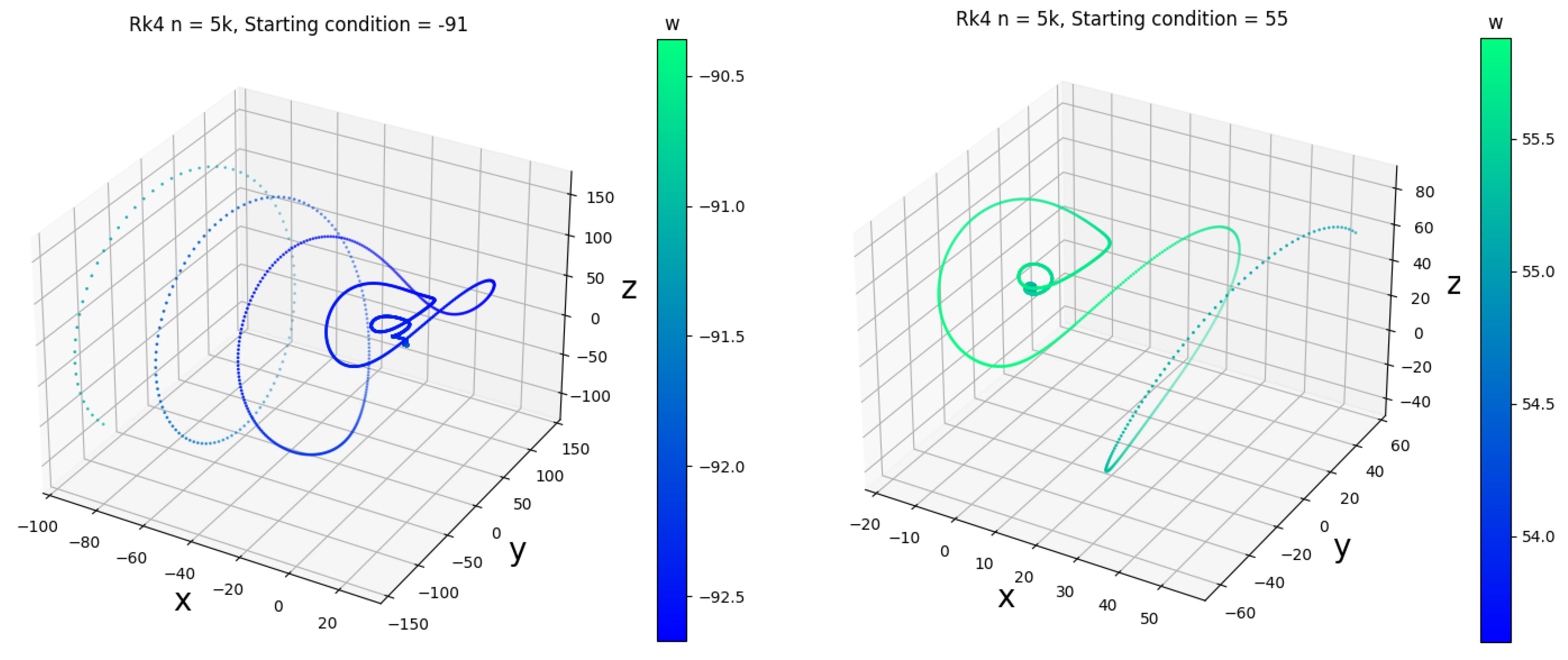
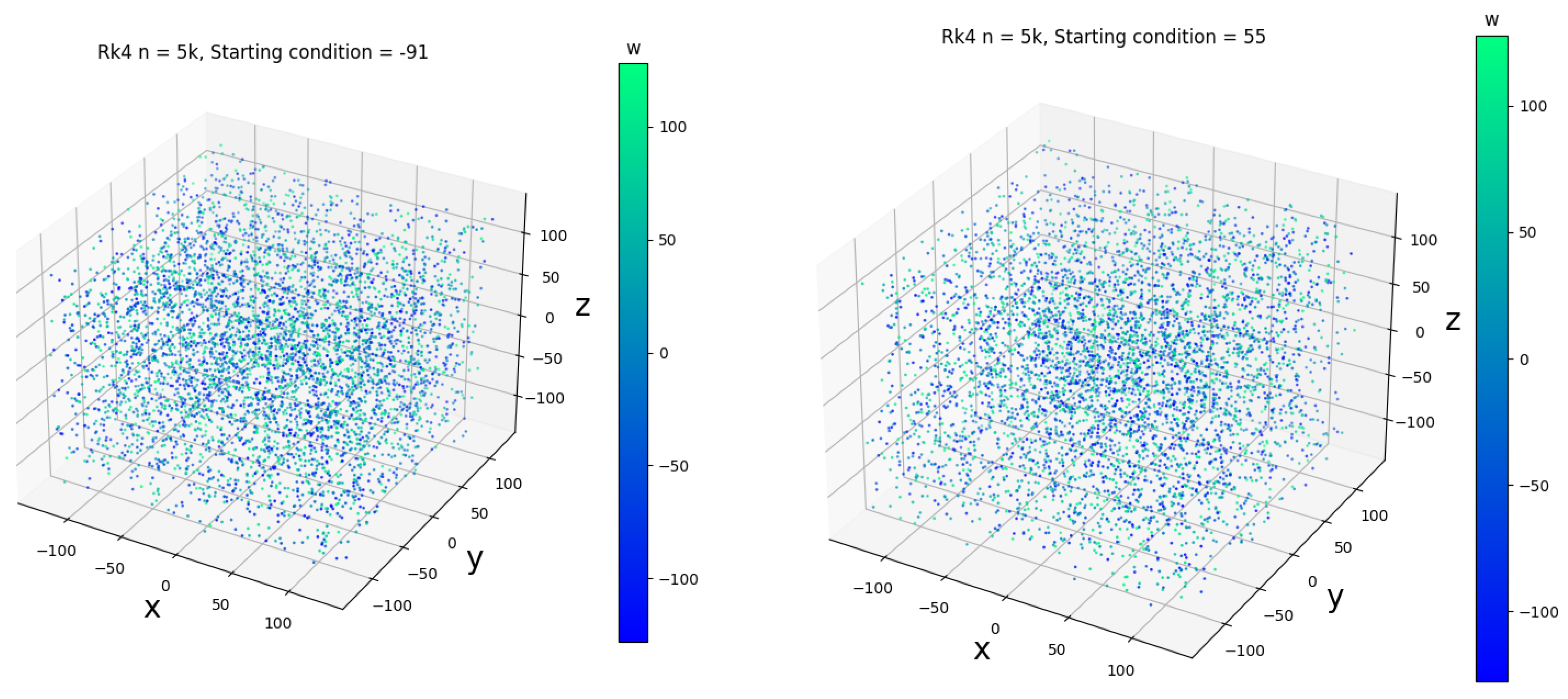
3.3. Computer Simulation
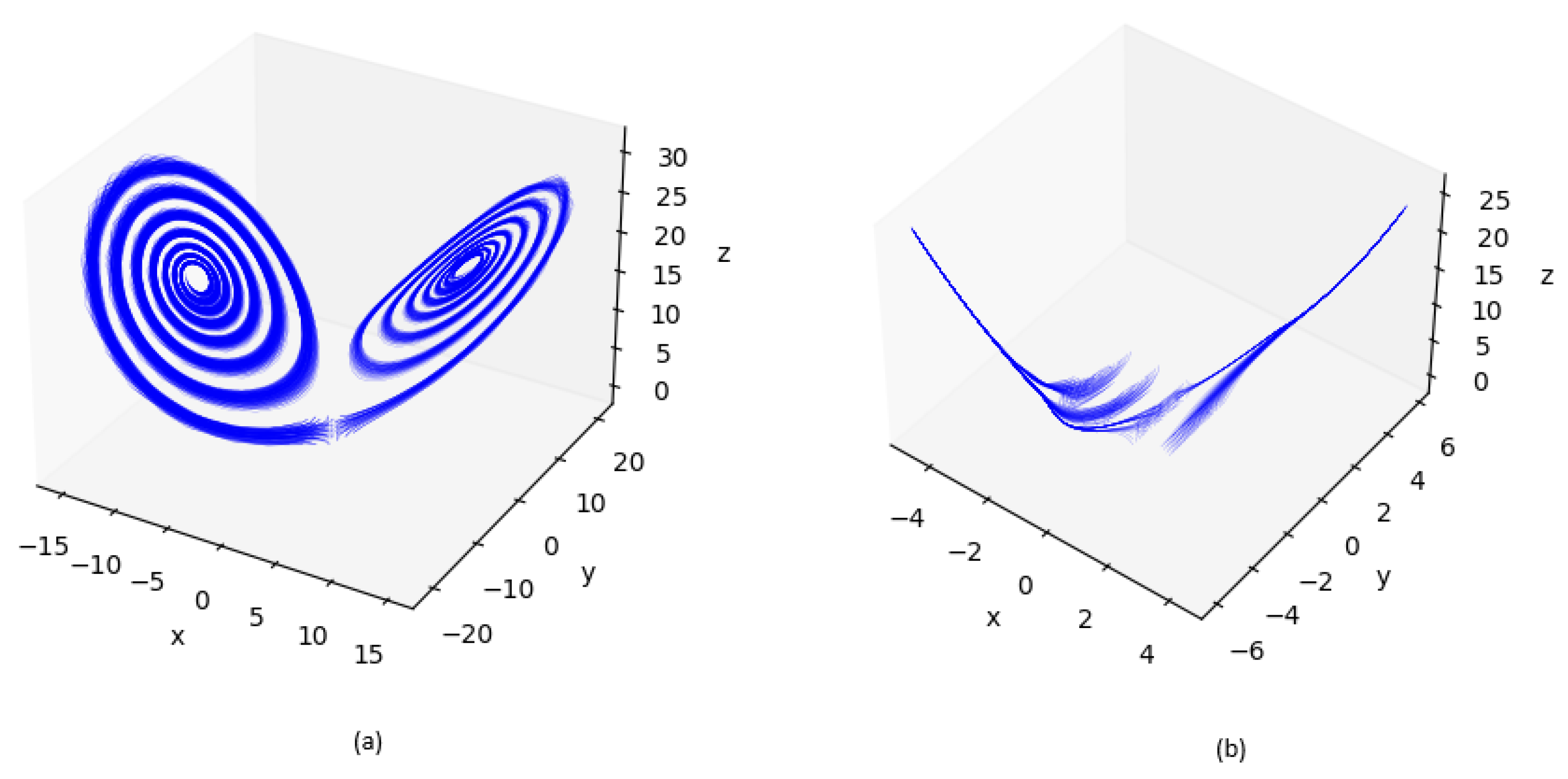
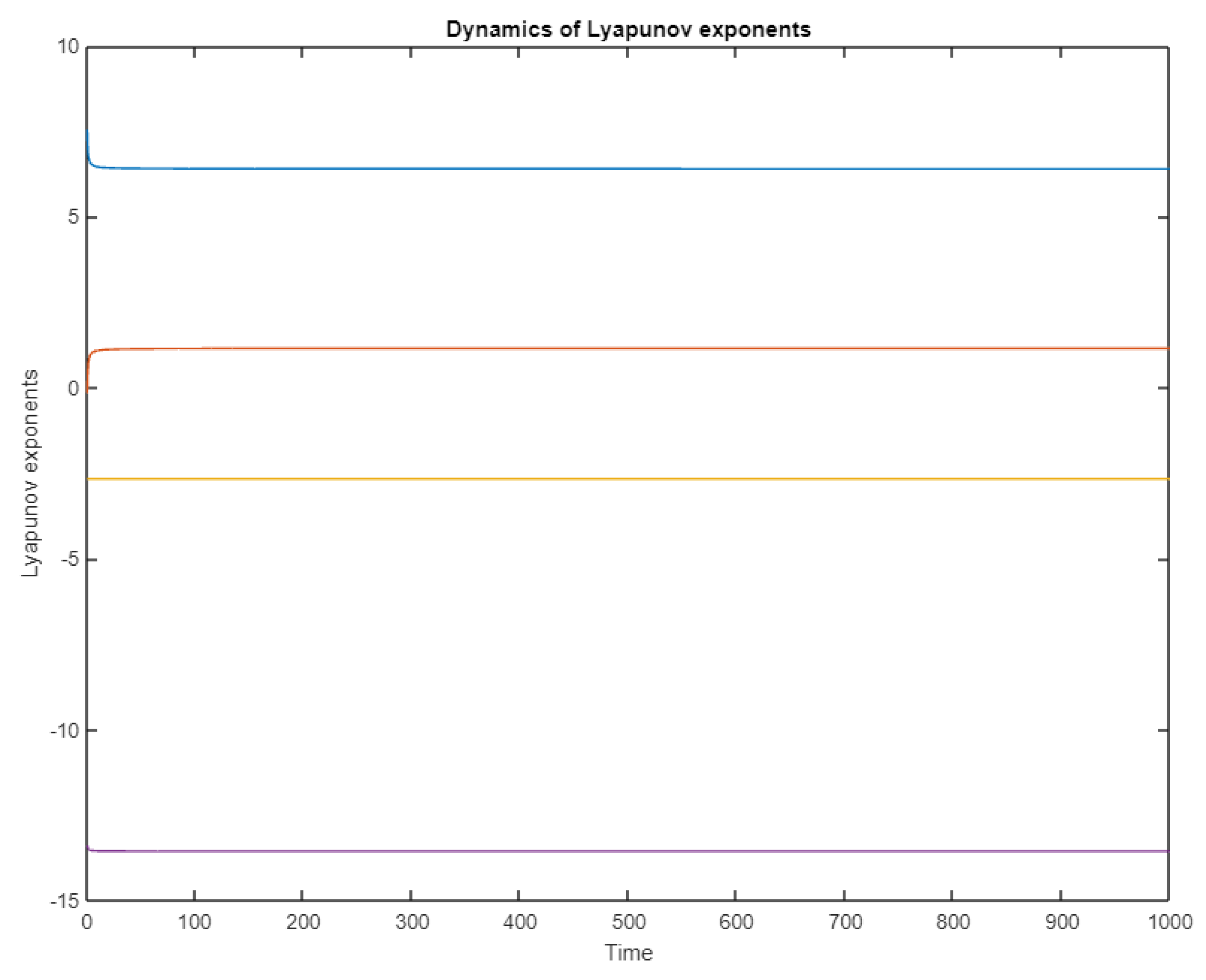
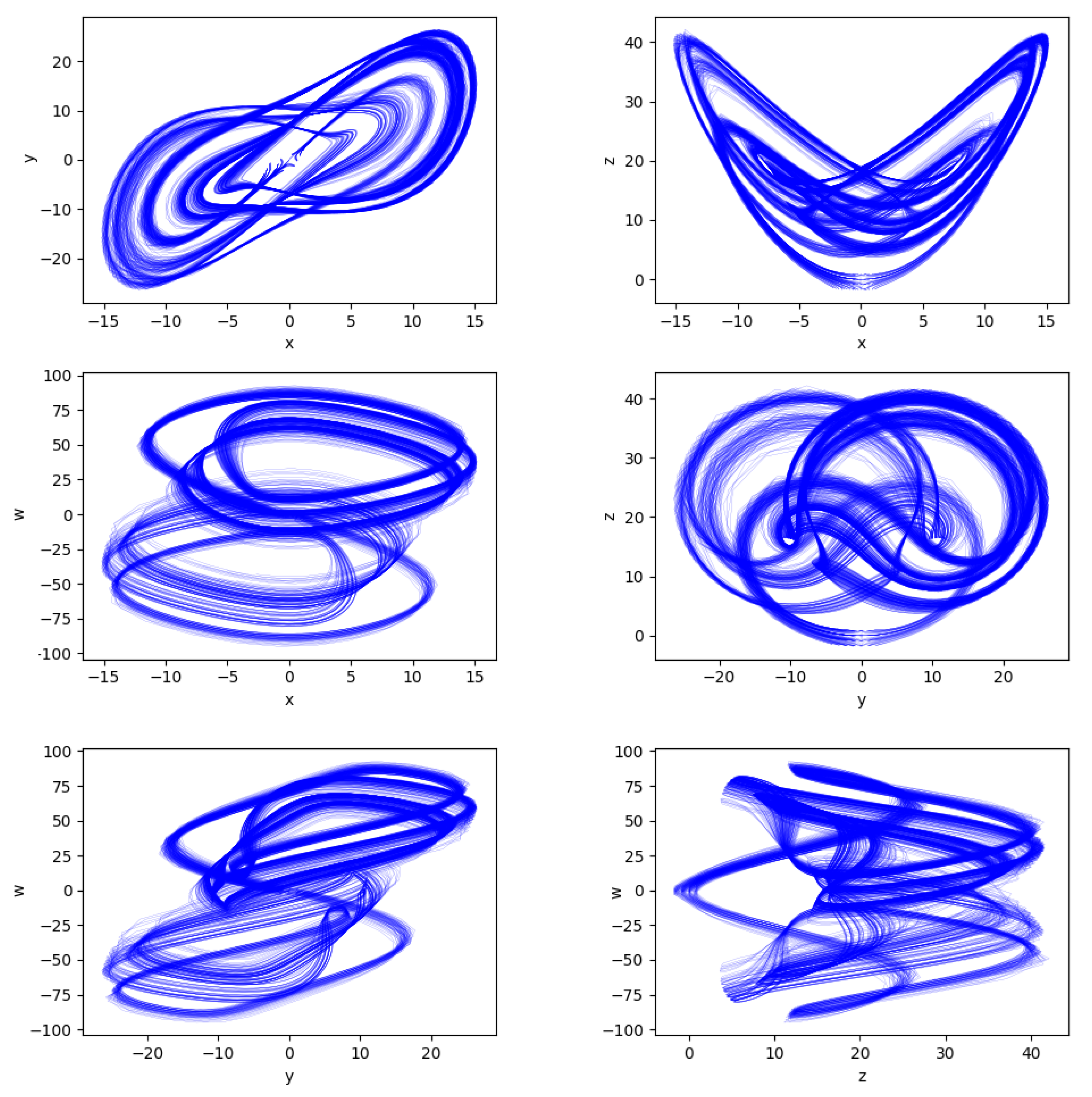
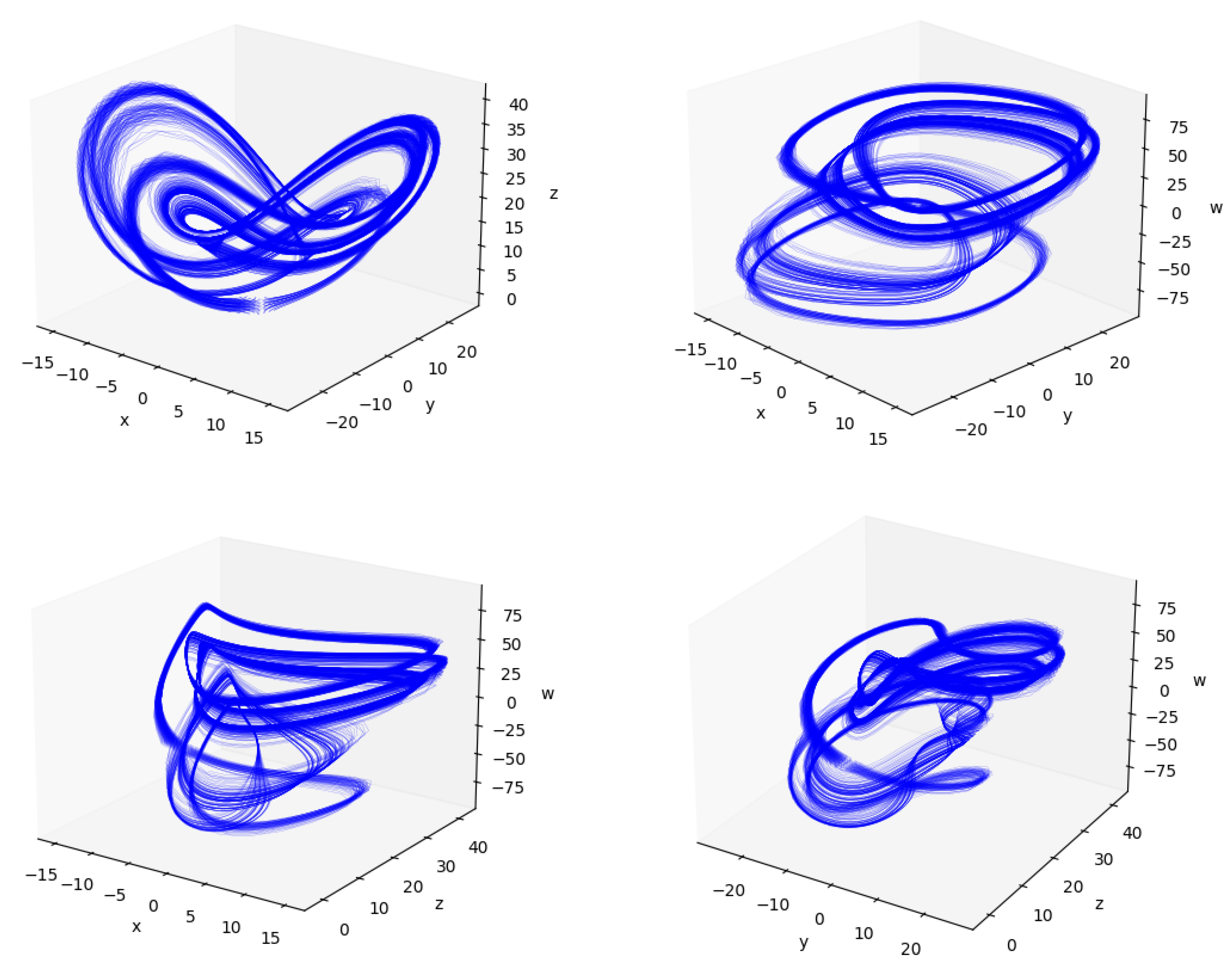
3.4. Dynamical Analysis of the Lorenz System
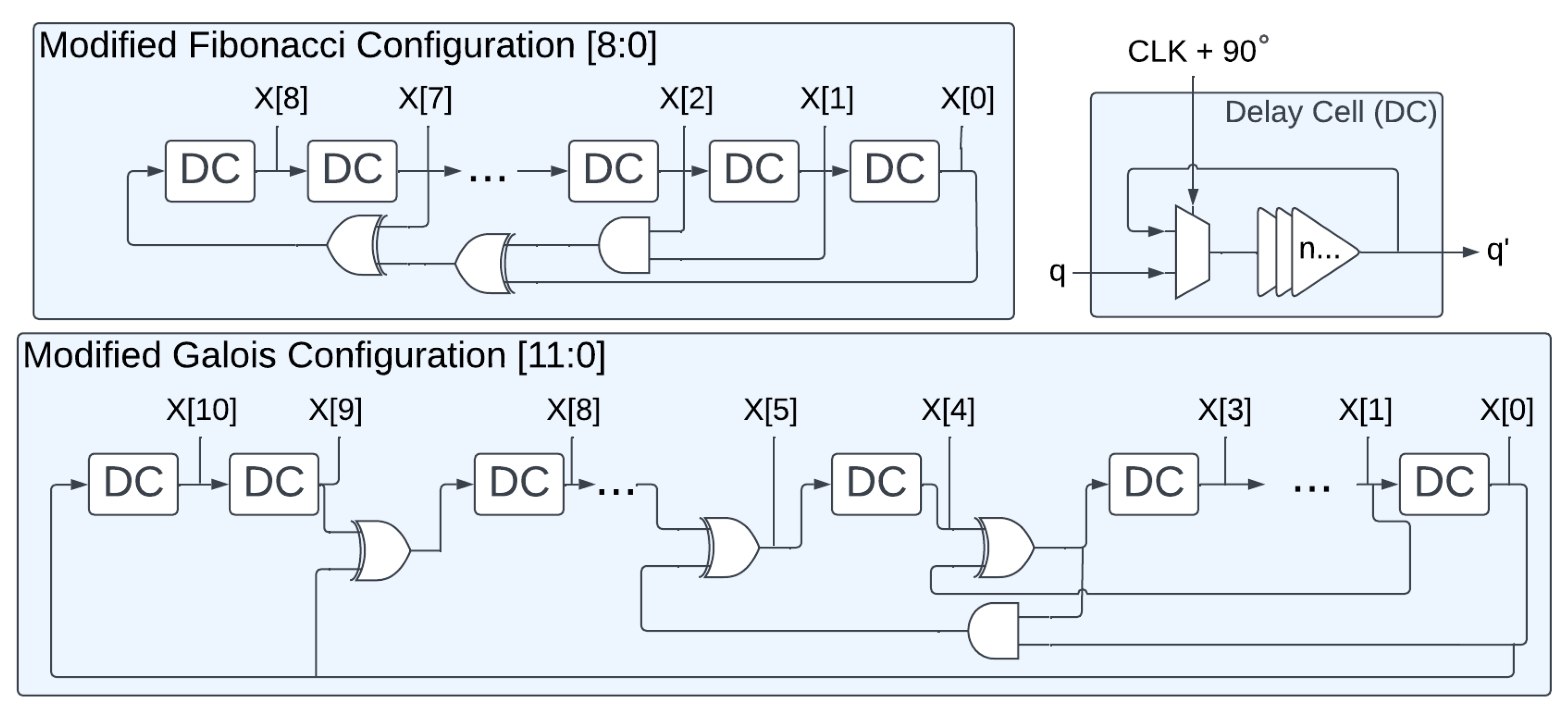
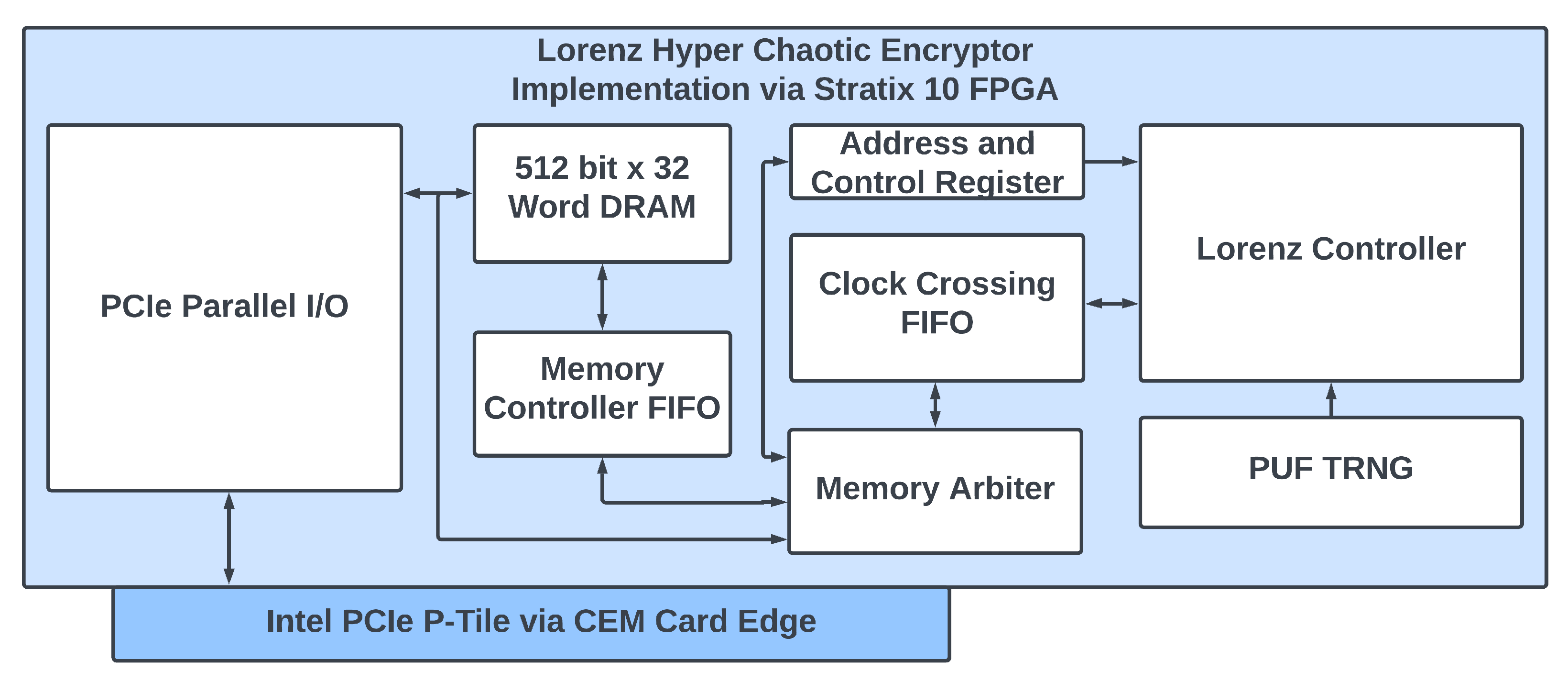
3.5. FPGA Implementation
3.5.1. RO PUF
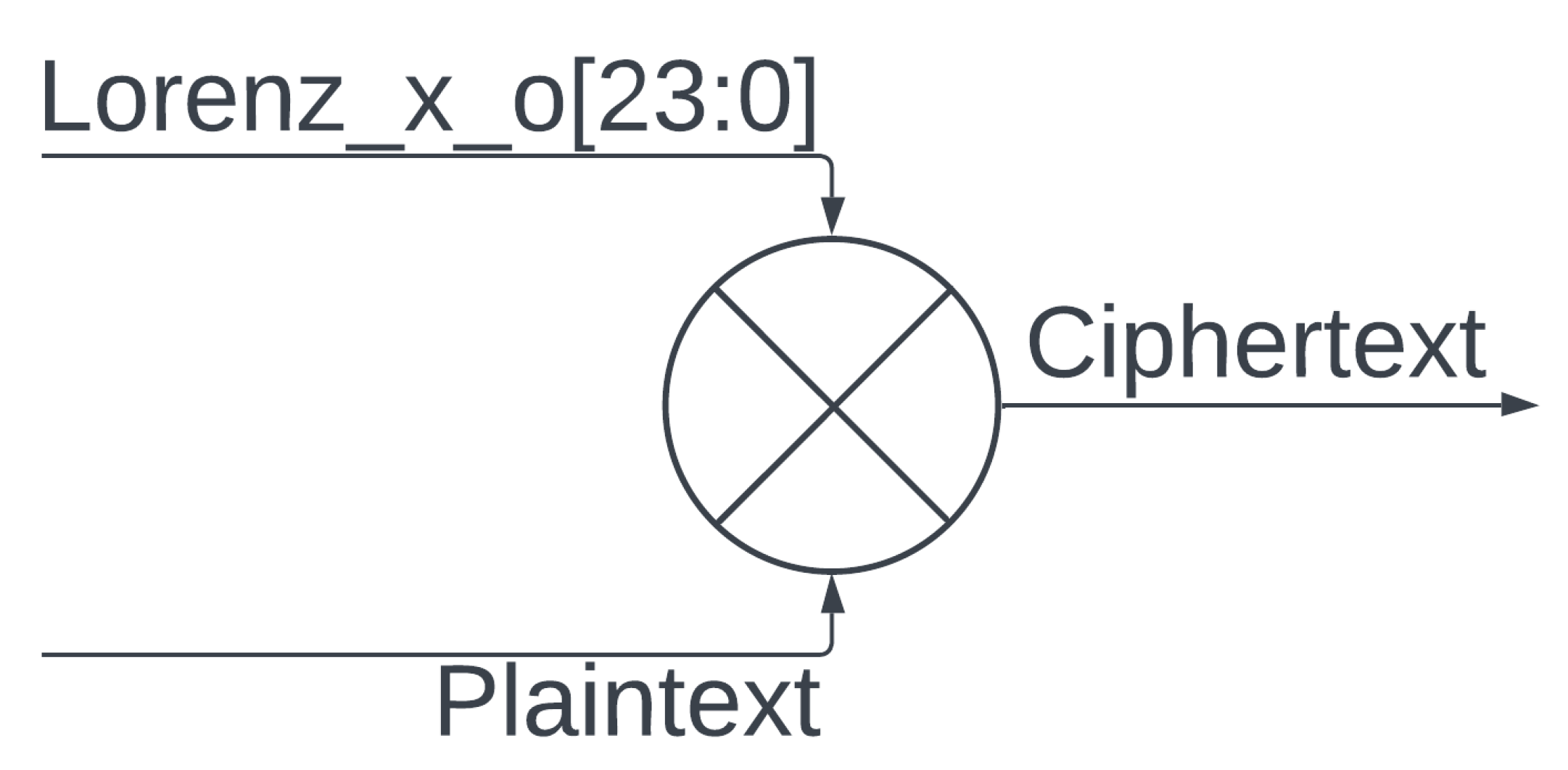
3.5.2. Lorenz Hyperchaotic System
- If set to encrypt, the LHCE will first capture an RNG and generate an output, with the input to the system being the hard-coded initial conditions.
- The plain-text RNG seed is encrypted with the output of the LHCE.
- The LHCE will reconfigure itself with the RNG as its initial condition.
- The LHCE will calculate its next key, with its input being its previous output, encrypting the plaintext with the generated key.
- This continues until the LHCE is reset, at which point a new initial condition will be determined via the TRNG, or the system is set to the decrypt mode.
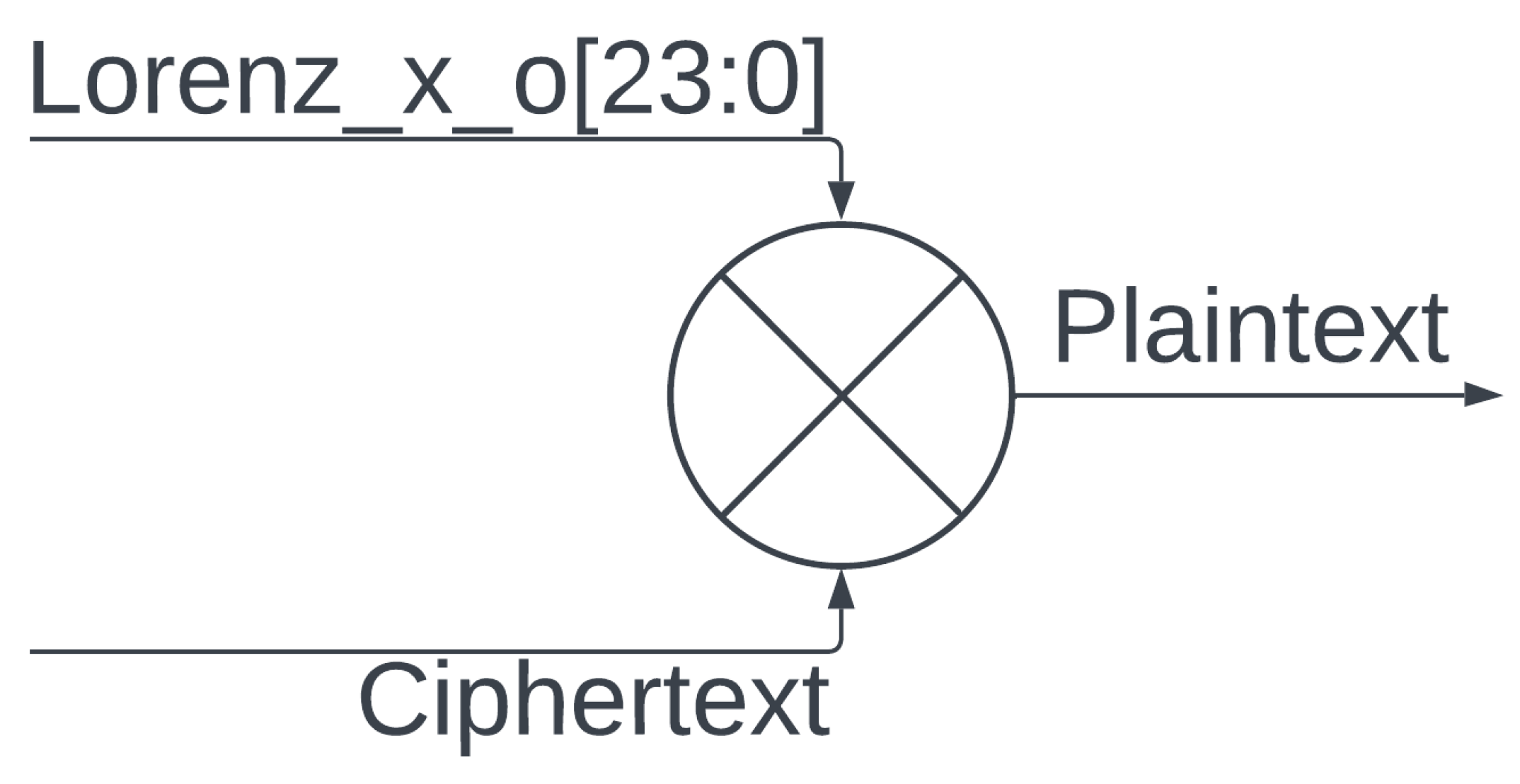
- If set to decrypt, the LHCE will wait for data to be input, expecting the first 24 bits of data to be the encrypted initial condition for the system.
- Once data are received, the generated output (with the hard-coded initial conditions being the input) of the LHCE is used to decrypt the ciphertext.
- These received data are the initial conditions used by the encryptor, so the decryptor reconfigures itself with this first packet as the initial condition.
- The LHCE will calculate its next key with its input being its previous output, decrypting the ciphertext along the way with the generated key.
- This continues until the LHCE is reset, at which point a new initial condition will be determined via the incoming data stream, or the system is set to encrypt mode.
3.6. PCIe Wrapper
4. Results
4.1. Resource Usage
4.2. Random Number Generation
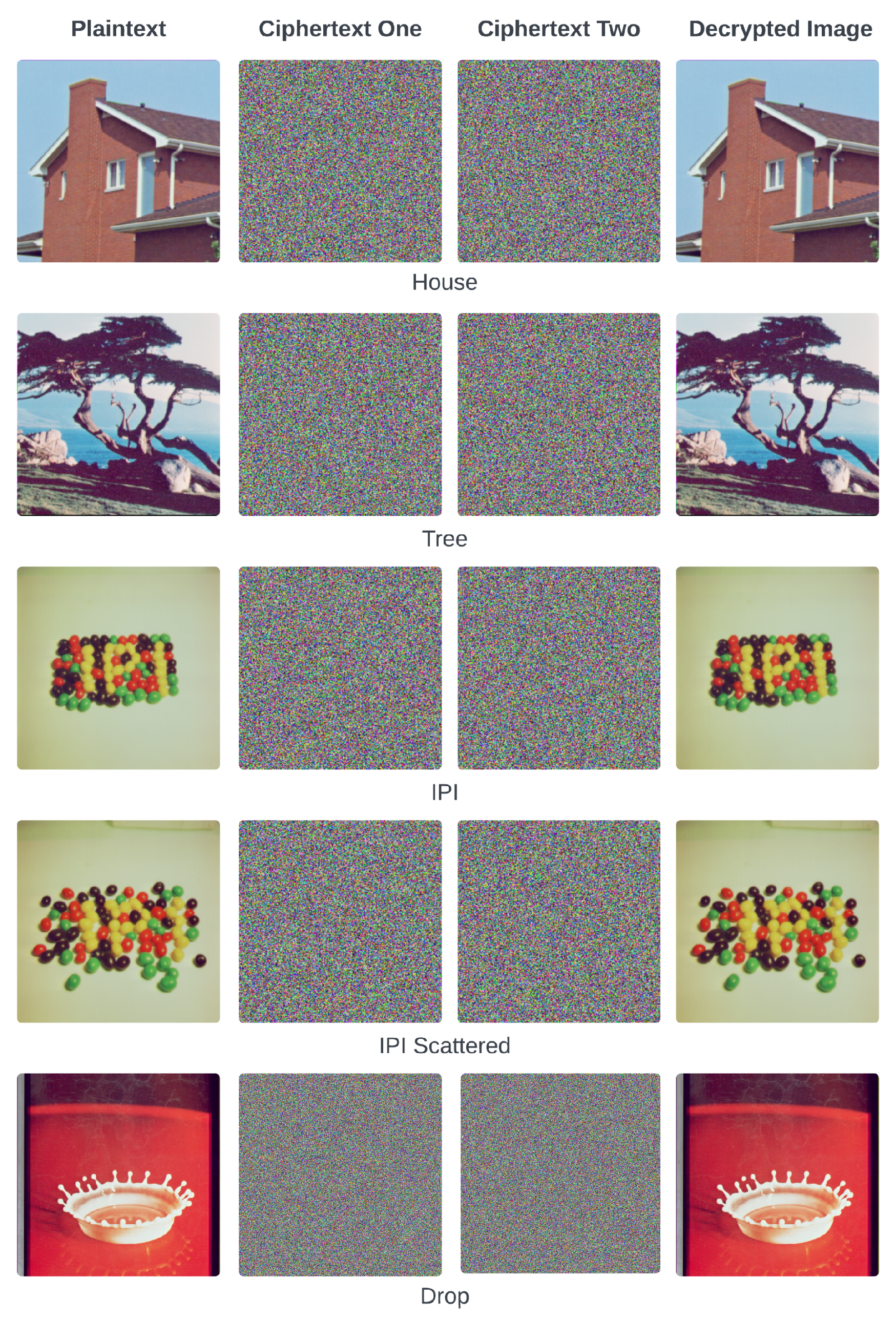
4.3. Image Encryption and Decryption
4.4. Statistical Analysis
4.5. Differential Attack Analysis
4.6. Keyspace Analysis
5. Discussion
- Extract and decrypt the bitstream from the FPGA to steal the hard-coded initial values to the LHCS (the private key).
- Replicate the system on an aggressor device.
- Intercept the victim’s data.
- Using the stolen private key, decode the incoming public key.
- Synchronize the public key refresh rate with the victim.
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Abbreviations
| FPGA | Field-Programmable Gate Array |
| Gbps | Gigabits per second |
| HDL | Hardware Description Language |
| RX | Receive |
| TX | Transmit |
| RTL | Register Transfer Level |
| TRNG | True Random Number Generator |
| IoT | Internet of Things |
| I/O | Input/Output |
| API | Application Programming Interface |
| PUF | Physically Unclonable Function |
| RO-PUF | Ring Oscillator Physically Unclonable Function |
| FIFO | First In, First Out Buffer |
| LHCS | Lorenz Hyperchaotic System |
| PCIe | Peripheral Component Interconnect Express |
| TLP | Transaction Layer Packet |
| DRAM | Dynamic Random Access Memory |
| PCC | Pearson Correlation Coefficient |
| UACI | Unified Average Change Intensity |
| NPCR | Number of Pixel Change Rates |
| NIST | National Institute of Standards and Technology |
References
- Magyari, A.; Chen, Y. Review of State-of-the-Art FPGA Applications in IoT Networks. Sensors 2022, 22, 7496. [Google Scholar] [CrossRef]
- Uganya, G.; Radhika; Vijayaraj, N. A survey on internet of things: Applications, recent issues, attacks, and security mechanisms. J. Circ. Syst. Comput. 2021, 30, 2130006. [Google Scholar] [CrossRef]
- Vaidyanathan, S.; Sampath, S. Global chaos synchronization of hyperchaotic Lorenz systems by sliding mode control. Commun. Comput. Inf. Sci. 2011, 205, 156–164. [Google Scholar]
- He, C.; Ming, K.; Wang, Y.; Wang, Z.J. A deep learning based attack for the chaos-based image encryption. arXiv 2019, arXiv:1907.12245. [Google Scholar]
- Munir, N.; Khan, M.; Jamal, S.S.; Hazzazi, M.M.; Hussain, I. Cryptanalysis of hybrid secure image encryption based on Julia set fractals and three-dimensional Lorenz chaotic map. Math. Comput. Simul. 2021, 190, 826–836. [Google Scholar] [CrossRef]
- Ahmad, M.; Aijaz, A.; Ansari, S.; Siddiqui, M.M.; Masood, S. Cryptanalysis of image cryptosystem using synchronized 4D lorenz stenflo hyperchaotic systems. In Information and Decision Sciences, Proceedings of the 6th International Conference on FICTA, Birmingham, UK, 6–8 September 2023; Springer: Berlin/Heidelberg, Germany, 2018; pp. 367–376. [Google Scholar]
- Fan, H.; Lu, H.; Zhang, C.; Li, M.; Liu, Y. Cryptanalysis of an image encryption algorithm based on random walk and hyperchaotic systems. Entropy 2021, 24, 40. [Google Scholar] [CrossRef] [PubMed]
- Bhandari, J.K.; Verma, Y.K.; Mishra, V.; Kumar, A.; Gupta, S.K. A PRBS Generator and Checker based BIST for Multipliers. In Proceedings of the 2023 International Conference on Innovative Data Communication Technologies and Application (ICIDCA), Uttarakhand, India, 14–16 March 2023; IEEE: Piscataway, NJ, USA, 2023; pp. 1–5. [Google Scholar]
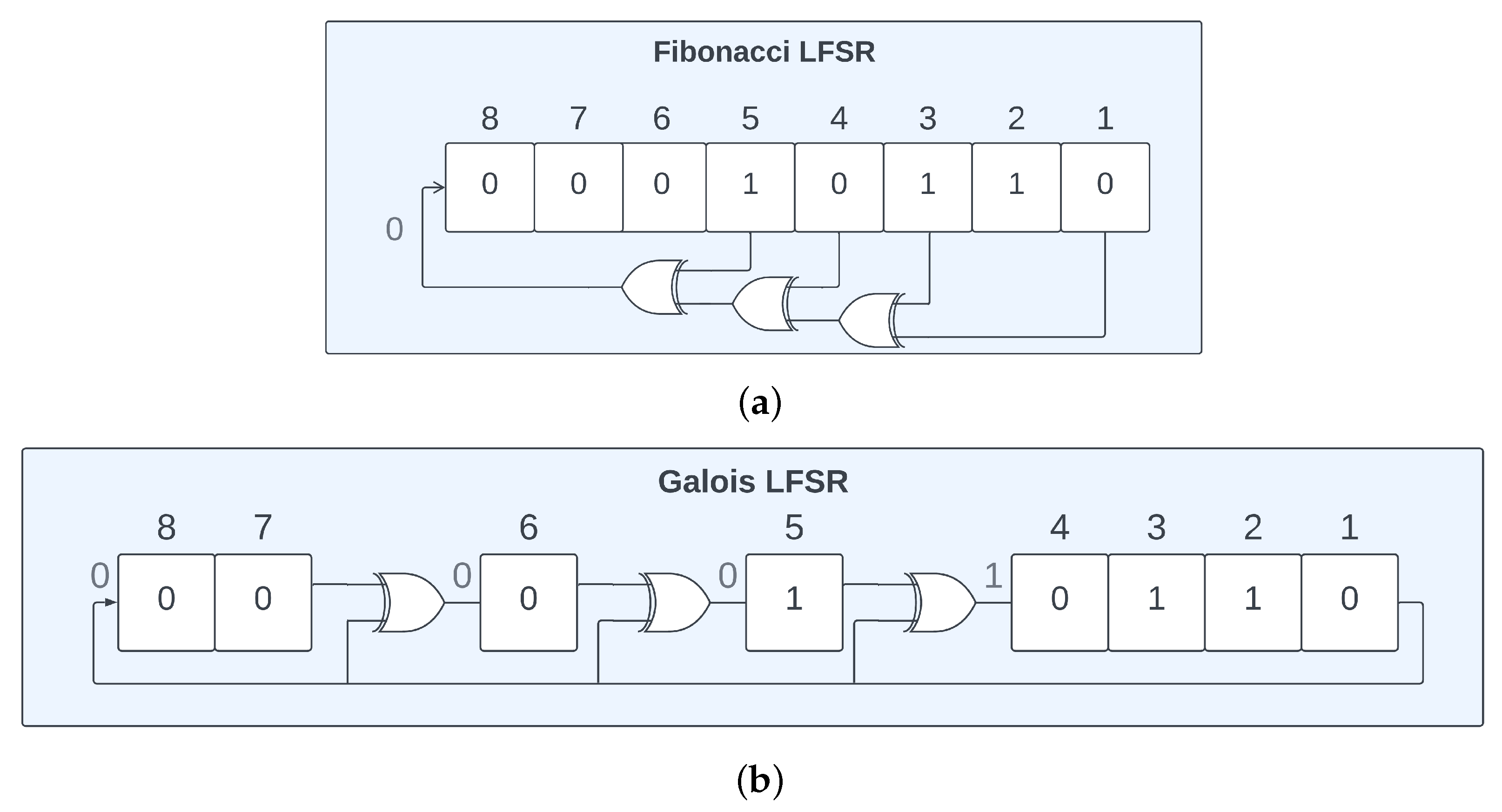
- Li, W.; Yang, X. A parallel and reconfigurable united architecture for Fibonacci and Galois LFSR. In Proceedings of the 2015 7th International Conference on Intelligent Human-Machine Systems and Cybernetics, Hangzhou, China, 26–27 August 2015; IEEE: Piscataway, NJ, USA, 2015; Volume 1, pp. 203–206. [Google Scholar]
- Dubrova, E. A transformation from the Fibonacci to the Galois NLFSRs. IEEE Trans. Inf. Theory 2009, 55, 5263–5271. [Google Scholar] [CrossRef]
- Della Sala, R.; Bellizia, D.; Scotti, G. A novel ultra-compact FPGA-compatible TRNG architecture exploiting latched ring oscillators. IEEE Trans. Circuits Syst. II Express Briefs 2021, 69, 1672–1676. [Google Scholar] [CrossRef]
- Prada-Delgado, M.A.; Martínez-Gómez, C.; Baturone, I. Auto-calibrated ring oscillator TRNG based on jitter accumulation. In Proceedings of the 2020 IEEE International Symposium on Circuits and Systems (ISCAS), Seville, Spain, 12–14 October 2020; IEEE: Piscataway, NJ, USA, 2020; pp. 1–4. [Google Scholar]
- Choi, S.; Shin, Y.; Yoo, H. Analysis of Ring-Oscillator-based True Random Number Generator on FPGAs. In Proceedings of the 2021 International Conference on Electronics, Information, and Communication (ICEIC), Jeju, Republic of Korea, 31 January–3 February 2021; IEEE: Piscataway, NJ, USA, 2021; pp. 1–3. [Google Scholar]
- Fujieda, N. On the Feasibility of TERO-Based True Random Number Generator on Xilinx FPGAs. In Proceedings of the 2020 30th International Conference on Field-Programmable Logic and Applications (FPL), Gothenburg, Sweden, 31 August–4 September 2020; pp. 103–108. [Google Scholar] [CrossRef]
- Hu, Y.; Jiang, Y.; Wang, W. Transient Effect Ring Oscillator PUF Based on Programmable Delay Lines. In Proceedings of the 2022 International Conference on Innovations in Science, Engineering and Technology (ICISET), Chittagong, Bangladesh, 26–27 February 2022; pp. 528–533. [Google Scholar] [CrossRef]
- Nannipieri, P.; Di Matteo, S.; Baldanzi, L.; Crocetti, L.; Belli, J.; Fanucci, L.; Saponara, S. True random number generator based on Fibonacci-Galois ring oscillators for FPGA. Appl. Sci. 2021, 11, 3330. [Google Scholar] [CrossRef]
- Tao, S.; Yu, Y.; Dubrova, E. FPGA Based True Random Number Generators Using Non-Linear Feedback Ring Oscillators. In Proceedings of the 2018 16th IEEE International New Circuits and Systems Conference (NEWCAS), Montreal, QC, Canada, 24–27 June 2018; pp. 213–216. [Google Scholar] [CrossRef]
- Anandakumar, N.N.; Hashmi, M.S.; Tehranipoor, M. FPGA-based Physical Unclonable Functions: A comprehensive overview of theory and architectures. Integration 2021, 81, 175–194. [Google Scholar] [CrossRef]
- He, Z.; Chen, W.; Zhang, L.; Chi, G.; Gao, Q.; Harn, L. A highly reliable arbiter PUF with improved uniqueness in FPGA implementation using Bit-Self-Test. IEEE Access 2020, 8, 181751–181762. [Google Scholar] [CrossRef]
- Mahalat, M.H.; Mandal, S.; Mondal, A.; Sen, B. An efficient implementation of arbiter PUF on FPGA for IoT application. In Proceedings of the 2019 32nd IEEE International System-on-Chip Conference (SOCC), Singapore, 3–6 September 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 324–329. [Google Scholar]
- Li, K.l.; Meng, Y.; Li, J.; Wang, S.k.; Yang, J. Research and design of a high-security configurable RO-PUF based on FPGA. Procedia Comput. Sci. 2021, 183, 40–45. [Google Scholar] [CrossRef]
- Zhou, K.; Liang, H.; Jiang, Y.; Huang, Z.; Jiang, C.; Lu, Y. FPGA-based RO PUF with low overhead and high stability. Electron. Lett. 2019, 55, 510–513. [Google Scholar] [CrossRef]
- Deng, D.; Hou, S.; Wang, Z.; Guo, Y. Configurable ring oscillator PUF using hybrid logic gates. IEEE Access 2020, 8, 161427–161437. [Google Scholar] [CrossRef]
- Garcia-Bosque, M.; Díez-SEñorans, G.; Sánchez-Azqueta, C.; Celma, S. Proposal and analysis of a novel class of PUFs based on Galois ring oscillators. IEEE Access 2020, 8, 157830–157839. [Google Scholar] [CrossRef]
- Chien, W.C.; Chang, Y.C.; Tsou, Y.T.; Kuo, S.Y.; Chang, C.R. STT-DPSA: Digital PUF-based secure authentication using STT-MRAM for the Internet of things. Micromachines 2020, 11, 502. [Google Scholar] [CrossRef]
- Farha, F.; Ning, H.; Ali, K.; Chen, L.; Nugent, C. SRAM-PUF-based entities authentication scheme for resource-constrained IoT devices. IEEE Internet Things J. 2020, 8, 5904–5913. [Google Scholar] [CrossRef]
- Dachowicz, A.; Atallah, M.; Panchal, J.H. Optical PUF design for anti-counterfeiting in manufacturing of metallic goods. In Proceedings of the International Design Engineering Technical Conferences and Computers and Information in Engineering Conference, Quebec City, QC, Canada, 26–29 August 2018; American Society of Mechanical Engineers: New York, NY, USA, 2018; Volume 51739, p. V01BT02A035. [Google Scholar]
- Ibrahim, O.A.; Sciancalepore, S.; Di Pietro, R. MAG-PUF: Magnetic Physical Unclonable Functions for Device Authentication in the IoT. In Proceedings of the Security and Privacy in Communication Networks: 18th EAI International Conference, SecureComm 2022, Virtual Event, 17–19 October 2022; Springer: Berlin/Heidelberg, Germany, 2023; pp. 130–149. [Google Scholar]
- Monteiro, C.; Takahashi, Y. Low-power two-phase clocking adiabatic PUF circuit. Electronics 2021, 10, 1258. [Google Scholar] [CrossRef]
- Monteiro, C.; Takahashi, Y. Ultra-Low-Power FinFETs-Based TPCA-PUF Circuit for Secure IoT Devices. Sensors 2021, 21, 8302. [Google Scholar] [CrossRef]
- Rusyn, V.; Mujiarto; Mamat, M.; Azharul, F.; Sanjaya, W.M.; Sambas, A.; Dwipriyoko, E.; Sutoni, A. Computer modelling of the information properties of hyper chaotic lorenz system and its application in secure communication system. Proc. J. Phys. Conf. Ser. IOP Publ. 2021, 1764, 012205. [Google Scholar] [CrossRef]
- Kushnir, M.; Galiuk, S.; Rusyn, V.; Kosovan, G.; Vovchuk, D. Computer modeling of information properties of deterministic chaos. In Proceedings of the Chaotic Modeling and Simulation International Conference (CHAOS2014), Lisbon, Portugal, 7–10 June 2014; pp. 265–276. [Google Scholar]
- Ye, G.; Wu, H.; Liu, M.; Shi, Y. Image encryption scheme based on blind signature and an improved Lorenz system. Expert Syst. Appl. 2022, 205, 117709. [Google Scholar] [CrossRef]
- Alexan, W.; ElBeltagy, M.; Aboshousha, A. Rgb image encryption through cellular automata, s-box and the lorenz system. Symmetry 2022, 14, 443. [Google Scholar] [CrossRef]
- Moon, S.; Baik, J.J.; Seo, J.M. Chaos synchronization in generalized Lorenz systems and an application to image encryption. Commun. Nonlinear Sci. Numer. Simul. 2021, 96, 105708. [Google Scholar] [CrossRef]
- Tariq, S.; Khan, M.; Alghafis, A.; Amin, M. A novel hybrid encryption scheme based on chaotic Lorenz system and logarithmic key generation. Multimed. Tools Appl. 2020, 79, 23507–23529. [Google Scholar] [CrossRef]
- Zou, C.; Zhang, Q.; Wei, X.; Liu, C. Image Encryption Based on Improved Lorenz System. IEEE Access 2020, 8, 75728–75740. [Google Scholar] [CrossRef]
- Ilyas, B.; Raouf, S.M.; Abdelkader, S.; Camel, T.; Said, S.; Lei, H. An Efficient and Reliable Chaos-Based IoT Security Core for UDP/IP Wireless Communication. IEEE Access 2022, 10, 49625–49656. [Google Scholar] [CrossRef]
- Moradi, A.; Barenghi, A.; Kasper, T.; Paar, C. On the vulnerability of FPGA bitstream encryption against power analysis attacks: Extracting keys from Xilinx Virtex-II FPGAs. In Proceedings of the 18th ACM Conference on Computer and Communications Security, Chicago, IL, USA, 17–21 October 2011; pp. 111–124. [Google Scholar]
- Duncan, A.; Rahman, F.; Lukefahr, A.; Farahmandi, F.; Tehranipoor, M. FPGA Bitstream Security: A Day in the Life. In Proceedings of the 2019 IEEE International Test Conference (ITC), Washington, DC, USA, 9–15 November 2019; pp. 1–10. [Google Scholar] [CrossRef]
- Ramesh, C.; Patil, S.B.; Dhanuskodi, S.N.; Provelengios, G.; Pillement, S.; Holcomb, D.; Tessier, R. FPGA side channel attacks without physical access. In Proceedings of the 2018 IEEE 26th Annual International Symposium on Field-Programmable Custom Computing Machines (FCCM), Boulder, CO, USA, 29 April–1 May 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 45–52. [Google Scholar]
- Bouteghrine, B.; Tanougast, C.; Sadoudi, S. Design and FPGA implementation of new multidimensional chaotic map for secure communication. J. Circuits Syst. Comput. 2021, 30, 2150280. [Google Scholar] [CrossRef]
- Yushkova, M.; Sanchez, A.; de Castro, A. Strategies for choosing an appropriate numerical method for FPGA-based HIL. Int. J. Electr. Power Energy Syst. 2021, 132, 107186. [Google Scholar] [CrossRef]
- Alcin, M.; Murat, T.; Erdoğmuş, P.; Koyuncu, I. FPGA-based dual core TRNG design using Ring and Runge-Kutta-Butcher based on chaotic oscillator. Chaos Theory Appl. 2021, 3, 20–28. [Google Scholar] [CrossRef]
- Yu, F.; Zhang, Z.; Shen, H.; Huang, Y.; Cai, S.; Jin, J.; Du, S. Design and FPGA implementation of a pseudo-random number generator based on a Hopfield neural network under electromagnetic radiation. Front. Phys. 2021, 9, 690651. [Google Scholar] [CrossRef]
- Garg, A.; Yadav, B.; Sahu, K.; Suneja, K. An FPGA based Real time Implementation of Nosé hoover Chaotic System using different numerical Techniques. In Proceedings of the 2021 7th International Conference on Advanced Computing and Communication Systems (ICACCS), Coimbatore, India, 19–20 March 2021; IEEE: Piscataway, NJ, USA, 2021; Volume 1, pp. 108–113. [Google Scholar]
- Letellier, C.; Rossler, O.E. Hyperchaos. Scholarpedia 2007, 2, 1936. [Google Scholar] [CrossRef]
- Lai, Q.; Wan, Z.; Kuate, P.D.K.; Fotsin, H. Coexisting attractors, circuit implementation and synchronization control of a new chaotic system evolved from the simplest memristor chaotic circuit. Commun. Nonlinear Sci. Numer. Simul. 2020, 89, 105341. [Google Scholar] [CrossRef]
- Rukhin, A.; Soto, J.; Nechvatal, J.; Smid, M.; Barker, E. A Statistical Test Suite for Random and Pseudorandom Number Generators for Cryptographic Applications; Technical Report; Booz-Allen and Hamilton Inc Mclean Va: Tysons Corner, VA, USA, 2001. [Google Scholar]
- Weber, A.G. The USC-SIPI Image Database: Version 5. 2006. Available online: http://sipi.usc.edu/database/ (accessed on 18 June 2023).
- Neamah, A.A.; Shukur, A.A. A Novel Conservative Chaotic System Involved in Hyperbolic Functions and Its Application to Design an Efficient Colour Image Encryption Scheme. Symmetry 2023, 15, 1511. [Google Scholar] [CrossRef]
- Rényi, A. On measures of entropy and information. In Proceedings of the Fourth Berkeley Symposium on Mathematical Statistics and Probability, Volume 1: Contributions to the Theory of Statistics; University of California Press: Berkeley, CA, USA, 1961; Volume 4, pp. 547–562. [Google Scholar]
- Khalid, I.; Shah, T.; Eldin, S.M.; Shah, D.; Asif, M.; Saddique, I. An integrated image encryption scheme based on elliptic curve. IEEE Access 2022, 11, 5483–5501. [Google Scholar] [CrossRef]
- Hu, X.; Wei, L.; Chen, W.; Chen, Q.; Guo, Y. Color image encryption algorithm based on dynamic chaos and matrix convolution. IEEE Access 2020, 8, 12452–12466. [Google Scholar] [CrossRef]
- Yang, F.; Mou, J.; Sun, K.; Cao, Y.; Jin, J. Color image compression-encryption algorithm based on fractional-order memristor chaotic circuit. IEEE Access 2019, 7, 58751–58763. [Google Scholar] [CrossRef]
- Cai, X.; Liu, C.; Wang, Y.; Zhang, H. A novel 4D chaotic system with nonhyperbolic hyperbolic shape equilibrium points: Analysis, circuit implementation and color image encryption. Int. J. Mod. Phys. B 2019, 33, 1950383. [Google Scholar] [CrossRef]
- Annaby, M.; Ayad, H.; Rushdi, M. A Difference-Equation-Based Robust Image Encryption Scheme with Chaotic Permutations and Logic Gates. J. Math. Imaging Vis. 2022, 64, 855–868. [Google Scholar] [CrossRef]
- Kaur, M.; Kumar, V. Efficient image encryption method based on improved Lorenz chaotic system. Electron. Lett. 2018, 54, 562–564. [Google Scholar] [CrossRef]




| Components | Base PCIe | Full System | LHCS w/ Controller | Net Utilization |
|---|---|---|---|---|
| ALMs | 10.7 k | 23.4 k | 12.7 k | 2% |
| ALUTs | 11.2 k | 26.1 k | 14.9 k | <1% |
| M20Ks | 89 | 177 | 86 | 2% |
| DSPs | 0 | 14 | 14 | <1% |
| PLLs | 1 | 2 | 1 | <1% |
| System | Power Usage |
|---|---|
| PCIe Base Design | 5948 mW |
| Full System | 6328 mW |
| LHCS/Controller | 380 mW |
| Test Type | p Value | Required Value | Result |
|---|---|---|---|
| Frequency (Monobit) | 0 | >0.01 | Non-Random |
| Frequency within a Block | 0 | >0.01 | Non-Random |
| Run | 0 | >0.01 | Non-Random |
| Longest run of ones | 0 | >0.01 | Non-Random |
| Binary Matrix Rank | −1 | >0.01 | Non-Random |
| Discrete Fourier Transform | 0.43 | >0.01 | Random |
| Maurer’s Universal Test | −1 | >0.01 | Non-Random |
| Non-overlapping Template | 1 | >0.01 | Random |
| Overlapping Template | 0 | >0.01 | Non-Random |
| Linear Complexity | 0.50 | >0.01 | Random |
| Serial | 0.50 | >0.01 | Random |
| Approximate Entropy | 1.0 | >0.01 | Random |
| Cummulative Sums | 1.0 | >0.01 | Random |
| Reverse Cummulative Sums | 1.0 | >0.01 | Random |
| Random Excursions | 0.22 | >0.01 | Random |
| Random Excursions Varient | 1.0 | >0.01 | Random |
| Image Cipher | Red | Green | Blue | Average |
|---|---|---|---|---|
| Ruler | 251 | 228 | 229 | 236 |
| Babboon | 265 | 265 | 217 | 249 |
| Plane | 286 | 259 | 232 | 259 |
| Peppers | 291 | 259 | 270 | 274 |
| House | 272 | 265 | 288 | 275 |
| Image Cipher | Red | Green | Blue | Average |
|---|---|---|---|---|
| Ruler | 7.9972 | 7.9975 | 7.9975 | 7.9974 |
| Babboon | 7.9993 | 7.9993 | 7.9994 | 7.9993 |
| Plane | 7.9992 | 7.9993 | 7.9994 | 7.9992 |
| Peppers | 7.9992 | 7.9993 | 7.9993 | 7.9992 |
| House | 7.9970 | 7.9971 | 7.9968 | 7.9970 |
| Test Type | Proposed | [53] | [54] | [55] | [56] | [51] |
|---|---|---|---|---|---|---|
| 275 | 241 | 287 | N/A | N/A | 260 | |
| Entropy | 7.9970 | 7.9990 | 7.994 | 7.9985 | 7.9890 | 7.9971 |
| Image Name | PCC | UACI | NPCR |
|---|---|---|---|
| Mandrill | 0.001 | 33.4% | 99.6% |
| Peppers | 0.003 | 33.5% | 99.6% |
| Resolution Chart | 0.010 | 33.4% | 99.6% |
| Boat | 0.001 | 33.5% | 99.6% |
| House | 0.002 | 33.5% | 99.6% |
| Plane | 0.002 | 33.5% | 99.6% |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Magyari, A.; Chen, Y. Integrating Lorenz Hyperchaotic Encryption with Ring Oscillator Physically Unclonable Functions (RO-PUFs) for High-Throughput Internet of Things (IoT) Applications. Electronics 2023, 12, 4929. https://doi.org/10.3390/electronics12244929
Magyari A, Chen Y. Integrating Lorenz Hyperchaotic Encryption with Ring Oscillator Physically Unclonable Functions (RO-PUFs) for High-Throughput Internet of Things (IoT) Applications. Electronics. 2023; 12(24):4929. https://doi.org/10.3390/electronics12244929
Chicago/Turabian StyleMagyari, Alexander, and Yuhua Chen. 2023. "Integrating Lorenz Hyperchaotic Encryption with Ring Oscillator Physically Unclonable Functions (RO-PUFs) for High-Throughput Internet of Things (IoT) Applications" Electronics 12, no. 24: 4929. https://doi.org/10.3390/electronics12244929
APA StyleMagyari, A., & Chen, Y. (2023). Integrating Lorenz Hyperchaotic Encryption with Ring Oscillator Physically Unclonable Functions (RO-PUFs) for High-Throughput Internet of Things (IoT) Applications. Electronics, 12(24), 4929. https://doi.org/10.3390/electronics12244929










