A Comprehensive Attack Flow Model and Security Analysis for Wi-Fi and WPA3
Abstract
:1. Introduction
2. Wi-Fi Security Protocols and Limitations
2.1. Wireless Equivalency Protocol
2.2. Wi-Fi Protected Access
2.2.1. Protocol Details
2.2.2. Limitations
2.3. Wi-Fi Protected Access Version 2
2.3.1. Protocol Details
2.3.2. Limitations
3. Attack Flow
3.1. Phase 1
3.1.1. State-No Key/No Access
3.1.2. Attack-De-Authentication Attack
3.1.3. Attack-Handshake Capture Dictionary Attack
3.1.4. Attack-PMKID Hash Dictionary Attack
3.1.5. Attack-Rogue Access Point
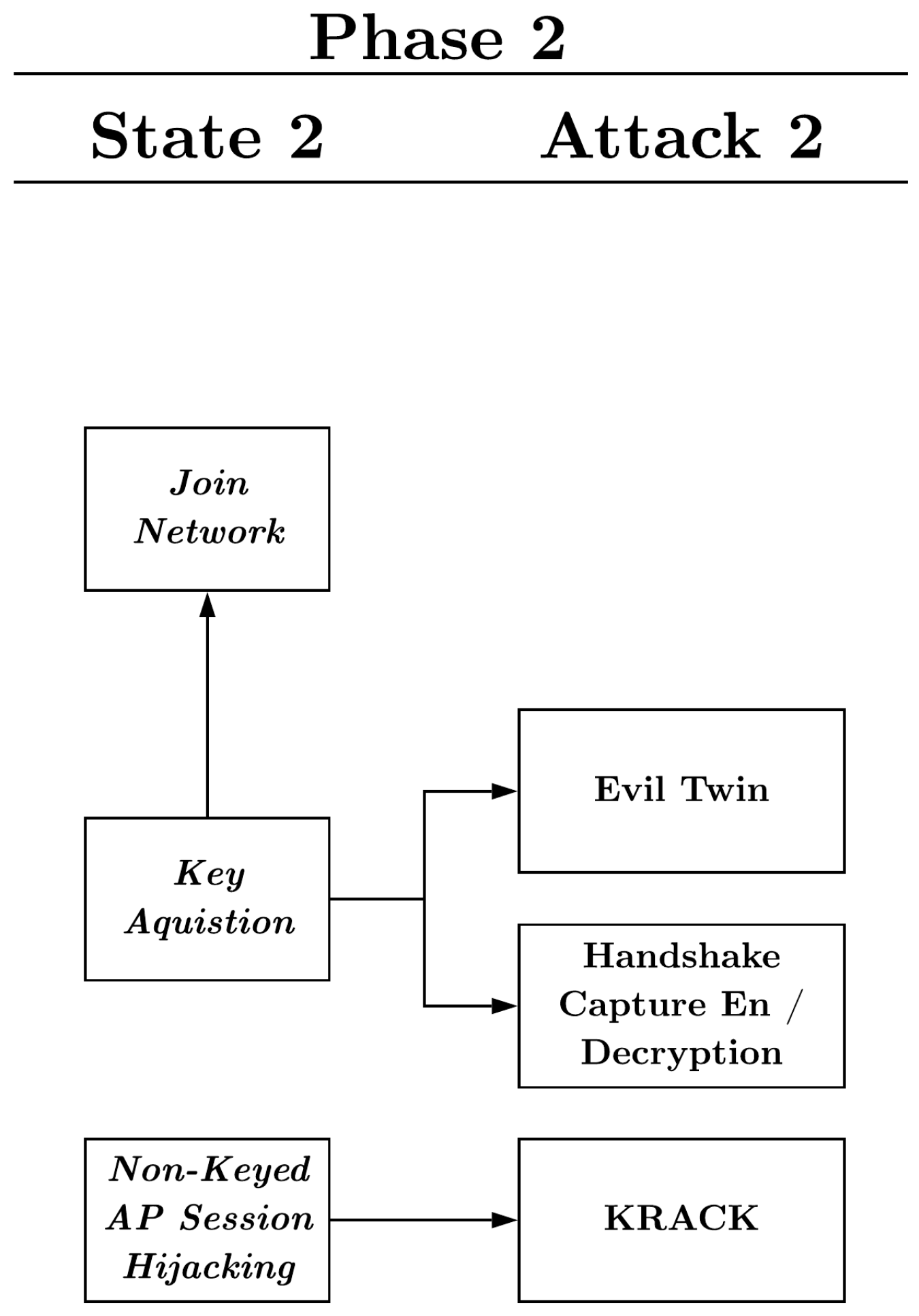
3.2. Phase 2
3.2.1. State-Key Acquisition
3.2.2. State-Join Network
3.2.3. State-Non-Keyed AP Session Hijacking
3.2.4. Attack-Evil Twin Attack
3.2.5. Attack-Handshake Capture Encryption/Decryption
3.2.6. Attack-KRACK Exploit
3.3. Phase 3
3.3.1. State-Man-in-the-Middle
3.3.2. State-Packet Sniffing
3.3.3. Attack-ARP Spoofing
3.4. Phase 4
3.4.1. State-Keyed AP Session Hijacking
3.4.2. State-Keyed Client Session Hijacking
3.4.3. Attack-SSL Stripping
3.4.4. Attack-DNS Spoofing
3.5. Outcomes
- Denial of service: preventing a user from accessing the Internet or other specific services through the gateway.
- Deception: tricking the user into believing he/she is communicating with one host or gateway, but is actually communicating with the adversary.
- Impersonation: taking the users identity and making a remote host or gateway believe the adversary is the user.
- Stolen information: taking sensitive information from the user, such as credentials or PII.
4. Wi-Fi Protected Access Version 3
4.1. Overview
- Spectrum management
- QoS (Quality of Service)
- DLS (Direct Link Setup)
- Block Ack (Acknowledgment)
- Radio measurement
- Fast BSS (Base Service Station) transition
- SA query
- Protected dual of public action
- Vendor-specific protected
4.2. Security Evaluation and Analysis
4.2.1. De-Authentication
4.2.2. Handshake Capture Dictionary Attack
4.2.3. PMKID Hash Dictionary Attack
4.2.4. Rogue Access Point
4.2.5. Evil Twin Attack
4.2.6. Handshake Capture En/Decryption
4.2.7. KRACK Exploit
4.2.8. ARP Spoofing
4.2.9. SSL Stripping
4.2.10. DNS Spoofing
5. Discussion
6. Other Defenses and Mitigations
6.1. Rogue Access Point
6.2. Evil Twin
6.3. ARP Spoofing
6.4. SSL Stripping
6.5. DNS Spoofing
7. Conclusions
Author Contributions
Funding
Conflicts of Interest
Abbreviations
| Ack | Acknowledgment |
| AES | Advanced Encryption Standard |
| AP | Access Point |
| ARP | Address Resolution Protocol |
| BSS | Base Service Station |
| CBC | Cipher-Block Chaining |
| CCMP | Counter Mode with Cipher Block Chaining Message Authentication Code Protocol |
| CRC | Cyclic Redundancy Check |
| CSA | Channel Switch Announcement |
| CTR | Counter Mode |
| DLS | Direct Link Setup |
| DNS | Domain Name Server |
| DoS | Denial of Service |
| EAP | Extensible Authentication Protocol |
| EAPOL | EAP over LAN |
| GTK | Group Temporal Key |
| HMAC | Hash Message Authentication Protocol |
| HTTP | HyperText Transfer Protocol |
| HSTS | HTTP Strict Transport Security |
| ICV | Integrity Check Value |
| IEEE | Electrical and Electronics Engineers |
| IP | Internet Protocol |
| IV | Initialization Vector |
| KRACK | Key Re-installation Attack |
| MAC | Medium Access Control |
| MIC | Message Integrity Code |
| MITM | Man-in-the-Middle |
| PBKDF2 | Password-Based Key Derivation Function 2 |
| PMF | Protected Management Frames |
| PMK | Pairwise Master Key |
| PMKID | Pairwise Master Key Identification |
| PN | Packet Number |
| PRNG | Pseudo Random Number Generator |
| PSK | Pre-Shared Key |
| PTK | Pairwise Transient Key |
| QoS | Quality of Service |
| RC4 | Rivest Cipher 4 |
| RF | Radio Frequency |
| RSN | Robust Security Network Information Element |
| SA | Security Association |
| SAE | Simultaneous Authentication of Equals |
| SSID | Service Set Identifier |
| SSL | Secured Socket Layer |
| TK | Temporal Key |
| TKIP | Temporal Key Integrity Protocol |
| TSC | TKIP Sequence Counter |
| VPN | Virtual Private Network |
| WEP | Wired Equivalent Privacy |
| WLAN | Wireless Local Area Networks |
| WPA | Wi-Fi Protected Access |
| WPA2 | Wi-Fi Protected Access II |
| WPA3 | Wi-Fi Protected Access III |
References
- Gast, M. 802.11 Wireless Networks: The Definitive Guide; O’Reilly Media, Inc.: Newton, MA, USA, 2005. [Google Scholar]
- Vanhoef, M.; Piessens, F. Key reinstallation attacks: Forcing nonce reuse in WPA2. In Proceedings of the 2017 ACM SIGSAC Conference on Computer and Communications Security, Dallas, TX, USA, 30 October–3 November 2017; pp. 1313–1328. [Google Scholar]
- Steube, J. New Attack on WPA/WPA2 Using PMKID. Available online: https://hashcat.net/forum/thread-7717.html (accessed on 30 October 2018).
- Simic, D.; Prodanovic, R. A survey of wireless security. J. Comput. Inf. Technol. 2007, 15, 237–255. [Google Scholar]
- Zou, Y.; Zhu, J.; Wang, X.; Hanzo, L. A survey on wireless security: Technical challenges, recent advances, and future trends. Proc. IEEE 2016, 1–39. [Google Scholar] [CrossRef]
- Fouque, P.A.; Martinet, G.; Valette, F.; Zimmer, S. On the Security of the CCM Encryption Mode and of a Slight Variant. In Proceedings of the International Conference on Applied Cryptography and Network Security, New York, NY, USA, 3–6 June 2008; pp. 411–428. [Google Scholar]
- Lashkari, A.H.; Danesh, M.M.S.; Samadi, B. A survey on wireless security protocols (WEP, WPA and WPA2/802.11 i). In Proceedings of the 2nd IEEE International Conference on Computer Science and Information Technology, Beijing, China, 8–11 August 2009; pp. 48–52. [Google Scholar]
- Stubblefield, A.; Ioannidis, J.; Rubin, A.D. A key recovery attack on the 802.11 b wired equivalent privacy protocol (WEP). ACM Trans. Inf. Syst. Secur. 2004, 7, 319–332. [Google Scholar] [CrossRef]
- Tews, E.; Weinmann, R.P.; Pyshkin, A. Breaking 104 bit WEP in less than 60 seconds. In International Workshop on Information Security Applications; Springer: Berlin, Germany, 2007; pp. 188–202. [Google Scholar]
- Tews, E.; Beck, M. Practical attacks against WEP and WPA. In Proceedings of the Second ACM Conference on Wireless Network Security, Zurich, Switzerland, 16–19 March 2009; pp. 79–86. [Google Scholar]
- Mavoungou, S.; Kaddoum, G.; Taha, M.; Matar, G. Survey on threats and attacks on mobile networks. IEEE Access 2016, 4, 4543–4572. [Google Scholar] [CrossRef]
- Tekade, P.S.; Shelke, C. A Survey on different Attacks on Mobile Devices and its Security. Int. J. Appl. Innov. Eng. Manag. 2014, 3, 247–251. [Google Scholar]
- Sen, J. A survey on wireless sensor network security. arXiv, 2010; arXiv:1011.1529. [Google Scholar]
- Wang, Y.; Attebury, G.; Ramamurthy, B. A Survey of Security Issues in Wireless Sensor Networks; IEEE Press: Piscataway, NJ, USA, 2006. [Google Scholar]
- Walters, J.P.; Liang, Z.; Shi, W.; Chaudhary, V. Wireless sensor network security: A survey. Secur. Distrib. Grid Mob. Perv. Comput. 2007, 1, 367. [Google Scholar]
- Christin, D.; Mogre, P.S.; Hollick, M. Survey on wireless sensor network technologies for industrial automation: The security and quality of service perspectives. Future Internet 2010, 2, 96–125. [Google Scholar] [CrossRef]
- Akyildiz, I.F.; Wang, X. A survey on wireless mesh networks. IEEE Commun. Mag. 2005, 43, S23–S30. [Google Scholar] [CrossRef]
- Sukhija, S.; Gupta, S. Wireless network security protocols a comparative study. Int. J. Emerg. Technol. Adv. Eng. 2012, 2, 357–364. [Google Scholar]
- Juwaini, M.; Alsaqour, R.; Abdelhaq, M.; Alsukour, O. A review on WEP wireless security protocol. J. Theor. Appl. Inf. Technol. 2012, 40, 39–43. [Google Scholar]
- Vanhoef, M.; Piessens, F. Practical verification of WPA-TKIP vulnerabilities. In Proceedings of the 8th ACM SIGSAC symposium on Information, computer and communications security, Hangzhou, China, 8–10 May 2013; pp. 427–436. [Google Scholar]
- Tripathi, A.; Damani, O.P. Relative encryption overhead in 802.11 g network. In Proceedings of the International Symposium on Telecommunications, Tehran, Iran, 27–28 Auguet 2008; pp. 420–423. [Google Scholar]
- Ferreira, R.A. A Probability Problem Arising from the Security of the Temporal Key Hash of WPA. Wirel. Pers. Commun. 2013, 70, 1235–1241. [Google Scholar] [CrossRef]
- Han, W.; Zheng, D.; Chen, K.f. Some remarks on the TKIP key mixing function of IEEE 802.11 i. J. Shanghai Jiaotong Univ. (Sci.) 2009, 14, 81–85. [Google Scholar] [CrossRef]
- Sheldon, F.T.; Weber, J.M.; Yoo, S.M.; Pan, W.D. The insecurity of wireless networks. IEEE Secur. Priv. 2012, 10, 54–61. [Google Scholar] [CrossRef]
- Cebula, S.L.; Ahmad, A.; Wahsheh, L.A.; Graham, J.M.; DeLoatch, S.L.; Williams, A.T. How secure is WiFi MAC layer in comparison with IPsec for classified environments? In Proceedings of the 14th Communications and Networking Symposium, Society for Computer Simulation International, Boston, MA, USA, 3–7 April 2011; pp. 109–116. [Google Scholar]
- Bellardo, J.; Savage, S. 802.11 Denial-of-Service Attacks: Real Vulnerabilities and Practical Solutions; Usenix Security Symposium: Washington, DC, USA, 2003; Volume 12, p. 2. [Google Scholar]
- Kumkar, V.; Tiwari, A.; Tiwari, P.; Gupta, A.; Shrawne, S. Vulnerabilities of Wireless Security protocols (WEP and WPA2). Int. J. Adv. Res. Comput. Eng. Technol. 2012, 1, 34. [Google Scholar]
- Wi-Fi Certified WPA3 Technology Overview. Available online: https://www.wi-fi.org/downloads-registered-guest (accessed on 30 October 2018).
- Harkins, D. Simultaneous authentication of equals: A secure, password-based key exchange for mesh networks. In Proceedings of the Second International Conference on Sensor Technologies and Applications, Cap Esterel, France, 25–31 August 2008; pp. 839–844. [Google Scholar]
- Clarke, D.; Hao, F. Cryptanalysis of the dragonfly key exchange protocol. IET Inf. Secur. 2014, 8, 283–289. [Google Scholar] [CrossRef]
- Harkins, D. Dragonfly Key Exchange. Aruba Networks. Available online: https://tools.ietf.org/html/rfc7664 (accessed on 30 October 2018).
- Lancrenon, J.; Škrobot, M. On the Provable Security of the Dragonfly protocol. In Proceedings of the International Information Security Conference, Trondheim, Norway, 19–21 September 2015; pp. 244–261. [Google Scholar]
- Koblitz, N. Elliptic curve cryptosystems. Math. Comput. 1987, 48, 203–209. [Google Scholar] [CrossRef]
- Wi-Fi Certified Enhanced Open Technology Overview. Available online: https://www.wi-fi.org/beacon/dan-harkins/wi-fi-certified-enhanced-open-transparent-wi-fi-protections-without-complexity (accessed on 30 October 2018).
- Ahmad, M.S.; Tadakamadla, S. Short paper: Security evaluation of IEEE 802.11w specification. In Proceedings of the fourth ACM conference on Wireless network security, Hamburg, Germany, 14–17 June 2011; pp. 53–58. [Google Scholar]
- Cisco. 802.11w Protected Management Frames; Cisco: San Jose, CA, USA, November 2017. [Google Scholar]
- Nikbakhsh, S.; Manaf, A.B.A.; Zamani, M.; Janbeglou, M. A novel approach for rogue access point detection on the client-side. In Proceedings of the 26th International Conference on Advanced Information Networking and Applications Workshops (WAINA), Fukuoka, Japan, 26–29 March 2012; pp. 684–687. [Google Scholar]
- Agrawal, N.; Pradeepkumar, B.; Tapaswi, S. Preventing ARP spoofing in WLAN using SHA-512. In Proceedings of the Computational Intelligence and Computing Research (ICCIC), Enathi, India, 26–28 December 2013; pp. 1–5. [Google Scholar]
- Behboodian, N.; Razak, S.A. ARP Poisoning Attack Detection and Protection in WLAN via Client Web Browser. In Proceedings of the International Conference on Emerging Trends in Computer and Image, Bangkok, Thailand, 23–24 December 2011; p. 20. [Google Scholar]
- Cisco. Wireless and Network Security Integration Solution Design Guide; Cisco: San Jose, CA, USA, December 2013. [Google Scholar]
- Clark, J.; van Oorschot, P.C. SoK: SSL and HTTPS: Revisiting past challenges and evaluating certificate trust model enhancements. In Proceedings of the 2013 IEEE Symposium on Security and Privacy (SP), Berkeley, CA, USA, 19–22 May 2013; pp. 511–525. [Google Scholar]








| Attack | Solved by WPA3 |
|---|---|
| Deauthentication | Yes |
| Handshake Capture Dictionary Attack | Yes |
| PMKID Hash Dictionary Attack | Yes |
| Rouge Access Point | Partially |
| Evil Twin Attack | No |
| Handshake Capture En/Decryption | Yes |
| KRACK Exploit | Yes |
| ARP Spoofing | Partially |
| SSL Stripping | No |
| DNS Spoofing | No |
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kohlios, C.P.; Hayajneh, T. A Comprehensive Attack Flow Model and Security Analysis for Wi-Fi and WPA3. Electronics 2018, 7, 284. https://doi.org/10.3390/electronics7110284
Kohlios CP, Hayajneh T. A Comprehensive Attack Flow Model and Security Analysis for Wi-Fi and WPA3. Electronics. 2018; 7(11):284. https://doi.org/10.3390/electronics7110284
Chicago/Turabian StyleKohlios, Christopher P., and Thaier Hayajneh. 2018. "A Comprehensive Attack Flow Model and Security Analysis for Wi-Fi and WPA3" Electronics 7, no. 11: 284. https://doi.org/10.3390/electronics7110284
APA StyleKohlios, C. P., & Hayajneh, T. (2018). A Comprehensive Attack Flow Model and Security Analysis for Wi-Fi and WPA3. Electronics, 7(11), 284. https://doi.org/10.3390/electronics7110284






