Cryptanalysis of Two Conditional Privacy Preserving Authentication Schemes for Vehicular Ad Hoc Networks
Abstract
1. Introduction
- We show that Zhang’s IBV scheme [5] is vulnerable to impersonation attacks where any member of a VANET can easily obtain the private information of other members and generate and sign messages on their behalf. We discuss causes and propose general improvements to the scheme to mitigate this attack. We also show that the same scheme [5] is vulnerable to repudiation attacks where malicious users can send messages with false information using fake identities and escape retribution accordingly. This encourages them to send false information to suit their own purposes and easily escape accountability in case their messages are reported to a trusted authority. Finally, we point out the deficiencies in Tao’s [6] cryptanalysis of Zhang’s IBV scheme [5].
- We show that Xiong’s CLAS scheme [9] is vulnerable to bogus information attacks since partial private keys and pseudo-identities are not adequately verified and can be replaced by the sender of the message and still perform successful verification at the receiver’s end. We also show that the scheme is vulnerable to the same repudiation attack that afflicts Zhang’s scheme and point out a mistake in the batch verification equation.
2. VANET Security Requirements
2.1. Attacks on Availability
2.2. Attacks on Authentication
2.3. Attacks on Integrity
2.4. Attacks on Conditional Privacy
2.5. Attacks on Non-Repudiation
2.6. Attacks on Confidentiality
3. Related Work: IBV and CLAS Schemes
3.1. IBV Schemes
3.1.1. History of IBV
3.1.2. IBV in the Context of VANETs
3.1.3. Criticisms of C. Zhang’s Scheme and Improvements
3.2. CLAS Schemes
3.2.1. History of CLAS Schemes
3.2.2. CLAS in the Context of VANETs
4. Preliminaries
4.1. Elliptic Curves
4.2. Chinese Remainder Theorem
4.3. Network Model
- Trusted Authority (TA): This is also known as the Trusted Third Party (TTP) or the Central Authority (CA). It is generally known to comprise a Key Generation Center (KGC) and a Tracing Authority/Tracing Manager (TRA/TRM). IBV schemes tend to combine the role of the KGC and the TRM, while CLAS schemes necessarily posit them as distinct entities. The KGC is meant to generate public and private keys (or partial keys) for all members to enable digital signature verification, while the TRM is meant to generate verifiable pseudo-identities for each member to enable traceability in case of disputes. Schemes occasionally propose redundant TAs with access to the same data repository to avert single points of failure.
- Roadside Units (RSUs): They are connected to the TA with secure wired links and to vehicles with insecure wireless connections. Different schemes assume different levels of RSU trustworthiness, where the predominant assumption is that RSUs are honest but curious. The role of RSUs varies in different schemes, from being merely a gateway to relay messages from the TA to vehicles (and back) to being a group manager that issues signing and verification keys to members within its domain and managing localized groups.
- Vehicles: Vehicles are assumed to be untrustworthy. They are equipped with onboard units (OBUs) which contain a tamper proof device (TPD). It is assumed that all vehicles will be equipped with TPDs, but schemes diverge on the assumption of an ideal TPD (secure enough to store the master secret key of the system for self-authentication) or a realistic TPD (where only the secret key of the corresponding user is stored, and authentication is carried out elsewhere).
5. Zhang et al.’s Scheme
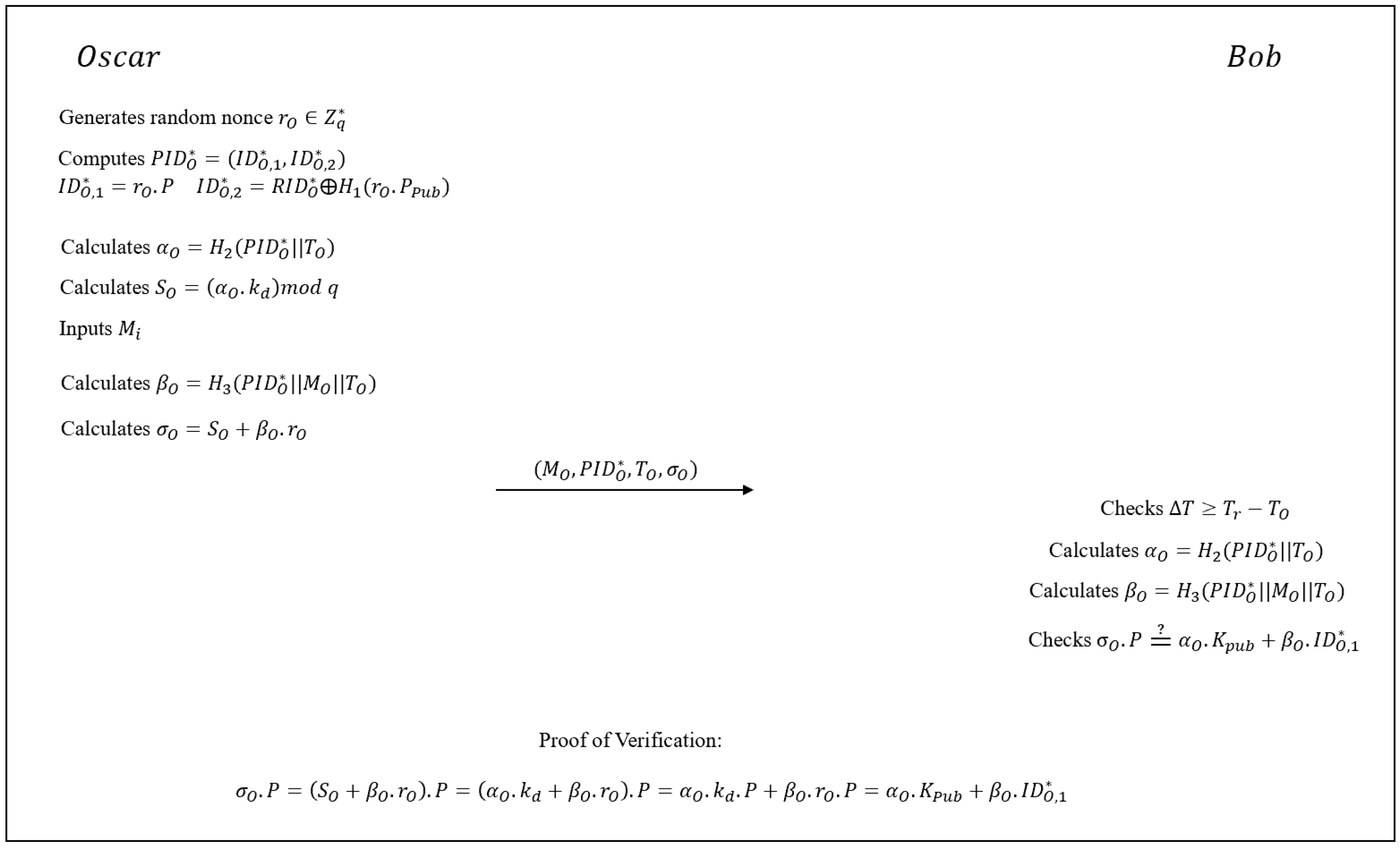
5.1. Description
5.2. Cryptanalysis
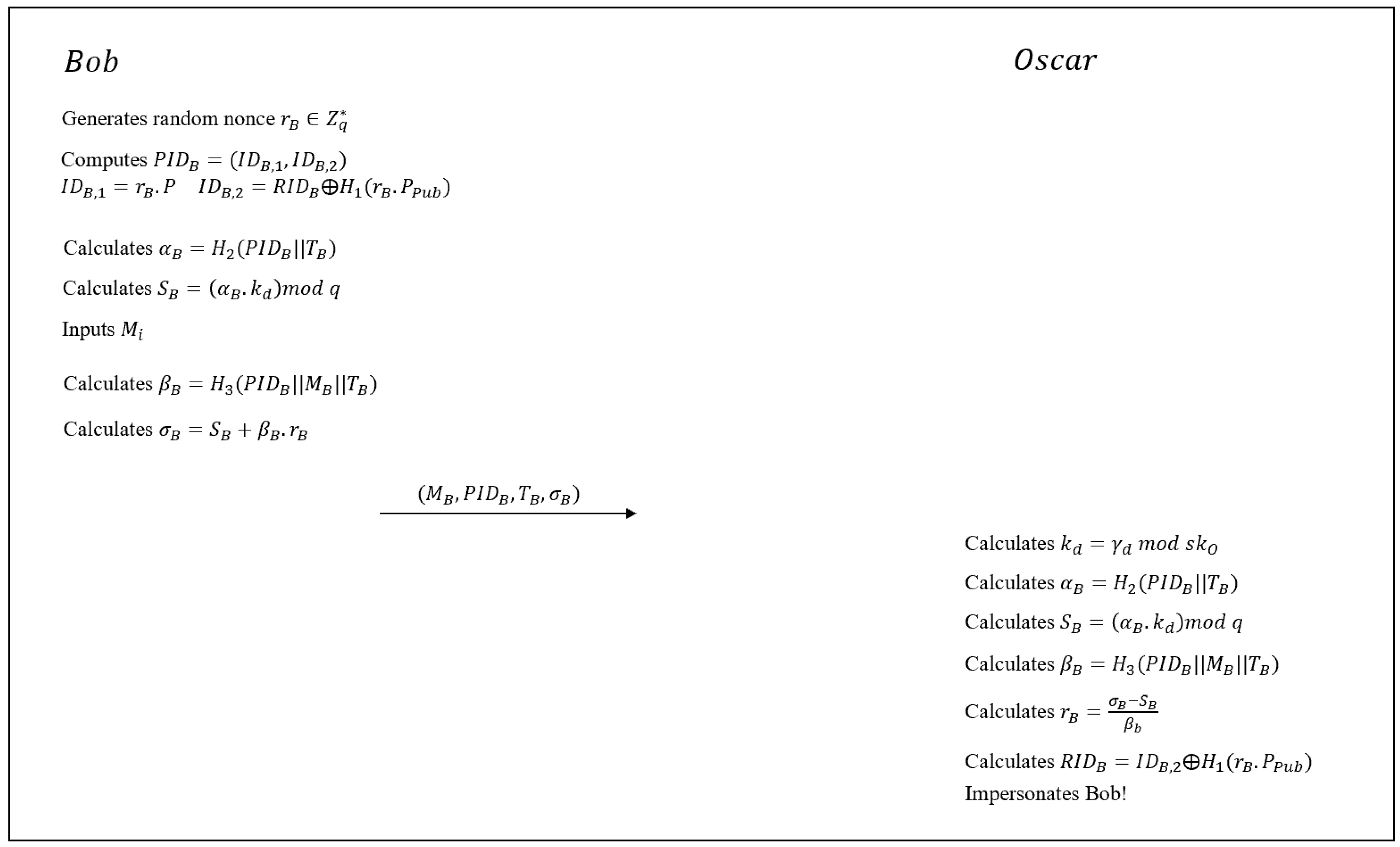
5.2.1. Impersonation Attack
5.2.2. Repudiation/Spoofing Attack
5.3. Causes and Countermeasures
5.3.1. Impersonation Attack
5.3.2. Repudiation Attack
5.4. A Commentary on the Cryptanalysis of This Scheme by Tao et al. [6]
6. Xiong et al.’s Scheme
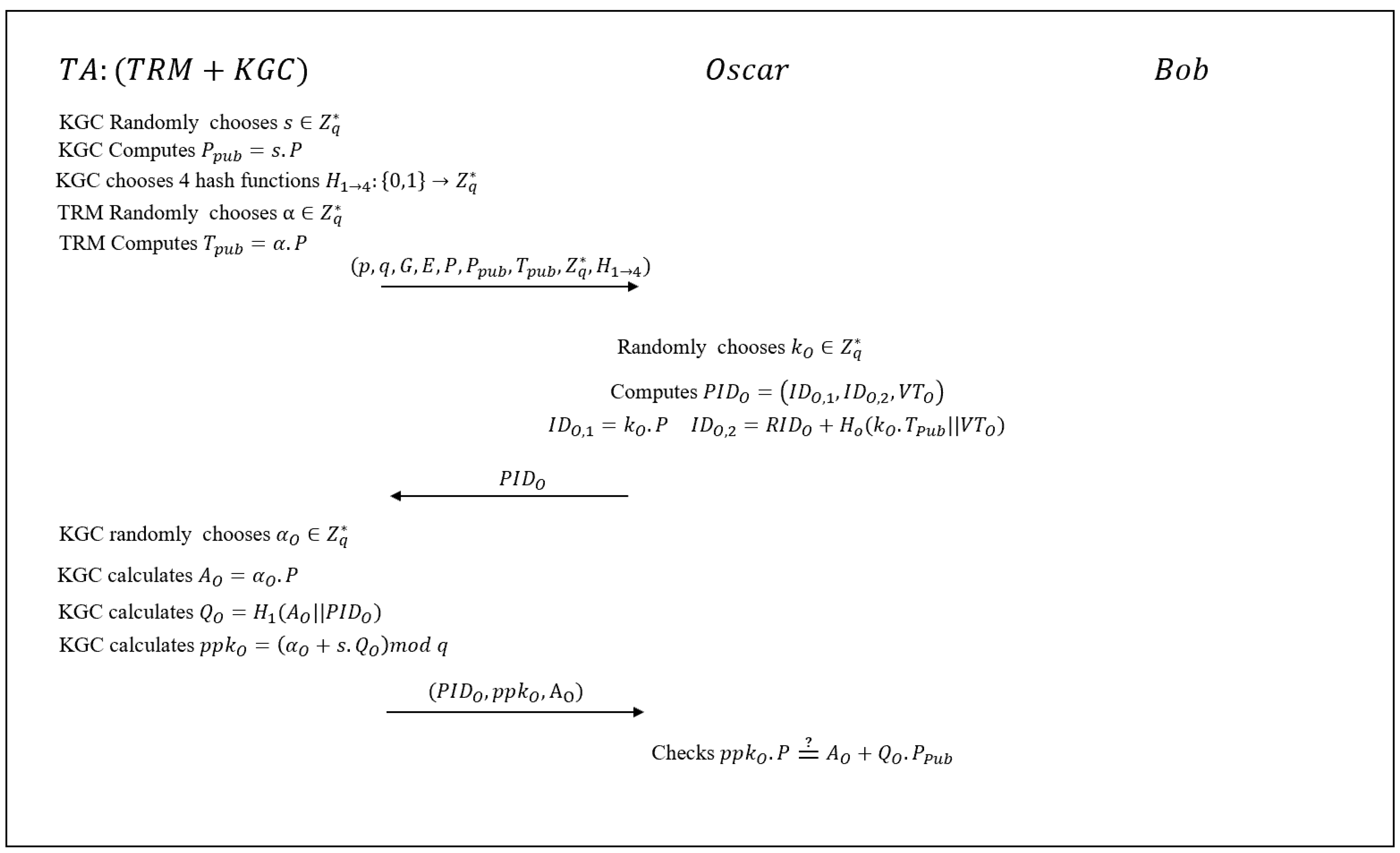
6.1. Description
6.2. Cryptanalysis
6.2.1. Bogus Information and Repudiation Attack
6.2.2. Other Flaws
6.3. Causes and Counter Measures
7. Conclusions and Future Work
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Hammi, B.; Monteuuis, J.-P.; Petit, J. PKIs in C-ITS: Security functions, architectures and projects: A survey. Veh. Commun. 2022, 38, 100531. [Google Scholar] [CrossRef]
- Chen, H.; Liu, J.; Wang, J.; Xun, Y. Towards secure intra-vehicle communications in 5G advanced and beyond: Vulnerabilities, attacks and countermeasures. Veh. Commun. 2022, 39, 100548. [Google Scholar] [CrossRef]
- Mannoni, V.; Berg, V.; Sesia, S.; Perraud, E. A comparison of the V2X communication systems: ITS-G5 and C-V2X. In Proceedings of the 2019 IEEE 89th Vehicular Technology Conference (VTC2019-Spring), Kuala Lumpur, Malaysia, 28 April–1 May 2019; pp. 1–5. [Google Scholar]
- Cominetti, E.L.; Silva, M.V.M.; Simplicio, M.A., Jr.; Patil, H.K.; Ricardini, J.E. Faster verification of V2X basic safety messages via Message Chaining. Veh. Commun. 2023, 44, 100662. [Google Scholar] [CrossRef]
- Zhang, J.; Cui, J.; Zhong, H.; Chen, Z.; Liu, L. PA-CRT: Chinese remainder theorem based conditional privacy-preserving authentication scheme in vehicular ad-hoc networks. IEEE Trans. Dependable Secur. Comput. 2019, 18, 722–735. [Google Scholar] [CrossRef]
- Tao, Q.; Ding, H.; Jiang, T.; Cui, X. B-DSPA: A Blockchain-based Dynamically Scalable Privacy-Preserving Authentication Scheme in Vehicular Ad-hoc Networks. IEEE Internet Things J. 2023, 11, 1385–1397. [Google Scholar] [CrossRef]
- Xiong, W.; Wang, R.; Wang, Y.; Zhou, F.; Luo, X. CPPA-D: Efficient conditional privacy-preserving authentication scheme with double-insurance in VANETs. IEEE Trans. Veh. Technol. 2021, 70, 3456–3468. [Google Scholar] [CrossRef]
- Shim, K.-A. Security Analysis of Conditional Privacy-Preserving Authentication Schemes for VANETs. IEEE Access 2023, 11, 33956–33963. [Google Scholar] [CrossRef]
- Xiong, W.; Wang, R.; Wang, Y.; Wei, Y.; Zhou, F.; Luo, X. Improved certificateless aggregate signature scheme against collusion attacks for vanets. IEEE Syst. J. 2022, 17, 1098–1109. [Google Scholar] [CrossRef]
- Raya, M.; Hubaux, J.-P. Securing vehicular ad hoc networks. J. Comput. Secur. 2007, 15, 39–68. [Google Scholar] [CrossRef]
- Chen, Y.; Yuan, J.; Zhang, Y. An improved password-authenticated key exchange protocol for VANET. Veh. Commun. 2021, 27, 100286. [Google Scholar] [CrossRef]
- Sharma, S.; Kaul, A. A survey on Intrusion Detection Systems and Honeypot based proactive security mechanisms in VANETs and VANET Cloud. Veh. Commun. 2018, 12, 138–164. [Google Scholar] [CrossRef]
- Gonçalves, F.; Ribeiro, B.; Gama, O.; Santos, A.; Costa, A.; Dias, B.; Macedo, J.; Nicolau, M.J. A systematic review on intelligent intrusion detection systems for VANETs. In Proceedings of the 2019 11th International Congress on Ultra Modern Telecommunications and Control Systems and Workshops (ICUMT), Dublin, Ireland, 28–30 October 2019; pp. 1–10. [Google Scholar]
- Bangui, H.; Buhnova, B. Recent advances in machine-learning driven intrusion detection in transportation: Survey. Procedia Comput. Sci. 2021, 184, 877–886. [Google Scholar] [CrossRef]
- Paar, C.; Pelzl, J. Understanding Cryptography: A Textbook for Students and Practitioners; Springer Science & Business Media: Berlin/Heidelberg, Germany, 2009. [Google Scholar]
- Raya, M.; Hubaux, J.-P. The security of vehicular ad hoc networks. In SASN ‘05: Proceedings of the 3rd ACM Workshop on Security of Ad Hoc and Sensor Networks; Association for Computing Machinery: New York, NY, USA, 2005; pp. 11–21. [Google Scholar]
- Noura, H.N.; Salman, O.; Couturier, R.; Chehab, A. LoRCA: Lightweight round block and stream cipher algorithms for IoV systems. Veh. Commun. 2022, 34, 100416. [Google Scholar] [CrossRef]
- Shamir, A. Identity-based cryptosystems and signature schemes. In Advances in Cryptology: Proceedings of CRYPTO 84 4; Springer: Berlin/Heidelberg, Germany, 1985; pp. 47–53. [Google Scholar]
- Boneh, D.; Franklin, M. Identity-based encryption from the Weil pairing. In Proceedings of Advances in Cryptology—CRYPTO 2001: 21st Annual International Cryptology Conference, Santa Barbara, CA, USA, 19–23 August 2001; pp. 213–229. [Google Scholar]
- Zhang, C.; Lu, R.; Lin, X.; Ho, P.-H.; Shen, X. An efficient identity-based batch verification scheme for vehicular sensor networks. In Proceedings of the IEEE INFOCOM 2008—The 27th Conference on Computer Communications, Phoenix, AZ, USA, 13–18 April 2008; pp. 246–250. [Google Scholar]
- Zhang, C.; Ho, P.-H.; Tapolcai, J. On batch verification with group testing for vehicular communications. Wirel. Netw. 2011, 17, 1851–1865. [Google Scholar] [CrossRef]
- Chim, T.W.; Yiu, S.-M.; Hui, L.C.; Li, V.O. SPECS: Secure and privacy enhancing communications schemes for VANETs. Ad Hoc Netw. 2011, 9, 189–203. [Google Scholar] [CrossRef]
- Shim, K.-A. CPAS: An efficient conditional privacy-preserving authentication scheme for vehicular sensor networks. IEEE Trans. Veh. Technol. 2012, 61, 1874–1883. [Google Scholar] [CrossRef]
- Lee, C.-C.; Lai, Y.-M. Toward a secure batch verification with group testing for VANET. Wirel. Netw. 2013, 19, 1441–1449. [Google Scholar] [CrossRef]
- Bayat, M.; Barmshoory, M.; Rahimi, M.; Aref, M.R. A secure authentication scheme for VANETs with batch verification. Wirel. Netw. 2015, 21, 1733–1743. [Google Scholar] [CrossRef]
- Tzeng, S.-F.; Horng, S.-J.; Li, T.; Wang, X.; Huang, P.-H.; Khan, M.K. Enhancing security and privacy for identity-based batch verification scheme in VANETs. IEEE Trans. Veh. Technol. 2015, 66, 3235–3248. [Google Scholar] [CrossRef]
- Ali, I.; Li, F. An efficient conditional privacy-preserving authentication scheme for Vehicle-To-Infrastructure communication in VANETs. Veh. Commun. 2020, 22, 100228. [Google Scholar] [CrossRef]
- Ogundoyin, S.O.; Kamil, I.A. An efficient authentication scheme with strong privacy preservation for fog-assisted vehicular ad hoc networks based on blockchain and neuro-fuzzy. Veh. Commun. 2021, 31, 100384. [Google Scholar] [CrossRef]
- Al-Riyami, S.S.; Paterson, K.G. Certificateless public key cryptography. In Advances in Cryptology—ASIACRYPT 2003; Springer: Berlin/Heidelberg, Germany, 2003; pp. 452–473. [Google Scholar]
- Zhong, H.; Han, S.; Cui, J.; Zhang, J.; Xu, Y. Privacy-preserving authentication scheme with full aggregation in VANET. Inf. Sci. 2019, 476, 211–221. [Google Scholar] [CrossRef]
- Mei, Q.; Xiong, H.; Chen, J.; Yang, M.; Kumari, S.; Khan, M.K. Efficient certificateless aggregate signature with conditional privacy preservation in IoV. IEEE Syst. J. 2020, 15, 245–256. [Google Scholar] [CrossRef]
- Qi, J.; Gao, T.; Deng, X.; Zhao, C. A pseudonym-based certificateless privacy-preserving authentication scheme for VANETs. Veh. Commun. 2022, 38, 100535. [Google Scholar] [CrossRef]
- Horng, S.-J.; Tzeng, S.-F.; Huang, P.-H.; Wang, X.; Li, T.; Khan, M.K. An efficient certificateless aggregate signature with conditional privacy-preserving for vehicular sensor networks. Inf. Sci. 2015, 317, 48–66. [Google Scholar] [CrossRef]
- Li, J.; Yuan, H.; Zhang, Y. Cryptanalysis and improvement of certificateless aggregate signature with conditional privacy-preserving for vehicular sensor networks. Cryptol. Eprint Arch. 2016. [Google Scholar]
- Zhao, Y.; Hou, Y.; Wang, L.; Kumari, S.; Khan, M.K.; Xiong, H. An efficient certificateless aggregate signature scheme for the Internet of Vehicles. Trans. Emerg. Telecommun. Technol. 2020, 31, e3708. [Google Scholar] [CrossRef]
- Ming, Y.; Shen, X. PCPA: A practical certificateless conditional privacy preserving authentication scheme for vehicular ad hoc networks. Sensors 2018, 18, 1573. [Google Scholar] [CrossRef]
- Cui, J.; Zhang, J.; Zhong, H.; Shi, R.; Xu, Y. An efficient certificateless aggregate signature without pairings for vehicular ad hoc networks. Inf. Sci. 2018, 451–452, 1–15. [Google Scholar] [CrossRef]
- Kamil, I.A.; Ogundoyin, S.O. An improved certificateless aggregate signature scheme without bilinear pairings for vehicular ad hoc networks. J. Inf. Secur. Appl. 2019, 44, 184–200. [Google Scholar] [CrossRef]
- Li, C.; Wu, G.; Xing, L.; Zhu, F.; Zhao, L. An efficient certificateless aggregate signature scheme designed for VANET. Comput. Mater. Contin. 2020, 63, 725–742. [Google Scholar]
- Malhi, A.K.; Batra, S. An efficient certificateless aggregate signature scheme for vehicular ad-hoc networks. Discret. Math. Theor. Comput. Sci. 2015, 17, 317–338. [Google Scholar] [CrossRef]
- Kumar, P.; Kumari, S.; Sharma, V.; Li, X.; Sangaiah, A.K.; Islam, S.H. Secure CLS and CL-AS schemes designed for VANETs. J. Supercomput. 2019, 75, 3076–3098. [Google Scholar] [CrossRef]
- Zhang, Y.; Deng, R.H.; Han, G.; Zheng, D. Secure smart health with privacy-aware aggregate authentication and access control in Internet of Things. J. Netw. Comput. Appl. 2018, 123, 89–100. [Google Scholar] [CrossRef]
- Xu, Z.; He, D.; Kumar, N.; Choo, K.-K.R. Efficient certificateless aggregate signature scheme for performing secure routing in VANETs. J. Secur. Commun. Netw. 2020, 2020, 5276813. [Google Scholar] [CrossRef]


| Notation | Term |
|---|---|
| CA | Central Authority |
| CRT | Chinese Remainder Theorem |
| C-ITS | Cooperative Intelligent Transportation Systems |
| CL | Certificateless (Schemes) |
| CLAS | Certificateless Aggregate Signature (Schemes) |
| CPPA | Conditional Privacy Preserving Authentication |
| DSRC | Dedicated Short Range Communications |
| EC(C) | Elliptic Curve (Cryptography) |
| ECDLP | Elliptic Curve Discrete Logarithm Problem |
| GS | Group Signature |
| IBC | Identity Based Cryptography |
| IBV | Identity Based Batch-Verification (Schemes) |
| KGC | Key Generation Center |
| MAC | Message Authentication Code |
| OBU | On Board Unit |
| PKI | Public Key Infrastructure |
| PID | Pseudo Identity |
| PWD | Password |
| RID | Real Identity |
| RSU | Roadside Unit |
| TA/TTP | Trusted Authority/Trusted Third Party |
| TPD | Tamper Proof Device |
| TRA/TRM | Tracing Authority/Tracing Manager |
| VANET | Vehicular Ad hoc Network |
| V2I | Vehicle-to-Infrastructure |
| V2V | Vehicle-to-Vehicle |
| V2X | Vehicle-to-Everything |
| Requirement | Description | Attacks | Protection |
|---|---|---|---|
| Availability | Timely arrival of critical information | Denial of service, spamming Blackhole, greyhole Malware | Frequency hopping Channel switching IDS |
| Authentication | Messages are sent by a legitimate user | Impersonation Sybil Wormhole, tunneling | Digital signatures MAC tags IDS |
| Integrity | Message contents have not been modified | Message/broadcast tampering Replay | Digital signatures MAC tags |
| Conditional Privacy | Only authorized entities have access to user identity | Location extraction attacks ID disclosure attacks | Pseudonyms Group signatures |
| Non-repudiation | Sender cannot deny having sent the message | Repudiation attacks | Public key cryptography |
| Confidentiality | Third party cannot extract meaningful information from any message | Eavesdropping Traffic analysis | Encryption |
| Phase | Scheme | Comments |
|---|---|---|
| Setup | TA chooses large prime , define | cyclic group of order |
| TA chooses large prime such that , define | cyclic group of order | |
| TA generates elliptic curve defined over finite field by the equation | and . We take point to be the generator of | |
| TA randomly chooses | TA’s secret key (for identity tracing) | |
| TA computes | generator of elliptic curve | |
| TA chooses 4 hash functions: | ||
| TA publishes params: ( | ||
| GroupKey computation | TA chooses from for vehicles | is the secret key of vehicle |
| TA calculates | ||
| TA calculates | ||
| TA calculates such that | ||
| TA calculates | ||
| TA calculates | ||
| TA chooses small random variable | the group key (or domain key) | |
| TA calculates | ||
| TA signs and lifetime using | TA’s secret key (for signing) | |
| TA computes | ||
| TA broadcasts: | ||
| Members compute group key as | Note: | |
| PID generation | Driver activates TPD using fingerprint | |
| TPD generates random nonce | ||
| TPD generates as , | Note: TA can compute: | |
| Signing | TPD obtains from broadcast | As mentioned in GK computation |
| TPD computes to obtain GK | ||
| TPD computes | Re-computable by verifier | |
| TPD computes | Re-computable by verifier (weakness) | |
| OBU inputs to be signed | message to be broadcasted | |
| TPD computes | Re-computable by verifier | |
| TPD computes | is only known to the signer | |
| TPD broadcasts | timestamp signature | |
| Verifying | Check freshness of such that | received time; predefined threshold (mitigates replay attacks) |
| Check (proof: LHS: → RHS) | ||
| Batch Verif. | Verifier received: , | |
| Check for freshness | For each message | |
| Generates random vector where such that is a small integer | Small exponent test | |
| Check (proof: LHS: ) | ||
| Phase | Scheme | Comments |
|---|---|---|
| Setup: TA = KGC + TRM | , defines | cyclic groups of order respectively |
| defined over finite field by the equation , | and . We take point to be the generator of | |
| KGC’s secret key | ||
| KGC computes | generator of elliptic curve | |
| TRM randomly chooses | TRM’s secret key | |
| TRM computes | ||
| PID Generation | pseudonym validity time Note: TRM can compute | |
| generates as: , | ||
| PPK Gen. | ||
| to securely | partial private key of vehicle | |
| checks: | ||
| USK Gen | randomly chooses | user secret key of vehicle |
| Re-computable by verifier | ||
| the public key of | ||
| Signing | randomly chooses | |
| computes | ||
| message | ||
| signature | ||
| sends: | ||
| Verifying | such that | Mitigates replay attacks |
| → RHS) | ||
| Agg. sign | , , , | |
| for freshness | ||
| randomly chooses | here is the receiver/verifier | |
| computes | (see Section 6.2.2) | |
| computes | ||
| computes | ||
| Batch Verify | computes | pair |
| computes | ||
| checks if (proof: LHS: → RHS) | ||
| computes (proof: LHS →RHS) |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kabil, A.M.; Aslan, H.; Azer, M. Cryptanalysis of Two Conditional Privacy Preserving Authentication Schemes for Vehicular Ad Hoc Networks. Cryptography 2024, 8, 4. https://doi.org/10.3390/cryptography8010004
Kabil AM, Aslan H, Azer M. Cryptanalysis of Two Conditional Privacy Preserving Authentication Schemes for Vehicular Ad Hoc Networks. Cryptography. 2024; 8(1):4. https://doi.org/10.3390/cryptography8010004
Chicago/Turabian StyleKabil, Ahmad Mohamad, Heba Aslan, and Marianne Azer. 2024. "Cryptanalysis of Two Conditional Privacy Preserving Authentication Schemes for Vehicular Ad Hoc Networks" Cryptography 8, no. 1: 4. https://doi.org/10.3390/cryptography8010004
APA StyleKabil, A. M., Aslan, H., & Azer, M. (2024). Cryptanalysis of Two Conditional Privacy Preserving Authentication Schemes for Vehicular Ad Hoc Networks. Cryptography, 8(1), 4. https://doi.org/10.3390/cryptography8010004









