A Fractional SAIDR Model in the Frame of Atangana–Baleanu Derivative
Abstract
:1. Introduction
2. Some Preliminaries
3. Existence of a Unique Solution
4. Stability Analysis by Fixed Point Theory
Stability Analysis of Iteration Method
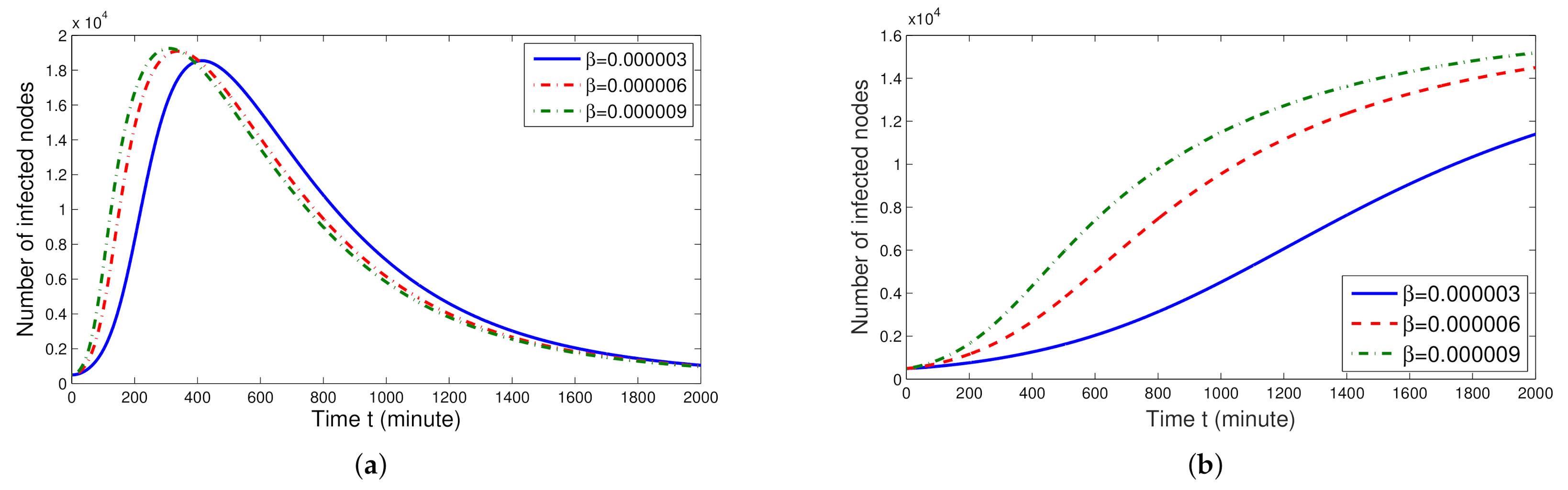
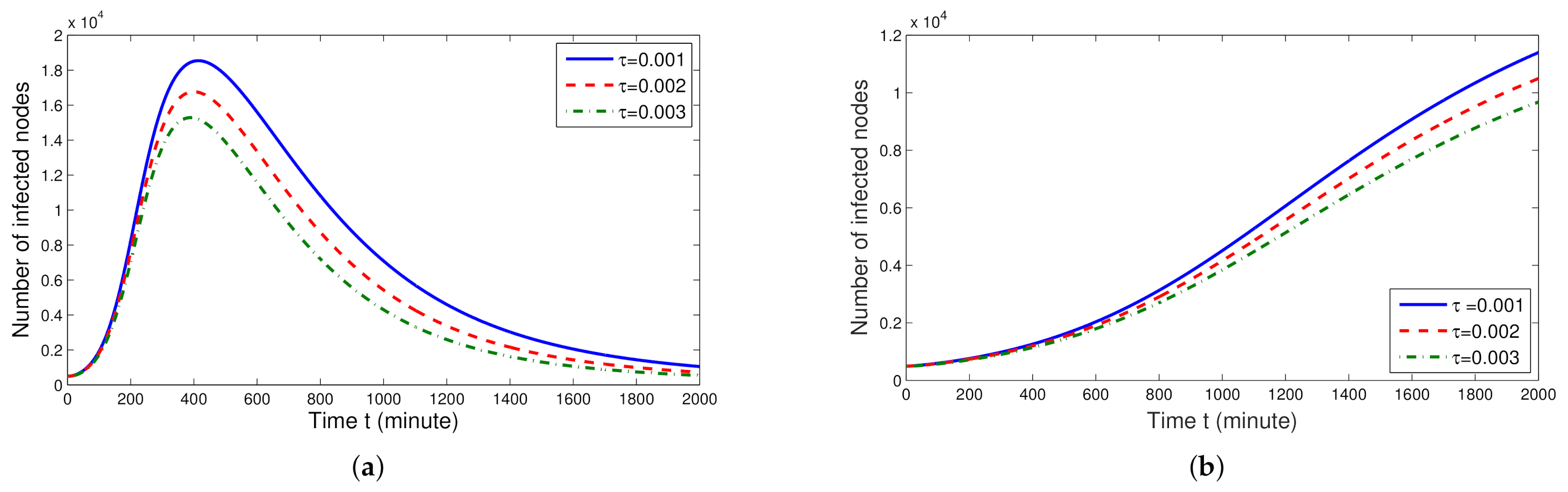
5. Numerical Results
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Abraham, S.; Smith, I.C. An overview of social engineering malware: Trends, tactics, and implications. Technol. Soc. 2010, 32, 183–196. [Google Scholar] [CrossRef]
- CNCENT/CC, CCKUN-A Mobile Malware Spreading in Social Relationship Networks by SMS. 2013. Available online: https://www.cert.org.cn/publish/main/8/2013/20130924145326642925406/20130924145326642925406_.html (accessed on 10 February 2021).
- Computer World, Android SMS Worm Selfmite Is Back, More Aggressive Than Ever. 2013. Available online: http://www.computerworld.com/article/2824619/android-sms-worm-selfmite-is-back-more-aggressive-than-ever.html (accessed on 10 February 2021).
- CNCENT/CC. The Bulletin about the Outbreak and Response of the xxShenQi Malware. 2014. Available online: https://www.cert.org.cn/publish/main/12/2014/20140803174220396365334/20140803174220396365334_.html (accessed on 10 February 2021).
- Podlubny, I. Fractional Differential Equations: An Introduction to Fractional Derivatives to Methods of Their Solution and Some of Their Applications; Academic Press: San Diego, CA, USA, 1999. [Google Scholar]
- Caputo, M.; Mainardi, F. A new dissipation model based on memory mechanism. Pure Appl. Geophys. 1971, 91, 134–147. [Google Scholar] [CrossRef]
- Caputo, M.; Fabrizio, F. A new definition of fractional derivative without singular kerne. Prog. Fract. Differ. Appl. 2015, 1, 73–85. [Google Scholar]
- Koca, I. Analysis of rubella disease model with non-local and non-singular fractional derivatives. Int. J. Optim. Control Theor. Appl. 2018, 8, 17–25. [Google Scholar] [CrossRef] [Green Version]
- Jajarmi, A.; Baleanu, D. A new fractional analysis on the interaction of HIV with CD4+ T-cells. Chaos Solitons Fractals 2018, 113, 221–229. [Google Scholar] [CrossRef]
- Uçar, S.; Özdemir, N.; Koca, I.; Altun, E. Novel analysis of the fractional glucose insulin regulatory system with non-singular kernel derivative. Eur. Phys. J. Plus 2020, 135, 414. [Google Scholar] [CrossRef]
- Özdemir, N.; Agrawal, O.P.; İskender, B.B.; Karadeniz, D. Fractional optimal control of a 2-dimensional distributed system using eigenfunctions. Nonlinear Dyn. 2009, 55, 251–260. [Google Scholar] [CrossRef]
- Baleanu, D.; Fernandez, A.; Akgül, A. On a fractional operator combining proportional and classical differintegrals. Mathematics 2020, 8, 13. [Google Scholar] [CrossRef] [Green Version]
- Uçar, E.; Özdemir, N.; Altun, E. Fractional order model of immune cells influenced by cancer cells. Math. Model. Nat. 2019, 14, 12. [Google Scholar]
- Evirgen, F.; Özdemir, N. Multistage adomian decomposition method for solving NLP problems over a nonlinear fractional dynamical system. J. Comput. Nonlinear Dyn. 2011, 6. [Google Scholar] [CrossRef]
- Evirgen, F. Conformable Fractional Gradient Based Dynamic System for Constrained Optimization Problem. Acta Phys. Pol. A 2017, 132, 1066–1069. [Google Scholar] [CrossRef]
- Uçar, E.; Özdemir, N. A fractional model of cancer-immune system with Caputo and Caputo–Fabrizio derivatives. Eur. Phys. J. Plus 2021, 136, 1–17. [Google Scholar] [CrossRef] [PubMed]
- Aljoudi, S.; Ahmad, B.; Alsaedi, A. Existence and uniqueness results for a coupled system of Caputo-Hadamard fractional differential equations with nonlocal Hadamard type integral boundary conditions. Fractal Fract. 2020, 4, 15. [Google Scholar] [CrossRef] [Green Version]
- Baleanu, D.; Hakimeh, M.; Shahram, R. A fractional differential equation model for the COVID-19 transmission by using the Caputo–Fabrizio derivative. Adv. Differ. Eq. 2020, 2020, 299. [Google Scholar] [CrossRef] [PubMed]
- Aliyu, A.I.; Inc, M.; Yusuf, A.; Baleanu, D. A fractional model of vertical transmission and cure of vector-borne diseases pertaining to the Atangana–Baleanu fractional derivatives. Chaos Solitons Fractals 2018, 116, 268–277. [Google Scholar] [CrossRef]
- Uçar, S. Analysis of a basic SEIRA model with Atangana-Baleanu derivative. AIMS Math. 2020, 5, 1411–1424. [Google Scholar] [CrossRef]
- Kumar, D.; Singh, J. New aspects of fractional epidemiological model for computer viruses with Mittag–Leffler law. In Mathematical Modelling in Health, Social and Applied Sciences; Dutta, H., Ed.; Springer: Singapore, 2020; pp. 283–301. [Google Scholar]
- Atangana, A.; Baleanu, D. New fractional derivatives with nonlocal and non-singular kernel: Theory and application to heat transfer model. Therm. Sci. 2016, 20, 763–769. [Google Scholar] [CrossRef] [Green Version]
- Fernandez, A.; Baleanu, D.; Srivastava, H.M. Series representations for fractional-calculus operators involving generalised Mittag-Leffler functions. Commun. Nonlinear Sci. Numer. 2019, 67, 517–527. [Google Scholar] [CrossRef] [Green Version]
- Baleanu, D.; Jajarmi, A.; Hajipour, M. On the nonlinear dynamical systems within the generalized fractional derivatives with Mittag-Leffler kernel. Nonlinear Dyn. 2018, 94, 397–414. [Google Scholar] [CrossRef]
- Qureshi, S.; Yusuf, A.; Shaikh, A.A.; Inc, M.; Baleanu, D. Fractional modeling of blood ethanol concentration system with real data application. Chaos 2019, 29, 131–143. [Google Scholar] [CrossRef]
- Uçar, S.; Uçar, E.; Özdemir, N.; Hammouch, Z. Mathematical analysis and numerical simulation for a smoking model with Atangana-Baleanu derivative. Chaos Solitons Fractals 2019, 118, 300–306. [Google Scholar] [CrossRef]
- Yavuz, M.; Özdemir, N.; Başkonuş, H.M. Solutions of partial differential equations using the fractional operator involving Mittag-Leffler kernel. Eur. Phys. J. Plus 2018, 133, 1–11. [Google Scholar] [CrossRef]
- Fernandez, A.; Husain, I. Modified Mittag-Leffler functions with applications in complex formulae for fractional calculus. Fractal Fract. 2020, 4, 15. [Google Scholar] [CrossRef]
- Xiao, X.; Fu, P.; Hu, G.; Sangiah, A.K.; Zheng, H.; Jiang, Y. SAIDR: A new dynamic model for SMS-based worm propagation in mobile networks. IEEE Access 2017, 5, 9935–9943. [Google Scholar] [CrossRef]
- Baleanu, D.; Fernandez, A. On some new properties of fractional derivatives with Mittag-Leffler kernel. Commun. Nonlinear Sci. Numer. Simul. 2018, 59, 444–462. [Google Scholar] [CrossRef] [Green Version]
- Gómez-Aguilar, J.F.; Rosales-García, J.J.; Bernal-Alvarado, J.J. Fractional mechanical oscillators. Rev. Mex. FíSica 2012, 58, 348–352. [Google Scholar]
- Qing, Y.; Rhoades, B.E. T-stability of Picard iteration in metric spaces. Fixed Point Theory Appl. 2008, 2008. [Google Scholar] [CrossRef] [Green Version]
- Mekkaoui, T.; Atangana, A. New numerical approximation of fractional derivative with non-local and non-singular kernel: Application to chaotic models. Eur. Phys. J. Plus 2017, 132, 1–16. [Google Scholar]

Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Uçar, E.; Uçar, S.; Evirgen, F.; Özdemir, N. A Fractional SAIDR Model in the Frame of Atangana–Baleanu Derivative. Fractal Fract. 2021, 5, 32. https://doi.org/10.3390/fractalfract5020032
Uçar E, Uçar S, Evirgen F, Özdemir N. A Fractional SAIDR Model in the Frame of Atangana–Baleanu Derivative. Fractal and Fractional. 2021; 5(2):32. https://doi.org/10.3390/fractalfract5020032
Chicago/Turabian StyleUçar, Esmehan, Sümeyra Uçar, Fırat Evirgen, and Necati Özdemir. 2021. "A Fractional SAIDR Model in the Frame of Atangana–Baleanu Derivative" Fractal and Fractional 5, no. 2: 32. https://doi.org/10.3390/fractalfract5020032





