On Global Quantum Communication Networking
Abstract
:1. Introduction
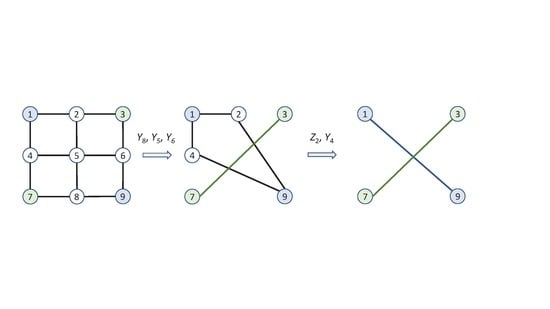
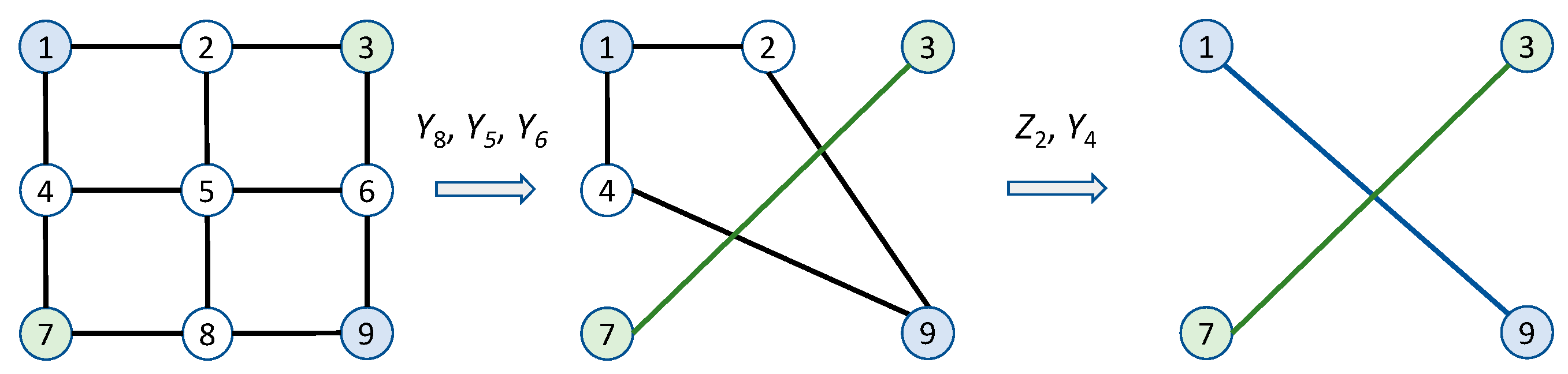
2. Proposed Cluster States-Based Quantum Communications Networks
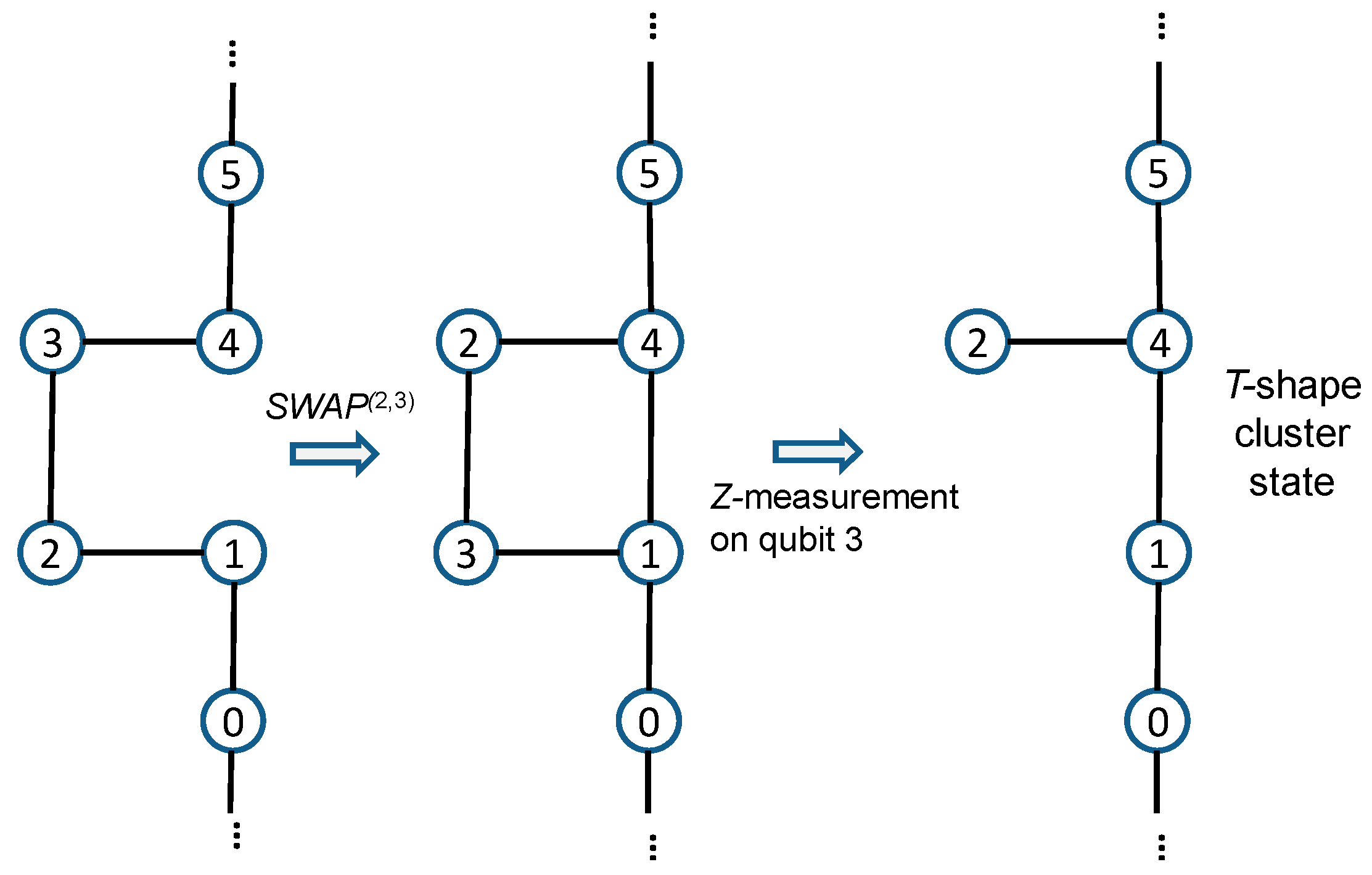
3. Extending the Distance between Nodes in QCN
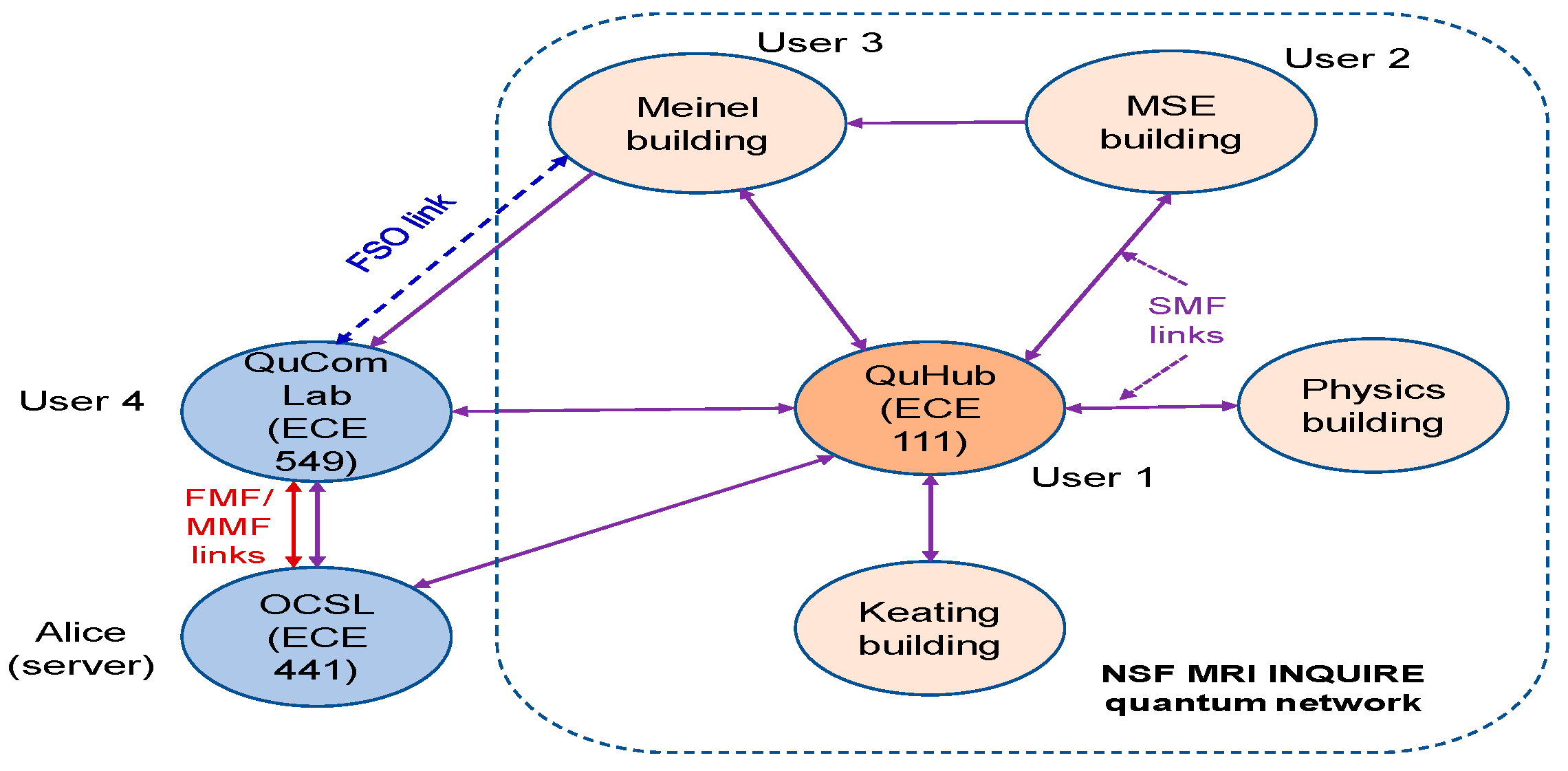
4. QCN under Development
5. Concluding Remarks
Funding
Conflicts of Interest
References
- Djordjevic, I.B. Physical-Layer Security and Quantum Key Distribution; Springer Nature Switzerland: Cham, Switzerland, 2019. [Google Scholar]
- Pljonkin, A.P. Features of the Photon Pulse Detection Algorithm in the Quantum Key Distribution System. In Proceedings of the 2017 International Conference on Cryptography, Security and Privacy (ICCSP ’17), Wuhan, China, 17–19 March 2017; Association for Computing Machinery: New York, NY, USA, 2017; pp. 81–84. [Google Scholar] [CrossRef] [Green Version]
- Pljonkin, A.P. Vulnerability of the synchronization process in the quantum key distribution system. Int. J. Cloud Appl. Comput. 2019, 9, 4. [Google Scholar] [CrossRef] [Green Version]
- Duan, L.-M.; Lukin, M.; Cirac, J.I.; Zoller, P. Long-distance quantum communication with atomic ensembles and linear optics. Nature 2001, 414, 413–418. [Google Scholar] [CrossRef] [Green Version]
- Qiu, J. Quantum communications leap out of the lab. Nature 2014, 508, 441–442. [Google Scholar] [CrossRef] [Green Version]
- Lo, H.-K.; Curty, M.; Qi, B. Measurement-device-independent quantum key distribution. Phys. Rev. Lett. 2012, 108, 130503. [Google Scholar] [CrossRef] [Green Version]
- Lucamarini, M.; Yuan, Z.L.; Dynes, J.F.; Shields, A.J. Overcoming the rate–distance limit of quantum key distribution without quantum repeaters. Nature 2018, 557, 400–403. [Google Scholar] [CrossRef]
- Fossier, S.; Diamanti, E.; Debuisschert, T.; Tualle-Brouri, R.; Grangier, P. Improvement of continuous-variable quantum key distribution systems by using optical preamplifiers. J. Phys. B 2009, 42, 114014. [Google Scholar] [CrossRef] [Green Version]
- Qu, Z.; Djordjevic, I.B. Four-dimensionally multiplexed eight-state continuous-variable quantum key distribution over turbulent channels. IEEE Photonics J. 2017, 9, 7600408. [Google Scholar] [CrossRef]
- Ralph, T.C. Continuous variable quantum cryptography. Phys. Rev. A 1999, 61, 010303. [Google Scholar] [CrossRef] [Green Version]
- Djordjevic, I.B. On the Discretized Gaussian Modulation (DGM)-based Continuous Variable-QKD. IEEE Access 2019, 7, 65342–65346. [Google Scholar] [CrossRef]
- Djordjevic, I.B. Optimized-Eight-State CV-QKD Protocol Outperforming Gaussian Modulation Based Protocols. IEEE Photonics J. 2019, 11, 4500610. [Google Scholar] [CrossRef]
- Djordjevic, I.B. Hybrid QKD Protocol Outperforming both DV- and CV-QKD Protocols. IEEE Photonics J. 2020, 12, 7600108. [Google Scholar] [CrossRef]
- Bernstein, D.J.; Buchmann, J.; Dahmen, E. Post-Quantum Cryptography; Springer: Berlin, Germany, 2009. [Google Scholar]
- Elliott, C.; Colvin, A.; Pearson, D.; Pikalo, O.; Schlafer, J.; Yeh, H. Current status of the DARPA quantum network (Invited Paper). In Proceedings of the SPIE 5815, Quantum Information and Computation III, Defense and Security, Orlando, FL, USA, 25 May 2005. [Google Scholar]
- Sasaki, M.; Fujiwara, M.; Ishizuka, H.; Klaus, W.; Wakui, K.; Takeoka, M.; Miki, S.; Yamashita, T.; Wang, Z.; Tanaka, A.; et al. Field test of quantum key distribution in the Tokyo QKD Network. Opt. Express 2011, 19, 10387–10409. [Google Scholar] [CrossRef] [PubMed]
- Alléaume, R.; Branciard, C.; Bouda, J.; Debuisschert, T.; Dianati, M.; Gisin, N.; Godfrey, M.; Grangier, P.; Länger, T.; Lütkenhaus, N.; et al. Using quantum key distribution for cryptographic purposes. J. Theor. Comput. Sci. 2014, 560, 62–81. [Google Scholar] [CrossRef]
- Nagayama, S.; Van Meter, R. Internet-Draft: IKE for IPsec with QKD. 2009. Available online: https://tools.ietf.org/html/draft-nagayama-ipsecme-ipsec-with-qkd-01 (accessed on 28 July 2020).
- Mink, A.; Frankel, S.; Perlner, R. Quantum Key Distribution (QKD) and Commodity Security Protocols: Introduction and Integration. Intern. J. Netw. Secur. Appl. 2009, 1, 101–112. [Google Scholar]
- Yin, J.; Cao, Y.; Li, Y.H.; Liao, S.K.; Zhang, L.; Ren, J.G.; Cai, W.Q.; Liu, W.Y.; Li, B.; Dai, H.; et al. Satellite-based entanglement distribution over 1200 kilometers. Science 2017, 356, 1140–1144. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Dequal, D.; Vallone, G.; Bacco, D.; Gaiarin, S.; Luceri, V.; Bianco, G.; Villoresi, P. Experimental single-photon exchange along a space link of 7000 km. Phys. Rev. A 2016, 93, 010301. [Google Scholar] [CrossRef] [Green Version]
- Briegel, H.J. Cluster States. In Compendium of Quantum Physics; Greenberger, D., Hentschel, K., Weinert, F., Eds.; Springer: Berlin/Heidelberg, Germany, 2009; pp. 96–105. [Google Scholar]
- Gilbert, G.; Hamrick, M.; Weinstein, Y.S. Efficient construction of photonic quantum-computational clusters. Phys. Rev. A 2006, 73, 064303. [Google Scholar] [CrossRef] [Green Version]
- Baldi, M.; Bianchi, M.; Chiaraluce, F. Security and complexity of the McEliece cryptosystem based on QC LDPC codes. IET Inf. Secur. 2013, 7, 212–220. [Google Scholar] [CrossRef] [Green Version]
- Sun, X.; Zou, D.; Qu, Z.; Djordjevic, I.B. Run-time reconfigurable adaptive LDPC coding for optical channels. Opt. Express 2018, 26, 29319–29329. [Google Scholar] [CrossRef]
- Ma, X.; Zeng, P.; Zhou, H. Phase-matching quantum key distribution. Phys. Rev. X 2018, 8, 031043. [Google Scholar] [CrossRef] [Green Version]
- Lo, H.-K.; Ma, X.; Chen, K. Decoy state quantum key distribution. Phys. Rev. Lett. 2005, 94, 230504. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Tamura, Y.; Sakuma, H.; Morita, K.; Suzuki, M.; Yamamoto, Y.; Shimada, K.; Honma, Y.; Sohma, K.; Fujii, T.; Hasegawa, T.; et al. The First 0.14-dB/km loss optical fiber and its impact on submarine transmission. J. Lightw. Technol. 2018, 36, 44–49. [Google Scholar] [CrossRef]
- Pan, Z.; Seshadreesan, K.P.; Clark, W.; Adcock, M.R.; Djordjevic, I.B.; Shapiro, J.H.; Guha, S. Secret Key Distillation over a Pure Loss Quantum Wiretap Channel under Restricted Eavesdropping. In Proceedings of the 2019 IEEE International Symposium on Information Theory (ISIT 2019), Paris, France, 7–12 July 2019; pp. 3032–3036. [Google Scholar]
- Pan, Z.; Djordjevic, I.B. Security of Satellite-Based CV-QKD under Realistic Assumptions. In Proceedings of the 22nd International Conference on Transparent Optical Networks ICTON 2020, Bari, Italy, 19–23 July 2020. [Google Scholar]
- Wang, T.-L.; Gariano, J.; Djordjevic, I.B. Employing Bessel-Gaussian Beams to Improve Physical-Layer Security in Free-Space Optical Communications. IEEE Photonics J. 2018, 10, 7907113. [Google Scholar] [CrossRef]
- Wang, T.-L.; Djordjevic, I.B.; Nagel, J. Laser Beam Propagation Effects on Secure Key Rates for Satellite-to-Ground Discrete Modulation CV-QKD. Appl. Opt. 2019, 58, 8061–8068. [Google Scholar] [CrossRef]




© 2020 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Djordjevic, I.B. On Global Quantum Communication Networking. Entropy 2020, 22, 831. https://doi.org/10.3390/e22080831
Djordjevic IB. On Global Quantum Communication Networking. Entropy. 2020; 22(8):831. https://doi.org/10.3390/e22080831
Chicago/Turabian StyleDjordjevic, Ivan B. 2020. "On Global Quantum Communication Networking" Entropy 22, no. 8: 831. https://doi.org/10.3390/e22080831