Percolation Theories for Quantum Networks
Abstract
1. Introduction
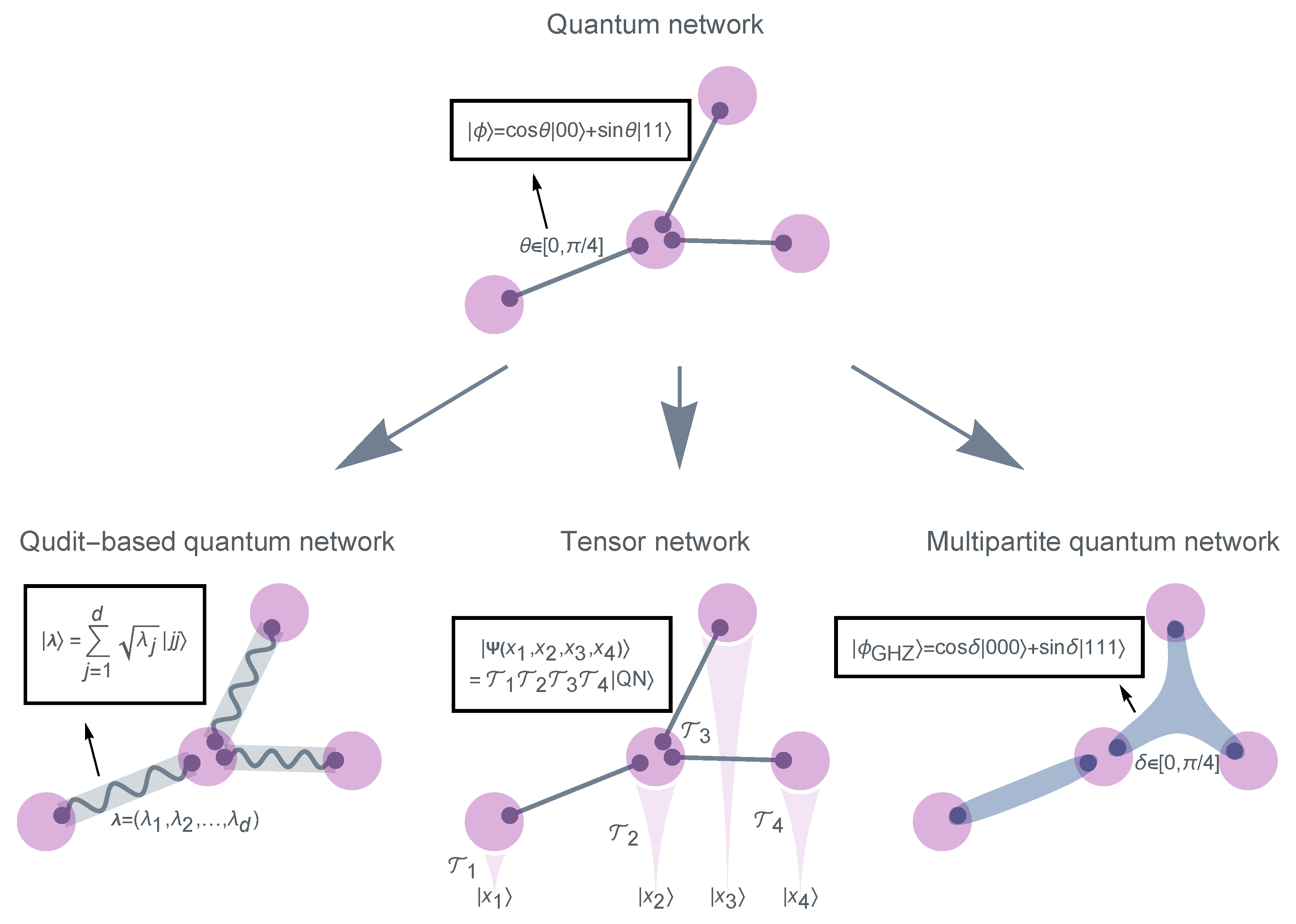
2. Quantum Networks (QN)
- 1.
- Each node (purple) comprises a collection of qubits (gray dots) that are entangled with qubits belonging to other nodes.
- 2.
- Each link (gray line) represents a bipartite entangled pure state connecting the two qubits at its endpoints.
- 3.
- A weight is assigned to each link to characterize the degree of the link’s entanglement.
2.1. Qudit-Based Quantum Networks
2.2. Quantum Networks Are the Basis of Tensor Networks
2.3. Multipartite Quantum Networks
3. Percolation of Complex Network
3.1. Percolation of Single-Layer Networks
3.2. Percolation of Networks of Networks
3.3. Percolation of Hypergraphs
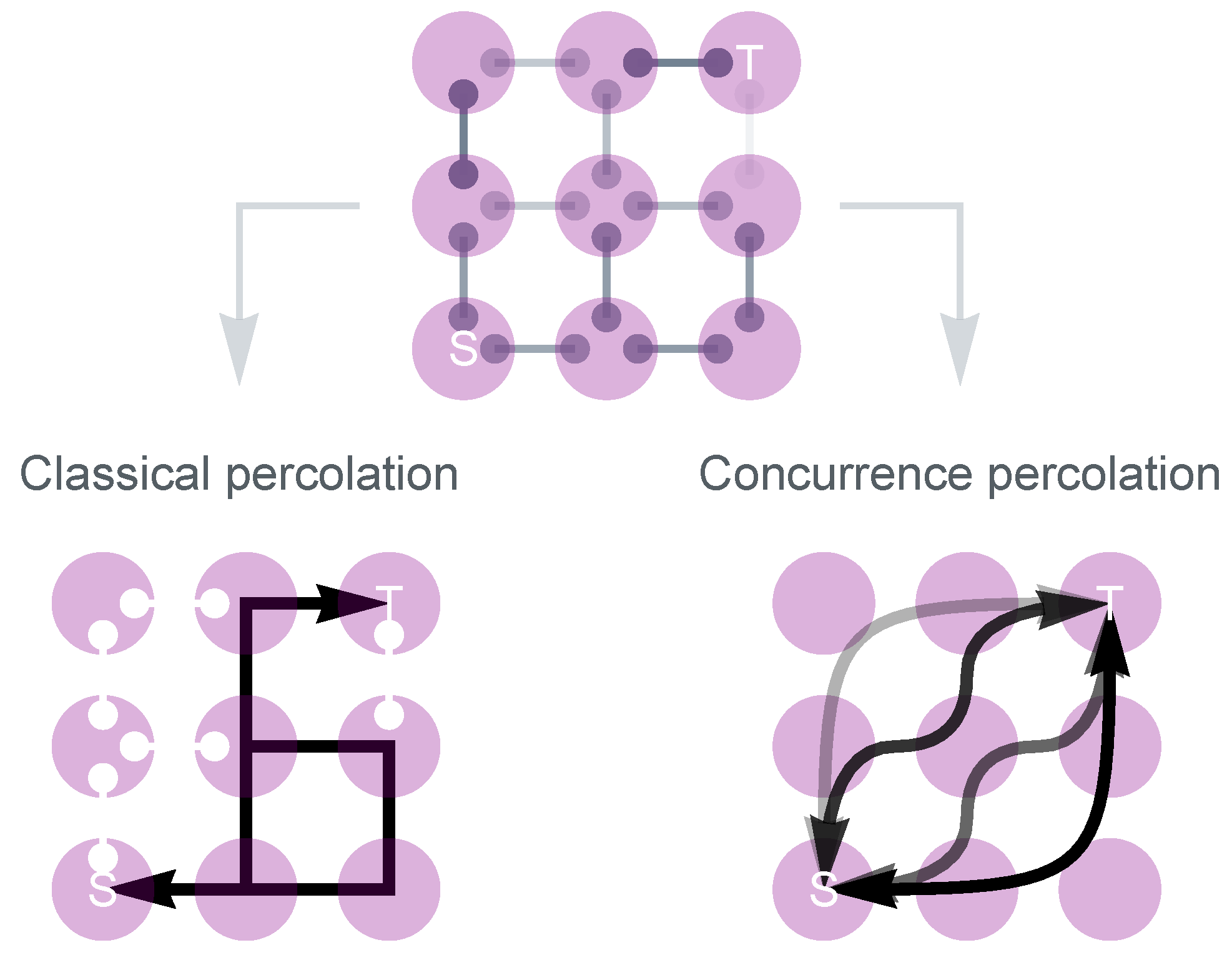
4. Classical Percolation in Quantum Networks
4.1. Classical Entanglement Percolation (CEP)
4.2. Quantum Entanglement Percolation (QEP)
5. Concurrence Percolation in Quantum Networks
5.1. No Need to Establish Singlets
5.2. Deterministic Entanglement Transmission (DET)
5.3. Concurrence Percolation Theory
5.4. Results
| [Unit: ] | Bethe Lattice (Degree k) | Square | Honeycomb | Triangular |
|---|---|---|---|---|
| CEP [10] | ||||
| QEP [10,148,160] | ||||
| QEP-GHZ [157] | ||||
| Concurrence [40] |
6. Algorithms
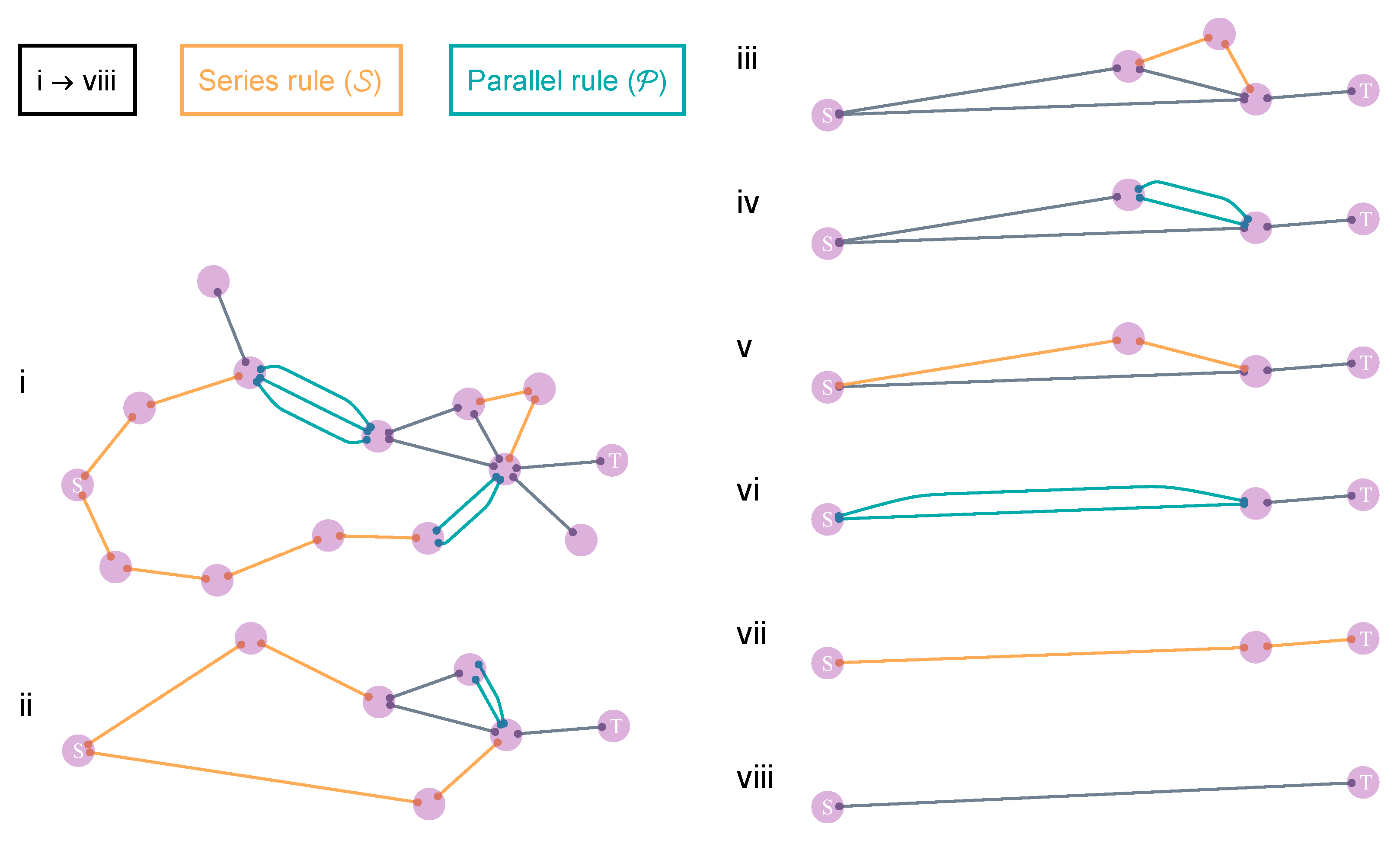
6.1. Identification of Series–Parallel Networks
6.2. Star-Mesh Transform
6.3. Fast Numerical Approximation for Concurrence Percolation
6.3.1. Parallel Approximation
6.3.2. Sm Approximation
6.3.3. Results
7. Discussion and Conclusions
- Optimality. Does there exist an optimal scheme for entanglement transmission? In the context of classical percolation, both classical entanglement percolation (CEP) and quantum entanglement percolation (QEP) fall short of yielding the optimal singlet conversion probability, especially as network size scales up [10]. The deterministic entanglement transmission (DET) [149], on the other hand, focuses on improving not the singlet conversion probability but the entanglement that can be deterministically obtained. It is found that the DET optimizes the average concurrence on either series (Figure 8a) or parallel topologies (Figure 8b), meaning that even when we relax the requirement of determinacy and consider the average entanglement of general probabilistic outcomes, the DET results remain the optimal on series or parallel topologies [149]. However, this result does not generalize to general series–parallel topologies (Figure 8e), where DET may not always offer the optimal average concurrence. This prompts us to ask how effective the DET actually is across various QN topologies. Answering this question could substantially deepen our comprehension of the maximum entanglement capacity of QN.
- Universality. As a statistical physics theory, the concurrence percolation also exhibits a second-order phase transition near the threshold , similar to classical percolation near . So, what can be said about the universality of this phase transition? It is found that the thermal critical exponent remains the same on different 2D lattices (square versus honeycomb versus triangular), suggesting that universality is likely at play near the critical threshold. Yet, the current definition of percolation based on connectivity rules (Table 2) does not clearly define an order parameter [40]. This lack of an order parameter hints at a missing degree of freedom in the connectivity-based model. This omission makes it challenging to determine other critical exponents besides (or its dynamic counterpart, ). Additionally, the existing data on (or ) do not allow us to distinguish between the universality classes of concurrence percolation and classical percolation [40]. Thus, an open question remains: are concurrence percolation and classical percolation simply two facets of a single underlying statistical theory if we overlook short-range details, or are they genuinely distinct theories at a macroscopic level?
- Experimental implementation. One of the greatest challenges of quantum information experiments is to achieve high-efficiency multi-body operations. For instance, two-body quantum gates like CNOT are considerably more challenging and less efficient to implement compared to single-body gates such as the rotation gates RX, RY, and RZ. In fact, the number of two-body gates often serves as a benchmark for gauging the computational complexity of quantum algorithms. Interestingly, a practical QN offers an easier path to scalability compared to universal quantum computers. This is since in a QN, only local operations are allowed on qubits across different nodes. This eliminates the need for complex gates like CNOT between qubits from different nodes. This design constraint substantially simplifies QN implementation and boosts its scalability. Recently, the experimental feasibility of the series/parallel rules of the DET scheme (Table 3) was also demonstrated on the IBM quantum computation platform Qiskit [184]. The series and parallel rules typically perform with fidelity rates of and , respectively [149]. These rates are expected to improve, given ongoing advancements in two-qubit gate fidelity [185,186]. Compared to the CEP/QEP schemes, the DET scheme has its advantages and drawbacks. On the upside, the DET inputs/outputs are only partially entangled, which generally makes them easier to produce and results in higher fidelity. On the flip side, circuit parameters are input-dependent, requiring precise initial state estimations through techniques like heralding [32] or tomography [187] before deployment. This brings us to a crucial question: to what extent can we experimentally scale the DET scheme for larger QNs? More importantly, given that the current CEP/QEP/DET schemes focus solely on pure states, there is an urgent need to extend these results to mixed states that are affected by noise—a vital step for the practical implementation of QNs.
- Other network-based tasks enhanced by entanglement. The feasibility of establishing entanglement over network structures also opens up further new possibilities of using entanglement to enhance some more general, nontrivial network-based tasks. For example, in Refs. [188,189], researchers studied the application of entanglement to enhance quantum games on both regular lattices and complex network structures, demonstrating that entanglement is a crucial resource for achieving favorable outcomes in the realm of quantum game theory. Additionally, similar improvements have been noted, such as in a quantum adaptation of the card game bridge, as highlighted in Ref. [190]. The discussion on networks of networks in Section 3.2 also provides an alternative perspective regarding entanglement. Rather than regarding it solely as a resource, we can view entanglement as a control parameter that regulates the interdependency between multiple network layers, potentially giving rise to novel critical or multicritical behaviors. Indeed, recent theoretical advancements in quantum phase transitions [191,192,193] have suggested that long-range entanglement among quantum spins at near absolute zero temperatures could trigger a shift from a second-order to a first-order phase transition. We hypothesize that this long-range entanglement may operate similarly to the introduction of interdependency among nodes across multiple layers, akin to classical networks-of-networks models. Yet, it is worth noting that the underlying physics governing this interdependency stems from entirely distinct principles within the quantum realm.
Author Contributions
Funding
Institutional Review Board Statement
Data Availability Statement
Conflicts of Interest
References
- Nielsen, M.A.; Chuang, I.L. Quantum Computation and Quantum Information, 10th ed.; Cambridge University Press: New York, NY, USA, 2010. [Google Scholar]
- Cohen, M.L.; Louie, S.G. Fundamentals of Condensed Matter Physics, 1st ed.; Cambridge University Press: Cambridge, UK, 2016. [Google Scholar]
- Plischke, M.; Bergersen, B. Equilibrium Statistical Physics, 2nd ed.; World Scientific: Singapore, 1994. [Google Scholar]
- Itzykson, C.; Drouffe, J.M. Statistical Field Theory: Volume 1, From Brownian Motion to Renormalization and Lattice Gauge Theory, 1st ed.; Cambridge University Press: New York, NY, USA, 1989. [Google Scholar]
- Itzykson, C.; Drouffe, J.M. Statistical Field Theory: Volume 2, Strong Coupling, Monte Carlo Methods, Conformal Field Theory and Random Systems, 1st ed.; Cambridge University Press: New York, NY, USA, 1989. [Google Scholar]
- Albert, R.; Barabási, A.L. Statistical Mechanics of Complex Networks. Rev. Mod. Phys. 2002, 74, 47–97. [Google Scholar] [CrossRef]
- Newman, M.; Barabási, A.L.; Watts, D.J. The Structure and Dynamics of Networks, 1st ed.; Princeton University Press: Princeton, NJ, USA, 2006. [Google Scholar]
- Chitambar, E.; Gour, G. Quantum Resource Theories. Rev. Mod. Phys. 2019, 91, 025001. [Google Scholar] [CrossRef]
- Cirac, J.I.; Zoller, P.; Kimble, H.J.; Mabuchi, H. Quantum State Transfer and Entanglement Distribution Among Distant Nodes in a Quantum Network. Phys. Rev. Lett. 1997, 78, 3221–3224. [Google Scholar] [CrossRef]
- Acín, A.; Cirac, J.I.; Lewenstein, M. Entanglement Percolation in Quantum Networks. Nat. Phys. 2007, 3, 256–259. [Google Scholar] [CrossRef]
- Kimble, H.J. The Quantum Internet. Nature 2008, 453, 1023–1030. [Google Scholar] [CrossRef]
- Broadfoot, S.; Dorner, U.; Jaksch, D. Entanglement Percolation with Bipartite Mixed States. Europhys. Lett. 2009, 88, 50002. [Google Scholar] [CrossRef]
- Lapeyre, G.J.; Wehr, J.; Lewenstein, M. Enhancement of Entanglement Percolation in Quantum Networks via Lattice Transformations. Phys. Rev. A 2009, 79, 042324. [Google Scholar] [CrossRef]
- Broadfoot, S.; Dorner, U.; Jaksch, D. Singlet Generation in Mixed-State Quantum Networks. Phys. Rev. A 2010, 81, 042316. [Google Scholar] [CrossRef]
- Albert, R.; Jeong, H.; Barabási, A.L. Error and Attack Tolerance of Complex Networks. Nature 2000, 406, 378–382. [Google Scholar] [CrossRef]
- Wu, L.; Zhu, S. Entanglement Percolation on a Quantum Internet with Scale-Free and Clustering Characters. Phys. Rev. A 2011, 84, 052304. [Google Scholar] [CrossRef]
- Li, Y.; Cavalcanti, D.; Kwek, L.C. Long-Distance Entanglement Generation with Scalable and Robust Two-Dimensional Quantum Network. Phys. Rev. A 2012, 85, 062330. [Google Scholar] [CrossRef]
- Perseguers, S.; Lapeyre, G.J., Jr.; Cavalcanti, D.; Lewenstein, M.; Acín, A. Distribution of Entanglement in Large-Scale Quantum Networks. Rep. Prog. Phys. 2013, 76, 096001. [Google Scholar] [CrossRef]
- Siomau, M. Gossip Algorithms in Quantum Networks. Phys. Lett. A 2017, 381, 136–139. [Google Scholar] [CrossRef]
- Carvacho, G.; Andreoli, F.; Santodonato, L.; Bentivegna, M.; Chaves, R.; Sciarrino, F. Experimental Violation of Local Causality in a Quantum Network. Nat. Commun. 2017, 8, 14775. [Google Scholar] [CrossRef] [PubMed]
- Das, S.; Khatri, S.; Dowling, J.P. Robust Quantum Network Architectures and Topologies for Entanglement Distribution. Phys. Rev. A 2018, 97, 012335. [Google Scholar] [CrossRef]
- Pirandola, S. End-to-End Capacities of a Quantum Communication Network. Commun. Phys. 2019, 2, 51. [Google Scholar] [CrossRef]
- Biamonte, J.; Faccin, M.; Domenico, M.D. Complex Networks from Classical to Quantum. Commun. Phys. 2019, 2, 53. [Google Scholar] [CrossRef]
- Unnikrishnan, A.; MacFarlane, I.J.; Yi, R.; Diamanti, E.; Markham, D.; Kerenidis, I. Anonymity for Practical Quantum Networks. Phys. Rev. Lett. 2019, 122, 240501. [Google Scholar] [CrossRef] [PubMed]
- Castellini, A.; Bellomo, B.; Compagno, G.; Lo Franco, R. Activating Remote Entanglement in a Quantum Network by Local Counting of Identical Particles. Phys. Rev. A 2019, 99, 062322. [Google Scholar] [CrossRef]
- Khabiboulline, E.T.; Borregaard, J.; De Greve, K.; Lukin, M.D. Optical Interferometry with Quantum Networks. Phys. Rev. Lett. 2019, 123, 070504. [Google Scholar] [CrossRef]
- Renou, M.O.; Wang, Y.; Boreiri, S.; Beigi, S.; Gisin, N.; Brunner, N. Limits on Correlations in Networks for Quantum and No-Signaling Resources. Phys. Rev. Lett. 2019, 123, 070403. [Google Scholar] [CrossRef]
- Hahn, F.; Pappa, A.; Eisert, J. Quantum Network Routing and Local Complementation. npj Quantum Inf. 2019, 5, 76. [Google Scholar] [CrossRef]
- Zhuang, Q.; Zhang, B. Quantum communication capacity transition of complex quantum networks. Phys. Rev. A 2021, 104, 022608. [Google Scholar] [CrossRef]
- Sadhu, A.; Somayajula, M.A.; Horodecki, K.; Das, S. Practical Limitations on Robustness and Scalability of Quantum Internet. arXiv 2023, arXiv:2308.12739. [Google Scholar]
- Kalb, N.; Reiserer, A.A.; Humphreys, P.C.; Bakermans, J.J.W.; Kamerling, S.J.; Nickerson, N.H.; Benjamin, S.C.; Twitchen, D.J.; Markham, M.; Hanson, R. Entanglement Distillation between Solid-State Quantum Network Nodes. Science 2017, 356, 928–932. [Google Scholar] [CrossRef]
- Humphreys, P.C.; Kalb, N.; Morits, J.P.J.; Schouten, R.N.; Vermeulen, R.F.L.; Twitchen, D.J.; Markham, M.; Hanson, R. Deterministic Delivery of Remote Entanglement on a Quantum Network. Nature 2018, 558, 268–273. [Google Scholar] [CrossRef]
- Pompili, M.; Hermans, S.L.N.; Baier, S.; Beukers, H.K.C.; Humphreys, P.C.; Schouten, R.N.; Vermeulen, R.F.L.; Tiggelman, M.J.; dos Santos Martins, L.; Dirkse, B.; et al. Realization of a Multinode Quantum Network of Remote Solid-State Qubits. Science 2021, 372, 259–264. [Google Scholar] [CrossRef] [PubMed]
- Riebe, M.; Monz, T.; Kim, K.; Villar, A.S.; Schindler, P.; Chwalla, M.; Hennrich, M.; Blatt, R. Deterministic Entanglement Swapping with an Ion-Trap Quantum Computer. Nat. Phys. 2008, 4, 839–842. [Google Scholar] [CrossRef]
- Almendros, M.; Huwer, J.; Piro, N.; Rohde, F.; Schuck, C.; Hennrich, M.; Dubin, F.; Eschner, J. Bandwidth-Tunable Single-Photon Source in an Ion-Trap Quantum Network. Phys. Rev. Lett. 2009, 103, 213601. [Google Scholar] [CrossRef] [PubMed]
- Essam, J.W. Percolation Theory. Rep. Prog. Phys. 1980, 43, 833–912. [Google Scholar] [CrossRef]
- Stauffer, D.; Aharony, A. Introduction to Percolation Theory, 2nd ed.; Taylor and Francis: London, UK, 1992. [Google Scholar]
- ben-Avraham, D.; Havlin, S. Diffusion and Reactions in Fractals and Disordered Systems, 1st ed.; Cambridge University Press: Cambridge, UK, 2000. [Google Scholar]
- Bunde, A.; Havlin, S. Fractals and Disordered Systems; Springer: Berlin/Heidelberg, Germany, 2012. [Google Scholar]
- Meng, X.; Gao, J.; Havlin, S. Concurrence Percolation in Quantum Networks. Phys. Rev. Lett. 2021, 126, 170501. [Google Scholar] [CrossRef]
- Perseguers, S. Entanglement Distribution in Quantum Networks. Ph.D. Thesis, Technische Universität München, München, Germany, 2010. [Google Scholar]
- Chitambar, E.; Leung, D.; Mančinska, L.; Ozols, M.; Winter, A. Everything You Always Wanted to Know About LOCC (But Were Afraid to Ask). Commun. Math. Phys. 2014, 328, 303–326. [Google Scholar] [CrossRef]
- Blok, M.S.; Ramasesh, V.V.; Schuster, T.; O’Brien, K.; Kreikebaum, J.M.; Dahlen, D.; Morvan, A.; Yoshida, B.; Yao, N.Y.; Siddiqi, I. Quantum Information Scrambling on a Superconducting Qutrit Processor. Phys. Rev. X 2021, 11, 021010. [Google Scholar] [CrossRef]
- Hu, X.M.; Guo, Y.; Liu, B.H.; Huang, Y.F.; Li, C.F.; Guo, G.C. Beating the Channel Capacity Limit for Superdense Coding with Entangled Ququarts. Sci. Adv. 2018, 4, eaat9304. [Google Scholar] [CrossRef] [PubMed]
- Orús, R. A Practical Introduction to Tensor Networks: Matrix Product States and Projected Entangled Pair States. Ann. Phys. 2014, 349, 117–158. [Google Scholar] [CrossRef]
- Meng, X.; Yang, T. Entanglement-Structured LSTM Boosts Chaotic Time Series Forecasting. Entropy 2021, 23, 1491. [Google Scholar] [CrossRef]
- Verstraete, F.; Cirac, J.I. Matrix Product States Represent Ground States Faithfully. Phys. Rev. B 2006, 73, 094423. [Google Scholar] [CrossRef]
- Bigoni, D.; Engsig-Karup, A.P.; Marzouk, Y.M. Spectral Tensor-Train Decomposition. SIAM J. Sci. Comput. 2016, 38, A2405–A2439. [Google Scholar] [CrossRef]
- Cirac, J.I.; Pérez-García, D.; Schuch, N.; Verstraete, F. Matrix Product States and Projected Entangled Pair States: Concepts, Symmetries, Theorems. Rev. Mod. Phys. 2021, 93, 045003. [Google Scholar] [CrossRef]
- Vidal, G. Class of Quantum Many-Body States That Can Be Efficiently Simulated. Phys. Rev. Lett. 2008, 101, 110501. [Google Scholar] [CrossRef]
- Farràs, O.; Martí-Farré, J.; Padró, C. Ideal Multipartite Secret Sharing Schemes. In Advances in Cryptology—EUROCRYPT 2007, Proceedings of the Annual International Conference on the Theory and Applications of Cryptographic Techniques, Barcelona, Spain, 20–24 May 2007; Naor, M., Ed.; Springer: Berlin/Heidelberg, Germany, 2007; Lecture Notes in Computer Science; pp. 448–465. [Google Scholar] [CrossRef]
- Dür, W.; Vidal, G.; Cirac, J.I. Three Qubits Can Be Entangled in Two Inequivalent Ways. Phys. Rev. A 2000, 62, 062314. [Google Scholar] [CrossRef]
- Battiston, F.; Amico, E.; Barrat, A.; Bianconi, G.; Ferraz de Arruda, G.; Franceschiello, B.; Iacopini, I.; Kéfi, S.; Latora, V.; Moreno, Y.; et al. The Physics of Higher-Order Interactions in Complex Systems. Nat. Phys. 2021, 17, 1093–1098. [Google Scholar] [CrossRef]
- Lambiotte, R.; Rosvall, M.; Scholtes, I. From Networks to Optimal Higher-Order Models of Complex Systems. Nat. Phys. 2019, 15, 313–320. [Google Scholar] [CrossRef]
- Bretto, A. Hypergraph Theory: An Introduction, 1st ed.; Springer: Cham, Switzerland, 2013. [Google Scholar]
- Kesten, H. Percolation Theory for Mathematicians; Springer: Berlin/Heidelberg, Germany, 1982; Volume 2. [Google Scholar]
- Turcotte, D.L. Fractals and Chaos in Geology and Geophysics; Cambridge University Press: Cambridge, UK, 1997. [Google Scholar]
- Stanley, H.E.; Ahlers, G. Introduction to Phase Transitions and Critical Phenomena; Oxford University Press: Oxford, UK, 1973. [Google Scholar]
- Grassberger, P. Spreading of Epidemic Processes Leading to Fractal Structures. In Fractals in Physics; Elsevier: Amsterdam, The Netherlands, 1986; pp. 273–278. [Google Scholar]
- Newman, M.E. Spread of Epidemic Disease on Networks. Phys. Rev. E 2002, 66, 016128. [Google Scholar] [CrossRef]
- Pastor-Satorras, R.; Vespignani, A. Immunization of Complex Networks. Phys. Rev. E 2002, 65, 036104. [Google Scholar] [CrossRef]
- Parshani, R.; Carmi, S.; Havlin, S. Epidemic Threshold for the Susceptible-Infectious-Susceptible Model on Random Networks. Phys. Rev. Lett. 2010, 104, 258701. [Google Scholar] [CrossRef]
- Lindquist, J.; Ma, J.; Van den Driessche, P.; Willeboordse, F.H. Effective Degree Network Disease Models. J. Math. Biol. 2011, 62, 143–164. [Google Scholar] [CrossRef] [PubMed]
- Vespignani, A. Modelling Dynamical Processes in Complex Socio-Technical Systems. Nat. Phys. 2012, 8, 32–39. [Google Scholar] [CrossRef]
- Pastor-Satorras, R.; Castellano, C.; Van Mieghem, P.; Vespignani, A. Epidemic Processes in Complex Networks. Rev. Mod. Phys. 2015, 87, 925. [Google Scholar] [CrossRef]
- Croccolo, F.; Roman, H.E. Spreading of Infections on Random Graphs: A Percolation-Type Model for COVID-19. Chaos Solitons Fractals 2020, 139, 110077. [Google Scholar] [CrossRef] [PubMed]
- MacKay, G.; Jan, N. Forest Fires as Critical Phenomena. J. Phys. Math. Gen. 1984, 17, L757. [Google Scholar] [CrossRef]
- Ritzenberg, A.L.; Cohen, R.J. First Passage Percolation: Scaling and Critical Exponents. Phys. Rev. B 1984, 30, 4038. [Google Scholar] [CrossRef]
- De Gennes, P.G. Scaling Concepts in Polymer Physics; Cornell University Press: Ithaca, NY, USA, 1979. [Google Scholar]
- Herrmann, H.J. Geometrical Cluster Growth Models and Kinetic Gelation. Phys. Rep. 1986, 136, 153–224. [Google Scholar] [CrossRef]
- Shapir, Y.; Aharony, A.; Harris, A.B. Localization and Quantum Percolation. Phys. Rev. Lett. 1982, 49, 486–489. [Google Scholar] [CrossRef]
- Soukoulis, C.M.; Li, Q.; Grest, G.S. Quantum Percolation in Three-Dimensional Systems. Phys. Rev. B 1992, 45, 7724–7729. [Google Scholar] [CrossRef]
- Motrunich, O.; Mau, S.C.; Huse, D.A.; Fisher, D.S. Infinite-Randomness Quantum Ising Critical Fixed Points. Phys. Rev. B 2000, 61, 1160–1172. [Google Scholar] [CrossRef]
- Chandrashekar, C.M.; Busch, T. Quantum Percolation and Transition Point of a Directed Discrete-Time Quantum Walk. Sci. Rep. 2014, 4, 6583. [Google Scholar] [CrossRef]
- Fostner, S.; Brown, R.; Carr, J.; Brown, S.A. Continuum Percolation with Tunneling. Phys. Rev. B 2014, 89, 075402. [Google Scholar] [CrossRef]
- Skinner, B.; Ruhman, J.; Nahum, A. Measurement-Induced Phase Transitions in the Dynamics of Entanglement. Phys. Rev. X 2019, 9, 031009. [Google Scholar] [CrossRef]
- Pant, M.; Towsley, D.; Englund, D.; Guha, S. Percolation Thresholds for Photonic Quantum Computing. Nat. Commun. 2019, 10, 1070. [Google Scholar] [CrossRef]
- Gardner, R.H.; Turner, M.G.; Dale, V.H.; O’Neill, R.V. A Percolation Model of Ecological Flows. In Landscape Boundaries: Consequences for Biotic Diversity and Ecological Flows; Springer: Berlin/Heidelberg, Germany, 1992; pp. 259–269. [Google Scholar]
- Vigolo, B.; Coulon, C.; Maugey, M.; Zakri, C.; Poulin, P. An Experimental Approach to the Percolation of Sticky Nanotubes. Science 2005, 309, 920–923. [Google Scholar] [CrossRef] [PubMed]
- Anekal, S.G.; Bahukudumbi, P.; Bevan, M.A. Dynamic Signature for the Equilibrium Percolation Threshold of Attractive Colloidal Fluids. Phys. Rev. E 2006, 73, 020403. [Google Scholar] [CrossRef]
- Berkowitz, B.; Balberg, I. Percolation Theory and Its Application to Groundwater Hydrology. Water Resour. Res. 1993, 29, 775–794. [Google Scholar] [CrossRef]
- Berkowitz, B.; Ewing, R.P. Percolation Theory and Network Modeling Applications in Soil Physics. Surv. Geophys. 1998, 19, 23–72. [Google Scholar] [CrossRef]
- Gaonac’h, H.; Lovejoy, S.; Schertzer, D. Percolating Magmas and Explosive Volcanism. Geophys. Res. Lett. 2003, 30, 1559. [Google Scholar] [CrossRef]
- King, P.R.; Masihi, M. Percolation Theory in Reservoir Engineering; World Scientific: Singapore, 2019. [Google Scholar]
- Ghanbarian, B.; Skaggs, T.H. Soil Water Retention Curve Inflection Point: Insight into Soil Structure from Percolation Theory. Soil Sci. Soc. Am. J. 2022, 86, 338–344. [Google Scholar] [CrossRef]
- Kacperski, K.; Hołyst, J.A. Phase Transitions as a Persistent Feature of Groups with Leaders in Models of Opinion Formation. Phys. Stat. Mech. Its Appl. 2000, 287, 631–643. [Google Scholar] [CrossRef]
- Watts, D.J. A Simple Model of Global Cascades on Random Networks. Proc. Natl. Acad. Sci. USA 2002, 99, 5766–5771. [Google Scholar] [CrossRef]
- Centola, D.; Eguíluz, V.M.; Macy, M.W. Cascade Dynamics of Complex Propagation. Phys. Stat. Mech. Appl. 2007, 374, 449–456. [Google Scholar] [CrossRef]
- Iniguez, G.; Kertész, J.; Kaski, K.K.; Barrio, R.A. Opinion and Community Formation in Coevolving Networks. Phys. Rev. E 2009, 80, 066119. [Google Scholar] [CrossRef]
- Echenique, P.; Gómez-Gardenes, J.; Moreno, Y. Dynamics of Jamming Transitions in Complex Networks. Europhys. Lett. 2005, 71, 325. [Google Scholar] [CrossRef]
- Vespignani, A. The Fragility of Interdependency. Nature 2010, 464, 984–985. [Google Scholar] [CrossRef] [PubMed]
- Li, D.; Fu, B.; Wang, Y.; Lu, G.; Berezin, Y.; Stanley, H.E.; Havlin, S. Percolation Transition in Dynamical Traffic Network with Evolving Critical Bottlenecks. Proc. Natl. Acad. Sci. USA 2015, 112, 669–672. [Google Scholar] [CrossRef] [PubMed]
- Del Vicario, M.; Bessi, A.; Zollo, F.; Petroni, F.; Scala, A.; Caldarelli, G.; Stanley, H.E.; Quattrociocchi, W. The Spreading of Misinformation Online. Proc. Natl. Acad. Sci. USA 2016, 113, 554–559. [Google Scholar] [CrossRef]
- Baggag, A.; Abbar, S.; Zanouda, T.; Srivastava, J. Resilience Analytics: Coverage and Robustness in Multi-Modal Transportation Networks. EPJ Data Sci. 2018, 7, 14. [Google Scholar] [CrossRef]
- Barabási, A.L.; Albert, R. Emergence of Scaling in Random Networks. Science 1999, 286, 509–512. [Google Scholar] [CrossRef]
- Zhou, B.; Meng, X.; Stanley, H.E. Power-Law Distribution of Degree–Degree Distance: A Better Representation of the Scale-Free Property of Complex Networks. Proc. Natl. Acad. Sci. USA 2020, 117, 14812–14818. [Google Scholar] [CrossRef]
- Meng, X.; Zhou, B. Scale-Free Networks beyond Power-Law Degree Distribution. Chaos Solitons Fractals 2023, 176, 114173. [Google Scholar] [CrossRef]
- Boguná, M.; Serrano, M.Á. Generalized Percolation in Random Directed Networks. Phys. Rev. E 2005, 72, 016106. [Google Scholar] [CrossRef]
- Badie-Modiri, A.; Rizi, A.K.; Karsai, M.; Kivelä, M. Directed Percolation in Temporal Networks. Phys. Rev. Res. 2022, 4, L022047. [Google Scholar] [CrossRef]
- Cohen, R.; ben-Avraham, D.; Havlin, S. Percolation Critical Exponents in Scale-Free Networks. Phys. Rev. E 2002, 66, 036113. [Google Scholar] [CrossRef] [PubMed]
- Gao, J.; Buldyrev, S.V.; Havlin, S.; Stanley, H.E. Robustness of a Network of Networks. Phys. Rev. Lett. 2011, 107, 195701. [Google Scholar] [CrossRef] [PubMed]
- Gao, J.; Buldyrev, S.V.; Stanley, H.E.; Havlin, S. Networks Formed from Interdependent Networks. Nat. Phys. 2012, 8, 40–48. [Google Scholar] [CrossRef]
- Kivelä, M.; Arenas, A.; Barthelemy, M.; Gleeson, J.P.; Moreno, Y.; Porter, M.A. Multilayer Networks. J. Complex Netw. 2014, 2, 203–271. [Google Scholar] [CrossRef]
- Gao, J.; Bashan, A.; Shekhtman, L.; Havlin, S. Introduction to Networks of Networks; IOP Publishing: Bristol, UK, 2022. [Google Scholar]
- Buldyrev, S.V.; Parshani, R.; Paul, G.; Stanley, H.E.; Havlin, S. Catastrophic Cascade of Failures in Interdependent Networks. Nature 2010, 464, 1025–1028. [Google Scholar] [CrossRef] [PubMed]
- Parshani, R.; Buldyrev, S.V.; Havlin, S. Interdependent Networks: Reducing the Coupling Strength Leads to a Change from a First to Second Order Percolation Transition. Phys. Rev. Lett. 2010, 105, 048701. [Google Scholar] [CrossRef]
- Huang, X.; Gao, J.; Buldyrev, S.V.; Havlin, S.; Stanley, H.E. Robustness of Interdependent Networks under Targeted Attack. Phys. Rev. E 2011, 83, 065101. [Google Scholar] [CrossRef] [PubMed]
- Shao, J.; Buldyrev, S.V.; Havlin, S.; Stanley, H.E. Cascade of Failures in Coupled Network Systems with Multiple Support-Dependence Relations. Phys. Rev. E 2011, 83, 036116. [Google Scholar] [CrossRef]
- Zhao, K.; Bianconi, G. Percolation on Interacting, Antagonistic Networks. J. Stat. Mech. Theor. Exp. 2013, 2013, P05005. [Google Scholar] [CrossRef]
- Gao, J.; Buldyrev, S.V.; Havlin, S.; Stanley, H.E. Robustness of a Network Formed by n Interdependent Networks with a One-to-One Correspondence of Dependent Nodes. Phys. Rev. E 2012, 85, 066134. [Google Scholar] [CrossRef]
- Dong, G.; Gao, J.; Tian, L.; Du, R.; He, Y. Percolation of Partially Interdependent Networks under Targeted Attack. Phys. Rev. E 2012, 85, 016112. [Google Scholar] [CrossRef] [PubMed]
- Dong, G.; Gao, J.; Du, R.; Tian, L.; Stanley, H.E.; Havlin, S. Robustness of Network of Networks under Targeted Attack. Phys. Rev. E 2013, 87, 052804. [Google Scholar] [CrossRef] [PubMed]
- Baxter, G.J.; Dorogovtsev, S.N.; Goltsev, A.V.; Mendes, J.F.F. Avalanche Collapse of Interdependent Networks. Phys. Rev. Lett. 2012, 109, 248701. [Google Scholar] [CrossRef] [PubMed]
- Liu, X.; Maiorino, E.; Halu, A.; Glass, K.; Prasad, R.B.; Loscalzo, J.; Gao, J.; Sharma, A. Robustness and Lethality in Multilayer Biological Molecular Networks. Nat. Commun. 2020, 11, 6043. [Google Scholar] [CrossRef]
- D’Agostino, G.; Scala, A. Networks of Networks: The Last Frontier of Complexity; Springer: Berlin/Heidelberg, Germany, 2014; Volume 340. [Google Scholar]
- Reis, S.D.; Hu, Y.; Babino, A.; Andrade Jr, J.S.; Canals, S.; Sigman, M.; Makse, H.A. Avoiding Catastrophic Failure in Correlated Networks of Networks. Nat. Phys. 2014, 10, 762–767. [Google Scholar] [CrossRef]
- Boccaletti, S.; Bianconi, G.; Criado, R.; Del Genio, C.I.; Gómez-Gardenes, J.; Romance, M.; Sendina-Nadal, I.; Wang, Z.; Zanin, M. The Structure and Dynamics of Multilayer Networks. Phys. Rep. 2014, 544, 1–122. [Google Scholar] [CrossRef]
- Bianconi, G. Multilayer Networks: Structure and Function; Oxford University Press: Oxford, UK, 2018. [Google Scholar]
- Gomez, S.; Diaz-Guilera, A.; Gomez-Gardenes, J.; Perez-Vicente, C.J.; Moreno, Y.; Arenas, A. Diffusion Dynamics on Multiplex Networks. Phys. Rev. Lett. 2013, 110, 028701. [Google Scholar] [CrossRef]
- Liu, X.; Li, D.; Ma, M.; Szymanski, B.K.; Stanley, H.E.; Gao, J. Network Resilience. Phys. Rep. 2022, 971, 1–108. [Google Scholar] [CrossRef]
- Bashan, A.; Berezin, Y.; Buldyrev, S.V.; Havlin, S. The Extreme Vulnerability of Interdependent Spatially Embedded Networks. Nat. Phys. 2013, 9, 667–672. [Google Scholar] [CrossRef]
- Lu, R.; Yu, W.; Lü, J.; Xue, A. Synchronization on Complex Networks of Networks. IEEE Trans. Neural Netw. Learn. Syst. 2014, 25, 2110–2118. [Google Scholar] [CrossRef]
- Ouyang, M. A Mathematical Framework to Optimize Resilience of Interdependent Critical Infrastructure Systems under Spatially Localized Attacks. Eur. J. Oper. Res. 2017, 262, 1072–1084. [Google Scholar] [CrossRef]
- Duan, D.; Lv, C.; Si, S.; Wang, Z.; Li, D.; Gao, J.; Havlin, S.; Stanley, H.E.; Boccaletti, S. Universal Behavior of Cascading Failures in Interdependent Networks. Proc. Natl. Acad. Sci. USA 2019, 116, 22452–22457. [Google Scholar] [CrossRef] [PubMed]
- Cellai, D.; López, E.; Zhou, J.; Gleeson, J.P.; Bianconi, G. Percolation in Multiplex Networks with Overlap. Phys. Rev. E 2013, 88, 052811. [Google Scholar] [CrossRef] [PubMed]
- Kenett, D.Y.; Perc, M.; Boccaletti, S. Networks of Networks—An Introduction. Chaos Solitons Fractals 2015, 80, 1–6. [Google Scholar] [CrossRef]
- De Domenico, M. More Is Different in Real-World Multilayer Networks. Nat. Phys. 2023, 19, 1247–1262. [Google Scholar] [CrossRef]
- Erdos, P.; Rényi, A. On Random Graphs. Public Math. Debr. 1959, 6, 290–297. [Google Scholar] [CrossRef]
- Erdos, P.; Rényi, A. On the Evolution of Random Graphs. Inst. Hung. Acad. Sci. 1960, 5, 17–61. [Google Scholar]
- Bollobás, B. Random Graphs; Academic: London, UK, 1985. [Google Scholar]
- Bretto, A. Hypergraph Theory: An Introduction. In Mathematical Engineering; Springer International Publishing: Berlin/ Heidelberg, Germany, 2013. [Google Scholar]
- Bianconi, G. Higher-Order Networks; Elements in the Structure and Dynamics of Complex Networks; Cambridge University Press: Cambridge, UK, 2021. [Google Scholar] [CrossRef]
- Bick, C.; Gross, E.; Harrington, H.; Schaub, M. What Are Higher-Order Networks? SIAM Rev. 2023, 65, 686–731. [Google Scholar] [CrossRef]
- Klamt, S.; Haus, U.; Theis, F. Hypergraphs and Cellular Networks. PLoS Computat. Biol. 2009, 5, e1000385. [Google Scholar] [CrossRef]
- Jost, J.; Mulas, R. Hypergraph Laplace Operators for Chemical Reaction Networks. Adv. Math. 2019, 351, 870–896. [Google Scholar] [CrossRef]
- Taramasco, C.; Cointet, J.-P.; Roth, C. Academic Team Formation as Evolving Hypergraphs. Scientometrics 2010, 85, 721–740. [Google Scholar] [CrossRef]
- Krumov, L.; Fretter, C.; Müller-Hannemann, M.; Weihe, K.; Hütt, M. Motifs in Co-Authorship Networks and Their Relation to the Impact of Scientific Publications. Eur. Phys. J. B 2011, 84, 535–540. [Google Scholar] [CrossRef]
- Neuhäuser, L.; Mellor, A.; Lambiotte, R. Multibody Interactions and Nonlinear Consensus Dynamics on Networked Systems. Phys. Rev. E 2020, 101, 032310. [Google Scholar] [CrossRef] [PubMed]
- Majhi, S.; Perc, M.; Ghosh, D. Dynamics on Higher-Order Networks: A review. J. R. Soc. Interface 2022, 19, 20220043. [Google Scholar] [CrossRef] [PubMed]
- Coutinho, B.; Wu, A.; Zhou, H.; Liu, Y. Covering Problems and Core Percolations on Hypergraphs. Phys. Rev. Lett. 2020, 124, 248301. [Google Scholar] [CrossRef]
- Sun, H.; Bianconi, G. Higher-Order Percolation Processes on Multiplex Hypergraphs. Phys. Rev. E 2021, 104, 034306. [Google Scholar] [CrossRef]
- Sun, H.; Radicchi, F.; Kurths, J.; Bianconi, G. The Dynamic Nature of Percolation on Networks with Triadic Interactions. Nat. Commun. 2023, 14, 1308. [Google Scholar] [CrossRef]
- Lee, J.; Goh, K.; Lee, D.; Kahng, B. (k,q)-core Decomposition of Hypergraphs. Chaos Solitons Fractals 2023, 173, 113645. [Google Scholar] [CrossRef]
- Peng, H.; Qian, C.; Zhao, D.; Zhong, M.; Ling, X.; Wang, W. Disintegrate Hypergraph Networks by Attacking Hyperedge. J. King Saud Univ. Comput. Inf. Sci. 2022, 34, 4679–4685. [Google Scholar] [CrossRef]
- Peng, H.; Qian, C.; Zhao, D.; Zhong, M.; Han, J.; Li, R.; Wang, W. Message Passing Approach to Analyze the Robustness of Hypergraph. arXiv 2023, arXiv:2302.14594. [Google Scholar]
- Bianconi, G.; Dorogovtsev, S. The Theory of Percolation on Hypergraphs. arXiv 2023, arXiv:2305.12297. [Google Scholar]
- Bose, S.; Vedral, V.; Knight, P.L. Purification via Entanglement Swapping and Conserved Entanglement. Phys. Rev. A 1999, 60, 194–197. [Google Scholar] [CrossRef]
- Perseguers, S.; Cirac, J.I.; Acín, A.; Lewenstein, M.; Wehr, J. Entanglement Distribution in Pure-State Quantum Networks. Phys. Rev. A 2008, 77, 022308. [Google Scholar] [CrossRef]
- Meng, X.; Cui, Y.; Gao, J.; Havlin, S.; Ruckenstein, A.E. Deterministic Entanglement Distribution on Series-Parallel Quantum Networks. Phys. Rev. Res. 2023, 5, 013225. [Google Scholar] [CrossRef]
- Nielsen, M.A. Conditions for a Class of Entanglement Transformations. Phys. Rev. Lett. 1999, 83, 436–439. [Google Scholar] [CrossRef]
- Żukowski, M.; Zeilinger, A.; Horne, M.A.; Ekert, A.K. “Event-Ready-Detectors” Bell Experiment via Entanglement Swapping. Phys. Rev. Lett. 1993, 71, 4287–4290. [Google Scholar] [CrossRef]
- Bennett, C.H.; Bernstein, H.J.; Popescu, S.; Schumacher, B. Concentrating Partial Entanglement by Local Operations. Phys. Rev. A 1996, 53, 2046–2052. [Google Scholar] [CrossRef]
- Vidal, G. Entanglement of Pure States for a Single Copy. Phys. Rev. Lett. 1999, 83, 1046–1049. [Google Scholar] [CrossRef]
- Duffin, R.J. Topology of Series-Parallel Networks. J. Math. Anal. Appl. 1965, 10, 303–318. [Google Scholar] [CrossRef]
- Kesten, H. The Critical Probability of Bond Percolation on the Square Lattice Equals 1/2. Commun. Math. Phys. 1980, 74, 41–59. [Google Scholar] [CrossRef]
- Hill, S.; Wootters, W.K. Entanglement of a Pair of Quantum Bits. Phys. Rev. Lett. 1997, 78, 5022–5025. [Google Scholar] [CrossRef]
- Perseguers, S.; Cavalcanti, D.; Lapeyre, G.J., Jr.; Lewenstein, M.; Acín, A. Multipartite Entanglement Percolation. Phys. Rev. A 2010, 81, 032327. [Google Scholar] [CrossRef]
- Pant, M.; Krovi, H.; Towsley, D.; Tassiulas, L.; Jiang, L.; Basu, P.; Englund, D.; Guha, S. Routing Entanglement in the Quantum Internet. npj Quantum Inf. 2019, 5, 25. [Google Scholar] [CrossRef]
- Kobayashi, H.; Le Gall, F.; Nishimura, H.; Rötteler, M. Perfect Quantum Network Communication Protocol Based on Classical Network Coding. In Proceedings of the 2010 IEEE International Symposium on Information Theory, Austin, TX, USA, 13–18 June 2010; pp. 2686–2690. [Google Scholar] [CrossRef]
- Cuquet, M.; Calsamiglia, J. Entanglement Percolation in Quantum Complex Networks. Phys. Rev. Lett. 2009, 103, 240503. [Google Scholar] [CrossRef] [PubMed]
- Lawler, E. Combinatorial Optimization: Networks and Matroids; Holtz, Rinehart and Winston: Austin, TX, USA, 1976. [Google Scholar]
- Monma, C.; Sidney, J. Sequencing with Series-Parallel Precedence Constraints. Math. Oper. Res. 1979, 4, 215–224. [Google Scholar] [CrossRef]
- Cohen, R.; Erez, K.; ben-Avraham, D.; Havlin, S. Resilience of the Internet to Random Breakdowns. Phys. Rev. Lett. 2000, 85, 4626–4628. [Google Scholar] [CrossRef]
- Bern, M.; Lawler, E.; Wong, A. Linear-Time Computation of Optimal Subgraphs of Decomposable Graphs. J. Algorithms 1987, 8, 216–235. [Google Scholar] [CrossRef]
- Borie, R.B.; Parker, R.G.; Tovey, C.A. Automatic Generation of Linear-Time Algorithms from Predicate Calculus Descriptions of Problems on Recursively Constructed Graph Families. Algorithmica 1992, 7, 555–581. [Google Scholar] [CrossRef]
- Kikuno, T.; Yoshida, N.; Kakuda, Y. A Linear Algorithm for the Domination Number of a Series-Parallel Graph. Discret. Appl. Math. 1983, 5, 299–311. [Google Scholar] [CrossRef]
- Takamizawa, K.; Nishizeki, T.; Saito, N. Linear-Time Computability of Combinatorial Problems on Series-Parallel Graphs. J. ACM 1982, 29, 623–641. [Google Scholar] [CrossRef]
- Baffi, L.; Petreschi, R. Parallel Maximal Matching on Minimal Vertex Series Parallel Digraphs. In Algorithms, Concurrency and Knowledge, Proceedings of the Asian Computing Science Conference, Pathumthani, Thailand, 11–13 December 1995; Kanchanasut, K., Lévy, J., Eds.; Springer: Berlin/Heidelberg, Germany, 1995; pp. 34–47. [Google Scholar]
- Bertolazzi, P.; Cohen, R.F.; Di Battista, G.; Tamassia, R.; Tollis, I.G. How to Draw a Series-Parallel Digraph. In Algorithm Theory—SWAT ’92, Proceedings of the Scandinavian Workshop on Algorithm Theory, Helsinki, Finland, 8–10 July 1992; Nurmi, O., Ukkonen, E., Eds.; Springer: Berlin/Heidelberg, Germany, 1992; pp. 272–283. [Google Scholar]
- Rendl, F. Quadratic Assignment Problems on Series-Parallel Digraphs. Z. Oper. Res. 1986, 30, A161–A173. [Google Scholar] [CrossRef]
- Steiner, G. A compact labeling scheme for series-parallel graphs. Discret. Appl. Math. 1985, 11, 281–297. [Google Scholar] [CrossRef]
- Bang-Jensen, J.; Gutin, G. Digraphs: Theory, Algorithms and Applications; Springer: Berlin/Heidelberg, Germany, 2008. [Google Scholar] [CrossRef]
- Valdes, J.; Tarjan, R.; Lawler, E. The Recognition of Series Parallel Digraphs. SIAM J. Comput. 1982, 11, 298–313. [Google Scholar] [CrossRef]
- Bodlaender, H.; van Antwerpen de Fluiter, B. Parallel Algorithms for Series Parallel Graphs and Graphs with Treewidth Twos. Algorithmica 2001, 29, 534–559. [Google Scholar] [CrossRef]
- Eppstein, D. Parallel Recognition of Series-Parallel Graphs. Inform. Comput. 1992, 98, 41–55. [Google Scholar] [CrossRef]
- He, X. Efficient Parallel Algorithms for Series Parallel Graphs. J. Algorithms 1991, 12, 409–430. [Google Scholar] [CrossRef]
- He, X.; Yesha, Y. Parallel Recognition and Decomposition of Two Terminal Series Parallel Graphs. Inform. Comput. 1987, 75, 15–38. [Google Scholar] [CrossRef][Green Version]
- Kron, G. Tensor Analysis of Networks; Wiley: Hoboken, NJ, USA, 1939. [Google Scholar]
- Versfeld, L. Remarks on Star-Mesh Transformation of Electrical Networks. Electron. Lett. 1970, 6, 597–599. [Google Scholar] [CrossRef]
- Malik, O.; Meng, X.; Havlin, S.; Korniss, G.; Szymanski, B.K.; Gao, J. Concurrence Percolation Threshold of Large-Scale Quantum Networks. Commun. Phys. 2022, 5, 193. [Google Scholar] [CrossRef]
- Krattenthaler, C. Lattice Path Enumeration. arXiv 2015, arXiv:1503.05930. [Google Scholar]
- Jensen, I. Enumeration of Self-Avoiding Walks on the Square Lattice. J. Phys. A 2004, 37, 5503–5524. [Google Scholar] [CrossRef]
- Roberts, B.; Kroese, D.P. Estimating the Number of s-t Paths in a Graph. J. Graph Algorithms Appl. 2007, 11, 195–214. [Google Scholar] [CrossRef]
- Treinish, M.; Gambetta, J.; Thomas, S.; Nation, P.; qiskit-bot; Kassebaum, P.; Rodríguez, D.M.; González, S.d.l.P.; Lishman, J.; Hu, S.; et al. Qiskit 0.42.0; Zenodo: Geneve, Switzerland, 2023. [Google Scholar]
- Calderon-Vargas, F.A.; Barron, G.S.; Deng, X.H.; Sigillito, A.J.; Barnes, E.; Economou, S.E. Fast High-Fidelity Entangling Gates for Spin Qubits in Si Double Quantum Dots. Phys. Rev. B 2019, 100, 035304. [Google Scholar] [CrossRef]
- Kandala, A.; Wei, K.X.; Srinivasan, S.; Magesan, E.; Carnevale, S.; Keefe, G.A.; Klaus, D.; Dial, O.; McKay, D.C. Demonstration of a High-Fidelity CNOT Gate for Fixed-Frequency Transmons with Engineered ZZ Suppression. Phys. Rev. Lett. 2021, 127, 130501. [Google Scholar] [CrossRef] [PubMed]
- Bantysh, B.I.; Chernyavskiy, A.Y.; Bogdanov, Y.I. Quantum Tomography Benchmarking. Quantum Inf. Process. 2021, 20, 339. [Google Scholar] [CrossRef]
- Li, Q.; He, Y.; Jiang, J.p. A Novel Clustering Algorithm Based on Quantum Games. J. Phys. A 2009, 42, 445303. [Google Scholar] [CrossRef]
- Miszczak, J.A.; Pawela, Ł.; Sładkowski, J. General Model for an Entanglement-Enhanced Composed Quantum Game on a Two-Dimensional Lattice. Fluct. Noise Lett. 2014, 13, 1450012. [Google Scholar] [CrossRef]
- Muhammad, S.; Tavakoli, A.; Kurant, M.; Pawłowski, M.; Żukowski, M.; Bourennane, M. Quantum Bidding in Bridge. Phys. Rev. X 2014, 4, 021047. [Google Scholar] [CrossRef]
- Pfleiderer, C. Why First Order Quantum Phase Transitions Are Interesting. J. Phys. Condens. Matter 2005, 17, S987. [Google Scholar] [CrossRef]
- de Lima, J.P.; Gonçalves, L.L. Quantum Transitions of the Isotropic XY Model with Long-Range Interactions on the Inhomogeneous Periodic Chain. Phys. Rev. B 2008, 77, 214424. [Google Scholar] [CrossRef]
- Li, J.; Lei, S. A Study of the Spin-1/2 XZ Chain with Long-Range Interactions in the External Magnetic Field. J. Magn. Magn. Mater. 2008, 320, 2823–2830. [Google Scholar] [CrossRef]












| (2, 3) | 1/( ) | −1 | ()/() | ()/() | (2)/() | |
| (3, 4) | 1/() | 1 | ()/() | ()/() | (2)/() | 2()/() |
| (4, ∞) | 1 | 1 | 3 | 1/2 | 5/2 | 4 |
| Classical | Concurrence | |
|---|---|---|
| Series rule | ||
| Parallel rule | ||
| Higher-order rules | Can be approximated by the star-mesh transform, by the following two-step argument: | |
| 1. The star-mesh transform can reduce an N-graph to an -graph (right panel) and is solvable by applying the series and parallel rules recursively through a group of coupled equations (see Section 6 for details). 2. Applying the transform consecutively on a network can reduce nodes one by one—and thus reduce any topology to two nodes, yielding the final (approximate) connectivity between them (bottom panel, i. → viii.). |  | |
 | ||
| CEP | DET | |
|---|---|---|
| Series | ||
| Parallel |
| Network Topology | (Fast Approximation) | [40] |
|---|---|---|
| Bethe Lattice () | 0.5 | 0.5 |
| Bethe Lattice () | 0.39 | 0.3918 |
| 2D square () | 0.40 | 0.416 |
| 2D square () | 0.44 | n/a |
| 2D square () | 0.5 | n/a |
| ER () | n/a | |
| ER () | n/a | |
| ER () | n/a | |
| BA () | n/a | |
| BA () | n/a |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Meng, X.; Hu, X.; Tian, Y.; Dong, G.; Lambiotte, R.; Gao, J.; Havlin, S. Percolation Theories for Quantum Networks. Entropy 2023, 25, 1564. https://doi.org/10.3390/e25111564
Meng X, Hu X, Tian Y, Dong G, Lambiotte R, Gao J, Havlin S. Percolation Theories for Quantum Networks. Entropy. 2023; 25(11):1564. https://doi.org/10.3390/e25111564
Chicago/Turabian StyleMeng, Xiangyi, Xinqi Hu, Yu Tian, Gaogao Dong, Renaud Lambiotte, Jianxi Gao, and Shlomo Havlin. 2023. "Percolation Theories for Quantum Networks" Entropy 25, no. 11: 1564. https://doi.org/10.3390/e25111564
APA StyleMeng, X., Hu, X., Tian, Y., Dong, G., Lambiotte, R., Gao, J., & Havlin, S. (2023). Percolation Theories for Quantum Networks. Entropy, 25(11), 1564. https://doi.org/10.3390/e25111564









