Design of Low-Density Parity-Check Code Pair for Joint Source-Channel Coding Systems Based on Graph Theory
Abstract
:1. Introduction
2. Preliminaries of JSCC
2.1. Representations of JSCC
- *
- : MI from the variable node (VN) of the source code to the check node (CN) of the source code.
- *
- : MI from the CN of the source code to the VN of the source code.
- *
- : MI from the CN of the source code to the VN of the channel code.
- *
- : MI from the VN of the channel code to the CN of the source code.
- *
- : MI from the VN of the channel code to the CN of the channel code.
- *
- : MI from the CN of the channel code to the VN of the channel code.
2.2. Encoding and Decoding of JSCC Systems
2.2.1. Encoder
2.2.2. Decoder
3. Construction of LDPC Code Pairs
3.1. Definitions and Theorems
3.2. Algorithm Description
| Algorithm 1: Construction of LDPC code pair |
| Require: : row number of source LDPC code : column weight of source LDPC code : column weight of channel LDPC code s: girth of the constructed source code and channel code. Ensure: Initialize: parity-check matrix for channel code , .
|
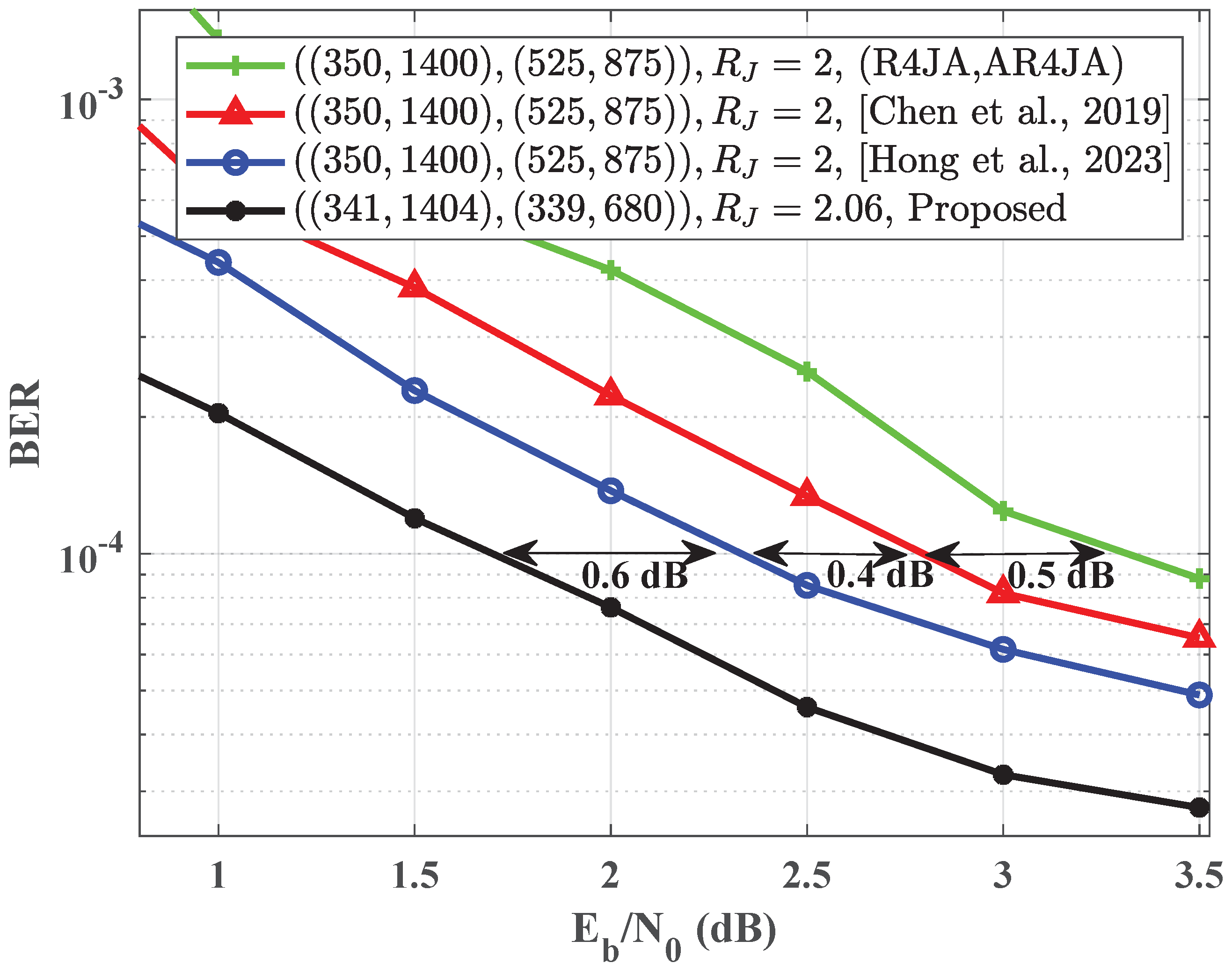
4. Simulation Results
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Data Availability Statement
Conflicts of Interest
References
- Shannon, C.E. A mathematical theory of communication. Bell Syst. Tech. J. 1948, 27, 379–423. [Google Scholar] [CrossRef] [Green Version]
- Guyader, A.; Fabre, E.; Guillemot, C.; Robert, M. Joint source-channel turbo decoding of entropy-coded sources. IEEE J. Sel. Areas Commun. 2001, 19, 1680–1696. [Google Scholar] [CrossRef]
- Hedayat, A.; Nosratinia, A. Performance analysis and design criteria for finite-alphabet source-channel codes. IEEE Trans. Commun. 2004, 52, 1872–1879. [Google Scholar] [CrossRef]
- Lakovic, K.; Villasenor, J. Combining variable length codes and turbo codes. In Proceedings of the IEEE 55th Vehicular Technology Conference, Birmingham, AL, USA, 6–9 May 2002; pp. 1719–1723. [Google Scholar]
- Lakovic, K.; Villasenor, J. On reversible variable length codes with turbo codes, and iterative source-channel decoding. In Proceedings of the IEEE International Symposium on Information Theory, Lausanne, Switzerland, 30 Jun–5 July 2002; p. 170. [Google Scholar]
- Jaspar, X.; Vandendorpe, L. Design and performance analysis of joint source-channel turbo schemes with variable length codes. In Proceedings of the IEEE International Conference on Communications, Seoul, Republic of Korea, 16–20 May 2005; pp. 526–530. [Google Scholar]
- Poulliat, C.; Declercq, D.; Lamy-Bergot, C.; Fijalkow, I. Analysis and optimization of irregular LDPC codes for joint source-channel decoding. IEEE Commun. Lett. 2005, 9, 1064–1066. [Google Scholar] [CrossRef]
- Zribi, A.; Pyndiah, R.; Zaibi, S. Low-complexity soft decoding of Huffman codes and iterative joint source channel decoding. IEEE Trans. Commun. 2012, 60, 1669–1679. [Google Scholar] [CrossRef]
- Fresia, M.; Pérez-Cruz, F.; Poor, H.V. Optimized concatenated LDPC codes for joint source-channel coding. In Proceedings of the IEEE International Symposium on Information Theory, Seoul, Republic of Korea, 28 June–3 July 2009; pp. 2131–2135. [Google Scholar]
- Fresia, M.; Perez-Cruz, F.; Poor, H.V.; Verdu, S. Joint source and channel coding. IEEE Signal Process. Mag. 2010, 27, 104–113. [Google Scholar] [CrossRef]
- He, J.; Wang, L.; Chen, P. A joint source and channel coding scheme base on simple protograph structured codes. In Proceedings of the International Symposium on Communications and Information Technologies, Gold Coast, Australia, 2–5 October 2012; pp. 65–69. [Google Scholar]
- Chen, C.; Wang, L.; Liu, S. The design of protograph LDPC codes as source codes in a JSCC system. IEEE Commun. Lett. 2018, 22, 672–675. [Google Scholar] [CrossRef]
- Chen, Q.; Wang, L.; Hong, S.; Xiong, Z. Performance improvement of JSCC scheme through redesigning channel code. IEEE Commun. Lett. 2016, 20, 1088–1091. [Google Scholar] [CrossRef]
- Xu, Z.; Wang, L.; Hong, S.; Chen, G. Design of Code Pair for Protograph LDPC Codes-Based JSCC System with Joint Shuffled Scheduling Decoding Algorithm. IEEE Commun. Lett. 2021, 25, 3770–3774. [Google Scholar] [CrossRef]
- Chen, Q.; Wang, L.; Hong, S.; Chen, Y. Integrated design of JSCC scheme based on double protograph LDPC codes system. IEEE Commun. Lett. 2019, 23, 218–221. [Google Scholar] [CrossRef]
- Hong, S.; Ke, J.; Wang, L. Global Design of Double Protograph LDPC Codes for Joint Source-Channel Coding. IEEE Commun. Lett. 2023, 14, 424–427. [Google Scholar] [CrossRef]
- Golmohammadi, A.; Mitchell, D.G. Concatenated Spatially Coupled LDPC Codes with Sliding Window Decoding for Joint Source-Channel Coding. IEEE Trans. Commun. 2021, 70, 851–864. [Google Scholar] [CrossRef]
- Djurdjevic, I.; Lin, S.; Abdel-Ghaffar, K. Graph-theoretic construction of low-density parity-check codes. IEEE Commun. Lett. 2003, 7, 171–173. [Google Scholar] [CrossRef]
- Ammar, B.; Honary, B.; Kou, Y.; Xu, J.; Lin, S. Construction of low-density parity-check codes based on balanced incomplete block designs. IEEE Trans. Inf. Theory 2004, 50, 1257–1269. [Google Scholar] [CrossRef]
- Kou, Y.; Lin, S.; Fossorier, M.P. Low-density parity-check codes based on finite geometries: A rediscovery and new results. IEEE Trans. Inf. Theory 2001, 47, 2711–2736. [Google Scholar] [CrossRef] [Green Version]
- Tang, H.; Xu, J.; Kou, Y.; Lin, S.; Abdel-Ghaffar, K. On algebraic construction of Gallager and circulant low density parity-check codes. IEEE Trans. Inf. Theory 2004, 50, 1269–1279. [Google Scholar] [CrossRef]
- Wu, G.; Lv, Y.; He, J. Design of high-rate LDPC codes based on matroid theory. IEEE Commun. Lett. 2019, 23, 2146–2149. [Google Scholar] [CrossRef]
- Hu, X.Y.; Eleftheriou, E.; Arnold, D.M. Regular and irregular progressive edge-growth tanner graphs. IEEE Trans. Inf. Theory 2005, 51, 386–398. [Google Scholar] [CrossRef]
- Divsalar, D.; Dolinar, S.; Jones, C.R.; Andrews, K. Capacity-approaching protograph codes. IEEE J. Sel. Areas Commun. 2009, 2009, 876–888. [Google Scholar] [CrossRef]
- Divsalar, D.; Dolinar, S.; Jones, C. Construction of protograph LDPC codes with linear minimum distance. In Proceedings of the IEEE International Symposium on Information Theory, Seattle, DC, USA, 9–14 July 2006; pp. 664–668. [Google Scholar]



Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Lv, Y.; He, J.; Xu, W.; Wang, L. Design of Low-Density Parity-Check Code Pair for Joint Source-Channel Coding Systems Based on Graph Theory. Entropy 2023, 25, 1189. https://doi.org/10.3390/e25081189
Lv Y, He J, Xu W, Wang L. Design of Low-Density Parity-Check Code Pair for Joint Source-Channel Coding Systems Based on Graph Theory. Entropy. 2023; 25(8):1189. https://doi.org/10.3390/e25081189
Chicago/Turabian StyleLv, Yijie, Jiguang He, Weikai Xu, and Lin Wang. 2023. "Design of Low-Density Parity-Check Code Pair for Joint Source-Channel Coding Systems Based on Graph Theory" Entropy 25, no. 8: 1189. https://doi.org/10.3390/e25081189