Critical Points in the Noiseberg Achievable Region of the Gaussian Z-Interference Channel
Abstract
:1. Introduction
2. Preliminaries
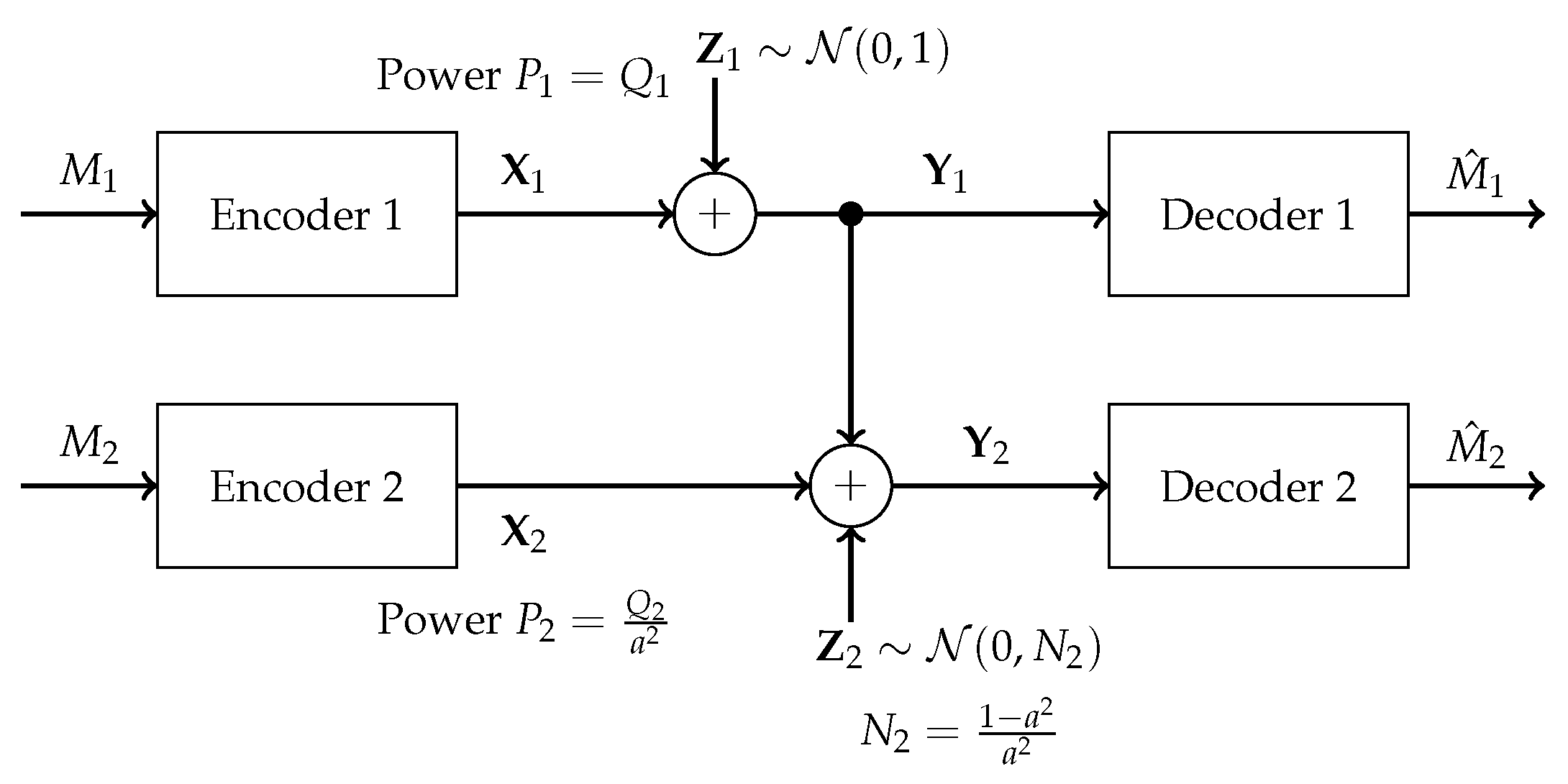
2.1. Noisebergs—A Brief Review
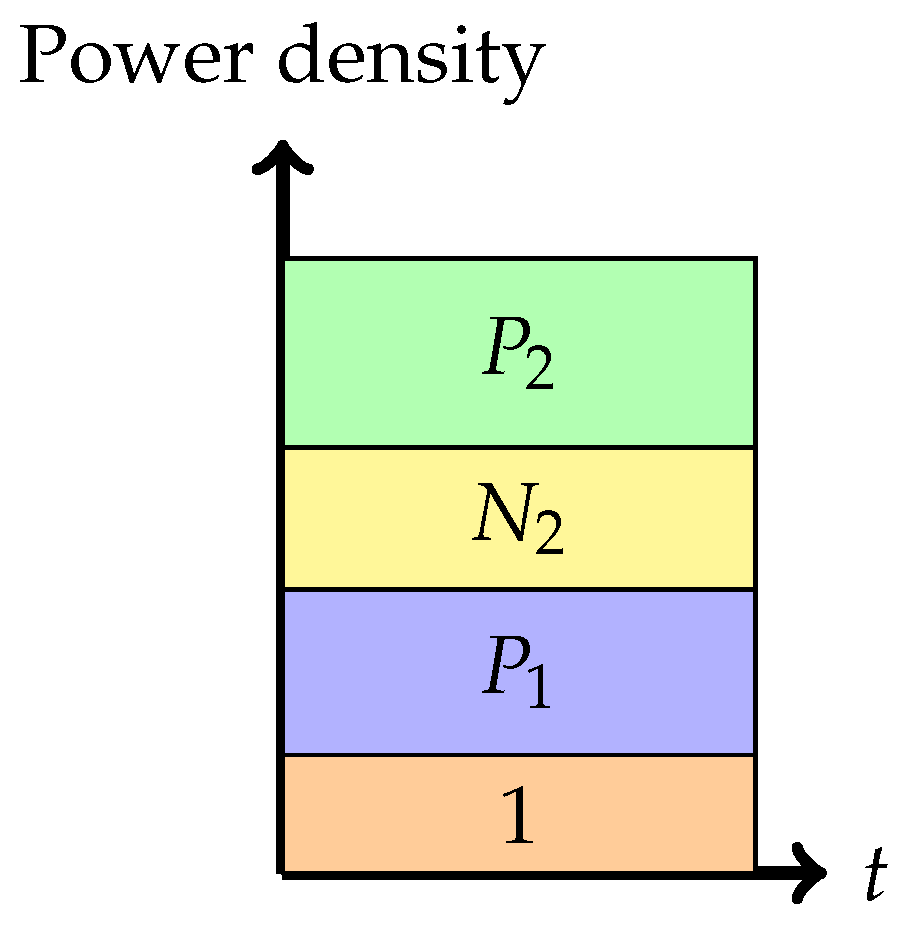
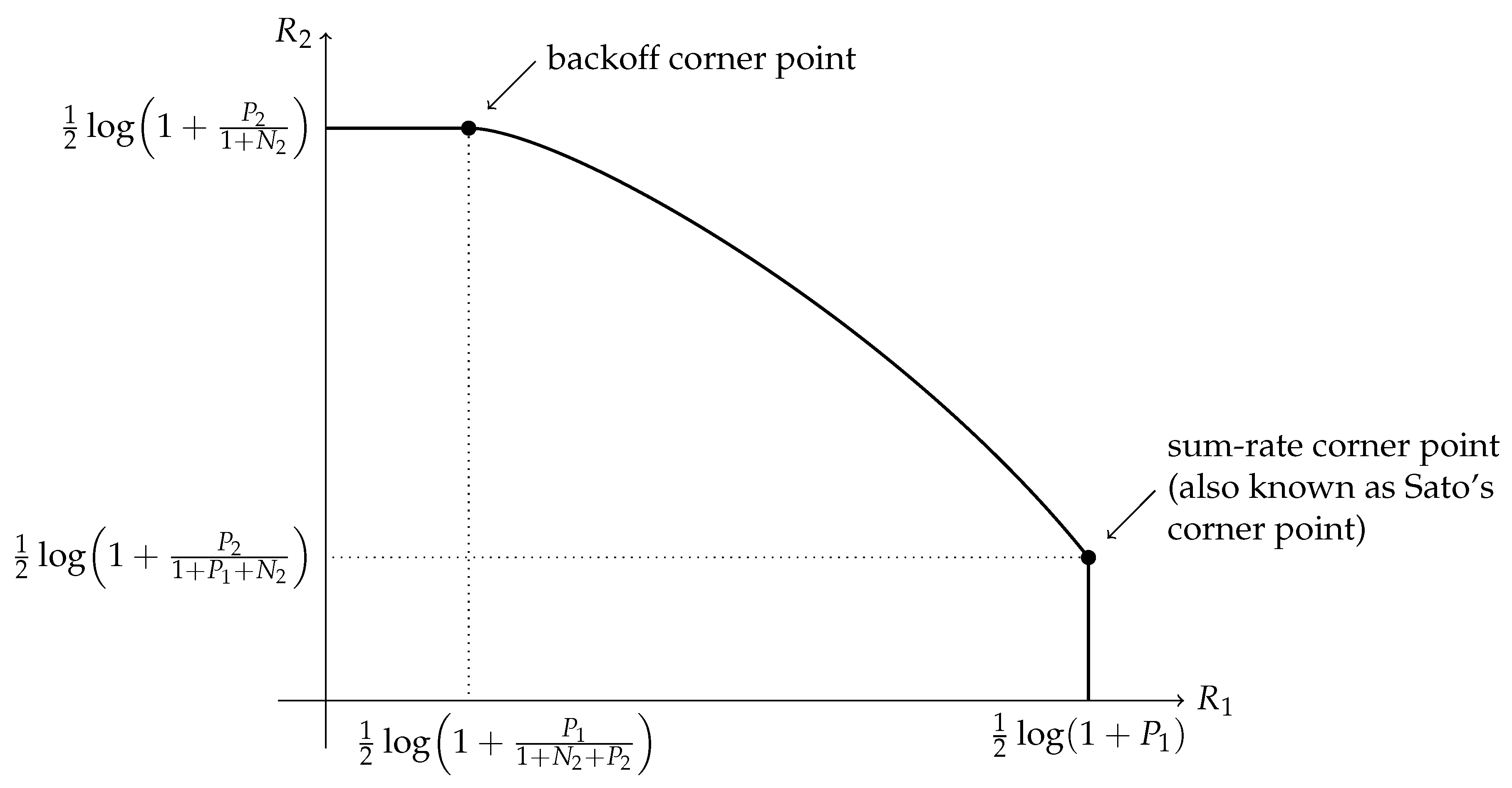
- Phase 1: Treating interference to be noise at the weaker receiver (Sato’s corner point)In this phase, the weaker receiver, , decodes its message by treating as noise. This is depicted pictorially in Figure 4. The decoding order in the picture is assumed to go from top to bottom. Any receiver will decode all the messages on top of its message (including its message) in any band by treating those below it as noise. The rate pair achieved in this phase is
- 2.
- Phase 2: Partial interference cancellation at the weaker receiver (or pure superposition coding)In this phase, the weaker receiver, , decodes a part of first, subtracts this from the received signal, and then decodes its own signal . The rate pair achieved in this phase isNote that . This can be seen as a mix of Phase 1 and Phase 3, to be seen next.
- 3.
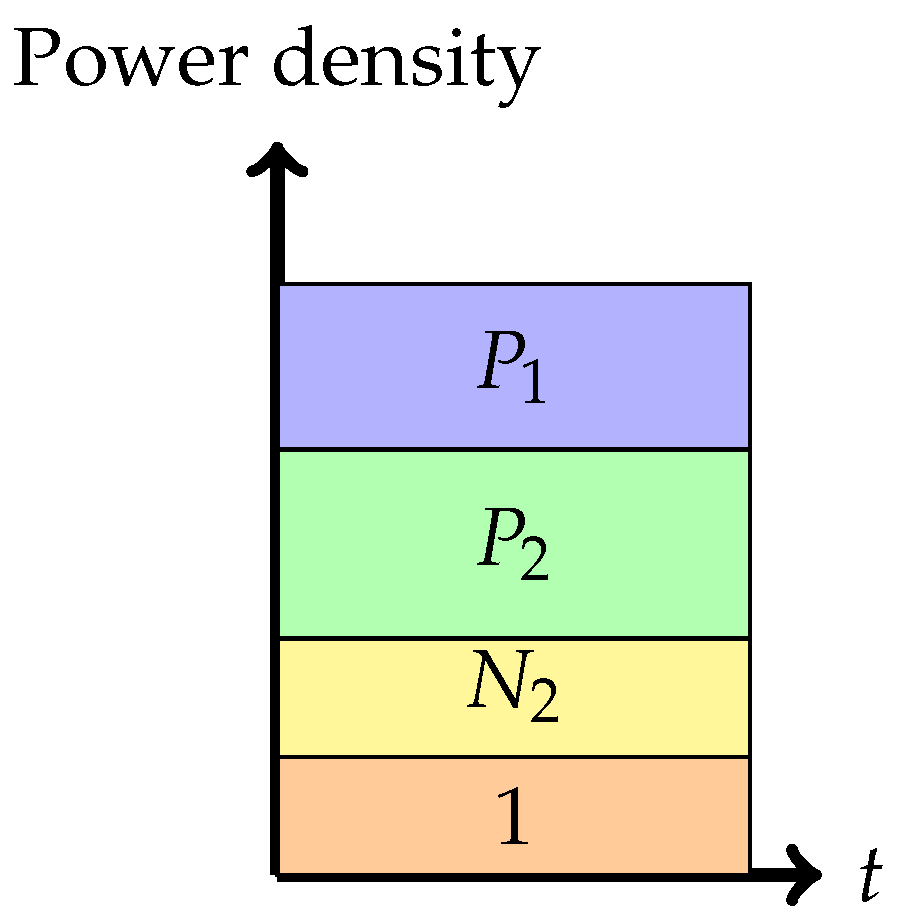
- Phase 3: Interference cancellation at the weaker receiver (the backoff corner point)In this phase, the weaker receiver, , decodes first, subtracts this from the received signal, and finally decodes its own signal . The rate pair achieved in this phase isNote that the rate for message 1 is solely determined by the ability of the weaker decoder to decode it. This encoding strategy is similar to that in a degraded message sets Gaussian broadcast channel where message 1 is meant to be communicated to both receivers.
- 4.
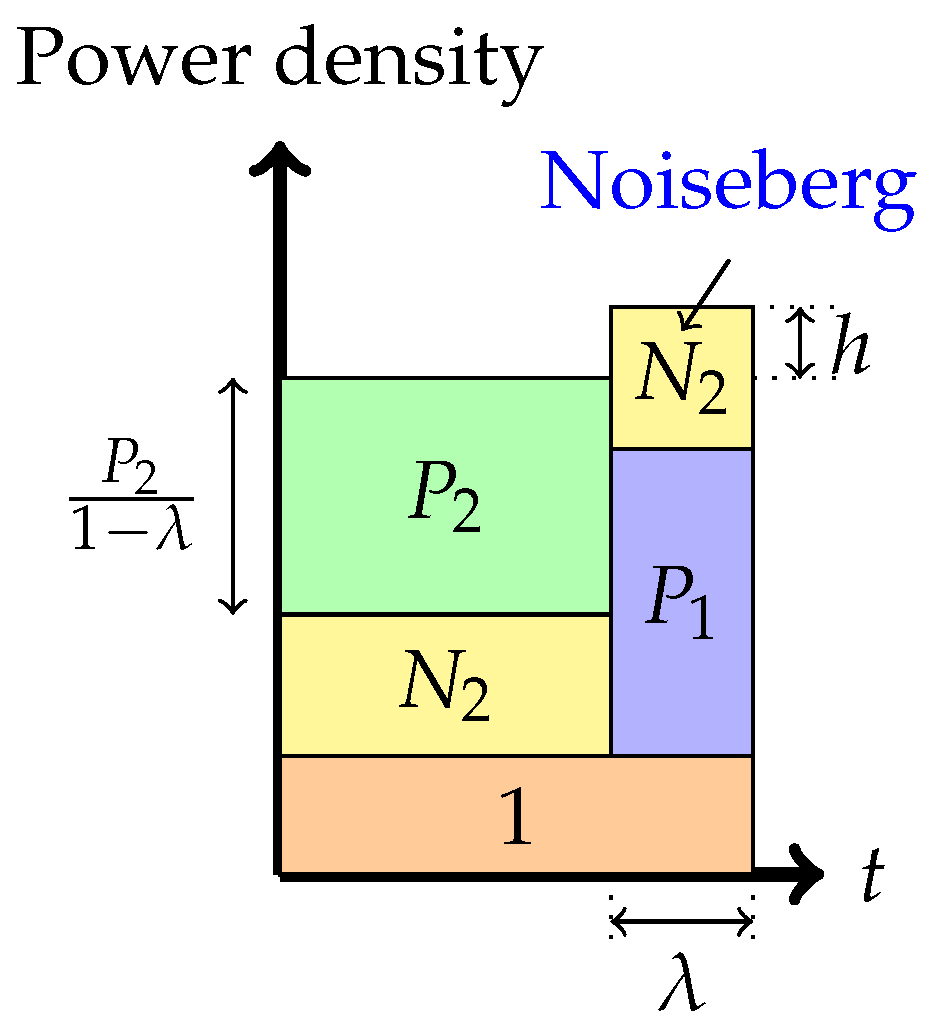
- Phase 4: Time-sharing between the following two strategies: Treating interference to be noise at the weaker receiver and transmitting solely to the stronger receiver (or multiplex strategy)In this phase, there is a time-sharing between two communication schemes. The first scheme, employed for () fraction of the time, employs the Phase 1 strategy, and the second scheme consists of transmission only to the stronger receiver. The total average power in each band is indicated in the figure. Therefore, one must divide the power by the band duration to obtain the height. It is this phase that leads to the noiseberg nomenclature. We denote by h the height difference between the slab in the second band and the power level of in the first band. This height difference comes from part of the noise spectrum of that floats above the signal level in the first band and characterizes what we call a noise-iceberg, or noiseberg. The flotation of the noise slab releases prime-rate space in the power × bandwidth plane, in a fashion that Archimedes would be sure to appreciate. In this phase, we obtain the following:The rate pairs achieved in this scheme arewhere denotes .
- 5.
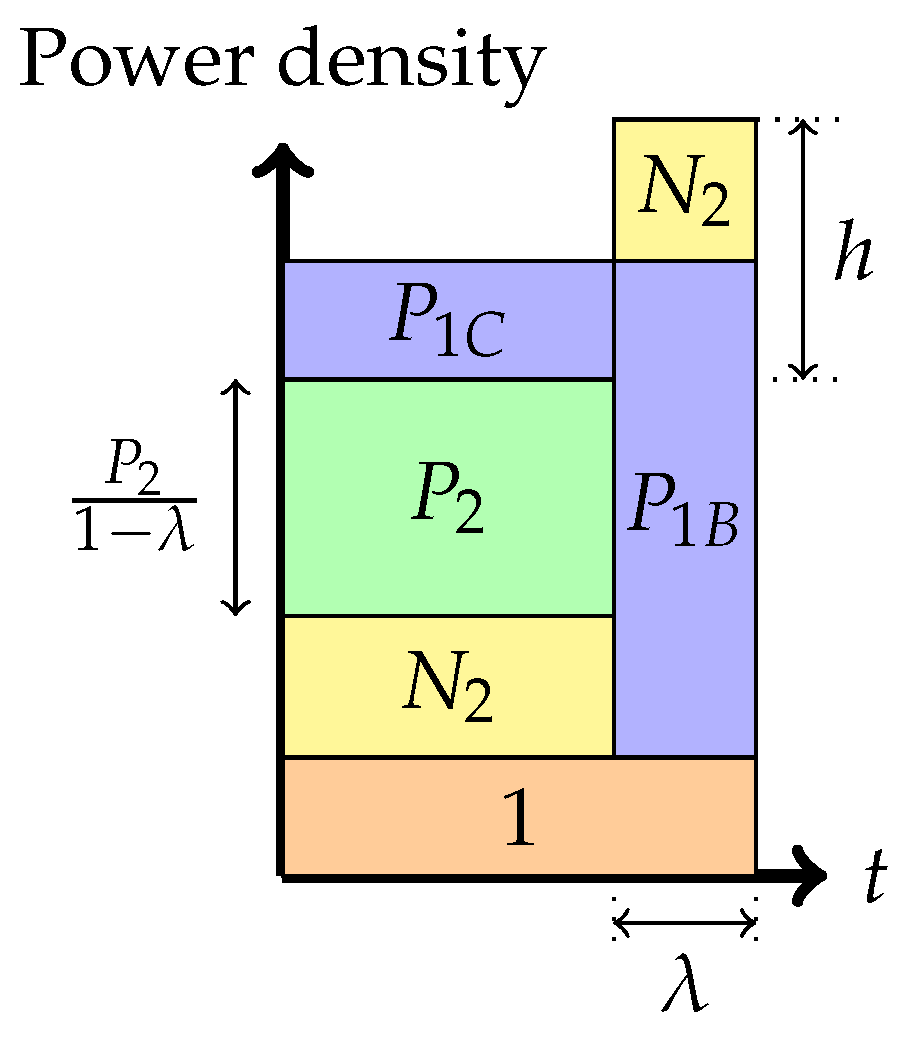
- Phase 5: Time-sharing between the following two strategies: Partial interference cancellation at the weaker receiver and transmitting solely to the stronger receiver (or overflow strategy)In this phase, as before, there is a time-sharing between two communication schemes. The first scheme, employed for () fraction of the time, employs the Phase 2 strategy, and the second scheme consists of transmission only to the stronger receiver. The total average power in each band is indicated in the figure. We denote by h the height difference between the top of the slab in the second band and the power level of in the first band. As argued in [16,24], the total heights of the two signal bands must agree via a water-filling argument.The noise band of height floats above the signal power band in the rightmost strategy. The floating of the noise band frees up prime frequency (or time) space in the spectrum for signal occupation.In this phase, we obtain the following:
- 6.
- Phase 6: Time-sharing between the following two strategies: Interference cancellation at the weaker receiver and transmitting solely to the stronger receiver (top boundary of the admissible parameter region)In this phase, there is also a time-sharing between two communication schemes. The first scheme, employed for () fraction of the time, employs the Phase 3 strategy, and the second scheme consists of transmission only to the stronger receiver. The total average power in each band is indicated in the figure. As in Phase 5, we denote by h the height difference between the top of the slab in the second band and the power level of in the first band. Again, as argued in [16,24], the total heights of the two bands must agree via a water-filling argument. In this phase, we obtain the following:
- 7.
- Phase 7: Time-division between transmitting solely to the two receiversIn this phase, for () fraction of the time, we transmit solely to the weaker receiver, and for fraction of the time, we transmit solely to the stronger receiver. In this phase, we obtain
2.2. The Gaussian Signaling Region
2.2.1. Slopes at the Corner Points
2.2.2. The Intermediate Regime,
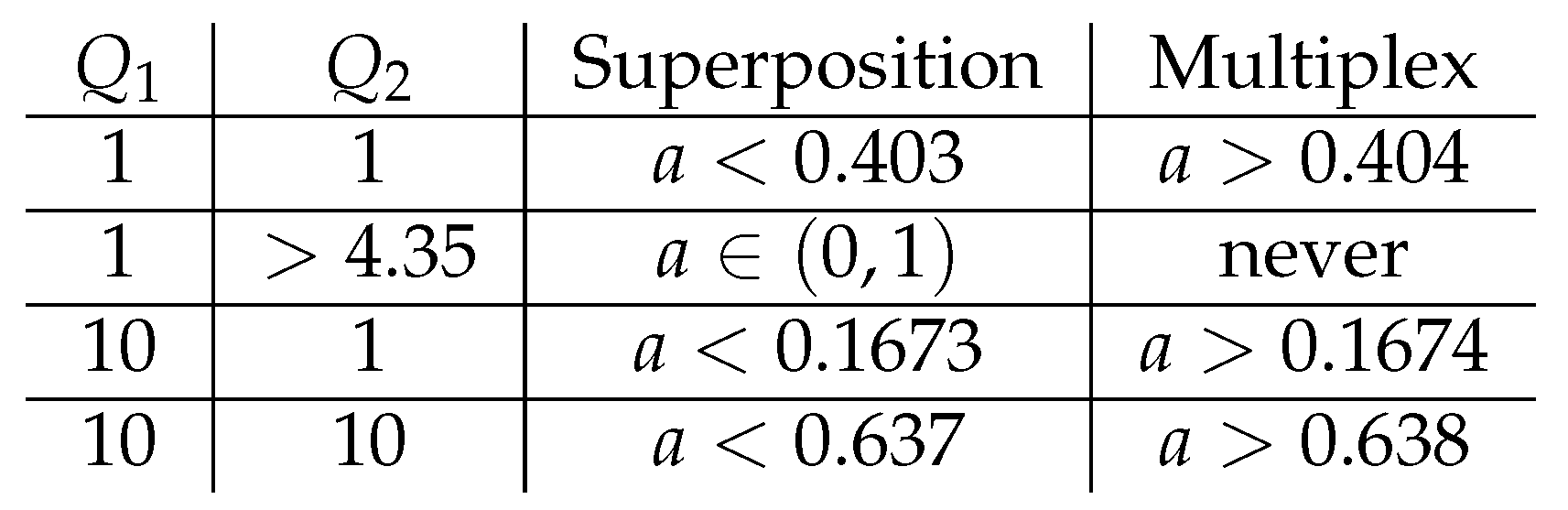
- : This corresponds to the at which is maximized when and . This corresponds to the transition between the multiplex and overflow regions.
- : This corresponds to the at which is maximized when and , in other words . This corresponds to the transition from the multiplex region to the non-naïve time-division region.
- : This corresponds to the at which is maximized when and . This corresponds to the transition from the time-division phase to the overflow region, with .
- : This corresponds to the at which is maximized when and . This corresponds to the transition from the overflow region to a pure superposition coding region.
- : This corresponds to the at which is maximized when and This corresponds to the transition from the interior of the admissible region to the top boundary of this region.
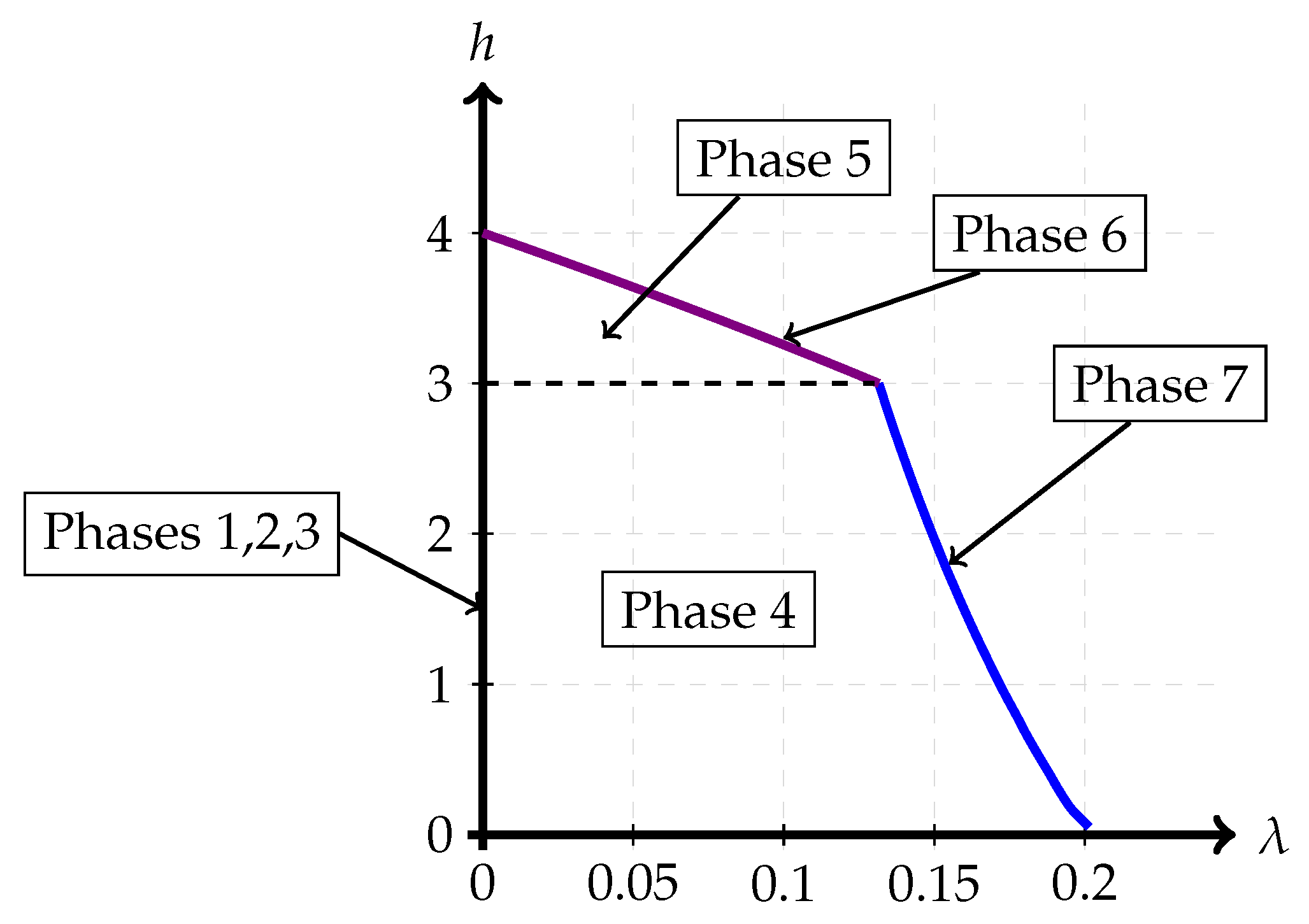
2.2.3. Trajectories in the Phase Space
- 1.
- Path 1: For some set of parameters (for example, ) numerical simulations indicate that the optimal path is Phase 1 → Phase 2 → Phase 3. This is the path of pure superposition evolution, and the locations of the phase transitions occur at and , respectively. This implies that the trajectory in the admissible region is only along the h-axis, i.e., with .
- 2.
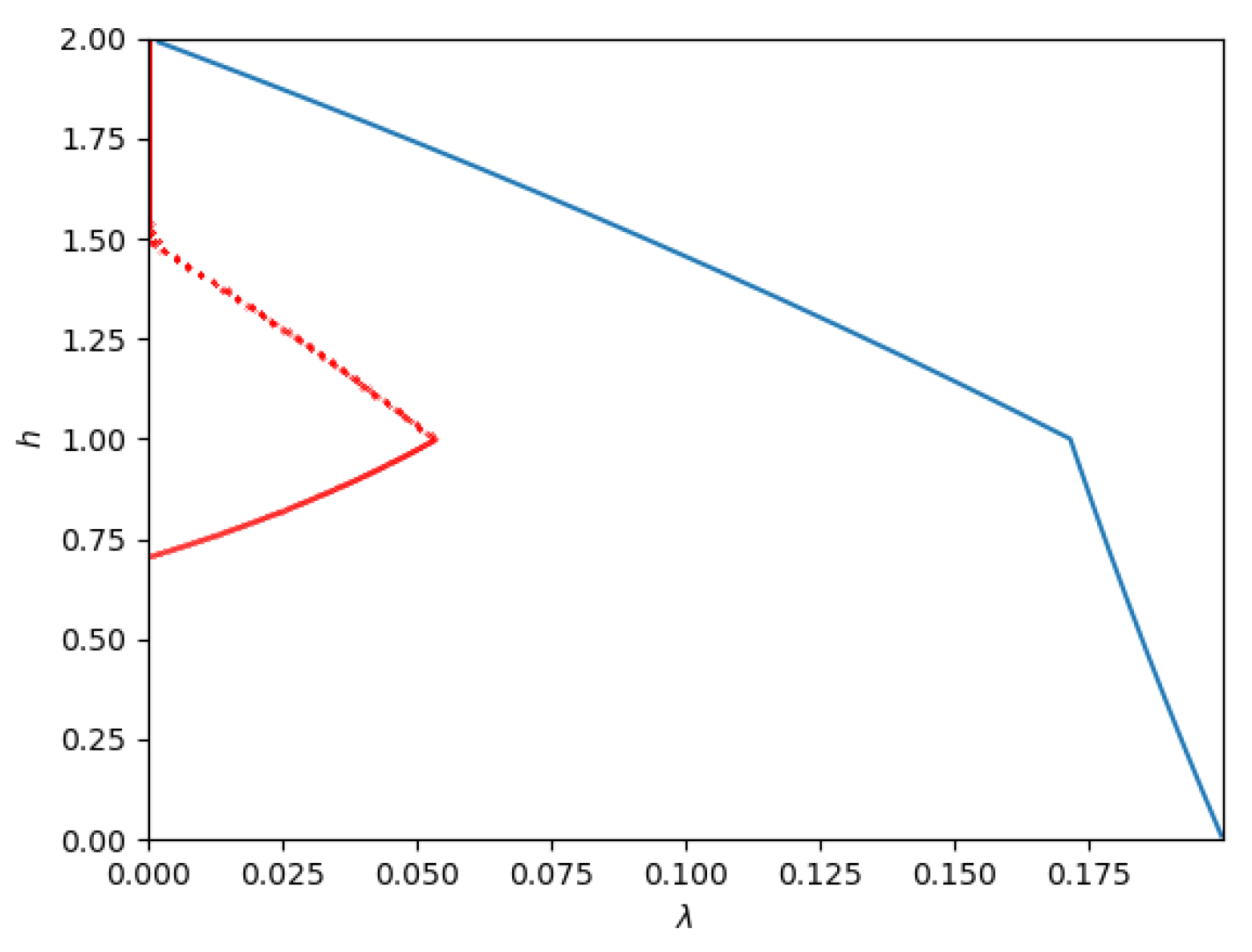
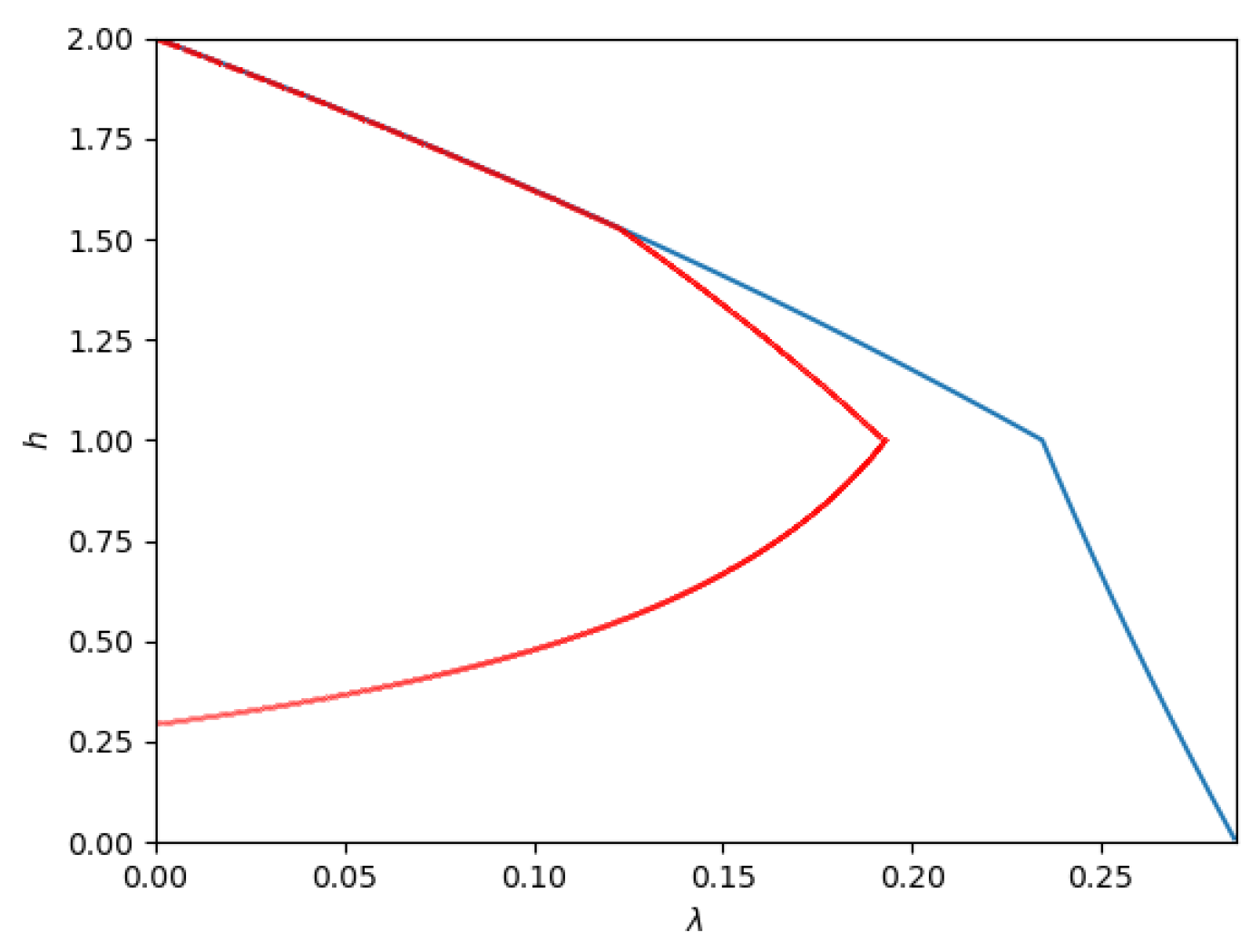
- Path 2: For some set of parameters (for example, ) the optimal path seems to be Phase 1 → Phase 4 → Phase 5 → Phase 2 → Phase 3. The phase transitions occur at (approximately) , , , and , respectively. This path is depicted in Figure 12.As the figure illustrates, it leaves Phase 1 (Sato’s point) and moves into Phase 4. Then, at , it moves from Phase 4 to Phase 5. Then, at , it moves from Phase 5 to Phase 2. Finally, at , the trajectory reaches the other corner point.
- 3.
- Path 3: For some set of parameters (for example ) the optimal path seems to be Phase 1 → Phase 4 → Phase 5 → Phase 6 → Phase 3. The phase transitions occur at (approximately) , , , and respectively.This path is depicted in Figure 13.As the figure illustrates, it leaves Phase 1 (Sato’s point) and moves into Phase 4. Then, at , it moves from Phase 4 to Phase 5. At a slightly larger , it enters Phase 6 and remains there until it reaches the new corner point at Phase 3.
- 4.
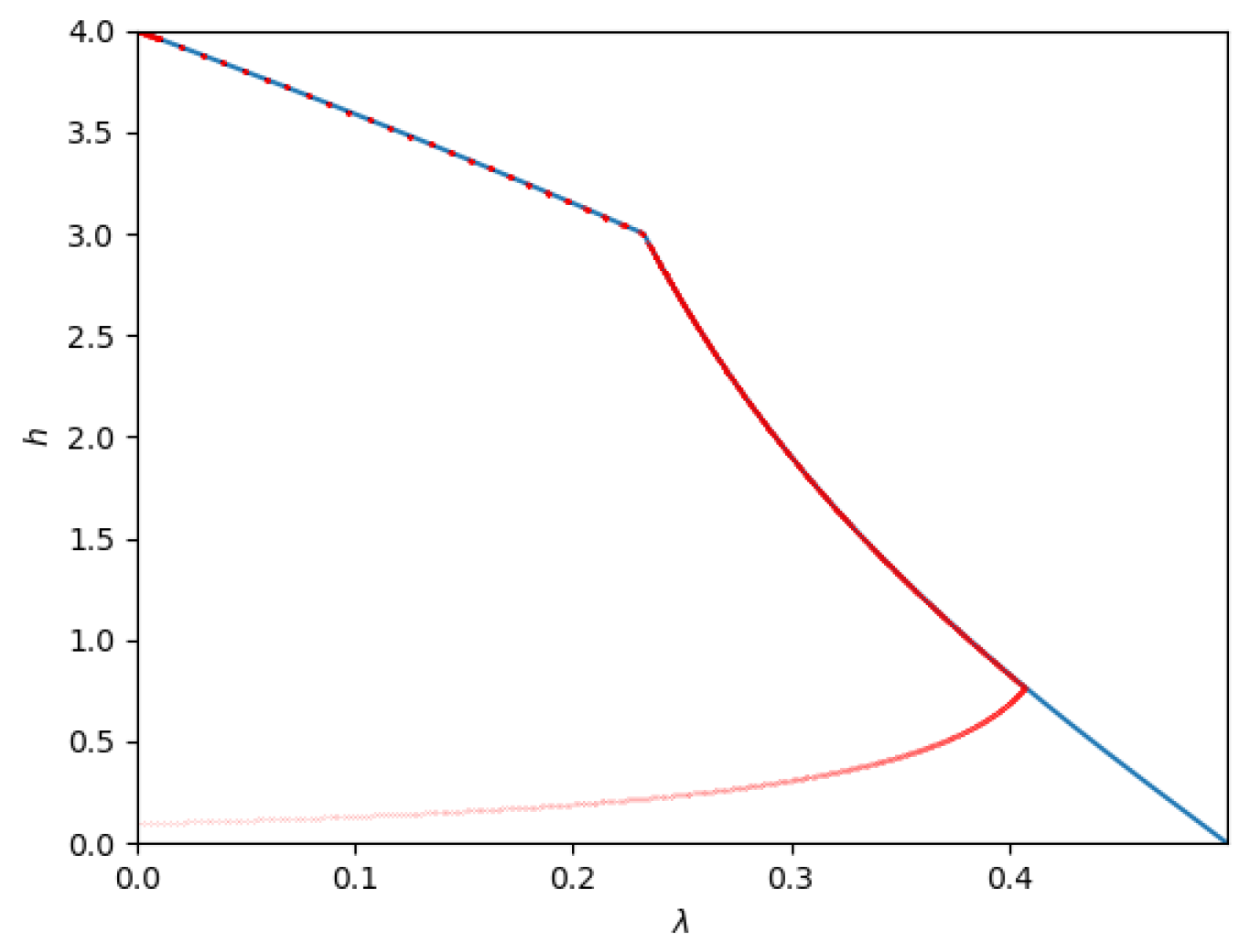
- Path 4: For some set of parameters (for example, ) the optimal path seems to be Phase 1 → Phase 4 → Phase 7 → Phase 6 → Phase 3. The phase transitions occur at (approximately) , , , and , respectively.This path is depicted in Figure 14.
2.3. To Mux or Not to Mux
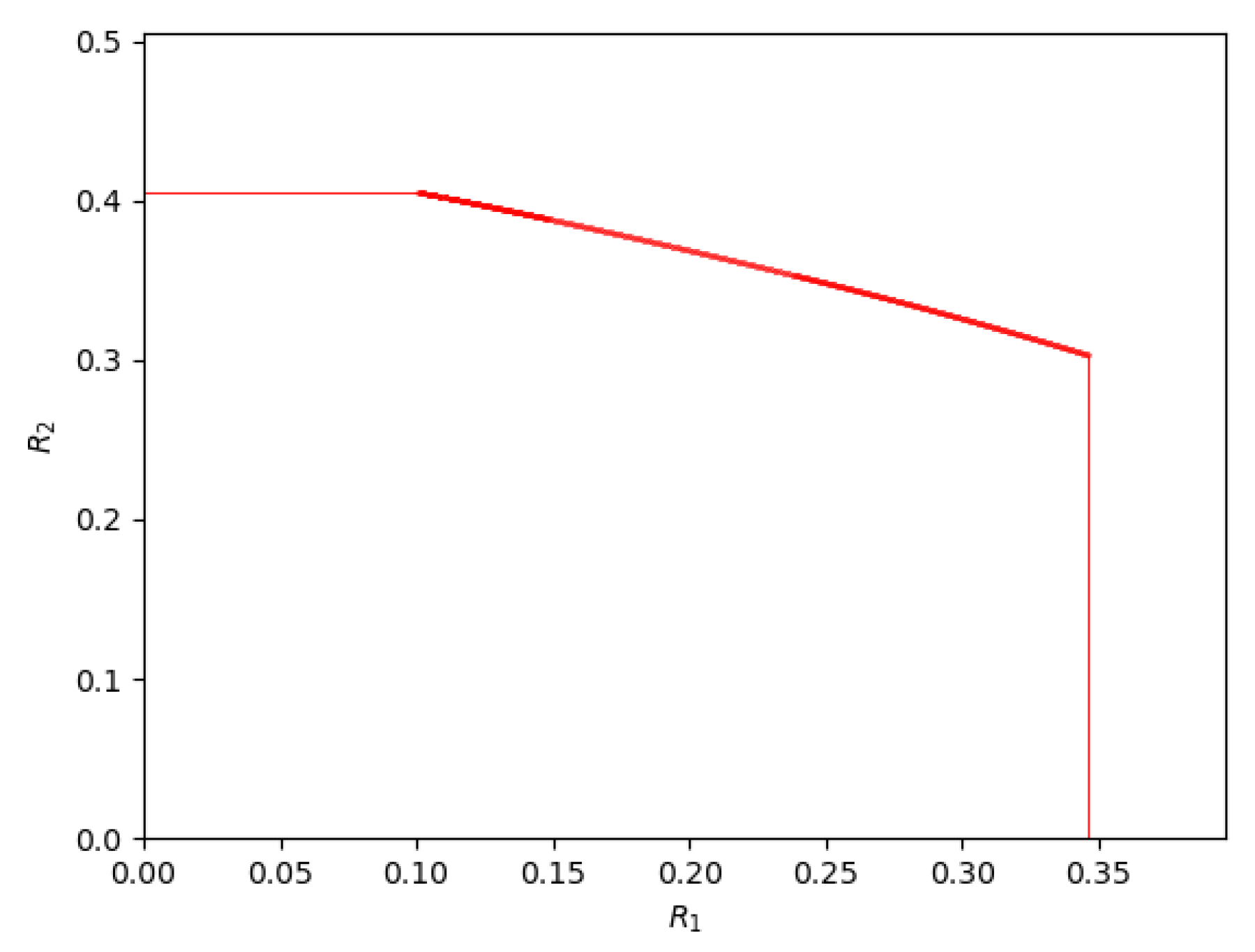
2.4. The Other Critical Points
3. Conclusions
Funding
Institutional Review Board Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Ahlswede, R. The capacity region of a channel with two senders and two receivers. Ann. Probab. 1974, 2, 805–814. [Google Scholar] [CrossRef]
- Carleial, A. A case where interference does not reduce capacity (Corresp.). IEEE Trans. Inf. Theory 1975, 21, 569–570. [Google Scholar] [CrossRef]
- Sato, H. Two-user communication channels. IEEE Trans. Inf. Theory 1977, 23, 295–304. [Google Scholar] [CrossRef]
- Carleial, A. Interference channels. IEEE Trans. Inf. Theory 1978, 24, 60–70. [Google Scholar] [CrossRef]
- Sato, H. On degraded Gaussian two-user channels (Corresp.). IEEE Trans. Inf. Theory 1978, 24, 637–640. [Google Scholar] [CrossRef]
- Han, T.S.; Kobayashi, K. A new achievable rate region for the interference channel. IEEE Trans. Inf. Theory 1981, 27, 49–60. [Google Scholar] [CrossRef]
- Sato, H. The capacity of the Gaussian interference channel under strong interference (Corresp.). IEEE Trans. Inf. Theory 1981, 27, 786–788. [Google Scholar] [CrossRef]
- Costa, M.H.M. On the Gaussian interference channel. IEEE Trans. Inf. Theory 1985, 31, 607–615. [Google Scholar] [CrossRef]
- Kramer, G. Outer bounds on the capacity of Gaussian interference channels. IEEE Trans. Inf. Theory 2004, 50, 581–586. [Google Scholar] [CrossRef]
- Sason, I. On achievable rate regions for the Gaussian interference channel. IEEE Trans. Inf. Theory 2004, 50, 1345–1356. [Google Scholar] [CrossRef]
- Kramer, G. Review of Rate Regions for Interference Channels. In Proceedings of the 2006 International Zurich Seminar on Communications, Zurich, Switzerland, 22–24 February 2006; pp. 162–165. [Google Scholar] [CrossRef]
- Etkin, R.H.; Tse, D.N.C.; Wang, H. Gaussian interference channel capacity to within one bit. IEEE Trans. Inf. Theory 2008, 54, 5534–5562. [Google Scholar] [CrossRef]
- Motahari, A.S.; Khandani, A.K. Capacity bounds for the Gaussian interference channel. IEEE Trans. Inf. Theory 2009, 55, 620–643. [Google Scholar] [CrossRef]
- Shang, X.; Kramer, G.; Chen, B. A new outer bound and the noisy-interference sum-rate capacity for Gaussian interference channels. IEEE Trans. Inf. Theory 2009, 55, 689–699. [Google Scholar] [CrossRef]
- Annapureddy, V.S.; Veeravalli, V.V. Gaussian interference networks: Sum capacity in the low-interference regime and new outer bounds on the capacity region. IEEE Trans. Inf. Theory 2009, 55, 3032–3050. [Google Scholar] [CrossRef]
- Costa, M.H.M. Noisebergs in Z Gaussian interference channels. In Proceedings of the 2011 Information Theory and Applications Workshop (ITA), La Jolla, CA, USA, 6–11 February 2011; pp. 1–6. [Google Scholar] [CrossRef]
- Costa, M.H.M.; Nair, C. On the achievable rate sum for symmetric Gaussian interference channels. In Proceedings of the 2012 Information Theory and Applications Workshop (ITA), San Diego, CA, USA, 5–10 February 2012. [Google Scholar]
- Mehanna, O.; Marcos, J.; Jindal, N. On achievable rates of the two-user symmetric Gaussian interference channel. In Proceedings of the 2010 48th Annual Allerton Conference on Communication, Control, and Computing (Allerton), Monticello, IL, USA, 29 September–1 October 2010; pp. 1273–1279. [Google Scholar] [CrossRef]
- Costa, M.H.M.; Nair, C. Phase transitions in the achievable sum-rate of symmetric Gaussian interference channels. In Proceedings of the 2013 Information Theory and Applications Workshop (ITA), San Diego, CA, USA, 10–15 February 2013; pp. 10–15. [Google Scholar]
- Costa, M.H.M.; Nair, C.; Ng, D.; Wang, Y.N. On the structure of certain non-convex functionals and the Gaussian Z-interference channel. In Proceedings of the 2020 IEEE International Symposium on Information Theory (ISIT), Los Angeles, CA, USA, 21–26 June 2020; pp. 1522–1527. [Google Scholar] [CrossRef]
- Gohari, A.; Nair, C.; Ng, D. An information inequality motivated by the Gaussian Z-interference channel. In Proceedings of the 2021 IEEE International Symposium on Information Theory (ISIT), Melbourne, Australia, 12–20 July 2021. [Google Scholar]
- Gohari, A.; Nair, C.; Zhao, J. On the capacity region of some classes of interference channels. In Proceedings of the 2024 IEEE International Symposium on Information Theory (ISIT), Athens, Greece, 7–12 July 2024; pp. 3136–3141. [Google Scholar] [CrossRef]
- Polyanskiy, Y.; Wu, Y. Wasserstein continuity of entropy and outer bounds for interference channels. arXiv 2015, arXiv:1504.04419. [Google Scholar] [CrossRef]
- Costa, M.H.M.; Gohari, A.; Nair, C.; Ng, D. A Proof of the Noiseberg Conjecture for the Gaussian Z-Interference Channel. In Proceedings of the 2023 IEEE International Symposium on Information Theory (ISIT), Taipei, Taiwan, 25–30 June 2023; pp. 1824–1829. [Google Scholar] [CrossRef]
- Costa, M.H.M. A third critical point in the achievable region of the Z-Gaussian interference channel. In Proceedings of the 2014 Information Theory and Applications Workshop (ITA), San Diego, CA, USA, 9–14 February 2014. [Google Scholar]
- Polyanskiy, Y.; Wu, Y. Wasserstein continuity of entropy and outer bounds for interference channels. IEEE Trans. Inf. Theory 2016, 62, 3992–4002. [Google Scholar] [CrossRef]
- Gohari, A.; Nair, C. Outer bounds for multiuser settings: The auxiliary receiver approach. IEEE Trans. Inf. Theory 2022, 68, 701–736. [Google Scholar] [CrossRef]
- Costa, M.H.M.; Nair, C.; Ng, D. On the Gaussian Z-interference channel. In Proceedings of the 2017 Information Theory and Applications Workshop (ITA), San Diego, CA, USA, 12–17 February 2017; pp. 1–15. [Google Scholar] [CrossRef]
- Costa, M.H.M.; Nair, C. Gaussian Z-interference channel: Around the corner. In Proceedings of the 2016 Information Theory and Applications Workshop (ITA), La Jolla, CA, USA, 31 January–5 February 2016; pp. 1–6. [Google Scholar] [CrossRef]
- Sason, I. On the corner points of the capacity region of a two-user Gaussian interference channel. IEEE Trans. Inf. Theory 2015, 61, 3682–3697. [Google Scholar] [CrossRef]
- Beigi, S.; Liu, S.; Nair, C.; Yazdanpanah, M. Some results on the scalar Gaussian interference channel. In Proceedings of the IEEE International Symposium on Information Theory (ISIT), Barcelona, Spain, 10–15 July 2016; pp. 2199–2203. [Google Scholar] [CrossRef]
- Ng, W.H. On Gaussian Extremizers for the Capacity Region of the Gaussian Interference Channel. Ph.D. Thesis, The Chinese University of Hong Kong, Hong Kong, China, 2021. [Google Scholar]

Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Costa, M.H.M.; Nair, C.; Ng, D. Critical Points in the Noiseberg Achievable Region of the Gaussian Z-Interference Channel. Entropy 2024, 26, 898. https://doi.org/10.3390/e26110898
Costa MHM, Nair C, Ng D. Critical Points in the Noiseberg Achievable Region of the Gaussian Z-Interference Channel. Entropy. 2024; 26(11):898. https://doi.org/10.3390/e26110898
Chicago/Turabian StyleCosta, Max H. M., Chandra Nair, and David Ng. 2024. "Critical Points in the Noiseberg Achievable Region of the Gaussian Z-Interference Channel" Entropy 26, no. 11: 898. https://doi.org/10.3390/e26110898
APA StyleCosta, M. H. M., Nair, C., & Ng, D. (2024). Critical Points in the Noiseberg Achievable Region of the Gaussian Z-Interference Channel. Entropy, 26(11), 898. https://doi.org/10.3390/e26110898