Abstract
Remote data backup technology avoids the risk of data loss and tampering, and has higher security compared to local data backup solutions. However, the data transmission channel for remote data backup is not secure, and the backup server cannot be fully trusted, so users usually encrypt the data before uploading it to the remote server. As a result, how to protect this encryption key is crucial. We design a User-Centric Design (UCD) data backup scheme based on multi-factor authentication to protect this encryption key. Our scheme utilizes a secret sharing scheme to divide the encryption key into three parts, which are stored in the laptop, the smart card, and the server. The encryption key can be easily reconstructed from any two parts with user’s private information password, identity and biometrics. As long as the biometrics has enough entropy, our scheme can resist replay attacks, impersonation user attacks, impersonation server attacks, malicious servers and offline password guessing attacks.
1. Introduction
In recent years, cloud computing technology has developed rapidly, and remote cloud storage services have been widely applied due to their higher security and scalability [1]. However, there is still a risk of data leakage during the data transmission to remote servers [2]. Therefore, people usually encrypt data before transmitting them, such as by using an AES encryption algorithm [3]. In this way, even if the data are leaked, the adversary cannot recover the plaintext. Usually, users store their encryption key in devices such as USBs and laptops, but these devices pose a risk of theft and tampering. Once the storage device is stolen or tampered with, the key will be leaked or lost. How to securely protect the encryption key is the core of remote cloud storage.
By using a -threshold secret sharing scheme, people can split the encryption key into n shares, and store the n shares in different devices. As long as the user obtains t shares, the user can reconstruct the encryption key. If the shares are stored in devices in plain text, once t devices are corrupt, the encryption key is leaked.
Chang et al. [4] proposed a data protection scheme based on Shamir’s -threshold secret sharing scheme to protect sensitive data. In their scheme, the server chooses the encryption key, and divides the key into three shares, which are stored in the laptop, the USB device, and the server, respectively. The user can reconstruct the key on the laptop with the help of the USB offline after the user obtains the authentication of the USB device via their identity and password. If the USB or laptop is unavailable, the user can reconstruct the key through the interaction of the laptop or USB device with the server online after the user obtains the authentication of the server. However, since the encryption key is chosen by the server, it requires the server to be fully trustable. This is infeasible in reality.
To solve the problem in Chang et al’s scheme, Liu et al. [5] proposed a user-centered design (UCD) data backup scheme. In their scheme, the encryption key is chosen by the data owner rather than the server. Similar to Chang et al.’s scheme, using Shamir’s -threshold secret sharing scheme, the encryption key is divided into three shares. The user stores the three shares in the laptop, the smart card, and the server, respectively. Whenever the user needs to encrypt/decrypt data, they can reconstruct the key with two of the three devices and their identity, password, and biometrics.
Hu et al. [6] found that the design of Liu et al.’s scheme in the authentication phase is unreasonable, as their scheme can not resist offline password-guessing attacks, server/user camouflage attacks, and so on. Then, Hu et al. presented an enhanced secure data backup scheme to overcome all above-mentioned security threats.
In 2023, Yi et al. [7] found that Hu et al.’s scheme cannot achieve their claimed security. Their scheme could not resist offline guessing attacks, replay attacks, and denial of service attacks. They also did not consider the situation of users rebuilding an incorrect key. Then, Yi et al. proposed an enhanced scheme to address the aforementioned issues. Yi et al. constructed an enhanced data backup scheme based on Shamir’s -threshold secret sharing scheme, a message authentication code, and a robust fuzzy extractor. In their scheme, the user chooses the encryption key. Then, by Shamir’s -threshold secret sharing scheme, the user divides the encryption key into three shares. The user computes pseudoshares using their private information such as identity, password, and biometrics and stores the three pseudoshares in the laptop, the smart card, and the server, respectively. Whenever the user needs to encrypt/decrypt data, he can reconstruct the key if he gets access to two of the three devices and types the correct private information (identity, password, and biometrics) to pass the multi-factor authentication.
In Yi et al.’s scheme, if the smart card/laptop is unavailable, the user needs to connect their laptop/smart card to the server and provides the valid identity, password, and biometrics to pass the authentication of the server. After the authentication phase, a session key is established between the user and the server. Then, the server uses the session key to encrypt the pseudoshare () stored on the server. Finally, the user obtains two shares and performs the recovery phase to reconstruct the encryption key.
Establishing a session key and using the session key to encrypt the pseudoshare involves more hash computations and more communication rounds between the laptop/smart card and the server.
We are wondering, can we reduce the hash computations and communication rounds between the laptop/smart card and the server?
Our Contribution. We answer the above question in the affirmative. We propose a data backup scheme which inherits the advantages of Yi et al.’s scheme while having higher execution efficiency. More precisely, our contributions are as follows:
- We propose a data backup scheme which fixes two encryption keys and shared between the laptop and the server, and the smart card and the server, respectively, during the registration phase. In this way, we can reduce ten hash computations and one round communication in the authentication phase, which improves the execution efficiency of our scheme. We recall that, in Yi et al.’s scheme, there are two communication rounds between the laptop/smart card and the server. This means that we have reduced the number of communication rounds by 50%.
- In addition, our scheme also enjoys other benefits, such as reducing two hash computations and four hash computations during the registration phase and the updating phase, respectively.
- We give the security analysis and performance evaluation of our new data backup scheme, which shows that our new scheme enjoys the same security of previous papers and has a higher execution efficiency.
1.1. Related Work
1.1.1. Key Management
Key management is one of the core issues in the field of cryptography, defined as a set of techniques and processes that enable the establishment and maintenance of encrypted key relationships between authorized parties. Under certain security policy controls, it completes the entire process from key generation to final destruction, including key generation, storage, distribution, use, backup, recovery, update, revocation, and destruction. According to their different characteristics, key management can be mainly divided into the following categories.
- Dynamic and Static Key Management
Static management adopts the principle of key pre-allocation, which ensures that the keys allocated to each participant throughout the entire lifecycle of the network are fixed. In this way, the key usage time is longer and the probability of being attacked significantly increases. On the contrary, in dynamic key management, encryption keys are updated throughout the entire network lifecycle, which significantly improves the security and lifecycle of the system.
- Centralized and Distributed Key Management
Centralized key management refers to a single central node responsible for generating, distributing, and updating encryption keys or session keys used by nodes in the system. Xu et al. proposed a key management scheme based on multi-party joint management [8], which uses an authoritative key generation center and multiple ordinary key generation centers to work together to generate keys. The addition of the authoritative center avoids the problem of malicious nodes randomly modifying selected strings to steal multiple user private keys. The advantage of centralized key management schemes is lower computational and transmission overhead, but it requires a trusted third party to act as the key generation center (KGC) and establish paired shared keys with each user during the registration phase.
In distributed key management, there is no clear key generation center, which can reduce dependence on central entities. Xu et al. [9] proposed a decentralized key management scheme based on a dynamic trust model, which does not require centralized or pre-established trust institutions and introduces three subsystems to integrate dynamic trust and key management. Zheng et al. [10] proposed a decentralized key management scheme based on secret sharing, which divides the key into multiple sub-keys and shares and distributes them to multiple nodes. Multiple nodes jointly maintain one key without a central node. In distributed key management, although the dependence on central entities is reduced, the resources of nodes are limited, and most schemes suffer from overly complex key algorithms and excessive resource consumption.
- Symmetric and Asymmetric Key Management
Symmetric key schemes refer to encryption techniques where both parties use the same pair of keys for encryption and decryption, with DES, 3DES, and AES algorithms being the main representatives. Symmetric key schemes have a high speed in encryption and decryption, and can improve the difficulty of information cracking by using long keys. However, the distribution of symmetric keys requires a strictly secure channel, which is difficult to guarantee. Moreover, all nodes that require communication need different key pairs, making the key distribution very difficult in large-scale networks.
Asymmetric key schemes use publicly available public keys and confidential private keys as encryption and decryption key pairs, which have high security and low storage requirements, and better meet the needs of identity authentication in networks. However, asymmetric encryption has lower encryption efficiency and is often combined with symmetric encryption algorithms to form a hybrid encryption scheme that balances security and efficiency.
Many scholars have proposed a series of key negotiation protocols. In 2014, Yang et al. [11] proposed a three-party authentication key protocol for smart cards, which was later proven by Park [12] to be unable to resist offline password-guessing attacks and internal privilege attacks. In 2017, Jiang et al. [13] proposed a three-factor lightweight authentication and key negotiation protocol for wireless sensor networks, but their scheme lacks perfect forward security, resistance to impersonation attacks, and message integrity.
1.1.2. Secure Multi-Party Computation
The basic idea of secure multi-party computation (MPC) was first introduced by Yao in 1982 in the “Millionaire” problem [14]. Afterwards, Goldreich, Micali, and Wigderson [15] extended two-party computation to multi-party computation and provided a security definition for secure multi-party computation. Generally speaking, secure multi-party computation allows a group of untrusted data holders to jointly calculate a predetermined function using their respective secret data as input without relying on any third party. This makes it possible to use secure multi-party computation to build privacy protection applications. The basic cryptographic primitives involved in MPC mainly include Oblivion Transfer (OT), Garbled Circuit (GC), secret sharing (SS), and so on. We mainly introduce the work related to secret sharing.
The secret sharing scheme is a protocol that securely distributes secret information to a certain group of users. Secret sharing can divide secret information into multiple parts and hand them over to different participants, each of whom can only obtain a portion of the information. Only when some participants collaborate together can the complete secret information be recovered. The linear secret sharing scheme (LSSS) refers to a sharing protocol in which a group of users can restore their own shares to their original secret values solely through linear operations. At present, research on secure multi-party computation based on secret sharing mainly focuses on linear secret sharing schemes.
The secret sharing scheme was initially independently proposed by Shamir and Blakley in 1979. The former was constructed based on interpolation polynomials [16], while the latter was based on hyperplane geometry [17]. Subsequently, more threshold secret sharing schemes were proposed, and their properties were continuously improved and strengthened through discussions. The BGW protocol [18] is a classic secure multi-party computation protocol constructed based on the secret sharing protocol. Ben Or and Rabinz [19] proposed the verifiable secret sharing scheme in 1989 and constructed a secure multi-party computation protocol based on it that includes an honest majority of participants.
1.1.3. Multi-Factor Authentication
The existing identity authentication protocols include three basic authentication factors [20]:
- Knowledge factors: what the user knows (such as passwords or PINs);
- Ownership factors: things owned by the user (such as tokens, smart cards, or smartphones);
- Biometric factors: the user’s biometrics (such as fingerprints or iris).
These three basic authentication factors can be used alone or in combination to form an identity authentication system.
Password-based authentication technology began in the 1970s, where the user’s identity and password were stored in the server’s authentication table, which was directly compared with the information on the authentication table when the user logged in. In 1981, Lamport [21] first proposed a password authentication scheme for non-secure channels. Subsequent solutions have been improved in terms of security, computational cost, and effectiveness [22,23,24]. These schemes are easy to implement, but the disadvantage is that the server needs to maintain a password table. Chen Ku [25] pointed out that they are vulnerable to verification table leakage attacks. In 1989, Harn, Huang, and Laih [26] proposed a password authentication scheme based on the public key encryption system. In this scheme, the Diffie Hellman public key [27] encryption technology is used, and the server no longer needs to protect the password table.
With the development of smart cards, people are beginning to attempt to combine smart cards with passwords to address the shortcomings of single-factor authentication schemes. In 1991, Chang and Wu [28] proposed a dual-factor identity authentication protocol based on the Chinese remainder theorem using smart cards. Afterwards, many scholars [29,30,31] conducted extensive research on this dual-factor identity authentication protocol. However, none of these schemes have achieved their claimed security, and dual-factor identity authentication schemes are easily vulnerable to existing internal attacks, anonymity attacks, and other attacks. Particularly, due to the inherent characteristics of smart cards, many schemes are unable to resist the loss of smart cards [32,33].
The emergence of biometric recognition technology has provided a new breakthrough point for identity authentication. Biometrics have many characteristics such as universality, uniqueness, and stability, which provide a more reliable and convenient way of identity verification. In 2002, Lee et al. [34] proposed an identity authentication protocol based on fingerprints and smart cards, which first applied three-factor authentication technology to remote identity authentication protocols. However, biometric technology also has some drawbacks, as users’ biometric information, such as fingerprints, can be easily obtained by adversaries. Furthermore, it is difficult for users to modify their biometric information. Therefore, many protocols [35,36,37] store hashed or encrypted biometric data, rather than the biometric information itself. However, this method is still unrealistic because the recognition data of biometric information are noisy, and the hash function is very sensitive to the input, which can lead to users being unable to successfully complete identity authentication themselves. Fortunately, Dodis et al. [38] proposed the concept of a fuzzy extractor in 2004, which can effectively address this issue.
Nowadays, a multi-factor authentication design for different systems and application scenarios has been widely studied and applied [39,40,41,42,43,44]. For example, Odyuo et al. [39] suggested a novel authentication algorithm based on device serialization and digital signature authentication. According to the suggested approach, a device will only be permitted access to the network if it has successfully completed multi-factor authentication; otherwise, the authentication procedure will fail and must be repeated from scratch. Braeken et al. [40] presented an authentication and key agreement protocol for users who want to have access to constrained sensor nodes deployed in the field, e.g., a doctor with healthcare nodes of a patient. In their protocol, both the sensor and user device provide direct multi-factor authentication relying on physical unclonable functions and biometrics, respectively. In [41], Mostafa et al. proposed an adaptive multi-factor multi-layer authentication framework that embeds an access control and intrusion detection mechanisms with an automated selection of authentication methods. They implemented multiple authentication factors through the user’s geographical location and browser confirmation method that enhance the identity verification of cloud users.
The arrangement of this article is as follows: Section 2 introduces the model of the scheme and some basic tools. In Section 3, we analyze the execution efficiency of Yi et al.’s scheme. In Section 4, we systematically introduce proposed scheme. In Section 5, we conduct a security analysis of the proposed scheme. In addition, we also compare the performance with the scheme proposed by Yi et al. Finally, we provide the conclusion in Section 6.
2. Preliminaries
In this chapter, we will first introduce some basic tools used in this paper, and then, we will introduce the model of our scheme. A brief review of Yi et al.’s scheme is given in Appendix A.
Table 1 summarizes the key abbreviations used throughout this paper for ease of reference.

Table 1.
The main abbreviation used in the paper.
2.1. Shamir’s (t-n) Threshold Secret Sharing Scheme
Shamir’s threshold secret sharing scheme is based on the Lagrange interpolation method. It splits the secret s and shares it with n participants. As long as at least t participants cooperate, the secret s can be reconstructed. However, as long as there are fewer than t participants cooperating, no information about the secret s can be obtained. Shamir’s threshold secret sharing scheme includes the following phases:
- PreparationLet be a finite field (p is a large odd prime number and ; n is the number of participants), is the shared secret, and at least out of the n participants are required to reconstruct s.
- Secret sharingFirstly, the secret dealer independently selects elements , and then constructs a polynomial of degree as follows:where Equation (1) satisfies and .Then, the dealer randomly selects n different non-zero elements , and computes for . The share is given to the corresponding participant .
- Secret reconstructionWe assume that the combiner receives t shares ; the polynomial can be reconstructed byand then the secret s can be recovered, since: .
2.2. Fuzzy Extractor
A fuzzy extractor can extract a random string R from noisy random data with enough entropy, such as biometrics. The extracted random string R can be used as the private key or random numbers in the cryptosystem. With the helper string P, it can reproduce the same R from biometric templates and , in case is sufficiently close to .
Definition 1
(Metric spaces). A metric space is a set with a distance function . For all , the distance function should satisfy the following conditions:
- 1.
- Reflexivity: = 0 if and only if ;
- 2.
- Symmetry: ;
- 3.
- Triangle inequality: .
Definition 2
(Min-entropy). For a random variable X, the min-entropy of X, denoted by , is defined by
Definition 3
where and denotes the uniform distribution on ℓ-bit binary strings.
(Robust fuzzy extractor). A robust fuzzy extractor FE consists of two probabilistic polynomial-time algorithms . They are described as follows:
- . It takes biometrics as input, and outputs an extracted random string and an auxiliary string P.
- . The reproduction algorithm takes P and as inputs, and outputs an extracted string R.
- Correctness: If , then, for all , it holds that .
- Security: Let W be a distribution on , if , then, for all PPT adversaries ,
Furthermore, these two algorithms satisfy Equation (5) when adversary involves the following game: : Compute and ,
2.3. Message Authentication Code
Definition 4
(Message authentication code). A message authentication code consists of three probabilistic polynomial-time algorithms . They are described as follows:
- : it takes a security parameter as input and outputs a key .
- : it takes a key k and a message as inputs, and outputs a tag t.
- : it takes a key k, a message m, and a tag t as inputs, and outputs a bit b; means valid and means invalid.
For every n, every , and every , it satisfies the following equation:
Definition 5
(Existentially unforgeable under an adaptive chosen-message attack). A message authentication code is existentially unforgeable under an adaptive chosen-message attack, if, for all probabilistic polynomial-time adversaries , the message authentication code satisfies the following equation:
where the experiment is defined as follows:
- A random key is chosen.
- The adversary is given oracle access to and outputs a pair . Formally, . Let Q denote the queries asked by during the execution.
- The output of the experiment is defined to be 1 if and only if and .
2.4. Model of Our Scheme
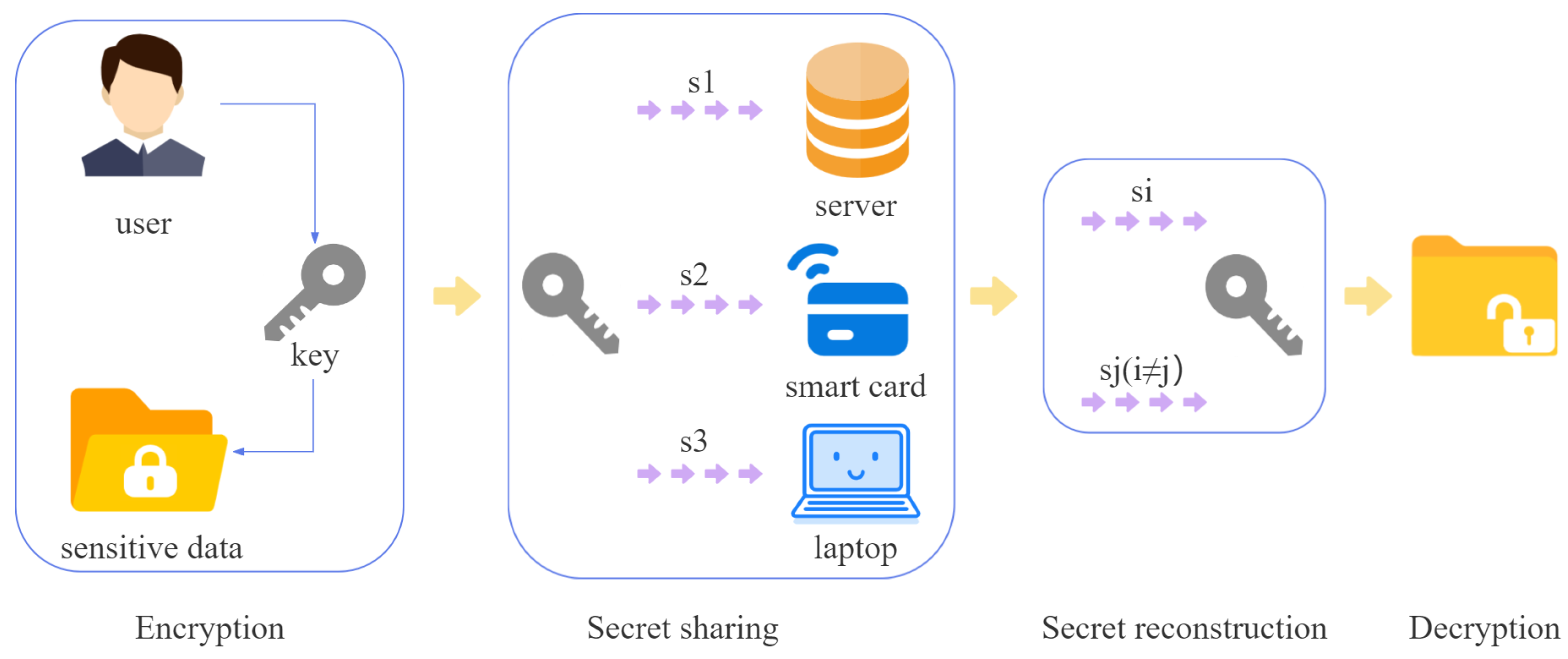
Like the scheme proposed by Yi et al., in our model, the user first selects a private key k to encrypt the sensitive data, then the user shares the private key k among the laptop, the smart card, and the server through Shamir’s (2,3) threshold secret sharing scheme. The private key k will be destroyed after the share generation. The user can recover the private key from any two shares using the Lagrange interpolation method. Our scheme mainly focuses on the secret sharing and secret reconstruction phase.
The specific process is shown in Figure 1.
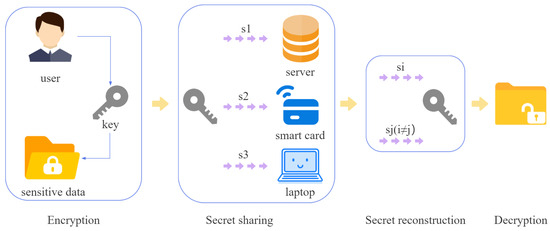
Figure 1.
Model of our data backup scheme.
2.5. Adversary Capabilities
In this section, we provide a precise description of the adversary’s capabilities.
- Capabilities of the adversary
- :
- The adversary can eavesdrop, modify, intercept, or redirect the information transferred on open channels.
- :
- When the adversary obtains a smart card or a laptop, the adversary can extract the information in it.
- :
- The adversary can modify the information on the smart card and the laptop.
- :
- The adversary can achieve at most two of the following conditions: (1) obtain the smart card; (2) obtain the laptop; (3) obtain the password; (4) obtain the biometrics; or (5) corrupt the server.
2.6. Security Goals
In this section, we describe the security goals of our scheme.
- Security goals
- :
- Even if the adversary has the above capabilities, the adversary cannot reconstruct the private key k.
- :
- When the adversary tampers with the smart card or the laptop, the user can quickly detect this attack.
- :
- When a malicious server sends a wrong message to the user, the user can quickly detect it.
3. Efficiency Analysis of Yi et al.’s Scheme
In this section, we will report the time consumption of each phase in Yi et al.’s scheme. Since the time complexity of the exclusive-OR operation and concatenation operation is negligible, we do not take them into account.
The notations to analyze the computational cost of each phase are as follows:
- :
- The time complexity of the hash function operation.
- :
- The time complexity of the symmetric key encryption/decryption operation.
- :
- The time complexity of the polynomial interpolation operation.
- :
- The time complexity of the message authentication code tag generation algorithm.
- :
- The time complexity of the message authentication code verification algorithm.
- :
- The time complexity of the fuzzy extractor generation algorithm.
- :
- The time complexity of the fuzzy extractor recovery algorithm.
- :
- The time complexity of generating three shares using Shamir’s secret sharing.
Among them, the main notations used to analyze the time complexity of the scheme are , and , while the other notations are only used in the some phases.
The computational cost of three entities at each phase is shown in Table 2. Furthermore, in Table 2, Case 1 is “possession of the laptop and the smart card”, Case 2 is “losing the smart card”, and Case 3 is “losing the laptop”.

Table 2.
Computational cost of Yi et al.’s scheme.
4. Proposed Scheme
We found that the performance of Yi et al’s scheme is not very ideal. In their scheme, the laptop and the smart card need to establish a session key with the server to obtain the server information, which involves a lot of hash operations. In addition, each updating phase requires going through the above steps.
Therefore, we proposed a more efficient solution: during the registration phase, the server negotiates an encryption key with the laptop and the smart card, respectively. In this way, we can reduce the computation required to establish a session key during the authentication phase, and improve the execution efficiency of the scheme.
In this chapter, we will introduce our more efficient data backup scheme, which consists of four phases: the registration phase, the authentication phase, the key reconstruction phase, and the updating phase.
Similar to Yi et al.’s scheme, in our scheme, the registration phase and key reconstruction phase are carried out on a secure channel. The interaction between the laptop and the smart cards occurs over a secure physical channel. Additionally, all other phases are carried out on the common channel.
The adversary capabilities and the security goals are consistent with those introduced in Section 2; therefore, they are omitted here.
4.1. Registration Phase
In the registration phase, the user uses the laptop to interact with the smart card and server to complete the distribution and storage of keys. The specific process is as follows (see Game 1):
| Game 1 Registration phase | ||||
| Smart card | Laptop (user) | Server | ||
| choose | ||||
| compute | ||||
| , | ||||
| , | ||||
| , | ||||
| , | ||||
| , | ||||
| , | ||||
| , | ||||
| , | ||||
| , | ||||
| choose | ||||
| compute | ||||
| store | ||||
| and | ||||
| store | ||||
| and | ||||
| store | ||||
| and | ||||
- The user chooses , a random number , and a first-degree polynomial , where k is the key to encrypt sensitive information, and r is a random number. The user chooses a symmetric encryption key for encrypted communication between the laptop and the server. The user chooses a symmetric encryption key for encrypted communication between the smart card and the server (e.g.,the user can choose and by using the key generation algorithm in AES).
- The user computes , and divides R into two parts which are, respectively, applied to the three pseudoshares and the message authentication code. The user computes three true shares , , and , three pseudoshares , , and , the authentication message , , and three tags , , and .
- The user sends the message to the server.
- After the server receives the message , the server chooses a random number X and generates , . Finally, the server stores values .
- The server sends the message Z to the user.
- The user stores values in the laptop.
- The user then sends to the smart card.
- The smart card stores .
4.2. Authentication Phase
If the user wants to recover the private key for decrypting the encrypted sensitive data, the user needs to first perform the authentication phase. According to the possession of secret shares, the authentication phase can be divided into the following threes case: (1) laptop and smart card; (2) laptop and server; and (3) smart card and server.
4.2.1. Laptop and Smart Card
The user can easily obtain the information needed to reconstruct the private key if he has the smart card and the laptop. The specific process is as follows (see Game 2):
| Game 2 Authentication phase: possession of the laptop and the smart card | ||
| Smart card | Laptop (user) | |
| compute | ||
| if , stop; | ||
| compute | ||
| if , stop; | ||
| else compute | ||
| check | ||
| if , stop; | ||
| compute | ||
- The user inserts the smart card into the card reader, and the card reader reads the information ) in the smart card.
- The user inputs , and computes , then divides into two parts and . Then, the laptop verifies whether is a valid tag for message (). If , the laptop stops; otherwise, the laptop sends message to the smart card.
- After receiving the message, the smart card verifies whether is a valid tag for message (). If , the smart card stops.
- The smart card computes , then checks if is equal to V.
- If , the procedure aborts; otherwise, the smart card sends to the laptop.
- After receiving , the user computes , and .
4.2.2. Laptop and Server
When the user’s smart card share is unavailable (e.g., the smart card may be lost, the share may be corrupt, etc.), the user needs to complete the authentication phase through the interaction between the laptop and the server. The specific process is as follows (see Game 3):
| Game 3 Authentication phase: laptop and server | ||
| Laptop (user) | Server | |
| input | ||
| compute | ||
| check | ||
| if , stop; | ||
| compute | ||
| check | ||
| if , stop; | ||
| otherwise, server authenticates user; | ||
| compute | ||
| compute | ||
| if , stop; | ||
| else, compute | ||
- The user inputs , computes , and divides into two parts and . Then, the user inputs their , , and current timestamp . The laptop computes , and , .
- The laptop sends to the server.
- After receiving the request message , the server checks whether the current timestamp or not. If , the server stops; otherwise, the server uses the symmetric key to compute .
- . The server check whether is equal to Y. If , the server stops; otherwise, the server authenticates the user identity.
- The server computes and sends to the laptop.
- After receiving the message , the laptop computes and . If , the laptop stops; otherwise, the user computes .
4.2.3. Smart Card and Server
When the user’s laptop share is unavailable (e.g., the laptop may be lost, the share may be corrupt, etc.), the user can use another device with a smart card reader to interact with the server and complete the authentication phase. The specific process is as follows (see Game 4):
| Game 4 Authentication phase: smart card and server | ||
| Smart card (user) | Server | |
| input | ||
| compute | ||
| check | ||
| if , stop; | ||
| compute | ||
| check | ||
| if , stop; | ||
| otherwise, server authenticates user; | ||
| compute | ||
| compute | ||
| if , stop; | ||
| else, compute | ||
- The user inputs , computes , and divides into two parts and . Then, the user inputs their , , and current timestamp . The laptop computes and , .
- The laptop sends to the server.
- After receiving the request message , the server checks whether the current timestamp or not. If , the server stops; otherwise, the server uses the symmetric key to compute .
- . The server check whether is equal to Y. If , the server stops; otherwise, the server authenticates the user identity.
- The server computes and sends to the laptop.
- After receiving the message , the laptop computes and . If , the laptop stops; otherwise, the user computes .
4.3. Key Reconstruction Phase
The user can easily recover key k through the Lagrange interpolation method if he knows two of the three tuples , and . For example, if the user knows and , the user can obtain the private key by computing .
4.4. Updating Phase
When the user has both the smart card and the laptop, the user can update their password or biometrics. When the user’s smart card share or laptop share is unavailable, the user can rebuild it by interacting with the server through another share.
4.4.1. Updating Password
The user can update the password to . Before updating the password, the user need to interact with the server through the laptop or the smart card to obtain stored on the server (Section 4.4.2, lines 5 and 6; Section 4.4.3, lines 5 and 6). After obtaining the information stored on the server, the subsequent process is as follows (see Game 5):
| Game 5 Updating password | ||||
| Smart card | Laptop (user) | Server | ||
| compute | ||||
| compute | ||||
| check | ||||
| if , stop; | ||||
| choose | ||||
| compute | ||||
| , | ||||
| , | ||||
| , | ||||
| , | ||||
| , | ||||
| , | ||||
| , | ||||
| store | ||||
| store | ||||
| compute | ||||
| if , stop; | ||||
| store | ||||
- The user inserts the smart card into the card reader, and the card reader reads the information in the smart card.
- The user obtains and the random number in the laptop, and inputs their biometrics and the old password . Then, the user computes and divides R into two parts and . After that, the laptop sends to the smart card.
- After receiving the message , the smart card computes and checks whether is equal to V. If , the smart card stops; otherwise, the smart card sends to the laptop.
- The user chooses a new random number and a new password and computes following values:, ,, ,, , ,, , .Then, the user stores in the laptop to replace and sends to the smart card.
- The smart card stores to replace .
- The laptop sends to the server.
- After receiving the message , the server calculates and checks if is equal to . If , the server replaces with ; otherwise, the server stops.
4.4.2. Updating Biometrics
The process of changing the biometrics is similar to that of changing the password. Before updating the biometrics, the user needs to interact with the server through the laptop or the smart card to obtain stored on the server (Section 4.4.2, lines 5 and 6; Section 4.4.3, lines 5 and 6). Furthermore, the subsequent process is as follows (see Game 6):
- The user inserts the smart card into the card reader, and the card reader reads the information in the smart card.
- The user obtains and the random number in the laptop, and inputs their biometrics and the password . Then, the user computes and divides R into two parts and . After that, the laptop sends to the smart card.
- After receiving the message , the smart card computes and checks whether is equal to V. If , the smart card stops; otherwise, the smart card sends to the laptop.
- The user chooses a new random number and inputs new biometrics and computes following values:, ,,, , ,, , ,, , .Then, the user stores in the laptop to replace and sends to the smart card.
- The smart card stores to replace .
- The laptop sends to the server.
- After receiving the message , the server calculates and checks if is equal to . If , the server replaces with ; otherwise, the server stops.
| Game 6 Updating biometrics | ||||
| Smart card | Laptop (user) | Server | ||
| compute | ||||
| compute | ||||
| check | ||||
| if , stop; | ||||
| choose | ||||
| compute | ||||
| , | ||||
| , | ||||
| , | ||||
| , | ||||
| , | ||||
| , | ||||
| , | ||||
| , | ||||
| store | ||||
| store | ||||
| compute | ||||
| if , stop; | ||||
| store | ||||
4.4.3. Rebuilding a New Smart Card
When the user’s smart card is unavailable, the user can use the laptop to interact with the server to rebuild it. The process of rebuilding a new smart card is as follows (see Game 7):
- The user chooses a new identity of smart card , a new random number , and a new first-degree polynomial , where is a random number and two new symmetric keys are and .
- The user computes three true shares , , and , three pseudoshares , , and , the authentication message , and , , .
- The laptop uses to replace and sends message to the server.
- After receiving the message , the server calculates and checks if is equal to . If , the server replaces with ; otherwise, the server stops.
- The laptop sends the message to the smart card.
- The user stores in the new smart card.
| Game 7 Rebuilding a new smart card | ||||
| New smart card | Laptop (user) | Server | ||
| choose | ||||
| f* (x)=r*x + k; | ||||
| compute | ||||
| , | ||||
| , | ||||
| , | ||||
| , | ||||
| , | ||||
| , | ||||
| , | ||||
| store | ||||
| compute | ||||
| if , stop; | ||||
| store | ||||
| store | ||||
4.4.4. Rebuilding a New Laptop
When the user’s laptop is unavailable, the user can use the smart card to interact with the server to rebuild it. The process of rebuilding a new laptop is as follows (see Game 8):
- The user chooses a new random number , a new first-degree polynomial , where is a random number, and two new symmetric keys and .
- The user computes three true shares , , and , three pseudoshares , , and , the authentication message , and , , .
- The new laptop sends the message to the smart card.
- The smart card uses to replace and sends the message to the new laptop.
- After receiving the message , the new laptop stores and sends message to the server.
- After receiving the message , the server computes and checks whether is equal to . If , the server uses to replace ; otherwise, the server stops.
| Game 8 Rebuilding a new laptop | ||||
| Smart card | New laptop (user) | Server | ||
| choose | ||||
| f*(x)=r*x + k; | ||||
| compute | ||||
| , | ||||
| , | ||||
| , | ||||
| , | ||||
| , | ||||
| , | ||||
| , | ||||
| store | ||||
| store | ||||
| compute | ||||
| compute | ||||
| if , stop; | ||||
| store | ||||
5. Security Analysis and Performance Evaluation
In this section, we mainly analyze the security and performance of our scheme. Our scheme is secure against all secure goals claimed in Section 2.5.
5.1. Security Analysis
5.1.1. Resist Replay Attacks
When the laptop or the smart card is unavailable, the user needs to complete mutual authentication with the server through another device. The attacker can participate in this interaction process and implement a replay attack. We claim that our scheme can resist replay attacks.
If the smart card is unavailable, the user needs to complete mutual authentication with the server to recover the private key. During the authentication phase, the laptop will send a message to the server, and the attacker may intercept the message and continuously send it to the server to carry out a replay attack. Our scheme resists the above replay attacks using timestamps. The specific process of resisting replay attacks is as follows:
- (1)
- After receiving the message, the server first needs to determine that is established.
- (2)
- When the laptop sends message to the server for the first time, we have . If the attacker continues to send the message to the server, the server will terminate the authentication process when the time does not satisfy equation .
From the above analysis, it can be found that our scheme can resist replay attacks if the smart card is unavailable. The same analysis can also be applied to the situation where the attacker implements replay attacks when the laptop is unavailable.
5.1.2. Resist Impersonation User Attacks
In this kind of attack, the attacker attempts to impersonate a legitimate user and interacts with the server. If the attacker wants to impersonate a legitimate user, the attacker must calculate the ciphertext to pass the server’s verification. It should be noted that , so the attacker must calculate a valid Y and a correct key . We recall that . The security of the fuzzy extractor guarantees that is almost uniformly distributed if the biometric information has a high enough entropy. Therefore, calculating Y requires the attacker knowing the correct password , obtaining the correct biometric information , and obtaining the values of Z and P stored in the smart card or the laptop. According to the description of the attacker’s ability, it is impossible for the attacker to obtain both the password and biometric information while obtaining the smart card or the laptop device. Therefore, the attacker cannot impersonate a legitimate user.
5.1.3. Resist Impersonation Server Attacks
In this kind of attack, the attacker attempts to impersonate a legitimate server and interacts with the user. When the adversary successfully impersonates the server, they may deceive users or steal sensitive information. For example, the adversary may also send incorrect information to the user, causing them to rebuild a wrong key.
We analyze the case where the adversary wants to impersonate a legitimate server by interacting with the user through the laptop. We review the process in Section 4.2.2. If the attacker wants to impersonate a legitimate server, the attacker needs to calculate a valid mac and a correct ciphertext to pass the user’s verification. We recall that and .
Since the biometric information has enough entropy, through the security of the fuzzy extractor, is almost uniformly distributed. Then, by the security of , it is infeasible for the adversary to forge a valid tag without biometric information . Through the security of the encryption scheme, it is infeasible to forge a valid ciphertext for message without the encryption key . Therefore, the adversary must obtain the biometric information , the valid , the encryption key , and the auxiliary string P. However, according to the description of the adversary’s abilities, it is impossible for the adversary to simultaneously corrupt the server, obtain biometric information, and obtain the laptop. A similar analysis can be used for the situation where the laptop is unavailable.
5.1.4. Resist Malicious Servers
In this attack, the attacker can act as a malicious server sending incorrect information to the user, causing them to rebuild a wrong key. We consider the situation where the server sends incorrect messages to the laptop. A similar analysis can also be applied to the situation where the server sends incorrect messages to the smart card.
We recall that, in our scheme, the server sends the message to the laptop. After the laptop receives this message, the laptop calculates and .
In the chapter on resisting impersonation server attacks, we have analyzed that the attacker cannot forge legitimate messages to pass the user’s verification. Furthermore, when the server sends mismatched and to the laptop, . Therefore, the user can determine the correctness of the messages sent by the server by checking the value of b. Thus, our scheme can resist malicious servers.
5.1.5. Resist Offline Guessing Attacks
There are two ways for the adversary to perform offline guessing password attacks. One way involves validating the value of V, and the other involves validating the value of Z. We will separately discuss how our scheme resists offline guessing attacks in these two scenarios.
- (1)
- The adversary validates the value of V. In our scheme, V is stored in the smart card; thus, the adversary can only carry out offline guessing attacks in this way if he obtains the smart card. We recall that and is a random number stored in the laptop. It should be noted that the adversary cannot simultaneously obtain the smart card, the biometric information, and the laptop, which means the adversary cannot know both and at the same time. Therefore, if the adversary wants to perform offline password-guessing attacks, he must guess the value of or correctly. The security of the fuzzy extractor guarantees that is almost uniformly distributed since the biometrc information has enough entropy, and through the randomness of , the adversary cannot guess V correctly in polynomial time.
- (2)
- The adversary validates the value of Z. In our scheme, Z is stored in the smart card and the laptop, thus the adversary can only carry out offline guessing attacks in this way if he obtains the smart card or the laptop. We recall that . We consider the worst-case scenario, where the adversary obtains the laptop, which means that the adversary obtains both Z and . We note that the adversary cannot simultaneously obtain the smart card, obtain the laptop, and corrupt the server, which means that the adversary cannot know both and Y at the same time. Therefore, if the adversary wants to perform offline password-guessing attacks, he must guess the value of or Y correctly. The security of the fuzzy extractor and the randomness of Y guarantees that, the adversary cannot guess Z correctly in polynomial time.
5.2. Performance Evaluation
In this section, we will show the time consumption of each phase. The notations we used in this section are the same as those in Section 3. Since the time complexity of the exclusive-OR operation and concatenation operation is negligible, we do not take them into account. Table 3 shows the time cost for each phase of our scheme while Table 4 shows the comparison between our scheme and Yi et al. ’s scheme in terms of efficiency.

Table 3.
Computational cost of our scheme.

Table 4.
Performance comparison between the proposed scheme and Yi et al.’s scheme.
Compared with Yi et al.’s scheme, our scheme reduces two hash computations during the registration phase; reduces twenty hash computations, adds four symmetric encryption and decryption computations during the authentication phase; and reduces four hash computations during the updating phase. According to the literature [45], we have . Therefore, our scheme consumes less time than Yi et al.’s scheme by .
In Table 5, we compare the computational cost and communication cost in the similar schemes. In the authentication protocol, the frequency of login and authentication is much higher than the frequency of user registration, and the update phase is only executed when the user has an update request, so we only consider the authentication phase. When evaluating the computational and communication costs of these schemes, we assume that the laptop identity , smart card identity , server identity , password , output of the hash function H, ciphertext of symmetric encryption algorithm, timestamp, and random number are 128 bits, and the length of the random number R generated by the fuzzy extractor is 256 bits. The computation time of the XOR operation can be ignored. According to [4,45,46,47], we have ms, ms, ms, and ms.

Table 5.
Performance comparison between the proposed scheme and similar schemes.
From the comparison results, it can be seen that the computational complexity of Liu et al.’s and Hu et al.’s schemes is significantly lower than the latter two schemes. However, as mentioned earlier (in the introduction), their protocol cannot achieve the security they claim. Their protocol’s small computational costs stems from a significant sacrifice in security. Our scheme achieves the same level of security as Yi et al.’s scheme, while also having higher efficiency. In addition, our scheme also reduces one round of communication in the authentication phase, which greatly reduces our communication costs. Among the four schemes, our scheme has the lowest communication cost.
6. Conclusions
This paper gave a systematic analysis of Yi et al.’s scheme and found that its efficiency is relatively low, because users need to establish a session key with the server using a laptop or a smart card before obtaining information stored on the server. This process involves a large amount of hash operations, and the above steps are repeated every time the update operation is performed. Therefore, we proposed a data backup scheme with better performance. Our scheme involves negotiating session keys in advance during the registration phase. In this way, we can reduce ten hash computations and one round of communication in the authentication phase. The experimental results show that our scheme has better execution efficiency and lower communication costs.
Meanwhile, this paper also carried out the security analysis of the scheme and ensured that the scheme has the same security as the scheme of Yi et al. [7].
Author Contributions
Conceptualization, L.W., Y.W., and J.Y.; methodology, L.W., Y.W., and J.Y.; formal analysis, L.W., Y.W., and J.Y.; investigation, L.W., Y.W., and J.Y.; writing—original draft preparation, L.W.; writing—review and editing, L.W.; visualization, L.W.; supervision, Y.W. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by the National Natural Science Foundation of China (Grant No. 62102077), Shanghai Sailing Program (Grant No. 21YF1401200), and Open Fund Program for State Key Laboratory of Information Security of China (Grant No. 2021-MS-05).
Institutional Review Board Statement
Not applicable.
Data Availability Statement
The original contributions presented in the study are included in the article, further inquiries can be directed to the corresponding author.
Conflicts of Interest
The authors declare no conflicts of interest.
Appendix A
In this section, we review Yi et al.’s scheme [7]. Their scheme consists of four phases: the registration phase, authentication phase, key reconstruction phase, and updating phase.
Appendix A.1. Registration Phase
In this phase, the user inserts their smart card into the card reader and enters their identity, password, and biometrics. After initial calculations, the corresponding information is distributed to laptops, smart cards, and servers for storage:
- The user chooses a robust fuzzy extractor , a message authentication code , and a hash function h. The user chooses , a random number , and a first-degree polynomial , where k is the key to encrypt sensitive information, and r is a random number.
- The user computes , and divides R into two parts and , which are, respectively, applied to the three pseudoshares and the message authentication code. The user computes three true shares and , the three pseudoshares , , and , the authentication message , , , and three tags , , and .
- The user sends a message to the server.
- After the server receives the message , the server chooses two random numbers and and generates and . Finally, the server stores values .
- The server sends the messages to the user.
- The user stores values in the laptop.
- The user then sends to the smart card.
- The smart card stores .
Appendix A.2. Authentication Phase
The authentication phase contains three situations: possession of the laptop and the smart card, losing the smart card, and losing the laptop. After performing the authentication phase, the user obtains the information required to recover the key.
Appendix A.2.1. Possession of the Laptop and the Smart Card
The users complete the authentication phase through the interaction between the laptop and the smart card. The specific process is as follows:
- The user inserts the smart card into the card reader, and the card reader reads the information in the smart card.
- The user inputs , and computes , then divides into two parts and . The smart card verifies whether is a valid tag for message , . If , the smart card stops; otherwise, the laptop verifies whether is a valid tag for message , . If , the laptop stops; otherwise, it continues.
- The user inputs their and to the smart card, and the laptop sends to the smart card.
- The smart card computes , then checks if is equal to V.
- If , the procedure aborts; otherwise, the smart card sends to the laptop.
- After receiving , the user computes .
Appendix A.2.2. Losing the Smart Card
When the user loses the smart card, he needs to complete the authentication phase through the interaction between the laptop and the server. The specific process is as follows:
Mutual authentication between the user and the server:
- The user inputs , computes and divides into two parts and . Then, the user inputs their . The laptop computes and , where is a random number chosen by the laptop, and is the current timestamp.
- The laptop sends to the server.
- After receiving the request message , the server checks whether the current timestamp or not. If , the server stops; otherwise, the server computes and checks whether is equal to or not. If they are not equal, the server stops; otherwise, the server authenticates the user. Then, the server chooses a random number , and computes , where is the current timestamp.
- The server sends message to the laptop.
- After receiving the response message , the laptop checks whether the current timestamp or not. If , the laptop stops; otherwise, the laptop computes and checks whether is equal to . If they are equal, the user authenticates the server; otherwise, the laptop stops.
Establishing a session key between the user and the server:
- The laptop computes and sends to the server.
- After receiving the message , the server checks whether is equal to CM1 or not. If they are equal, it sets the session key . The server computes and sends to the laptop.
- After receiving the message , the user computes . The user computes . If , the user stops; otherwise, the user computes .
Appendix A.2.3. Losing the Laptop
The process is similar to the case of losing the smart card.
Appendix A.3. Key Reconstruction Phase
When the user has two of three tuples:, and , he can easily reconstruct the key k by using the Lagrangian interpolation polynomial.
Appendix A.4. Updating Phase
During the updating phase, the user can rebuild their smart cards, laptops, or update passwords and biometrics.
Appendix A.4.1. Updating Password
The specific process is as follows:
- The user inserts the smart card into the card reader, and the card reader reads the information in the smart card.
- The user inputs biometrics , the old password , and obtains the old random number , in the laptop and the in the smart card.
- The user computes , and divides R into two parts and . The user checks if is equal to V. If they are equal, the user continues; otherwise, the user stops.
- The user chooses a new random number and a new password and computes following values:Then the user stores in the laptop to replace and stores in the smart card to replace .
Appendix A.4.2. Updating Biometrics
The process is similar to the case of updating the password.
Appendix A.4.3. Rebuilding a New Smart Card
The user first needs to establish a session key with the server, which is consistent with the loss of the smart card during the authentication phase. After the user establishes the session key, the specific process is as follows:
- The user chooses a new identity of the smart card , a new random number , and a new first-degree polynomial , where is a random number.
- The user computes three true shares and , three pseudoshares and , the authentication message , and and .
- The laptop uses to replace and sends message to the server.
- After receiving the message , the server computes and checks if is equal to . If , the server uses to replace . Otherwise, the server stops.
- The user stores in the smart card.
Appendix A.4.4. Rebuilding a New Laptop
The process is similar to the case of rebuilding a smart card.
References
- Wei, L.; Zhu, H.; Cao, Z.; Dong, X.; Jia, W.; Chen, Y.; Vasilakos, A.V. Security and privacy for storage and computation in cloud computing. Inf. Sci. 2014, 258, 371–386. [Google Scholar] [CrossRef]
- Zhou, J.; Cao, Z.; Dong, X.; Vasilakos, A.V. Security and Privacy for Cloud-Based IoT: Challenges. IEEE Commun. Mag. 2017, 55, 26–33. [Google Scholar] [CrossRef]
- Katz, J.; Lindell, Y. Introduction to Modern Cryptography; Chapman and Hall/CRC: Boca Raton, FL, USA, 2007. [Google Scholar] [CrossRef]
- Chang, C.C.; Chou, Y.C.; Sun, C.Y. Novel and practical scheme based on secret sharing for laptop data protection. IET Inf. Secur. 2015, 9, 100–107. [Google Scholar] [CrossRef]
- Liu, Y.; Zhong, Q.; Chang, L.; Xia, Z.; He, D.; Cheng, C. A secure data backup scheme using multi-factor authentication. IET Inf. Secur. 2017, 11, 250–255. [Google Scholar] [CrossRef]
- Hu, H.; Lin, C.; Chang, C.C.; Chen, L. Enhanced secure data backup scheme using multi-factor authentication. IET Inf. Secur. 2019, 13, 649–658. [Google Scholar] [CrossRef]
- Yi, J.; Wen, Y. An Improved Data Backup Scheme Based on Multi-Factor Authentication. In Proceedings of the 9th International Conference on Big Data Security on Cloud (BigDataSecurity), IEEE International Conference on High Performance and Smart Computing, (HPSC) and IEEE International Conference on Intelligent Data and Security (IDS), New York, NY, USA, 6–8 May 2023. [Google Scholar] [CrossRef]
- Shengwei, X.; Chunrui, G.; Xinyu, L. IBC improved key managerment scheme based on multi-party co-management. Comput. Appl. Softw. 2020, 37, 314–317. [Google Scholar]
- Xu, Z.; Jiang, H. A Framework of Decentralized PKI Key Management Based on Dynamic Trust. In Proceedings of the Security and Management, 2008; pp. 258–264. Available online: https://www.researchgate.net/profile/Hai-Jiang-7/publication/221199867_A_Framework_of_Decentralized_PKI_Key_Management_Based_on_Dynamic_Trust/links/56d8615108aee1aa5f7e6ffd/A-Framework-of-Decentralized-PKI-Key-Management-Based-on-Dynamic-Trust.pdf (accessed on 12 June 2024).
- Zheng, X.; Wang, H.; Chen, Y.; Liu, H.; Liu, R. A decentralized key management scheme via neighborhood prediction in mobile wireless networks. In Proceedings of the 7th IEEE International Conference on Mobile ad Hoc and Sensor Systems (IEEE MASS 2010), San Francisco, CA, USA, 8–12 November 2010; pp. 51–60. [Google Scholar]
- Yang, H.; Zhang, Y.; Zhou, Y.; Fu, X.; Liu, H.; Vasilakos, A.V. Provably secure three-party authenticated key agreement protocol using smart cards. Comput. Netw. 2014, 58, 29–38. [Google Scholar] [CrossRef]
- Park, S.; Park, H.J. Privacy preserving three-party authenticated key agreement protocol using smart cards. Int. J. Secur. Its Appl. 2014, 8, 307–320. [Google Scholar] [CrossRef]
- Jiang, Q.; Zeadally, S.; Ma, J.; He, D. Lightweight three-factor authentication and key agreement protocol for internet-integrated wireless sensor networks. IEEE Access 2017, 5, 3376–3392. [Google Scholar] [CrossRef]
- Yao, A.C. Protocols for secure computations. In Proceedings of the 23rd Annual Symposium on Foundations of Computer Science (SFCS 1982), Chicago, IL, USA, 3–5 November 1982; pp. 160–164. [Google Scholar]
- Goldreich, O.; Micali, S.; Wigderson, A. How to play any mental game, or a completeness theorem for protocols with honest majority. In Providing Sound Foundations for Cryptography: On the Work of Shafi Goldwasser and Silvio Micali; ACM Digital Library: New York, NY, USA, 2019; pp. 307–328. [Google Scholar]
- Shamir, A. How to share a secret. Commun. ACM 1979, 22, 612–613. [Google Scholar] [CrossRef]
- Blakley, G.R. Safeguarding cryptographic keys. In Proceedings of the International Workshop on Managing Requirements Knowledge, New York, NY, USA, 4–7 June 1979; IEEE Computer Society: Washington, DC, USA, 1979; pp. 313–318. [Google Scholar]
- Ben-Or, M.; Goldwasser, S.; Wigderson, A. Completeness theorems for non-cryptographic fault-tolerant distributed computation. In Providing Sound Foundations For Cryptography: On the Work of Shafi Goldwasser and Silvio Micali; ACM Digital Library: New York, NY, USA, 2019; pp. 351–371. [Google Scholar]
- Rabin, T.; Ben-Or, M. Verifiable secret sharing and multiparty protocols with honest majority. In Proceedings of the Twenty-First Annual ACM Symposium on Theory of Computing, Seattle, WA, USA, 14–17 May 1989; pp. 73–85. [Google Scholar]
- Jiang, Q.; Wei, F.; Fu, S.; Ma, J.; Li, G.; Alelaiwi, A. Robust extended chaotic maps-based three-factor authentication scheme preserving biometric template privacy. Nonlinear Dyn. 2015, 83, 2085–2101. [Google Scholar] [CrossRef]
- Lamport, L. Password authentication with insecure communication. Commun. ACM 1981, 24, 770–772. [Google Scholar] [CrossRef]
- Nam, J.; Choo, K.K.; Han, S.; Paik, J.; Won, D. Two-Round Password-Only Authenticated Key Exchange in the Three-Party Setting. Symmetry 2015, 7, 105–124. [Google Scholar] [CrossRef]
- Juang, W.S.; Chen, S.T.; Liaw, H.T. Robust and Efficient Password-Authenticated Key Agreement Using Smart Cards. IEEE Trans. Ind. Electron. 2008, 55, 2551–2556. [Google Scholar] [CrossRef]
- Sood, S.K.; Sarje, A.K.; Singh, K. An improvement of Xu et al.’s authentication scheme using smart cards. In Proceedings of the Third Annual ACM Bangalore Conference, Bangalore, India, 22–23 January 2010. [Google Scholar] [CrossRef]
- Chen, C.M.; Ku, W.C. Stolen-Verifier Attack on Two New Strong-Password Authentication Protocols (Regular Section). IEICE Trans. Commun. 2002, 85, 2519–2521. [Google Scholar]
- Harn, L.; Huang, D.; Laih, C.S. Password authentication based on public-key distribution cryptosystem. In Proceedings of the Fifth International Conference on Data Engineering, Los Angeles, CA, USA, 6–10 February 1989. [Google Scholar] [CrossRef]
- Diffie, W.; Hellman, M. New Directions in Cryptography (1976). In Ideas That Created the Future; The MIT Press: Cambridge, MA, USA, 2021; pp. 421–440. [Google Scholar] [CrossRef]
- Chang, C.C.; Wu, T.C. Remote password authentication with smart cards. IEE Proc. Comput. Digit. Tech. 1991, 138, 165. [Google Scholar] [CrossRef]
- Chang, C.C.; Laih, C. Comment on remote password authentication with smart cards. IEE Proc.-E 1992, 139, 372. [Google Scholar]
- Tan, K.; Zhu, H. Remote password authentication scheme based on cross-product. Comput. Commun. 1999, 22, 390–393. [Google Scholar] [CrossRef]
- Hwang, M.S.; Li, L.H. A new remote user authentication scheme using smart cards. IEEE Trans. Consum. Electron. 2000, 46, 28–30. [Google Scholar] [CrossRef]
- Yang, G.; Wong, D.S.; Wang, H.; Deng, X. Two-factor mutual authentication based on smart cards and passwords. J. Comput. Syst. Sci. 2008, 74, 1160–1172. [Google Scholar] [CrossRef]
- Hsieh, W.B.; Leu, J.S. Exploiting hash functions to intensify the remote user authentication scheme. Comput. Secur. 2012, 31, 791–798. [Google Scholar] [CrossRef]
- Lee, J.; Ryu, S.; Yoo, K. Fingerprint-based remote user authentication scheme using smart cards. Electron. Lett. 2002, 38, 1. [Google Scholar] [CrossRef]
- Li, C.T.; Hwang, M.S. An efficient biometrics-based remote user authentication scheme using smart cards. J. Netw. Comput. Appl. 2010, 33, 1–5. [Google Scholar] [CrossRef]
- Das, A.K. Analysis and improvement on an efficient biometric-based remote user authentication scheme using smart cards. IET Inf. Secur. 2011, 5, 145–151. [Google Scholar] [CrossRef]
- Om, H.; Reddy, M.R. Geometric based remote password authentication using biometrics. J. Discret. Math. Sci. Cryptogr. 2013, 16, 207–220. [Google Scholar] [CrossRef]
- Dodis, Y.; Reyzin, L.; Extractors, A.S.F. How to generate strong keys from biometrics and other noisy, data April 13. In Proceedings of the Eurocrypt, Interlaken, Switzerland, 2–6 May 2004. [Google Scholar]
- Odyuo, N.; Lodh, S.; Walling, S. Multifactor Mutual Authentication of IoT Devices and Server. In Proceedings of the 2023 5th International Conference on Smart Systems and Inventive Technology (ICSSIT), Tirunelveli, India, 23–25 January 2023. [Google Scholar] [CrossRef]
- Braeken, A. Highly Efficient Bidirectional Multifactor Authentication and Key Agreement for Real-Time Access to Sensor Data. IEEE Internet Things J. 2023, 10, 21089–21099. [Google Scholar] [CrossRef]
- Mostafa, A.M.; Ezz, M.; Elbashir, M.K.; Alruily, M.; Hamouda, E.; Alsarhani, M.; Said, W. Strengthening Cloud Security: An Innovative Multi-Factor Multi-Layer Authentication Framework for Cloud User Authentication. Appl. Sci. 2023, 13, 10871. [Google Scholar] [CrossRef]
- Maes, J.G.; Rahman, K.A.; Mukherjee, A. Hybrid Smartwatch Multi-factor Authentication. In Proceedings of the 2023 IEEE 17th International Symposium on Medical Information and Communication Technology (ISMICT), Lincoln, NE, USA, 10–12 May 2023. [Google Scholar] [CrossRef]
- Kumar, R.; Singh, S.; Singh, P.K. A secure and efficient computation based multifactor authentication scheme for Intelligent IoT-enabled WSNs. Comput. Electr. Eng. 2023, 105, 108495. [Google Scholar] [CrossRef]
- Li, X.; Peng, J.; Obaidat, M.S.; Wu, F.; Khan, M.K.; Chen, C. A Secure Three-Factor User Authentication Protocol With Forward Secrecy for Wireless Medical Sensor Network Systems. IEEE Syst. J. 2020, 14, 39–50. [Google Scholar] [CrossRef]
- Tan, Z. A chaotic maps-based authenticated key agreement protocol with strong anonymity. Nonlinear Dyn. 2013, 72, 311–320. [Google Scholar] [CrossRef]
- Maliberan, E.V.; Sison, A.M.; Medina, R.P. A new approach in expanding the hash size of MD5. Int. J. Commun. Netw. Inf. Secur. 2018, 10, 374–379. [Google Scholar] [CrossRef]
- Wang, F.; Xu, G.; Xu, G.; Wang, Y.; Peng, J. A Robust IoT-Based Three-Factor Authentication Scheme for Cloud Computing Resistant to Session Key Exposure. Wirel. Commun. Mob. Comput. 2020, 2020, 3805058. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).