Abstract
Path planning is necessary in many applications using unmanned underwater vehicles (UUVs). The main class of tasks is the planning of safe routes with minimal energy costs and/or minimal levels of emitted physical and information signals. Since the action planner is on board the UUV, the main focus is on methods and algorithms that allow it to build reference trajectories while minimizing the number of calculations. The study is devoted to the problem of the optimal route planning for a UUV with a non-uniform radiation pattern. The problem is stated in the form of two point variational problem for which necessary and sufficient optimality conditions are proved. Particular attention is paid to cases where optimality conditions are not met. These cases are directly related to found specific forms of a radiation pattern. Sufficient optimality conditions are extended on the class of two-link and multi-link motion paths. Software tools have been developed and computer simulations have been performed for various types of radiation patterns.
1. Introduction
Various military and civil engineering applications that deal with the search of the optimal trajectories for space, air, naval and ground vehicles cover control tasks with various target functions, resource and control constraints. Examples of such tasks are: minimizing the risk of detection by aircraft radars; minimizing the risk of detection of a submarine by various sensors through different physical fields; minimizing cumulative damage during the passage of contaminated areas, etc. Despite the large variety of controlled mobile vehicles, the control tasks associated with them have common traits. First of all, these are traditional mission planning tasks, which include setting a safe course taking into account natural and artificial constraints (terrain, hydrology, weather conditions), as well as maintaining stability on a given course. In addition, the problem of optimal maneuvering in emergency situations (sharply changing weather conditions, etc.), as a rule, is typical. The success of the mission is estimated by the value of a certain function (optimization criterion), the minimization of which is the main task of the control system. Classical optimization criteria are associated with minimizing the energy costs, time (velocity problem), or miss criterion. Recently, there has been interest in non-traditional criteria, such as increasing the covertness of movement (when moving in a threat environment, considering the map of potential threats). It has led to a new area of control problems known as “trajectory/path planning in the threat environment.” The threat environment is defined as a set of agents, called conflicting, that the controlled vehicle must avoid while performing its main task [1,2,3,4,5,6].
The route planning problems are usually associated with path planning (PP) and trajectory planning (TP) problems. The path planning task consists of determining the points through which the UUV must pass to reach the prescribed destination from the starting position, while describing the UUV’s movement over time is considered to be the trajectory planning task [7]. The approach describing detection mechanisms given in [8,9,10] is used to formulate trajectory planning problem for UUV evading from detection. The estimation of the integral level of the signal that is sent to the input of a spatially distributed information and an observation system during the entire observation time is performed. In literature such a system is called a sensor [10]. The estimation of the signal integral level at the sensor input is fulfilled to solve the TP-problem with optimizing the control law for a mobile vehicle that moves from a fixed starting point to a fixed end point of the route during a given period of time. The UUV’s goal is an evasion from the detection by an observer (group of observers) located in a given area. This approach corresponds to the process of mobile vehicle detection based on an estimation of primary emitted physical signals [6]. Therefore statements of such problems are based on the estimation of physical signals emitted by the vehicle. The formalization of these problems can differ in dependence of many parameters: physical nature of detection fields, classes of acceptable control, the type of quality criteria, the number of detectors, the volume of information available to conflicting parties. As a result, based on known data, a distribution map of normalized or absolute levels of risks (threats) is created, as shown in Reference [11].
Similar approaches are used in Reference [2], where the problem of the automated path planning of combat unmanned aerial vehicles (UAVs) in the presence of radar-controlled surface-to-air missiles is considered and solved. A pre-built map of aircraft damage risks is based on the interaction of three subsystems: the aircraft and its characteristics, the radar and its capabilities, and the missile and its striking properties. Based on this map, the route with the lowest risk of damage is found.
As mentioned above, on the one hand, there is a variety of mathematical criteria describing the success of missions performed by mobile vehicles: the probability of rescue, the motion time on the trajectory, the mathematical expectation of the time interval until the first detection on the path, the path length [4,8,9,10,12,13,14]. On the other hand, despite this variety there are too few analytical results available to realize optimal trajectories in TP problems. In Reference [5], the optimal path consists of lines and circular arcs (2D Dubins curves). In Reference [10] the optimal path is presented by circle or Legandre’s functions arcs as well as in [15]. Indeed, numerical algorithms are well described in the literature.
At the initial stage, the mission planner is faced with one of two tasks:
- •
- minimizing the integral risk for a given trajectory length;
- •
- minimizing the length of the UUV motion path for a given value of the integral risk.
These problems are formulated as two-point problems of variations calculus or as optimal control problems on the plane in the presence of coordinate, phase, and integral constraints, and can be solved by one of the standard numerical methods that will set the trajectory of the UUV as the projection on the horizontal plane from 3D-space. Planning the UUV trajectory in the projection on a vertical plane is carried out using, for example, a terrain map, on which the mission planner interactively chooses the depth-levels of the trajectory, setting reference points for the beginning and end of the movement on the specified depth. Horizontal movement on a given depth is carried out along a flat trajectory obtained from solving the variational problems discussed above. The smooth conjugation of the trajectories of adjacent depths can be performed by a polynomial or spline approximation, taking into account the curvature constraint. An example of on-board realization of mission-planner for a mobile underwater robot is described in [16].
A good summary of path planning algorithms for UUVs is given in Reference [7]. These algorithms include the shortest graph-based path algorithm known as A*, the artificial potential field algorithm, sequential quadratic programming and so on. Additionally, an approach based on ant-colony behavior is often used [11,17]. In recent years, due to the progress of neural networks, the deep learning and specifically deep reinforcement learning approaches [18,19] are becoming more and more popular.
The present article deals with the problem of stealth intrusion of UUV into the protected area in the conditions of a network-centric counteraction of the opposite side, equipped by the means of the detection of UUV. Following the work in Reference [6], the signal emitted by a mobile vehicle has a non-uniform space pattern. The TP problem of UUV’s evasion from detection by stationary sonar system (SSS) is considered. In the case of a passive mode of reception, the SSS detects UUV using a radiated signal generated by UUV’s motion [20]. An indicator of the success of the object’s stealth intrusion into the area is the integral risk of UUV detection on some assigned route [1,6]. When the TP problem is solved, the maximal UUV invisibility is achieved by choosing such trajectory and the law of velocity as time functions, which minimize the risk of detection. On the the other hand, an indicator of the effectiveness of the detection by SSS is the probability of detection of a moving UUV in the conditions of receiving a signal against random background noise of the aquatic environment [21]. Therefore equal values of detection risk assigned to given trajectory may match different values of detection probabilities depending on levels of a random background acoustic noise.
The current article expands and continues research presented in the article [6]. The need for new research emerged from a computer modeling of optimal UUV routes, conducted by the authors of the article using software, specially developed for this purpose. It turned out that for some types of radiation patterns the model trajectory has a sawtooth shape. This means that the UUV moves, constantly changing its heading angle. Accordingly, it is necessary to determine whether such trajectories are a feature of the developed numerical scheme for implementing the algorithm, or whether such trajectories are actually locally optimal in theory. A lot of new results have been revealed. It happens that the sawtooth trajectory shape appears due to violation of sufficient optimality conditions for extreme trajectories. In the current article new lemmas and theorems for the two-link and multi-link optimal trajectories are proven, as well as a lot of modeling examples are developed to illustrate all the obtained results. Additionally, special cases of radiation patterns leading to degeneration of necessary and sufficient conditions are studied. Moreover, the current research deals with the problem in a more general form, which allows studying of more various types of physical signals compared to the previous article [6].
The proposed work has the following structure. Section 2 discusses two statements of optimal TP problem as a two-pointed classical variation problem. The variables transformation, according to [22], is determined to reformulate the initial task to be more convenient for the further solution form. In Section 3 necessary optimality conditions are derived. Further in Section 4 sufficient optimality conditions are proved. Section 5 studies the conditions of the degeneration of Euler-Lagrange equations. The radiation patterns satisfying such conditions and the ones corresponding to zero Hessian are found. Section 6 proposes the extension of sufficient optimality conditions onto the class of two-link trajectories. Section 7 presents a number of examples, that illustrate and support analytical results obtained in the paper. Last Section 8 concludes the article and suggests a direction for future work.
2. Trajectory Planning Problem
The mobile vehicle moves on the plane in the detection region of the searching system, presented by one observer that is called a sensor. Let us formulate the problem of finding the optimal trajectories of the object as the variational problem with integral functional of object’s detection by the sensor, which is called risk of detection, or, for simplicity, just risk [6,10].
2.1. About the Risk Functional
The risk depends on the instantaneous level of physical signal , radiated by the mobile vehicle and received by the sensor [6]. This signal is the function of the characteristics of the mobile vehicle and the sensor
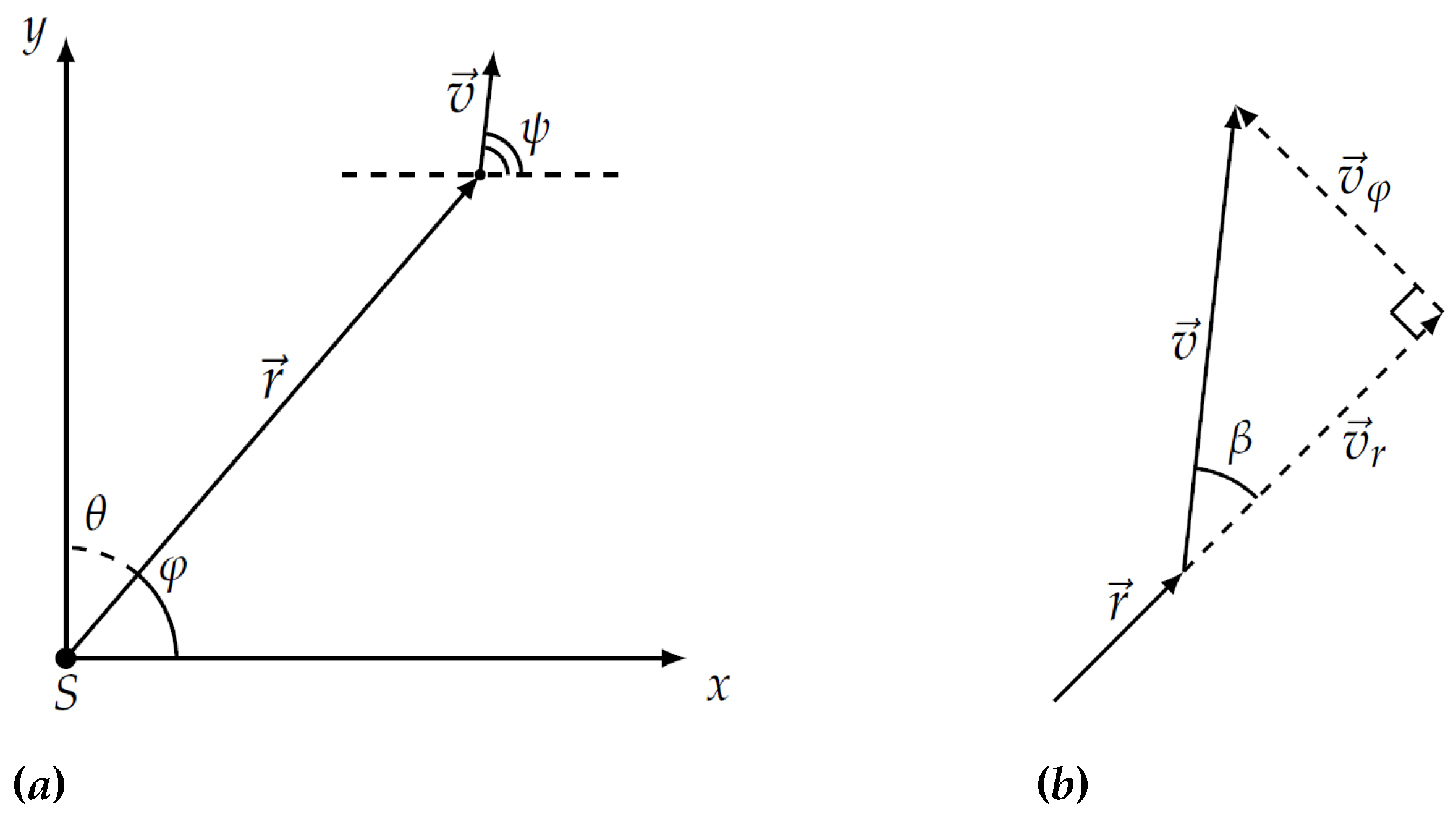
where multiplier is responsible for the diagram of the sensor antenna, is the radiation pattern of the mobile vehicle in the direction toward the sensor which forms the angle with velocity vector, r is the current distance between sensor and evading vehicle, v—absolute instant velocity of the object, —signal saturation factor in the physical medium of detection. The geometric meaning of angles and is as follows. Here is the angle of rotation of object’s velocity vector and is the angle of rotation of radius vector as shown in Figure 1a. Angle is the angle in triangle built from radial and transversal velocities of the object, e.g., the angle between velocity vector of the vehicle and its projection on radius vector as shown in Figure 1b. The exponent characterizes the physical field used for detection. Depending on value this can be magnetic, thermal, acoustic or electromagnetic fields. Further in the paper the case of will be considered.
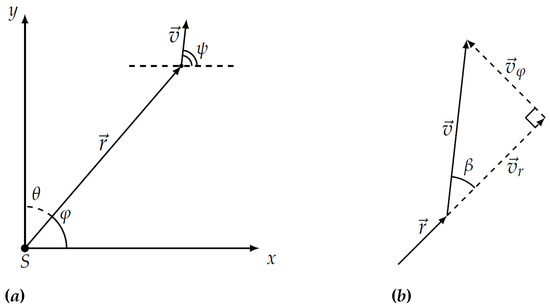
Figure 1.
The mobile vehicle in the Cartesian plane with sensor S (a) and its velocity vectors , , and (b).
For simplicity let us consider the sensor antenna diagram to be homogeneous, so , and that there is no additional signal attenuation or gain in the environment, so .
The risk R is the integral value of the signal given by Equation (1), so the criterion of optimization is a function of phase coordinates of the vehicle and its relative disposition to the sensor:
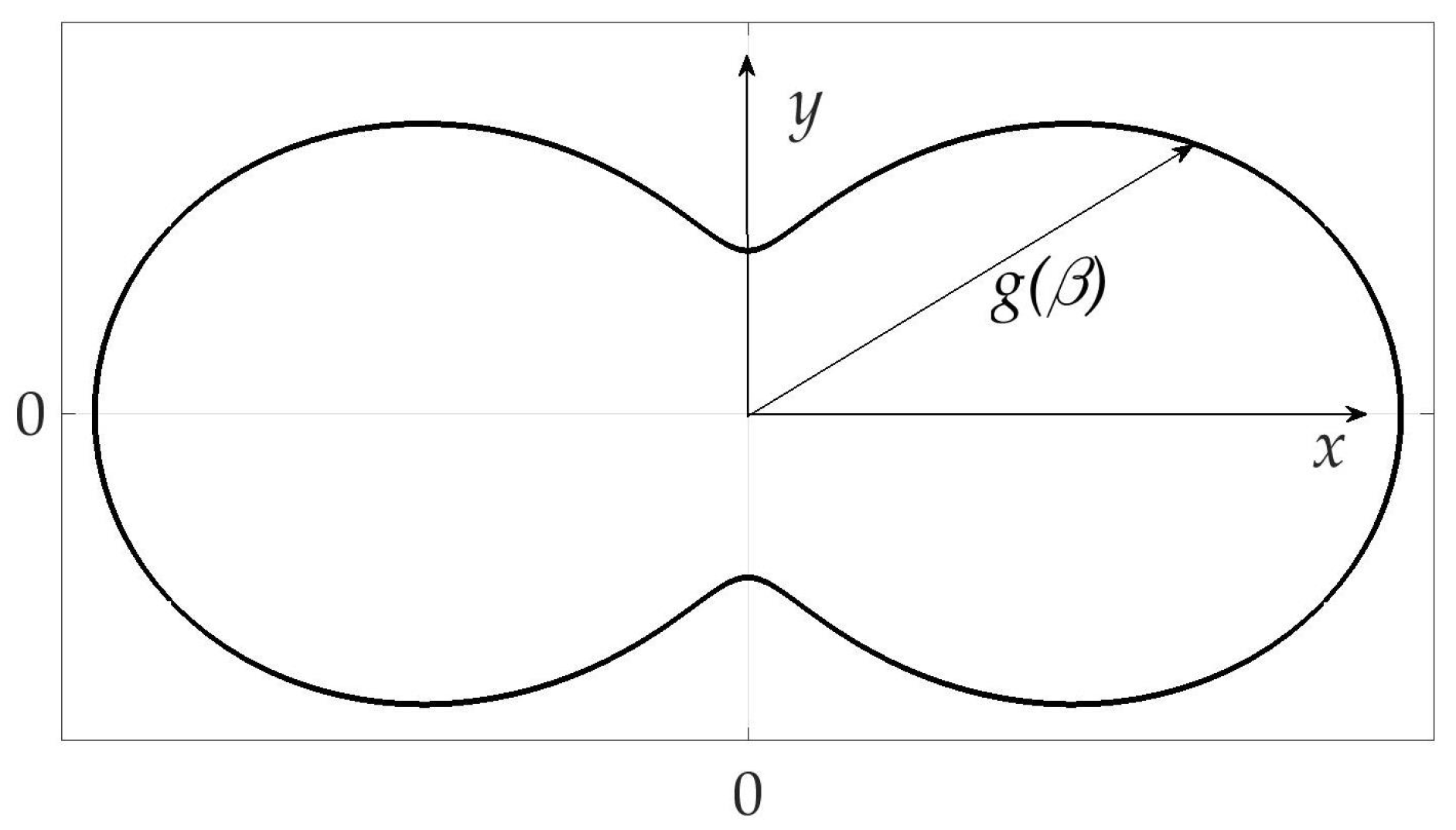
The example of radiation pattern is presented in Figure 2. The axes X and Y are oriented with the object in such a way that Y points to the upper side of the object, X-to the right one, and angle is counted counter-clockwise from axes X. Function itself is a length of radius-vector for every , thus .
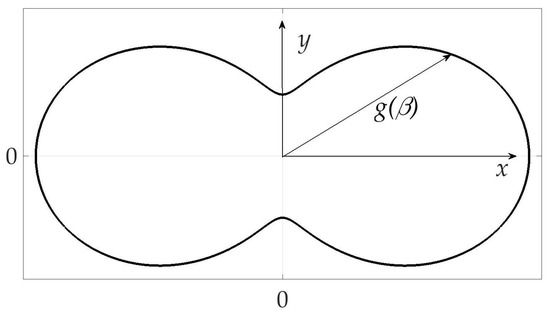
Figure 2.
Radiation pattern of the mobile vehicle.
2.2. Mathematical Statement of the Problem
The task of the mobile vehicle is to pass from start point A to final point B with as minimal risk on the trajectory as possible. The polar coordinate system in 2D space is introduced to rewrite the optimal trajectory planning problem.
As mentioned in the introduction, in [22] it was proven that for the problems of this type there is a transformation of coordinates which leads the functional to the convenient value for the next investigation form and to the coordinate space , where . It occurs that in this coordinate space optimal trajectories are geodetic, e.g., presented as straight lines. For the considered problem Equation (2) there is such a transformation too.
According to Lemma 1 [6] the original TP problem can be rewritten as the problem with the functional Equation (3).
Problem 1.
It is required to find the trajectory , which minimizes the functional
with boundary conditions
Written in this form, the initial problem is more convenient for analytical solution, as the optimization functional depends only on the derivatives of coordinates.
3. The Necessary Optimality Conditions
First of all, the necessary conditions for extremal trajectory must be considered, e.g., the candidates for optimal trajectories are to be found. Due to the form of the Equation (3) this functional has the number of the first integrals. For example, as was shown in [6], Lagrangian remain its value S* along the extremal trajectory .
Additionally, in [6] the theorem about the necessary condition of optimality for the trajectory was stated and proven. From Theorem 1 [6]
Theorem 1.
Suppose that for all is a twice continuously differentiated function of β, where , are some constant values, and , exist and are continuous functions of t. Then the extremal trajectory satisfies the following system of equations
It follows that the extremal trajectory, which can be the solution for Problem 1 can be represented in the parametric form of logarithmic spiral
The explicit form of the UUV extremal trajectory equation on the plane is
Next two lemmas define the velocity law of the vehicle on the extremal trajectory and the risk value on it.
Lemma 1.
The velocity law on the extremal trajectory Equation (6) is represented as follows
We need to reformulate Lemma 4 from Reference [6] as follows
Lemma 2.
The proof of Lemma 2 remains valid as shown in Reference [6].
4. The Sufficient Optimality Conditions
Now let us prove that obtained above extremal trajectory given by Equation (6) is the optimal solution to the Problem 1, e.g., it brings the strong minimum to the functional Equation (3). The Hessian matrix shall be investigated for that cause.
Lemma 3.
Let , – thrice continuously differentiated function of β, then Hessian matrix equals
where
and the Hessian itself is the determinant of the matrix
Next theorem gives the sufficient condition of extremal trajectory optimality.
Theorem 2.
Proof.
If the Hessian matrix is positively defined then the Legandre conditions are fulfilled. So second order minor is the same with Hessian itself and by the theorem condition. Choose any first order minor and from Equation (9) and find its sign. At least one of them is positive because both values are fixed on the optimal trajectory and their sum equals
In a previous article [6] this theorem was considered for the particular case of . Of course, expression from Equation (11) equals the same from [6] after substituting this . Taking into account that leads to the statement that both values and are strictly positive too.
The Jacobin conditions have the form
as , , , .
Using minors of the Hessian matrix from Equation (9), the summands of equations from Equation (12) can be found
The Equation (12) takes the form
which coincides with explicit form of Euler–Lagrange Equations (17) for considered Problem 1.
Here , , S* are constant values, representing three first integrals of Euler–Lagrange system. It means that the sufficient conditions of strong minimum of risk functional Equation (3) are fulfilled [23]. □
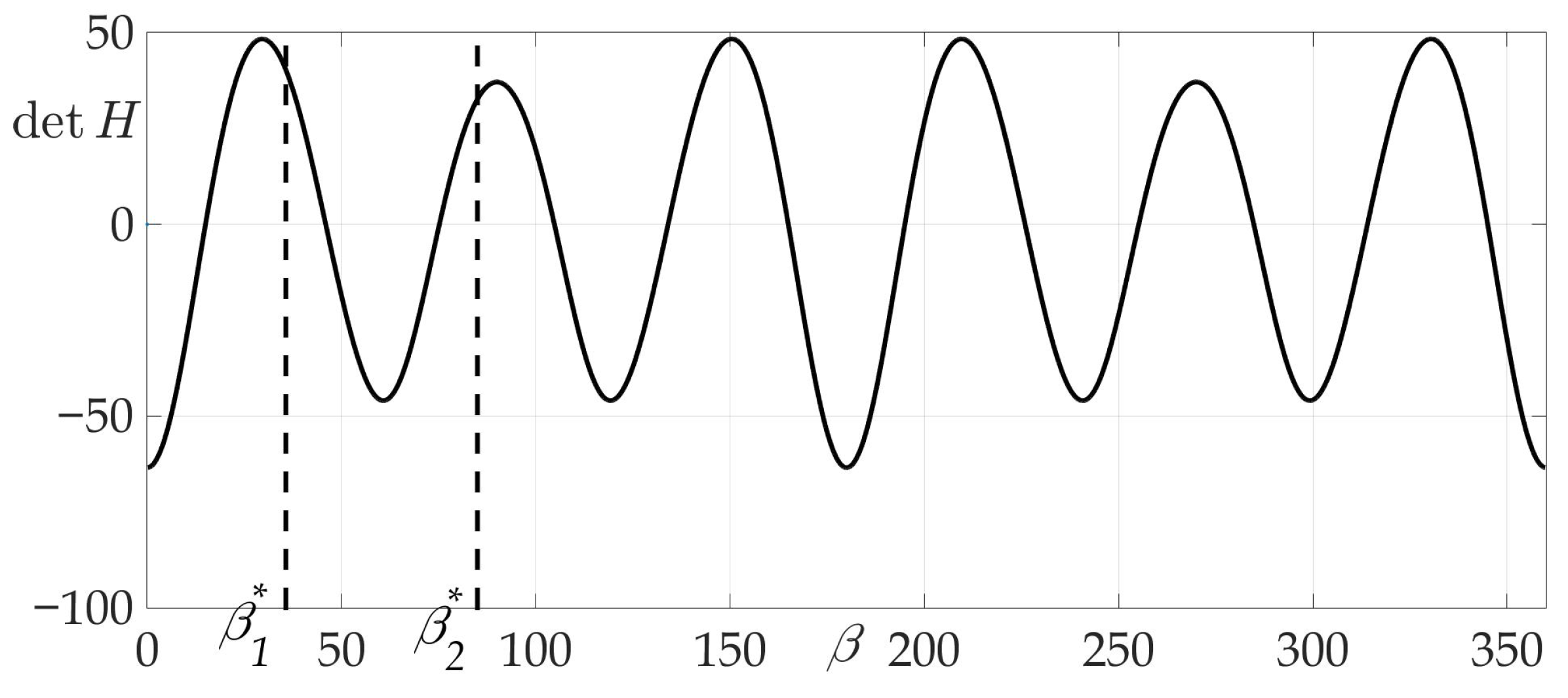
Thus, positivity of the determinant of the Hessian matrix guarantees the logarithmic spiral to be optimal solution of the problem. Theorem 2 allows for any to answer if extremal trajectory (6) is optimal or not. Indeed, the sign of Hessian (10) depends on the sign of the third multiplier, which depends only on the function . If in conditions of Theorem 2 , then sufficient optimality conditions are not fulfilled and the optimal trajectory may have a more complicated form and consist of several logarithmic spirals. These cases are discussed in the paper further.
5. Degeneration of Euler–Lagrange Equations and Zero Hessian Cases
First of all the case of degeneration of Euler–Lagrange Equations (17) should be considered. The thing is that both equations may coincide to each other for some radiation pattern and some constant values , .
Lemma 4.
The function , where , brings the Euler–Lagrange system (17) to degeneration.
Proof.
Let us multiply the first equation from system (17) by , the second one by and then sum these two new equations up. Similarly, let us multiply the first equation from system (17) by , the second one by and then sum these two new equations up. A new system of equations appears
Dividing the second equation from system of Equations (18) on the first one can obtain
where and is some constant value, and depends from vehicle velocity direction. Integration of the right part of Equation (19) on gives
with undefined constant of integration . Now integrating left part of Equation (19) one can obtain
Using both parts of Equation (21) as powers for the exponent leads to the statement of the Lemma, where and is some constant value. □
According to Lemma 4 obtained special form of function degenerates Euler–Lagrange equations only with one specific value of the parameter , that responds to the direction associated with boundary conditions of the problem 1 expressed through constants and when it is already solved.
Corollary 1.
The function from Lemma 4 brings the Lagrangian of the functional (3) to the form
Proof of Corollary 1 is given in Appendix A.
In addition to Theorem 1 the next theorem presents the form of extremal trajectories now for the special type of radiation pattern from Lemma 4.
Theorem 3.
All the curves satisfying equation on the coordinate plane with some constants , , are extremal when satisfies Lemma 4.
Proof.
It is enough to remember Corollary 1 to state that S is a constant on the extremal trajectory locally in vicinity directions where is continuously differentiated function. Then from Equation (22) it follows the theorem’s statement. □
So, among the set of optimal paths leading from A to B that satisfy the Equation (22), there is also the logarithmic spiral shown in Equation (6) with the same value of the risk function.
After analysis of degeneration of necessary optimality conditions it is time to consider the sufficient conditions too. One of the interesting for research cases is the case of zero Hessian (10)
Lemma 5.
Proof.
Dividing of Equation (23) by brings it to the form:
Introducing a new variable allows us to rewrite Equation (25) in a form
Solving Equation (26) gives
where is an arbitrary constant. After returning to function this equation becomes
Addressing the proof of Lemma 4 and Equation (19) it is fair to state that
□
Now comparing radiation pattern given by Lemma 4 and the one settled by Lemma 5 we have the identity of both expressions at fixed and some value of . Numerical modelling for the zero Hessian case will be held in Section 7.
6. Two-Link Trajectories
This section considers optimal trajectories for radiation patterns which do not satisfy sufficient conditions from Section 4. For simplicity and analytical solvability of the problems only two-link trajectories are considered. The risk on the optimal two-link trajectory passing through points A, B, C is given by the next Lemma.
Lemma 6.
The minimum value of risk on a two-segment trajectory that passes through the points A, C, B in the time interval T is equal to
where
The proof of Lemma 6 is proposed in Appendix A.
Lemma 6 allows us to check the type of optimal trajectory. If the risk on the two-link trajectory is less than on the logarithmic spiral directly connecting the points A, B, then two-link trajectory is optimal.
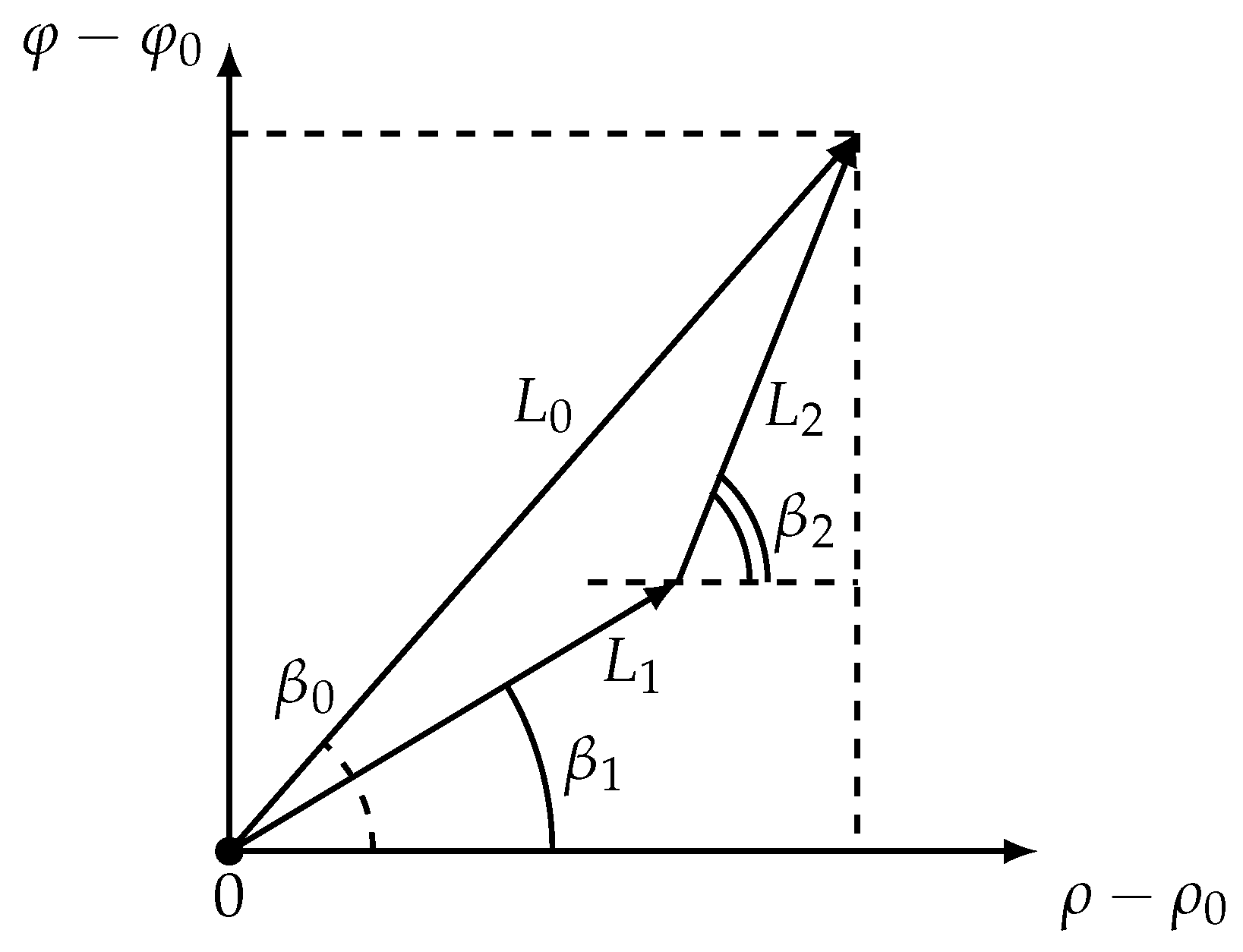
As was stated in [22], in space logarithmic spirals are presented as straight lines. Considering optimal two-link trajectories in space (Figure 3) allows to rewrite Equation (27) in a simpler way.
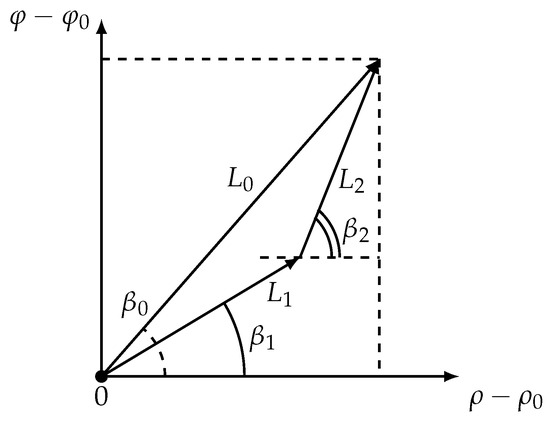
Figure 3.
The mobile vehicle in the coordinate system.
Corollary 2.
The minimum value of risk on a two-segment trajectory that passes through the points A, C, B in the time interval T can be represented as
where
The proof of Corollary 2 is given in Appendix A.
A few words should be said about the applicability of the formula (29). The expression under parentheses must always be positive. Indeed, as shown in Figure 3, either an inequality or an inequality is satisfied due to the geometry. Because in both cases this expression is positive.
According to proof of Lemma 6 the value of risk on two-link extremal trajectory equals
Problem 2.
It is needed to find a quad that
Instead of solving the optimization Problem 2 of finding the minimum of for four variables, we will solve two consecutive optimization Problem 3 for pairs (, ) and (, ). This is possible because Lemma 6 found the unique pair and that gives the minimum.
Problem 3.
It is needed to find a quad that gives consecutive minimum of , so
Next theorem states a result about the structure of the optimal two-link trajectories.
Theorem 4.
Optimal angles * for two-link optimal trajectory do not depend on the direction between start and end points, are fully defined by radiation pattern and satisfy
Proof.
To prove this theorem an expression from (29) must be investigated. After omitting non-dependable on constants and T the variable can be considered
This formula should be minimized by and , e.g.,
The first equation of System (36) leads to the expression
After simplifying the last equation becomes
This equation may be presented as a product of two multipliers so one equation from the next list of two equations is fulfilled
The first equation corresponds to the case of one-link extremal trajectory, so it does not represent an interest.
Similarly the second equation of System (36) leads to the expression
After simplifying it becomes
Again, a list of two equations is fair where at least one of them is fulfilled
The first equation corresponds to the case of one-segment trajectory, because it is already explored.
So, any optimal two-link trajectory for specific radiation pattern is constructed from segments of two optimal directions * and *. Moreover, it can be shown, that optimal multi-link trajectories are based on these segments as well.
The next lemma specifies a system of equations derived in Theorem 4, which allows us to find optimal angles * and * that minimize a risk functional on two-link trajectory.
Lemma 7.
Angles * for optimal trajectory can be found from system
where
The proof of Lemma 7 is proposed in Appendix A.
Let us ask the question of what value the risk will take in the case when the radiation pattern corresponds to the case of zero Hessian.
Lemma 8.
Radiation pattern makes two-link trajectory risk a constant value for any .
Proof.
Substituting this radiation pattern into Equation (29) and getting rid of the module in function gives
Simplifying this expression leads to the chain of equations
From here it follows that R is a constant value for any and depends only on boundary conditions and fixed time on route T. Moreover, the function of radiation pattern from Lemma 4 makes expression from Equation (41) even simpler, as in this case
□
7. Examples and Illustration of the Results
The current article develops the analytical methods for the constructing of optimal reference trajectories. However, in the first part of work [6] an explicit form criterion for the PP problem for various noise conditions and two types of decision rules are given, based on a comparison of threshold statistics. The real-world data describing these statistics can be used for practical applications of research introduced in these articles. Detection probabilities can be obtained through the calculation of the risk criterion. Certainly, practical aspects make all the analytical models and estimations much more complicated, but still the presented in the article research can be helpful for finding reference paths for UUVs.
Matlab scripts have been developed to simulate, validate numerically found analytical solutions and support lemmas and theorems. Each of the examples below demonstrates results for different chosen radiation patterns and illustrates one of the cases discussed throughout the article. In each example the start point A has coordinates (50, 0) and end point B—(0,100) on Cartesian plane, so , . Sensor S is situated in the origin.
7.1. Example 1. Logarithmic Spiral
The first example considers a simple case of positive Hessian on the whole range of or (here and further in some examples angle may be also considered in degrees), or on the range of or due to symmetry , with radiation pattern
where , . Radiation pattern described by Equation (42) was considered in [6], but in the case of , when and is constant due to Lemma 3. However, now this is not the same case, as .
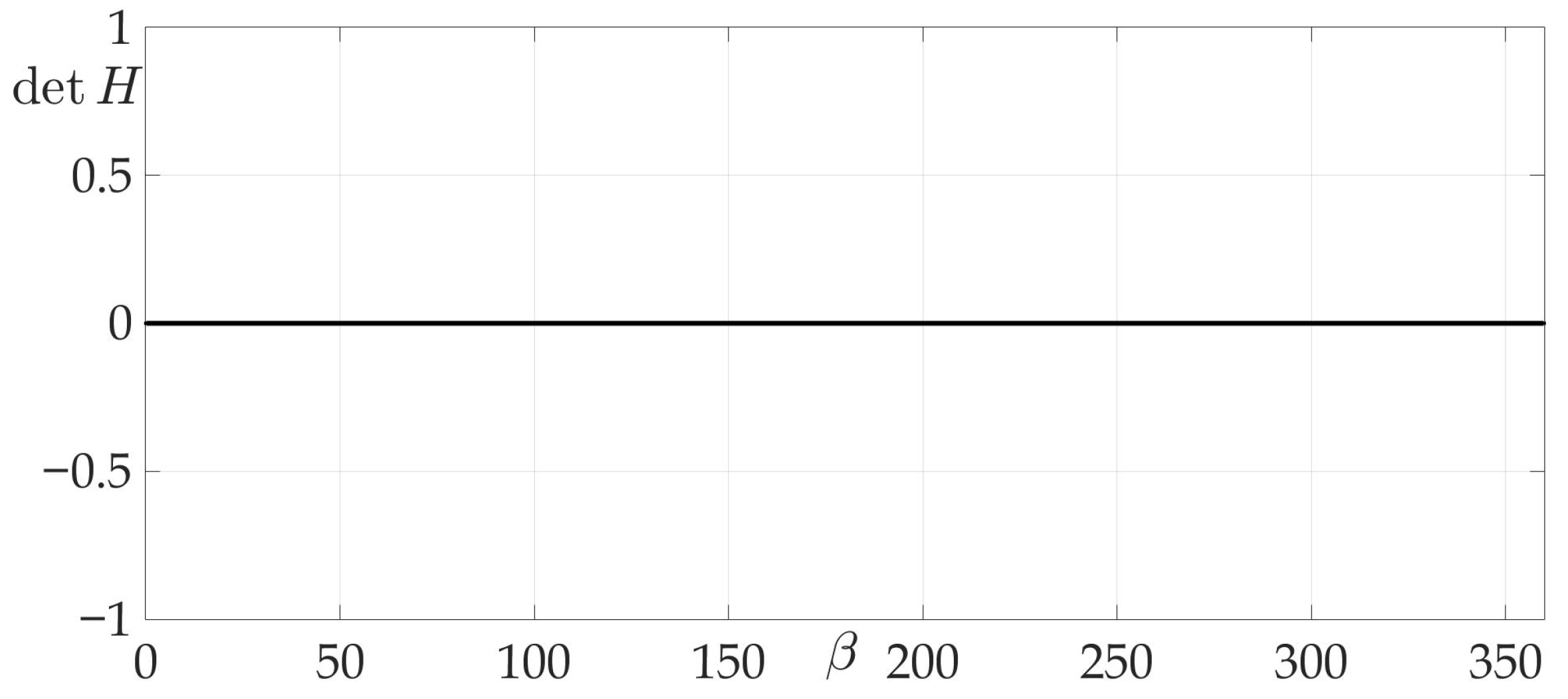
Figure 4a shows a radiation pattern as a function of angle and Figure 4b—as a curve on Cartesian plane in respect to the mobile vehicle, where is a length of the radius-vector. Figure 5 shows the dependence of the Hessian . As one can see, it is positive for all angles, thus the sufficient condition of Theorem 2 is fulfilled, meaning that logarithmic spiral is the optimal solution with minimal risk on trajectory risk on the trajectory .
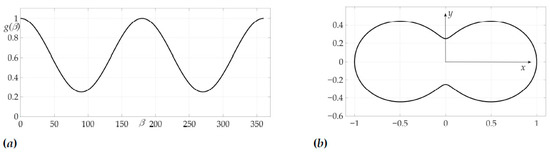
Figure 4.
Radiation pattern as an dependence in polar coordinates (a) and on the Cartesian plane (b).
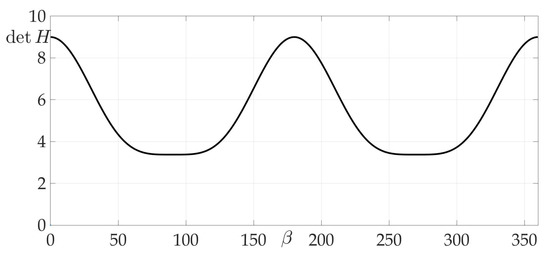
Figure 5.
Dependence of Hessian from .
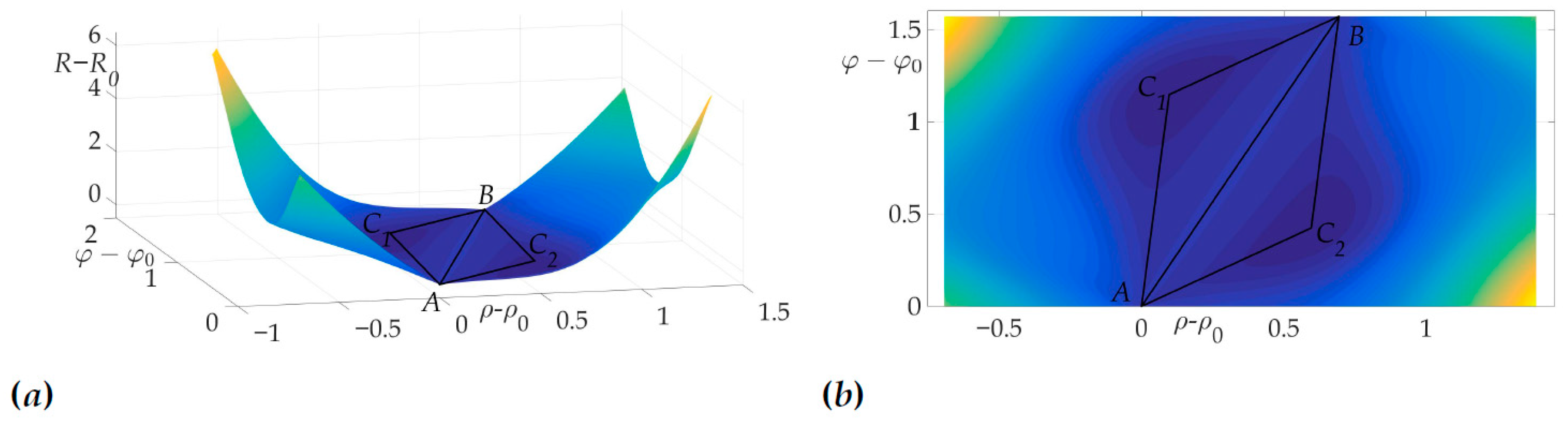
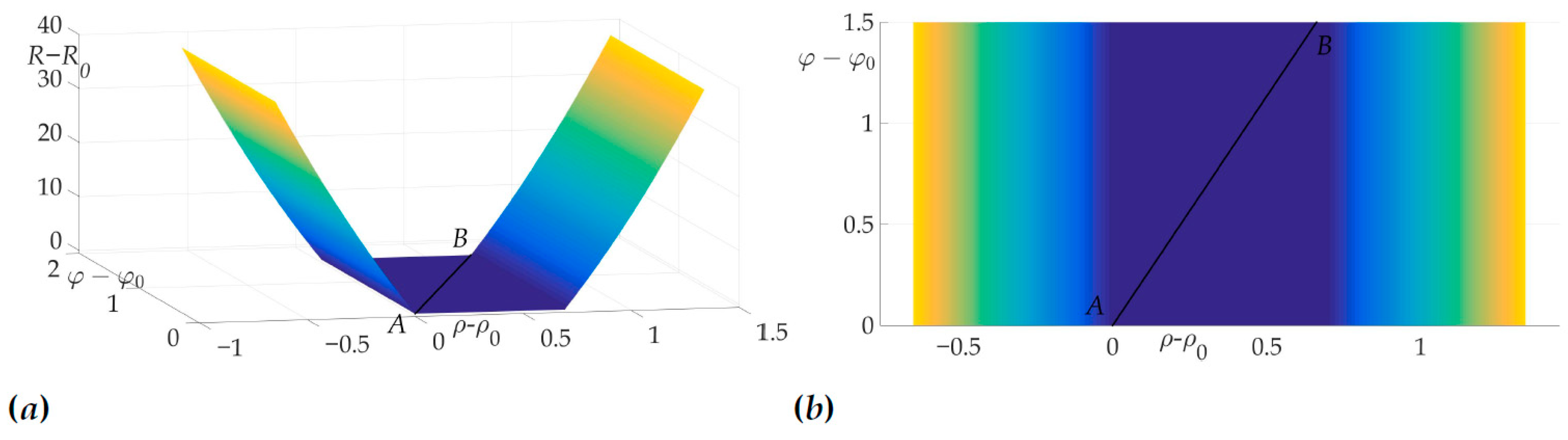
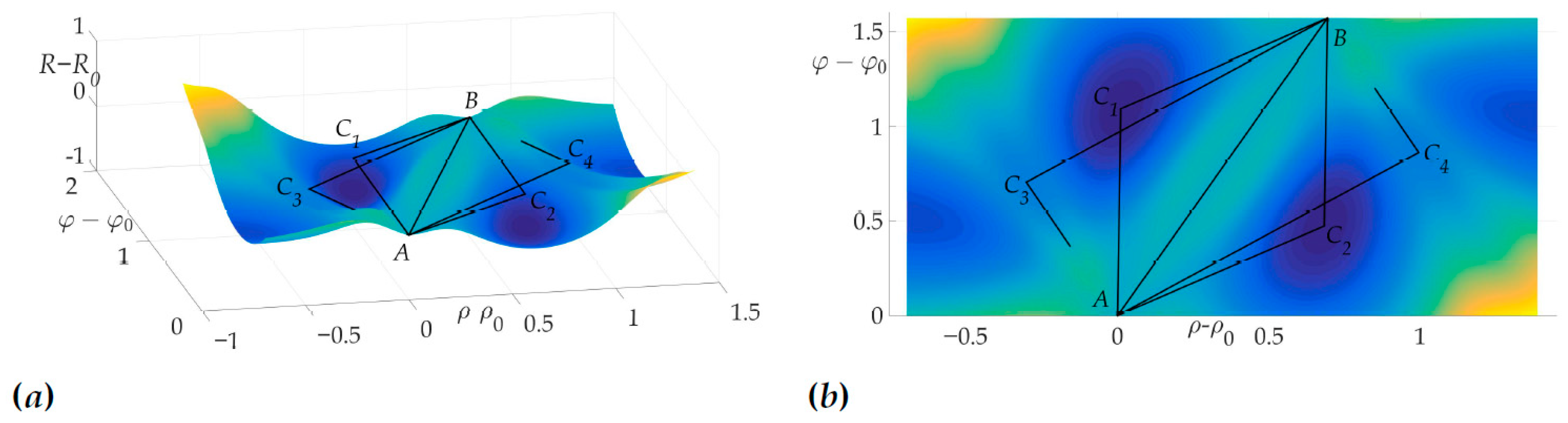
This fact is illustrated in Figure 6a and Figure 6b. Figure 6a shows the surface of the risk above plane, e.g., the vertical axis is the value of risk on two-link trajectory with fixed start and end points A and B and switch point C with coordinates . Figure 6b illustrates the projection of this surface on the plane . The black color shows the optimal trajectory , which is a line segment, as mentioned in [22].
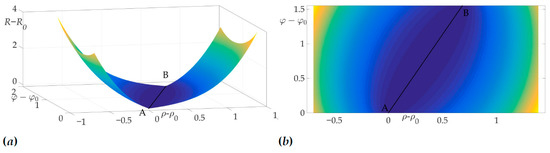
Figure 6.
Optimal trajectory in space (a) and its projection on plane (b).
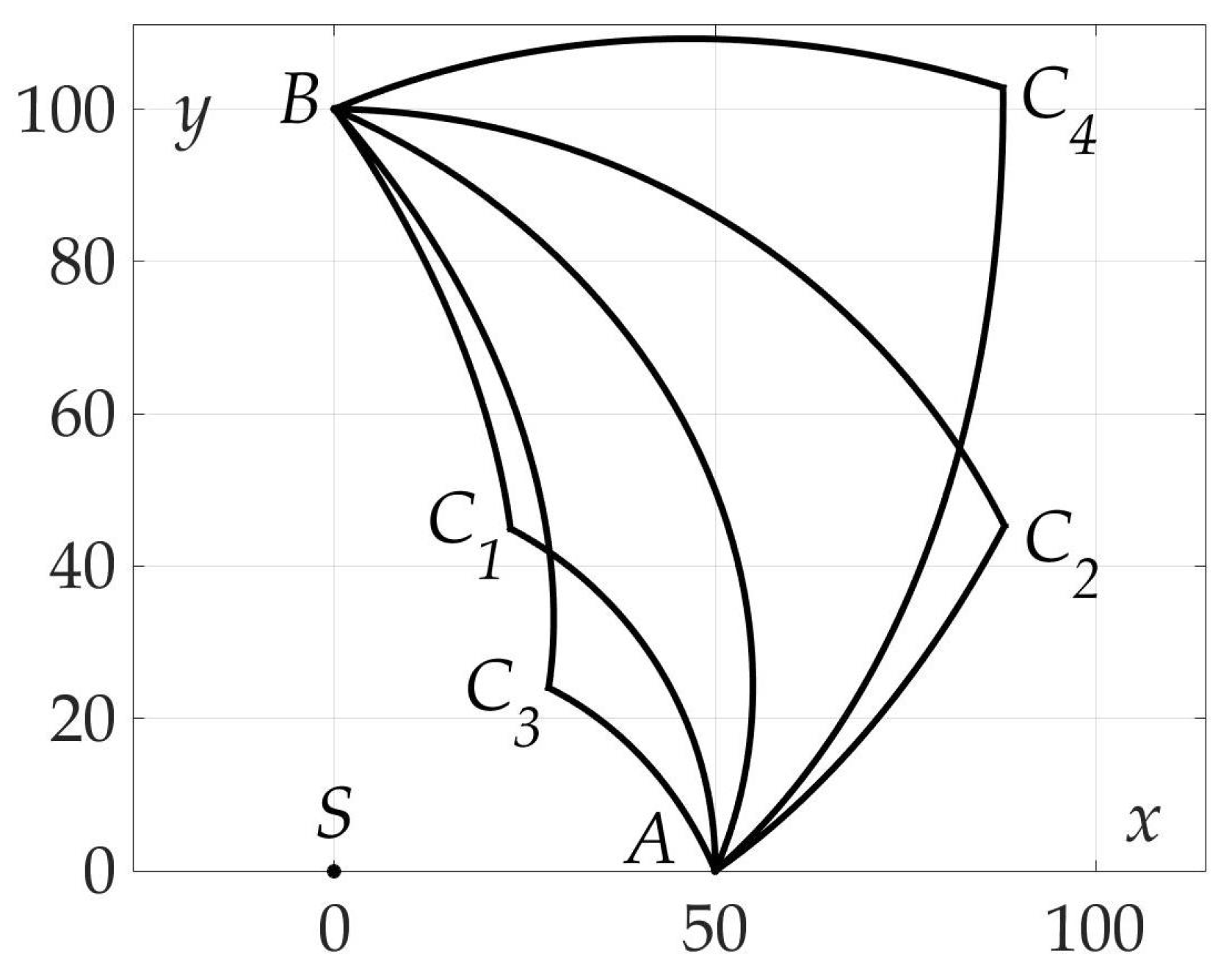
Figure 7 demonstrates the found optimal trajectory on Cartesian plane.
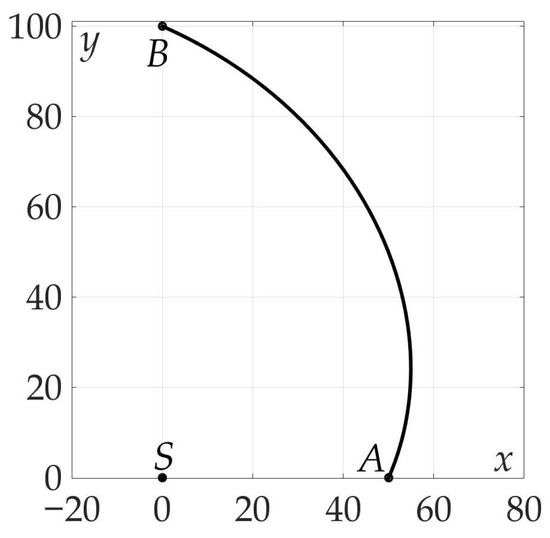
Figure 7.
Optimal trajectory on Cartesian plane.
7.2. Example 2. Two-Link Optimal Trajectory
The second example illustrates a case of two-link optimal trajectory. As in previous example, . Radiation pattern is more complicated and, as shown in Figure 8, is presented as an ellipse with cosine wave
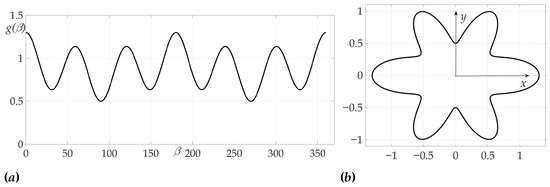
Figure 8.
Radiation pattern as an dependence polar coordinates (a) and on the Cartesian plane (b).
Figure 9 shows that, in contrast to Example 1, Hessian is not positive for all ’s, that means that sufficient conditions are not satisfied. Both one-link and two-link trajectories , are shown in Figure 10 and Figure 11. A programming module in Matlab has been developed to compute optimal *, * based on system of Equation (39) from Lemma 7. Route points coordinates are found , . Trajectories and are symmetrical in a sense of angles * and *: corresponds to segments and , –to segments and . The values of found risks on these trajectories are
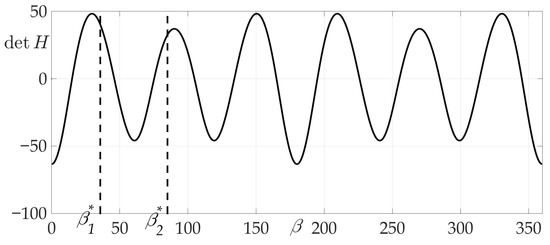
Figure 9.
Dependence of Hessian from .
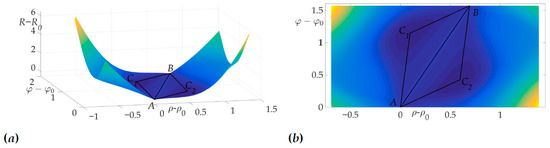
Figure 10.
Optimal trajectory in space (a) and its projection on plane (b).
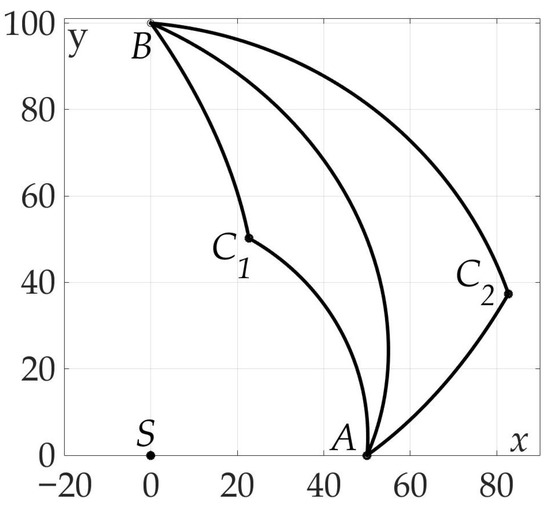
Figure 11.
Optimal trajectory on Cartesian plane.
Obviously, the two-link paths are preferable in a sense of risk minimization by almost 37%. In this example a unique pair is a solution of Problem 3.
7.3. Example 3. The Case of Null Hessian
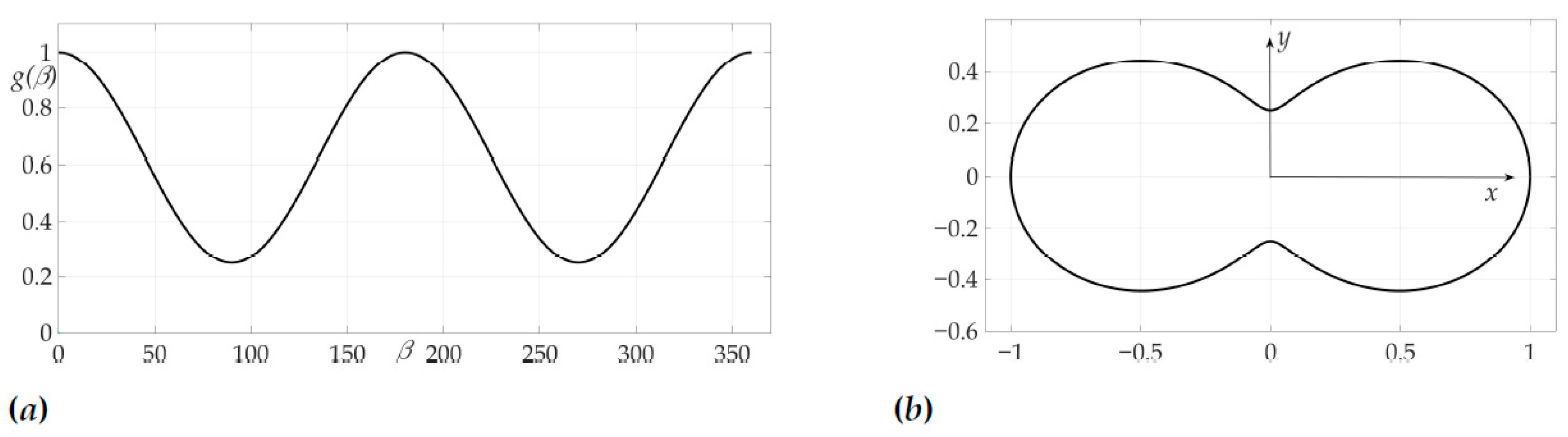
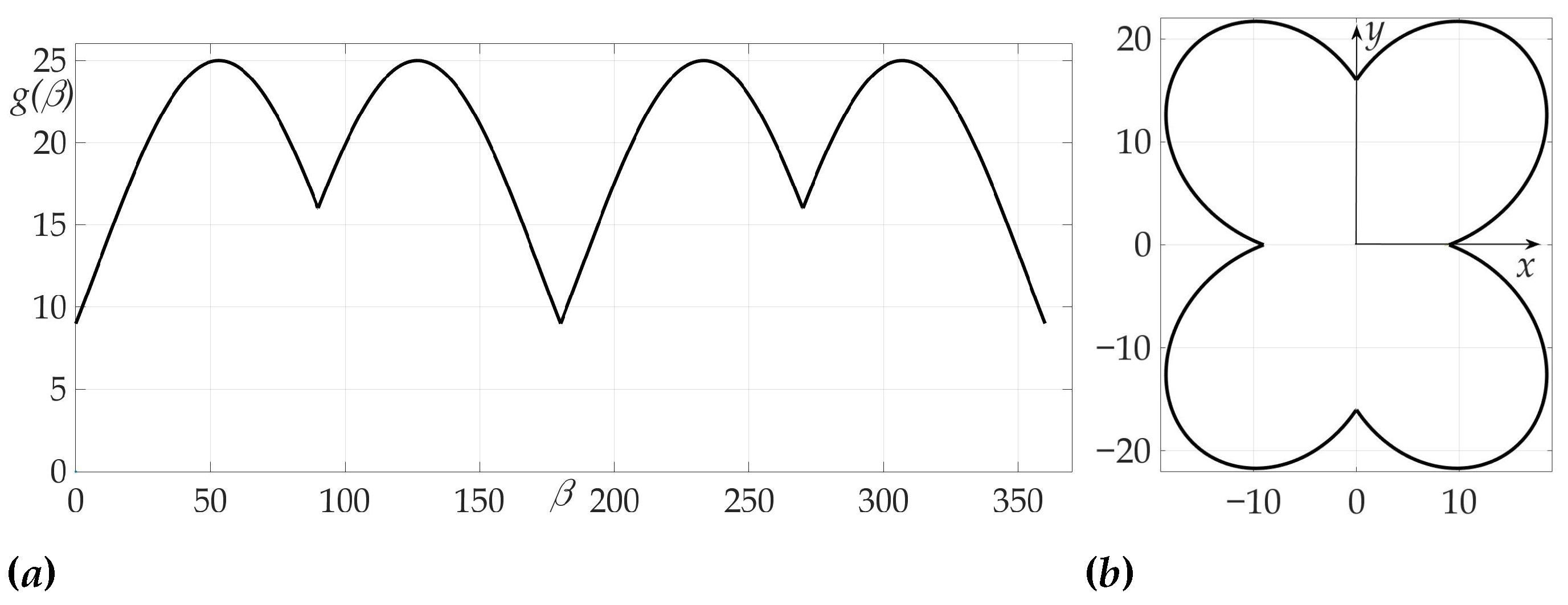
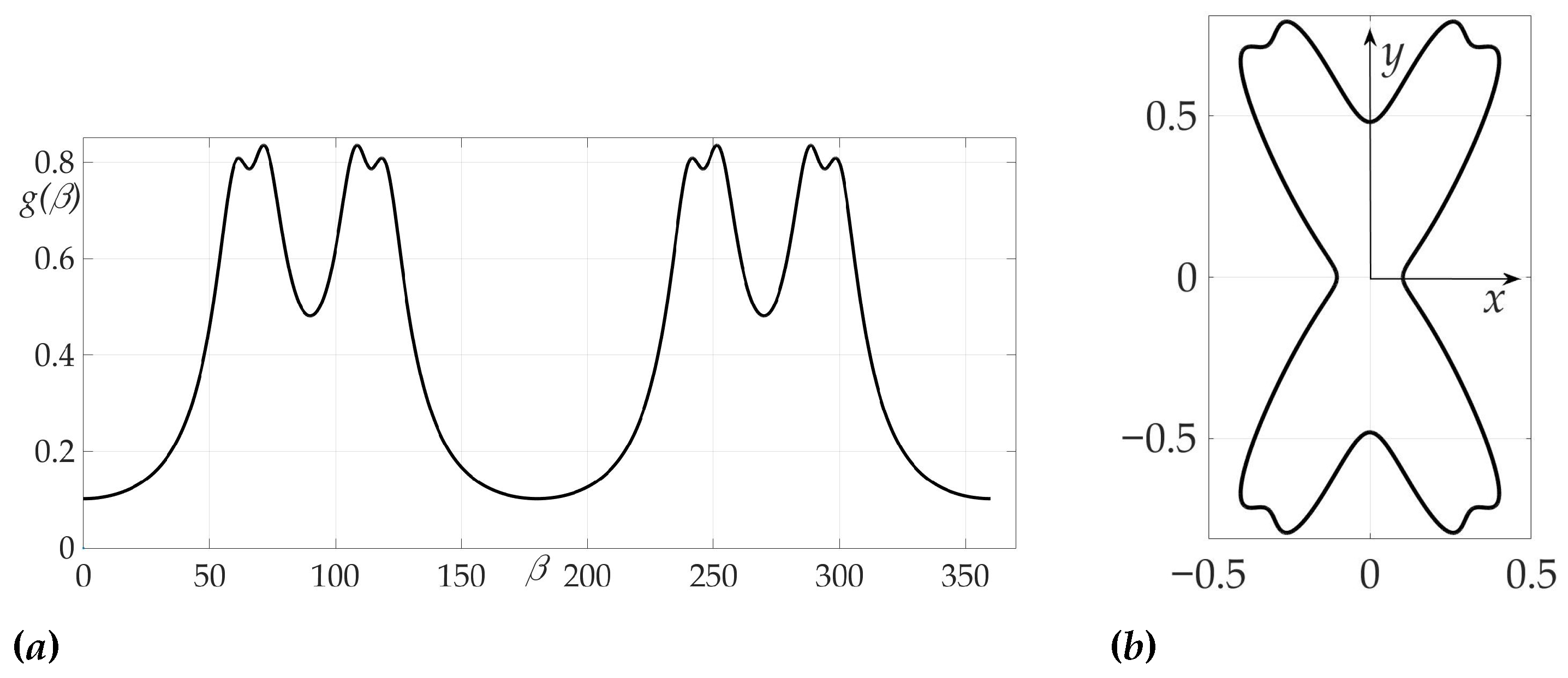
The third example is devoted to the case of radiation pattern, described in Lemma 5 of Section 5, e.g., the function that nulls the Hessian. We choose in this example . The radiation pattern is presented on Figure 12 and has a form
where , and .
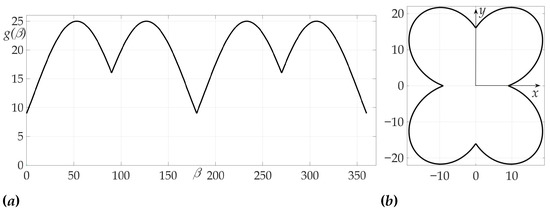
Figure 12.
Radiation pattern as an dependence in polar coordinates (a) and on the Cartesian plane (b).
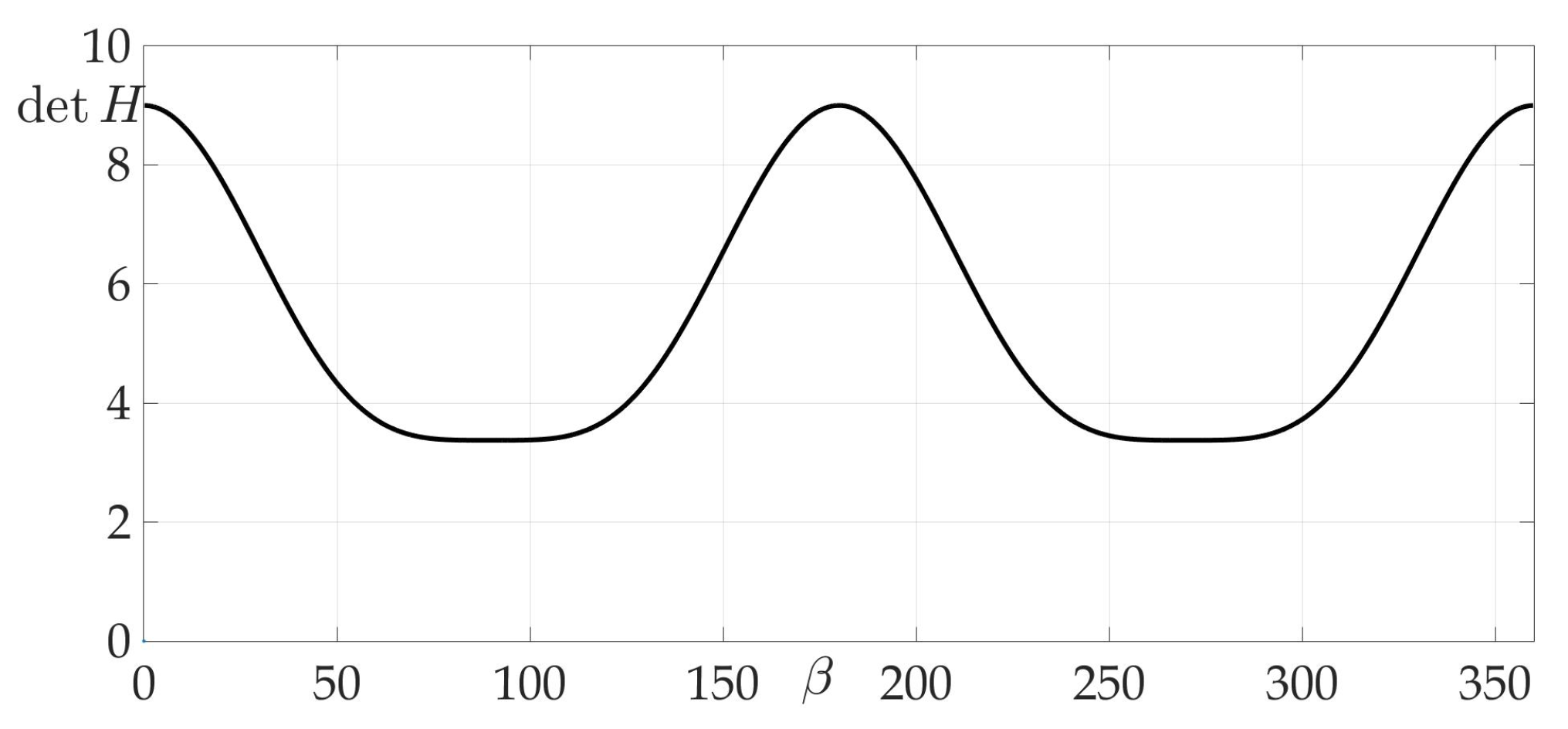
Figure 13 confirms the zeroing of Hessian for given radiation pattern at each of the intervals , , , .
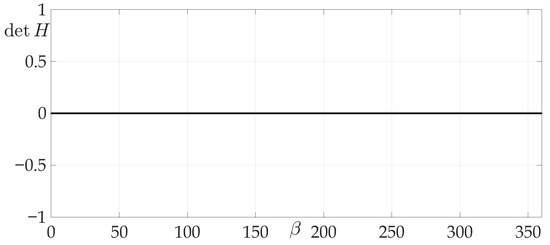
Figure 13.
Dependence of Hessian from .
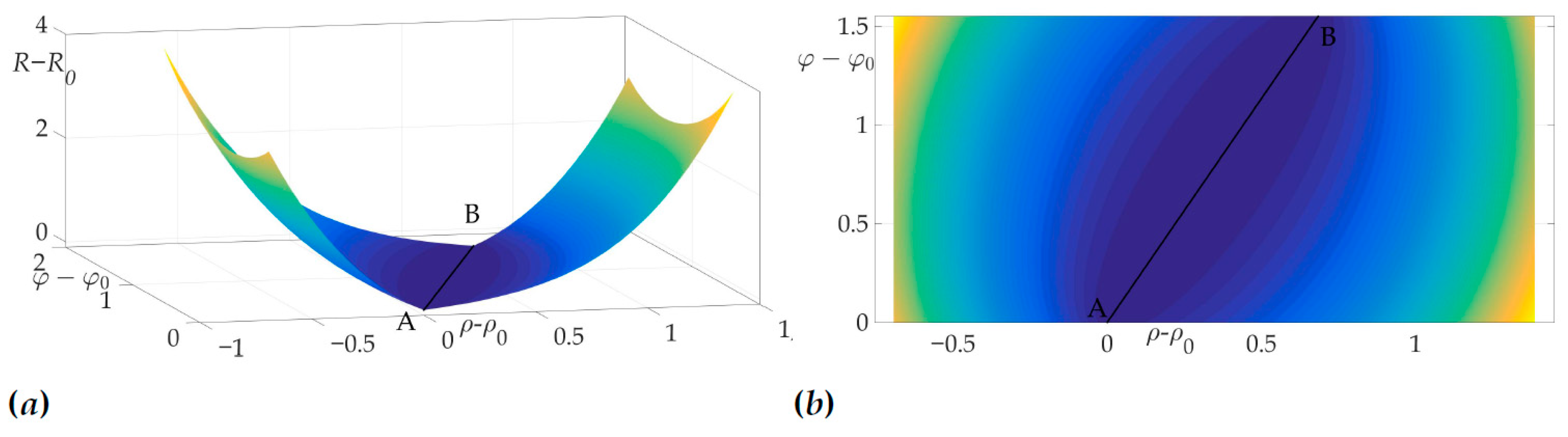
Figure 14 demonstrates the validity of Lemma 8, as it is clear from the risk surface, that risk values of all two-link trajectories lie on a plateau, e.g., they are constant. That means that any two-link trajectory has the same risk value, which equals .
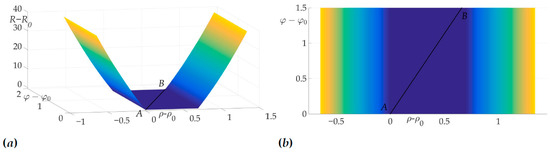
Figure 14.
Optimal trajectory in space (a) and its projection on plane (b).
7.4. Example 4. The Case of Some Extremes of Risk Function
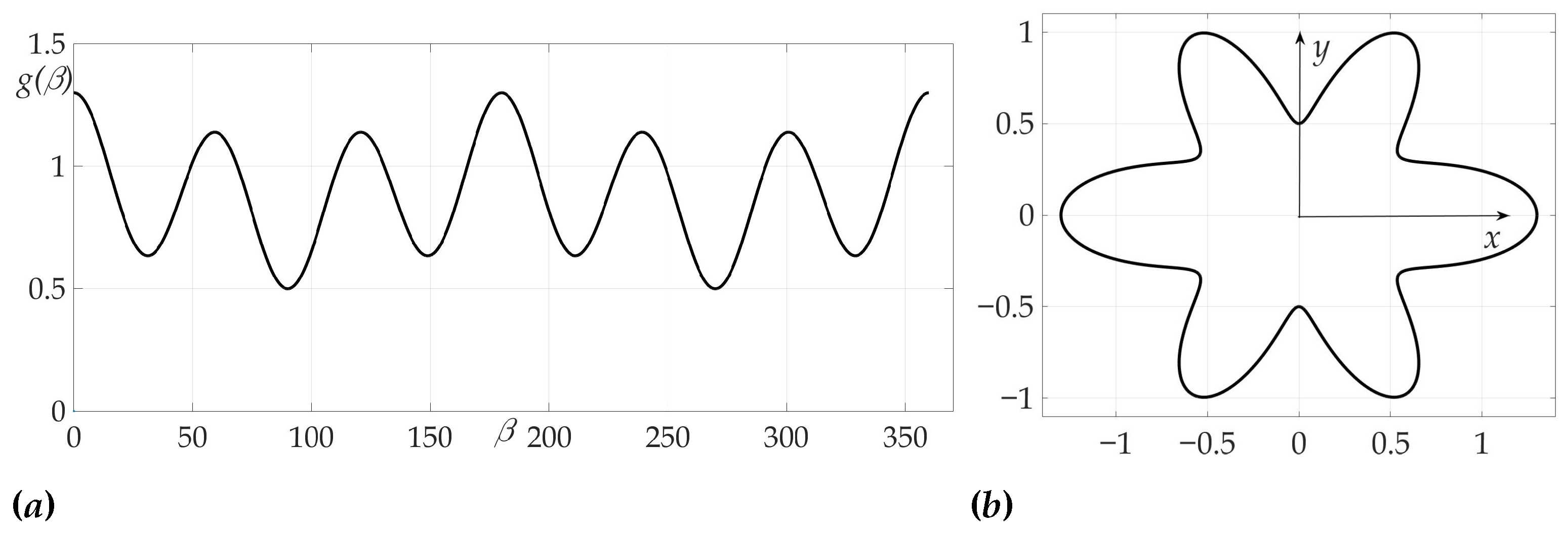
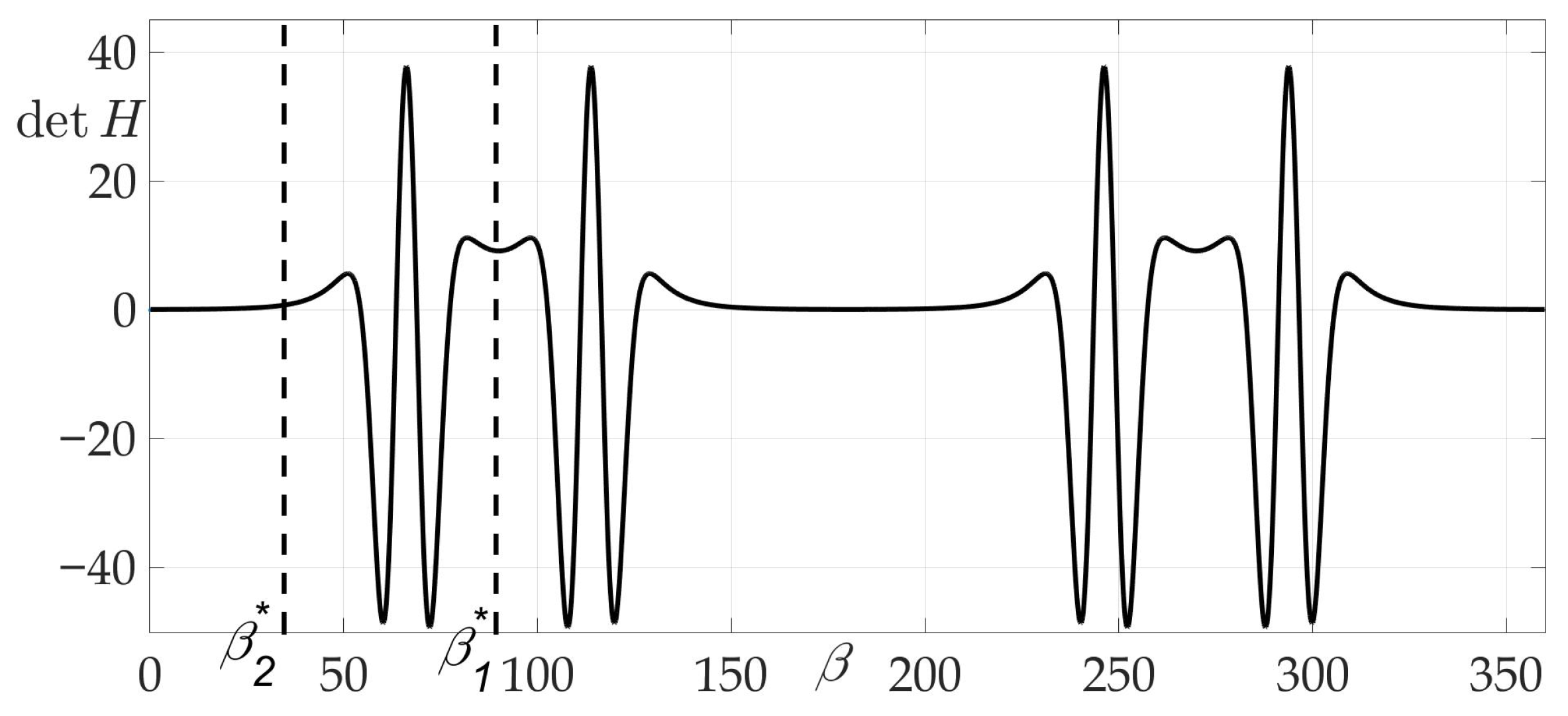
The fourth example considers a complex radiation pattern, shown in Figure 15. In this example .
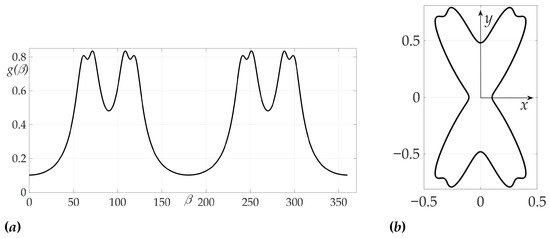
Figure 15.
Radiation pattern as an dependence in polar coordinates (a) and on the Cartesian plane (b).
The peculiarity of this case and chosen radiation pattern can be observed in Figure 16, Figure 17 and Figure 18 —the risk surface contains not only local minimums, but also local maximums, that can be obtained from Theorem 4 and Lemma 8. Trajectories and are two-link trajectories which pass through points and of the risk function local maximum on variables for Problem 3.
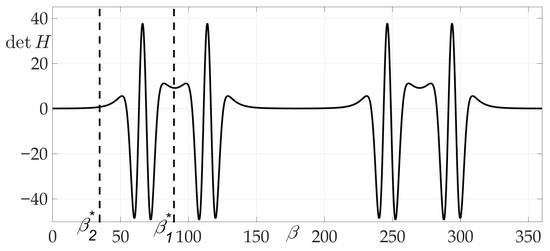
Figure 16.
Dependence of Hessian from .
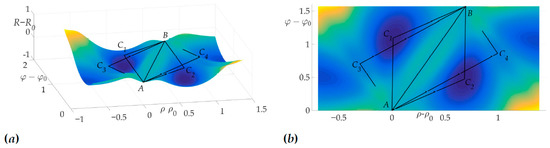
Figure 17.
Optimal trajectory in space (a) and its projection on plane (b).
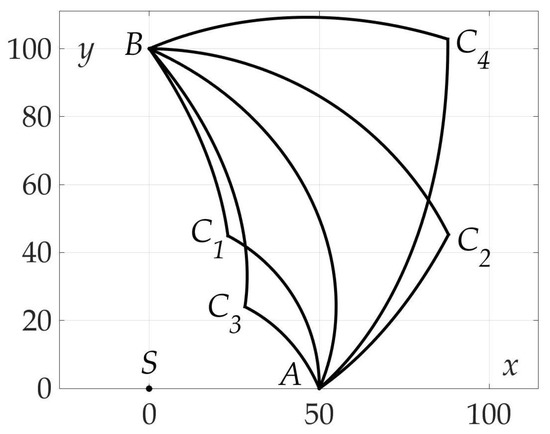
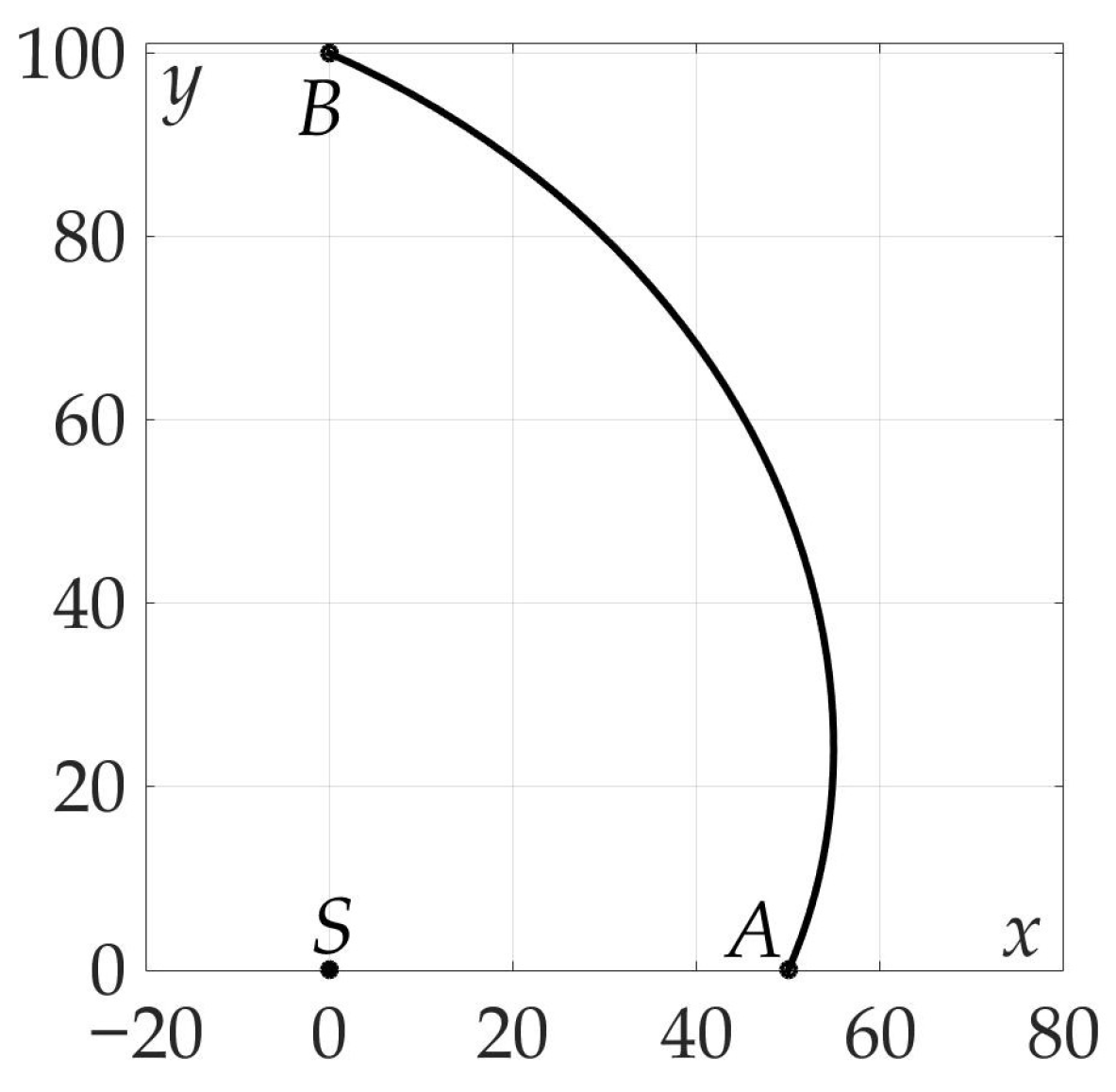
Figure 18.
Optimal trajectory on Cartesian plane.
Route points coordinates are found: , . Optimal angles * and *: , . The values of found risks on these trajectories are . Thus, the gain in risk on two-link trajectory over straight path is approximately 80%.
7.5. Example 5. Independence of Optimal Angle Values * and * from
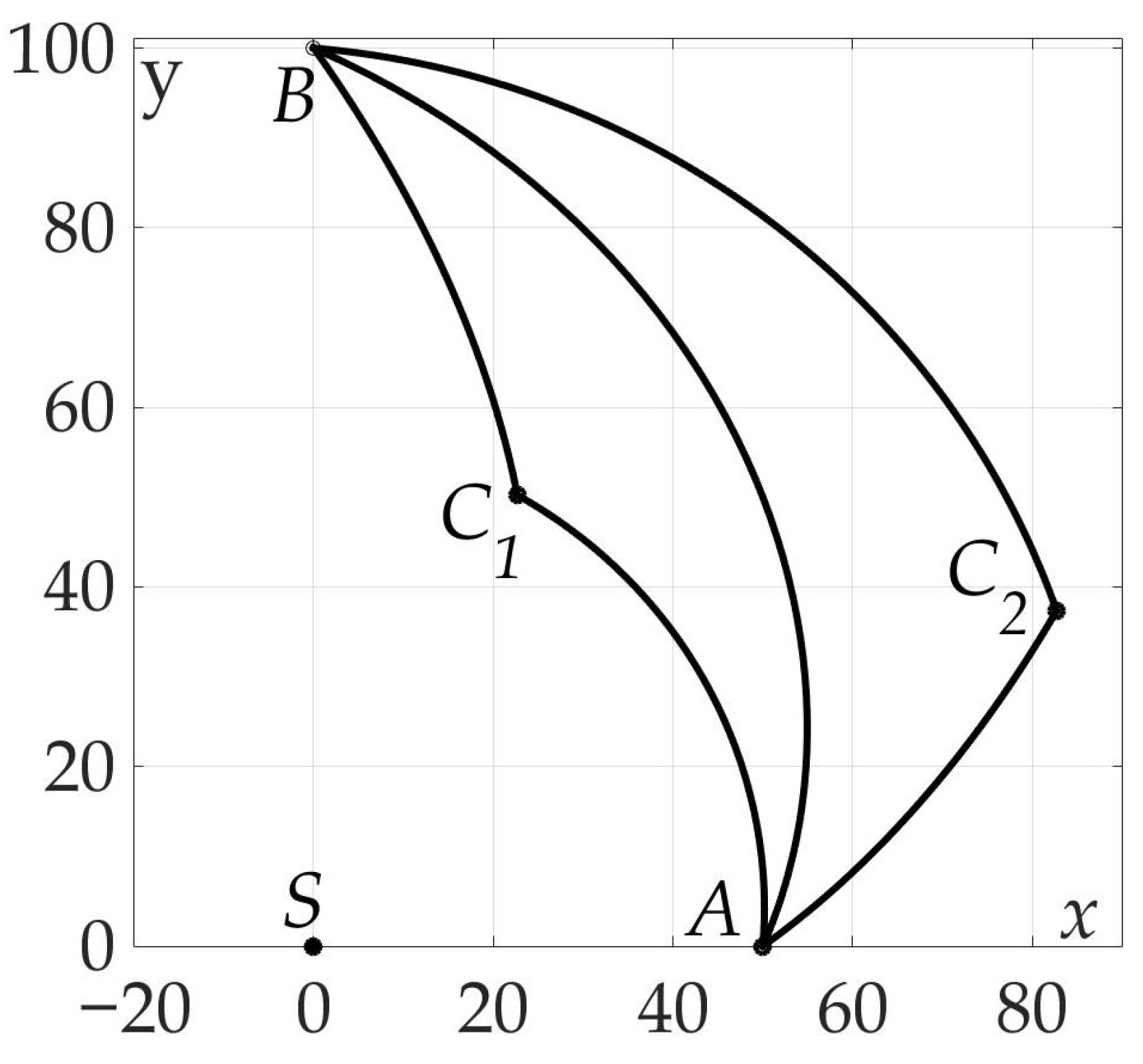
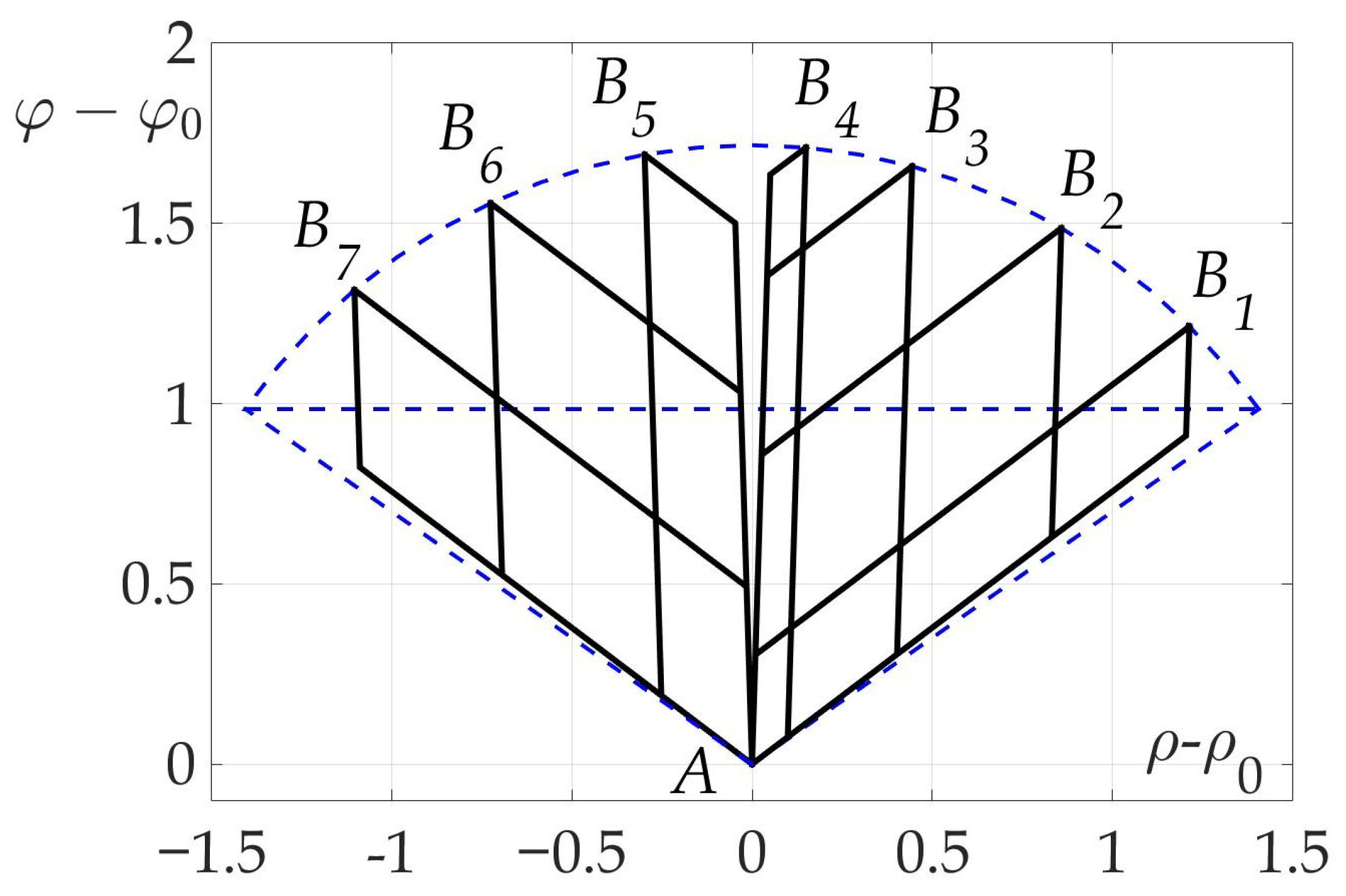
The last example illustrates Theorem 4. A number of trajectories considered with different end points , and the same start point A for a mobile vehicle with fixed radiation pattern. Optimal two-link paths found using numerical algorithm and shown on the plane in Figure 19. It is clear that all of them consist of line segments of two angles * and *-the optimal angles described in Theorem 4.
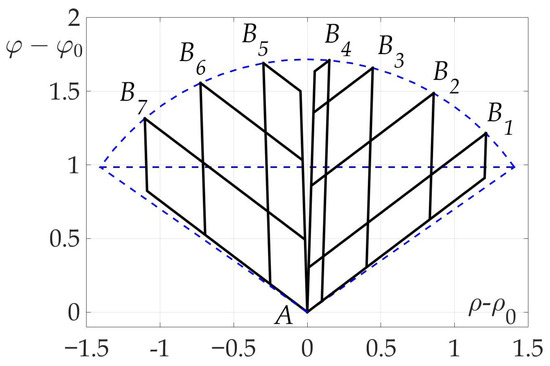
Figure 19.
Some optimal two-link paths with different .
8. Conclusions
The article considers an optimal trajectory planning problem in a threat environment for any type of a mobile vehicle. The main feature of the problem setting is the non-uniform radiation pattern of the vehicle. The TP-problem is set as a variation’s calculus problem, and then it is solved analytically. A series of lemmas and theorems is formulated and proved in the paper. Necessary and sufficient optimality conditions for trajectory considered and examined. Moreover, specific cases of radiation patterns, degenerating these conditions, are studied. As well as simple one-link optimal trajectories, more complex two-link ones are investigated. All analytical solutions are verified numerically and visualised in Matlab programming modules.
The considered problem and the whole class of such TP problems are extremely relevant to modern-warfare applications. Discussed mobile vehicle can be actualized in practice as a UUV or UAV, for example. Obtained solutions can be helpful for design of on-board real-time algorithms for route planning modules of these objects and modules themselves. As shown in examples solving TP problem can significantly reduce the risk value and provide more safety for UUV on the found optimal route in the threat environment.
Future work can be focused on complication and generalization of the mathematical model and optimization functional of the problem. Current article studies search system, that contains only one detection sensor. Increasing the number of sensors and their processed frequencies presents an interesting and important challenge for applications. Physical features of the signal carrying medium, such as attenuation factor, are also yet to be considered.
Author Contributions
Conceptualization, A.A.G.; methodology, A.A.G. and V.P.Y.; software, V.P.Y.; validation, V.P.Y. and P.V.L.; formal analysis, A.A.G., V.P.Y. and P.V.L.; investigation, A.A.G., V.P.Y. and P.V.L.; writing—original draft preparation, A.A.G., P.V.L.; writing—review and editing, A.A.G., P.V.L.; visualization, V.P.Y.; supervision, A.A.G.; project administration, A.A.G.; funding acquisition, A.A.G. All authors have read and agreed to the published version of the manuscript.
Funding
The work of A.A.G. was partially supported by Russian Science Foundation grant 21-19-00128; the work of P.V.L. was partially supported by Russian Foundation for Basic Research grant 20-38-90215; the work of V.P.Y. was partially supported by Programm of Basic Research of RAS.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Data sharing not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
Abbreviations
The following abbreviations are used in this manuscript:
| UUV | Unmanned underwater vehicle |
| PP | Path planning |
| TP | Trajectory planning |
| UAV | Unmanned aerial vehicle |
| SSS | Stationary sonar system |
Appendix A. Proofs
Proof of Lemma 3.
After calculating the first partial derivatives of S with respect to , , using equality , one can get
Proof of Corollary 1.
The next chain of equations is valid
From the last equation follows that
□
Proof of Lemma 6.
According to Lemma 2 the values of risk on each segment are
where notations are introduced as follows
The restriction on times and has a linear form
Now the sum of must be minimized by , . Let us find optimal values of and by solving next optimization problem
The necessary condition of extremum of the function described by Equation (A9) is equality to zero of its derivative on variable :
Due to the fact, that Equation (A9) presents a continuous, differentiable function with and , Equation (A10) states condition of the minimum of , e.g., its unique solution is the :
Thus and are
After substituting Equations (A12) into the first two equations of system (A6), the final expressions for signals and can be obtained
As one can see, Equation (A13) is similar to Equation (A14), e.g., values of signal are equal on two segments of the optimal trajectory.
The whole risk on the full trajectory:
□
Proof of Corollary 2.
From triangles in Figure 3 the equations follow
From the first equation can be expressed
Proof of Lemma 7.
Let us multiple one equation from system (34) by another
This equation leads to the chain of expressions
where new variables and are used
From tangent functions in Equation (A20) it is easy to go to cosine functions
Now instead of multiplying let us divide one equation from system (34) by another
This equation leads to the chain of expressions
Using variables and introduced in Equation (A21), the last equation can be rewritten as
This equation can be transformed to
References
- Galyaev, A.A.; Maslov, E.P. Optimization of a mobile object evasion laws from detection. J. Comput. Syst. Sci. Int. 2010, 49, 560–569. [Google Scholar] [CrossRef]
- Kabamba, P.; Meerkov, S.; Zeitz, F. Optimal Path Planning for Unmanned Combat Aerial Vehicles to Defeat Radar Tracking. J. Guid. Control. Dyn. 2006, 29, 279–288. [Google Scholar] [CrossRef]
- Sidhu, H.; Mercer, G.; Sexton, M. Optimal trajectories in a threat environment. J. Battlef. Technol. 2006, 9, 33–39. [Google Scholar]
- Pachter, L.S.; Pachter, M. Optimal path for avoiding a radiating source. In Proceedings of the 40 IEEE Conference on Decision and Control (Cat. No.01CH37228), Orlando, FL, USA, 4–7 December 2001; pp. 3581–3686. [Google Scholar]
- Chung, H.; Polak, E.; Royset, J. On the Optimal Detection of an Underwater Intruder in a Channel using Unmanned Underwater Vehicles. Naval Res. Logist. 2010, 57, 405–417. [Google Scholar] [CrossRef]
- Galyaev, A.A.; Dobrovidov, A.V.; Lysenko, P.V.; Shaikin, M.E.; Yakhno, V.P. Path Planning in Threat Environment for UUV with Non-Uniform Radiation Pattern. Sensors 2020, 20, 2076. [Google Scholar] [CrossRef] [PubMed]
- Panda, M.; Das, B.; Subudhi, B.; Pati, B.B. A Comprehensive Review of Path Planning Algorithms for Autonomous Underwater Vehicles. Int. J. Autom. Comput. 2020. [Google Scholar] [CrossRef]
- Vian, J.L.; More, J.R. Trajectory optimization with risk minimization for military aircraft. AIAA J. Guid. Contr. Dynam. 1989, 12, 311–317. [Google Scholar] [CrossRef]
- Wang, Z.-j. Maximizing the Probability an aerial anti-submarine torpedo detects its target. J. Marine Sci. Appl. 2009, 8, 175–181. [Google Scholar] [CrossRef]
- Zabarankin, M.; Uryasev, S.; Murphey, R. Aircraft Routing under the Risk of Detection. Naval Res. Logist. 2006, 53, 728–747. [Google Scholar] [CrossRef]
- Zhang, M.; Su, C.; Liu, Y.; Hu, M.; Zhu, Y. Unmanned Aerial Vehicle Route Planning in the Presence of a Threat Environment Based on a Virtual Globe Platform. ISPRS Int. J. Geo-Inf. 2016, 5, 184. [Google Scholar] [CrossRef]
- Keung, G.; Li, B.; Zhang, Q. The Intrusion Detection in Mobile Sensor Network. Proc. ACM MobiHoc. 2010, 20, 11–20. [Google Scholar] [CrossRef]
- Sidhu, H.; Mercer, G. Two continuous methods for determining a minimal risk path through a minefield. Anziam. J. 2006, 48, 293–306. [Google Scholar]
- Hespanha, J.P.; Kizilocak, H.H.; Ateskan, Y.S. Probabilistic map building for aircraft-tracking radars. Proc. Am. Control. Conf. 2001, 6, 4381–4386. [Google Scholar]
- Galyaev, A.A.; Lysenko, P.V. Evasion of moving object from single detector at given velocity. Control. Probl. 2020, 1, 83–91. [Google Scholar]
- Barrios-dV, S.; Lopez-Franco, M.; Rios, J.D.; Arana-Daniel, N.; Lopez-Franco, C.; Alanis, A.Y. An Autonomous Path Controller in a System on Chip for Shrimp Robot. Electronics 2020, 9, 441. [Google Scholar] [CrossRef]
- Ajeil, F.H.; Ibraheem, I.K.; Azar, A.T.; Humaidi, A.J. Grid-Based Mobile Robot Path Planning Using Aging-Based Ant Colony Optimization Algorithm in Static and Dynamic Environments. Sensors 2020, 20, 1880. [Google Scholar] [CrossRef] [PubMed]
- Cui, J.-H.; Wei, R.-X.; Liu, Z.-C.; Zhou, K. UAV Motion Strategies in Uncertain Dynamic Environments: A Path Planning Method Based on Q-Learning Strategy. Appl. Sci. 2018, 8, 2169. [Google Scholar] [CrossRef]
- Panov, A.I.; Yakovlev, K.S.; Suvorov, R. Grid Path Planning with Deep Reinforcement Learning: Preliminary Results. Procedia Comput. Sci. 2018, 123, 347–353. [Google Scholar] [CrossRef]
- Rehbock, V.; Caccetta, L.; Hallam, C.L.; O’Dowd, R. Optimal Submarine Transit Paths Through Sonar Fields; Research Report; Department of Mathematics and Statistics, Curtin University of Technology: Western, Australia, 2000. [Google Scholar]
- Shaikin, M.E. On statistical risk funstional in a control problem for an object moving in a conflict environment. J. Comput. Syst. Sci. Int. 2011, 1, 22–31. [Google Scholar]
- Galyaev, A.A. Evasion on plane from a single mobile observer in the conflict environment. Autom. Remote. Control. 2014, 75, 1017–1024. [Google Scholar] [CrossRef]
- Zelinka, I.; Snášel, V.; Abraham, A. (Eds.) Handbook of Optimization; Intelligent Systems Reference Library; Springer: Berlin, Germany, 2013. [Google Scholar]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).