Enhancing Trust in Transactive Energy with Individually Linkable Pseudonymous Trading Using Smart Contracts
Abstract
:1. Introduction
- New functionality: previous systems had to decide between total anonymity and capacity to respond to errors. By enabling total but revocable privacy, ILPTS enables functionality not seen in other transactive energy market proposals. This would enable a DSO to be more responsive to network errors and to provide novel services such as in-home maintenance to users.
- Enhanced privacy: ILPTS would enhance the privacy of the basic blockchain-based TEM model by providing anonymity to energy clients. When implemented in a model that already provides this anonymity, ILPTS improves its functionality while retaining the existing anonymity. When implemented in a model with partial trust—i.e., anonymity in the public market but identities registered with the DSO—ILPTS improves privacy by hiding the user’s identity more comprehensively, creating an effectively trustless system.
- Equity: ILPTS improves the fairness of TEM models by enabling repudiation and mediation, obviating the need for coarse punitive measures such as disconnecting power, and reducing false positives in fraud and malware detection.
- Improved security: while enabling the previously mentioned benefits, ILPTs’s novel registration process is secure and fully distributed. Information is concealed and encrypted at every stage. In addition, the deanonymization process can only be initiated by the monitoring smart contract, greatly reducing the potential for abuse.
2. Related Work
3. Background and Motivation
3.1. Network Architecture
- Distribution system operator (DSO): a centralized authority that authenticates users and manages the distribution (or retail) energy market.
- Smart meters: users connect to the grid and distributed market via smart meters.
- Fog nodes: auxiliary network computing nodes with elevated status and trust.
- Blockchain: a distributed ledger on which transactions and other information will be recorded.
- Smart contracts: scripts that execute on the blockchain and that may facilitate additional functionality or public information transfer.
3.2. Blockchain Markets
3.3. Reputation Mechanisms
3.4. Coin Mixing
3.5. Problem Statement
3.6. Design Requirements
- Trustless: The system architecture supporting the scheme shall not rely on any participant being 100% honest.
- Distributed: The scheme shall rely on as few central authorities as possible in order to function.
- Individual Identification: The scheme shall allow an individual to be identified from their pseudonym; not just a batch of users.
- Total Anonymity: When trading, users shall be anonymous to all parties, including the DSO.
- Transparency: The operations performed should be transparent to all users to promote trust in the system and fellow participants.
- Restorable Privacy: After a user has been identified, they shall be able to resume trading under a new pseudonym with total anonymity.
- Automated: The process of registering, validating, deanonymizing, and reanonymizing users shall be automated and require no manual intervention.
- Snoop-Resistant: A curious party shall be prevented from revealing the true identity of a particular pseudonym, regardless of their level of privilege in the system. This shall be true at every stage of the process, including registration and deanonymization.
4. Methodology
5. ILPTS Scheme
5.1. Overview
5.2. Formal Description
5.2.1. Onboarding
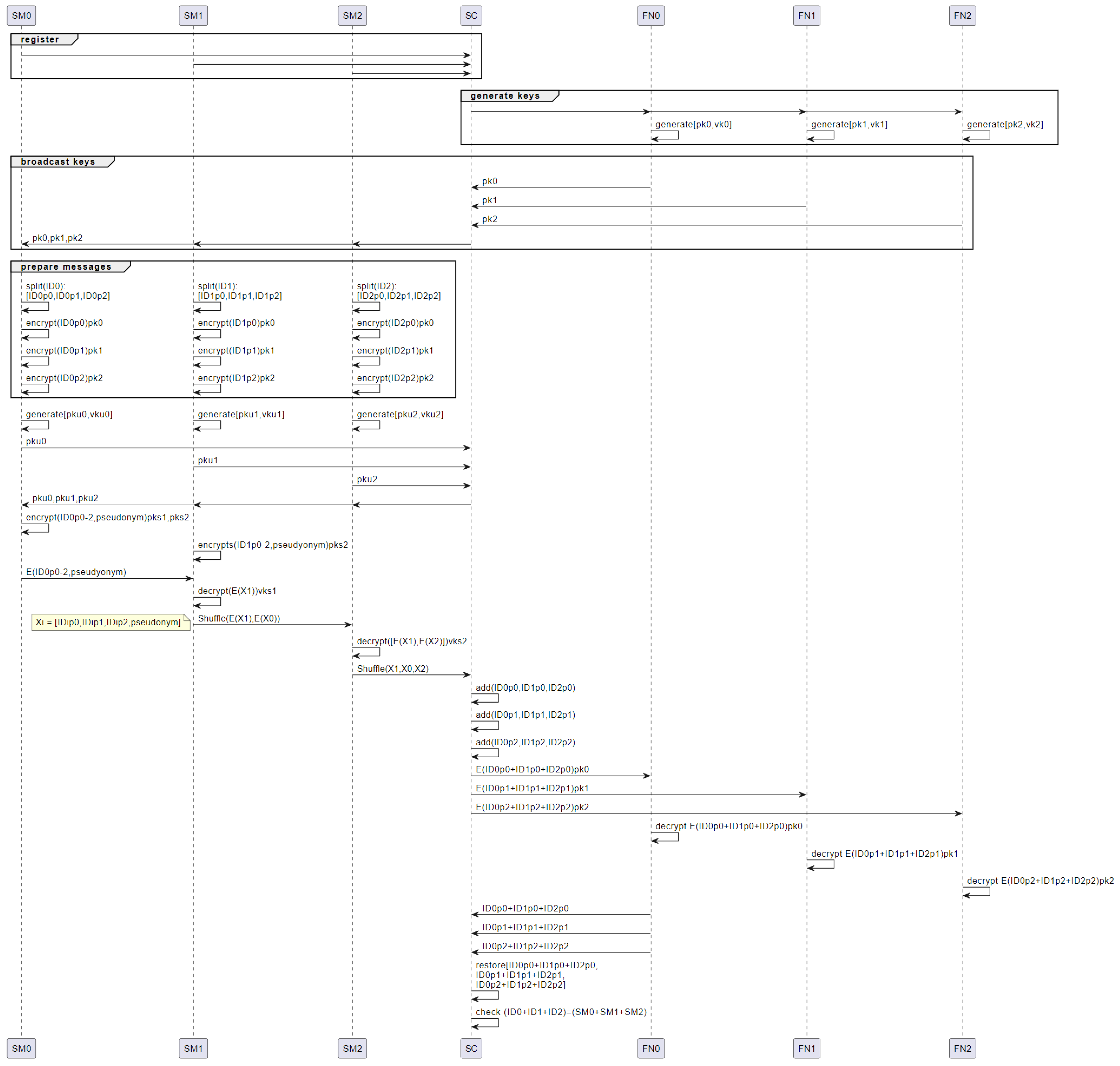
- A batch of users with identifiers through join.
- A subset of fog nodes is requested, denoted through .
- Fog nodes through generate public keys through respectively.
- Each fog node sends its public key to the smart contract .
- The smart contract sends all public keys to each of the users .
| real ID of user | |
| part j of | |
| fog node | |
| of fog node | |
| of user | |
| list of s in batch B | |
| pseudonym of user | |
| ⊕ | homomorphic addition |
| smart contract | |
| cyphertext of X encrypted using | |
| divisions of data | |
| n | max FN ID when registering () |
| threshold to reconstruct data | |
| k | max FN ID when deanonymizing () |
| B | batch of users registering |
| number of users in batch | |
| N | max user ID when registering () |
| X sends W to Y | |
| X receives Z from Y | |
| registration data of user | |
| list containing registration data | |
| state of list at user | |
| randomize order of elements in list Y | |
| use [35] to generate |
| Algorithm 1 Registration. |
|
| Algorithm 2 Validation. |
|
5.2.2. Deanonymization
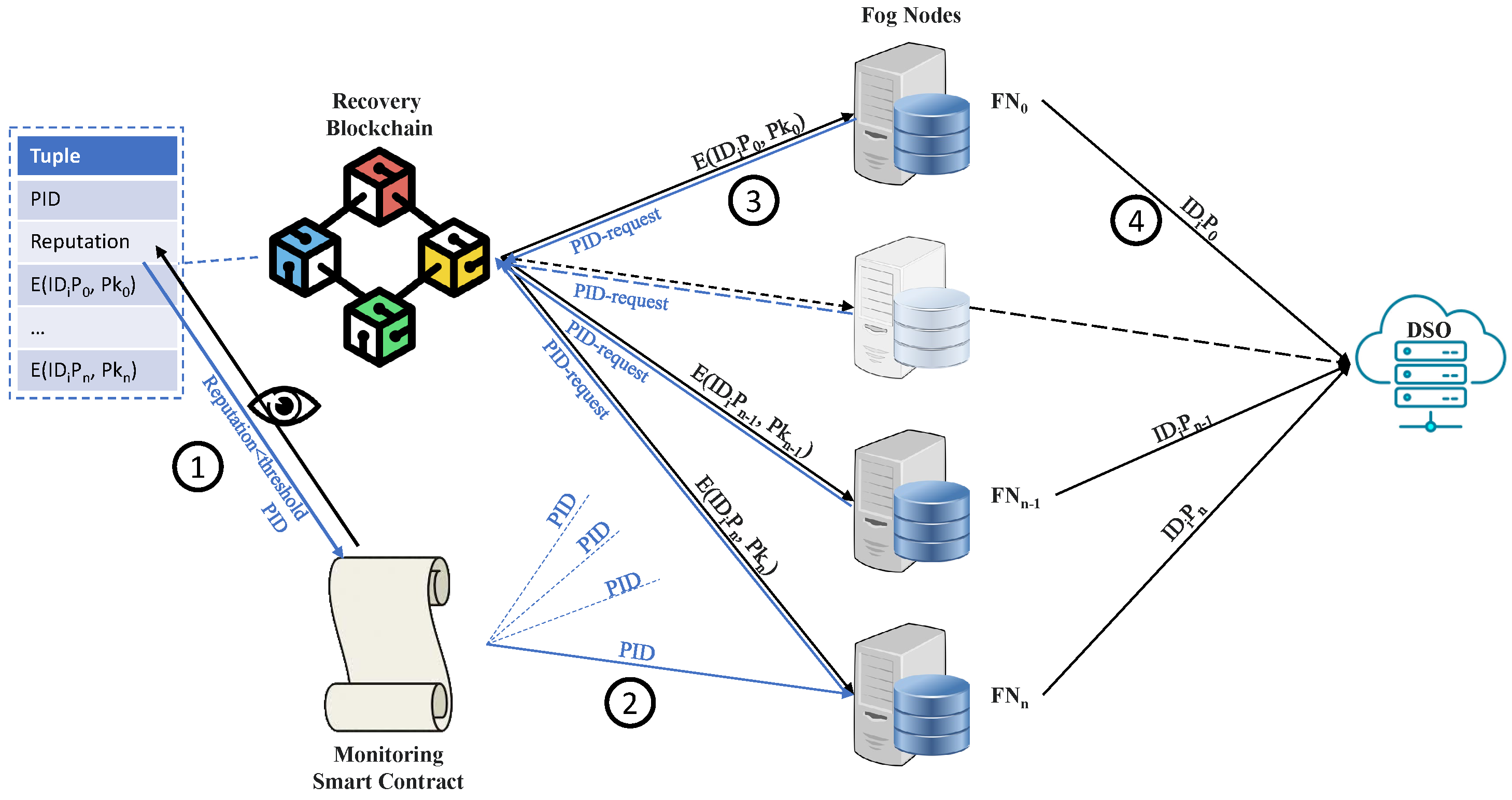
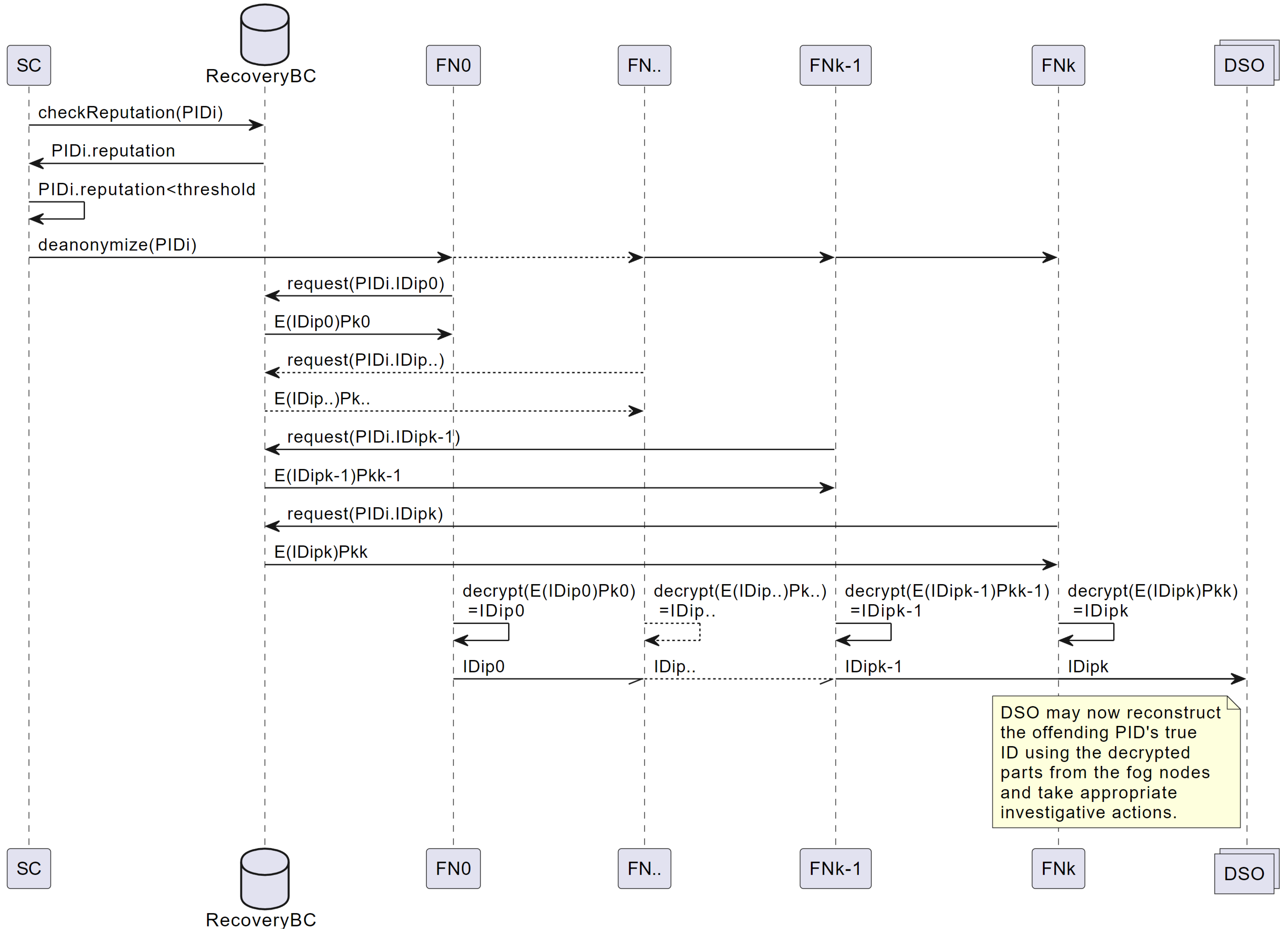
- When the smart contract finds a reputation value below the threshold, it sends the of the offending pseudonymous user to all fog nodes.
- Each fog node then retrieves the appropriate encrypted ID part from the tuple containing on the recovery blockchain.
- Each fog node uses its private key to decrypt , producing .
- The fog nodes each send this plaintext to the DSO.
- The DSO then performs .
- The DSO can now use its customer database to retrieve ’s contact details and resolve the abnormality.
5.3. Full Sequence Diagrams
6. Discussion and Analysis
6.1. Design Evaluation against Requirements
- Trustless: The system successfully achieves a nearly trustless architecture. Registration and deanonymization are both automated and distributed, meaning no central authority or trusted third party is required. The only trust involved is that the fog nodes will correctly decrypt and forward the appropriate information to the DSO during deanonymization, but they are incentivized to do so, as we discuss in Section 6.2. Fog nodes could theoretically collude to deanonymize individual users, but due to the properties of the secret sharing scheme employed, such an attack would require k or more malicious nodes [35].
- Decentralized: The registration process requires a blockchain, which is decentralized by nature, smart contracts, and fog nodes—no central authority. From this perspective, the scheme succeeds at this design goal. The fog nodes are semi-trusted; however, only a subset are required and they are interchangeable to a point. The monitoring and deanonymization processes are handled entirely by a smart contract and fog nodes. The information is of course transmitted to the DSO, but the process of deanonymizing the user for them is entirely automated and distributed. Moreover, the information sent to the DSO is not pre-reconstructed, making it less vulnerable to attacks (which we discuss in Section 6.2).
- Individual Identification: ILTPS successfully allows users to sign up in batch, with validation that does not compromise the anonymity of their pseudonym, while still enabling individual identification when necessary.
- Total Anonymity: Total anonymity is achieved since the true identities of the pseudonyms are split into many pieces which are each encrypted by different fog nodes. This property is important because previous schemes have had to decide between sacrificing a level of anonymity (by registering with the DSO) or traceability (having no mechanism to identify a pseudonym).
- Transparency: The registration and validation process happen entirely on-chain and automatically, providing assurance to market participants that their peers have been honestly validated. In addition, the recovery blockchain is publicly visible and read-only, so manipulation is both improbable and detectable.
- Restorable Privacy: A user can be reanonymized by simply undergoing the registration process again. If no new users are being added, a subset of existing users can be re-registered automatically to facilitate the batch registration process.
- Automated: All information exchange and validation are handled automatically by an on-chain smart contract, fulfilling this design goal. Additionally, reputation monitoring and requests to fog nodes to deanonymize a target user are also handled automatically by a smart contract.
- Snoop-Resistant: This design goal is achieved because the deanonymization process is initiated by the smart contract. The contract is written in such a way that manually initiating this process is not possible; it only occurs when a user’s reputation is detected to have fallen below a certain threshold.
6.2. Threat Analysis
6.2.1. Trust
- Failure to oblige will cost their privileged status in the network, creating an implicit incentive to comply.
- Only k of n fog nodes need to comply (and not fault) in order for deanonymization to be successfully performed, meaning that some number of nodes could, in fact, maliciously not comply without affecting the integrity of the scheme. This ratio can be set arbitrarily by the DSO to their desired security level.
6.2.2. Reputation Attack
6.2.3. Man-in-the-Middle Attack
- (A)
- during registration
- (B)
- during registration
- (C)
- during registration
- (D)
- during deanonymization
- (E)
- during deanonymization
6.2.4. Robustness to Failure
6.2.5. Collusion
6.3. Synergies
6.4. Improvements
7. Conclusions and Future Work
- Users are totally anonymous to all parties;
- This anonymity can be uncovered only by an autonomous system under specific circumstances;
- Anonymity can be restored when required;
- The solution does not contain centralized vulnerabilities.
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| AMI | Advanced Metering Infrastructure |
| A-PoL | Anonymous Proof of Location |
| CHEA | Cyclic Homomorphic Encryption Aggregation |
| DSO | Distributed System Operator |
| EV | Electric Vehicle |
| FN | Fog Node |
| HE | Homomorphic Encryption |
| ID | Identifier |
| ILPTS | Individually Linkable Pseudonymous Trading Scheme |
| PID | Pseudonymous ID |
| SG | Smart Grid |
| SM | Smart Meter |
| TE | Transactive Energy |
| TEM | Transactive Energy Market |
| VPP | Virtual Power Plant |
References
- Lombardi, F.; Aniello, L.; De Angelis, S.; Margheri, A.; Sassone, V. A Blockchain-based Infrastructure for Reliable and Cost-effective IoT-aided Smart Grids. In Proceedings of the Living in the Internet of Things: Cybersecurity of the IoT, London, UK, 28–29 March 2018. [Google Scholar] [CrossRef]
- Uribe-Pérez, N.; Hernández, L.; De la Vega, D.; Angulo, I. State of the Art and Trends Review of Smart Metering in Electricity Grids. Appl. Sci. 2016, 6, 68. [Google Scholar] [CrossRef]
- Hassan, A.; Afrouzi, H.N.; Siang, C.H.; Ahmed, J.; Mehranzamir, K.; Wooi, C.L. A survey and bibliometric analysis of different communication technologies available for smart meters. Clean. Eng. Technol. 2022, 7, 100424. [Google Scholar] [CrossRef]
- Chen, T.; Alsafasfeh, Q.; Pourbabak, H.; Su, W. The Next-Generation U.S. Retail Electricity Market with Customers and Prosumers–A Bibliographical Survey. Energies 2018, 11, 8. [Google Scholar] [CrossRef]
- Sousa-Dias, D.; Amyot, D.; Rahimi-Kian, A.; Mylopoulos, J. A Review of Cybersecurity Concerns for Transactive Energy Markets. Energies 2023, 16, 4838. [Google Scholar] [CrossRef]
- Kirli, D.; Couraud, B.; Robu, V.; Salgado-Bravo, M.; Norbu, S.; Andoni, M.; Antonopoulos, I.; Negrete-Pincetic, M.; Flynn, D.; Kiprakis, A. Smart contracts in energy systems: A systematic review of fundamental approaches and implementations. Renew. Sustain. Energy Rev. 2022, 158, 112013. [Google Scholar] [CrossRef]
- Khan, H.; Masood, T. Impact of Blockchain Technology on Smart Grids. Energies 2022, 15, 7189. [Google Scholar] [CrossRef]
- Asghar, M.R.; Dán, G.; Miorandi, D.; Chlamtac, I. Smart Meter Data Privacy: A Survey. IEEE Commun. Surv. Tutor. 2017, 19, 2820–2835. [Google Scholar] [CrossRef]
- McDaniel, P.; McLaughlin, S. Security and Privacy Challenges in the Smart Grid. IEEE Secur. Priv. 2009, 7, 75–77. [Google Scholar] [CrossRef]
- Eisele, S.; Eghtesad, T.; Campanelli, K.; Agrawal, P.; Laszka, A.; Dubey, A. Safe and Private Forward-Trading Platform for Transactive Microgrids. ACM Trans. Cyber-Phys. Syst. 2021, 5, 1–29. [Google Scholar] [CrossRef]
- Duguma, D.G.; Zhang, J.; Aboutalebi, M.; Zhang, S.; Banet, C.; Bjørkli, C.; Baramashetru, C.; Eliassen, F.; Zhang, H.; Muringani, J.; et al. Privacy-preserving transactive energy systems: Key topics and open research challenges. arXiv 2023, arXiv:2312.11564. [Google Scholar]
- Sharma, G.; Joshi, A.M.; Mohanty, S.P. sTrade: Blockchain based secure energy trading using vehicle-to-grid mutual authentication in smart transportation. Sustain. Energy Technol. Assess. 2023, 57, 103296. [Google Scholar] [CrossRef]
- Garg, S.; Kaur, K.; Kaddoum, G.; Gagnon, F.; Rodrigues, J.J.P.C. An Efficient Blockchain-Based Hierarchical Authentication Mechanism for Energy Trading in V2G Environment. In Proceedings of the 2019 IEEE International Conference on Communications Workshops (ICC Workshops), Shanghai, China, 20–24 May 2019; pp. 1–6. [Google Scholar] [CrossRef]
- Li, D.; Yang, Q.; An, D.; Yu, W.; Yang, X.; Fu, X. On Location Privacy-Preserving Online Double Auction for Electric Vehicles in Microgrids. IEEE Internet Things J. 2019, 6, 5902–5915. [Google Scholar] [CrossRef]
- Li, D.; Yang, Q.; Yu, W.; An, D.; Yang, X.; Zhao, W. A strategy-proof privacy-preserving double auction mechanism for electrical vehicles demand response in microgrids. In Proceedings of the 2017 IEEE 36th International Performance Computing and Communications Conference (IPCCC), San Diego, CA, USA, 10–12 December 2017; pp. 1–8. [Google Scholar] [CrossRef]
- Baza, M.; Amer, R.; Rasheed, A.; Srivastava, G.; Mahmoud, M.; Alasmary, W. A Blockchain-Based Energy Trading Scheme for Electric Vehicles. In Proceedings of the 2021 IEEE 18th Annual Consumer Communications & Networking Conference (CCNC), Las Vegas, NV, USA, 9–12 January 2021; pp. 1–7. [Google Scholar] [CrossRef]
- Baza, M.; Sherif, A.; Mahmoud, M.M.E.A.; Bakiras, S.; Alasmary, W.; Abdallah, M.; Lin, X. Privacy-Preserving Blockchain-Based Energy Trading Schemes for Electric Vehicles. IEEE Trans. Veh. Technol. 2021, 70, 9369–9384. [Google Scholar] [CrossRef]
- Bergquist, J.; Laszka, A.; Sturm, M.; Dubey, A. On the Design of Communication and Transaction Anonymity in Blockchain-Based Transactive Microgrids. In Proceedings of the 1st Workshop on Scalable and Resilient Infrastructures for Distributed Ledgers (SERIAL ’17), New York, NY, USA, 11–15 December 2017. [Google Scholar] [CrossRef]
- Laszka, A.; Dubey, A.; Walker, M.; Schmidt, D. Providing Privacy, Safety, and Security in IoT-Based Transactive Energy Systems using Distributed Ledgers. In Proceedings of the Seventh International Conference on the Internet of Things, Linz, Austria, 22–25 October 2017. [Google Scholar] [CrossRef]
- Khorasany, M.; Dorri, A.; Razzaghi, R.; Jurdak, R. Lightweight blockchain framework for location-aware peer-to-peer energy trading. Int. J. Electr. Power Energy Syst. 2021, 127, 106610. [Google Scholar] [CrossRef]
- Mollah, M.B.; Zhao, J.; Niyato, D.; Lam, K.Y.; Zhang, X.; Ghias, A.M.Y.M.; Koh, L.H.; Yang, L. Blockchain for Future Smart Grid: A Comprehensive Survey. IEEE Internet Things J. 2021, 8, 18–43. [Google Scholar] [CrossRef]
- Ziu, D.; Verber, M.; Croce, V. iVPP P2P Transactive Energy Framework, 2022. EU Horizon 2020 Project IANOS, Deliverable D4.9. Available online: https://ianos.eu/wp-content/uploads/2022/09/IANOS_D4.9.pdf (accessed on 1 May 2024).
- Kang, E.S.; Pee, S.J.; Song, J.G.; Jang, J.W. A Blockchain-Based Energy Trading Platform for Smart Homes in a Microgrid. In Proceedings of the 2018 3rd International Conference on Computer and Communication Systems (ICCCS), Nagoya, Japan, 27–30 April 2018; pp. 472–476. [Google Scholar] [CrossRef]
- Honari, K.; Rouhani, S.; Falak, N.E.; Liu, Y.; Li, Y.; Liang, H.; Dick, S.; Miller, J. Smart Contract Design in Distributed Energy Systems: A Systematic Review. Energies 2023, 16, 4797. [Google Scholar] [CrossRef]
- Münsing, E.; Mather, J.; Moura, S. Blockchains for decentralized optimization of energy resources in microgrid networks. In Proceedings of the 2017 IEEE Conference on Control Technology and Applications (CCTA), Kohala Coast, HI, USA, 27–30 August 2017; pp. 2164–2171. [Google Scholar] [CrossRef]
- Buterin, V. Ethereum White Paper: A Next Generation Smart Contract & Decentralized Application Platform. 2013. Available online: https://ethereum.org/en/whitepaper/ (accessed on 1 May 2024).
- Zaman, I.; He, M. A Multilayered Semi-Permissioned Blockchain Based Platform for Peer to Peer Energy Trading. In Proceedings of the 2021 IEEE Green Technologies Conference (GreenTech), Virtual, 7–9 April 2021; pp. 279–285. [Google Scholar] [CrossRef]
- Nazari, M.; Khorsandi, S.; Babaki, J. Security and Privacy Smart Contract Architecture for Energy Trading based on Blockchains. In Proceedings of the 2021 29th Iranian Conference on Electrical Engineering (ICEE), Tehran, Iran, 18–20 May 2021; pp. 596–600. [Google Scholar] [CrossRef]
- Zhang, P.; Wu, P.; Liu, Y.; Chen, Y.; Li, Y.; Yan, J.; Ghafouri, M. Toward a Blockchain-Based, Reputation-Aware Secure Transactive Energy Market. Blockchains 2024, 2, 61–78. [Google Scholar] [CrossRef]
- Jayachandran, M.; Rao, K.P.; Gatla, R.K.; Kalaivani, C.; Kalaiarasy, C.; Logasabarirajan, C. Operational concerns and solutions in smart electricity distribution systems. Util. Policy 2022, 74, 101329. [Google Scholar] [CrossRef]
- Ruffing, T.; Moreno-Sanchez, P.; Kate, A. CoinShuffle: Practical Decentralized Coin Mixing for Bitcoin. In Proceedings of the Computer Security—ESORICS 2014: 19th European Symposium on Research in Computer Security, Wroclaw, Poland, 7–11 September 2014; Kutyłowski, M., Vaidya, J., Eds.; Springer International Publishing: Cham, Switzerland, 2014; pp. 345–364. [Google Scholar]
- Chen, G.; He, M.; Gao, J.; Liu, C.; Yin, Y.; Li, Q. Blockchain-Based Cyber Security and Advanced Distribution in Smart Grid. In Proceedings of the 2021 IEEE 4th International Conference on Electronics Technology (ICET), Chengdu, China, 7–10 May 2021; pp. 1077–1080. [Google Scholar] [CrossRef]
- Afzal, M.; Li, J.; Amin, W.; Huang, Q.; Umer, K.; Ahmad, S.A.; Ahmad, F.; Raza, A. Role of blockchain technology in transactive energy market: A review. Sustain. Energy Technol. Assess. 2022, 53, 102646. [Google Scholar] [CrossRef]
- Zhuang, P.; Zamir, T.; Liang, H. Blockchain for Cybersecurity in Smart Grid: A Comprehensive Survey. IEEE Trans. Ind. Inform. 2021, 17, 3–19. [Google Scholar] [CrossRef]
- Shamir, A. How to Share a Secret. Commun. ACM 1979, 22, 612–613. [Google Scholar] [CrossRef]
- Paillier, P. Public-Key Cryptosystems Based on Composite Degree Residuosity Classes. In Proceedings of the Advances in Cryptology — EUROCRYPT ’99: International Conference on the Theory and Application of Cryptographic Techniques, Prague, Czech Republic, 2–6 May 1999; Stern, J., Ed.; Springer: Berlin/Heidelberg, Germany, 1999; pp. 223–238. [Google Scholar]
- Paillier, P.; Pointcheval, D. Efficient Public-Key Cryptosystems Provably Secure Against Active Adversaries. In Proceedings of the Advances in Cryptology—ASIACRYPT’99, Singapore, 14–18 November 1999; Lam, K.Y., Okamoto, E., Xing, C., Eds.; Springer: Berlin/Heidelberg, Germany, 1999; pp. 165–179. [Google Scholar]
- Chaum, D.L. Untraceable Electronic Mail, Return Addresses, and Digital Pseudonyms. Commun. ACM 1981, 24, 84–90. [Google Scholar] [CrossRef]
- Song, Z.; Zhong, W.; Zhou, T.; Chen, D.; Ding, Y.; Yang, X. SEMDA: Secure and Efficient Multidimensional Data Aggregation in Smart Grid without a Trusted Third Party. Secur. Commun. Netw. 2023, 2023, 6693296. [Google Scholar] [CrossRef]
- Sousa-Dias, D.; Amyot, D.; Rahimi-Kian, A.; Bashari, M.; Mylopoulos, J. Cyclic Homomorphic Encryption Aggregation (CHEA)—A Novel Approach to Data Aggregation in the Smart Grid. Energies 2024, 17, 878. [Google Scholar] [CrossRef]
| Approach | Type of Study | User Anonymity | Discusses Social Outcomes | Privacy-Preserving | Homomorphic Encryption | Modular | Fraud Detection | Auction Clearing Procedure | Decentralized | Employs a Cryptosystem | Blockchain | Smart Contracts | EV Focus | Extends Other Schemes | Registration Procedure | Facilitates P2P Trading |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Sharma et al. [12] | P | y | n | y | n | n | n | n | y | y | y | y | y | n | y | n |
| Garg et al. [13] | S | y | n | n | n | y | n | n | n | y | y | n | y | n | y | y |
| Li et al. [14] | S | y | y | y | n | y | n | y | n | n | n | n | y | n | n | y |
| Li et al. [15] | S | y | n | y | y | y | n | y | n | y | n | n | y | n | n | n |
| Eisele et al. [10] | P | y | n | y | n | n | n | n | y | n | y | y | n | n | y | y |
| Baza et al. [16] | S | y | n | y | n | y | y | n | y | y | y | n | y | y | n | y |
| Baza et al. [17] | S | y | n | y | n | y | y | n | y | y | y | y | y | n | n | n |
| Bergquist et al. [18] | S | y | n | y | n | y | n | n | y | y | y | y | n | y | n | n |
| Laszka et al. [19] | S | y | n | y | n | y | n | n | y | n | y | n | n | y | n | y |
| Khorasany et al. [20] | P | y | n | y | n | y | y | n | y | y | y | y | n | n | n | y |
| Mollah et al. [21] | R | y | y | - | n | - | y | y | y | y | y | y | n | - | n | - |
| Ziu et al. [22] | P | n | y | n | n | n | n | y | y | n | y | y | n | n | n | y |
| Kang et al. [23] | P | n | n | n | n | n | n | n | y | n | y | y | n | n | n | y |
| Honari et al. [24] | R | n | y | - | n | - | y | y | n | n | y | y | y | - | y | - |
| ILPTS | S | y | y | y | y | y | y | n | y | y | y | y | n | y | y | n |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Sousa-Dias, D.; Amyot, D.; Rahimi-Kian, A.; Mylopoulos, J. Enhancing Trust in Transactive Energy with Individually Linkable Pseudonymous Trading Using Smart Contracts. Energies 2024, 17, 3568. https://doi.org/10.3390/en17143568
Sousa-Dias D, Amyot D, Rahimi-Kian A, Mylopoulos J. Enhancing Trust in Transactive Energy with Individually Linkable Pseudonymous Trading Using Smart Contracts. Energies. 2024; 17(14):3568. https://doi.org/10.3390/en17143568
Chicago/Turabian StyleSousa-Dias, Daniel, Daniel Amyot, Ashkan Rahimi-Kian, and John Mylopoulos. 2024. "Enhancing Trust in Transactive Energy with Individually Linkable Pseudonymous Trading Using Smart Contracts" Energies 17, no. 14: 3568. https://doi.org/10.3390/en17143568







