Secure Communication for Uplink Cellular Networks Assisted with Full-Duplex Device-to-Device User
Abstract
:1. Introduction
- (1)
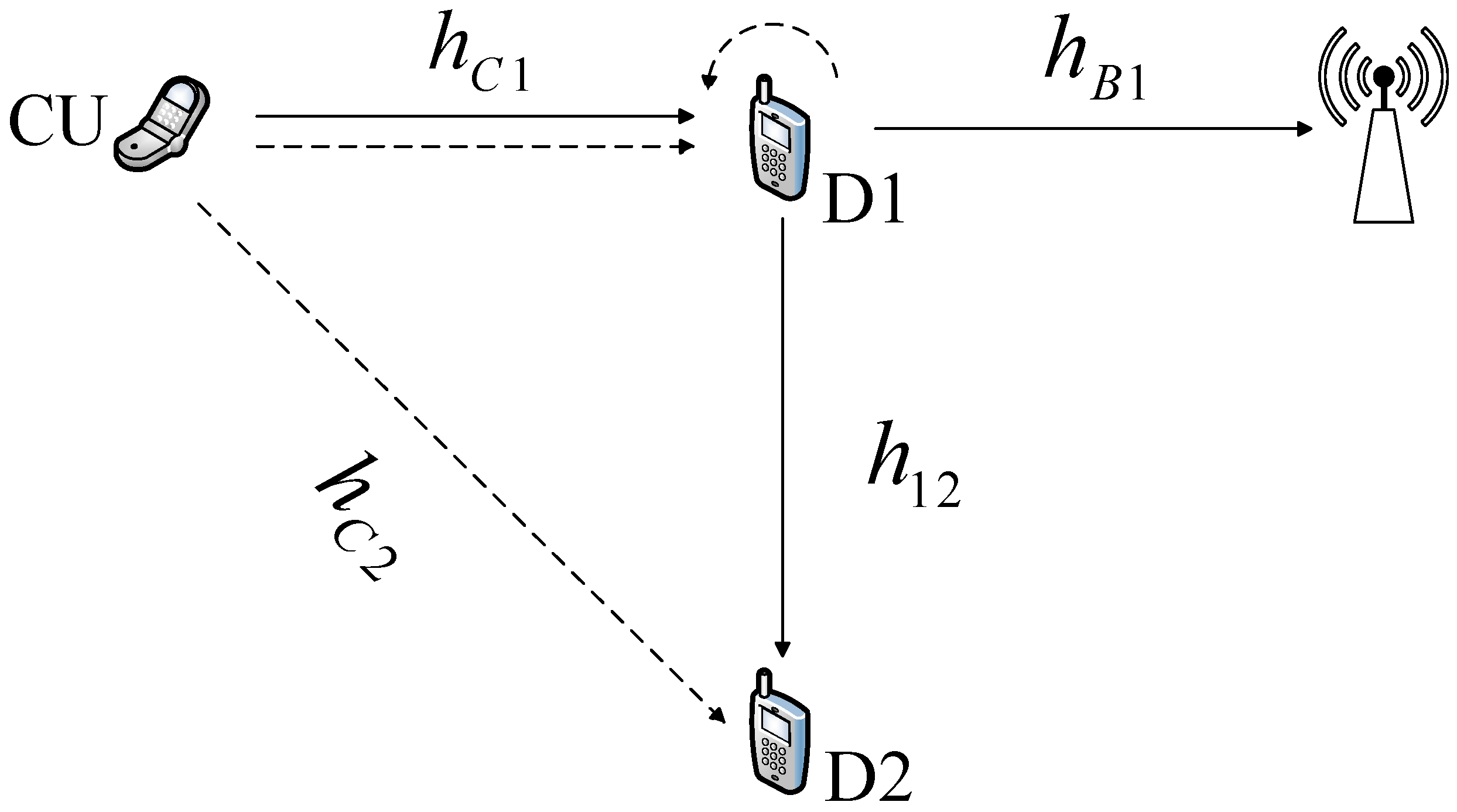
- A novel secure cooperative communication model is proposed to simultaneously solve the problems of long-distance cellular uplink transmission and reliability of auxiliary transmission. In the established system model, the D2D user can play the role of relay to assist in the information transmission from CU to BS. As the low spectrum efficiency of HD, the relay in this paper is operated in FD mode to shorten the transmission time slot, which is not involved in [9,10,11,12]. Unlike the existing works, we consider the reliability of D2D user-assisted transmission, which means that the relay is untrusted at the data level. Alternatively, the relay may decode confidential information from the received signal. In order to ensure secure communication between the CU and the BS, the CU transmits a signal that combines a confidential signal and an interference signal to reduce the signal to noise ratio (SNR) of the untrusted relay.
- (2)
- Based on physical layer security, the secrecy rate is defined as the rate difference between the legal link and wiretapping link. Therefore, we first derive the expression of the secrecy rate of the cellular uplink for the untrusted relay. If the secrecy rate is greater than a positive threshold, it indicates that the D2D user cannot successfully decode the confidential information. Considering the interference of the CU to the D2D user, the instantaneous rate expression of D2D is obtained. Subsequently, an optimization problem to maximize the D2D link rate is formulated.
- (3)
- For the optimization problem formulated, we jointly optimized the power allocation factors of the CU and the D2D user. Specifically, the optimal power allocation factor at the D2D user is obtained based on the monotonicity of the objective function. Then we prove that the power allocation factor at CU is optimal.
2. System Model
3. Problem Formulation and Analysis
4. Simulation Results and Analysis
5. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Matinmikko-Blue, M.; Yrjola, S.; Seppanen, V.; Ahokangas, P.; Hammainen, H.; Latva-Aho, M. Analysis of spectrum valuation approaches: The viewpoint of local 5G networks in shared spectrum bands. In Proceedings of the 2018 IEEE International Symposium on Dynamic Spectrum Access Networks (DySPAN), Seoul, Korea, 22–25 October 2018; pp. 1–9. [Google Scholar]
- Kour, H.; Jha, R.K. Power optimization using spectrum sharing for next generation cellular networks. In Proceedings of the 2019 11th International Conference on Communication Systems & Networks (COMSNETS), Bengaluru, India, 7–11 January 2019; pp. 562–564. [Google Scholar]
- Bhandari, S.; Bhandari, M.; Joshi, S. Spectrum sharing in cognitive radio networks for 5G Vision. In Proceedings of the 2019 Second International Conference on Advanced Computational and Communication Paradigms (ICACCP), Gangtok, India, 25–28 February2019; pp. 1–6. [Google Scholar]
- Yu, C.-H.; Doppler, K.; Ribeiro, C.B.; Tirkkonen, O. Resource sharing optimization for device-to-device communication underlaying cellular networks. IEEE Trans. Wirel. Commun. 2011, 10, 2752–2763. [Google Scholar] [CrossRef]
- Fodor, G.; Dahlman, E.; Mildh, G.; Parkvall, S.; Reider, N.; Miklós, G.; Turányi, Z. Design aspects of network assisted device-to-device communications. IEEE Commun. Mag. 2012, 50, 170–177. [Google Scholar] [CrossRef]
- Jung, Y.-A.; Song, H.-K.; You, Y.-H. Improved joint estimation of set information and frequency offset for LTE device-to-device communications. Appl. Sci. 2019, 10, 77. [Google Scholar] [CrossRef] [Green Version]
- Al-Gumaei, Y.A.; Aslam, N.; Al-Saman, A.M.; Al-Hadhrami, T.; Noordin, K.A.; Fazea, Y. Non-cooperative power control game in D2D underlying networks with variant system conditions. Electronics 2019, 8, 1113. [Google Scholar] [CrossRef] [Green Version]
- Cao, Y.; Jiang, T.; Wang, C. Cooperative device-to-device communications in cellular networks. IEEE Wirel. Commun. 2015, 22, 124–129. [Google Scholar] [CrossRef]
- Jiang, L.; Qin, C.; Zhang, X.; Tian, H. Secure beamforming design for SWIPT in cooperative D2D communications. China Commun. 2017, 14, 20–33. [Google Scholar] [CrossRef]
- Pei, Y.; Liang, Y.-C. Resource allocation for device-to-device communications overlaying two-way cellular networks. IEEE Trans. Wirel. Commun. 2013, 12, 3611–3621. [Google Scholar] [CrossRef]
- Shalmashi, S.; Ben Slimane, S. Cooperative device-to-device communications in the downlink of cellular networks. In Proceedings of the 2014 IEEE Wireless Communications and Networking Conference (WCNC), Istanbul, Turkey, 6–9 April 2014; pp. 2265–2270. [Google Scholar]
- Wu, Q.; Li, G.Y.; Chen, W.; Ng, D.W.K. Energy-efficient D2D overlaying communications with spectrum-power trading. IEEE Trans. Wirel. Commun. 2017, 16, 4404–4419. [Google Scholar] [CrossRef]
- Kim, J.-B.; Lee, I.-H.; Lee, J. Capacity scaling for D2D aided cooperative relaying systems using NOMA. IEEE Wirel. Commun. Lett. 2017, 7, 42–45. [Google Scholar] [CrossRef]
- Ali, K.S.; ElSawy, H.; Alouini, M.-S. Modeling cellular networks with full-duplex D2D communication: A stochastic geometry approach. IEEE Trans. Commun. 2016, 64, 4409–4424. [Google Scholar] [CrossRef] [Green Version]
- Vu, H.V.; Tran, N.H.; Le-Ngoc, T. Full-duplex device-to-device cellular networks: Power control and performance analysis. IEEE Trans. Veh. Technol. 2019, 68, 3952–3966. [Google Scholar] [CrossRef]
- Le, A.T.; Tran, L.C.; Huang, X.; Guo, Y.J. Beam-based analog self-interference cancellation in full-duplex MIMO systems. IEEE Trans. Wirel. Commun. 2020, 19, 2460–2471. [Google Scholar] [CrossRef] [Green Version]
- Sim, M.S.; Chung, M.; Kim, D.K.; Chae, C.-B. Low-complexity nonlinear self-interference cancellation for full-duplex radios. In Proceedings of the 2016 IEEE Globecom Workshops, Washington, DC, USA, 4–8 December 2016; pp. 1–6. [Google Scholar]
- Jha, U.S.; Harris, F. Spectral efficiency enhancements utilizing analog RF frontend in-band interference cancellation. In Proceedings of the 2017 20th International Symposium on Wireless Personal Multimedia Communications (WPMC), Bali, Indonesia, 17–20 December 2017; pp. 112–116. [Google Scholar]
- Wang, L.; Tian, F.; Svensson, T.; Feng, D.; Song, M.; Li, S. Exploiting full duplex for device-to-device communications in heterogeneous networks. IEEE Commun. Mag. 2015, 53, 146–152. [Google Scholar] [CrossRef]
- Del Puerto-Flores, J.A.; Cortez, J.; Gutierrez, C.A.; Del Valle-Soto, C.; Velazquez, R.; Valdivia, L.J. Performance of MRC detection in OFDM system with virtual carriers over V2V channels. In Proceedings of the 2019 IEEE 39th Central America and Panama Convention (CONCAPAN XXXIX), Guatemala City, Guatemala, 20–22 November 2019; pp. 1–6. [Google Scholar]
- Vij, S.; Jain, A. 5G: Evolution of a secure mobile technology. In Proceedings of the 2016 3rd International Conference on Computing for Sustainable Global Development, New Delhi, India, 16–18 March 2016; pp. 2192–2196. [Google Scholar]
- Fang, D.; Qian, Y.; Hu, R.Q. Security for 5G mobile wireless networks. IEEE Access 2017, 6, 4850–4874. [Google Scholar] [CrossRef]
- Wang, W.; Teh, K.C.; Li, K.H. Enhanced physical layer security in D2D spectrum sharing networks. IEEE Wirel. Commun. Lett. 2016, 6, 1. [Google Scholar] [CrossRef]
- Khoshafa, M.H.; Ngatched, T.M.N.; Ahmed, M.H.; Ibrahim, A. Improving physical layer security of cellular networks using full-duplex jamming relay-aided D2D communications. IEEE Access 2020, 8, 53575–53586. [Google Scholar] [CrossRef]
- Li, Q.; Ren, P.; Xu, D. Security enhancement and QoS provisioning for NOMA-based cooperative D2D networks. IEEE Access 2019, 7, 129387–129401. [Google Scholar] [CrossRef]
- Yang, Z.; Ding, Z.; Fan, P.; Karagiannidis, G.K. On the performance of non-orthogonal multiple access systems with partial channel information. IEEE Trans. Commun. 2015, 64, 654–667. [Google Scholar] [CrossRef]
- Hanif, M.F.; Ding, Z.; Ratnarajah, T.; Karagiannidis, G.K. A Minorization-maximization method for optimizing sum rate in the downlink of non-orthogonal multiple access systems. IEEE Trans. Signal Process. 2015, 64, 76–88. [Google Scholar] [CrossRef] [Green Version]







| Parameter | Value |
|---|---|
| Bandwidth | 5 Hz |
| Noise power | −70 dBm |
| Path loss exponent | 2 |
| The distance between CU and D1 | 200 m |
| The distance between CU and D2 | 200 m |
| The distance between D1 and D2 | 200 m |
| The distance between D1 and BS | 300 m |
| Power of CU | 1 W |
| Power of D1 | 1 W |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Song, X.; Xia, L.; Xu, S.; Wang, Y. Secure Communication for Uplink Cellular Networks Assisted with Full-Duplex Device-to-Device User. Future Internet 2020, 12, 175. https://doi.org/10.3390/fi12100175
Song X, Xia L, Xu S, Wang Y. Secure Communication for Uplink Cellular Networks Assisted with Full-Duplex Device-to-Device User. Future Internet. 2020; 12(10):175. https://doi.org/10.3390/fi12100175
Chicago/Turabian StyleSong, Xin, Lin Xia, Siyang Xu, and Yue Wang. 2020. "Secure Communication for Uplink Cellular Networks Assisted with Full-Duplex Device-to-Device User" Future Internet 12, no. 10: 175. https://doi.org/10.3390/fi12100175
APA StyleSong, X., Xia, L., Xu, S., & Wang, Y. (2020). Secure Communication for Uplink Cellular Networks Assisted with Full-Duplex Device-to-Device User. Future Internet, 12(10), 175. https://doi.org/10.3390/fi12100175




