Design of Relay Switching to Combat an Eavesdropper in IoT-NOMA Wireless Networks
Abstract
:1. Introduction
- (i)
- This study designed a green-and-cooperative IoT wireless network, where IoT relays and IoT devices are powered by solar and communicate using RF.
- (ii)
- To prolong IoT network lifetime, this study adopted SWIPT for EH at coupled relays by applying PS protocol. In particular, the study optimized OP performance of legitimate IoT devices by PS factor optimization in the first-half transmission block time period.
- (iii)
- In the second-half transmission block time period, the EH at the rest IoT relay intercepts the confidential information being exchanged between legitimate IoT devices. For clarity, the study proposed a selected IoT relay for forwarding signal to legitimate IoT devices using EH while another IoT relay for transmitting jamming signals to illegitimate device using EH as well. In this way, the study reached IP performance at an illegitimate device tending to one.
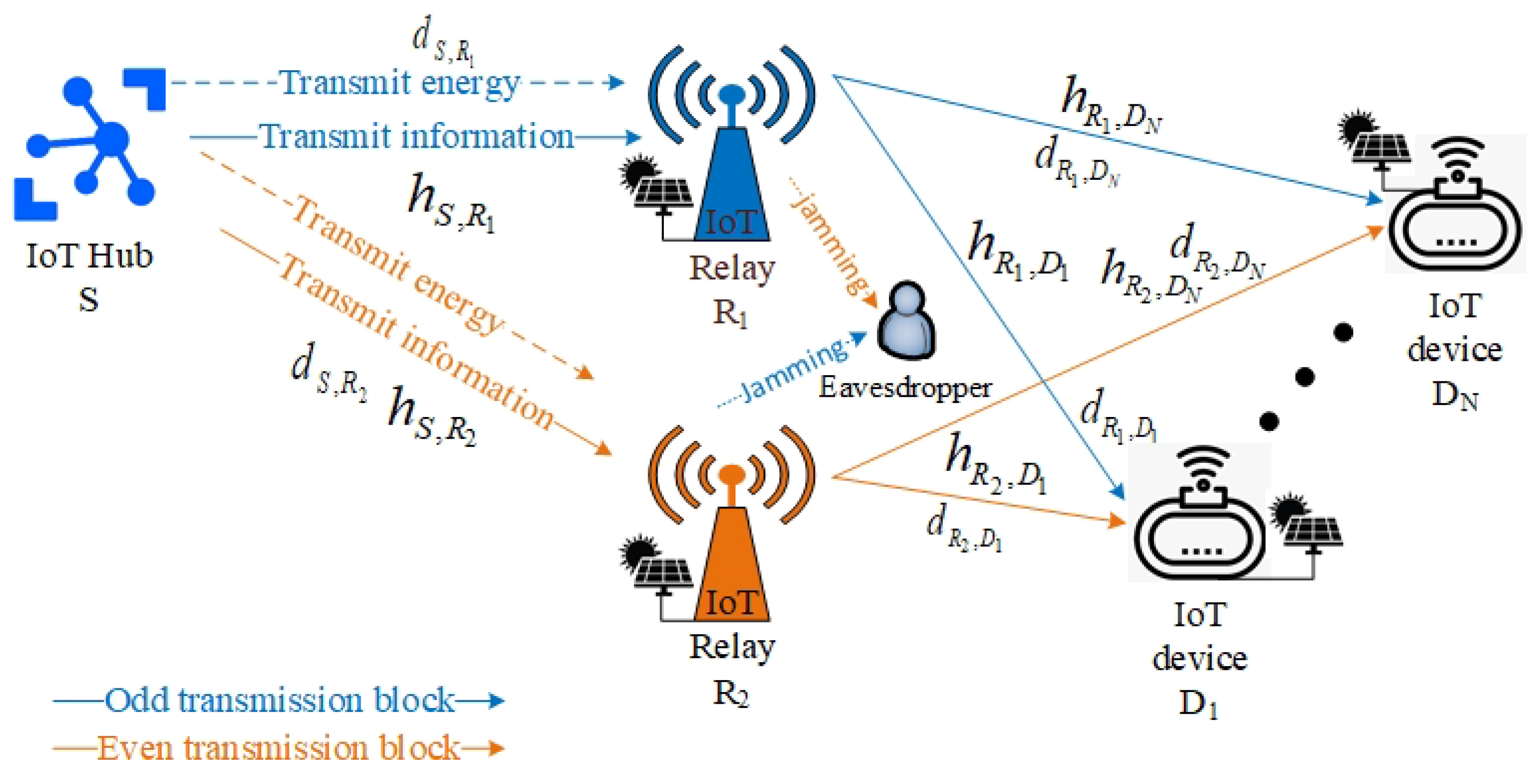
2. System Model and Formulation
2.1. Signal Transmission Block Time Period
| Algorithm 1 Algorithm for switching relay selection |
| Input: ; |
| ; |
| ; |
| ; |
| ; |
| Output: The selected relay forwarded legitimate signals while the other relay transmitted jamming signals. |
| 1: while true do |
| 2: if then |
| 3: Function_Information_Processing(); |
| 4: Function_Forwarding_Signal(); |
| 5: Function_Jamming_Signal(); |
| 6: ; |
| 7: else |
| 8: ; |
| 9: ; |
| 10: end if |
| 11: end while |
2.2. Relay Selection Strategy
- (i)
- If variable is non-zero, it means that an IoT relay has been selected. The selected IoT relay has to process legitimate information and then forward legitimate information after, while the non-selected IoT relay has to transmit a jamming signal. We counted down variable .
- (ii)
- If variable is zero, it means that the selected IoT relay finishing its obligation. Algorithm 1 swaps obligations between IoT relays and resets variable .
2.3. Formulations
3. System Performance Analysis
3.1. Outage Probability
| Algorithm 2 The algorithm for investigation OP at IoT relay for in transmission block |
| Input: Initialize the parameters as distances and ( and ), path-loss exponent factor , PA factors as (9), randomly generate samples for each fading channel over Rayleigh distribution; |
| Output: Simulation (Sim) results of OP at the relay (). |
| 1: Calculate SINR at IoT relay by applying (12)–(15); |
| 2: Calculate achievable bit-rate at IoT relay by applying (16) or (17); |
| 3: Find the minimum of achievable data rate by applying (18) or (19); |
| 4: Initialize variable ; |
| 5: for to samples do |
| 6: if then |
| 7: ; |
| 8: end if |
| 9: end for |
| 10: return OP at the IoT relay in transmission block as given . |
| Algorithm 3 Algorithm for investigation OP at IoT device in a transmission block |
| Input: Initialize the parameters as in Algorithm 2; |
| Output: Simulation (Sim) results of OP at the IoT device ; |
| 1: Calculate SINR at relay by applying (12) and (13) for or (14) and (15) for ; |
| 2: Calculate achievable bit-rate at relay as (16) for or (17) for ; |
| 3: Find the minimum of achievable data rate ; |
| 4: Calculate SINR at device applying (22) and (23) for or (24) and (25) for ; |
| 5: Calculate achievable bit-rate at device by applying (26) for or (27) for ; |
| 6: Find the minimum of achievable data rate ; |
| 7: Initialize variable ; |
| 8: for to samples do |
| 9: if then |
| 10: ; |
| 11: end if |
| 12: end for |
| 13: return OP at device in transmission block as given ; |
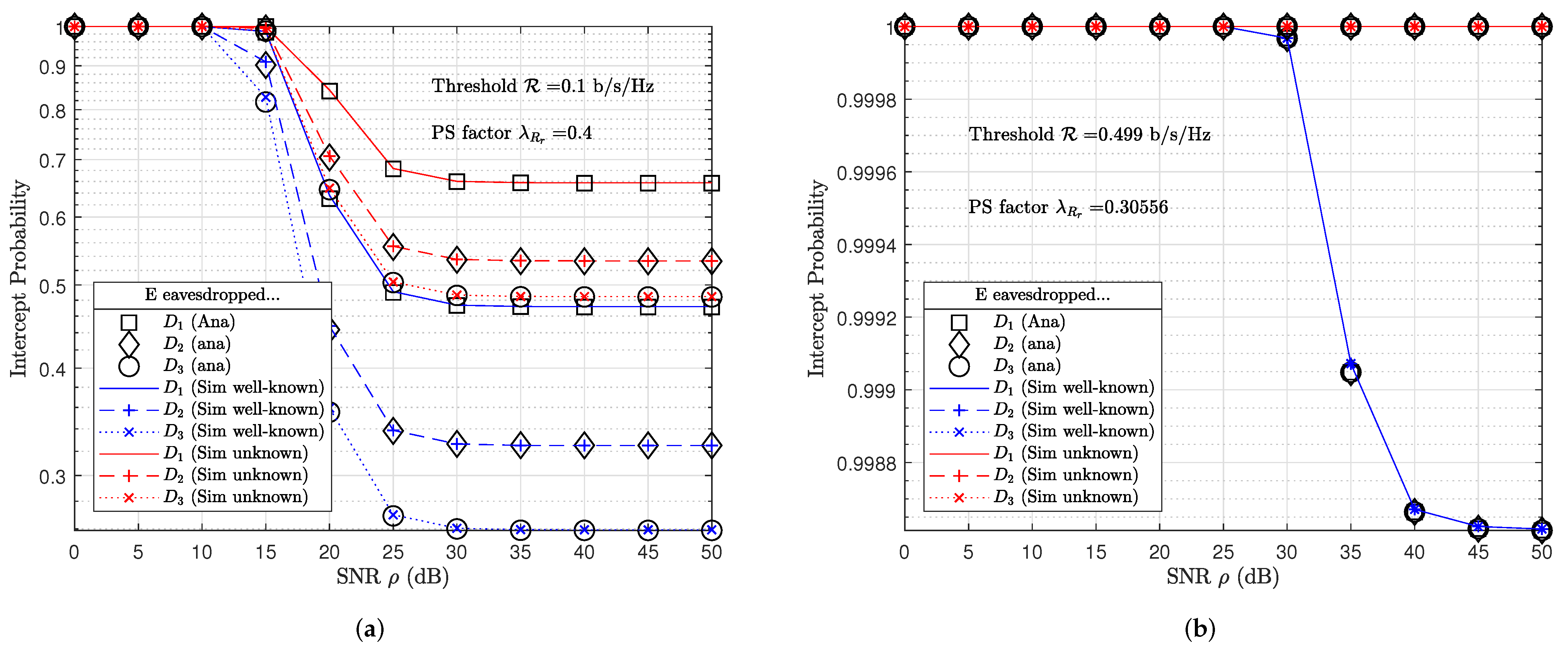
3.2. IP at Eavesdropper
3.3. System Throughput Maximization
3.4. PS Factor Optimization and IP Maximization
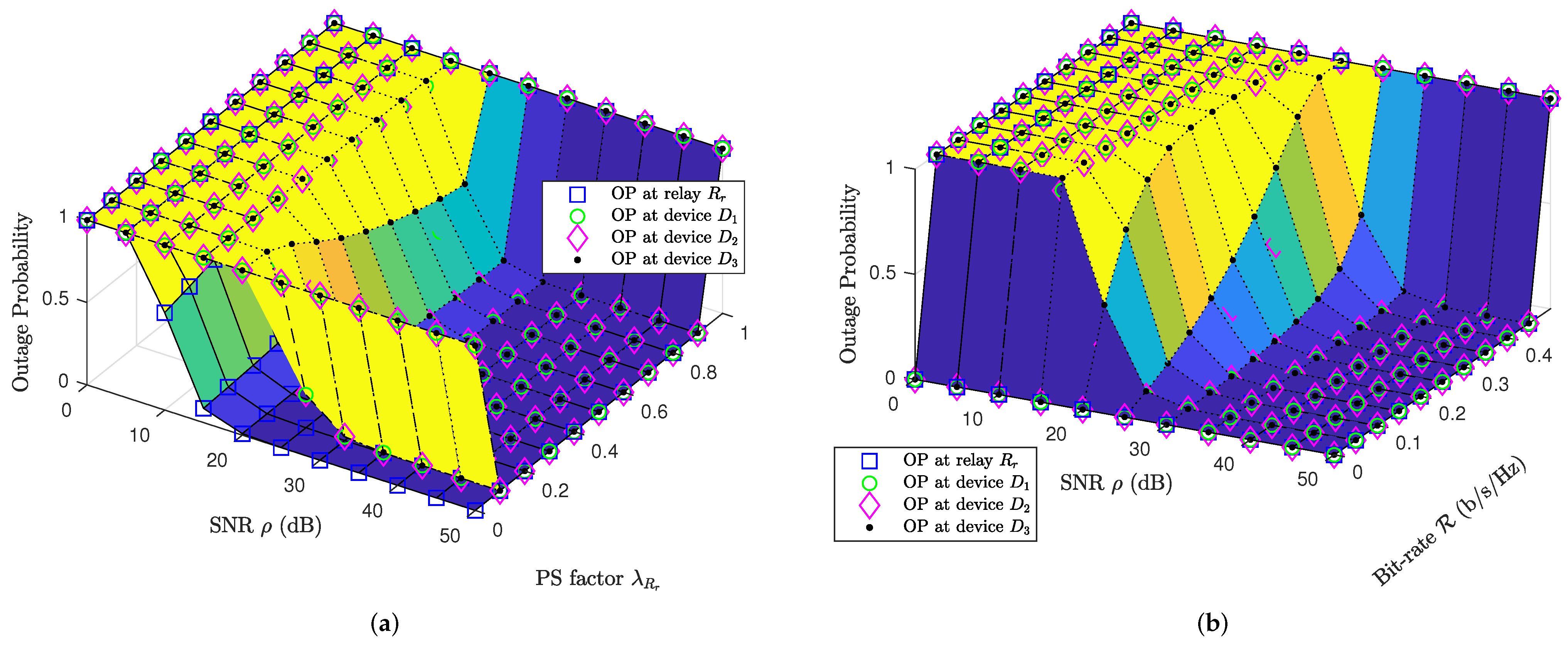
4. Numerical Results
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Appendix A. Proof of Theorem 1
Appendix B. Proof of Theorem 2
Appendix C. Proof of Theorem 3
References
- Qian, L.P.; Feng, A.; Huang, Y.; Wu, Y.; Ji, B.; Shi, Z. Optimal SIC ordering and computation resource allocation in MEC-aware NOMA NB-IoT networks. IEEE Internet Things J. 2018, 6, 2806–2816. [Google Scholar] [CrossRef]
- Qian, L.P.; Shi, B.; Wu, Y.; Sun, B.; Tsang, D.H. NOMA-enabled mobile edge computing for Internet of Things via joint communication and computation resource allocations. IEEE Internet Things J. 2019, 7, 718–733. [Google Scholar] [CrossRef]
- Jameel, F.; Khan, W.U.; Chang, Z.; Ristaniemi, T.; Liu, J. Secrecy analysis and learning-based optimization of cooperative NOMA SWIPT systems. In Proceedings of the 2019 IEEE International Conference on Communications Workshops (ICC Workshops), Shanghai, China, 20–24 May 2019; pp. 1–6. [Google Scholar]
- Liu, M.; Gui, G.; Zhao, N.; Sun, J.; Gacanin, H.; Sari, H. UAV-aided air-to-ground cooperative nonorthogonal multiple access. IEEE Internet Things J. 2019, 7, 2704–2715. [Google Scholar] [CrossRef]
- Khan, W.U.; Yu, Z.; Yu, S.; Sidhu, G.A.S.; Liu, J. Efficient power allocation in downlink multi-cell multi-user NOMA networks. IET Commun. 2019, 13, 396–402. [Google Scholar] [CrossRef]
- Khan, W.U.; Jameel, F.; Sidhu, G.A.S.; Ahmed, M.; Li, X.; Jäntti, R. Multiobjective optimization of uplink NOMA-enabled vehicle-to-infrastructure communication. IEEE Access 2020, 8, 84467–84478. [Google Scholar] [CrossRef]
- Laneman, J.; Wornell, G. Distributed space-time-coded protocols for exploiting cooperative diversity in wireless networks. IEEE Trans. Inf. Theory 2003, 49, 2415–2425. [Google Scholar] [CrossRef] [Green Version]
- Sadek, A.K.; Han, Z.; Ray Liu, K.J. A Distributed Relay-Assignment Algorithm for Cooperative Communications in Wireless Networks. In Proceedings of the 2006 IEEE International Conference on Communications, Istanbul, Turkey, 11–15 June 2006; Volume 4, pp. 1592–1597. [Google Scholar]
- Bletsas, A.; Khisti, A.; Reed, D.; Lippman, A. A simple Cooperative diversity method based on network path selection. IEEE J. Sel. Areas Commun. 2006, 24, 659–672. [Google Scholar] [CrossRef] [Green Version]
- Zhao, Y.; Adve, R.; Lim, T.J. Improving Amplify-and-Forward Relay Networks: Optimal Power Allocation versus Selection. In Proceedings of the 2006 IEEE International Symposium on Information Theory, Seattle, WA, USA, 9–14 July 2006; pp. 1234–1238. [Google Scholar] [CrossRef] [Green Version]
- Michalopoulos, D.S.; Karagiannidis, G.K.; Tsiftsis, T.A.; Mallik, R.K. WLC41-1: An Optimized User Selection Method for Cooperative Diversity Systems. In Proceedings of the IEEE Globecom2006, San Francisco, CA, USA, 27 November–1 December 2006; Volume 2006, pp. 1–6. [Google Scholar] [CrossRef]
- Madan, R.; Mehta, N.B.; Molisch, A.F.; Zhang, J. Energy-Efficient Cooperative Relaying over Fading Channels with Simple Relay Selection. IEEE Trans. Wirel. Commun. 2008, 7, 3013–3025. [Google Scholar] [CrossRef] [Green Version]
- Jing, Y.; Jafarkhani, H. Single and multiple relay selection schemes and their achievable diversity orders. IEEE Trans. Wirel. Commun. 2009, 8, 1414–1423. [Google Scholar] [CrossRef]
- Laneman, J.N.; Tse, D.N.; Wornell, G.W. Cooperative diversity in wireless networks: Efficient protocols and outage behavior. IEEE Trans. Inf. Theory 2004, 50, 3062–3080. [Google Scholar] [CrossRef]
- Tran, T.N.; Voznak, M. Switchable Coupled Relays Aid Massive Non-Orthogonal Multiple Access Networks with Transmit Antenna Selection and Energy Harvesting. Sensors 2021, 21, 1101. [Google Scholar] [CrossRef] [PubMed]
- Yang, Z.; Ding, Z.; Fan, P.; Al-Dhahir, N. The impact of power allocation on cooperative non-orthogonal multiple access networks with SWIPT. IEEE Trans. Wirel. Commun. 2017, 16, 4332–4343. [Google Scholar] [CrossRef] [Green Version]
- Tran, T.N.; Voznak, M.; Fazio, P.; Ho, V.C. Emerging cooperative MIMO-NOMA networks combining TAS and SWIPT protocols assisted by an AF-VG relaying protocol with instantaneous amplifying factor maximization. Aeu-Int. J. Electron. Commun. 2021, 135, 153695. [Google Scholar] [CrossRef]
- Tran, T.N.; Vo, T.P.; Fazio, P.; Voznak, M. SWIPT Model Adopting a PS Framework to Aid IoT Networks Inspired by the Emerging Cooperative NOMA Technique. IEEE Access 2021, 9, 61489–61512. [Google Scholar] [CrossRef]
- Jameel, F.; Wyne, S.; Ding, Z. Secure communications in three-step two-way energy harvesting DF relaying. IEEE Commun. Lett. 2017, 22, 308–311. [Google Scholar] [CrossRef]
- Cao, Y.; Zhao, N.; Pan, G.; Chen, Y.; Fan, L.; Jin, M.; Alouini, M.S. Secrecy Analysis for Cooperative NOMA Networks With Multi-Antenna Full-Duplex Relay. IEEE Trans. Commun. 2019, 67, 5574–5587. [Google Scholar] [CrossRef] [Green Version]
- Tran, T.N.; Voznak, M. On secure system performance over SISO, MISO and MIMO-NOMA wireless networks equipped a multiple antenna based on TAS protocol. Eurasip J. Wirel. Commun. Netw. 2020, 2020, 11. [Google Scholar] [CrossRef]
- Laneman, J.N.; Wornell, G.W. Energy-efficient antenna sharing and relaying for wireless networks. In Proceedings of the 2000 IEEE Wireless Communications and Networking Conference. Conference Record (Cat. No. 00TH8540), Chicago, IL, USA, 23–28 September 2000; Volume 1, pp. 7–12. [Google Scholar]
- Yang, H.C.; Alouini, M.S. MRC and GSC diversity combining with an output threshold. IEEE Trans. Veh. Technol. 2005, 54, 1081–1090. [Google Scholar] [CrossRef]
- Lioumpas, A.S.; Karagiannidis, G.K.; Tsiftsis, T.A. Adaptive generalized selection combining (A-GSC) receivers. IEEE Trans. Wirel. Commun. 2008, 7, 5214–5219. [Google Scholar] [CrossRef] [Green Version]
- Zhao, N.; Wang, W.; Wang, J.; Chen, Y.; Lin, Y.; Ding, Z.; Beaulieu, N.C. Joint Beamforming and Jamming Optimization for Secure Transmission in MISO-NOMA Networks. IEEE Trans. Commun. 2019, 67, 2294–2305. [Google Scholar] [CrossRef] [Green Version]
- Li, B.; Qi, X.; Huang, K.; Fei, Z.; Zhou, F.; Hu, R.Q. Security-reliability tradeoff analysis for cooperative NOMA in cognitive radio networks. IEEE Trans. Commun. 2018, 67, 83–96. [Google Scholar] [CrossRef]
- Zhou, F.; Chu, Z.; Sun, H.; Hu, R.Q.; Hanzo, L. Artificial noise aided secure cognitive beamforming for cooperative MISO-NOMA using SWIPT. IEEE J. Sel. Areas Commun. 2018, 36, 918–931. [Google Scholar] [CrossRef]
- Zhou, F.; Chu, Z.; Wu, Y.; Al-Dhahir, N.; Xiao, P. Enhancing PHY security of MISO NOMA SWIPT systems with a practical non-linear EH model. In Proceedings of the 2018 IEEE International Conference on Communications Workshops (ICC Workshops), Kansas City, MO, USA, 20–24 May 2018; pp. 1–6. [Google Scholar]
- Jameel, F.; Wyne, S.; Kaddoum, G.; Duong, T.Q. A comprehensive survey on cooperative relaying and jamming strategies for physical layer security. IEEE Commun. Surv. Tutor. 2018, 21, 2734–2771. [Google Scholar] [CrossRef] [Green Version]
- Vilela, J.P.; Bloch, M.; Barros, J.; McLaughlin, S.W. Wireless secrecy regions with friendly jamming. IEEE Trans. Inf. Forensics Secur. 2011, 6, 256–266. [Google Scholar] [CrossRef]
- Ding, X.; Song, T.; Zou, Y.; Chen, X. Security-reliability tradeoff for friendly jammer assisted user-pair selection in the face of multiple eavesdroppers. IEEE Access 2016, 4, 8386–8393. [Google Scholar] [CrossRef]
- Bayat, S.; Louie, R.H.; Han, Z.; Vucetic, B.; Li, Y. Physical-layer security in distributed wireless networks using matching theory. IEEE Trans. Inf. Forensics Secur. 2013, 8, 717–732. [Google Scholar] [CrossRef]
- Lv, L.; Zhou, F.; Chen, J.; Al-Dhahir, N. Secure Cooperative Communications With an Untrusted Relay: A NOMA-Inspired Jamming and Relaying Approach. IEEE Trans. Inf. Forensics Secur. 2019, 14, 3191–3205. [Google Scholar] [CrossRef]
- Perera, T.D.P.; Jayakody, D.N.K. Analysis of time-switching and power-splitting protocols in wireless-powered cooperative communication system. Phys. Commun. 2018, 31, 141–151. [Google Scholar] [CrossRef]
- Nguyen, N.P.; Duong, T.Q.; Ngo, H.Q.; Hadzi-Velkov, Z.; Shu, L. Secure 5G wireless communications: A joint relay selection and wireless power transfer approach. IEEE Access 2016, 4, 3349–3359. [Google Scholar] [CrossRef]
- Lu, X.; Wang, P.; Niyato, D.; Kim, D.I.; Han, Z. Wireless Networks With RF Energy Harvesting: A Contemporary Survey. IEEE Commun. Surv. Tutor. 2015, 17, 757–789. [Google Scholar] [CrossRef] [Green Version]
- Tran, T.N.; Voznak, M. Adaptive multiple access assists multiple users over multiple-input-multiple-output non-orthogonal multiple access wireless networks. Int. J. Commun. Syst. 2021, 10, e4803. [Google Scholar] [CrossRef]
- Men, J.; Ge, J.; Zhang, C. Performance analysis of nonorthogonal multiple access for relaying networks over Nakagami-m fading channels. IEEE Trans. Veh. Technol. 2016, 66, 1200–1208. [Google Scholar] [CrossRef]




| Studies | Number of Relays | RS | Number of Devices | SWIPT | Jamming Signal |
|---|---|---|---|---|---|
| [21] | 0 | no | 2 | no | no |
| [18] | 1 | no | 2 | yes | no |
| [25] | 0 | no | K | no | yes |
| [20] | 1 | no | 2 | no | yes |
| [33] | 1 | no | 1 | no | yes |
| [35] | K | yes | 1 | yes | no |
| This study | 2 | yes | N | yes | yes |
| Number of devices | |
| Distances | m, m, m, m, m |
| Path-loss exponent | |
| Channel gains | , , , , |
| Fixed bit-rate thresholds | b/s/Hz |
| Optimal bit-rate thresholds | b/s/Hz as given by (54) with tolerance factor for |
| Fixed PS factor | |
| PS factor | as given by (55) |
| PA factors | , , and as given by [21,37] |
| SNRs | dB |
| Status of jamming signal |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Tran, T.-N.; Ho, V.-C.; Vo, T.P.; Tran, K.N.N.; Voznak, M. Design of Relay Switching to Combat an Eavesdropper in IoT-NOMA Wireless Networks. Future Internet 2022, 14, 71. https://doi.org/10.3390/fi14030071
Tran T-N, Ho V-C, Vo TP, Tran KNN, Voznak M. Design of Relay Switching to Combat an Eavesdropper in IoT-NOMA Wireless Networks. Future Internet. 2022; 14(3):71. https://doi.org/10.3390/fi14030071
Chicago/Turabian StyleTran, Thanh-Nam, Van-Cuu Ho, Thoai Phu Vo, Khanh Ngo Nhu Tran, and Miroslav Voznak. 2022. "Design of Relay Switching to Combat an Eavesdropper in IoT-NOMA Wireless Networks" Future Internet 14, no. 3: 71. https://doi.org/10.3390/fi14030071







