Bot-Based Emergency Software Applications for Natural Disaster Situations
Abstract
:1. Introduction
1.1. Research Objectives
1.2. Contribution
1.3. Outline
2. Platform Design
3. Bot-Based Applications for Natural Disasters
3.1. Jayma Application
- 1.
- Send alerts: The administrator sends alert messages to the users included in the Jayma network.
- 2.
- Access to the main menu: Lists all the application options (Figure 4a).
- 3.
- Information: Provides information on meeting points or safe areas. These are safe geographic locations (latitude and longitude) and are activated by the administrator. Upon accessing the link, the bot delivers a Google Maps map with the last known location and the route to the closest meeting point (Figure 4b–d).
- 4.
- Report user status: The bot asks the user for the location. Once the bot receives the location, it asks the user if they are well. The bot notifies the user’s contacts of their status and location. In case the user is unwell, the bot asks what is the problem (panic/injured/infrastructure problems/needs supplies). See Figure 4e,f.
- 5.
- Contact management: Adds new contacts to the Jayma network. It also allows deleting a contact and listing current contacts. To include a person as a new contact, the app sends a message to that person with a link to the bot.
3.2. Rimay Application
- 1.
- Enrollment: Users request to register as volunteers. When the coordinator accepts the request, the data associated with the volunteer are stored in the system. In addition, the coordinator can assign the coordinator role to new users (Figure 5a,b).
- 2.
- Create event: The coordinator creates an event such as a forest fire. In addition, the coordinator can create tasks for each event, such as distributing face masks. Tasks have information such as where the face masks are stored and a job description. Volunteers can accept or decline assignments. Volunteers can also finish assignments when they are completed. The coordinator can also finish the event when it is complete. (Figure 6a).
- 3.
- Delete user: The coordinator can delete users from the system.
- 4.
- Send file: The coordinator can send a file to the volunteers.
- 5.
- Help/Status: Reports the status of volunteers.
- 6.
- Send report: Volunteers can send a report (attached file) to the coordinator. See Figure 6b.
3.3. Ayni Application
- 1.
- Create emergency: The coordinator creates a specific emergency and selects volunteers to participate in it.
- 2.
- View emergency details: Displays the specifications of an emergency.
- 3.
- Create Task: The coordinator creates tasks assigned to the emergency. In turn, it chooses volunteers who are asked if they want to participate in the assigned task.
- 4.
- Create volunteer: People register into the system.
- 5.
- Task details: Displays the task specifications.
- 6.
- Volunteer details: Displays the volunteers characteristics.
- 7.
- Volunteers agree to participate: A volunteer agrees to participate in an emergency.
- 8.
- Tasks per emergency: Displays the tasks for each emergency.
- 9.
- Active tasks for emergencies: Only active tasks assigned to emergencies are displayed.
- 10.
- Tasks completed by emergency: Only tasks completed by emergencies are displayed.
- 11.
- Volunteer accepts task: A volunteer accepts the task.
- 12.
- Volunteer completes task: A volunteer informs that the assigned task has been completed.
4. Experiments
4.1. Platform Configuration
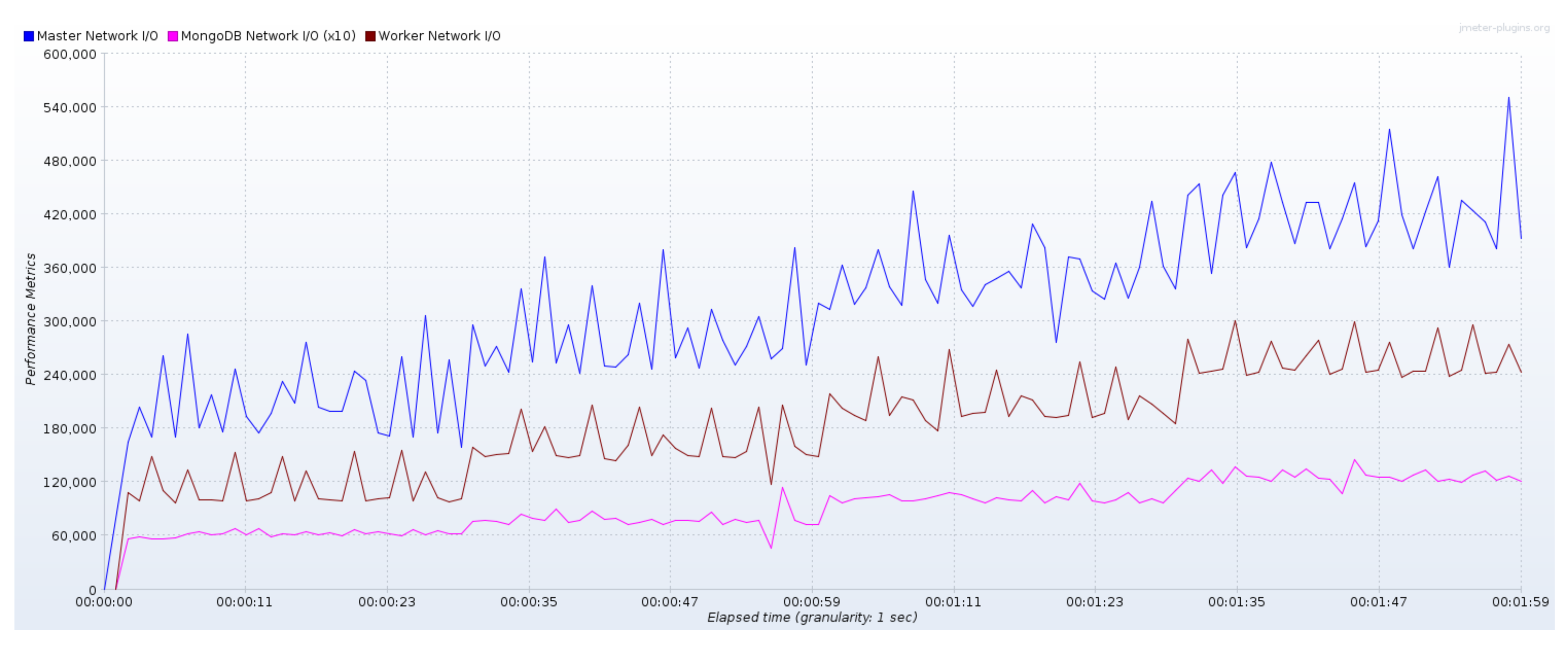
4.2. Bottlenecks and Performance Evaluation for Ayni
4.3. Bottlenecks and Performance Evaluation for Rimay
4.4. Bottlenecks and Performance Evaluation for Jayma
5. Related Work
6. Discussion
7. Conclusions and Future Work
Author Contributions
Funding
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Wang, C.; Du, W.; Chen, Z.; Chen, N.; Wang, W. An Event Modeling Software for Natural Disasters: Design and Implementation. In Proceedings of the International Conference on Geoinformatics, Kunming, China, 28–30 June 2018; pp. 1–4. [Google Scholar]
- Segura, A.; Olmedo, G.; Acosta, F.; Santillán, M. Designing a system for monitoring and broadcasting early warning signs of natural disasters for Digital Terrestrial Television. In Proceedings of the IEEE Latin-American Conference on Communications (LATINCOM), Arequipa, Peru, 4–6 November 2015; pp. 1–6. [Google Scholar]
- Mas Machuca, C.; Secci, S.; Vizarreta, P.; Kuipers, F.; Gouglidis, A.; Hutchison, D.; Jouet, S.; Pezaros, D.; Elmokashfi, A.; Heegaard, P.; et al. Technology-related disasters: A survey towards disaster-resilient Software Defined Networks. In Proceedings of the International Workshop on Resilient Networks Design and Modeling (RNDM), Halmstad, Sweden, 13–15 September 2016; pp. 35–42. [Google Scholar]
- Loor, F.; Manriquez, M.; Gil-Costa, V.; Marin, M. Feasibility of P2P-STB based crowdsourcing to speed-up photo classification for natural disasters. Cluster Comput. 2021, 25, 279–302. [Google Scholar] [CrossRef]
- Wu, X.; Mazurowski, M.; Chen, Z.; Meratnia, N. Emergency message dissemination system for smartphones during natural disasters. In Proceedings of the International Conference on ITS Telecommunications, St. Petersburg, Russia, 23–25 August 2011; pp. 258–263. [Google Scholar]
- Erdelj, M.; Natalizio, E. Drones, smartphones and sensors to face natural disasters. In Proceedings of the ACM Workshop on Micro Aerial Vehicle Networks, Systems, and Applications, Munich, Germany, 10–15 June 2018; pp. 75–86. [Google Scholar]
- Blank, G.; Lutz, C. Representativeness of Social Media in Great Britain: Investigating Facebook, LinkedIn, Twitter, Pinterest, Google+, and Instagram. Am. Behav. Sci. 2017, 61, 741–756. [Google Scholar] [CrossRef]
- Sutikno, T.; Handayani, L.; Stiawan, D.; Riyadi, M.A.; Subroto, I.M.I. WhatsApp, viber and telegram: Which is the best for instant messaging? Int. J. Electr. Comput. Eng. 2016, 6, 909. [Google Scholar]
- Kryvasheyeu, Y.; Chen, H.; Obradovich, N.; Moro, E.; Van Hentenryck, P.; Fowler, J.; Cebrian, M. Rapid assessment of disaster damage using social media activity. Sci. Adv. 2016, 2, e1500779. [Google Scholar] [CrossRef] [Green Version]
- Lu, Y.; Hu, X.; Wang, F.; Kumar, S.; Liu, H.; Maciejewski, R. Visualizing social media sentiment in disaster scenarios. In Proceedings of the International Conference on World Wide Web, Florence, Italy, 18–22 May 2015; pp. 1211–1215. [Google Scholar]
- Battineni, G.; Chintalapudi, N.; Amenta, F. AI Chatbot Design during an Epidemic like the Novel Coronavirus. Healthcare 2020, 8, 154. [Google Scholar] [CrossRef]
- Syed, H.A.; Schorch, M.; Pipek, V. Disaster Learning Aid: A Chatbot Centric Approach for Improved Organizational Disaster Resilience. In Information Systems for Crisis Response and Management Conference; Virginia Tech: Blacksburg, VA, USA, 2020; pp. 448–457. [Google Scholar]
- Tsai, M.H.; Chan, H.Y.; Chan, Y.L.; Shen, H.K.; Lin, P.Y.; Hsu, C.W. A Chatbot System to Support Mine Safety Procedures during Natural Disasters. Sustainability 2021, 13, 654. [Google Scholar] [CrossRef]
- Bradshaw, S.; Brazil, E.; Chodorow, K. Mongodb: The Definitive Guide: Powerful and Scalable Data Storage; O’Reilly Media: Sebastopol, CA, USA, 2019. [Google Scholar]
- Lakshman, A.; Malik, P. Cassandra: A decentralized structured storage system. Oper. Syst. Rev. 2010, 44, 35–40. [Google Scholar] [CrossRef]
- Osborne, G.; Weninger, T. Ozy: A General Orchestration Container. In Proceedings of the International Conference on Web Services (ICWS), San Francisco, CA, USA, 27 June–2 July 2016; pp. 609–616. [Google Scholar]
- Adufu, T.; Choi, J.; Kim, Y. Is container-based technology a winner for high performance scientific applications? In Proceedings of the Asia-Pacific Network Operations and Management Symposium (APNOMS), Busan, Korea, 19–21 August 2015; pp. 507–510. [Google Scholar]
- Burns, B.; Beda, J.; Hightower, K. Kubernetes: Up and Running: Dive into the Future of Infrastructure; O’Reilly Media: Sebastopol, CA, USA, 2019. [Google Scholar]
- Merkel, D. Docker: Lightweight Linux Containers for Consistent Development and Deployment. Linux 2014, 2014, 2. [Google Scholar]
- DeJonghe, D. Nginx CookBook; O’Reilly Media: Sebastopol, CA, USA, 2020. [Google Scholar]
- Erinle, B. Performance Testing with JMeter 2.9; Packt Ltd.: Birmingham, UK, 2013. [Google Scholar]
- Massei, M.; Poggi, S.; Agresta, M.; Ferrando, A. Development planning based on interoperable agent driven simulation. Comput. Sci. 2014, 5, 395–407. [Google Scholar] [CrossRef]
- Merkuryeva, G.; Merkuryev, Y.; Sokolov, B.V.; Potryasaev, S.; Zelentsov, V.A.; Lektauers, A. Advanced river flood monitoring, modelling and forecasting. Comput. Sci. 2015, 10, 77–85. [Google Scholar] [CrossRef]
- Barnes, B.; Dunn, S.; Pearson, C.; Wilkinson, S. Improving human behaviour in macroscale city evacuation agent-based simulation. Disaster Risk Reduct. 2021, 60, 102289. [Google Scholar] [CrossRef]
- Wang, Z.; Jia, G. A novel agent-based model for tsunami evacuation simulation and risk assessment. Nat. Hazards 2021, 105, 2045–2071. [Google Scholar] [CrossRef]
- Moe, T.L.; Pathranarakul, P. An integrated approach to natural disaster management. Disaster Prev. Manag. 2006, 15, 396–413. [Google Scholar]
- Banipal, K. Strategic approach to disaster management: Lessons learned from Hurricane Katrina. Disaster Prev. Manag. 2006, 15, 484–494. [Google Scholar] [CrossRef]
- Careem, M.; De Silva, C.; De Silva, R.; Raschid, L.; Weerawarana, S. Sahana: Overview of a Disaster Management System. In Proceedings of the 2006 International Conference on Information and Automation, Colombo, Sri Lanka, 15–17 December 2006; pp. 361–366. [Google Scholar]
- Bekhor, S.; Cohen, S.; Doytsher, Y.; Kanza, Y.; Sagiv, Y. A Personalized GeoSocial App for Surviving an Earthquake. In Proceedings of the ACM SIGSPATIAL International Workshop on the Use of GIS in Emergency Management, Bellevue, WC, USA, 3–6 November 2015; pp. 1–6. [Google Scholar]
- Betke, H. A Volunteer Coordination System Approach for Crisis Committees. In Proceedings of the International Conference on Information Systems for Crisis Response and Management, Rochester, NY, USA, 20–23 May 2018; pp. 786–795. [Google Scholar]
- Horstmann, A.C.; Winter, S.; Rösner, L.; Krämer, N.C. S.O.S. on my phone: An analysis of motives and incentives for participation in smartphone-based volunteering. Contingencies Crisis Manag. 2018, 26, 193–199. [Google Scholar] [CrossRef] [Green Version]
- Catarci, T.; de Rosa, F.; de Leoni, M.; Mecella, M.; Angelaccio, M.; Dustdar, S.; Gonzalvez, B.; Iiritano, G.; Krek, A.; Vetere, G.; et al. WORKPAD: 2-Layered Peer-to-Peer for Emergency Management through Adaptive Processes. In Proceedings of the Collaborative Computing: Networking, Applications and Worksharing, Atlanta, GA, USA, 17–20 November 2006; pp. 1–9. [Google Scholar]
- Freitas, D.P.; Borges, M.R.S.; de Carvalho, P.V.R. A conceptual framework for developing solutions that organise social media information for emergency response teams. Behav. Inf. Technol. 2020, 39, 360–378. [Google Scholar] [CrossRef]
- Qian, K.; Claudel, C. Real-time mobile sensor management framework for city-scale environmental monitoring. Comput. Sci. 2020, 45, 101205. [Google Scholar] [CrossRef]
- Alfeo, A.L.; Cimino, M.G.; De Francesco, N.; Lega, M.; Vaglini, G. Design and simulation of the emergent behavior of small drones swarming for distributed target localization. Comput. Sci. 2018, 29, 19–33. [Google Scholar] [CrossRef]
- Kerkez, B.; Glaser, S.D.; Bales, R.C.; Meadows, M.W. Design and performance of a wireless sensor network for catchment-scale snow and soil moisture measurements. Water Resour. Res. 2012, 48. [Google Scholar] [CrossRef]
- Weimer, J.E.; Sinopoli, B.; Krogh, B.H. A relaxation approach to dynamic sensor selection in large-scale wireless networks. In Proceedings of the International Conference on Distributed Computing Systems Workshops, Beijing, China, 17–20 June 2008; pp. 501–506. [Google Scholar]
- Krause, A.; Singh, A.; Guestrin, C. Near-optimal sensor placements in Gaussian processes: Theory, efficient algorithms and empirical studies. Mach. Learn. Res. 2008, 9, 235–284. [Google Scholar]
- Tokekar, P.; Branson, E.; Vander Hook, J.; Isler, V. Tracking aquatic invaders: Autonomous robots for monitoring invasive fish. IEEE Robot. Autom. Mag. 2013, 20, 33–41. [Google Scholar] [CrossRef]
- Tokekar, P.; Vander Hook, J.; Mulla, D.; Isler, V. Sensor planning for a symbiotic UAV and UGV system for precision agriculture. IEEE Trans. Robot. 2016, 32, 1498–1511. [Google Scholar] [CrossRef]
- Whitehead, K.; Hugenholtz, C.H. Remote sensing of the environment with small unmanned aircraft systems (UASs), part 1: A review of progress and challenges. Unmanned Veh. Syst. 2014, 2, 69–85. [Google Scholar] [CrossRef]
- Wu, B.; Fu, R.; Chen, J.; Zhu, J.; Gao, R. Research on Natural Disaster Early Warning System Based on UAV Technology. In IOP Conference Series: Earth and Environmental Science; IOP Publishing: Chengdu, China, 2021; Volume 787, pp. 1–8. [Google Scholar]
- Jones, B.; Jones, R. Public service chatbots: Automating conversation with BBC News. Digit. J. 2019, 7, 1032–1053. [Google Scholar] [CrossRef]
- Angelov, S.; Lazarova, M. E-Commerce Distributed Chatbot System. In Proceedings of the Balkan Conference on Informatics, Sofia, Bulgaria, 26–28 September 2019; pp. 1–8. [Google Scholar]
- Licapa-Rodriguez, R.; Gomez-Ramos, J.; Mauricio, D. EcoBot: Virtual assistant for e-commerce of ecological bricks based on Facebook Messenger. In Proceedings of the IEEE Engineering International Research Conference (EIRCON), Lima, Peru, 27–29 October 2021; pp. 1–4. [Google Scholar]
- Tran, A.D.; Pallant, J.I.; Johnson, L.W. Exploring the impact of chatbots on consumer sentiment and expectations in retail. Retail. Consum. Serv. 2021, 63, 102718. [Google Scholar] [CrossRef]
- Fadhlallah, G.M. A Deep Learning-Based Approach for Chatbot: Medical Assistance a Case Study. Master’s Thesis, Facultédes Lettres et des Langues FLL, Biskra, Argelia, 2021. [Google Scholar]
- Dharmapuri Sridhar, M.P. Real-Time Flood Mapping for Disaster Management Decision Support in Chennai. Master’s Thesis, System Design and Management Program, MIT, Cambridge, MA, USA, 2017. [Google Scholar]
- Tsai, M.H.; Yang, C.H.; Chen, J.Y.; Kang, S.C. Four-Stage Framework for Implementing a Chatbot System in Disaster Emergency Operation Data Management: A Flood Disaster Management Case Study. KSCE Civ. Eng. 2021, 25, 503–515. [Google Scholar] [CrossRef]
- Rotondi, L.; Zuddas, M.; Marsella, P.; Rosati, P. A Facebook Page Created Soon After the Amatrice Earthquake for Deaf Adults and Children, Families, and Caregivers Provides an Easy Communication Tool and Social Satisfaction in Maxi-Emergencies. Prehosp. Disaster Med. 2019, 34, 137–141. [Google Scholar] [CrossRef]
- Ahmady, S.E.; Uchida, O. Telegram-Based Chatbot Application for Foreign People in Japan to Share Disaster-Related Information in Real-Time. In Proceedings of the Conference on Computer and Communication Systems (ICCCS), Shanghai, China, 15–18 May 2020; pp. 177–181. [Google Scholar]


















| Task | #Requests (Single) | #Requests (Distributed) |
|---|---|---|
| 01 Create Emergency | 100 | 180 |
| 02 Create Task | 200 | 360 |
| 03 Create Volunteer | 60 | 100 |
| 04 View Emergency Details | 400 | 770 |
| 05 Task Details | 400 | 760 |
| 06 Volunteer Details | 60 | 100 |
| 07 Volunteers Agree to Participate | 400 | 750 |
| 08 Tasks per Emergency | 400 | 750 |
| 09 Active Tasks for Emergencies | 400 | 750 |
| 10 Tasks Completed by Emergency | 200 | 380 |
| 11 Volunteer Accepts Tasks | 400 | 770 |
| 12 Volunteer Completes Tasks | 200 | 380 |
| Task | Avg. Time (ms.) | # Tasks per s. | Exec. Time (s.) |
|---|---|---|---|
| Enrollment | 88.93 | 2.72 | 132.28 |
| 2.94 | 204.33 | ||
| 3.03 | 276.49 | ||
| 3.09 | 348.68 | ||
| Create event | 7.38 | 1.89 | 94.99 |
| 2.1 | 143.2 | ||
| 2.2 | 191.24 | ||
| 2.25 | 239.28 | ||
| Send report | 112.03 | 3.85 | 109.03 |
| 4.23 | 165.29 | ||
| 4.42 | 221.4 | ||
| 4.52 | 278.4 | ||
| Help/Status | 7.32 | 1.63 | 36.9 |
| 2.22 | 45.05 | ||
| 2.64 | 53.07 | ||
| 2.95 | 61.09 |
| Task | #Requests (Single) | #Requests (Distributed) |
|---|---|---|
| Send alert | <1200 | <1680 |
| Access to the main menu | >1500 | >1500 |
| Information | >1500 | >1500 |
| Report user status | >1500 | >1500 |
| Contact management | <120 | <1100 |
| App/Ref. | Perf. | Usab. | Scal. | Fault Tol. | Validation | Type | Deployment |
|---|---|---|---|---|---|---|---|
| Rimay | Yes | − | Yes | Yes | (A), (C) | (2) | Parall./Distrib. |
| Ayni | Yes | − | Yes | Yes | (A), (C) | (2) | Parall./Distrib. |
| Jayma | Yes | − | Yes | Yes | (A), (C) | (2) | Parall./Distrib. |
| [13] | − | − | − | Yes | (A) | (2) | Distrib. |
| [22,23,24] | − | − | − | − | (B), (C) | (2) | Sequential |
| [25] | − | − | − | − | (B), (D) | (2) | Sequential |
| [27] | − | − | − | Yes | − | (3) | Distrib. |
| [28] | − | − | − | − | (C) | (2) | Sequential |
| [29] | − | − | − | − | − | (3) | Not Specified |
| [30] | Yes | Yes | − | − | (B) | (2) | Not Specified |
| [31] | − | − | − | − | − | (3) | Sequential |
| [32] | − | − | − | − | − | (2) | Distrib. |
| [33] | − | − | − | − | (B) | (1), (2) | Not Specified |
| [48] | − | − | Yes | Yes | − | (2) | Sequential |
| [49] | − | Yes | − | − | (C) | (1), (2) | Sequential |
| [50] | − | Yes | − | − | (C) | (2) | Sequential |
| [51] | − | − | − | − | − | (2) | Sequential |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ovando-Leon, G.; Veas-Castillo, L.; Gil-Costa, V.; Marin, M. Bot-Based Emergency Software Applications for Natural Disaster Situations. Future Internet 2022, 14, 81. https://doi.org/10.3390/fi14030081
Ovando-Leon G, Veas-Castillo L, Gil-Costa V, Marin M. Bot-Based Emergency Software Applications for Natural Disaster Situations. Future Internet. 2022; 14(3):81. https://doi.org/10.3390/fi14030081
Chicago/Turabian StyleOvando-Leon, Gabriel, Luis Veas-Castillo, Veronica Gil-Costa, and Mauricio Marin. 2022. "Bot-Based Emergency Software Applications for Natural Disaster Situations" Future Internet 14, no. 3: 81. https://doi.org/10.3390/fi14030081
APA StyleOvando-Leon, G., Veas-Castillo, L., Gil-Costa, V., & Marin, M. (2022). Bot-Based Emergency Software Applications for Natural Disaster Situations. Future Internet, 14(3), 81. https://doi.org/10.3390/fi14030081






