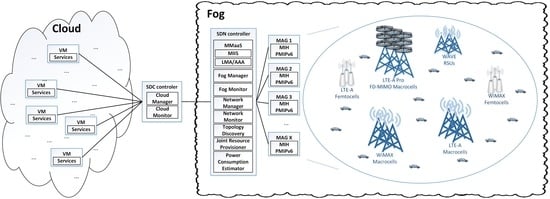
Handover Management in 5G Vehicular Networks
Abstract
:1. Introduction
- The HO management services, namely the velocity and alternative network monitoring, the HO initiation, the network selection, and the HO execution are performed at the Fog and the Cloud infrastructures to reduce the workload at the vehicle;
- Both predictive and reactive HOs modes are supported for the mobility transfer;
- The vehicle’s velocity is considered in order for unnecessary HOs to short-range cells (such as Femtocells) to be avoided, since a vehicle that moves with high velocity will remain for a short time period inside their coverage area;
- HO initiation is performed by taking into consideration the user satisfaction, which is estimated using both the Signal-to-Noise-plus-Interference (SINR) and the perceived Quality of Service (QoS) parameters, due to the fact that users that perceive a good SINR may not be satisfied by the QoS that they also perceive from their current networks;
- Network selection takes into consideration contradictory criteria for different application types and users’ SLAs to satisfy the requirements of demanding services;
- The HO scheme applies an improved version of the MIH framework and the FPMIPv6 protocol.
2. Related Work
3. Preliminaries
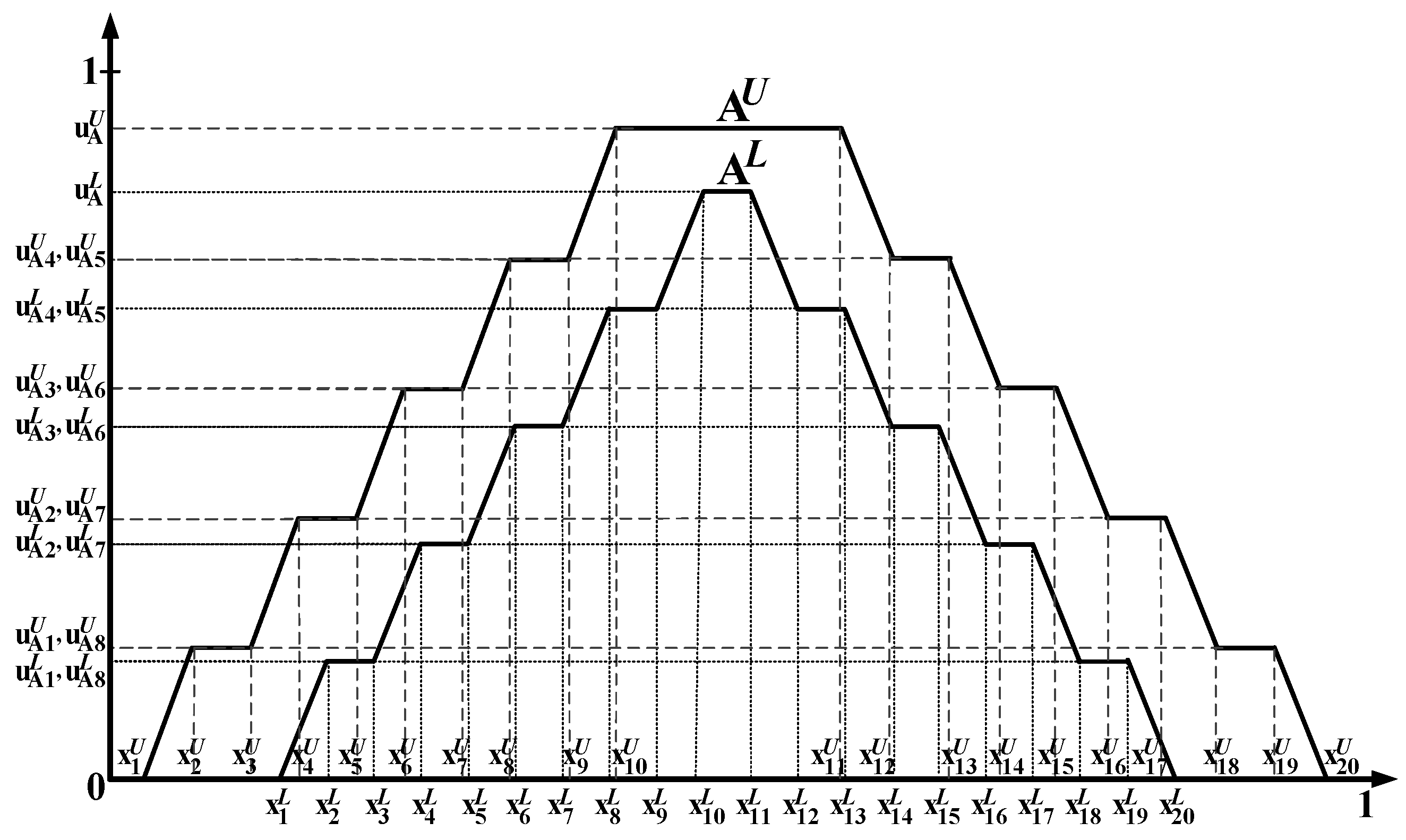
3.1. The Interval-Valued Icosagonal Fuzzy Numbers
3.2. The Equalized Universe Method
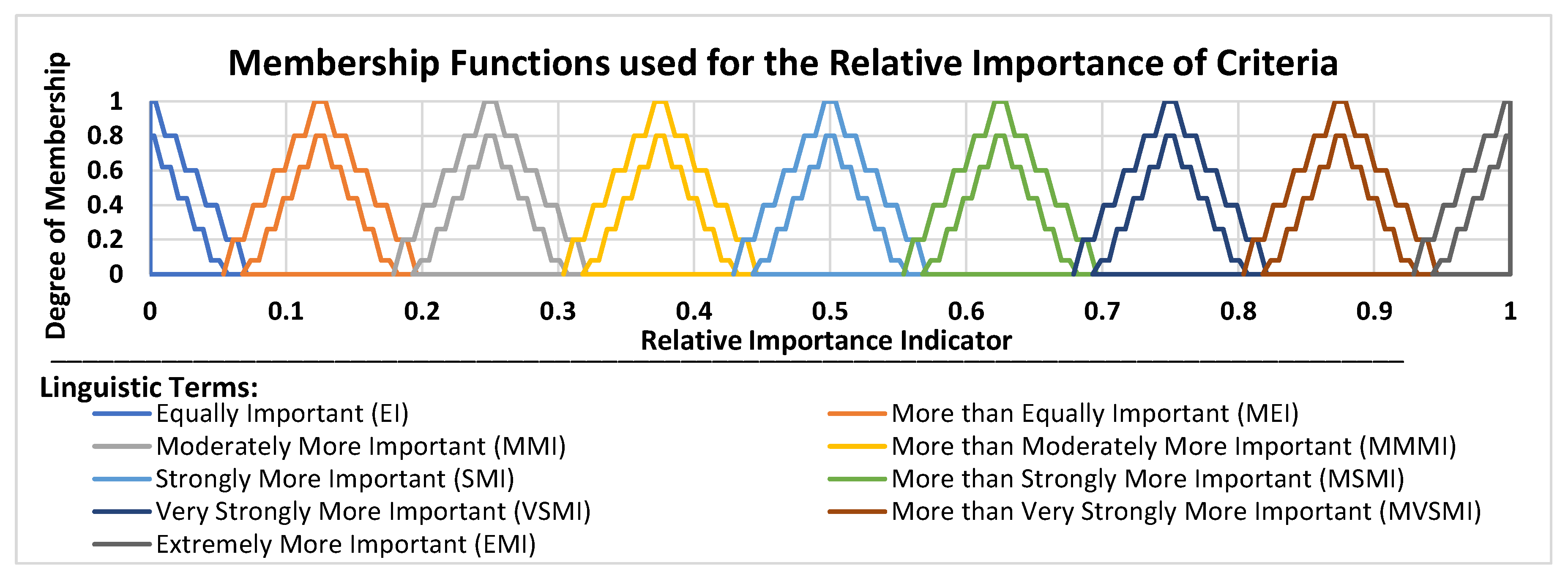
3.3. The Icosagonal Fuzzy Analytic Network Process
3.4. The Mamdani Icosagonal Fuzzy Inference System
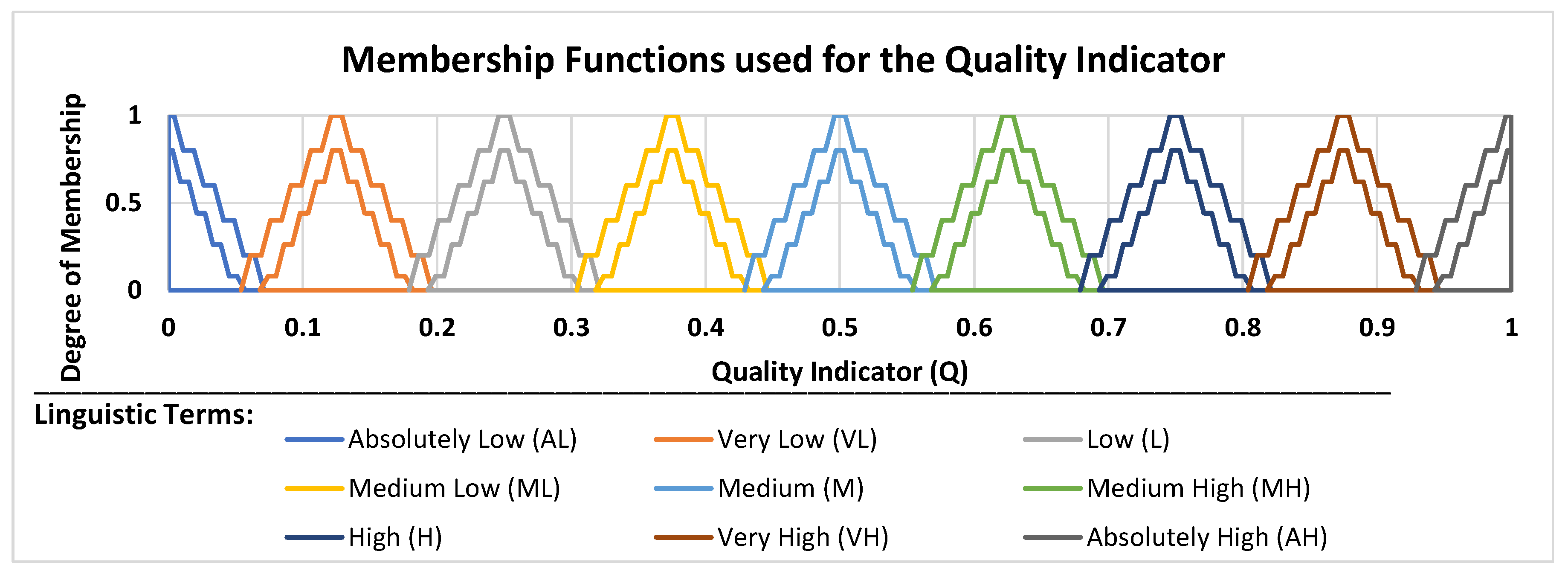
3.5. The Dynamic Icosagonal Fuzzy TOPSIS with Adaptive Criteria Weights
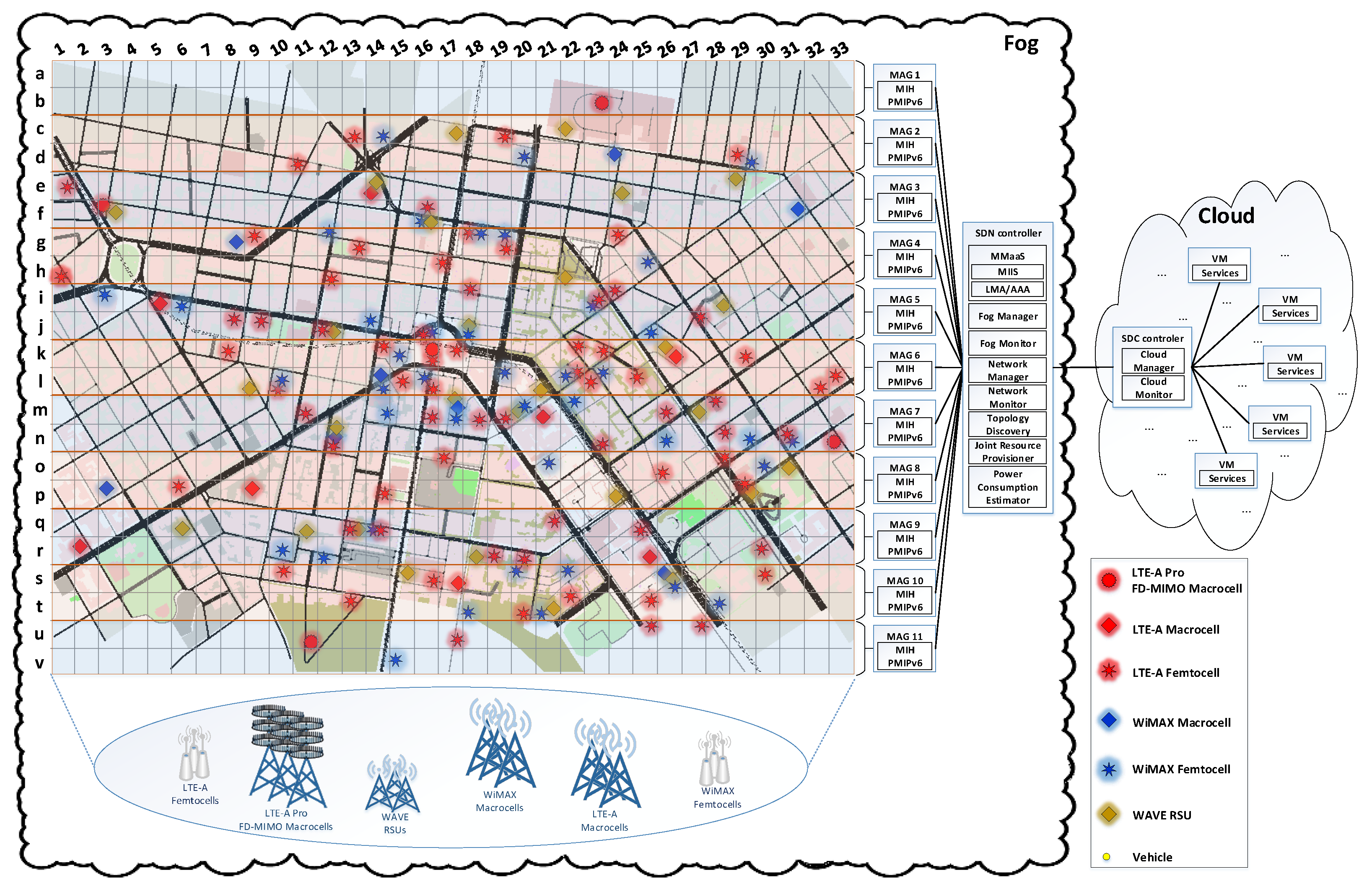
4. The Proposed Mobility Management Scheme
4.1. Velocity and Alternative Network Monitoring
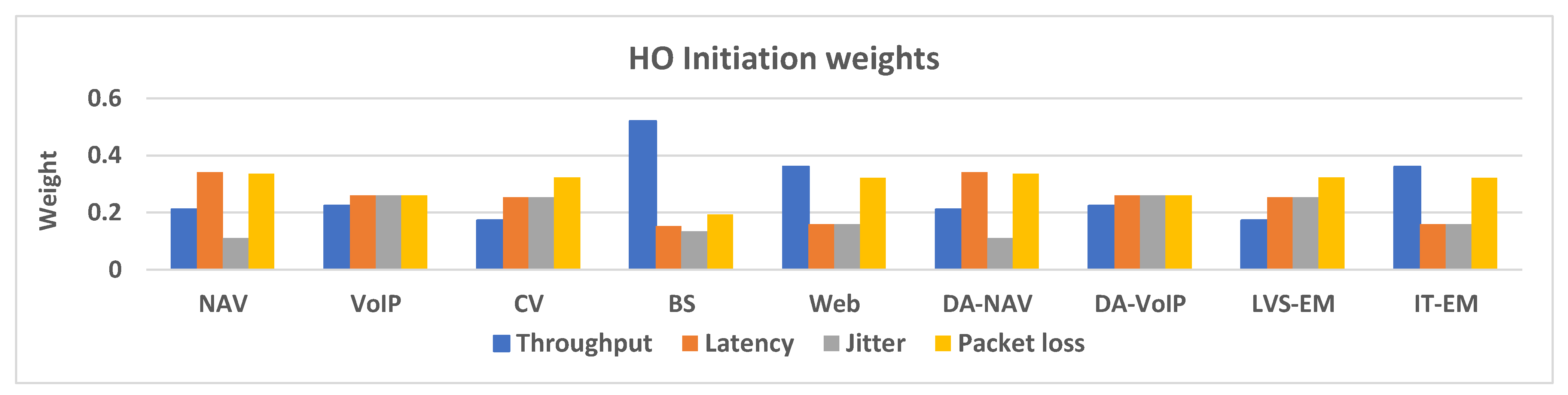
4.2. HO Initiation
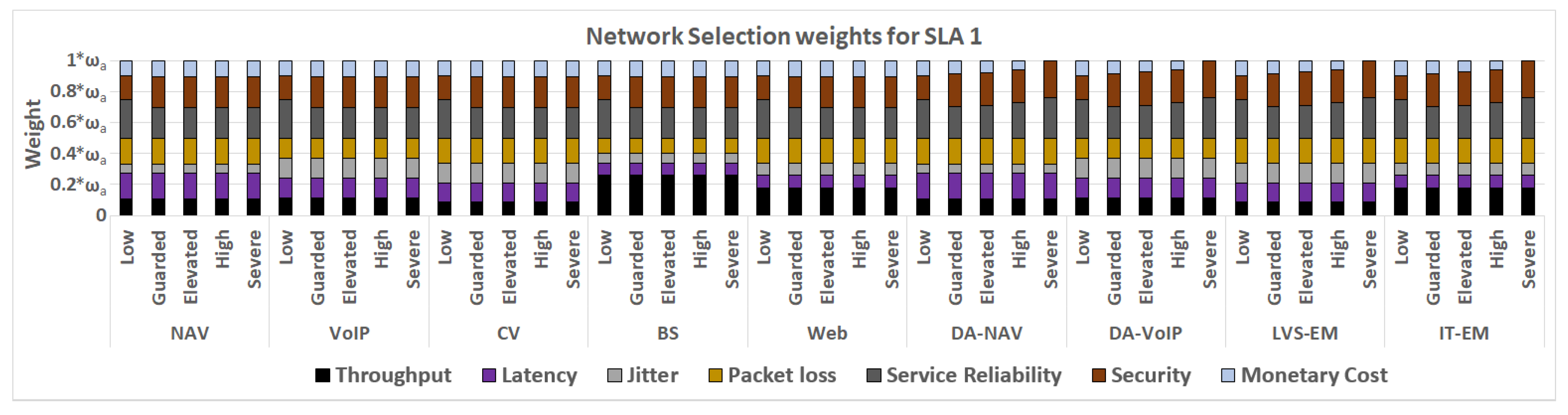
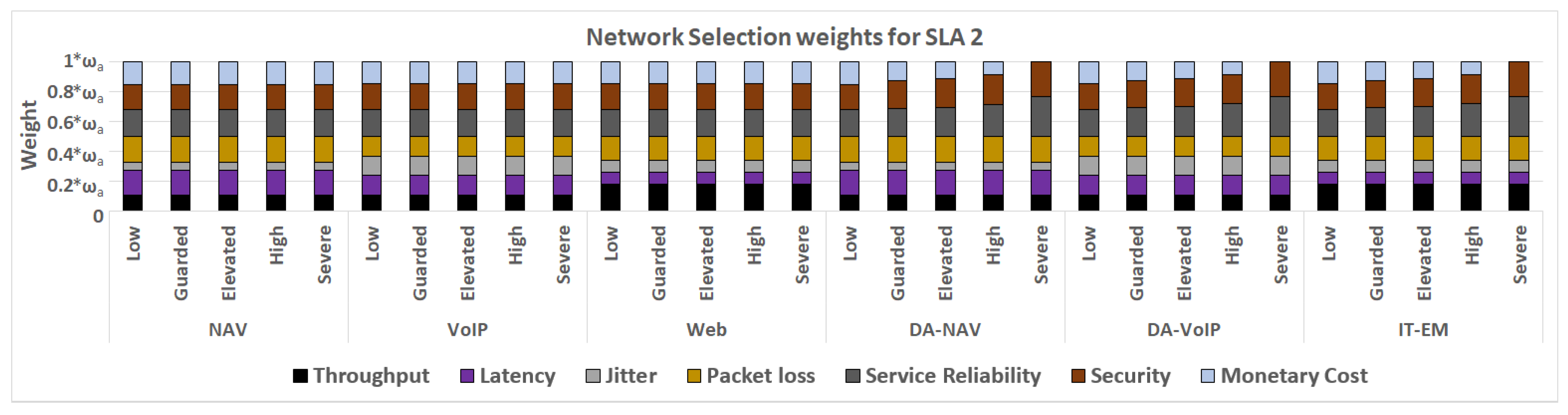
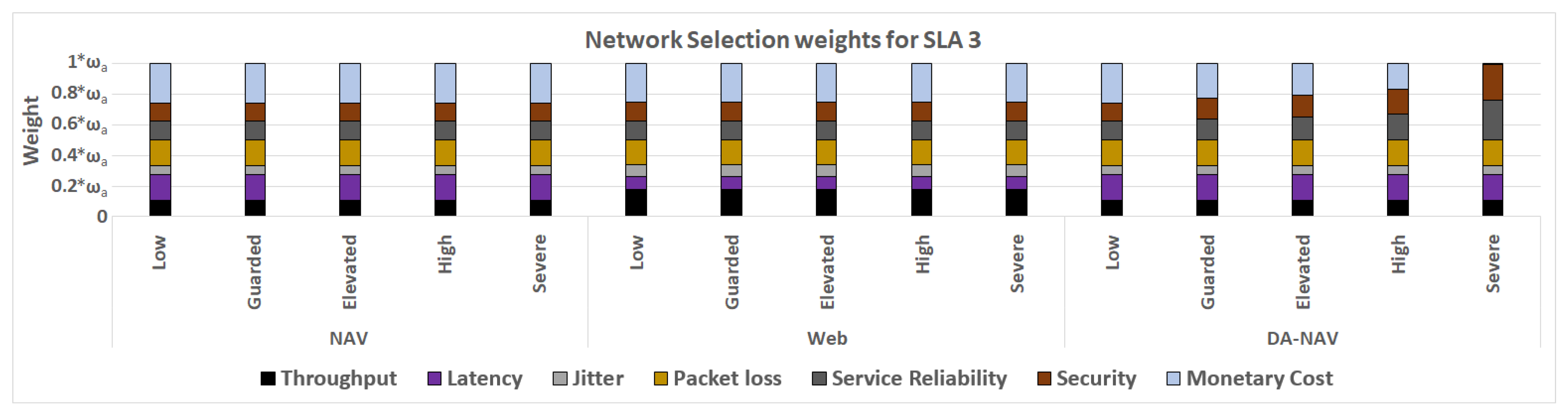
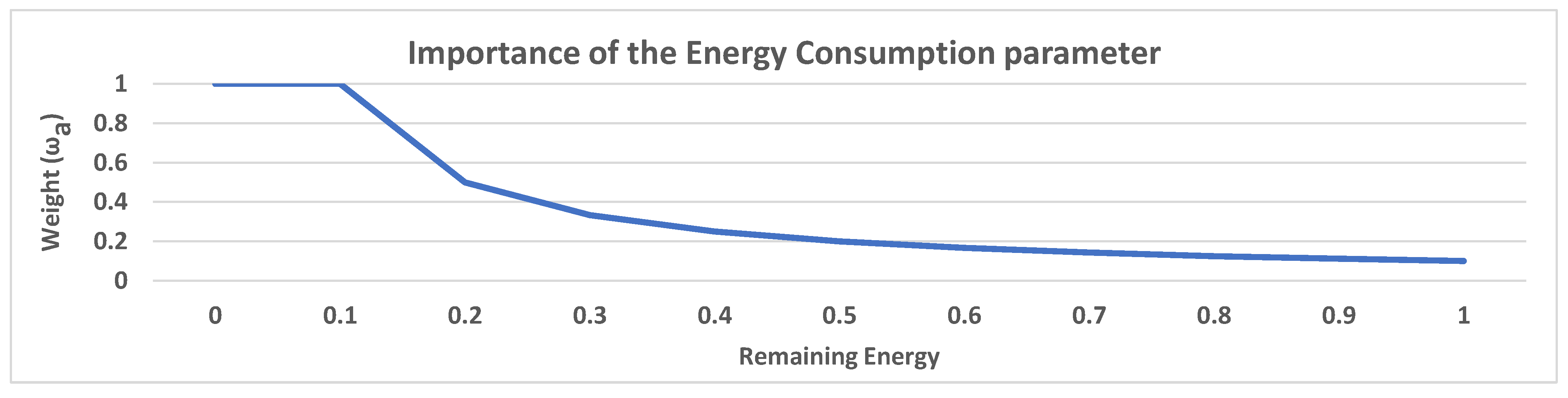
4.3. Network Selection
4.4. HO Execution
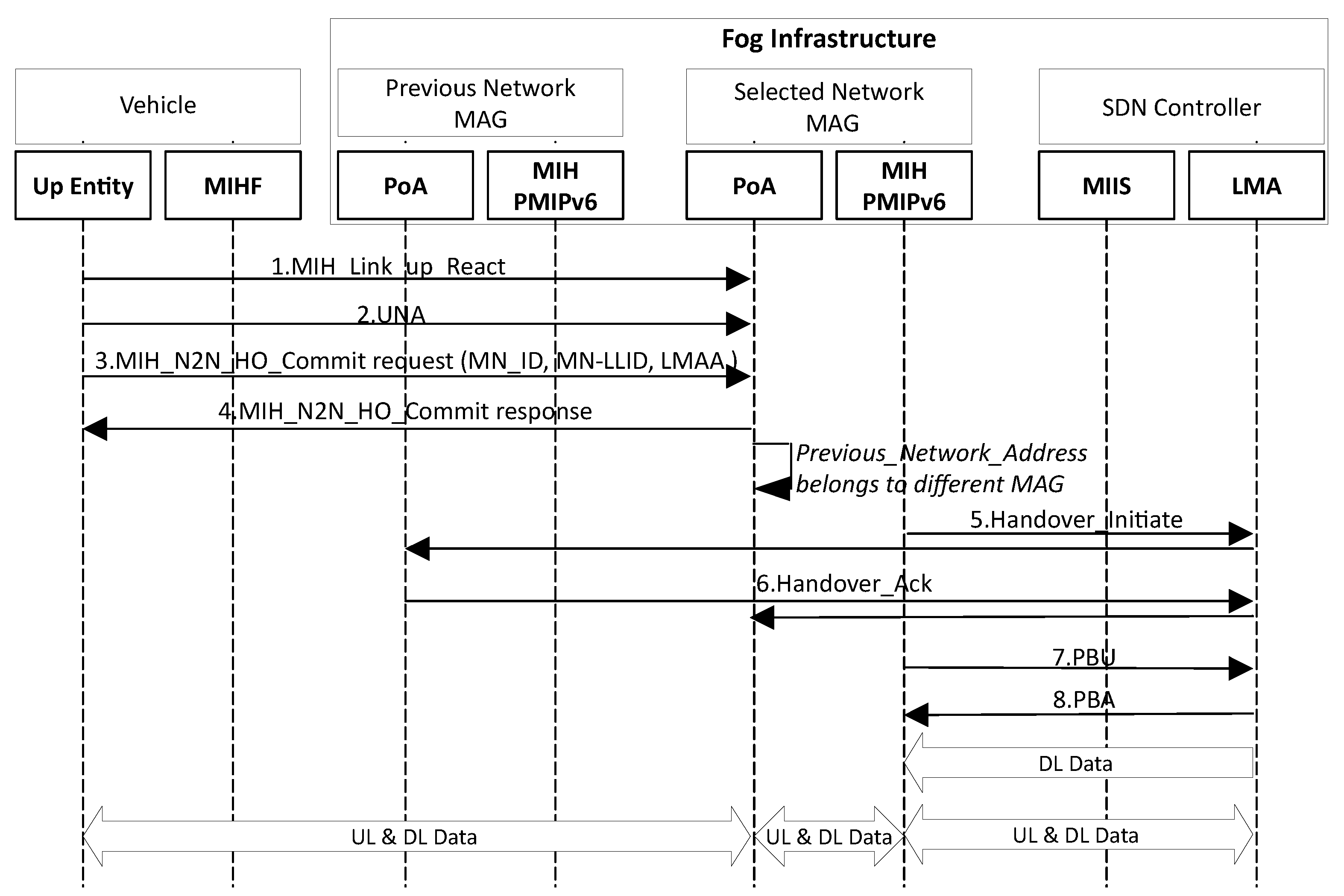
4.4.1. Proposed Predictive HO Scheme
4.4.2. Proposed Reactive HO Scheme
4.5. The Computational Complexity of the Proposed Scheme
5. Simulation Setup and Results
5.1. Study of a Simulation Snapshot
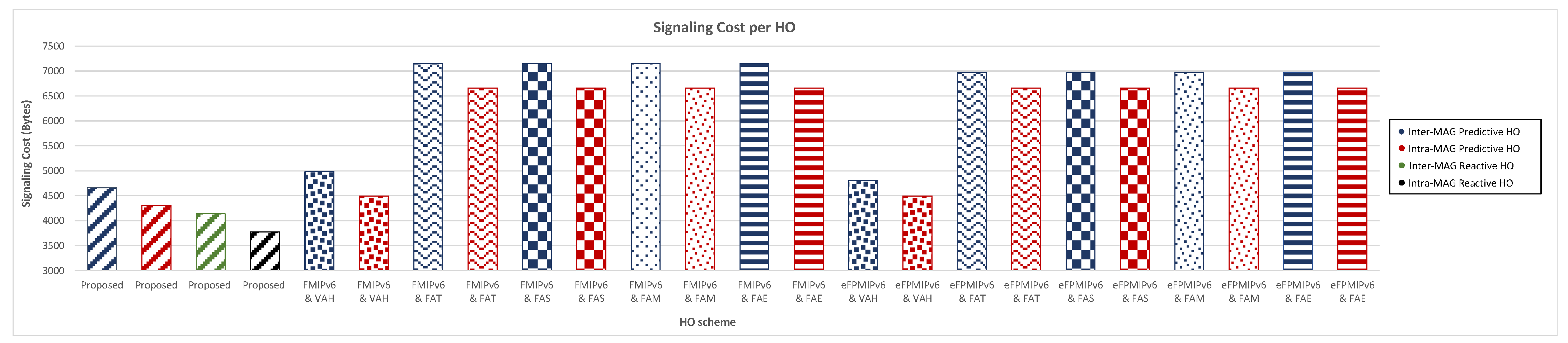
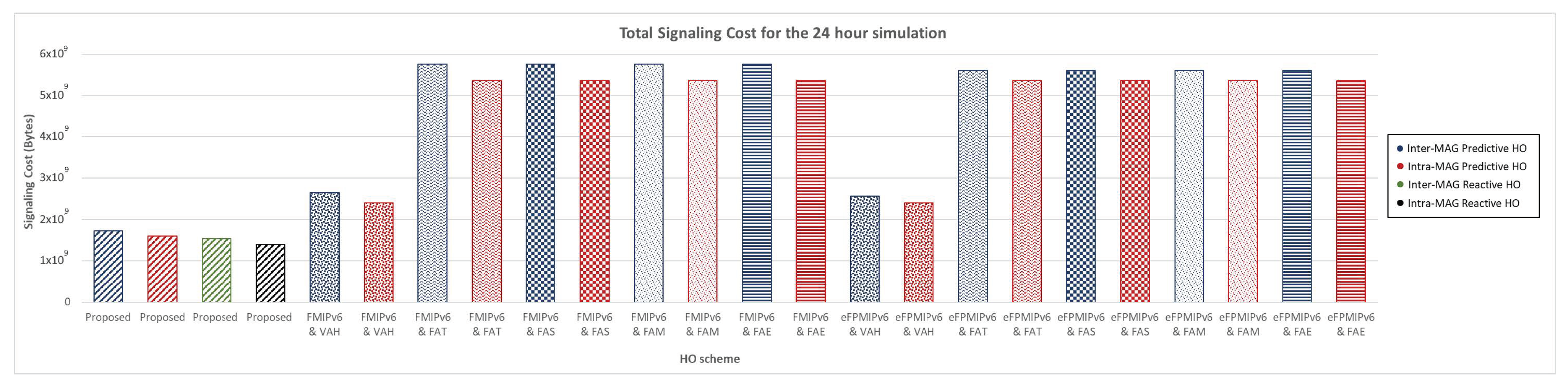
5.2. Twenty-Four-Hour Evaluation Results
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
Sample Availability
Appendix A. The Positions and the Frequencies of the Simulated Networks
| Network | Position | Geographic Latitude | Geographic Longitude | Downlink and Uplink Spectrum in MHz (WiMAX Band) | MAG |
|---|---|---|---|---|---|
| WAVE 1 | c17 | 37.9875 | 23.728611 | 5875–5885 (SCH1) | 2 |
| WAVE 2 | c22 | 37.9875 | 23.730833 | 5895–5905 (SCH2) | 2 |
| WAVE 3 | e14 | 37.986667 | 23.726944 | 5895–5905 (SCH2) | 3 |
| WAVE 4 | e24 | 37.986389 | 23.731944 | 5905–5915 (SCH3) | 3 |
| WAVE 5 | e29 | 37.986667 | 23.734444 | 5875–5885 (SCH1) | 3 |
| WAVE 6 | f3 | 37.986389 | 23.721389 | 5875–5885 (SCH1) | 3 |
| WAVE 7 | f16 | 37.986111 | 23.728056 | 5905–5915 (SCH3) | 3 |
| WAVE 8 | h22 | 37.985 | 23.730556 | 5915–5925 (SCH4) | 4 |
| WAVE 9 | i28 | 37.984444 | 23.734167 | 5895–5905 (SCH2) | 5 |
| WAVE 10 | j12 | 37.984444 | 23.725556 | 5895–5905 (SCH2) | 5 |
| WAVE 11 | j18 | 37.984167 | 23.728611 | 5875–5885 (SCH1) | 5 |
| WAVE 12 | k26 | 37.983889 | 23.732778 | 5905–5915 (SCH3) | 6 |
| WAVE 13 | l9 | 37.983333 | 23.723889 | 5875–5885 (SCH1) | 6 |
| WAVE 14 | l21 | 37.983333 | 23.730278 | 5895–5905 (SCH2) | 6 |
| WAVE 15 | m17 | 37.983056 | 23.728333 | 5915–5925 (SCH4) | 7 |
| WAVE 16 | m20 | 37.983056 | 23.73 | 5905–5915 (SCH3) | 7 |
| WAVE 17 | m27 | 37.982778 | 23.733333 | 5875–5885 (SCH1) | 7 |
| WAVE 18 | n12 | 37.982222 | 23.725833 | 5905–5915 (SCH3) | 7 |
| WAVE 19 | o31 | 37.981944 | 23.735278 | 5905–5915 (SCH3) | 8 |
| WAVE 20 | p24 | 37.981389 | 23.731667 | 5905–5915 (SCH3) | 8 |
| WAVE 21 | p29 | 37.981389 | 23.734444 | 5895–5905 (SCH2) | 8 |
| WAVE 22 | q6 | 37.981111 | 23.722778 | 5905–5915 (SCH3) | 9 |
| WAVE 23 | q11 | 37.980833 | 23.725278 | 5915–5925 (SCH4) | 9 |
| WAVE 24 | q13 | 37.980833 | 23.726389 | 5875–5885 (SCH1) | 9 |
| WAVE 25 | r18 | 37.980278 | 23.728611 | 5895–5905 (SCH2) | 9 |
| WAVE 26 | s15 | 37.98 | 23.727222 | 5905–5915 (SCH3) | 10 |
| WAVE 27 | s26 | 37.980278 | 23.7325 | 5915–5925 (SCH4) | 10 |
| WAVE 28 | t21 | 37.979444 | 23.730278 | 5875–5885 (SCH1) | 10 |
| Network | Position | Geographic Latitude | Geographic Longitude | Number of Antennas | MAG |
|---|---|---|---|---|---|
| LTE-A Pro FD-MIMO Macrocell 1 | b23 | 37.987778 | 23.731667 | 64 | 1 |
| LTE-A Pro FD-MIMO Macrocell 2 | f3 | 37.986389 | 23.721111 | 64 | 3 |
| LTE-A Pro FD-MIMO Macrocell 3 | k16 | 37.983889 | 23.728056 | 64 | 6 |
| LTE-A Pro FD-MIMO Macrocell 4 | n33 | 37.982222 | 23.736111 | 64 | 7 |
| LTE-A Pro FD-MIMO Macrocell 5 | u11 | 37.978889 | 23.725278 | 64 | 11 |
| Spectrum in MHz for each Antenna | |||||
| Antenna Identifier | Downlink and Uplink Spectrum in MHz (LTE Band) | ||||
| 1 | 462.5–467.5 and 452.5–457.5 (31) | ||||
| 2 | 734–739 and 704–709 (17) | ||||
| 3 | 739–744 and 709–714 (17) | ||||
| 4 | 758–763 and 714–719 (28) | ||||
| 5 | 763–768 and 719–724 (28) | ||||
| 6 | 768–773 and 724–729 (28) | ||||
| 7 | 773–778 and 729–734 (28) | ||||
| 8 | 860–865 and 815–820 (18) | ||||
| 9 | 865–870 and 820–825 (18) | ||||
| 10 | 870–875 and 825–830 (18) | ||||
| 11 | 875–880 and 830–835 (19) | ||||
| 12 | 880–885 and 835–840 (19) | ||||
| 13 | 885–890 and 840–845 (19) | ||||
| 14 | 925–930 and 890–895 (8) | ||||
| 15 | 930–935 and 895–900 (8) | ||||
| 16 | 935–940 and 900–905 (8) | ||||
| 17 | 940–945 and 905–910 (8) | ||||
| 18 | 945–950 and 910–915 (8) | ||||
| 19 | 1475.9–1480.9 and 1427.9–1432.9 (11) | ||||
| 20 | 1480.9–1485.9 and 1432.9–1437.9 (11) | ||||
| 21 | 1485.9–1490.9 and 1437.9–1442.9 (11) | ||||
| 22 | 1490.9–1495.9 and 1442.9–1447.9 (11) | ||||
| 23 | 1495.9–1500.9 and 1447.9–1452.9 (11) | ||||
| 24 | 1525–1530 and 1625.5–1630.5 (24) | ||||
| 25 | 1530–1535 and 1630.5–1635.5 (24) | ||||
| 26 | 1535–1540 and 1635.5–1640.5 (24) | ||||
| 27 | 1540–1545 and 1640.5–1645.5 (24) | ||||
| 28 | 1545–1550 and 1645.5–1650.5 (24) | ||||
| 29 | 1550–1555 and 1650.5–1655.5 (24) | ||||
| 30 | 1805–1810 and 1710–1715 (3) | ||||
| 31 | 1810–1815 and 1715–1720 (3) | ||||
| 32 | 1815–1820 and 1720–1725 (3) | ||||
| 33 | 1820–1825 and 1725–1730 (3) | ||||
| 34 | 1825–1830 and 1730–1735 (3) | ||||
| 35 | 1830–1835 and 1735–1740 (3) | ||||
| 36 | 1835–1840 and 1740–1745 (3) | ||||
| 37 | 1840–1845 and 1745–1750 (3) | ||||
| 38 | 1845–1850 and 1750–1755 (3) | ||||
| 39 | 1850–1855 and 1755–1760 (3) | ||||
| 40 | 1855–1860 and 1760–1765 (3) | ||||
| 41 | 1860–1865 and 1765–1770 (3) | ||||
| 42 | 1865–1870 and 1770–1775 (3) | ||||
| 43 | 1870–1875 and 1775–1780 (3) | ||||
| 44 | 1875–1880 and 1780–1785 (3) | ||||
| 45 | 1930–1935 and 1880–1885 (2) | ||||
| 46 | 1935–1940 and 1885–1890 (2) | ||||
| 47 | 1940–1945 and 1890–1895 (2) | ||||
| 48 | 1945–1950 and 1895–1900 (2) | ||||
| 49 | 1950–1955 and 1900–1905 (2) | ||||
| 50 | 1955–1960 and 1905–1910 (2) | ||||
| 51 | 2600–2605 and 1910–1915 (15) | ||||
| 52 | 2605–2610 and 1915–1920 (15) | ||||
| 53 | 2110–2115 and 1960–1965 (1) | ||||
| 54 | 2115–2120 and 1965–1970 (1) | ||||
| 55 | 2120–2125 and 1970–1975 (1) | ||||
| 56 | 2125–2130 and 1975–1980 (1) | ||||
| 57 | 2180–2185 and 2000–2005 (23) | ||||
| 58 | 2185–2190 and 2005–2010 (23) | ||||
| 59 | 2190–2195 and 2010–2015 (23) | ||||
| 60 | 2195–2200 and 2015–2020 (23) | ||||
| 61 | 2595–2600 and 2020–2025 (16) | ||||
| 62 | 2350–2355 and 2305–2310 (30) | ||||
| 63 | 2355–2360 and 2310–2315 (30) | ||||
| 64 | 2620–2625 and 2500–2505 (7) | ||||
| Network | Position | Geographic Latitude | Geographic Longitude | Downlink and Uplink Spectrum in MHz (LTE Band) | MAG |
|---|---|---|---|---|---|
| LTE Macrocell 1 | e14 | 37.986389 | 23.726667 | 3515–3520 and 3415–3420 (22) | 3 |
| LTE Macrocell 2 | i5 | 37.985 | 23.722222 | 2675–2690 and 2565–2570 (7) | 5 |
| LTE Macrocell 3 | k26 | 37.983611 | 23.733056 | 3510–3515 and 3410–3415 (22) | 6 |
| LTE Macrocell 4 | m21 | 37.982778 | 23.730278 | 3520–3525 and 3420–3425 (22) | 7 |
| LTE Macrocell 5 | p9 | 37.981667 | 23.724167 | 3525–3530 and 3425–3430 (22) | 8 |
| LTE Macrocell 6 | r2 | 37.980833 | 23.720556 | 3510–3515 and 3410–3415 (22) | 9 |
| LTE Macrocell 7 | r25 | 37.980556 | 23.732222 | 2675–2690 and 2565–2570 (7) | 9 |
| LTE Macrocell 8 | s17 | 37.979722 | 23.728333 | 3515–3520 and 3415–3420 (22) | 10 |
| LTE Femtocell 1 | c13 | 37.987222 | 23.726389 | 3530–3535 and 3430–3435 (22) | 2 |
| LTE Femtocell 2 | c19 | 37.987222 | 23.729444 | 3525–3530 and 3425–3430 (22) | 2 |
| LTE Femtocell 3 | d11 | 37.986944 | 23.725 | 3520–3525 and 3420–3425 (22) | 2 |
| LTE Femtocell 4 | d29 | 37.986944 | 23.734444 | 3525–3530 and 3425–3430 (22) | 2 |
| LTE Femtocell 5 | e1 | 37.986667 | 23.720556 | 3520–3525 and 3420–3425 (22) | 3 |
| LTE Femtocell 6 | f16 | 37.986389 | 23.728056 | 3535–3540 and 3435–3440 (22) | 3 |
| LTE Femtocell 7 | g9 | 37.985833 | 23.724167 | 3530–3535 and 3430–3435 (22) | 4 |
| LTE Femtocell 8 | g13 | 37.985833 | 23.726389 | 3540–3545 and 3440–3445 (22) | 4 |
| LTE Femtocell 9 | g18 | 37.985833 | 23.728889 | 3545–3550 and 3445–3450 (22) | 4 |
| LTE Femtocell 10 | g19 | 37.985556 | 23.729722 | 3550–3555 and 3450–3455 (22) | 4 |
| LTE Femtocell 11 | g24 | 37.985833 | 23.731944 | 3540–3545 and 3440–3445 (22) | 4 |
| LTE Femtocell 12 | h1 | 37.985278 | 23.720278 | 3545–3550 and 3445–3450 (22) | 4 |
| LTE Femtocell 13 | h12 | 37.985 | 23.725833 | 3555–3560 and 3455–3460 (22) | 4 |
| LTE Femtocell 14 | h17 | 37.985278 | 23.728333 | 3560–3565 and 3460–3465 (22) | 4 |
| LTE Femtocell 15 | i18 | 37.985 | 23.728611 | 3540–3545 and 3440–3445 (22) | 5 |
| LTE Femtocell 16 | i23 | 37.984722 | 23.731389 | 3555–3560 and 3455–3460 (22) | 5 |
| LTE Femtocell 17 | i24 | 37.985 | 23.731667 | 3535–3540 and 3435–3440 (22) | 5 |
| LTE Femtocell 18 | j8 | 37.984722 | 23.723889 | 3530–3535 and 3430–3435 (22) | 5 |
| LTE Femtocell 19 | j9 | 37.984444 | 23.724444 | 3535–3540 and 3435–3440 (22) | 5 |
| LTE Femtocell 20 | j12 | 37.984444 | 23.725556 | 3545–3550 and 3445–3450 (22) | 5 |
| LTE Femtocell 21 | j16 | 37.984167 | 23.727778 | 3570–3575 and 3470–3475 (22) | 5 |
| LTE Femtocell 22 | j27 | 37.984444 | 23.733611 | 3550–3555 and 3450–3455 (22) | 5 |
| LTE Femtocell 23 | k8 | 37.983889 | 23.723611 | 3550–3555 and 3450–3455 (22) | 6 |
| LTE Femtocell 24 | k14 | 37.984167 | 23.726944 | 3565–3570 and 3465–3470 (22) | 6 |
| LTE Femtocell 25 | k16 | 37.983611 | 23.728056 | 3575–3580 and 3475–3480 (22) | 6 |
| LTE Femtocell 26 | k17 | 37.983889 | 23.728611 | 3585–3590 and 3485–3490 (22) | 6 |
| LTE Femtocell 27 | k22 | 37.984167 | 23.731111 | 3580–3585 and 3480–3485 (22) | 6 |
| LTE Femtocell 28 | k23 | 37.983889 | 23.731667 | 3565–3570 and 3465–3470 (22) | 6 |
| LTE Femtocell 29 | k29 | 37.983611 | 23.734444 | 3525–3530 and 3425–3430 (22) | 6 |
| LTE Femtocell 30 | l10 | 37.983056 | 23.724722 | 3560–3565 and 3460–3465 (22) | 6 |
| LTE Femtocell 31 | l15 | 37.983333 | 237.275 | 3550–3555 and 3450–3455 (22) | 6 |
| LTE Femtocell 32 | l16 | 37.983056 | 23.727778 | 3540–3545 and 3440–3445 (22) | 6 |
| LTE Femtocell 33 | l22 | 37.983611 | 23.730833 | 3545–3550 and 3445–3450 (22) | 6 |
| LTE Femtocell 34 | l23 | 37.983333 | 23.731111 | 3560–3565 and 3460–3465 (22) | 6 |
| LTE Femtocell 35 | l25 | 37.983333 | 23.732222 | 3575–3580 and 3475–3480 (22) | 6 |
| LTE Femtocell 36 | l32 | 37.983056 | 23.736111 | 3530–3535 and 3430–3435 (22) | 6 |
| LTE Femtocell 37 | l33 | 37.983333 | 23.736389 | 3570–3575 and 3470–3475 (22) | 6 |
| LTE Femtocell 38 | m11 | 37.982778 | 23.725278 | 3555–3560 and 3455–3460 (22) | 7 |
| LTE Femtocell 39 | m16 | 37.982778 | 23.728056 | 3580–3585 and 3480–3485 (22) | 7 |
| LTE Femtocell 40 | m18 | 37.982778 | 23.728611 | 3535–3540 and 3435–3440 (22) | 7 |
| LTE Femtocell 41 | m19 | 37.982778 | 23.729722 | 3590–3595 and 3490–3495 (22) | 7 |
| LTE Femtocell 42 | m26 | 37.982778 | 23.732778 | 3585–3590 and 3485–3490 (22) | 7 |
| LTE Femtocell 43 | m28 | 37.983056 | 23.733889 | 3540–3545 and 3440–3445 (22) | 7 |
| LTE Femtocell 44 | n12 | 37.982222 | 23.725833 | 3595–3600 and 3495–3500 (22) | 7 |
| LTE Femtocell 45 | n23 | 37.982222 | 23.731389 | 3530–3535 and 3430–3435 (22) | 7 |
| LTE Femtocell 46 | n28 | 379.825 | 23.733889 | 3555–3560 and 3455–3460 (22) | 7 |
| LTE Femtocell 47 | n31 | 379.825 | 23.735278 | 3560–3565 and 3460–3465 (22) | 7 |
| LTE Femtocell 48 | o17 | 37.982222 | 23.728056 | 3565–3570 and 3465–3470 (22) | 8 |
| LTE Femtocell 49 | o26 | 37.981944 | 237.325 | 3570–3575 and 3470–3475 (22) | 8 |
| LTE Femtocell 50 | o28 | 379.825 | 23.734444 | 3580–3585 and 3480–3485 (22) | 8 |
| LTE Femtocell 51 | p6 | 37.981667 | 23.722778 | 3520–3525 and 3420–3425 (22) | 8 |
| LTE Femtocell 52 | p14 | 37.981389 | 23.726944 | 3530–3535 and 3430–3435 (22) | 8 |
| LTE Femtocell 53 | p29 | 37.981667 | 23.734444 | 3585–3590 and 3485–3490 (22) | 8 |
| LTE Femtocell 54 | q13 | 37.980833 | 23.726111 | 3540–3545 and 3440–3445 (22) | 9 |
| LTE Femtocell 55 | q14 | 37.980833 | 23.726667 | 3550–3555 and 3450–3455 (22) | 9 |
| LTE Femtocell 56 | q21 | 37.981111 | 23.730556 | 3540–3545 and 3440–3445 (22) | 9 |
| LTE Femtocell 57 | q25 | 37.980833 | 23.732222 | 3535–3540 and 3435–3440 (22) | 9 |
| LTE Femtocell 58 | r19 | 37.980278 | 23.728889 | 3560–3565 and 3460–3465 (22) | 9 |
| LTE Femtocell 59 | r20 | 37.980278 | 23.729444 | 3575–3580 and 3475–3480 (22) | 9 |
| LTE Femtocell 60 | r30 | 37.980556 | 23.734444 | 3590–3595 and 3490–3495 (22) | 9 |
| LTE Femtocell 61 | s10 | 37.980278 | 23.724722 | 3535–3540 and 3435–3440 (22) | 10 |
| LTE Femtocell 62 | s16 | 37.979722 | 23.727778 | 3580–3585 and 3480–3485 (22) | 10 |
| LTE Femtocell 63 | s30 | 37.980278 | 23.734444 | 3525–3530 and 3425–3430 (22) | 10 |
| LTE Femtocell 64 | t13 | 37.979722 | 23.726389 | 3520–3525 and 3420–3425 (22) | 10 |
| LTE Femtocell 65 | t20 | 37.979444 | 23.729722 | 3550–3555 and 3450–3455 (22) | 10 |
| LTE Femtocell 66 | t22 | 37.979722 | 23.730556 | 3570–3575 and 3470–3475 (22) | 10 |
| LTE Femtocell 67 | t25 | 37.98 | 23.732222 | 3565–3570 and 3465–3470 (22) | 10 |
| LTE Femtocell 68 | u17 | 37.978889 | 23.728333 | 3575–3580 and 3475–3480 (22) | 11 |
| LTE Femtocell 69 | u25 | 37.979167 | 23.732222 | 3530–3535 and 3430–3435 (22) | 11 |
| LTE Femtocell 70 | u27 | 37.979167 | 23.733333 | 3520–3525 and 3420–3425 (22) | 11 |
| Network | Position | Geographic Latitude | Geographic Longitude | Downlink and Uplink Spectrum in MHz (WiMAX Band) | MAG |
|---|---|---|---|---|---|
| WiMAX Macrocell 1 | d24 | 37.987222 | 23.731944 | 746–757 and 778–783 (7) | 2 |
| WiMAX Macrocell 2 | f31 | 37.986111 | 23.735833 | 2315–2320 and 2345–2350 (2) | 3 |
| WiMAX Macrocell 3 | g8 | 37.985833 | 23.723889 | 2315–2320 and 2345–2350 (2) | 4 |
| WiMAX Macrocell 4 | l14 | 37.983611 | 23.726667 | 810–815 and 800–805 (7) | 6 |
| WiMAX Macrocell 5 | m17 | 37.983056 | 23.728333 | 1795–1800 and 1785–1790 (8) | 7 |
| WiMAX Macrocell 6 | n12 | 37.982222 | 23.725833 | 1800–1805 and 1790–1795 (8) | 7 |
| WiMAX Macrocell 7 | p3 | 37.981944 | 23.721111 | 746–757 and 778–783 (7) | 8 |
| WiMAX Macrocell 8 | s26 | 37.980278 | 23.7325 | 1925–1930 and 1920–1925 (8) | 10 |
| WiMAX Femtocell 1 | c14 | 37.9875 | 23.727222 | 2625–2630 and 2505–2510 (3) | 2 |
| WiMAX Femtocell 2 | d20 | 37.986944 | 23.73 | 2630–2635 and 2510–2525 (3) | 2 |
| WiMAX Femtocell 3 | d29 | 37.986944 | 23.734722 | 2625–2630 and 2505–2510 (3) | 2 |
| WiMAX Femtocell 4 | f16 | 37.986111 | 23.728056 | 2635–2640 and 2525–2530 (3) | 3 |
| WiMAX Femtocell 5 | g12 | 37.986111 | 23.725833 | 2640–2645 and 2530–2535 (3) | 4 |
| WiMAX Femtocell 6 | g18 | 37.985833 | 23.728889 | 2645–2650 and 2535–2540 (3) | 4 |
| WiMAX Femtocell 7 | g19 | 37.985833 | 23.729444 | 2640–2645 and 2530–2535 (3) | 4 |
| WiMAX Femtocell 8 | h25 | 37.985556 | 23.7325 | 2630–2635 and 2510–2525 (3) | 4 |
| WiMAX Femtocell 9 | i3 | 37.985 | 23.720833 | 2625–2630 and 2505–2510 (3) | 5 |
| WiMAX Femtocell 10 | i6 | 37.984722 | 23.722778 | 2640–2645 and 2530–2535 (3) | 5 |
| WiMAX Femtocell 11 | i23 | 37.984722 | 23.731389 | 2650–2655 and 2540–2545 (3) | 5 |
| WiMAX Femtocell 12 | j14 | 37.984444 | 23.726667 | 2625–2630 and 2505–2510 (3) | 5 |
| WiMAX Femtocell 13 | j16 | 37.984167 | 23.728056 | 2655–2660 and 2545–2550 (3) | 5 |
| WiMAX Femtocell 14 | j18 | 37.984167 | 23.728611 | 2630–2635 and 2510–2525 (3) | 5 |
| WiMAX Femtocell 15 | j25 | 37.984167 | 23.7325 | 2625–2630 and 2505–2510 (3) | 5 |
| WiMAX Femtocell 16 | k15 | 37.983889 | 23.727222 | 2650–2655 and 2540–2545 (3) | 6 |
| WiMAX Femtocell 17 | l10 | 37.983056 | 23.724722 | 2630–2635 and 2510–2525 (3) | 6 |
| WiMAX Femtocell 18 | l14 | 37.983333 | 23.727222 | 2635–2640 and 2525–2530 (3) | 6 |
| WiMAX Femtocell 19 | l16 | 37.983333 | 23.727778 | 2640–2645 and 2530–2535 (3) | 6 |
| WiMAX Femtocell 20 | l19 | 37.983611 | 23.729444 | 2645–2650 and 2535–2540 (3) | 6 |
| WiMAX Femtocell 21 | l22 | 37.983611 | 23.730556 | 2660–2665 and 2550–2555 (3) | 6 |
| WiMAX Femtocell 22 | l23 | 37.983611 | 23.731389 | 2635–2640 and 2525–2530 (3) | 6 |
| WiMAX Femtocell 23 | m14 | 37.983056 | 23.727222 | 2665–2670 and 2555–2560 (3) | 7 |
| WiMAX Femtocell 24 | m17 | 37.982778 | 23.728333 | 2625–2630 and 2505–2510 (3) | 7 |
| WiMAX Femtocell 25 | m20 | 37.983056 | 23.73 | 2670–2675 and 2560–2565 (3) | 7 |
| WiMAX Femtocell 26 | m22 | 37.983333 | 23.730833 | 2655–2660 and 2545–2550 (3) | 7 |
| WiMAX Femtocell 27 | n26 | 37.982222 | 23.732778 | 2650–2655 and 2540–2545 (3) | 7 |
| WiMAX Femtocell 28 | n29 | 37.9825 | 23.734444 | 2645–2650 and 2535–2540 (3) | 7 |
| WiMAX Femtocell 29 | n31 | 37.982222 | 23.735556 | 2635–2640 and 2525–2530 (3) | 7 |
| WiMAX Femtocell 30 | o21 | 37.981944 | 23.730278 | 2640–2645 and 2530–2535 (3) | 8 |
| WiMAX Femtocell 31 | o30 | 37.981944 | 23.734722 | 2625–2630 and 2505–2510 (3) | 8 |
| WiMAX Femtocell 32 | q14 | 37.980833 | 23.726667 | 2635–2640 and 2525–2530 (3) | 9 |
| WiMAX Femtocell 33 | r10 | 37.980556 | 23.724722 | 2625–2630 and 2505–2510 (3) | 9 |
| WiMAX Femtocell 34 | r12 | 37.980278 | 23.725556 | 2630–2635 and 2510–2525 (3) | 9 |
| WiMAX Femtocell 35 | s20 | 37.98 | 23.729167 | 2650–2655 and 2540–2545 (3) | 10 |
| WiMAX Femtocell 36 | s22 | 37.98 | 23.730556 | 2630–2635 and 2510–2525 (3) | 10 |
| WiMAX Femtocell 37 | s26 | 37.98 | 23.7325 | 2640–2645 and 2530–2535 (3) | 10 |
| WiMAX Femtocell 38 | t18 | 37.979167 | 23.728333 | 2635–2640 and 2525–2530 (3) | 10 |
| WiMAX Femtocell 39 | t21 | 37.979444 | 23.73 | 2625–2630 and 2505–2510 (3) | 10 |
| WiMAX Femtocell 40 | t28 | 37.979444 | 23.734167 | 2635–2640 and 2525–2530 (3) | 10 |
| WiMAX Femtocell 41 | v15 | 37.978333 | 23.726944 | 2630–2635 and 2510–2525 (3) | 11 |
Appendix B. The Networks and Their Quality Indicator per SLA
| Disaster Management Services of SLA1 | ||||||||||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Disaster-Aware NAV | Disaster-Aware VoIP | Live Video Streaming for Emergency Manipulation | Image Transmission for Emergency Manipulation | |||||||||||||||||||||||||||||
| Network | Throughput | Latency | Jitter | Packet Loss |
Energy Consumption |
Service Reliability | Security | Monetary Cost | Throughput | Latency | Jitter | Packet Loss |
Energy Consumption |
Service Reliability | Security | Monetary Cost | Throughput | Latency | Jitter | Packet Loss |
Energy Consumption |
Service Reliability | Security | Monetary Cost | Throughput | Latency | Jitter | Packet Loss |
Energy Consumption |
Service Reliability | Security | Monetary Cost |
| WAVE 1 | AH | H | VH | AH | M | H | VH | L | VH | AH | AH | H | M | H | H | L | VH | VH | VH | H | M | H | VH | L | H | AH | VH | AH | M | VH | VH | ML |
| WAVE 7 | AH | VH | H | H | MH | VH | VH | ML | AH | AH | AH | VH | MH | VH | VH | L | H | H | H | H | MH | H | VH | L | AH | AH | AH | VH | MH | H | H | ML |
| WAVE 11 | VH | AH | AH | AH | M | H | AH | ML | AH | AH | H | VH | M | AH | H | ML | VH | VH | VH | H | M | VH | H | ML | H | AH | AH | AH | M | H | H | ML |
| WAVE 13 | VH | AH | AH | VH | MH | AH | H | L | VH | H | VH | H | MH | AH | H | L | H | VH | VH | VH | MH | AH | AH | ML | AH | AH | H | VH | MH | H | H | ML |
| WAVE 17 | VH | AH | VH | VH | M | AH | H | ML | H | AH | H | VH | M | AH | AH | L | VH | VH | VH | H | M | VH | AH | L | AH | AH | H | VH | M | H | AH | L |
| WAVE 18 | VH | H | VH | H | MH | VH | AH | L | AH | H | AH | H | MH | AH | AH | ML | H | VH | VH | AH | MH | VH | AH | L | H | AH | AH | VH | MH | H | H | ML |
| WAVE 19 | AH | H | VH | AH | M | VH | AH | L | H | AH | AH | H | M | VH | AH | ML | H | AH | VH | VH | M | VH | AH | ML | H | AH | VH | AH | M | VH | VH | L |
| WAVE 21 | H | VH | VH | H | H | AH | H | ML | H | AH | H | H | H | AH | VH | L | AH | AH | AH | H | H | AH | AH | L | VH | VH | VH | AH | H | H | AH | ML |
| LTE FD-MIMO 3 | AH | AH | AH | AH | AL | VH | AH | VL | AH | VH | AH | VH | AL | VH | VH | AL | AH | AH | VH | VH | AL | AH | VH | VL | VH | AH | AH | VH | AL | AH | VH | VL |
| LTE FD-MIMO 4 | AH | VH | VH | AH | AL | VH | VH | AL | AH | VH | AH | VH | AL | VH | AH | VL | AH | AH | AH | VH | AL | VH | VH | AL | VH | AH | AH | AH | AL | AH | VH | VL |
| LTE Macrocell 1 | AH | VH | AH | H | MH | H | H | L | VH | AH | AH | VH | MH | VH | H | ML | VH | AH | H | VH | MH | AH | VH | ML | VH | AH | H | H | MH | AH | AH | L |
| LTE Macrocell 2 | VH | H | AH | H | H | H | AH | ML | H | AH | AH | H | H | H | VH | ML | H | VH | AH | AH | H | H | VH | ML | VH | VH | VH | VH | H | VH | VH | L |
| LTE Macrocell 3 | VH | H | VH | AH | MH | AH | AH | L | VH | H | VH | H | MH | H | AH | L | VH | H | H | VH | MH | AH | VH | L | VH | AH | VH | H | MH | H | H | ML |
| LTE Macrocell 4 | H | AH | H | VH | MH | H | AH | ML | H | AH | VH | VH | MH | VH | AH | L | AH | VH | AH | H | MH | VH | H | ML | H | AH | VH | H | MH | H | H | L |
| LTE Macrocell 5 | AH | AH | H | VH | M | AH | VH | L | AH | H | AH | VH | M | AH | VH | ML | VH | VH | AH | H | M | VH | H | L | AH | VH | H | AH | M | AH | H | ML |
| LTE Macrocell 6 | VH | AH | H | H | MH | AH | VH | L | VH | VH | AH | H | MH | VH | H | ML | VH | VH | AH | VH | MH | H | H | L | AH | VH | H | H | MH | H | AH | ML |
| LTE Macrocell 7 | VH | AH | VH | H | H | VH | VH | L | AH | H | H | AH | H | AH | VH | L | H | VH | AH | AH | H | AH | H | L | AH | VH | AH | AH | H | AH | VH | L |
| LTE Femtocell 30 | H | VH | VH | VH | M | H | H | ML | AH | H | H | H | M | H | AH | L | H | AH | H | H | M | AH | VH | ML | AH | AH | H | VH | M | VH | AH | L |
| LTE Femtocell 38 | AH | AH | H | AH | M | AH | VH | ML | AH | H | H | VH | M | H | VH | L | AH | VH | VH | AH | M | VH | H | ML | AH | AH | H | VH | M | VH | VH | L |
| LTE Femtocell 53 | AH | H | AH | AH | M | H | AH | L | H | VH | AH | AH | M | AH | AH | L | H | VH | AH | H | M | AH | VH | L | VH | AH | AH | AH | M | AH | VH | L |
| WiMAX Macrocell 1 | H | H | VH | VH | M | H | AH | ML | VH | AH | VH | AH | M | H | VH | L | H | AH | H | AH | M | VH | VH | ML | H | AH | H | H | M | H | AH | L |
| WiMAX Macrocell 3 | AH | H | AH | AH | MH | VH | H | L | H | VH | AH | H | MH | H | VH | ML | AH | H | VH | VH | MH | AH | H | ML | H | VH | AH | VH | MH | H | AH | L |
| WiMAX Macrocell 4 | AH | AH | VH | VH | M | H | H | L | VH | VH | VH | H | M | H | AH | L | VH | H | AH | VH | M | AH | VH | L | AH | H | AH | VH | M | H | VH | ML |
| WiMAX Macrocell 5 | AH | VH | AH | VH | H | H | H | ML | AH | AH | VH | AH | H | VH | AH | L | H | H | AH | VH | H | AH | VH | L | H | AH | H | H | H | AH | AH | ML |
| WiMAX Macrocell 6 | VH | AH | VH | AH | H | VH | VH | ML | H | VH | H | AH | H | AH | AH | ML | H | H | H | H | H | AH | AH | L | AH | AH | VH | H | H | VH | VH | ML |
| WiMAX Macrocell 7 | H | AH | H | H | M | H | AH | L | H | VH | AH | VH | M | AH | VH | L | H | AH | H | H | M | H | H | L | AH | VH | VH | AH | M | H | VH | ML |
| WiMAX Macrocell 8 | H | H | AH | H | M | VH | H | L | H | AH | H | H | M | VH | AH | ML | AH | H | H | VH | M | AH | H | L | H | AH | VH | AH | M | AH | AH | ML |
| WiMAX Femtocell 13 | AH | VH | VH | VH | M | AH | AH | L | AH | H | VH | VH | M | H | H | ML | H | VH | H | H | M | AH | AH | ML | H | H | VH | AH | M | AH | H | ML |
| WiMAX Femtocell 17 | VH | VH | VH | H | H | H | VH | L | AH | VH | H | H | H | H | AH | ML | AH | H | VH | VH | H | H | H | ML | AH | VH | H | AH | H | H | AH | L |
| Non-Disaster Management Services of SLA1 | ||||||||||||||||||||||||||||||||
| NAV | VoIP | CV | ||||||||||||||||||||||||||||||
| Network | Throughput | Latency | Jitter | Packet Loss |
Energy Consumption |
Service Reliability | Security | Monetary Cost | Throughput | Latency | Jitter | Packet Loss |
Energy Consumption |
Service Reliability | Security | Monetary Cost | Throughput | Latency | Jitter | Packet Loss |
Energy Consumption |
Service Reliability | Security | Monetary Cost | ||||||||
| WAVE 1 | VH | MH | VH | H | M | AH | H | L | AH | AH | AH | VH | M | AH | H | ML | VH | VH | VH | AH | M | AH | VH | L | ||||||||
| WAVE 7 | MH | MH | MH | MH | MH | VH | H | ML | AH | AH | H | VH | MH | VH | AH | ML | VH | AH | AH | H | MH | VH | AH | ML | ||||||||
| WAVE 11 | VH | MH | VH | VH | M | H | VH | ML | H | AH | H | VH | M | AH | VH | L | VH | AH | AH | VH | M | VH | VH | L | ||||||||
| WAVE 13 | MH | VH | VH | H | MH | AH | H | L | VH | VH | H | VH | MH | VH | VH | ML | H | H | H | H | MH | VH | VH | L | ||||||||
| WAVE 17 | H | H | H | MH | M | VH | VH | ML | H | H | VH | H | M | AH | AH | L | H | VH | VH | H | M | VH | H | L | ||||||||
| WAVE 18 | H | MH | VH | H | MH | VH | AH | ML | AH | H | H | VH | MH | VH | AH | L | AH | VH | H | VH | MH | AH | VH | L | ||||||||
| WAVE 19 | MH | VH | MH | MH | M | AH | H | ML | H | VH | AH | VH | M | AH | AH | ML | H | VH | AH | VH | M | VH | VH | ML | ||||||||
| WAVE 21 | MH | H | MH | H | H | VH | VH | ML | VH | H | H | H | H | VH | H | ML | VH | H | VH | H | H | VH | AH | L | ||||||||
| LTE FD-MIMO 3 | AH | VH | VH | VH | AL | VH | VH | VL | AH | VH | AH | AH | AL | AH | VH | AL | VH | VH | AH | VH | AL | AH | AH | AL | ||||||||
| LTE FD-MIMO 4 | VH | AH | VH | AH | AL | AH | VH | AL | AH | VH | AH | AH | AL | AH | AH | AL | AH | AH | AH | AH | AL | AH | VH | AL | ||||||||
| LTE Macrocell 1 | H | VH | VH | VH | MH | VH | AH | ML | H | VH | VH | H | MH | VH | H | L | VH | H | AH | VH | MH | VH | AH | ML | ||||||||
| LTE Macrocell 2 | MH | VH | VH | VH | H | VH | VH | L | H | H | AH | VH | H | VH | AH | L | VH | AH | VH | VH | H | VH | VH | ML | ||||||||
| LTE Macrocell 3 | H | VH | H | VH | MH | VH | AH | ML | VH | VH | H | AH | MH | VH | VH | L | H | VH | VH | AH | MH | AH | AH | ML | ||||||||
| LTE Macrocell 4 | H | MH | VH | H | MH | H | VH | ML | AH | VH | VH | H | MH | H | VH | ML | AH | H | H | VH | MH | VH | VH | L | ||||||||
| LTE Macrocell 5 | MH | MH | H | MH | M | AH | H | ML | AH | H | AH | AH | M | AH | VH | ML | H | H | AH | AH | M | H | AH | ML | ||||||||
| LTE Macrocell 6 | MH | VH | H | H | MH | AH | H | L | H | H | AH | AH | MH | VH | H | L | AH | AH | H | H | MH | H | VH | L | ||||||||
| LTE Femtocell 30 | H | H | VH | VH | M | AH | VH | L | H | VH | VH | AH | M | VH | AH | ML | AH | AH | VH | VH | M | VH | H | ML | ||||||||
| LTE Femtocell 38 | MH | VH | VH | VH | M | H | VH | ML | VH | VH | VH | H | M | VH | H | ML | AH | AH | H | AH | M | H | VH | ML | ||||||||
| LTE Femtocell 53 | MH | MH | VH | H | M | H | VH | ML | AH | VH | AH | AH | M | AH | VH | L | VH | H | AH | VH | M | H | AH | ML | ||||||||
| WiMAX Macrocell 1 | MH | VH | H | VH | M | AH | AH | L | AH | AH | VH | H | M | VH | AH | ML | VH | H | AH | AH | M | AH | VH | L | ||||||||
| WiMAX Macrocell 3 | H | H | VH | VH | MH | VH | AH | ML | H | AH | H | VH | MH | AH | H | L | AH | H | AH | VH | MH | VH | H | L | ||||||||
| WiMAX Macrocell 4 | VH | H | MH | VH | M | H | VH | ML | AH | H | AH | H | M | AH | H | ML | AH | AH | AH | VH | M | AH | H | L | ||||||||
| WiMAX Macrocell 5 | H | VH | H | VH | H | AH | AH | L | AH | VH | AH | AH | H | H | H | ML | H | VH | AH | H | H | H | H | L | ||||||||
| WiMAX Macrocell 6 | H | H | H | H | H | VH | VH | L | H | H | VH | VH | H | AH | VH | L | AH | AH | H | VH | H | VH | AH | L | ||||||||
| WiMAX Macrocell 7 | MH | VH | VH | VH | M | VH | AH | L | VH | AH | H | AH | M | H | VH | ML | AH | AH | H | VH | M | AH | AH | L | ||||||||
| WiMAX Macrocell 8 | MH | MH | H | VH | M | H | H | ML | VH | AH | H | AH | M | VH | VH | ML | VH | H | VH | AH | M | VH | VH | ML | ||||||||
| WiMAX Femtocell 13 | H | H | VH | H | M | AH | VH | L | VH | AH | VH | AH | M | AH | H | ML | VH | VH | H | H | M | VH | AH | L | ||||||||
| WiMAX Femtocell 17 | VH | VH | MH | H | H | AH | VH | ML | AH | VH | H | H | H | AH | AH | L | VH | H | VH | H | H | AH | VH | ML | ||||||||
| NAV | VoIP | |||||||||||||||||||||||||||||||
| Network | Throughput | Latency | Jitter | Packet Loss |
Energy Consumption |
Service Reliability | Security | Monetary Cost | Throughput | Latency | Jitter | Packet Loss |
Energy Consumption |
Service Reliability | Security | Monetary Cost | ||||||||||||||||
| WAVE 1 | AH | H | H | VH | M | VH | AH | ML | AH | AH | VH | AH | M | H | H | ML | ||||||||||||||||
| WAVE 7 | VH | H | VH | VH | MH | VH | VH | ML | AH | VH | AH | VH | MH | H | H | ML | ||||||||||||||||
| WAVE 11 | AH | VH | VH | AH | M | AH | H | ML | H | H | AH | H | M | H | VH | L | ||||||||||||||||
| WAVE 13 | H | H | H | H | MH | VH | AH | ML | AH | H | VH | AH | MH | AH | H | ML | ||||||||||||||||
| WAVE 17 | H | VH | AH | H | M | VH | VH | ML | H | VH | H | VH | M | H | AH | ML | ||||||||||||||||
| WAVE 18 | H | H | H | VH | MH | AH | VH | ML | VH | AH | H | AH | MH | AH | AH | ML | ||||||||||||||||
| WAVE 19 | AH | AH | H | H | M | AH | VH | ML | VH | VH | AH | VH | M | AH | H | ML | ||||||||||||||||
| WAVE 21 | VH | AH | AH | AH | H | AH | AH | ML | H | AH | H | AH | H | AH | VH | L | ||||||||||||||||
| LTE FD-MIMO 3 | VH | VH | AH | VH | AL | VH | VH | VL | AH | VH | AH | AH | AL | VH | VH | AL | ||||||||||||||||
| LTE FD-MIMO 4 | VH | VH | VH | AH | AL | AH | VH | VL | VH | AH | VH | VH | AL | AH | AH | AL | ||||||||||||||||
| LTE Macrocell 1 | AH | VH | VH | AH | MH | AH | H | ML | H | AH | AH | H | MH | H | AH | L | ||||||||||||||||
| LTE Macrocell 2 | AH | VH | H | AH | H | AH | H | L | AH | AH | AH | VH | H | H | H | ML | ||||||||||||||||
| LTE Macrocell 3 | VH | H | VH | H | MH | VH | AH | ML | VH | VH | AH | VH | MH | VH | VH | L | ||||||||||||||||
| LTE Macrocell 4 | VH | AH | VH | VH | MH | H | AH | L | H | AH | AH | VH | MH | VH | AH | ML | ||||||||||||||||
| LTE Macrocell 5 | H | VH | VH | AH | M | H | AH | L | VH | H | VH | AH | M | AH | H | ML | ||||||||||||||||
| LTE Macrocell 6 | VH | AH | VH | AH | MH | H | H | ML | AH | H | H | VH | MH | H | H | ML | ||||||||||||||||
| LTE Macrocell 7 | VH | VH | VH | AH | H | H | AH | L | VH | VH | AH | H | H | H | H | L | ||||||||||||||||
| LTE Femtocell 30 | H | AH | AH | H | M | AH | AH | ML | VH | H | VH | AH | M | VH | VH | ML | ||||||||||||||||
| LTE Femtocell 38 | AH | H | H | H | M | VH | VH | ML | H | H | H | H | M | AH | H | ML | ||||||||||||||||
| LTE Femtocell 53 | VH | AH | AH | H | M | AH | AH | L | H | VH | H | VH | M | AH | AH | ML | ||||||||||||||||
| WiMAX Macrocell 1 | VH | H | VH | AH | M | H | H | L | VH | AH | H | VH | M | AH | H | ML | ||||||||||||||||
| WiMAX Macrocell 3 | AH | AH | H | AH | MH | H | AH | ML | H | VH | AH | AH | MH | VH | H | ML | ||||||||||||||||
| WiMAX Macrocell 4 | AH | AH | VH | AH | M | AH | H | ML | VH | AH | H | VH | M | H | H | L | ||||||||||||||||
| WiMAX Macrocell 5 | AH | VH | VH | H | H | VH | VH | ML | H | VH | VH | H | H | H | VH | L | ||||||||||||||||
| WiMAX Macrocell 6 | VH | VH | AH | AH | H | AH | H | ML | H | VH | AH | AH | H | H | VH | ML | ||||||||||||||||
| WiMAX Macrocell 7 | H | AH | VH | AH | M | VH | AH | L | VH | H | H | AH | M | H | H | ML | ||||||||||||||||
| WiMAX Macrocell 8 | H | H | AH | H | M | VH | VH | L | VH | H | H | AH | M | AH | H | L | ||||||||||||||||
| WiMAX Femtocell 13 | H | VH | H | AH | M | H | H | ML | H | VH | VH | AH | M | VH | H | ML | ||||||||||||||||
| WiMAX Femtocell 17 | VH | H | VH | AH | H | AH | H | L | H | AH | VH | VH | H | AH | H | ML | ||||||||||||||||
| Disaster Management Services of SLA2 | ||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Disaster-Aware NAV | Disaster-Aware VoIP | Image Transmission for Emergency Manipulation | ||||||||||||||||||||||
| Network | Throughput | Latency | Jitter | Packet Loss | Energy Consumption | Service Reliability | Security | Monetary Cost | Throughput | Latency | Jitter | Packet Loss | Energy Consumption | Service Reliability | Security | Monetary Cost | Throughput | Latency | Jitter | Packet Loss | Energy Consumption | Service Reliability | Security | Monetary Cost |
| WAVE 6 | H | H | M | VH | MH | H | MH | MH | H | H | MH | VH | MH | H | H | H | VH | VH | MH | VH | MH | M | MH | H |
| WAVE 11 | H | VH | H | H | M | M | H | H | H | VH | MH | H | M | VH | M | H | M | H | VH | VH | M | M | MH | VH |
| WAVE 15 | H | M | H | H | M | MH | M | VH | MH | MH | MH | H | M | MH | M | MH | H | H | VH | MH | M | H | MH | MH |
| WAVE 20 | VH | H | H | H | M | MH | MH | VH | MH | MH | MH | VH | M | MH | MH | MH | H | MH | M | MH | M | M | MH | H |
| WAVE 27 | MH | VH | MH | MH | H | VH | H | H | H | MH | H | H | H | MH | MH | H | M | MH | H | H | H | M | H | VH |
| LTE FD-MIMO 2 | VH | VH | H | H | AL | VH | VH | M | AH | AH | VH | VH | AL | AH | H | ML | VH | VH | VH | AH | AL | VH | VH | M |
| LTE FD-MIMO 3 | VH | AH | AH | VH | AL | H | VH | M | AH | VH | VH | VH | AL | VH | H | M | H | AH | AH | H | AL | AH | VH | MH |
| LTE FD-MIMO 4 | VH | H | H | VH | AL | VH | VH | ML | AH | H | VH | H | AL | H | AH | M | VH | AH | AH | AH | AL | AH | VH | ML |
| LTE Macrocell 1 | VH | H | H | M | MH | MH | M | MH | MH | H | H | MH | MH | H | M | VH | MH | H | MH | M | MH | H | H | VH |
| LTE Macrocell 2 | H | M | H | M | H | MH | H | VH | MH | VH | VH | MH | H | M | MH | VH | MH | H | MH | H | H | H | MH | H |
| LTE Macrocell 3 | MH | MH | H | H | MH | H | VH | MH | H | MH | MH | M | MH | MH | VH | MH | MH | H | MH | MH | MH | MH | MH | MH |
| LTE Macrocell 4 | M | H | MH | H | MH | MH | VH | VH | M | VH | H | H | MH | H | H | MH | MH | H | MH | MH | MH | MH | MH | H |
| LTE Macrocell 5 | VH | H | M | MH | M | VH | MH | MH | VH | M | VH | H | M | H | H | H | H | MH | M | VH | M | VH | M | H |
| LTE Macrocell 7 | MH | H | H | MH | H | MH | MH | MH | VH | M | M | VH | H | H | H | H | H | H | VH | H | H | H | MH | MH |
| LTE Femtocell 25 | M | H | H | VH | M | H | VH | VH | VH | H | VH | MH | M | MH | VH | VH | VH | M | H | H | M | H | MH | VH |
| WiMAX Macrocell 3 | VH | MH | H | VH | MH | H | M | H | M | H | VH | MH | MH | MH | MH | VH | M | H | H | H | MH | M | VH | H |
| WiMAX Macrocell 4 | VH | VH | MH | H | M | M | MH | H | MH | MH | MH | MH | M | M | VH | H | H | MH | H | H | M | M | MH | H |
| WiMAX Macrocell 5 | VH | MH | VH | H | H | MH | M | VH | H | VH | H | H | H | H | VH | MH | MH | VH | MH | MH | H | VH | VH | H |
| WiMAX Macrocell 6 | MH | H | MH | VH | H | H | H | VH | M | H | M | VH | H | H | VH | H | VH | H | MH | MH | H | MH | MH | H |
| WiMAX Macrocell 7 | M | H | MH | M | M | MH | H | MH | M | H | VH | MH | M | H | MH | MH | VH | MH | H | H | M | MH | MH | H |
| WiMAX Macrocell 8 | MH | MH | VH | M | M | H | MH | MH | M | VH | M | M | M | H | H | VH | MH | VH | MH | VH | M | VH | VH | H |
| NAV | VoIP | Web | ||||||||||||||||||||||
| Network | Throughput | Latency | Jitter | Packet Loss | Energy Consumption | Service Reliability | Security | Monetary Cost | Throughput | Latency | Jitter | Packet Loss | Energy Consumption | Service Reliability | Security | Monetary Cost | Throughput | Latency | Jitter | Packet Loss | Energy Consumption | Service Reliability | Security | Monetary Cost |
| WAVE 6 | MH | M | H | MH | MH | AH | M | H | MH | VH | VH | M | MH | MH | AH | VH | MH | VH | VH | MH | MH | M | H | H |
| WAVE 11 | MH | ML | H | H | M | H | VH | H | MH | AH | M | H | M | AH | H | H | M | MH | VH | MH | M | MH | H | MH |
| WAVE 15 | MH | H | H | H | M | VH | VH | MH | H | MH | VH | H | M | MH | M | VH | M | H | M | H | M | H | VH | H |
| WAVE 20 | M | H | M | VH | M | H | H | VH | VH | M | MH | H | M | H | MH | MH | VH | M | MH | H | M | VH | MH | H |
| WAVE 27 | VH | MH | MH | MH | H | MH | MH | VH | H | VH | MH | M | H | H | H | H | VH | H | M | MH | H | H | H | MH |
| LTE FD-MIMO 2 | AH | VH | AH | AH | AL | AH | MH | ML | VH | VH | VH | AH | AL | VH | AH | M | H | H | VH | VH | AL | VH | AH | ML |
| LTE FD-MIMO 3 | VH | H | H | H | AL | H | H | ML | VH | VH | AH | AH | AL | AH | H | L | VH | VH | VH | AH | AL | H | VH | M |
| LTE FD-MIMO 4 | VH | AH | H | VH | AL | AH | VH | ML | AH | H | AH | VH | AL | VH | VH | ML | H | AH | H | H | AL | VH | AH | M |
| LTE Macrocell 1 | M | MH | MH | H | MH | MH | VH | MH | MH | MH | H | MH | MH | MH | M | MH | MH | VH | H | MH | MH | M | VH | H |
| LTE Macrocell 2 | ML | MH | MH | H | H | MH | H | M | MH | M | VH | H | H | MH | VH | MH | VH | VH | VH | MH | H | MH | M | H |
| LTE Macrocell 3 | MH | MH | M | MH | MH | MH | VH | MH | H | MH | MH | H | MH | MH | MH | M | H | H | VH | MH | MH | MH | H | H |
| LTE Macrocell 4 | M | M | MH | M | MH | M | H | MH | VH | MH | MH | MH | MH | M | MH | MH | M | H | H | H | MH | MH | H | VH |
| LTE Macrocell 5 | M | M | M | ML | M | VH | M | MH | H | M | H | H | M | H | H | H | H | M | H | H | M | VH | M | H |
| LTE Macrocell 7 | H | M | MH | MH | H | VH | MH | MH | H | MH | MH | M | H | H | H | H | H | H | H | MH | H | MH | MH | MH |
| LTE Femtocell 25 | ML | H | M | MH | M | MH | H | M | H | VH | VH | H | M | H | MH | MH | H | H | H | MH | M | H | MH | H |
| WiMAX Macrocell 3 | M | M | VH | H | MH | VH | VH | H | MH | AH | M | VH | MH | AH | M | MH | MH | MH | H | H | MH | H | M | VH |
| WiMAX Macrocell 4 | MH | M | M | VH | M | H | VH | H | AH | M | H | M | M | AH | M | H | H | H | M | H | M | MH | MH | MH |
| WiMAX Macrocell 5 | M | MH | H | MH | H | H | H | H | H | VH | VH | H | H | MH | H | VH | MH | MH | MH | M | H | MH | MH | MH |
| WiMAX Macrocell 6 | MH | M | MH | H | H | MH | MH | MH | MH | MH | H | H | H | AH | VH | MH | MH | MH | VH | VH | H | MH | MH | H |
| WiMAX Macrocell 7 | ML | H | H | H | M | H | VH | H | VH | H | H | H | M | M | H | H | MH | M | M | H | M | MH | M | VH |
| WiMAX Macrocell 8 | MH | ML | MH | VH | M | MH | H | VH | VH | AH | M | H | M | VH | MH | VH | H | MH | MH | H | M | VH | MH | MH |
| Non-Disaster Management Services | Disaster Management Services | |||||||||||||||||||||||
| NAV | Web | Disaster-Aware NAV | ||||||||||||||||||||||
| Network | Throughput | Latency | Jitter | Packet Loss | Energy Consumption | Service Reliability | Security | Monetary Cost | Throughput | Latency | Jitter | Packet Loss | Energy Consumption | Service Reliability | Security | Monetary Cost | Throughput | Latency | Jitter | Packet Loss | Energy Consumption | Service Reliability | Security | Monetary Cost |
| WAVE 5 | M | H | ML | M | MH | MH | M | AH | H | M | M | MH | MH | H | M | AH | ML | ML | MH | H | MH | ML | M | VH |
| WAVE 8 | VL | M | M | MH | M | MH | H | AH | MH | MH | MH | M | M | MH | M | AH | ML | L | M | MH | M | M | L | AH |
| WAVE 18 | L | L | ML | MH | MH | H | VH | AH | ML | MH | M | H | MH | MH | MH | AH | M | ML | M | ML | MH | M | MH | VH |
| LTE FD-MIMO 1 | H | H | M | H | AL | M | MH | M | MH | MH | H | MH | AL | H | MH | M | H | M | H | H | AL | H | VH | VH |
| LTE FD-MIMO 3 | H | M | MH | MH | AL | M | M | M | H | MH | MH | H | AL | MH | H | H | H | H | H | MH | AL | M | H | VH |
| LTE FD-MIMO 4 | H | H | MH | H | AL | H | H | M | M | VH | M | MH | AL | MH | H | MH | MH | MH | M | H | AL | MH | H | MH |
| LTE Macrocell 3 | ML | M | L | ML | MH | ML | H | VH | M | M | H | M | MH | ML | M | VH | M | M | MH | M | MH | M | H | VH |
| LTE Macrocell 4 | L | L | M | ML | MH | L | MH | AH | L | MH | M | M | MH | M | M | AH | ML | MH | M | MH | MH | M | MH | AH |
| LTE Macrocell 5 | L | ML | ML | VL | M | MH | ML | AH | M | ML | MH | MH | M | MH | L | AH | MH | M | ML | ML | M | MH | M | VH |
| LTE Macrocell 8 | VL | ML | ML | ML | M | ML | H | AH | M | MH | M | H | M | ML | MH | VH | H | ML | L | ML | M | H | MH | VH |
| LTE Femtocell 4 | H | H | MH | H | MH | ML | ML | AH | H | ML | M | H | MH | MH | MH | AH | ML | M | M | M | MH | H | MH | VH |
| LTE Femtocell 16 | ML | M | M | M | MH | MH | ML | VH | MH | M | M | MH | MH | H | MH | VH | MH | L | M | L | MH | ML | MH | AH |
| LTE Femtocell 17 | MH | L | L | M | MH | ML | MH | AH | M | H | H | ML | MH | MH | ML | VH | MH | ML | ML | M | MH | M | L | AH |
| LTE Femtocell 44 | ML | MH | M | VL | MH | L | H | VH | ML | MH | L | ML | MH | ML | MH | AH | L | ML | MH | MH | MH | MH | H | VH |
| WiMAX Macrocell 1 | VL | ML | ML | M | M | MH | M | VH | MH | M | M | M | M | MH | ML | VH | ML | L | ML | M | M | ML | H | AH |
| WiMAX Macrocell 2 | M | L | MH | H | MH | ML | M | AH | MH | ML | MH | ML | MH | MH | MH | AH | L | H | M | MH | MH | M | L | VH |
| WiMAX Macrocell 4 | M | ML | ML | MH | M | MH | H | AH | MH | MH | ML | M | M | M | M | VH | H | H | M | M | M | L | ML | VH |
| WiMAX Macrocell 5 | ML | M | MH | ML | H | M | MH | VH | M | M | ML | ML | H | M | ML | VH | MH | M | MH | MH | H | M | ML | AH |
| WiMAX Macrocell 6 | M | L | M | M | H | ML | M | VH | M | M | H | H | H | M | ML | VH | M | M | M | H | H | M | M | AH |
| WiMAX Macrocell 7 | VL | MH | MH | M | M | MH | MH | AH | ML | ML | ML | M | M | M | ML | AH | L | MH | M | L | M | ML | M | VH |
| WiMAX Femtocell 3 | VL | M | MH | M | MH | M | M | AH | MH | M | M | H | MH | ML | M | VH | M | M | MH | ML | MH | MH | M | VH |
| WiMAX Femtocell 11 | ML | MH | ML | ML | MH | MH | ML | AH | MH | MH | ML | MH | MH | H | MH | AH | M | M | H | MH | MH | M | M | AH |
References
- Sami, H.; Mourad, A.; El-Hajj, W. Vehicular-OBUs-As-On-Demand-Fogs: Resource and Context Aware Deployment of Containerized Micro-Services. IEEE/ACM Trans. Netw. 2020, 28, 778–790. [Google Scholar] [CrossRef]
- Laghari, A.A.; Jumani, A.K.; Laghari, R.A. Review and State of Art of Fog Computing. Arch. Comput. Methods Eng. 2021, 28, 3631–3643. [Google Scholar] [CrossRef]
- Sun, W.; Wang, L.; Liu, J.; Kato, N.; Zhang, Y. Movement Aware CoMP Handover in Heterogeneous Ultra-Dense Networks. IEEE Trans. Commun. 2020, 69, 340–352. [Google Scholar] [CrossRef]
- Haroon, M.S.; Muhammad, F.; Abbas, G.; Abbas, Z.H.; Hassan, A.K.; Waqas, M.; Kim, S. Interference Management in Ultra-dense 5G Networks with Excessive Drone Usage. IEEE Access 2020, 8, 102155–102164. [Google Scholar] [CrossRef]
- Skondras, E.; Michalas, A.; Vergados, D.J.; Michailidis, E.T.; Miridakis, N.I.; Vergados, D.D. Network Slicing on 5G Vehicular Cloud Computing Systems. Electronics 2021, 10, 1474. [Google Scholar] [CrossRef]
- Skondras, E.; Michalas, A.; Vergados, D.J.; Michailidis, E.T.; Miridakis, N.I. A Network Slicing Algorithm for 5G Vehicular Networks. In Proceedings of the 2021 12th International Conference on Information, Intelligence, Systems and Applications (IISA), Chania Crete, Greece, 12–14 July 2021; pp. 1–7. [Google Scholar]
- 609.3-2016—IEEE Standard for Wireless Access in Vehicular Environments (WAVE)—Networking Services. Available online: https://ieeexplore.ieee.org/document/7458115 (accessed on 28 February 2022).
- TS 36.305 (V16.1.0): LTE. Evolved Universal Terrestrial Radio Access Network (E-UTRAN). In Stage 2 Functional Specification of User Equipment (UE) Positioning in E-UTRAN (Rel.16); Technical Specification, 3GPP: Edinburgh, UK, 2020. [Google Scholar]
- P802.16/D4; IEEE Draft Standard for Air Interface for Broadband Wireless Access Systems (Revision of IEEE Std 802.16-2012). IEEE Standard; IEEE: Piscataway, NJ, USA, 2017; Volume 1, pp. 1–3534.
- Speicher, S.; Sirotkin, S.; Palat, S.; Davydov, A. 5G System Overview. In 5G Radio Access Network Architecture: The Dark Side of 5G; Wiley Online Library: Hoboken, NJ, USA, 2021; pp. 37–122. [Google Scholar]
- Bruschi, R.; Pajo, J.F.; Davoli, F.; Lombardo, C. Managing 5G Network Slicing and Edge Computing with the MATILDA Telecom Layer Platform. In Computer Networks; Elsevier: Amsterdam, The Netherlands, 2021; p. 108090. [Google Scholar]
- Palas, M.R.; Islam, M.R.; Roy, P.; Razzaque, M.A.; Alsanad, A.; AlQahtani, S.A.; Hassan, M.M. Multi-criteria handover mobility management in 5G cellular network. Comput. Commun. 2021, 174, 81–91. [Google Scholar] [CrossRef]
- Hu, T.; Zhang, Z.; Yi, P.; Liang, D.; Li, Z.; Ren, Q.; Hu, Y.; Lan, J. SEAPP: A secure application management framework based on REST API access control in SDN-enabled cloud environment. J. Parallel Distrib. Comput. 2021, 147, 108–123. [Google Scholar] [CrossRef]
- Dalla-Costa, A.G.; Bondan, L.; Wickboldt, J.A.; Both, C.B.; Granville, L.Z. Orchestra: A Customizable Split-Aware NFV Orchestrator for Dynamic Cloud Radio Access Networks. IEEE J. Sel. Areas Commun. 2020, 38, 1014–1024. [Google Scholar] [CrossRef]
- Guan, J.; Sharma, V.; You, I.; Atiquzzaman, M.; Imran, M. Extension of MIH for FPMIPv6 (EMIH-FPMIPv6) to support optimized heterogeneous handover. Future Gener. Comput. Syst. 2019, 97, 775–791. [Google Scholar] [CrossRef]
- Alfoudi, A.S.D.; Newaz, S.S.; Ramlie, R.; Lee, G.M.; Baker, T. Seamless mobility management in heterogeneous 5G networks: A coordination approach among distributed sdn controllers. In Proceedings of the 2019 IEEE 89th Vehicular Technology Conference (VTC2019-Spring), Kuala Lumpur, Malaysia, 28 April–1 May 2019; pp. 1–6. [Google Scholar]
- Lahby, M.; Leghris, C.; Adib, A. New multi access selection method based on Mahalanobis distance. Appl. Math. Sci. 2012, 6, 2745–2760. [Google Scholar]
- Martinez, I.; Ramos, V. NetANPI: A network selection mechanism for LTE traffic offloading based on the Analytic Network Process. In Proceedings of the 2015 36th IEEE Sarnoff Symposium, Newark, NJ, USA, 20–22 September 2015; pp. 117–122. [Google Scholar]
- Lassoued, I.; Bonnin, J.M.; Ben Hamouda, Z.; Belghith, A. A methodology for evaluating vertical handoff decision mechanisms. In Proceedings of the Seventh International Conference on Networking (ICN 2008), Cancun, Mexico, 13–18 April 2008; pp. 377–384. [Google Scholar]
- Roszkowska, E.; Kacprzak, D. The fuzzy saw and fuzzy TOPSIS procedures based on ordered fuzzy numbers. Inf. Sci. 2016, 369, 564–584. [Google Scholar] [CrossRef]
- Kaur, S.; Sehra, S.K.; Sehra, S.S. A framework for software quality model selection using TOPSIS. In Proceedings of the IEEE International Conference on Recent Trends in Electronics, Information and Communication Technology (RTEICT), Bengaluru, India, 20–21 May 2016; pp. 736–739. [Google Scholar]
- TS 36.839 Version 11.1.0: Mobility Enhancements in Heterogeneous Networks (Release 11); Technical Specification; 3GPP: Edinburgh, UK, 2012.
- Skondras, E.; Michalas, A.; Vergados, D.D. Mobility management on 5g vehicular cloud computing systems. Veh. Commun. 2019, 16, 15–44. [Google Scholar] [CrossRef]
- Pacheco, L.; Medeiros, I.; Santos, H.; Oliveira, H.; Rosário, D.; Cerqueira, E.; Neto, A. A Handover Algorithm for Video Sharing over Vehicular Networks. In Proceedings of the 2019 9th IEEE Latin-American Symposium on Dependable Computing (LADC), Natal, Brazil, 19–21 November 2019; pp. 1–9. [Google Scholar]
- 300 (V13.7.0): Evolved Universal Terrestrial Radio Access Network (E-UTRAN) (Rel.13); Technical Specification; 3GPP: Edinburgh, UK, 2017.
- Poolnisai, P.; Punchalard, R. Handover Trigger Point for high-velocity mobiles. In Proceedings of the 2019 7th IEEE International Electrical Engineering Congress (iEECON), Hua Hin, Thailand, 6–8 March 2019; pp. 1–4. [Google Scholar]
- Aghabozorgi, S.; Bayati, A.; Nguyen, K.k.; Despins, C.; Cheriet, M. Toward predictive handover mechanism in software-defined enterprise Wi-Fi networks. In Proceedings of the 2019 IEEE Sustainability through ICT Summit (StICT), Montreal, QC, Canada, 18–19 June 2019; pp. 1–6. [Google Scholar]
- Michalas, A.; Sgora, A.; Vergados, D.D. An integrated MIH-FPMIPv6 mobility management approach for evolved-packet system architectures. J. Netw. Comput. Appl. 2017, 91, 104–119. [Google Scholar] [CrossRef]
- TS 24.302 (V14.3.0): Access to the 3GPP Evolved Packet Core (EPC) via non-3GPP Access Networks (Rel.14); Technical Specification, 3GPP: Edinburgh, UK, 2017.
- Smida, E.B.; Fantar, S.G.; Youssef, H. Predictive handoff mechanism for video streaming in a cloud-based urban vanet. In Proceedings of the 2017 IEEE/ACS 14th International Conference on Computer Systems and Applications (AICCSA), Hammamet, Tunisia, 30 October–3 November 2017; pp. 1170–1177. [Google Scholar]
- Dalla Cia, M.; Mason, F.; Peron, D.; Chiariotti, F.; Polese, M.; Mahmoodi, T.; Zorzi, M.; Zanella, A. Mobility-aware handover strategies in smart cities. In Proceedings of the 2017 IEEE International Symposium on Wireless Communication Systems (ISWCS), Bologna, Italy, 28–31 August 2017; pp. 438–443. [Google Scholar]
- Kumar, H.; Singh, M.K.; Gupta, M.; Madaan, J. Moving towards smart cities: Solutions that lead to the smart city transformation framework. Technol. Forecast. Soc. Chang. 2020, 153, 119281. [Google Scholar] [CrossRef]
- Kapoor, S.; Grace, D.; Clarke, T. A base station selection scheme for handover in a mobility-aware ultra-dense small cell urban vehicular environment. In Proceedings of the 2017 IEEE 28th Annual International Symposium on Personal, Indoor, and Mobile Radio Communications (PIMRC), Montreal, QC, Canada, 8–13 October 2017; pp. 1–5. [Google Scholar]
- Brahim, M.B.; Mir, Z.H.; Znaidi, W.; Filali, F.; Hamdi, N. QoS-aware video transmission over hybrid wireless network for connected vehicles. IEEE Access 2017, 5, 8313–8323. [Google Scholar] [CrossRef]
- Arshad, R.; ElSawy, H.; Sorour, S.; Al-Naffouri, T.Y.; Alouini, M.S. Velocity-aware handover management in two-tier cellular networks. IEEE Trans. Wirel. Commun. 2017, 16, 1851–1867. [Google Scholar] [CrossRef] [Green Version]
- Sambuc, R. Fonctions and Floues: Application a L’aide au Diagnostic en Pathologie Thyroidienne; Faculté de Médecine de Marseille: Marseille, France, 1975. [Google Scholar]
- Ashtiani, B.; Haghighirad, F.; Makui, A.; ali Montazer, G. Extension of fuzzy TOPSIS method based on interval-valued fuzzy sets. Appl. Soft Comput. 2009, 9, 457–461. [Google Scholar] [CrossRef]
- Raju, V.; Jayagopal, R. An Arithmetic Operations of Icosagonal fuzzy number using Alpha cut. Int. J. Pure Appl. Math. 2018, 120, 137–145. [Google Scholar]
- Cintra, M.E.; Camargo, H.A.; Monard, M.C. Genetic generation of fuzzy systems with rule extraction using formal concept analysis. Inf. Sci. 2016, 349, 199–215. [Google Scholar] [CrossRef]
- Skondras, E.; Michailidis, E.T.; Michalas, A.; Vergados, D.J.; Miridakis, N.I.; Vergados, D.D. A network slicing framework for uav-aided vehicular networks. Drones 2021, 5, 70. [Google Scholar] [CrossRef]
- Skondras, E.; Zoumi, E.; Michalas, A.; Vergados, D.D. A Network Selection Algorithm for supporting Drone Services in 5G Network Architectures. In Proceedings of the 2019 IEEE Wireless Telecommunications Symposium (WTS), New York, NY, USA, 9–12 April 2019; pp. 1–6. [Google Scholar]
- Iqbal, J.; Khan, M.; Afaq, M.; Ali, A. Performance analysis of vertical handover techniques based on IEEE 802.21: Media independent handover standard. Trans. Emerg. Telecommun. Technol. 2019, 32, e3695. [Google Scholar] [CrossRef]
- Praptodiyono, S.; Firmansyah, T.; Alaydrus, M.; Santoso, M.I.; Osman, A.; Abdullah, R. Mobile IPv6 Vertical Handover Specifications, Threats, and Mitigation Methods: A Survey. Secur. Commun. Netw. 2020, 2020, 5429630. [Google Scholar] [CrossRef]
- Skondras, E.; Michalas, A.; Sgora, A.; Vergados, D.D. A Vertical Handover management scheme for VANET Cloud Computing systems. In Proceedings of the 2017 IEEE Symposium on Computers and Communications (ISCC), Heraklion, Greece, 3–6 July 2017; pp. 371–376. [Google Scholar]
- Kosmopoulos, I.; Skondras, E.; Michalas, A.; Vergados, D.D. An Efficient Mobility Management Scheme for 5G Network Architectures. In Proceedings of the 2020 5th South-East Europe Design Automation, Computer Engineering, Computer Networks and Social Media Conference (SEEDA-CECNSM), Corfu, Greece, 25–27 September 2020; pp. 1–6. [Google Scholar]
- Lee, J.W.; Yoo, S.J. Probabilistic Path and Data Capacity Based Handover Decision for Hierarchical Macro-and Femtocell Networks. Mob. Inf. Syst. 2016, 2016. [Google Scholar] [CrossRef]
- Merwaday, A.; Güvenç, I. Handover count based velocity estimation and mobility state detection in dense HetNets. IEEE Trans. Wirel. Commun. 2016, 15, 4673–4688. [Google Scholar] [CrossRef]
- Bi, Y.; Zhou, H.; Xu, W.; Shen, X.S.; Zhao, H. An efficient PMIPv6-based handoff scheme for urban vehicular networks. IEEE Trans. Intell. Transp. Syst. 2016, 17, 3613–3628. [Google Scholar] [CrossRef]
- Network Simulator 3 (NS3). Available online: https://www.nsnam.org/ (accessed on 15 January 2022).
- Hellenic Telecommunications and Post Commission (EETT). 2021. Available online: http://keraies.eett.gr/ (accessed on 18 January 2022).
- Su, G.; You, P.; Yong, S. Comparative Handover Performance Analysis of MIPv6 and FMIPv6 in LEO Satellite Networks. In Proceedings of the 2017 IEEE International Conference on Network and Information Systems for Computers (ICNISC), Shanghai, China, 14–16 April 2017; pp. 30–36. [Google Scholar]
- Zhang, L.; Tian, Y.C. An enhanced fast handover triggering mechanism for Fast Proxy Mobile IPv6. Wirel. Netw. 2018, 24, 513–522. [Google Scholar] [CrossRef] [Green Version]
- Goyal, R.K.; Kaushal, S.; Sangaiah, A.K. The utility based non-linear fuzzy AHP optimization model for network selection in heterogeneous wireless networks. Appl. Soft Comput. 2017, 67, 800–811. [Google Scholar] [CrossRef]
- Charilas, D.E.; Markaki, O.I.; Psarras, J.; Constantinou, P. Application of fuzzy AHP and ELECTRE to network selection. In Mobile Lightweight Wireless Systems; Springer: Berlin/Heidelberg, Germany, 2009; pp. 63–73. [Google Scholar]
- Sharma, V.; Guan, J.; Kim, J.; Kwon, S.; You, I.; Palmieri, F.; Collotta, M. MIH-SPFP: MIH-based secure cross-layer handover protocol for Fast Proxy Mobile IPv6-IoT networks. J. Netw. Comput. Appl. 2019, 125, 67–81. [Google Scholar] [CrossRef]


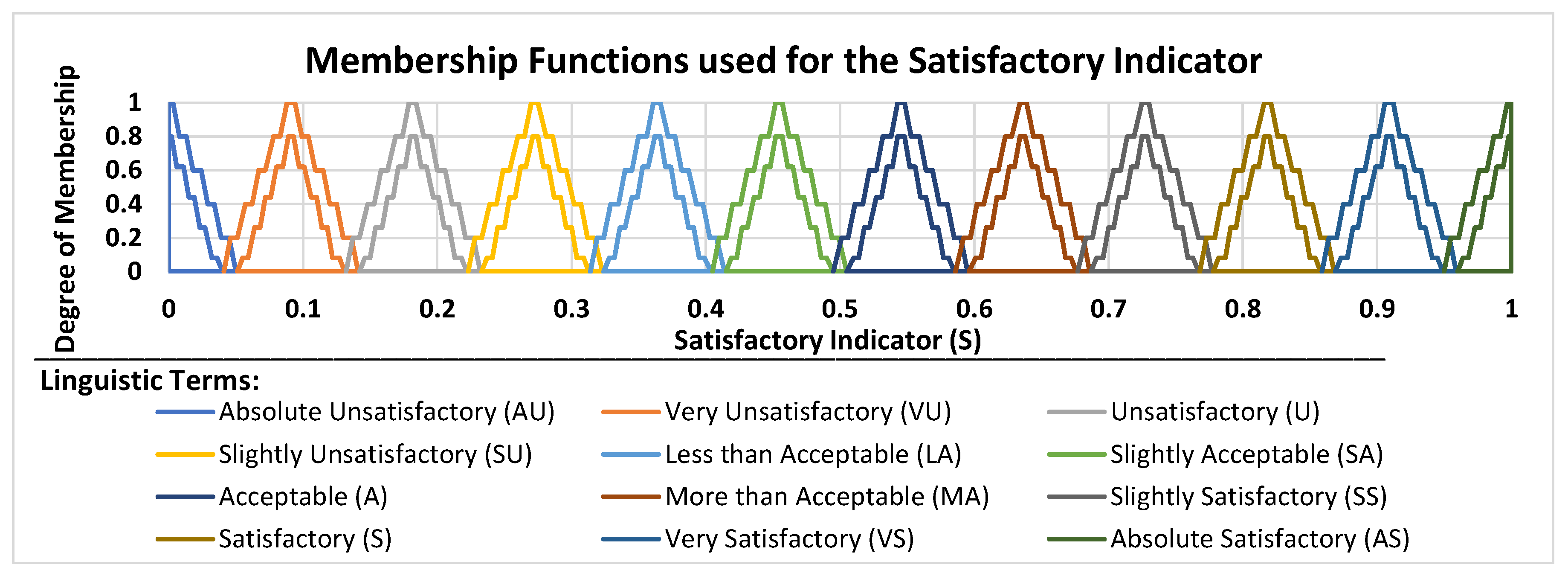

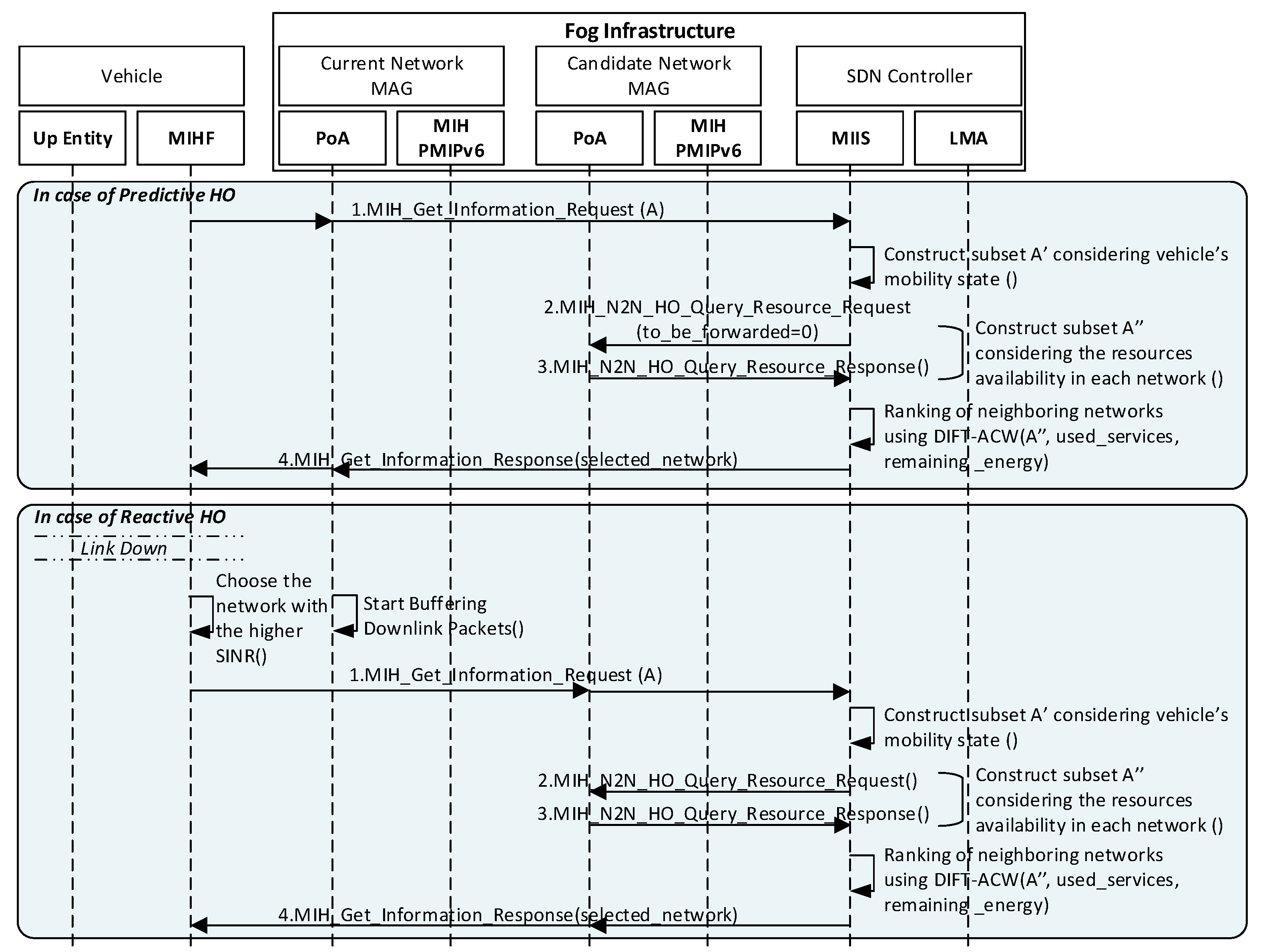
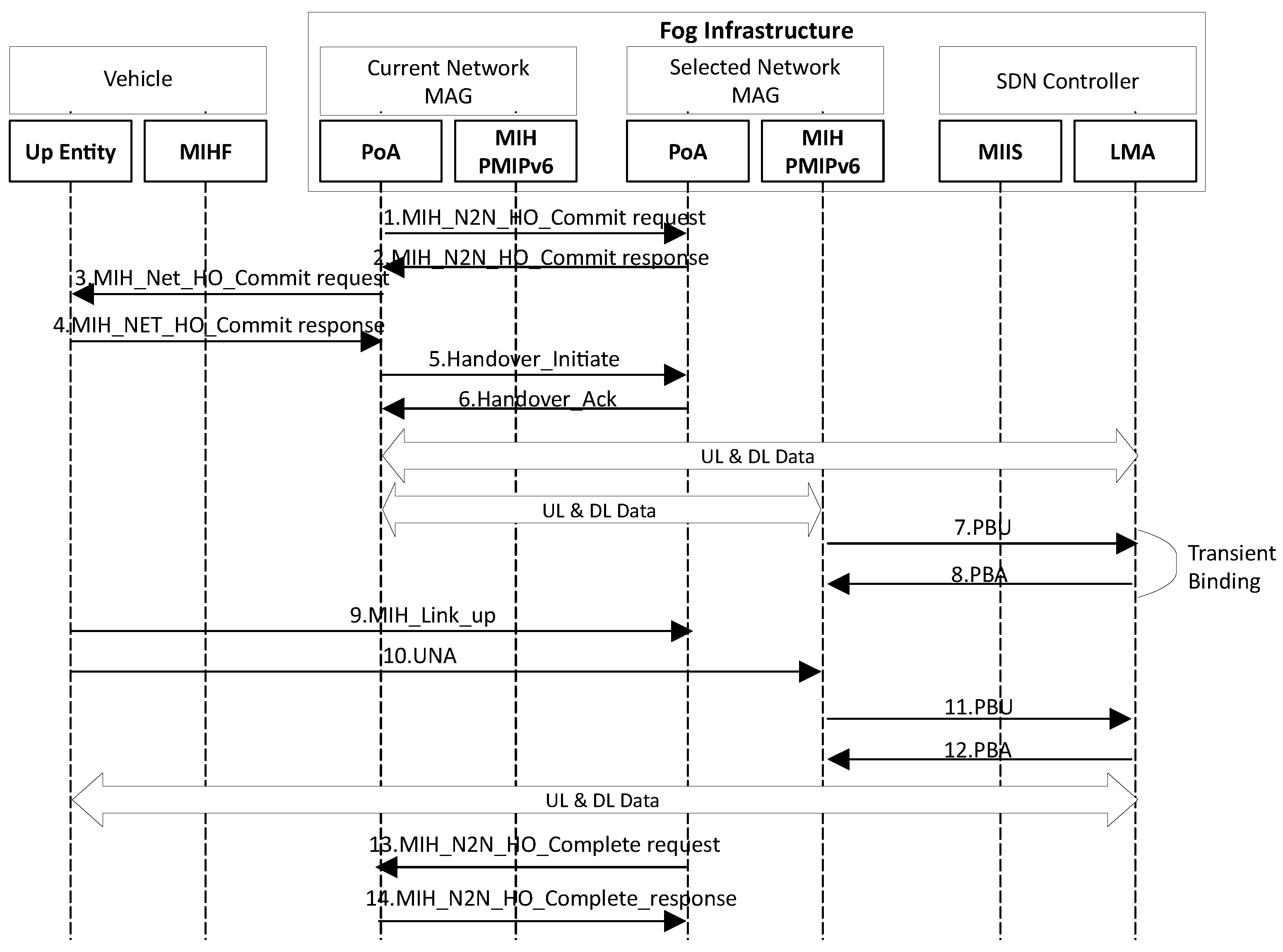
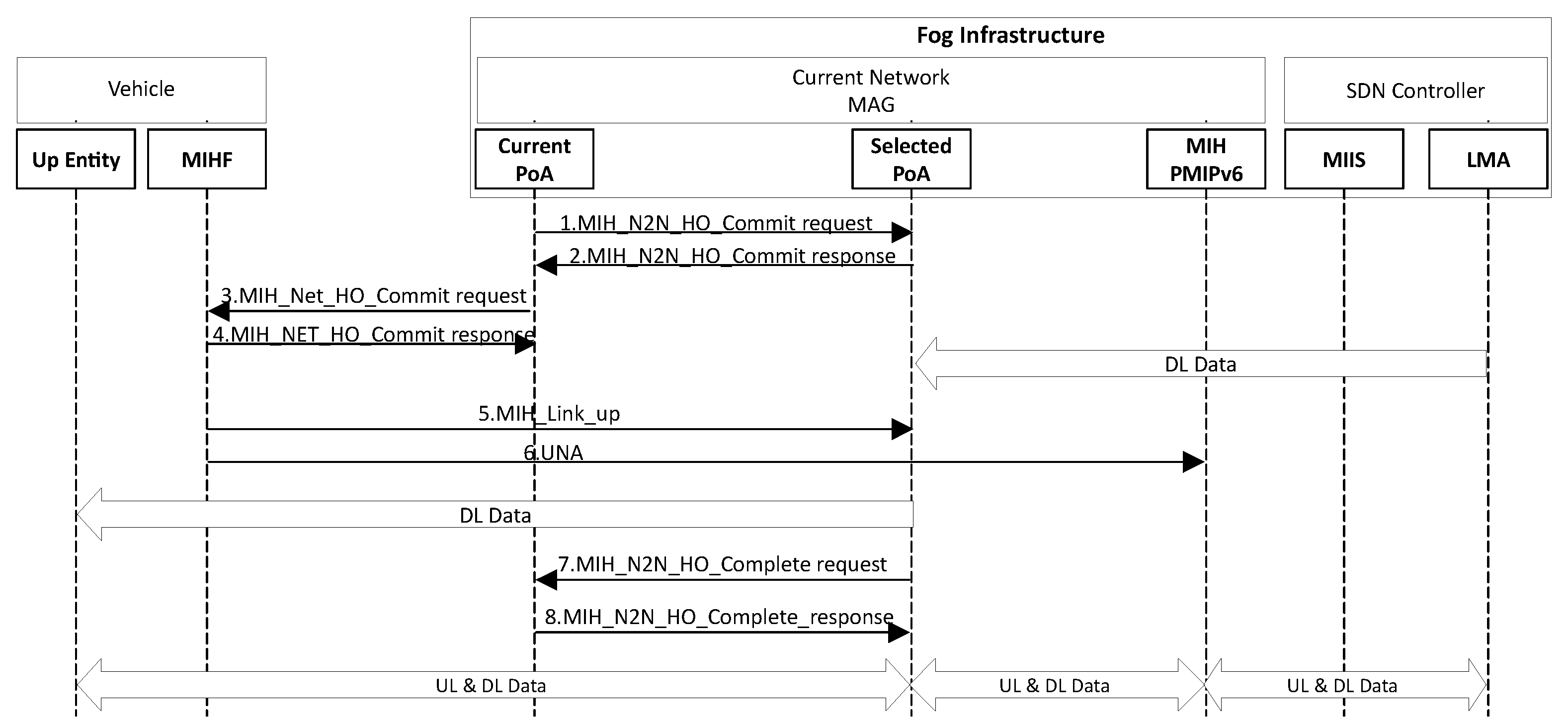



| Parameter | Value |
|---|---|
| Simulation duration | 86,400 s (24 h) |
| Network count | WAVE RSUs: 28 LTE-A Pro FD-MIMO Macrocell BSs: 5 LTE-A Macrocell BSs: 8 LTE-A Femtocell BSs: 70 WiMAX Macrocell BSs: 8 WiMAX Femtocell BSs: 41 Total: 160 |
| Cell radius | WAVE RSUs: 150 m LTE-A Pro FD-MIMO Macrocells: 320 m LTE-A/WiMAX Macrocells: 400 m LTE/WiMAX Femtocells: 30 m |
| Networks positions | According to the Hellenic Telecommunications and Post Commission (EETT) [50] data (see Appendix A) |
| Networks frequencies | See Appendix A |
| Service Layer Agreement (SLA) count | 3 |
| HO initiation threshold per SLA | : (: , : ) : : , : ) : (: , : ) |
| Vehicle count | 77,797 |
| Average arrival rate of vehicles | 0.900428241 vehicles/second |
| Average departure rate of vehicles | 0.895439815 vehicles/s |
| Vehicles per SLA | SLA1: 25,933 vehicles (33.3342%) SLA2: 25,932 vehicles (33.3329%) SLA3: 25,932 vehicles (33.3329%) |
| Services | Navigation Assistance (NAV) Voice over IP (VoIP) Conversational Video (CV) Buffered Streaming (BS) Web Browsing (WB) |
| Vehicles per velocity | Normal: 25,933 vehicles (33.3342%) Medium: 25,932 vehicles (33.3329%) High: 25,932 vehicles (33.3329%) |
| Vehicular User | SLA | Services | Current Position (Latitude, Longitude) | Velocity | Disaster Severity Level | Remaining Energy |
|---|---|---|---|---|---|---|
| 1 | 1 | NAV, VoIP, IT-EM | 37.984459, 23.728205 | Normal | Elevated | 80% |
| 2 | 1 | CV, Web | 37.981693, 23.734297 | High | Low or No | 95% |
| 3 | 1 | BS, Web, DA-NAV, LVS-EM | 37.982949, 23.725033 | Normal | Severe | 4% |
| 4 | 1 | NAV, CV, DA-VoIP | 37.986155, 23.728610 | Medium | Elevated | 55% |
| 5 | 2 | Web, DA-NAV, DA-VoIP | 37.983713, 23.727900 | High | High | 12% |
| 6 | 2 | NAV, Web, IT-EM | 37.981198, 23.732510 | Normal | Guarded | 100% |
| 7 | 2 | VoIP, Web, DA-NAV, IT-EM | 37.985405, 23.721205 | Medium | Severe | 72% |
| 8 | 3 | DA-NAV | 37.984896, 23.731628 | High | Guarded | 60% |
| 9 | 3 | Web, DA-NAV | 37.982396, 23.725600 | Medium | High | 7% |
| 10 | 3 | NAV, Web | 37.986878, 23.734662 | High | Low or No | 58% |
| Vehicle | The PoAs That Provide Network Coverage in the Current Location |
|---|---|
| 1 | WAVE 11, LTE-A Pro FD-MIMO Macrocell 3, LTE Macrocell 1, LTE Macrocell 4, WiMAX Macrocell 4, WiMAX Macrocell 5, WiMAX Macrocell 6, WiMAX Femtocell 13 |
| 2 | WAVE 17, WAVE 19, WAVE 21, LTE-A Pro FD-MIMO Macrocell 4, LTE Macrocell 3, LTE Macrocell 4, LTE Macrocell 7, LTE Femtocell 53, WiMAX Macrocell 8 |
| 3 | WAVE 13, WAVE 18, LTE-A Pro FD-MIMO Macrocell 3, LTE Macrocell 2, LTE Macrocell 5, LTE Femtocell 30, LTE Femtocell 38, WiMAX Macrocell 3, WiMAX Macrocell 4, WiMAX Macrocell 5, WiMAX Macrocell 6, WiMAX Macrocell 7, WiMAX Femtocell 17 |
| 4 | WAVE 1, WAVE 7, LTE-A Pro FD-MIMO Macrocell 3, LTE Macrocell 1, WiMAX Macrocell 1, WiMAX Macrocell 4, WiMAX Macrocell 5 |
| 5 | WAVE 11, WAVE 15, LTE-A Pro FD-MIMO Macrocell 3, LTE Macrocell 1, LTE Macrocell 4, LTE Macrocell 5, LTE Femtocell 25, WiMAX Macrocell 4, WiMAX Macrocell 5, WiMAX Macrocell 6 |
| 6 | WAVE 20, WAVE 27, LTE-A Pro FD-MIMO Macrocell 4, LTE Macrocell 3, LTE Macrocell 4, LTE Macrocell 7, WiMAX Macrocell 8 |
| 7 | WAVE 6, LTE-A Pro FD-MIMO Macrocell 2, LTE Macrocell 2, WiMAX Macrocell 3, WiMAX Macrocell 7 |
| 8 | WAVE 8, LTE-A Pro FD-MIMO Macrocell 1, LTE Macrocell 3, LTE Macrocell 4, LTE Femtocell 16, LTE Femtocell 17, WiMAX Macrocell 1, WiMAX Macrocell 2, WiMAX Macrocell 5, WiMAX Femtocell 11 |
| 9 | WAVE 18, LTE-A Pro FD-MIMO Macrocell 3, LTE Macrocell 5, LTE Macrocell 8, LTE Femtocell 44, WiMAX Macrocell 4, WiMAX Macrocell 5, WiMAX Macrocell 6, WiMAX Macrocell 7 |
| 10 | WAVE 5, LTE-A Pro FD-MIMO Macrocell 1, LTE Macrocell 3, LTE Femtocell 4, WiMAX Macrocell 1, WiMAX Macrocell 2, WiMAX Femtocell 3 |
| Vehicle | Current PoA i | () | Handover Required | |||
|---|---|---|---|---|---|---|
| 1 | WiMAX Femtocell 13 | 0.778401 | 0.15 (−4.75 dB) | 0.090777 | 0.81843 | Yes |
| 2 | LTE Macrocell 4 | 0.703974 | 0.07 (−7.55 dB) | 0.062243 | 0.81843 | Yes |
| 3 | WiMAX Macrocell 5 | 0.781015 | 0.28 (−0.2 dB) | 0.16270 | 0.81843 | Yes |
| 4 | WiMAX Macrocell 4 | 0.825158 | 0.18 (−3.7 dB) | 0.14235 | 0.81843 | Yes |
| 5 | LTE Macrocell 5 | 0.630301 | 0.01 (−9.65 dB) | 0.024904 | 0.63642 | Yes |
| 6 | LTE Macrocell 7 | 0.982691 | 0.82 (18.7 dB) | 0.97462 | 0.63642 | No |
| 7 | WiMAX Macrocell 7 | 0.806098 | 0.04 (−8.6 dB) | 0.025393 | 0.63642 | Yes |
| 8 | LTE Femtocell 16 | 0.686169 | 0.31 (0.85 dB) | 0.18159 | 0.45457 | Yes |
| 9 | LTE Femtocell 44 | 0.72937 | 0.32 (1.2 dB) | 0.18158 | 0.45457 | Yes |
| 10 | LTE Macrocell 3 | 0.868325 | 0.03 (−8.95 dB) | 0.025203 | 0.45457 | Yes |
| Vehicle | Selected Network |
|---|---|
| 1 | LTE-A Pro FD-MIMO Macrocell 3 |
| 2 | LTE-A Pro FD-MIMO Macrocell 4 |
| 3 | LTE-A Pro FD-MIMO Macrocell 3 |
| 4 | WiMAX Macrocell 5 |
| 5 | WiMAX Macrocell 6 |
| 6 | LTE Macrocell 7 |
| 7 | LTE-A Pro FD-MIMO Macrocell 2 |
| 8 | LTE-A Pro FD-MIMO Macrocell 1 |
| 9 | WiMAX Macrocell 5 |
| 10 | WAVE 5 |
| Communicating Components | Number of Hops |
|---|---|
| 1 | |
| 1 | |
| 1 | |
| 2 |
| Message Name | Size (Bytes) | Abbreviation |
|---|---|---|
| MIH_Link_Going_down | 78 | |
| MIH_GET_Information_request | 1500 | |
| MIH_GET_Information_response | 1500 | |
| MIH_Net_HO_Candidate_Query_request | 63 + 11·n + 8·m·n | |
| MIH_Net_HO_Candidate_Query_response | 77 + 101·m | |
| MIH_N2N_HO_Query_Resource_request | 150 + 11·m | |
| MIH_N2N_HO_Query_Resource_response | 165 | |
| MIH_N2N_HO_Commit_request | 213 | |
| MIH_N2N_HO_Commit_request (Extended) | 264 | |
| MIH_N2N_HO_Commit_response | 92 | |
| MIH_N2N_HO_Commit_response (Extended) | 92 | |
| MIH_Net_HO_Commit_request | 122 | |
| MIH_Net_HO_Commit_response | 103 | |
| Handover_Initiate | 72 | |
| Handover_Ack | 32 | |
| PBU | 76 | |
| PBA | 52 | |
| MIH_Link_up | 95 | |
| UNA | 52 | |
| MIH_N2N_HO_Complete_request | 109 | |
| MIH_N2N_HO_Complete_response | 112 | |
| RS | 16 | |
| RA | 64 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kosmopoulos, I.; Skondras, E.; Michalas, A.; Michailidis, E.T.; Vergados, D.D. Handover Management in 5G Vehicular Networks. Future Internet 2022, 14, 87. https://doi.org/10.3390/fi14030087
Kosmopoulos I, Skondras E, Michalas A, Michailidis ET, Vergados DD. Handover Management in 5G Vehicular Networks. Future Internet. 2022; 14(3):87. https://doi.org/10.3390/fi14030087
Chicago/Turabian StyleKosmopoulos, Ioannis, Emmanouil Skondras, Angelos Michalas, Emmanouel T. Michailidis, and Dimitrios D. Vergados. 2022. "Handover Management in 5G Vehicular Networks" Future Internet 14, no. 3: 87. https://doi.org/10.3390/fi14030087
APA StyleKosmopoulos, I., Skondras, E., Michalas, A., Michailidis, E. T., & Vergados, D. D. (2022). Handover Management in 5G Vehicular Networks. Future Internet, 14(3), 87. https://doi.org/10.3390/fi14030087