Securing Wireless Sensor Networks Using Machine Learning and Blockchain: A Review
Abstract
1. Introduction
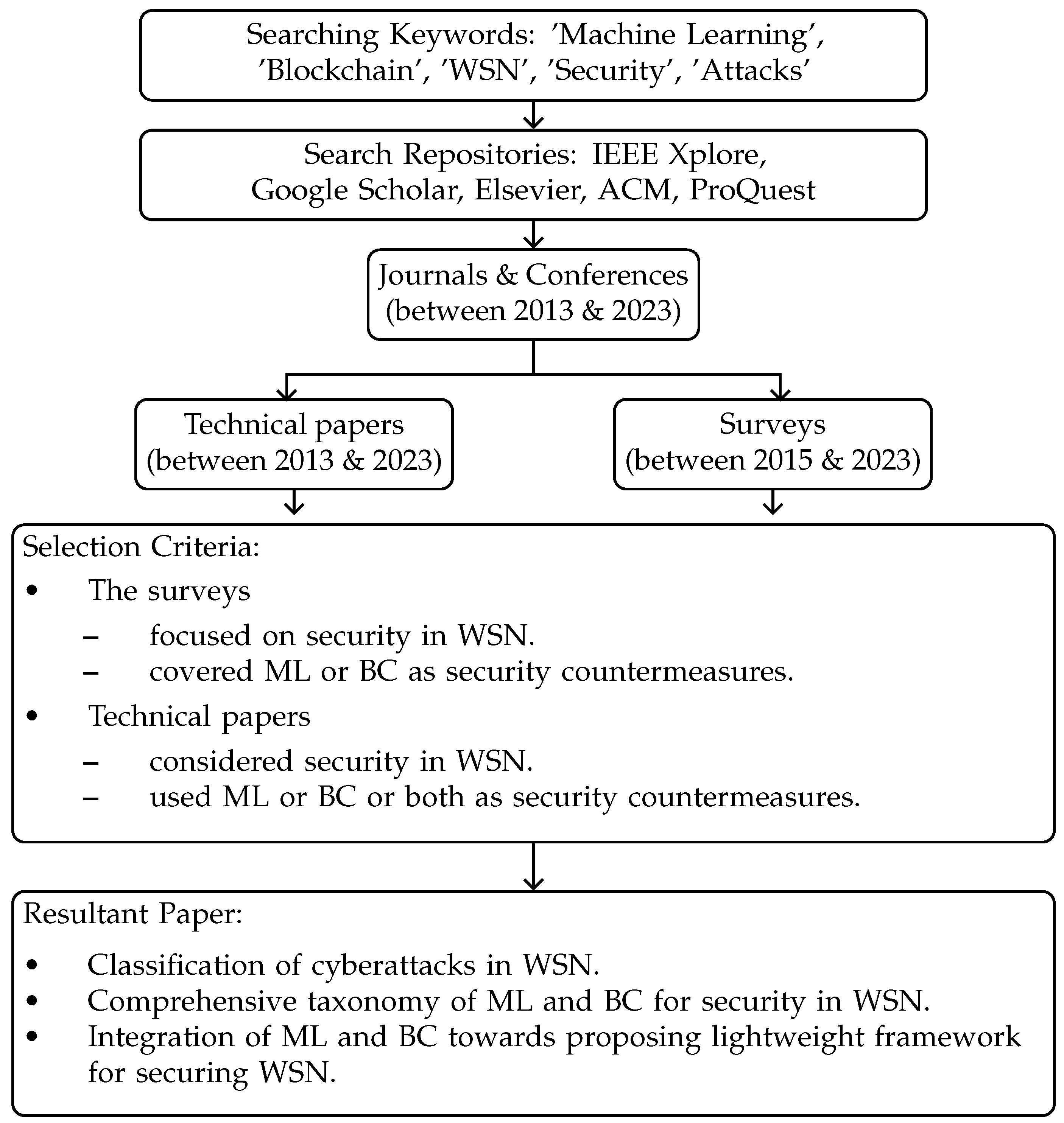
2. Existing Surveys on ML and BC in WSN
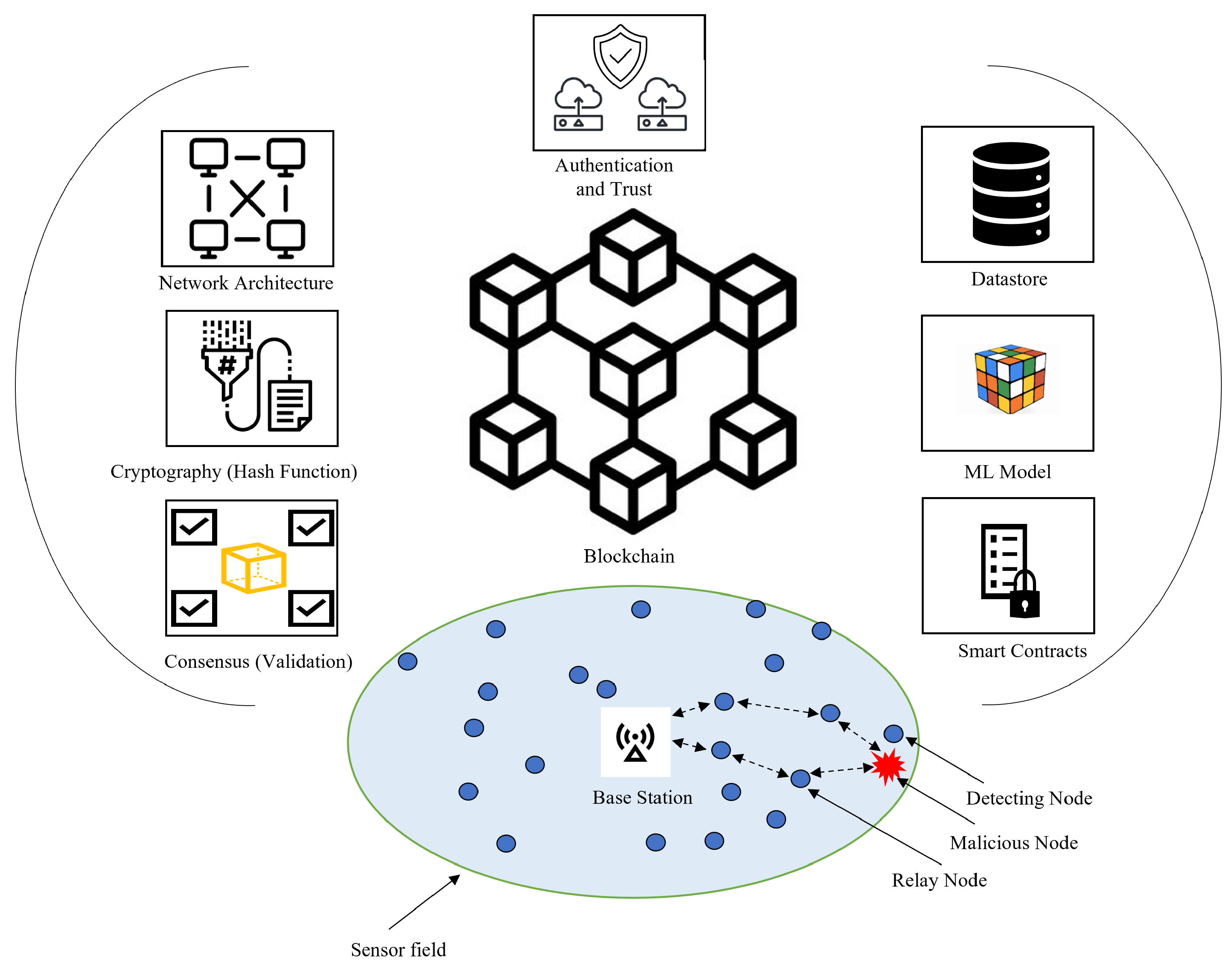
3. WSN Security Requirements
- Integrity: transmitted messages cannot be tampered with due to illegal actions when moving from one node to the other.
- Availability: legitimate (and authenticated) nodes can effectively access the network/provided services.
- Scalability: the network should be able to cope with increases in size and to adapt to the dynamic addition and removal of various nodes, and node functionalities must be incorporated with sensor nodes for every service without affecting the network’s security level.
- Mutual Authentication: the identities of any pair of nodes engaged in communication must be recognized before they interact.
- Non-repudiation: the nodes cannot deny the implemented operations or alter the messages they send.
- Confidentiality: the privacy of sensitive data transmitted over the network medium must be preserved by ensuring that any intruder or other neighboring network intercepting the communication channels cannot obtain any confidential information.
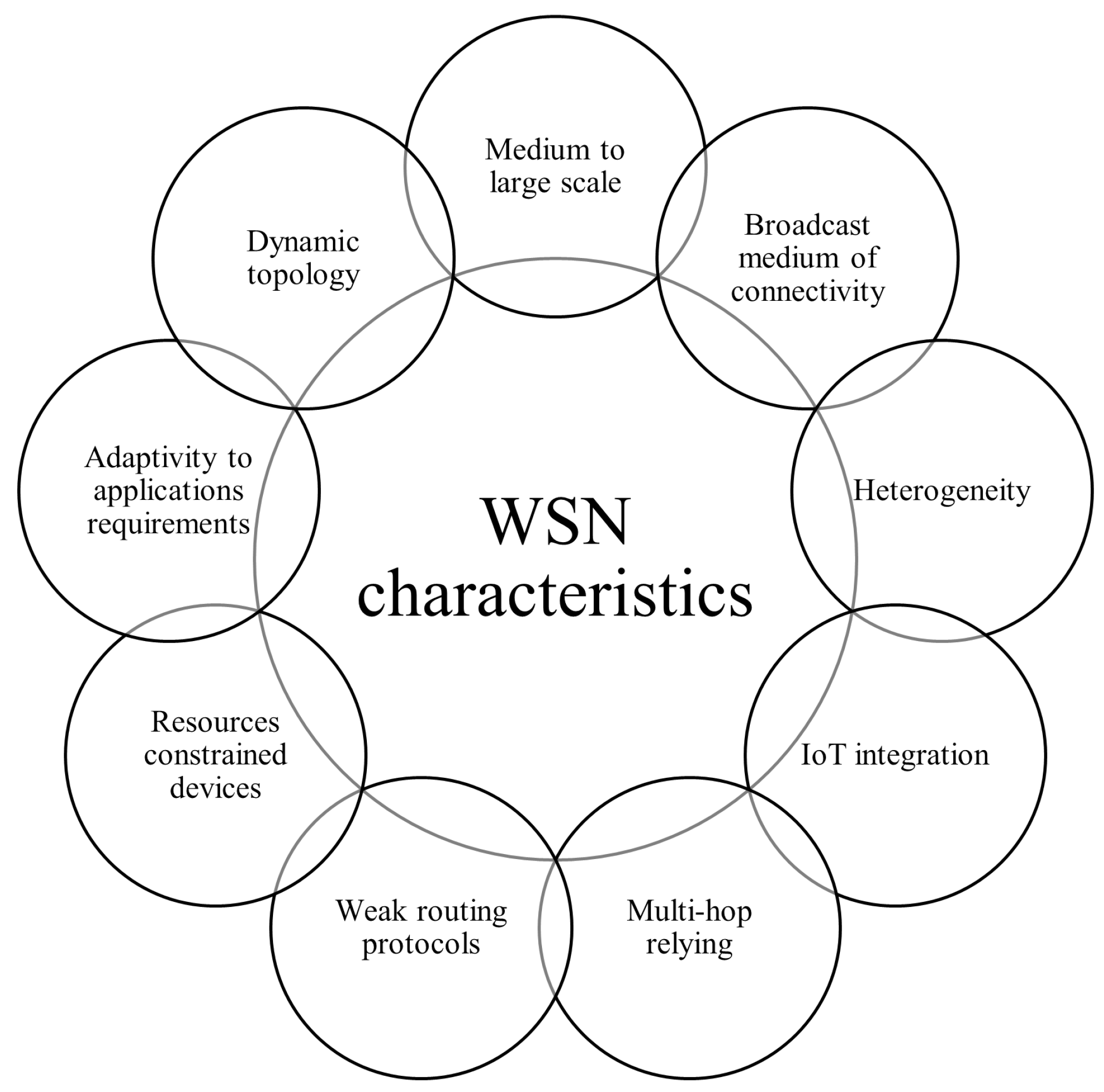
4. WSN Design Challenges and Unique Characteristics
- WSNs can be used in a wide range of applications with different security requirements; however, they must be able to ensure privacy, confidentiality, integrity, freshness, and authentication.
- Sensor nodes must be heterogeneous in terms of fabrication and energy-saving strategies, such as sleep, idle, and wake-up modes, which dictates the need to provide different underlying network architectures for the different heterogeneous applications.
- WSNs have many appealing applications, creating a need for different levels of secure functionalities and service requirements, such as secure node selection, data aggregation [36], localization, and routing.
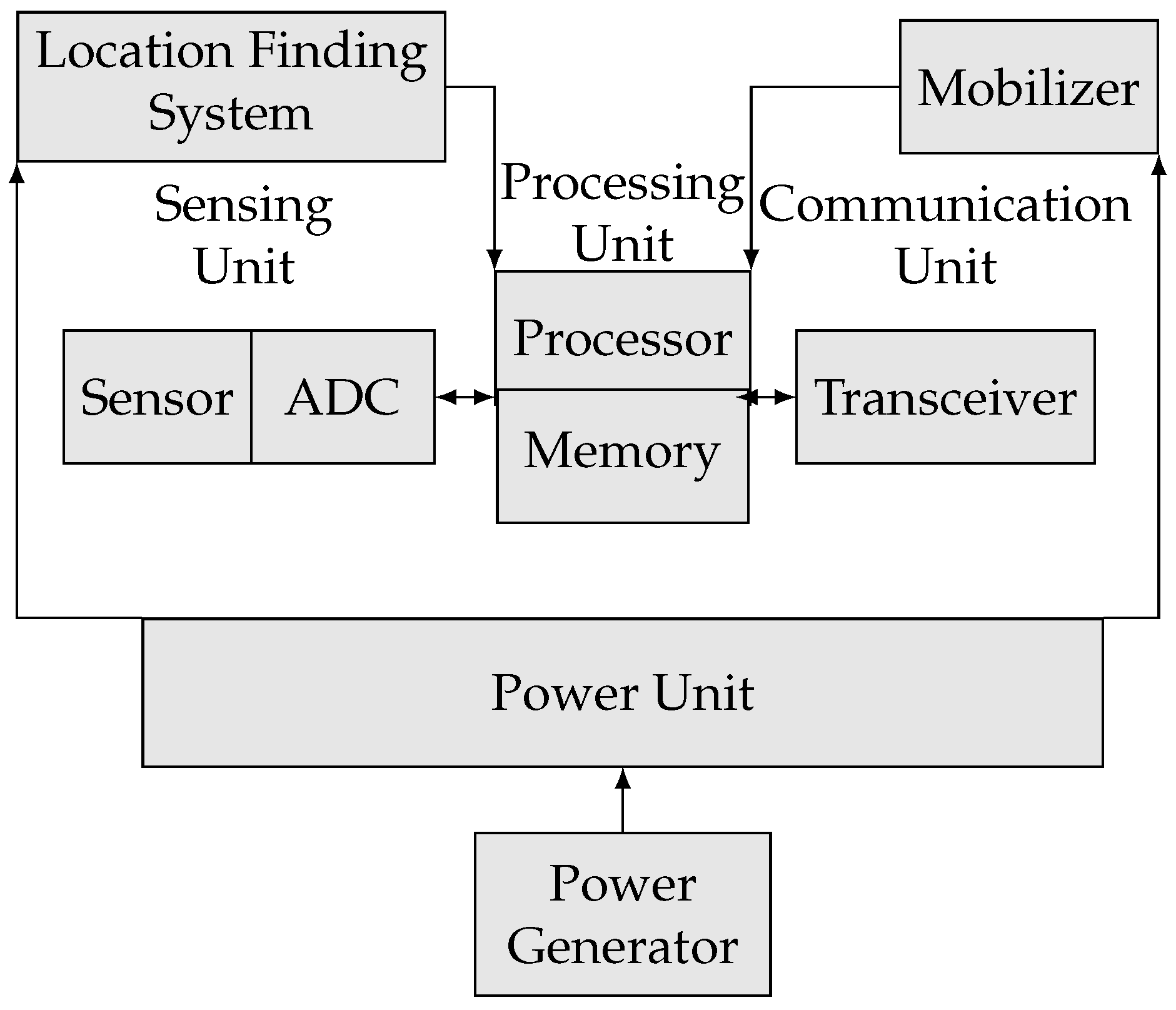
- Resource-constrained devices have limited memory, power, and transmitting bandwidth. For example, TelosB [37] is an ultra-low-power sensor with a a 16 bit processor and 8 MHz RISC microcontroller with only 10 Kb RAM, 48 Kb program memory, and 1024 Kb flash storage. The required total space for a typical code, such as TinyOS, which is the de facto standard operating system for wireless sensors, is approximately 4 Kb [38]. Therefore, any implemented security algorithm within the network must not be computationally demanding beyond these limitations.
- Security algorithms must be able to manage unsupervised sensors, which could be exposed to physical attack by demolishing the hardware or to attackers equipping sensors with extra hardware to perform hidden or malicious functions prior to their being deployed in the network area.
- Determining the adopted broadcast dynamic channel used as a wireless communication medium is challenging, as it is unattended and might be affected by collision and interference issues. WSN communication links are usually based on the 802.15.4 standard, and can be implemented via the use of other technologies as well, such as Bluetooth, ZigBee, PLC, WiFi, 4G, and 5G.
- The lack of fixed physical infrastructure is a significant design challenge due to the rapidly changing connectivity between nodes.
- A dynamic underlying network topology results from node failure, deployment of new nodes, possible variations in node position (which is especially the case under harsh environmental conditions), node mobility. The resulting flexibility in terms of link connectivity presents a design challenge for security algorithms, which must be able to adapt to network node variations in order to obtain the extra measure of protection provided by monitoring of corrupted nodes.
- WSN routing protocols have weaknesses, including malicious routing information injection, alteration, or spoofing, which might lead to network disruptions such as creation of routing loops, broadcasting of fake error messages to partition the network, attracting or repelling network traffic from particular nodes, extending or shortening route paths, and increasing end-to-end latency. These issues are likely to complicate the design of security routing techniques [39].
- Medium- to large-scale networks of hundreds or thousands of nodes deployed randomly or uniformly throughout the network field presents a challenge when designing security algorithms that are sufficiently flexible to support different security-level requirements.
- The scalability of WSNs implies handling large amounts of data that may have inconsistent, noisy, erroneous, redundant, and missing values, which requires designing intelligent security approaches that can correctly interpret data to drive intelligent decision-making.
- Data transmission over multi-hop relaying creates a significant threat, as relays could be eavesdroppers [40], and communicated data may be breached, tampered with, or forged.
- Time synchronization is an issue, as nodes are independently controlled in the field. Local clocks should be coordinated to avoid synchronization uncertainties, which could cause sensed data to become ambiguous and unreliable.
- Unexpected and unusual sensor behavior patterns may arise during WSN deployment in unpredictable and hazardous environments, potentially changing the entire historical pattern of the sensed data.
5. Cyberattacks in WSN Contexts
6. Architecture of WSN vs. Architecture of IDS
6.1. Naive or Flat-Based WSN Architecture for Centralized IDS
6.2. Naive or Flat-Based WSN Architecture for Stand-Alone IDS
6.3. Naive or Flat-Based WSN Architecture for Distributed or Cooperative IDS
6.4. Naive or Flat WSN Architecture for Agent-Based IDS
6.5. Hierarchical WSN Architecture for Distributed or Cooperative IDS
7. Types of IDS
8. ML and Cyberattack Detection
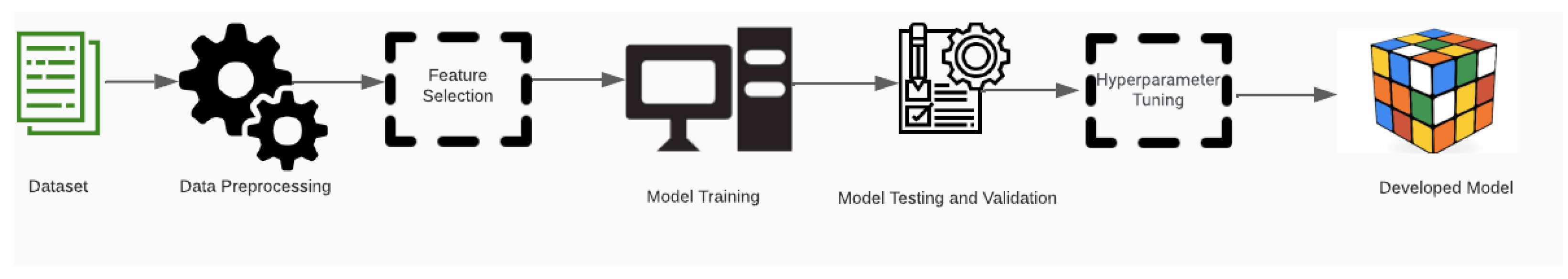
8.1. ML Methodology
8.2. Existing ML-Based approaches
8.2.1. Classical Machine Learning
8.2.2. Deep Learning
8.2.3. Deep Reinforcement Learning
8.2.4. Federated Learning
8.3. ML Challenges in WSN
8.3.1. Challenges Related to Constrained Resources
8.3.2. Challenges Related to Applications and Routing Algorithms
8.3.3. Challenges Related to the ML Framework
8.3.4. Challenges Related to Cross-Layer Attack Detection
8.4. Datasets
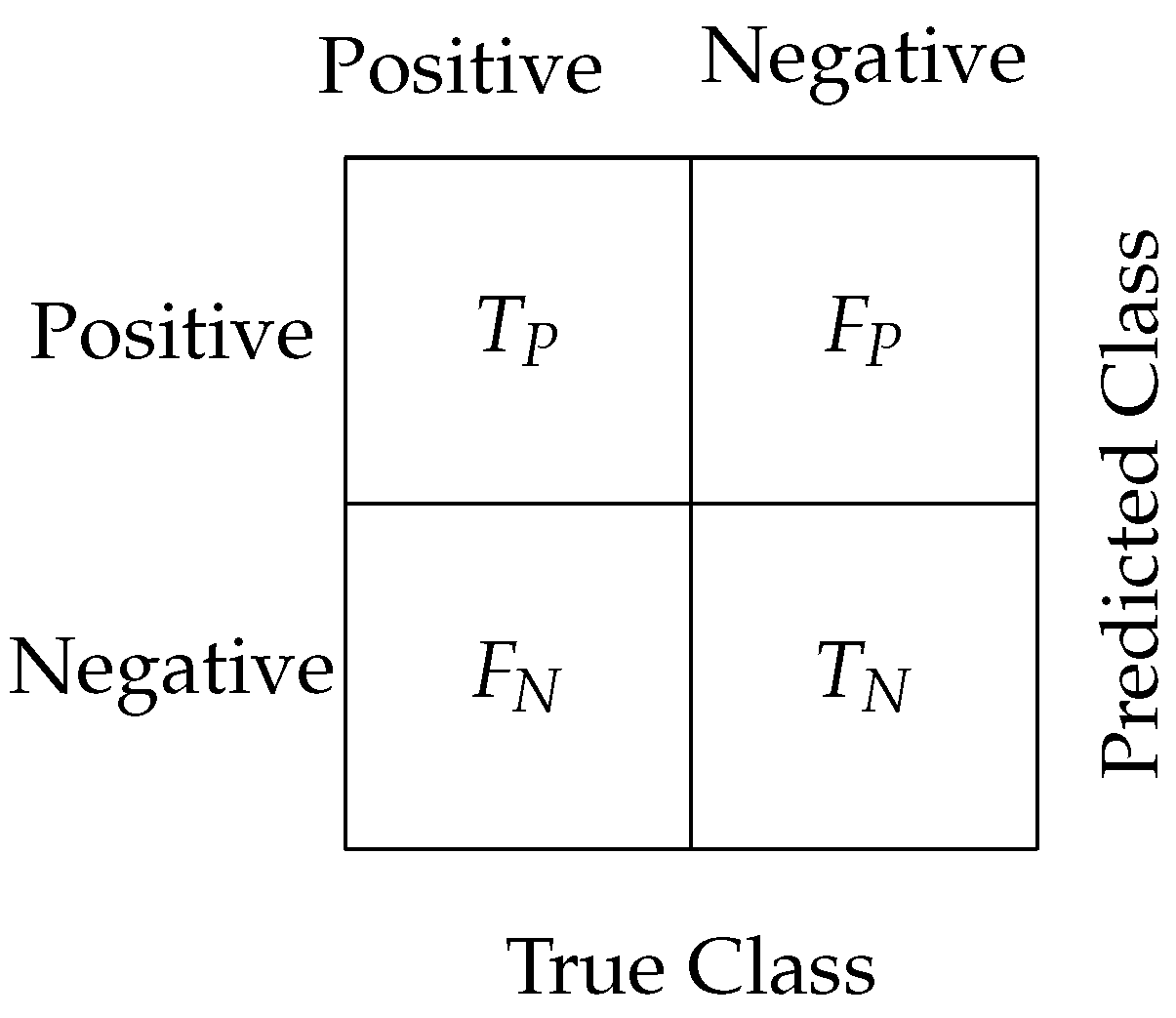
8.5. Evaluation Metrics
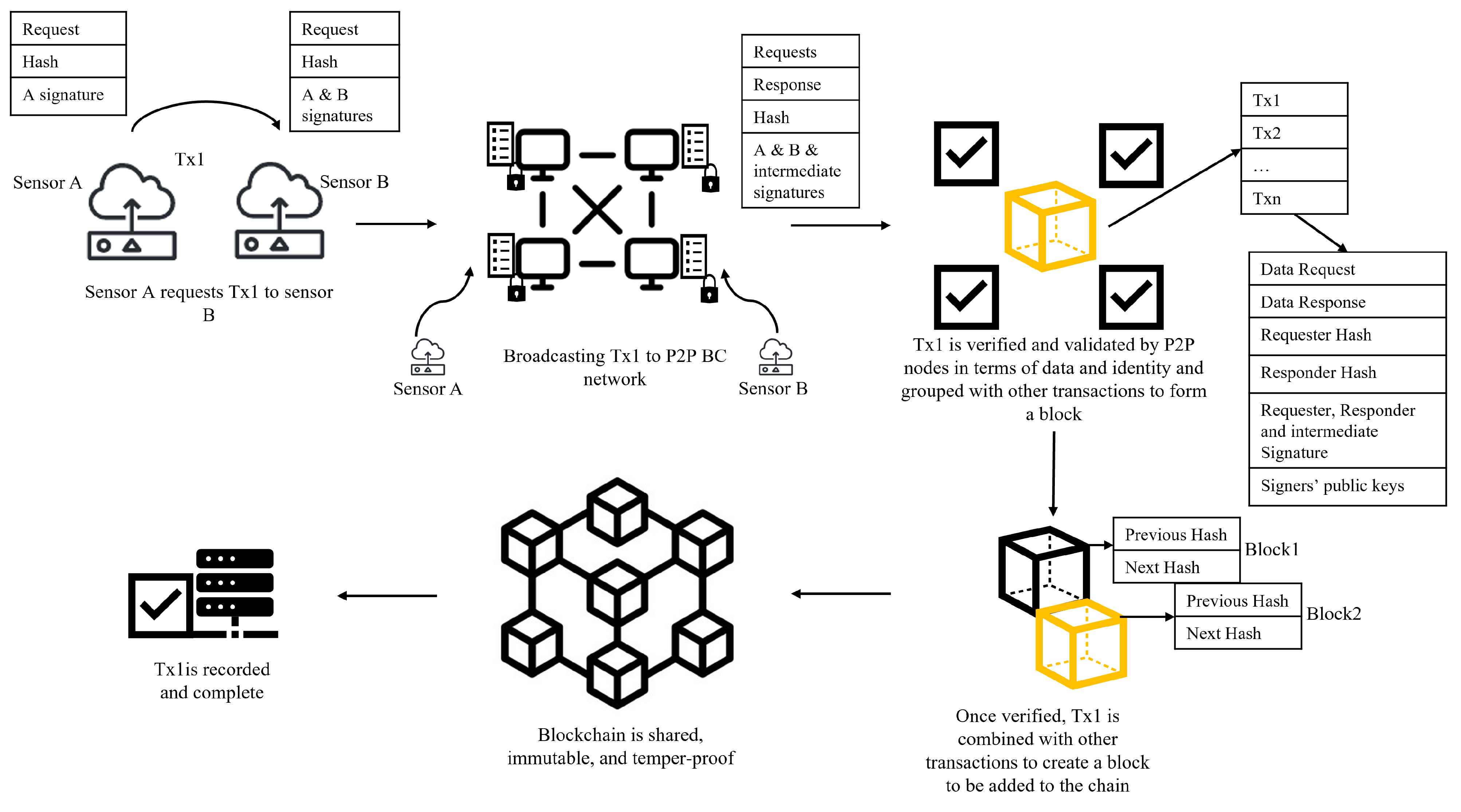
9. BC and Cyberattack Prevention
9.1. BC Background
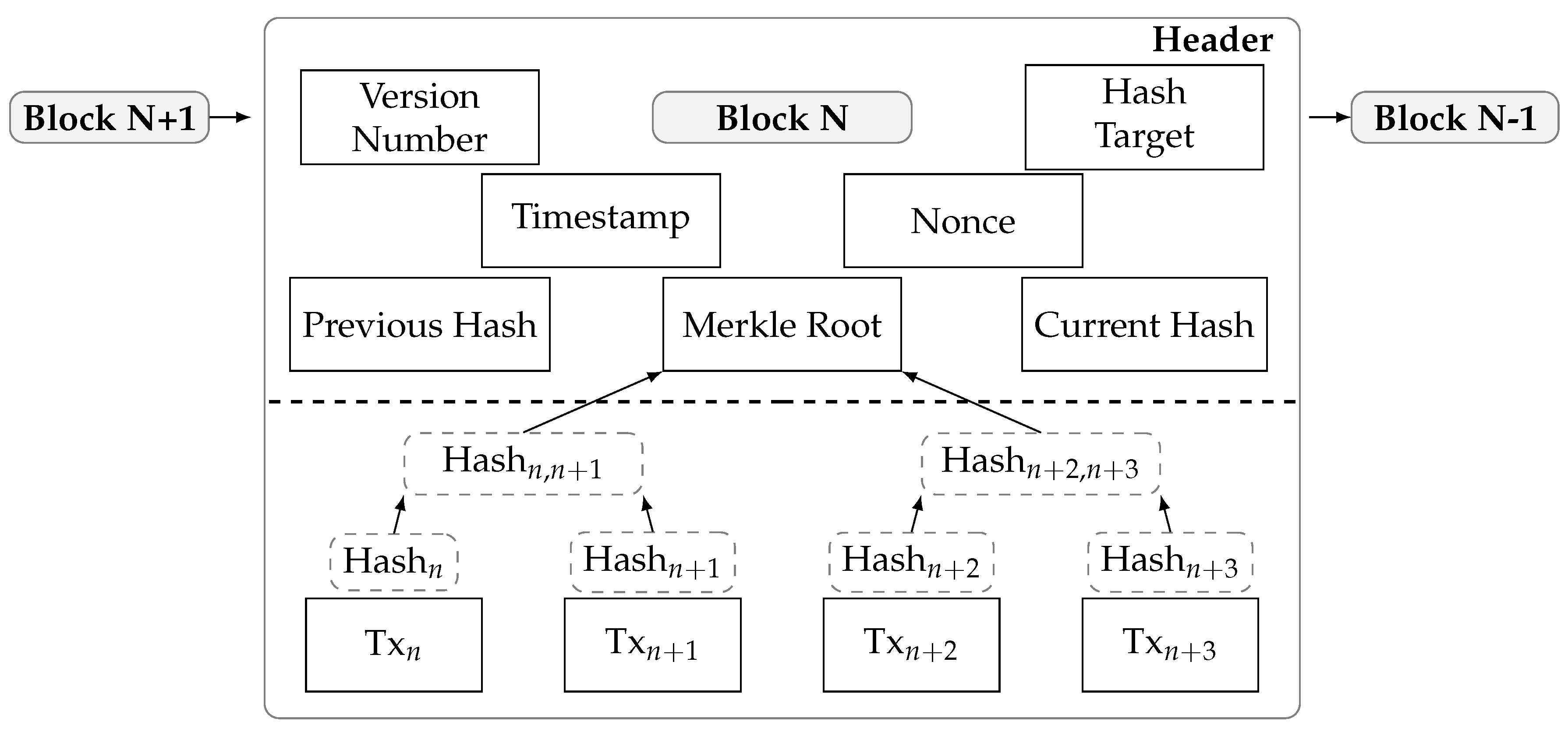
- Version number: indicates validation rules that the BC must follow.
- Previous hash: a 256-bit value that points to the previous block (sometimes called a parent block) and affects the current block’s hash to ensure the chain structure’s uniqueness.
- Timestamp: the block’s approximate creation time, which is required for traceability.
- Nonce: a one-time use number in the block header that is required in order to state the number of leading zeros for the hash value. This number can then be used to determine the level of difficulty when calculating the hash of a block and for verification to ensure consensus.
- Merkle root: sometimes called the ‘hash of all hashes’, this uniquely identifies the block; its calculation depends on the block’s transactions [106]. The Merkle tree is used to verify the validity of the transactions instead of downloading the entire chain. Figure 8 illustrates the Merkle tree’s structure, which is represented through the individual hashes of the transactions or leaf nodes; each set of child hashes is combined and hashed again up the tree until the root is reached [102]. Changing one transaction causes a change in the whole chain of hashes up to the Merkle root value [102].
- Hash target or nBits: a threshold value that the block header hash must not exceed in order for the block to be valid; the nBit value is usually continuously adjustable and increases with the number of leading zeros.
9.2. BC Features
- Data immutability: data are protected using cryptographic hashes unique to each block, disallowing manipulation or alteration after registration in the BC network.
- Decentralization: the absence of a trusted supervised centralized authority; decentralization ensures a lower failure rate, makes the network less prone to malicious attacks, and reduces reliance on a third party.
- Transparency: every involved node in the network is aware of the updated stored data.
- Security and Resilience: any data manipulation requires the approval of more than half of the miner nodes, which is extremely difficult to obtain practically.
- Data Encryption: the provision of public and private keys for data encryption and decryption, respectively, via the use of an asymmetric encryption algorithm for every two communicating nodes; the public key is shared between all nodes in the network to encrypt the data, and the targeted receiver can decrypt the data using its own private key.
- Digital Signatures: digital signing of transactions using a digital signature algorithm, such as the elliptic-curve digital signature algorithm (ECDSA), to approve transaction content and originate node identities.
- Consensus: every node in the network should agree on the current state of the distributed ledger, which is made possible using one of several popular consensus mechanisms, such as Proof-of-Work (PoW), Proof of Authority (PoA), Proof of Capacity (PoC), Proof of Share Stake (PoS), Delegated Proof of Stake (DPoS), Raft, Proof of Elapsed Time (PoET), and practical Byzantine fault tolerance (PBFT) [111].
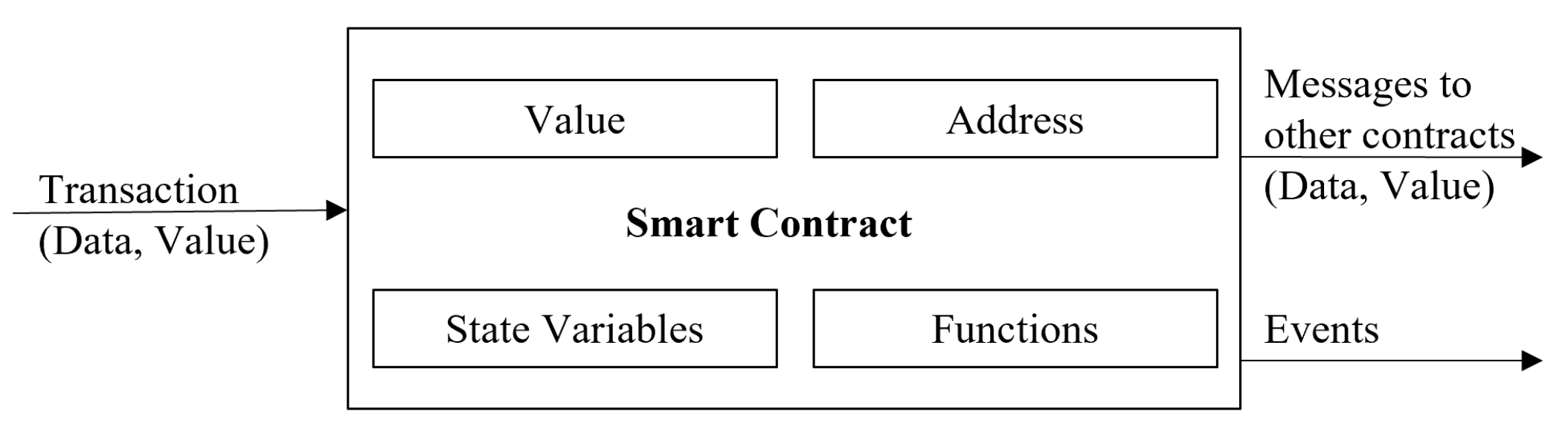
- Smart contract: a piece of code that adds customizability to a BC. It represents an arrangement and executes itself automatically under a predetermined set of rules and conditions without a third party. Smart contracts can be used for node verification and authentication. The input of the smart contract is the transaction, which is executed with a corresponding code that consists of the value, address, functions, and state to generate the output events (see Figure 9) [112].
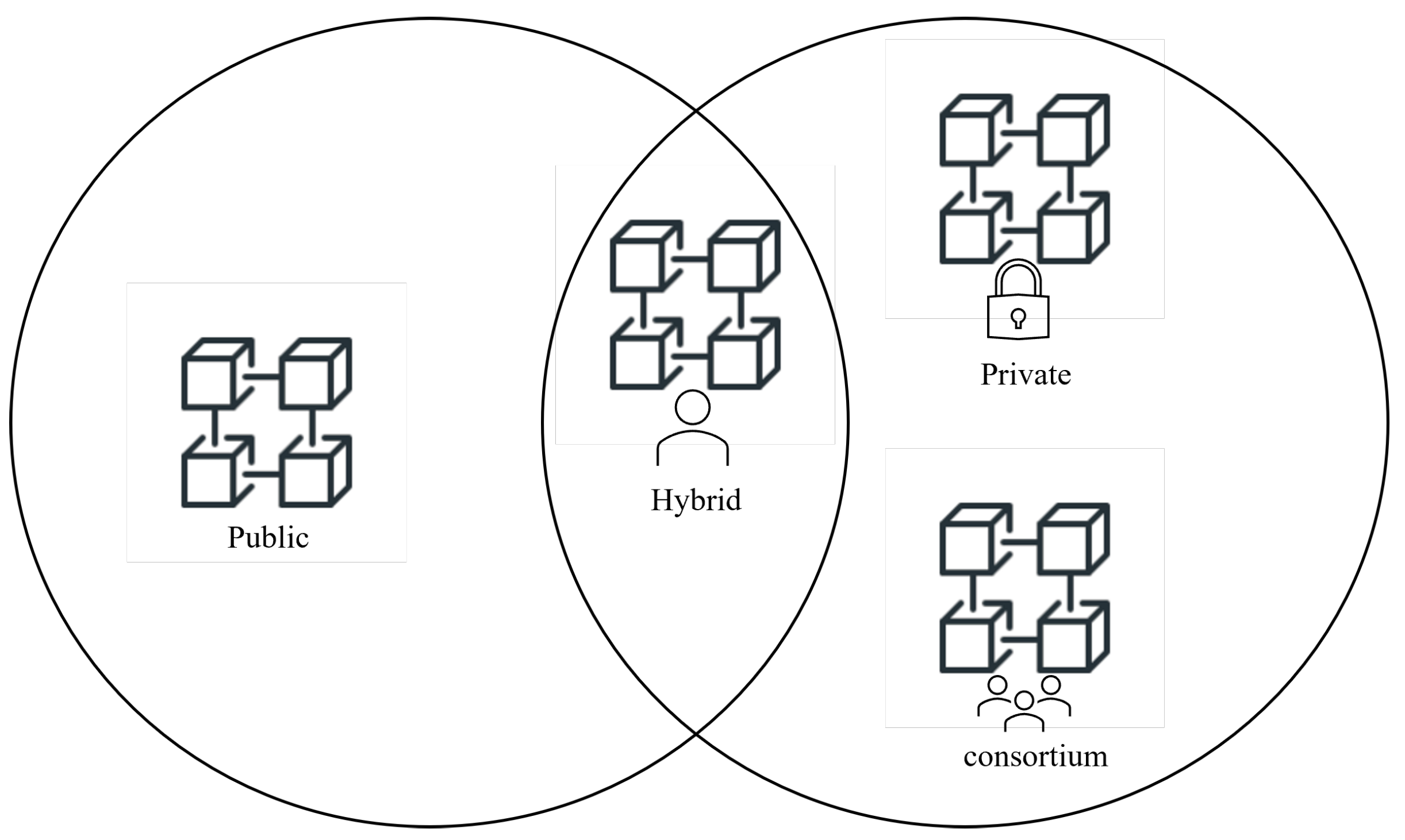
9.3. Types of BC
9.4. Performance Evaluation Metrics
- Transaction Throughput: the maximum amount of transactions that are processed and committed by the BC in a specific period of time, usually represented by transactions per second (tps).
- Response time: the time required to handle and verify the transactions processed by peers. The response time increases with increasing batch size, such as when the number of transactions in the queue grows; this can result in system congestion, as peers are required to handle more transactions.
- Latency: the period of time between when the transaction is invoked by a node and the time the transaction is added to the ledger.
- Transaction size: the amount of data in the transaction to be added to the next block.
- Block size: the size of the block, that is, the number of transactions included in the block.
- Storage Overhead: the storage capacity required for BC operations, which may exceed the node’s storage capabilities due to the large amount of data accumulated by security tasks [118].
- Residual energy: the remaining energy in the sensor nodes; this metric is important to consider for energy-related attacks which shorten the network lifetime by wasting nodes’ energy by launching malicious activities [119].
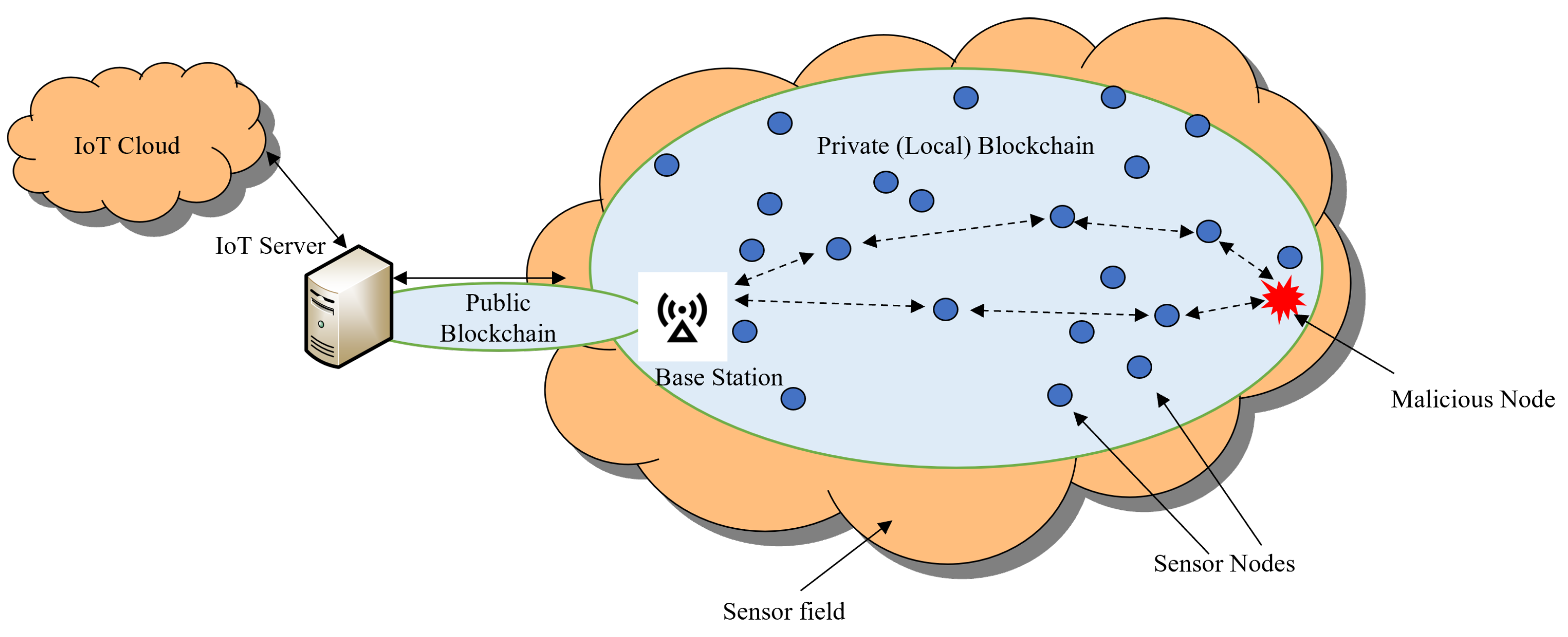
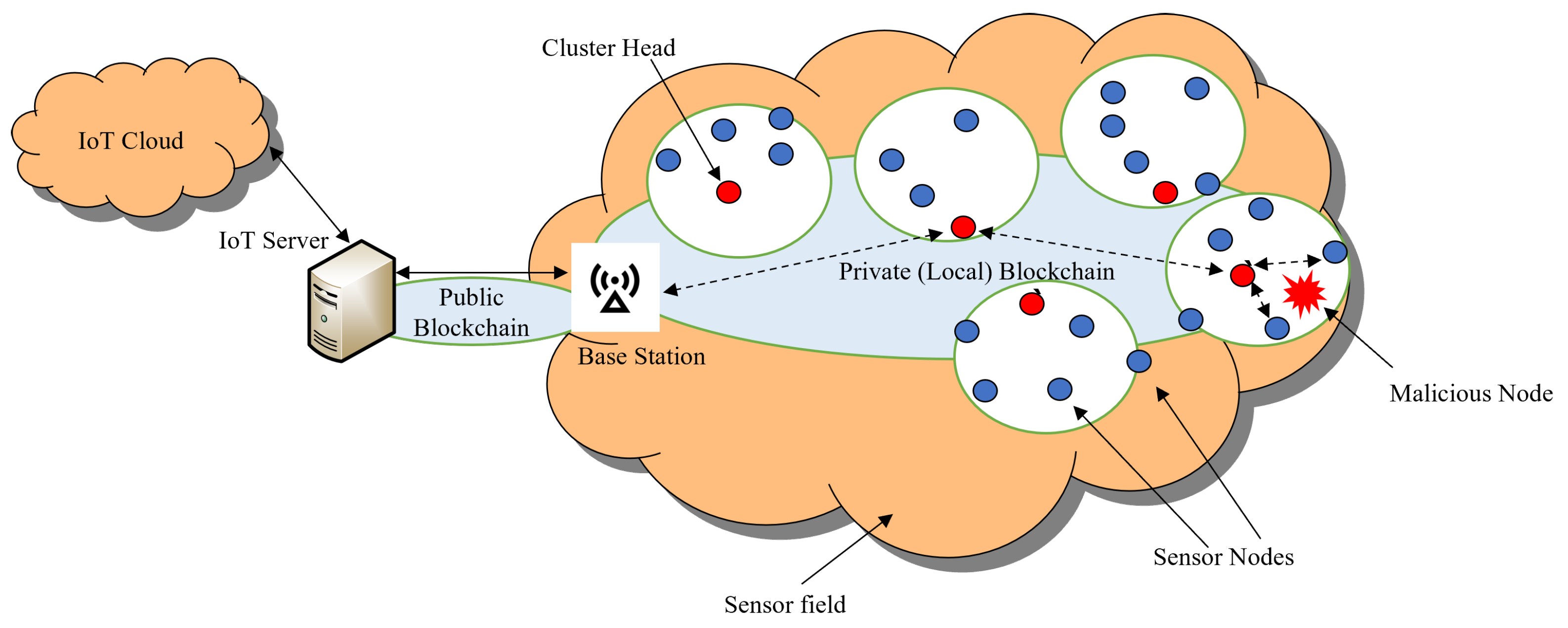
9.5. Securing WSNs Using BC
9.6. BC Challenges in WSNs
- Scalability and Storage: the amount of generated data grows exponentially with an increase in the number of devices deployed in different IoT applications, which leads to an increase in the rate of transaction execution and in the storage capacity needed to keep the ledger up to date [124]. Scalability becomes a severe bottleneck with an increasing number of transactions, and limits the practical development of BC in WSN contexts. With BC technology, blocks are not stored in a central server; however, a subset of the nodes need to keep a copy of the entire ledger in their own limited storage, which means that maintaining enough storage space for the ledger may not be feasible. Moreover, the size of the ledger increases over time, while most of nodes have low storage capacity of 10 KB to 100 KB memory at the most.The ledger storage requirement remains an open research issue. According to [125], certain IoT devices are limited to up to 8 MB of memory, most of which is used for storing the software that manages the device; therefore, lightweight mechanisms that limit the ledger size and allow it to be stored by each node are highly recommended. The authors of [118] defined three strategies for data storage by IoT sensors: full storage, in which all nodes store the full current data; partial storage, in which each node stores only part of the data, allowing it to be restored when combined with data from other nodes; and persistent storage, in which low-priority or old data can be stored in a remote centralized database. Similar criteria can be suggested to reduce storage overhead.Efficient consensus protocols, optimizing block size, sharding, pruning, lighting protocols, and off-chain storage have been proposed in the literature to address scalability issues. For instance, PBFT is considered a suitable protocol for fixed and small-size networks, although it is not scalable for larger numbers of IoT devices [126]. Sharding is one of the newer mechanisms to support scalability; it aims to split the overhead of processing transactions between multiple ‘shards’, or subgroups, of consensus nodes. These groups work in parallel to maximize performance while significantly avoiding the overhead due to duplication of communication, computation, and storage per full node, allowing the system to scale to larger networks [127]. Scalability can be increased by pruning the size of blocks on the BC, which includes removing older transactions to control memory usage [128]. Lighting protocols aim to lower the verification process period by only allowing full nodes to store the complete ledger, with lightweight nodes only keeping a portion of it. In off-chain storage, only hashes are stored in the ledger, whereas actual data are stored off-chain i.e., in the cloud, to support the scalability in dense WSNs.
- Consensus mechanisms: common consensus mechanisms such as PoA, PoS, and PoC are primarily designed to work for monetary transactions, and are not suitable for adoption in WSNs and constrained-resource IoT devices [129]. PoW is not common in IoT and WSN applications, as it is demanding in terms of computational power; while PoC is energy efficient, it depends on a node’s storage capacity and monetary stake, and monetary stakes do not exist in IoT and WSNs [130]. In addition, the most commonly known consensus mechanisms do not perform as desired in their raw mode because of massive requirements and scalability issues [131].
- Communication Overhead and Synchronization: a significant amount of communication overhead is required to synchronize the BC copies, as there is a need to forward every verified transaction to all peers. Establishing keys and authenticating nodes with cryptography, which is determined by the encryption type (either asymmetric or symmetric), causes high communication overhead and key storage [118]. Time consistency during time synchronization between sensor nodes requires exchanging a number of messages depending on synchronization frequency.
- Computation Overhead: heterogeneous IoT devices have different processing capabilities for running encryption and decryption, which leads to variations in processing time. Integrating a BC into the sensor network enables a logical peer-to-peer network to validate and store transactions locally, which is straightforward for personal computers or workstations; however, it might be difficult for tiny sensors with limited computational resources.
- Complexity and Energy Wastage: most widely employed BCs use PoW as a consensus mechanism, where the network participants must solve a mathematical problem or cryptographic puzzle in order to validate and authenticate transactions. PoW uses a significant amount of computational resources, causing energy losses; therefore, it is not practically suitable for IoT networks [30,111]. In addition, severe latency affects WSN stability in delay-sensitive applications [132].
- Guaranteeing Security: many malicious activities target IoT and WSNs. A single attack can harm a large number of devices or be used to destroy another system, as monitor nodes can be turned into malicious nodes to launch further attacks. The network’s ability to manage advanced cyberattacks is degraded due to the constrained resources of IoT devices. However, a BC relies on sophisticated hash functions, which require heavy computation and consensus mechanisms that consume network bandwidth.
- Compatibility and Standardization: standardization for BC security applications is needed in to ensure that devices meet a reasonable set of standards and have fundamental security and privacy capabilities and to diminish risks associated with cyberattacks against IoT devices [133].
9.7. BC in the Literature
| BC Type | Ref. | Security Threat | Study Highlights |
|---|---|---|---|
| Private | [120] | DDOS and Linking attacks | Relies only on AES symmetric encryption for data integrity |
| [138] | Data Tampering | BC-based trust model and node authentication using smart contracts to reduce latency. | |
| [106] | Data Tampering | Performance evaluation of the computational complexity associated with the ledger. | |
| [147] | Internal attacks | Three-phase sequential detection using sensor node hash values, node signatures, and voting degree | |
| [146] | Worm attack | Relies on IOTA Tangle | |
| [142] | Sybil attack | Relies on IOTA Tangle | |
| Consortium | [136] | Internal attacks | Utilizes a smart contract in conjunction with BC |
| Hybrid | [109] | Sybil, MITM, DoS, Message Substitution, and Replay attacks | Identity management and secure authentication mechanism |
| [139] | Internal attacks | Employs HECC to generate public and private keys | |
| [145] | DoS and Sybil attacks | Employs dual public and private BCs which implement a PoW and PoA consensus, respectively, for authentication of each BC. | |
| N/A | [140] | Greyhole and blackhole internal attacks | Test-bed experiments using a data-driven trust mechanism to reduce network transaction throughput. |
| [52] | Physical or logical data tampering | Limits the size of the BC and uses a time window with a circular buffer mechanism to reduce the BC’s length. | |
| [149] | Attacks on the localization process | Uses both behaviour and data trust values to determine the reliability level. | |
| [129] | Injection, data tampering, firmware modification, listening to traffic | Proposes a new consensus algorithm model to reduce mining time. | |
| [144] | Routing attacks | Utilizes BC as a shared memory for route determination to avoid untrusted nodes | |
| [141] | Routing attacks (blackhole, replay, and MITM) | Relies on BC block technology to protect the flow routing tables at the nodes against routing attacks in an SDN-enabled WSN | |
| [148] | Internal attacks | Uses a subjective probability measure as a reputation level model for peer trust |
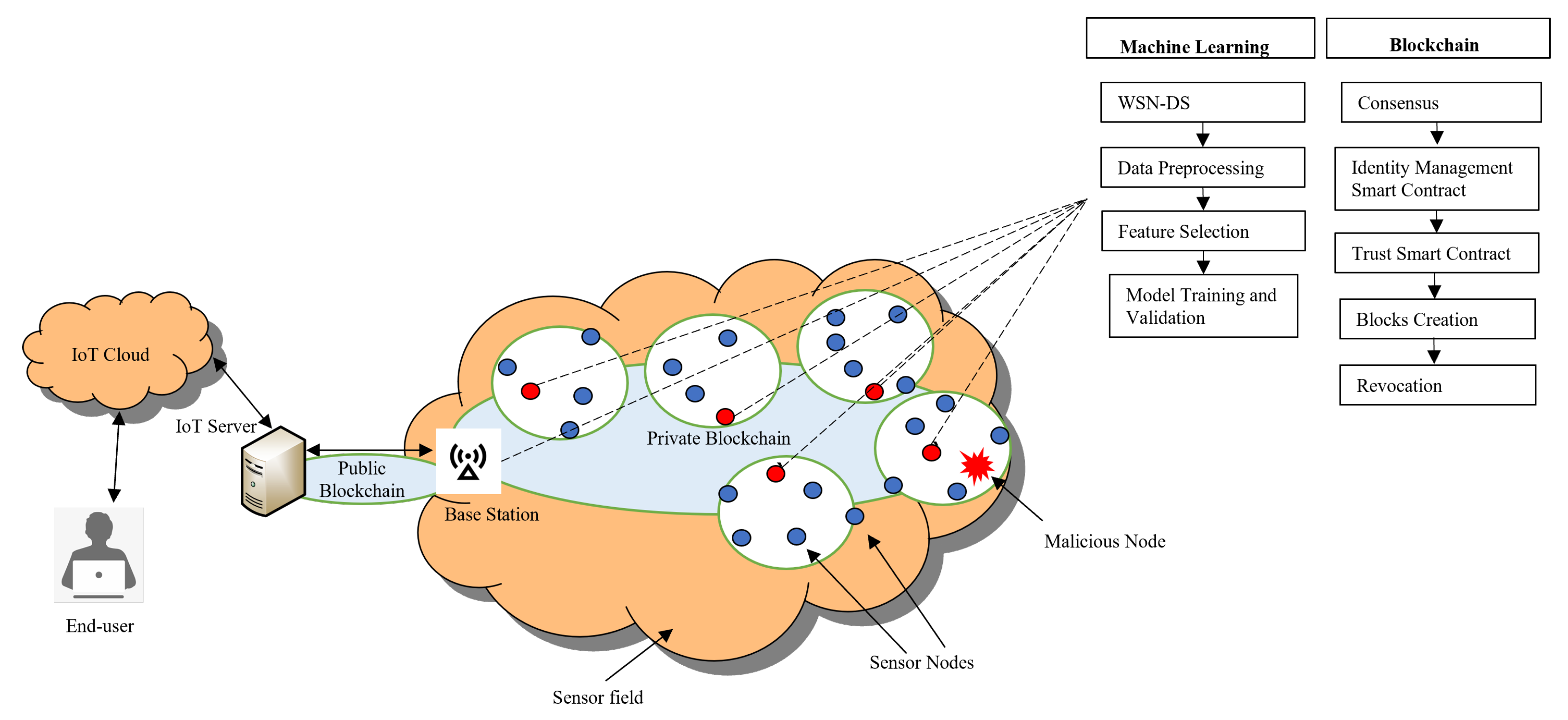
10. BC–ML Integration
10.1. Related Work
10.2. Research Challenges
- Integration performance: BC and ML integration performance depends on each technology’s performance; however, having both technologies operating within the same system rsises the idea of using each technology to improve the functional performance of the other. For example, ML model detection performance can be degraded by data tampering. In this regard, BC can protect the data transactions used to train the ML models along with the recorded decisions (i.e., output) of attack classification with confidence, disallowing tampering. These records can be reviewed and audited at any time by authorized nodes, and can be used to improve future ML detection decisions. In this way, incremental ML models can improve their future decision-making to detect novel attacks and handle drift in networks that change dynamically over time [65].
- Scalability: a measure of how well systems are used in conjunction with WSNs, scalability is related to network capacity in terms of the number of nodes that can join and the transaction volume that can be generated and processed over the network. The selection of the BC type and consensus mechanism highly affect scalability. For instance, the PBFT and PoA consensus mechanisms can improve transaction throughput compared to PoW, which usually supports only a few dozen transactions per second. Frequent authentication and peer trust requirements coupled with increased ledger size as the number of nodes and data increase present a challenge when aiming for a scalable ML–BC integrated security framework; however, many solutions have been presented in the literature that support scalability when employing BC technology. Among these solutions is the use of a hybrid BC, which utilizes a public BC connected to multiple private BCs wherein each private BC operates with one WSN. This structure limits the transaction volume and size of the ledger, ensuring better scalability. Among the known consensus mechanisms, voting or multiparty consensus works better with private BCs, and their combination is a candidate for use in cooperative WSNs. Another consensus mechanism is Proof-of-Authentication (PoAh), proposed in [158] for resource-scarce networks, adn which could be tested for WSNs. ML algorithms, on the other hand, can be used to code smart contracts for a more scalable approach to effective detection of malicious nodes.
- Lightweight schemes: to reduce overhead, the development and refinement of lightweight BC–ML integrated schemes while maintaining the same desired security level is essential. Deploying BC involves many elements, such as trust, authentication, access control, smart contracts, and consensus mechanisms, and each element can be implemented using a variety of options. The complexity of a BC can be refined by considering lightweight schemes in terms of storage, processing, and communication for each element involved in the deployed BC. For instance, in [152] the authors suggested Interplanetary File System (IPFS) to record the detection process, with the aim of reducing the cost of data storage in WSN; however, they did not consider the communication overhead required to upload and download data between IPFS and BS. In terms of consensus, PBFT and PoA are preferable, as they offer reduced computation and delay compared to PoW.
- Vulnerability: the ultimate goal of combining ML and BC into one system is the potential increase in security level; however, this integration does not completely eliminate threats. The root of these possible threats can be understood by considering that even though data my be safely protected by BC, it could be susceptible to tampering before it is securely recorded in the ledger.Considering the two approaches for BC implementation, namely, public and private, a public BC is open and accessible to all nodes, whereas a private BC is not. Therefore, a is preferable when higher levels of security are desired [159]. However, private BCs limit access to the large amount of data required to develop an efficient ML model, especially with the amount of continuously developed attack types, which makes an ML–BC integrated system vulnerable to newly developed attacks. Other possible threats might be due to malfunctioning or faulty sensors, or even sensors equipped with extra hardware allowing them to be operated maliciously, and which cannot be detected unless physically tested. These challenges add up when considering that nodes can become malicious and threaten the network security after joining the network. In addition, smart contracts can be vulnerable to possible smart contract-based attacks due to bugs in the smart contract code. ML can be used for smart contract verification and vulnerability detection [160].
- Managing network resources: limited-resource sensor nodes represent a key technical challenge when developing an ML–BC integrated solution considering encryption, trust and authentication, and validation of transactions through consensus. The ledger grows exponentially over time, and eventually may not fit within a node’s memory. These technical challenges in terms of storage and processing translate into high power consumption, extending across all aspects of system design. The authors of [161] suggested a solution to this problem by switching to symmetric instead of asymmetric BC encryption in order to simplify the system’s computational complexity. The computational complexity can be reduced using a simplified method for hash function calculation, such as SHA-256 [161]. Another proposed direction is dedicating specific nodes with high capabilities, such as CHs and BS nodes, for ledger storage, with other nodes only keeping the constant-length hash value of the data in the ledger to be referenced when needed. In addition, old data can be migrated from the CHs and BS toward the IoT cloud or external storage (i.e., IPFS).
- Legal issues: proliferation of different standards or a lack of security regulation can represent a challenge when designing systems involving two different technologies. Setting standards for such integrated solutions can potentially be done at the level of manufacturing and fabrication, that is, at the sensor stage.
11. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Abbas, G.; Mehmood, A.; Carsten, M.; Epiphaniou, G.; Lloret, J. Safety, Security and Privacy in Machine Learning Based Internet of Things. J. Sens. Actuator Netw. 2022, 11, 38. [Google Scholar] [CrossRef]
- Bajaj, K.; Sharma, B.; Singh, R. Integration of WSN with IoT applications: A vision, architecture, and future challenges. In Integration of WSN and IoT for Smart Cities; Springer: Berlin/Heidelberg, Germany, 2020; pp. 79–102. [Google Scholar]
- Pavithran, D.; Shaalan, K.; Al-Karaki, J.N.; Gawanmeh, A. Towards building a blockchain framework for IoT. Clust. Comput. 2020, 23, 2089–2103. [Google Scholar] [CrossRef]
- Sinha, P.; Jha, V.K.; Rai, A.K.; Bhushan, B. Security vulnerabilities, attacks and countermeasures in wireless sensor networks at various layers of OSI reference model: A survey. In Proceedings of the 2017 International Conference on Signal Processing and Communication (ICSPC), Coimbatore, India, 28–29 July 2017; pp. 288–293. [Google Scholar]
- Panda, M. Security in wireless sensor networks using cryptographic techniques. Am. J. Eng. Res. (AJER) 2014, 3, 50–56. [Google Scholar]
- Hussain, F.; Hussain, R.; Hassan, S.A.; Hossain, E. Machine learning in IoT security: Current solutions and future challenges. IEEE Commun. Surv. Tutor. 2020, 22, 1686–1721. [Google Scholar] [CrossRef]
- Xu, L.D.; Lu, Y.; Li, L. Embedding Blockchain Technology Into IoT for Security: A Survey. IEEE Internet Things J. 2021, 8, 10452–10473. [Google Scholar] [CrossRef]
- Kumar, D.P.; Amgoth, T.; Annavarapu, C.S.R. Machine learning algorithms for wireless sensor networks: A survey. Inf. Fusion 2019, 49, 1–25. [Google Scholar] [CrossRef]
- Alsheikh, M.A.; Lin, S.; Niyato, D.; Tan, H.P. Machine Learning in Wireless Sensor Networks: Algorithms, Strategies, and Applications. IEEE Commun. Surv. Tutor. 2014, 16, 1996–2018. [Google Scholar] [CrossRef]
- Bout, E.; Loscri, V.; Gallais, A. How Machine Learning Changes the Nature of Cyberattacks on IoT Networks: A Survey. IEEE Commun. Surv. Tutor. 2022, 24, 248–279. [Google Scholar] [CrossRef]
- Tahsien, S.M.; Karimipour, H.; Spachos, P. Machine learning based solutions for security of Internet of Things (IoT): A survey. J. Netw. Comput. Appl. 2020, 161. [Google Scholar] [CrossRef]
- da Costa, K.A.P.; Papa, J.P.; Lisboa, C.O.; Munoz, R.; de Albuquerque, V.H.C. Internet of Things: A survey on machine learning-based intrusion detection approaches. Comput. Netw. 2019, 151, 147–157. [Google Scholar] [CrossRef]
- Ahmad, R.; Alsmadi, I. Machine learning approaches to IoT security: A systematic literature review. Internet Things 2021, 14, 100365. [Google Scholar] [CrossRef]
- Haji, S.H.; Ameen, S.Y. Attack and Anomaly Detection in IoT Networks using Machine Learning Techniques: A Review. Asian J. Res. Comput. Sci. 2021, 9, 30–46. [Google Scholar] [CrossRef]
- Faraj, O.; Megias, D.; Ahmad, A.M.; Garcia-Alfaro, J. Taxonomy and challenges in machine learning-based approaches to detect attacks in the internet of things. In Proceedings of the 15th International Conference on Availability, Reliability and Security, Virtual, 25–28 August 2020; pp. 1–10. [Google Scholar]
- Mamdouh, M.; Elrukhsi, M.A.I.; Khattab, A. Securing the internet of things and wireless sensor networks via machine learning: A survey. In Proceedings of the 2018 International Conference on Computer and Applications (ICCA), Beirut, Lebanon, 25–26 August 2018; pp. 215–218. [Google Scholar]
- Mehta, A.; Sandhu, J.K.; Sapra, L. Machine Learning in Wireless Sensor Networks: A Retrospective. In Proceedings of the 2020 Sixth International Conference on Parallel, Distributed and Grid Computing (PDGC), Solan, India, 6–8 November 2020; pp. 328–331. [Google Scholar] [CrossRef]
- Baraneetharan, E. Role of machine learning algorithms intrusion detection in WSNs: A survey. J. Inf. Technol. 2020, 2, 161–173. [Google Scholar]
- Gunduz, S.; Arslan, B.; Demirci, M. A Review of Machine Learning Solutions to Denial-of- Services Attacks in Wireless Sensor Networks. In Proceedings of the 2015 IEEE 14th International Conference on Machine Learning and Applications (ICMLA), Miami, FL, USA, 9–11 December 2015. [Google Scholar] [CrossRef]
- Kim, T.; Vecchietti, L.F.; Choi, K.; Lee, S.; Har, D. Machine Learning for Advanced Wireless Sensor Networks: A Review. IEEE Sens. J. 2021, 21, 12379–12397. [Google Scholar] [CrossRef]
- Ramotsoela, D.; Abu-Mahfouz, A.; Hancke, G. A survey of anomaly detection in industrial wireless sensor networks with critical water system infrastructure as a case study. Sensors 2018, 18, 2491. [Google Scholar] [CrossRef] [PubMed]
- Ahmad, R.; Wazirali, R.; Abu-Ain, T. Machine Learning for Wireless Sensor Networks Security: An Overview of Challenges and Issues. Sensors 2022, 22, 4730. [Google Scholar] [CrossRef]
- Jesus, E.F.; Chicarino, V.R.; De Albuquerque, C.V.; Rocha, A.A.A. A Survey of How to Use Blockchain to Secure Internet of Things and the Stalker Attack. Secur. Commun. Netw. 2018, 2018, 9675050. [Google Scholar] [CrossRef]
- Liao, Z.; Pang, X.; Zhang, J.; Xiong, B.; Wang, J. Blockchain on Security and Forensics Management in Edge Computing for IoT: A Comprehensive Survey. IEEE Trans. Netw. Serv. Manag. 2021, 19, 1159–1175. [Google Scholar] [CrossRef]
- Sengupta, J.; Ruj, S.; Das Bit, S. A Comprehensive Survey on Attacks, Security Issues and Blockchain Solutions for IoT and IIoT. J. Netw. Comput. Appl. 2020, 149, 102481. [Google Scholar] [CrossRef]
- Khan, M.A.; Salah, K. IoT security: Review, blockchain solutions, and open challenges. Future Gener. Comput. Syst. 2018, 82, 395–411. [Google Scholar] [CrossRef]
- Darla, S.; Naveena, C. Survey on Securing Internet of Things through Block chain Technology. In Proceedings of the 2022 International Conference on Electronics and Renewable Systems (ICEARS), Tuticorin, India, 16–18 March 2022; pp. 836–844. [Google Scholar] [CrossRef]
- Uddin, M.A.; Stranieri, A.; Gondal, I.; Balasubramanian, V. A survey on the adoption of blockchain in IoT: Challenges and solutions. Blockchain Res. Appl. 2021, 2, 100006. [Google Scholar] [CrossRef]
- Pohrmen, F.H.; Das, R.K.; Saha, G. Blockchain-based security aspects in heterogeneous Internet-of-Things networks: A survey. Trans. Emerg. Telecommun. Technol. 2019, 30, e3741. [Google Scholar] [CrossRef]
- Miglani, A.; Kumar, N. Blockchain management and machine learning adaptation for IoT environment in 5G and beyond networks: A systematic review. Comput. Commun. 2021, 178, 37–63. [Google Scholar] [CrossRef]
- Matin, M.A.; Islam, M.M. Overview of wireless sensor network. Wirel. Sens.-Netw.-Technol. Protoc. 2012, 1, 3. [Google Scholar]
- Khan, Z.A.; Samad, A. A study of machine learning in wireless sensor network. Int. J. Comput. Netw. Appl. 2017, 4, 105–112. [Google Scholar] [CrossRef]
- Rehana, J. Security of wireless sensor network. In Proceedings of the Seminar on Internetworking, Helsinki University of Technology, Glasgow, UK, 24–28 August 2009. [Google Scholar]
- Sora, D. Security Issues in Wireless Sensor Networks. Int. J. Online Biomed. Eng. (IJOE) 2010, 6, 26–30. [Google Scholar] [CrossRef]
- Patel, N.R.; Kumar, S. Wireless Sensor Networks’ Challenges and Future Prospects. In Proceedings of the 2018 International Conference on System Modeling & Advancement in Research Trends (SMART), Moradabad, India, 23–24 November 2018; pp. 60–65. [Google Scholar] [CrossRef]
- de Farias, C.M.; Pirmez, L.; Delicato, F.C.; Pires, P.F.; Guerrieri, A.; Fortino, G.; Cauteruccio, F.; Terracina, G. A multisensor data fusion algorithm using the hidden correlations in Multiapplication Wireless Sensor data streams. In Proceedings of the 2017 IEEE 14th International Conference on Networking, Sensing and Control (ICNSC), Calabria, Italy, 16–18 May 2017; pp. 96–102. [Google Scholar] [CrossRef]
- Karray, F.; Jmal, M.W.; Garcia-Ortiz, A.; Abid, M.; Obeid, A.M. A comprehensive survey on wireless sensor node hardware platforms. Comput. Netw. 2018, 144, 89–110. [Google Scholar] [CrossRef]
- Xie, H.; Yan, Z.; Member, S.; Yao, Z. Data Collection for Security Measurement in Wireless Sensor Networks: A Survey. IEEE Internet Things J. 2019, 6, 2205–2224. [Google Scholar] [CrossRef]
- Alam, S.; De, D. Analysis of security threats in wireless sensor network. arXiv 2014, arXiv:1406.0298. [Google Scholar] [CrossRef]
- Walters, J.P.; Liang, Z.; Shi, W.; Chaudhary, V. Wireless sensor network security: A survey. In Security in distributed, Grid, and Pervasive Computing; Auerbach Publications: Boca Raton, FL, USA, 2006; pp. 208–222. [Google Scholar]
- Chapter 16—Wireless Sensor Network Security. In Computer and Information Security Handbook, 2nd ed.; Vacca, J.R., Ed.; Morgan Kaufmann: Boston, MA, USA, 2013; pp. 301–322. [Google Scholar] [CrossRef]
- Elhoseny, M.; Hassanien, A.E. Secure data transmission in WSN: An overview. In Dynamic Wireless Sensor Networks; Springer: Cham, Switzerland, 2019; pp. 115–143. [Google Scholar]
- Shahzad, F.; Pasha, M.; Ahmad, A. A survey of active attacks on wireless sensor networks and their countermeasures. arXiv 2017, arXiv:1702.07136. [Google Scholar]
- Mathew, A.; Terence, J.S. A survey on various detection techniques of sinkhole attacks in WSN. In Proceedings of the 2017 International Conference on Communication and Signal Processing (ICCSP), Chennai, India, 6–8 April 2017; pp. 1115–1119. [Google Scholar]
- Dewal, P.; Narula, G.S.; Jain, V.; Baliyan, A. Security attacks in Wireless sensor networks: A survey. In Cyber Security; Springer: Berlin/Heidelberg, Germany, 2018; pp. 47–58. [Google Scholar]
- Kaur, R.; Kaur Sandhu, J. A Study on Security Attacks in Wireless Sensor Network. In Proceedings of the 2021 International Conference on Advance Computing and Innovative Technologies in Engineering (ICACITE), Greater Noida, India, 4–5 March 2021; pp. 850–855. [Google Scholar] [CrossRef]
- Ismail, S.; Khoei, T.T.; Marsh, R.; Kaabouch, N. A Comparative Study of Machine Learning Models for Cyber-attacks Detection in Wireless Sensor Networks. In Proceedings of the 2021 IEEE 12th Annual Ubiquitous Computing, Electronics & Mobile Communication Conference (UEMCON), New York, NY, USA, 1–4 December 2021; pp. 1–5. [Google Scholar]
- Pruthi, V.; Mittal, K.; Sharma, N.; Kaushik, I. Network layers threats & its countermeasures in WSNs. In Proceedings of the 2019 International Conference on Computing, Communication, and Intelligent Systems (ICCCIS), Greater Noida, India, 18–19 October 2019; pp. 156–163. [Google Scholar]
- Yang, G.; Dai, L.; Wei, Z. Challenges, threats, security issues and new trends of underwater wireless sensor networks. Sensors 2018, 18, 3907. [Google Scholar] [CrossRef] [PubMed]
- de Lima Pinto, E.M.; Lachowski, R.; Pellenz, M.E.; Penna, M.C.; Souza, R.D. A machine learning approach for detecting spoofing attacks in wireless sensor networks. In Proceedings of the 2018 IEEE 32nd International Conference on Advanced Information Networking and Applications (AINA), Krakow, Poland, 16–18 May 2018; pp. 752–758. [Google Scholar]
- Bhattasali, T.; Chaki, R. A Survey of Recent Intrusion Detection Systems for wireless sensor network. In Advances in Network Security and Applications, Proceedings of the 4th International Conference, CNSA 2011, Chennai, India, 15–17 July 2011; Springer: Berlin/Heidelberg, Germany, 2011; pp. 268–269. [Google Scholar]
- Tiberti, W.; Carmenini, A.; Pomante, L.; Cassioli, D. A Lightweight Blockchain-based Technique for Anti-Tampering in Wireless Sensor Networks. In Proceedings of the 2020 23rd Euromicro Conference on Digital System Design (DSD), Kranj, Slovenia, 26–28 August 2020; pp. 577–582. [Google Scholar]
- Periyanayagi, S.; Sumathy, V. Swarm-based defense technique for tampering and cheating attack in WSN using CPHS. Pers. Ubiquitous Comput. 2018, 22, 1165–1179. [Google Scholar] [CrossRef]
- Numan, M.; Subhan, F.; Khan, W.Z.; Hakak, S.; Haider, S.; Reddy, G.T.; Jolfaei, A.; Alazab, M. A Systematic Review on Clone Node Detection in Static Wireless Sensor Networks. IEEE Access 2020, 8, 65450–65461. [Google Scholar] [CrossRef]
- Gupta, S.; Verma, H.K.; Sangal, A.L. Security attacks & prerequisite for wireless sensor networks. Int. J. Eng. Adv. Technol. (IJEAT) 2013, 2, 558–566. [Google Scholar]
- Premkumar, M.; Sundararajan, T.V. DLDM: Deep learning-based defense mechanism for denial of service attacks in wireless sensor networks. Microprocess. Microsyst. 2020, 79, 103278. [Google Scholar] [CrossRef]
- Mohapatra, H. Handling of Man-In-The-Middle Attack in WSN Through Intrusion Detection System. Int. J. Emerg. Trends Eng. Res. 2020, 8, 1503–1510. [Google Scholar] [CrossRef]
- Yahyaoui, A.; Abdellatif, T.; Attia, R. Hierarchical anomaly based intrusion detection and localization in IoT. In Proceedings of the 2019 15th International Wireless Communications & Mobile Computing Conference (IWCMC), Tangier, Morocco, 24–28 June 2019; pp. 108–113. [Google Scholar]
- Somaya, H.; Tomader, M. Build a malware detection software for IOT network Using Machine learning. In Proceedings of the 4th International Conference on Networking, Information Systems & Security, Kenitra, Morocco, 1–2 April 2021; pp. 1–8. [Google Scholar]
- Dener, M.; Al, S.; Orman, A. STLGBM-DDS: An Efficient Data Balanced DoS Detection System for Wireless Sensor Networks on Big Data Environment. IEEE Access 2022, 10, 92931–92945. [Google Scholar] [CrossRef]
- Park, T.; Cho, D.; Kim, H. An effective classification for DoS attacks in wireless sensor networks. In Proceedings of the 2018 Tenth International Conference on Ubiquitous and Future Networks (ICUFN), Prague, Czech Republic, 3–6 July 2018; pp. 689–692. [Google Scholar]
- Quincozes, S.E.; Kazienko, J.F. Machine learning methods assessment for denial of service detection in wireless sensor networks. In Proceedings of the 2020 IEEE 6th World Forum on Internet of Things (WF-IoT), New Orleans, LA, USA, 2–16 June 2020; pp. 1–6. [Google Scholar]
- Alsubaie, F.; Al-Akhras, M.; Alzahrani, H.A. Using machine learning for intrusion detection system in wireless body area network. In Proceedings of the 2020 First International Conference of Smart Systems and Emerging Technologies (SMARTTECH), Riyadh, Saudi Arabia, 3–5 November 2020; pp. 100–104. [Google Scholar]
- Alsulaiman, L.; Al-Ahmadi, S. Performance evaluation of machine learning techniques for DOS detection in wireless sensor network. arXiv 2021, arXiv:2104.01963. [Google Scholar] [CrossRef]
- Ifzarne, S.; Tabbaa, H.; Hafidi, I.; Lamghari, N. Anomaly detection using machine learning techniques in wireless sensor networks. J. Phys. Conf. Ser. 2021, 1743, 012021. [Google Scholar] [CrossRef]
- Batiha, T.; Krömer, P. Design and analysis of efficient neural intrusion detection for wireless sensor networks. Concurr. Comput. Pract. Exp. 2021, 33, e6152. [Google Scholar] [CrossRef]
- Al-Akhras, M.; Al-Issa, A.I.; Alsahli, M.S.; Alawairdhi, M. POSTER: Feature Selection to Optimize DoS Detection in Wireless Sensor Networks. In Proceedings of the 2020 First International Conference of Smart Systems and Emerging Technologies (SMARTTECH), Riyadh, Saudi Arabia, 3–5 November 2020; pp. 263–265. [Google Scholar]
- Batiha, T.; Prauzek, M.; Krömer, P. Intrusion Detection in Wireless Sensor Networks by an Ensemble of Artificial Neural Networks; Springer: Singapore, 2019; Volume 142, pp. 323–333. [Google Scholar] [CrossRef]
- Ismail, S.; Dawoud, D.; Reza, H. A Lightweight Multilayer Machine Learning Detection System for Cyber-attacks in WSN. In Proceedings of the 2022 IEEE 12th Annual Computing and Communication Workshop and Conference (CCWC), Virtual, 26–29 January 2022; pp. 481–486. [Google Scholar] [CrossRef]
- Ismail, S.; Reza, H. Evaluation of Naïve Bayesian Algorithms for Cyber-Attacks Detection in Wireless Sensor Networks. In Proceedings of the 2022 IEEE World AI IoT Congress (AIIoT), Seattle, WA, USA, 6–9 June 2022; pp. 283–289. [Google Scholar]
- Meng, D.; Dai, H.; Sun, Q.; Xu, Y.; Shi, T. Novel Wireless Sensor Network Intrusion Detection Method Based on LightGBM Model. IAENG Int. J. Appl. Math. 2022, 52, 1–7. [Google Scholar]
- Luo, T.; Nagarajan, S.G. Distributed anomaly detection using autoencoder neural networks in WSN for IoT. In Proceedings of the 2018 IEEE International Conference on Communications (ICC), Kansas City, MO, USA, 20–24 May 2018; pp. 1–6. [Google Scholar]
- Sherubha, P.; Amudhavalli, P.; Sasirekha, S. Clone attack detection using random forest and multi objective cuckoo search classification. In Proceedings of the 2019 International Conference on Communication and Signal Processing (ICCSP), Melmaruvathur, India, 4–6 April 2019; pp. 0450–0454. [Google Scholar]
- Otoum, S.; Kantarci, B.; Mouftah, H. Empowering reinforcement learning on big sensed data for intrusion detection. In Proceedings of the ICC 2019-2019 IEEE international conference on communications (ICC), Shanghai, China, 20–24 May 2019; pp. 1–7. [Google Scholar]
- Subasini, C.; Karuppiah, S.; Sheeba, A.; Padmakala, S. Developing an attack detection framework for wireless sensor network-based healthcare applications using hybrid convolutional neural network. Trans. Emerg. Telecommun. Technol. 2021, 32, e4336. [Google Scholar] [CrossRef]
- Salmi, S.; Oughdir, L. CNN-LSTM Based Approach for Dos Attacks Detection in Wireless Sensor Networks. Int. J. Adv. Comput. Sci. Appl. 2022, 13. [Google Scholar] [CrossRef]
- Salmi, S.; Oughdir, L. Performance evaluation of deep learning techniques for DoS attacks detection in wireless sensor network. J. Big Data 2023, 10, 1–25. [Google Scholar] [CrossRef]
- Otoum, S.; Kantarci, B.; Mouftah, H.T. On the feasibility of deep learning in sensor network intrusion detection. IEEE Netw. Lett. 2019, 1, 68–71. [Google Scholar] [CrossRef]
- Hussain, K.; Xia, Y.; Onaizah, A.N.; Manzoor, T.; Jalil, K. Hybrid of WOA-ABC and Proposed CNN for Intrusion Detection System in wireless sensor networks. Optik 2022, 170145. [Google Scholar] [CrossRef]
- Nguyen, T.T.; Reddi, V.J. Deep reinforcement learning for cyber security. IEEE Trans. Neural Netw. Learn. Syst. 2019. [CrossRef] [PubMed]
- Benaddi, H.; Ibrahimi, K.; Benslimane, A.; Qadir, J. A deep reinforcement learning based intrusion detection system (drl-ids) for securing wireless sensor networks and internet of things. In Proceedings of the International Wireless Internet Conference, Taichung, Taiwan, 26–27 November 2019; pp. 73–87. [Google Scholar]
- Niknam, S.; Dhillon, H.S.; Reed, J.H. Federated learning for wireless communications: Motivation, opportunities, and challenges. IEEE Commun. Mag. 2020, 58, 46–51. [Google Scholar] [CrossRef]
- Kamel, R.M.; El Mougy, A. Retrospective sensing based on federated learning in the IoT. In Proceedings of the 2020 IEEE 45th LCN Symposium on Emerging Topics in Networking (LCN Symposium), Sydney, Australia, 16–19 November 2020; pp. 150–161. [Google Scholar]
- Kim, S.; Cai, H.; Hua, C.; Gu, P.; Xu, W.; Park, J. Collaborative anomaly detection for internet of things based on federated learning. In Proceedings of the 2020 IEEE/CIC International Conference on Communications in China (ICCC), Chongqing, China, 9–11 August 2020; pp. 623–628. [Google Scholar]
- Mertens, J.; Galluccio, L.; Morabito, G. Federated learning through model gossiping in wireless sensor networks. In Proceedings of the 2021 IEEE International Black Sea Conference on Communications and Networking (BlackSeaCom), Bucharest, Romania, 24–28 May 2021; pp. 1–6. [Google Scholar]
- Banerjee, J.; Maiti, S.; Chakraborty, S.; Dutta, S.; Chakraborty, A.; Banerjee, J.S. Impact of Machine Learning in Various Network Security Applications. In Proceedings of the 2019 3rd International Conference on Computing Methodologies and Communication (ICCMC), Erode, India, 27–29 March 2019; pp. 276–281. [Google Scholar] [CrossRef]
- Wang, S.; Tuor, T.; Salonidis, T.; Leung, K.K.; Makaya, C.; He, T.; Chan, K. Adaptive federated learning in resource constrained edge computing systems. IEEE J. Sel. Areas Commun. 2019, 37, 1205–1221. [Google Scholar] [CrossRef]
- Zahariadis, T.; Trakadas, P.; Maniatis, S.; Karkazis, P.; Leligou, H.C.; Voliotis, S. Efficient detection of routing attacks in wireless sensor networks. In Proceedings of the 2009 16th International Conference on Systems, Signals and Image Processing, Chalkida, Greece, 18–20 June 2009; pp. 1–4. [Google Scholar]
- Loo, C.E.; Ng, M.Y.; Leckie, C.; Palaniswami, M. Intrusion detection for routing attacks in sensor networks. Int. J. Distrib. Sens. Netw. 2006, 2, 313–332. [Google Scholar] [CrossRef]
- Amouri, A.; Alaparthy, V.T.; Morgera, S.D. Cross layer-based intrusion detection based on network behavior for IoT. In Proceedings of the 2018 IEEE 19th Wireless and Microwave Technology Conference (WAMICON), Sand Key, FL, USA, 9–10 April 2018; pp. 1–4. [Google Scholar] [CrossRef]
- Pande, S.; Khamparia, A.; Gupta, D. Feature selection and comparison of classification algorithms for wireless sensor networks. J. Ambient. Intell. Humaniz. Comput. 2021, 1–13. [Google Scholar] [CrossRef]
- Almomani, I.; Al-Kasasbeh, B.; Al-Akhras, M. WSN-DS: A Dataset for Intrusion Detection Systems in Wireless Sensor Networks. J. Sens. 2016, 2016. [Google Scholar] [CrossRef]
- Tavallaee, M.; Bagheri, E.; Lu, W.; Ghorbani, A.A. A detailed analysis of the KDD CUP 99 data set. In Proceedings of the 2009 IEEE Symposium on Computational Intelligence for Security and Defense Applications, Ottawa, ON, Canada, 8–10 July 2009; pp. 1–6. [Google Scholar]
- Sharafaldin, I.; Lashkari, A.H.; Ghorbani, A.A. Toward generating a new intrusion detection dataset and intrusion traffic characterization. ICISSp 2018, 1, 108–116. [Google Scholar]
- Moustafa, N.; Slay, J. UNSW-NB15: A comprehensive data set for network intrusion detection systems (UNSW-NB15 network data set). In Proceedings of the 2015 Military Communications and Information Systems Conference (MilCIS), Canberra, Australia, 10–12 November 2015; pp. 1–6. [Google Scholar]
- Tharwat, A. Classification assessment methods. Appl. Comput. Inform. 2018, 17, 168–192. [Google Scholar] [CrossRef]
- Panda, M.; Abd Allah, A.M.; Hassanien, A.E. Developing an Efficient Feature Engineering and Machine Learning Model for Detecting IoT-Botnet Cyber Attacks. IEEE Access 2021, 9, 91038–91052. [Google Scholar] [CrossRef]
- Alsahli, M.S.; Almasri, M.M.; Al-Akhras, M.; Al-Issa, A.I.; Alawairdhi, M. Evaluation of Machine Learning Algorithms for Intrusion Detection System in WSN. Int. J. Adv. Comput. Sci. Appl. 2021, 12, 617–626. [Google Scholar] [CrossRef]
- Haber, S.; Stornetta, W.S. How to Time-Stamp a Digital Document. In Proceedings of the Advances in Cryptology-CRYPTO’ 90; Menezes; Menezes, A.J., Vanstone, S.A., Eds.; Springer: Berlin/Heidelberg, Germany, 1991; pp. 437–455. [Google Scholar]
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. Decentralized Bus. Rev. 2008, 21260. Available online: https://bitcoin.org/bitcoin.pdf (accessed on 21 August 2018).
- Wang, X.; Zha, X.; Ni, W.; Liu, R.P.; Guo, Y.J.; Niu, X.; Zheng, K. Survey on blockchain for Internet of Things. Comput. Commun. 2019, 136, 10–29. [Google Scholar] [CrossRef]
- Gao, W.; Hatcher, W.G.; Yu, W. A Survey of Blockchain: Techniques, Applications, and Challenges. In Proceedings of the 2018 27th International Conference on Computer Communication and Networks (ICCCN), Hangzhou, China, 30 July–2 August 2018; pp. 1–11. [Google Scholar] [CrossRef]
- Zhang, S.; Lee, J.H. Analysis of the main consensus protocols of blockchain. ICT Express 2020, 6, 93–97. [Google Scholar] [CrossRef]
- Gagneja, K.; Gagneja, K.; Kiefer, R. Security Protocol for Internet of Things (IoT): Blockchain-based Implementation and Analysis. In Proceedings of the 2020 Sixth International Conference on Mobile And Secure Services (MobiSecServ), Miami, FL, USA, 22–23 February 2020. [Google Scholar] [CrossRef]
- Monrat, A.A.; Schelén, O.; Andersson, K. A survey of blockchain from the perspectives of applications, challenges, and opportunities. IEEE Access 2019, 7, 117134–117151. [Google Scholar] [CrossRef]
- Hsiao, S.J. Employing Blockchain Technology to Strengthen Security of Wireless Sensor Networks. IEEE Access 2021, 9, 72326–72341. [Google Scholar] [CrossRef]
- Xu, R.; Chen, Y.; Blasch, E.; Chen, G. Blendcac: A blockchain-enabled decentralized capability-based access control for iots. In Proceedings of the IEEE 2018 International Congress on Cybermatics: 2018 IEEE Conferences on Internet of Things, Green Computing and Communications, Cyber, Physical and Social Computing, Smart Data, Blockchain, Computer and Information Technology, iThings/Gree Halifax, Halifax, NS, Canada, 30 July–3 August 2018; pp. 1027–1034. [Google Scholar] [CrossRef]
- Khalil, A.A.; Franco, J.; Parvez, I.; Uluagac, S.; Rahman, M.A. A Literature Review on Blockchain-enabled Security and Operation of Cyber-Physical Systems. In Proceedings of the 2022 IEEE 46th Annual Computers, Software, and Applications Conference (COMPSAC), Los Alamitos, CA, USA, 27 June–1 July 2022. [Google Scholar]
- Cui, Z.; Xue, F.; Zhang, S.; Cai, X.; Cao, Y.; Zhang, W.; Chen, J. A Hybrid BlockChain-Based Identity Authentication Scheme for Multi-WSN. IEEE Trans. Serv. Comput. 2020, 13, 241–251. [Google Scholar] [CrossRef]
- Mamdouh, M.; Awad, A.I.; Khalaf, A.A.; Hamed, H.F. Authentication and Identity Management of IoHT Devices: Achievements, Challenges, and Future Directions. Comput. Secur. 2021, 111, 102491. [Google Scholar] [CrossRef]
- Salimitari, M.; Chatterjee, M. A Survey on Consensus Protocols in Blockchain for IoT Networks. arXiv 2018, arXiv:1809.05613v4, 1–15. [Google Scholar]
- Mohanta, B.K.; Panda, S.S.; Jena, D. An overview of smart contract and use cases in blockchain technology. In Proceedings of the 2018 9th International Conference on Computing, Communication and Networking Technologies (ICCCNT), Bengaluru, India, 10–12 July 2018; pp. 1–4. [Google Scholar]
- Teslya, N.; Ryabchikov, I. Blockchain platforms overview for industrial IoT purposes. In Proceedings of the Conference of Open Innovation Association, FRUCT, Jyvaskyla, Finland, 15–18 May 2018; pp. 250–256. [Google Scholar] [CrossRef]
- Ismail, S.; Reza, H.; Zadeh, H.K.; Vasefi, F. A Blockchain-based IoT Security Solution Using Multichain. In Proceedings of the 2023 IEEE 13th Annual Computing and Communication Workshop and Conference (CCWC), Las Vegas, NV, USA, 8–11 March 2023; pp. 1105–1111. [Google Scholar] [CrossRef]
- Alkurdi, F.; Elgendi, I.; Munasinghe, K.S.; Sharma, D.; Jamalipour, A. Blockchain in IoT Security: A Survey. In Proceedings of the 2018 28th International Telecommunication Networks and Applications Conference, ITNAC 2018, Sydney, Australia, 21–23 November 2018; pp. 1–4. [Google Scholar] [CrossRef]
- Liu, Y.; Yu, F.R.; Li, X.; Ji, H.; Leung, V.C. Blockchain and Machine Learning for Communications and Networking Systems. IEEE Commun. Surv. Tutor. 2020, 22, 1392–1431. [Google Scholar] [CrossRef]
- Honar Pajooh, H.; Rashid, M.; Alam, F.; Demidenko, S. Hyperledger fabric blockchain for securing the edge internet of things. Sensors 2021, 21, 359. [Google Scholar] [CrossRef]
- Tian, Y.; Wang, Z.; Xiong, J.; Ma, J. A Blockchain-Based Secure Key Management Scheme With Trustworthiness in DWSNs. IEEE Trans. Ind. Inform. 2020, 16, 6193–6202. [Google Scholar] [CrossRef]
- Goyat, R.; Kumar, G.; Alazab, M.; Saha, R.; Thomas, R.; Rai, M.K. A secure localization scheme based on trust assessment for WSNs using blockchain technology. Future Gener. Comput. Syst. 2021, 125, 221–231. [Google Scholar] [CrossRef]
- Guerrero-Sanchez, A.E.; Rivas-Araiza, E.A.; Gonzalez-Cordoba, J.L.; Toledano-Ayala, M.; Takacs, A. Blockchain mechanism and symmetric encryption in a wireless sensor network. Sensors 2020, 20, 2798. [Google Scholar] [CrossRef]
- Rathee, G.; Balasaraswathi, M.; Chandran, K.P.; Gupta, S.D.; Boopathi, C. A secure IoT sensors communication in industry 4.0 using blockchain technology. J. Ambient. Intell. Humaniz. Comput. 2021, 12, 533–545. [Google Scholar] [CrossRef]
- Ismail, S.; Dawoud, D.; Reza, H. Towards A Lightweight Identity Management and Secure Authentication for IoT Using Blockchain. In Proceedings of the 2022 IEEE World AI IoT Congress (AIIoT), Seattle, WA, USA, 6–9 June 2022; pp. 77–83. [Google Scholar] [CrossRef]
- Miraz, M.H. Blockchain of things (BCoT): The fusion of blockchain and IoT technologies. In Advanced Applications of Blockchain Technology; Springer: Berlin/Heidelberg, Germany, 2020; pp. 141–159. [Google Scholar]
- Biswas, S.; Sharif, K.; Li, F.; Nour, B.; Wang, Y. A scalable blockchain framework for secure transactions in IoT. IEEE Internet Things J. 2019, 6, 4650–4659. [Google Scholar] [CrossRef]
- Kushch, S.; Prieto-Castrillo, F. A rolling blockchain for a dynamic WSNs in a smart city. arXiv 2018, arXiv:1806.113991, 1–8. [Google Scholar]
- Lao, L.; Li, Z.; Hou, S.; Xiao, B.; Guo, S.; Yang, Y. A survey of IoT applications in blockchain systems: Architecture, consensus, and traffic modeling. ACM Comput. Surv. (CSUR) 2020, 53, 1–32. [Google Scholar] [CrossRef]
- Zamani, M.; Movahedi, M.; Raykova, M. RapidChain: Scaling blockchain via full sharding. In Proceedings of the ACM Conference on Computer and Communications Security, Toronto, ON, Canada, 15–19 October 2018. [Google Scholar] [CrossRef]
- Cherupally, S.R.; Boga, S.; Podili, P.; Kataoka, K. Lightweight and Scalable DAG based distributed ledger for verifying IoT data integrity. Int. Conf. Inf. Netw. 2021, 2021, 267–272. [Google Scholar] [CrossRef]
- Buldin, I.D.; Gorodnichev, M.G.; Makhrov, S.S.; Denisova, E.N. Next Generation Industrial Blockchain-Based Wireless Sensor Networks. In Proceedings of the 2018 Wave Electronics and its Application in Information and Telecommunication Systems (WECONF), Saint Petersburg, Russia, 3–7 June 2018; pp. 1–5. [Google Scholar] [CrossRef]
- Baig, M.A.; Ali Sunny, D.; Alqahtani, A.; Alsubai, S.; Binbusayyis, A.; Muzammal, M. A Study on the Adoption of Blockchain for IoT Devices in Supply Chain. Comput. Intell. Neurosci. 2022, 2022, 9228982. [Google Scholar] [CrossRef]
- Goyal, H.; Saha, S. Reli: Real-time lightweight byzantine consensus in low-power iot-systems. In Proceedings of the 2022 18th International Conference on Network and Service Management (CNSM), Thessaloniki, Greece, 31 October–4 November 2022; pp. 275–281. [Google Scholar]
- Gopalakrishnan, K. Security vulnerabilities and issues of traditional wireless sensors networks in IoT. In Principles of Internet of Things (IoT) Ecosystem: Insight Paradigm; Springer: Berlin/Heidelberg, Germany, 2020; pp. 519–549. [Google Scholar]
- Waheed, N.; He, X.; Ikram, M.; Usman, M.; Hashmi, S.S.; Usman, M. Security and Privacy in IoT Using Machine Learning and Blockchain: Threats and Countermeasures. ACM Comput. Surv. 2021, 53, 1–37. [Google Scholar] [CrossRef]
- Marchang, J.; Ibbotson, G.; Wheway, P. Will blockchain technology become a reality in sensor networks? In Proceedings of the 2019 Wireless Days (WD), Manchester, UK, 24–26 April 2019; pp. 1–4. [Google Scholar]
- Shammar, E.A.; Zahary, A.T.; Al-Shargabi, A.A. A survey of IoT and blockchain integration: Security perspective. IEEE Access 2021, 9, 156114–156150. [Google Scholar] [CrossRef]
- She, W.; Liu, Q.; Tian, Z.; Chen, J.S.; Wang, B.; Liu, W. Blockchain trust model for malicious node detection in wireless sensor networks. IEEE Access 2019, 7, 38947–38956. [Google Scholar] [CrossRef]
- Arifeen, M.M.; Al Mamun, A.; Ahmed, T.; Kaiser, M.S.; Mahmud, M. A Blockchain-Based Scheme for Sybil Attack Detection in Underwater Wireless Sensor Networks. In Proceedings of International Conference on Trends in Computational and Cognitive Engineering; Kaiser, M.S., Bandyopadhyay, A., Mahmud, M., Ray, K., Eds.; Springer: Singapore, 2021; pp. 467–476. [Google Scholar]
- Chanana, R.; Singh, A.K.; Killa, R.; Agarwal, S.; Mehra, P.S. Blockchain Based Secure Model for Sensor Data in Wireless Sensor Network. In Proceedings of the 2020 6th International Conference on Signal Processing and Communication (ICSC), Noida, India, 5–7 March 2020; pp. 288–293. [Google Scholar] [CrossRef]
- Mubarakali, A. An efficient authentication scheme using blockchain technology for wireless sensor networks. Wirel. Pers. Commun. 2021, 1, 1–15. [Google Scholar] [CrossRef]
- Sivaganesan, D. A data driven trust mechanism based on blockchain in IoT sensor networks for detection and mitigation of attacks. J. Trends Comput. Sci. Smart Technol. (TCSST) 2021, 3, 59–69. [Google Scholar]
- Karakoç, E.; Çeken, C. Black hole attack prevention scheme using a blockchain-block approach in SDN-enabled WSN. Int. J. Hoc Ubiquitous Comput. 2021, 37, 37–49. [Google Scholar] [CrossRef]
- Soltani, R.; Saxena, L.; Joshi, R.; Sampalli, S. Protecting Routing Data in WSNs with use of IOTA Tangle. Procedia Comput. Sci. 2022, 203, 197–204. [Google Scholar] [CrossRef]
- Javed, S.; Khan, M.A.; Abdullah, A.M.; Alsirhani, A.; Alomari, A.; Noor, F.; Ullah, I. An Efficient Authentication Scheme Using Blockchain as a Certificate Authority for the Internet of Drones. Drones 2022, 6, 264. [Google Scholar] [CrossRef]
- Lazrag, H.; Chehri, A.; Saadane, R.; Rahmani, M.D. Efficient and secure routing protocol based on Blockchain approach for wireless sensor networks. Concurr. Comput. Pract. Exp. 2021, 33, e6144. [Google Scholar] [CrossRef]
- Awan, S.; Javaid, N.; Ullah, S.; Khan, A.U.; Qamar, A.M.; Choi, J.G. Blockchain Based Secure Routing and Trust Management in Wireless Sensor Networks. Sensors 2022, 22, 411. [Google Scholar] [CrossRef]
- Chen, Y.; Yang, X.; Li, T.; Ren, Y.; Long, Y. A blockchain-empowered authentication scheme for worm detection in wireless sensor network. Digit. Commun. Netw. 2022. [CrossRef]
- Almaiah, M.A. A New Scheme for Detecting Malicious Attacks in Wireless Sensor Networks Based on Blockchain Technology. In Artificial Intelligence and Blockchain for Future Cybersecurity Applications; Maleh, Y., Baddi, Y., Alazab, M., Tawalbeh, L., Romdhani, I., Eds.; Springer International Publishing: Cham, Switzerland, 2021; pp. 217–234. [Google Scholar] [CrossRef]
- Moinet, A.; Darties, B.; Baril, J.L. Blockchain based trust & authentication for decentralized sensor networks. arXiv 2017, arXiv:1706.01730. [Google Scholar]
- Kim, T.H.; Goyat, R.; Rai, M.K.; Kumar, G.; Buchanan, W.J.; Saha, R.; Thomas, R. A novel trust evaluation process for secure localization using a decentralized blockchain in wireless sensor networks. IEEE Access 2019, 7, 184133–184144. [Google Scholar] [CrossRef]
- Pundir, S.; Wazid, M.; Singh, D.P.; Das, A.K.; Rodrigues, J.J.P.C.; Park, Y. Intrusion detection protocols in wireless sensor networks integrated to Internet of Things deployment: Survey and future challenges. IEEE Access 2019, 8, 3343–3363. [Google Scholar] [CrossRef]
- Revanesh, M.; Sridhar, V. A trusted distributed routing scheme for wireless sensor networks using blockchain and meta-heuristics-based deep learning technique. Trans. Emerg. Telecommun. Technol. 2021, 32, e4259. [Google Scholar] [CrossRef]
- Nouman, M.; Qasim, U.; Nasir, H.; Almasoud, A.; Imran, M.; Javaid, N. Malicious Node Detection using Machine Learning and Distributed Data Storage using Blockchain in WSNs. IEEE Access 2023, 11, 6106–6121. [Google Scholar] [CrossRef]
- Yang, X.; Chen, Y.; Qian, X.; Li, T.; Lv, X. BCEAD: A blockchain-empowered ensemble anomaly detection for wireless sensor network via isolation forest. Secur. Commun. Netw. 2021, 2021, 9430132. [Google Scholar] [CrossRef]
- Sajid, M.B.E.; Ullah, S.; Javaid, N.; Ullah, I.; Qamar, A.M.; Zaman, F. Exploiting Machine Learning to Detect Malicious Nodes in Intelligent Sensor-Based Systems Using Blockchain. Wirel. Commun. Mob. Comput. 2022, 9, 24695–24707. [Google Scholar] [CrossRef]
- Yang, J.; He, S.; Xu, Y.; Chen, L.; Ren, J. A trusted routing scheme using blockchain and reinforcement learning for wireless sensor networks. Sensors 2019, 19, 970. [Google Scholar] [CrossRef]
- Abd El-Moghith, I.A.; Darwish, S.M. Towards designing a trusted routing scheme in wireless sensor networks: A new deep blockchain approach. IEEE Access 2021, 9, 103822–103834. [Google Scholar] [CrossRef]
- Rajasoundaran, S.; Kumar, S.; Selvi, M.; Ganapathy, S.; Rakesh, R.; Kannan, A. Machine learning based volatile block chain construction for secure routing in decentralized military sensor networks. Wirel. Netw. 2021, 27, 4513–4534. [Google Scholar] [CrossRef]
- Puthal, D.; Mohanty, S.P.; Nanda, P.; Kougianos, E.; Das, G. Proof-of-Authentication for Scalable Blockchain in Resource-Constrained Distributed Systems. In Proceedings of the 2019 IEEE International Conference on Consumer Electronics (ICCE), Berlin, Germany, 8–11 September 2019; pp. 1–5. [Google Scholar] [CrossRef]
- Mingxiao, D.; Xiaofeng, M.; Zhe, Z.; Xiangwei, W.; Qijun, C. A review on consensus algorithm of blockchain. In Proceedings of the 2017 IEEE International Conference on Systems, Man, and Cybernetics (SMC), Banff, AB, Canada, 5–8 October 2017; pp. 2567–2572. [Google Scholar] [CrossRef]
- Zhou, Q.; Zheng, K.; Zhang, K.; Hou, L.; Wang, X. Vulnerability Analysis of Smart Contract for Blockchain-Based IoT Applications: A Machine Learning Approach. IEEE Internet Things J. 2022, 9, 24695–24707. [Google Scholar] [CrossRef]
- Wang, S.Y.; Hsu, Y.J.; Hsiao, S.J. Integrating blockchain technology for data collection and analysis in wireless sensor networks with an innovative implementation. In Proceedings of the 2018 International Symposium on Computer, Consumer and Control (IS3C), Taichung, Taiwan, 6–8 December 2018; pp. 149–152. [Google Scholar]
- Omar, S.; Ngadi, A.; Jebur, H.H. Machine learning techniques for anomaly detection: An overview. Int. J. Comput. Appl. 2013, 79, 33–41. [Google Scholar] [CrossRef]
- Zhao, J.; Shetty, S.; Pan, J.W.; Kamhoua, C.; Kwiat, K. Transfer learning for detecting unknown network attacks. Eurasip J. Inf. Secur. 2019, 2019, 1. [Google Scholar] [CrossRef]
- Lu, Y.; Tang, Q.; Wang, G. On enabling machine learning tasks atop public blockchains: A crowdsourcing approach. In Proceedings of the 2018 IEEE International Conference on Data Mining Workshops (ICDMW), Singapore, 17–20 November 2018; pp. 81–88. [Google Scholar]
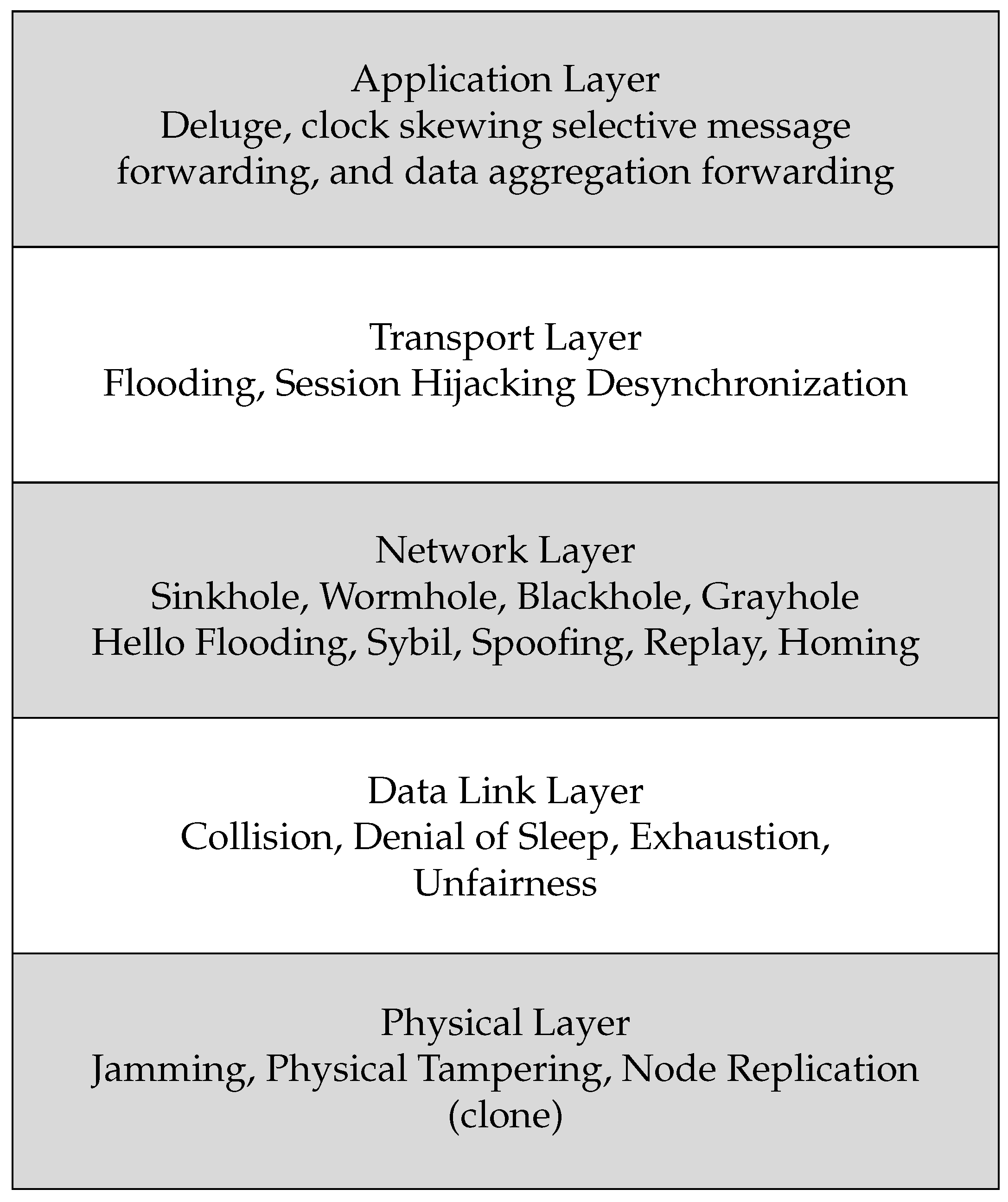

| Attack Type | Affected Stack Layer | Attack Name | Definition |
|---|---|---|---|
| Active | Multi-layer | Man-in-the-Middle | A malicious node intercepts a message passing between two sensor nodes with the aim of modifying, injecting, or deleting content before relaying the message again. |
| Denial-of-Service | An attacker performs malicious activities to prevent original users from accessing system resources. | ||
| Distributed Denial-of-Service | A more powerful version of DoS attack that overwhelms the targeted nodes with excessive messages to exhaust their resources, leading to a system overload that prevents it from answering some or all legitimate messages. | ||
| Application | Deluge | An attacker tries to remotely reprogram a sensor node. | |
| Misdirection | An attacker forwards packets to the wrong destinations or paths by misdirecting packets or altering routes towards a malicious node. | ||
| Clock skewing | Disrupts sensors that requir synchronization for successful communication; an attacker desynchronizes sensor clocks by generating false timing information, leading to desynchronization of the victim nodes. | ||
| Selective Forwarding | Malicious nodes drop a portion of a received message while forwarding most of the message, impacting data integrity. | ||
| Transport | Flooding | An attacker sends a large number of useless packets to a legitimate node, preventing it from communicating normally and consuming its resources. | |
| Session Hijacking | An attacker exploits a valid session, pretends to be a victim node, and obtains fake access to the session. | ||
| De-synchronization | An attacker intercepts sequence numbers or controls flag packets that it attempts to forge; if the attacker can desynchronize two communicating nodes, the receiver node must request retransmission from the sender for the lost packet. Frequent retransmission consumes network resources and increases traffic over the network. | ||
| Network | Reply | An attacker records the messages sent between nodes and re-transmits them later to waste the target node’s resources. | |
| Selective Forwarding or Grayhole | A malicious node selectively, constantly, or randomly drops packets while forwarding the remaining packets to a particular destination, which happens when relay nodes do not forward messages they receive. | ||
| Neglect and Greed | A special case of selective forwarding attack in which the attacker arbitrarily drops some of the received packets while acknowledging the source node (neglect attack) or sends its own packets with higher priority to other nodes (greed attack) [49]. | ||
| Homing | An attacker analyzes traffic using a traffic pattern analysis algorithm to recognize the nodes with special responsibilities, such as cluster heads (CHs) or base station (BS), which are the attack targets. Afterwards, additional DoS attacks may be launched toward these nodes to jam or destroy them. | ||
| Spoofing | An attacker forges its identity by impersonating another node and falsifying the identity field in routing messages to launch DoS attacks by injecting fraudulent data packets, such as falsely advertising services to other nodes or providing incorrect routing and control information to compromise network operation [50]. | ||
| Blackhole | A malicious node, usually located in the center, does not forward traffic and drops the packets completely. | ||
| Wormhole | A collusion-based attack in which two or more malicious nodes create a low-latency data delivery tunnel between two or more malicious nodes to perform other attacks, such as a blackhole attack. For instance, the nodes may establish a low-latency tunnel by which one malicious node misroutes the packets to be forwarded and sends them to its partner using a faked routing path to disrupt routing operations in the network. | ||
| Sybil | A single attacker node assumes several identities or steals them from other authorized nodes to create several sybil nodes that can be virtually present in different neighborhoods, then attack the network to cause problems with multipath routing, network topology, storage access, and detection [50]. | ||
| Sinkhole | A malicious node identifies itself as a blackhole to attract network traffic. The attacker observes path requests and falsely offers the shortest or most power-efficient paths to the BS. As the attacker is in the relay path between the communicating nodes, it is able to change or alter the packets passing between them [44]. | ||
| Hello Flooding | An attacker broadcasts advertisement ‘Hello’ messages with high power, asking network nodes to join an existing WSN and tricking the nodes into believing that it is located in their neighborhood. The nodes choose to route their packets through the attacker, which has a longer transmission range than normal nodes, leading to additional delays and energy waste. | ||
| Data link | Collision | An attacker sends signals while another node is transmitting a message, causing interference that alters data packets or causes them to be considered invalid. Collision usually occurs when multiple nodes transmit data at the same frequency and data rate. | |
| Denial of Sleep (Sleep Deprivation) | A Malicious node prevents legitimate nodes from entering low-power sleep mode, causing them to keep wasting their energy [51]. | ||
| Power Exhaustion | In order to drain the victim node’s power, an attacker sends packets over the channel continually by requesting calculations or the receipt or transmission of unnecessary data, which leads to starvation. The source of the attack can be a PC or laptop. | ||
| Unfairness | A malicious node continuously sends packets without waiting a reasonable time to let other nodes use the channel. This is a kind of exhaustion-based attack which disrupts equal load sharing in the WSN. | ||
| Physical | Jamming | An attacker sends a radio signal that interferes with the sensor network’s use of certain radio frequencies. | |
| Physical or Node Tampering | An attacker physically accesses a compromised node and takes over the control, for example, to obtain sensitive information such as transmission keys [52,53]. | ||
| Node Replication or Clone | An attacker captures a compromised node, obtains access to the stored credentials, purposefully duplicates the node’s identity, and then deploys clones in key positions of the WSN [54] to initiate different internal attacks. | ||
| Passive | Camouflage Adversaries | A camouflaged node deceives the other nodes and attract packets from them in order to either misroute the packets or eventually drop the packets. | |
| Eavesdropping and Traffic Analysis | The most common attack on privacy, also called sniffing or snooping, where an attacker simply discovers the content of communications. | ||
| Passive Information Gathering | If the content of messages from network communication media, such as message identification numbers (IDs), nodes locations, and timestamps, is not encrypted then an attacker with the appropriate receiver can collect and observe the information. | ||
| Replay or Duplication | An attacker copies a stream of messages between communicating nodes, then replays the stream to one or more of the nodes [55] |
| BC | ML | Ref. | Attack | Study Highlights |
|---|---|---|---|---|
| Public | Deep CNN | [151] | Internal | Trusted distributed routing using BC while avoiding routing paths with congestion and malicious nodes using DL-CNN |
| Hidden Markov Model (HMM) | [137] | Sybil | Trust model for identifying Sybil nodes; trust value is evaluated via HMM, and the trust values are then added to the BC | |
| Histogram Gradient Boost (HGB) | [152] | DoS | BC-based authentication mechanism in which IPFS is integrated with BC for data storage, and HGB detection module to mitigate DoS attacks | |
| Private | Isolated forest algorithm | [153] | Internal | Isolated forest algorithm for anomaly detection in the BC |
| Genetic Algorithm (GA)-based SVM and GA-based DT | [154] | Grayhole, mistreatment, and MITM | ML models for malicious node detection and registration along with authentication mechanism and data storage routing using BC | |
| Consortium | RL | [155] | Blackhole | Trusted routing with the use of BC and reinforcement learning |
| DNN | [156] | Routing, specifically Blackhole | Trusted routing with the use of BC and DNN | |
| Hybrid | Gaussian NB | [122] | Internal | BC-based identity management and secure authentication mechanism with Gaussian NB detection module to mitigate DoS attacks |
| N/A | Generative Adversarial Networks (GAN) | [157] | Network layer | Authentication and validation of current routing data using a Generative Adversarial Network-based BC-enabled secured routing protocol |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ismail, S.; Dawoud, D.W.; Reza, H. Securing Wireless Sensor Networks Using Machine Learning and Blockchain: A Review. Future Internet 2023, 15, 200. https://doi.org/10.3390/fi15060200
Ismail S, Dawoud DW, Reza H. Securing Wireless Sensor Networks Using Machine Learning and Blockchain: A Review. Future Internet. 2023; 15(6):200. https://doi.org/10.3390/fi15060200
Chicago/Turabian StyleIsmail, Shereen, Diana W. Dawoud, and Hassan Reza. 2023. "Securing Wireless Sensor Networks Using Machine Learning and Blockchain: A Review" Future Internet 15, no. 6: 200. https://doi.org/10.3390/fi15060200
APA StyleIsmail, S., Dawoud, D. W., & Reza, H. (2023). Securing Wireless Sensor Networks Using Machine Learning and Blockchain: A Review. Future Internet, 15(6), 200. https://doi.org/10.3390/fi15060200








