Abstract
The tremendous growth of about 8 billion devices connected to each other in various domains of Internet of Things (IoT)-based applications have attracted researchers from both industry and academia. IoT is a network of several devices connected with each other to provide sensing capabilities, particularly in smart grid (SG) environment. Various challenges such as the efficient handling of massive IoT data can be addressed with advances in fog computing. The secure data aggregation challenge is one such issue in IoT-based smart grid systems, which include millions of smart meters. Typical SG-based data aggregation approaches have high computation and communication costs, however, many efforts have been made to overcome these limitations while leveraging fog computing but no satisfactory results have been obtained. Moreover, existing solutions also suffer from high storage requirements. The traditional data aggregation schemes such as GCEDA (Grouping of Clusters for Efficient Data Aggregation) and SPPDA (Secure Privacy-Preserving Data Aggregation) also suffer from a few shortcomings. SPPDA follows a mixed aggregation architecture that includes trees and clusters which can lead to some performance complexities and is not energy-efficient, whereas GCEDA does not support heterogeneity. To overcome these problems, this research provides a fog-assisted strategy for secure and efficient data aggregation in smart grid. The concept of smart grid is implemented in fog environment, which was not the case in previous schemes. We used communication between smart meters (SMs) and fog nodes (FNs) to transmit confidential data in compressed form towards FN. The FN further aggregates the received data which can then be updated in cloud repositories later. We presented two algorithms—data aggregation and data extraction at FN and cloud, respectively, to achieve secure communication. The performance of the proposed strategy has been evaluated against existing data aggregation techniques GCEDA and SPPDA for various performance parameters such as storage, communication cost and transmission cost. The proposed scheme overcomes the limitation of heterogeneity and mixed aggregation which was faced in GCEDA and SPPDA and the results revealed outstanding performance in comparison with both, so the proposed solution can be used in a smart grid environment for efficient and secure data transmission.
1. Introduction
The Internet of Things (IoT) is a vast interconnection of smart devices performing sensing and data sharing across multiple servers and depositories. IoT leads to an increase in the use of smart devices in various fields. The smart grid (SG) is one such next-generation network. The integration of information with communication technologies in power grid operations has led to the evolution of smart grid architecture, enabling it to regulate generation and consumption of electricity [1]. IoT has changed the face of traditional power systems—the new structure incorporated bigger databases, new matrices and innovations, whereas the others were still facing security challenges [2]. It is not a fiction as nowadays SG might also be used in conjunction with an existing power grid in many utility companies. It can be used to enhance the performance and reliability of the system by establishing two-way communication using advanced sensors [3]. As a result, utility firms may enhance the production, transmission, circulation and control of power [4]. Furthermore, the SG-IoT network provides companies with the ability to analyze and diagnose faults which can help prevent any kind of power outages; along with this, they can predict power demands, streamline the billing procedure and incorporate distributed renewable energy resources into the grid smoothly [5]. SG [6,7] has a lot of possible security and privacy issues. For example, utility firms utilize metering data to support operational strategies such as power demand estimates and to efficiently regulate and optimize power supply and distribution. However, it is evident that such data analysis raises privacy issues. Furthermore, a hostile attacker might try to collect user data consumption and extrapolate personal information from it (such as living behaviours, financial position, etc.) [8].
In typical data aggregation techniques for SG, it is the responsibility of the gateway to combine Smart Metre (SM) readings and transfer them to the Control Centre (CC). As transmitting single SM readings might compromise one’s privacy, data aggregation is a better option. The values of SG parameters are concatenated to create data aggregation. Delimiters may be used to designate the beginning and end points of parameters. They also rely on the type of application [9]. The following are the well-known categories in SG-IoT environments: (1) Static nodes and sinks: To monitor power consumption in smart homes where SMs are fixed, data from each SMs are sent to FNs in a cyclic/acyclic way, which may then be shared with cloud servers at massive data depositories; (2) Moveable sensor nodes with fixed sink: The sink is stationary, whereas the sensor nodes are moveable, similar to persons who wear smart wearables and work or stroll outside. The aggregation related to data consumption is computed at FNs positioned at fixed location. (3) Mobile sensor nodes and sinks: IoT-enabled WSNs (Wireless Sensor Networks) in the third category are utilised for monitoring purposes all over the world. Both the sink and sensor nodes are movable in this category, making it difficult to determine the optimum pathways that are always changing owing to the movement of SMs and the FN.
A basic SG-IoT network design has a number of smart devices linked to a smart meter, which stores the consumption of every device and sends it to a gateway known as an aggregator. The SM readings are delivered in an encrypted form to protect user privacy. Before delivering encrypted readings to a CC, the aggregator is in charge of gathering them. This saves time while maintaining privacy. Here, fog nodes also plays an important role—they act as an independent device in fog environment having capability to perform functions such as data processing and storing on their own, instead of sending data all the way to the cloud. They also helps in fast response and reduce latency as all the work is done close to the end device.
A variety of cloud-based smart grid systems [10,11] have been developed recently, where smart meters send consumption data to the cloud. This information can be used for billing purposes, predictive analytics and forecasting power demands, among other things. The process of sending data to the cloud can be time-consuming and a reason for latency in case of a large number of SMs. In addition, communication of large-size data from each SM would add extra transmission overhead and high delay in the network. To overcome these restrictions, we may utilize fog computing [12] to partially transfer the processing and storage capabilities of the cloud to the terminal device’s edge. Further, to reduce bottleneck during transmission, data from SMs can be sent in compressed form in an acyclic fashion.
The FNs execute data aggregation in the cloud-fog-based aggregation techniques [10,11,13] and SMs perform data compression for transmission at FN. On the other hand, in typical aggregation approaches, the “aggregator” is intended to aggregate and supply storage. However, in classic systems, the aggregator is not a distinct component. It can be any network device. Using FNs to execute data aggregation, we may use fog computing’s characteristics for effective communication, processing and storage (as indicated by previous fog-enabled approaches) for safe data aggregation. We may use the inherent data aggregation to perform the data aggregation.
This research describes a fog-assisted data aggregation strategy for Smart Grid (SG) that makes use of communication between SMs and FNs. We have suggested work with current schemes for data aggregation techniques employing SMs, FNs, cloud and control centre. We have highlighted how fog nodes can be used for SM- to-FN level connection to efficiently share data and reduce transmission costs. Moreover, data aggregation algorithm at FNs and data extraction algorithm at cloud server are also presented. The proposed scheme aids in monitoring and saving of values in a cyclic exchange method based on a specified delay with fog nodes which can further be shared with cloud repositories. A query request is initiated by the FNs for obtaining data from SMs. Only those SMs which meet the condition of the query would be able to transmit responses. Each SM compresses its data and each FN aggregates data received from different SMs before sending to the FNs and cloud, respectively.
Problem Definition and Motivation
Security is the main concern while aggregating and forwarding the data, as there may be a case where a user’s sensitive information may get leaked by the sensor node. To overcome this, the previous schemes of GCEDA and SPPDA were proposed. SPPDA adopted a mixed data aggregation architecture which includes tree and cluster whereas GCEDA supports aggregation but does not aid heterogeneity. Moreover, these schemes have additional limitations, for example, they were not energy efficient, increase in size of the cluster leads to computation overhead and the whole procedure has been divided into inter and inner clusters, affecting the complexity. All these limitations made the above traditional schemes unsuitable for IoT-based fog environment where heterogeneity is the key requirement with scalability. In an overview, the main endeavours of our proposed scheme are:
- In the existing works, a huge amount of data is sent to BS across a point-to-point network which can lead to increase in communication costs. Schemes such as in [14,15,16] aggregate data without using any kind of compression method but only asymmetric keys, which increases communication costs owing to huge message length, memory requirements and computation time. The proposed scheme is capable of sending huge amount of data in an aggregated manner with a compression technique—securely and efficiently through the network;
- Previous schemes were not implemented in IoT-based fog environment, but the proposed approach makes use of this environment. Computation is high due to the large number of heterogeneous devices’ data which is challenging due to more energy consumption along with security constraint. The SDAFA scheme uses a compression technique before transmitting the data, which ensures the security as well as energy conservation;
- The proposed scheme uses timestamps to validate the data and if the timestamp expires for a message, then the message is rejected for real-time data of smart meters (this is done to avoid processing of the delayed data which is of no use after a certain amount of time because specific actions such as prediction of uncertain events requires instant action), whereas there was no equivalent to this in existing schemes;
- Based on the limitations we have studied in existing or previous work, a technique has been proposed that uses a three-layer model to reduce the communication cost and improve energy conservation as described in Algorithm 1, Section 5;
- We performed a comparative analysis with GCEDA and SPPDA for various performance parameters, such as storage space, communication cost and transmission cost, and proved that the proposed solution outperforms state-of-the-art techniques and can be used for efficient and secure data transmission in a smart grid environment.
The paper is organized as follows: Section 2 provides knowledge on related studies. The system model with various security goals and the identified problem is presented in Section 3. The problems identified in existing work and how they can be overcome by our work is discussed in Section 4. The proposed scheme for secure data aggregation in SG network is detailed in Section 5 along with data aggregation and data extraction algorithms. The validation of the proposed scheme is analyzed in Section 6. Lastly, Section 7 concludes the study.
2. Related Work
This section reviews the related work on data aggregations algorithms in IoT-enabled smart networks using various methodologies. Data aggregation helps to prevent recurring transmissions and ensures a single, secure message. It also effects the energy usage, since single-bit transmission in WSN-IoT requires around 50 nanojoules [17]. Multi-hop pathways are used in network aggregation to collect data by incorporating intermediary nodes for compute sharing. This lowers resource usage and extends the network’s lifespan [18]. There are two sorts of data aggregation techniques: arrangement-based and arrangement-free. The first one is not aware of other next-hop sensor nodes. Here, each sensor node sends data using its own identification and the other sensor node forwards data to the sink node. Cluster, Tree, Flat Network-based, and Grid-based methods are among the latter [19]. Formation of clusters improves communication in which various nodes share and distribute data among neighbouring nodes along with remote nodes [14]. Compression should be used in these circumstances to minimise data sizes and lower communication costs. Lossless compression and Lossy compression are the two forms of data compression. The former method assumes that no information is lost in any way. The original data may be recovered from compressed data without bit loss using the lossless data compression approach. In the latter technique, some data may be lost during data compression.
Presently existing fog-based data aggregation approaches in SG suffer from numerous drawbacks. Lyu et al. [10] developed an one-time-pad (OTP) homomorphic encryption-based privacy-preserving fog-enabled data aggregation technique (PPFA). Being hypothesized as unconditionally secure, OTP have certain drawbacks. First, the key must have the same length as the message. Second, OTP necessitates the creation of a new key each time an encryption is required. Third, moving/storing numerous keys is a time-consuming process. A fault-tolerant scheme with lower computational cost was proposed in [10], but it requires additional communication among FNs, TA (Trusted Authority), CC and SMs, leading to additional cost.
Wang et al. [11] suggested an anonymous fog-enabled SG data aggregation technique that effectively protects users’ privacy while also ensuring data integrity and metering data source authenticity. The authors employed a pairing-based signature system for data integration and source authentication of users’ data. On the other hand, the Weil-pairing-based signature technique is computationally costly when it comes to validating signatures. The writers have worked hard to maintain anonymity. Revocation of rogue terminal devices and FNs can also be accomplished quickly. Liu et al. [12] demonstrated a fog-based privacy-preservation scheme for SG data aggregation that enables the service provider for multiple function queries on encryption of meter data. The authors of [20,21,22,23,24] have worked on IoT applications and events where Markov model has been used. However, none of them is suitable for a smart grid environment.
However, these standard data aggregation approaches do not make use of the fog computing paradigm’s capabilities, and as a result, they suffer from latency concerns. Moreover, communication of large-size aggregated data on network introduces additional overhead and delay. To address this, various data aggregation schemes with data compression have also been proposed in the recent past. To this end, Xiaodong et al. [25] proposed a multidimensional aggregation approach that utilizes neighbour key finding and is safe. All sensor nodes communicate data in compressed form to data aggregation using this approach. The identification of participating sensing devices is not communicated to BS in this technique. Lalos et al. [26] offer a viable data exchange mechanism for vital sign monitoring data transmission. This paper suggests the use of cooperative compressed sensing (CCS) to compress signals. Table 1 shows the limitations of a few schemes that encouraged us to design the new scheme.

Table 1.
Comparison of a few existing fog-enabled data aggregation schemes.
3. System Model
The fog layer is located between the cloud and the IoT devices. It provides location awareness, networking and storage capabilities to bring cloud services and IoT devices closer [27]. As shown in Figure 1, we design a three-tier network hierarchy system for smart metering. IoT devices are highly dispersed devices with problem-solving and latency-sensitive requirements that are positioned at the network’s edge. We presume that there are SMs connected to their corresponding FNs at the bottom layer of the architecture. Electric appliance usage data are collected by the SMs and forwarded to their respective FNs. The FNs, which are the terminal device’s processing and storage resources, make up the intermediate layer. As FNs have computing capabilities, they can process and aggregate data coming from SMs, while cloud being at the top layer can cause latency. FNs being just a step away from network devices, sending data from end devices to FNs is more cost effective than sending all the way from the end to the cloud.
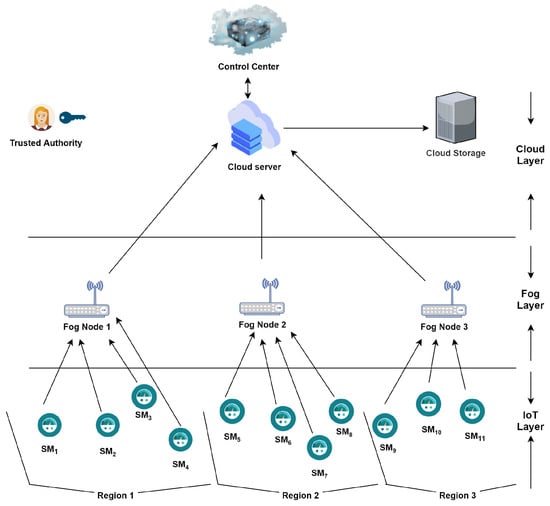
Figure 1.
A three-layered network hierarchical architecture for smart metering.
As the cloud collects the aggregated data from all the regions, fog nodes only aggregate the user’s data from connected SMs and forward them to the cloud. In data-intensive IoT, fog–cloud interaction solves latency and bandwidth concerns. We presume that all sensing devices, i.e., SMs are not sending data in a true cyclic fashion and are instead exchanging data according to a threshold delay or a request from the FN. It aids in avoiding the physical sensing bottleneck in an IoT-enabled WSN, and are communicating information gleaned from their senses. The data can be cached by the devices for a period of time to lessen the physical world’s sensing bottleneck. Different SMs share their data in this situation in order to prepare an aggregated message. The data received by the FNs can then be sent to the cloud server. Only three FNs are displayed in this scenario to demonstrate FN to SMs and FN to cloud connection and data aggregation. It can be scaled to a large number of FNs, where SMs are privileged to send data directly to the fog nodes. As shown in Figure 1, the system model of the proposed scheme consists of the following components.
3.1. Major Components
- Trusted Authority (TA): Being the most trustworthy component of the system, TA creates the secure public and private keys. In addition to this, it is capable of producing extra secret parameters and distributing them to every user and CC. Once the key distribution is complete, there is no use of TA in the data aggregation process.
- Smart Meters (SMs): It collects usage data for every appliance on a user’s property. Additionally, for the purposes of maintaining privacy, data integration and sender authentication, SMs can also undergo encryption operations. SMs can report their data consumption to their local fog node.
- Fog Nodes (FN): They play an important role in extending the cloud’s processing and the storage capabilities to network edge. In our suggested paradigm, FN is in charge of aggregating and transmitting user consumption data to CC. FN additionally ensures the metering data’s data integrity and source authenticity.
- Cloud: The cloud validates the integrity and source authentication of the aggregated data coming from the fog nodes before storing them.
- Control Center: The control center (CC) has cloud access and receives aggregated data from the FNs. It uses the secret key to decrypt the data and allows the user to consume the aggregated data.
Figure 2 shows all the major components of the scheme proposed in this paper.
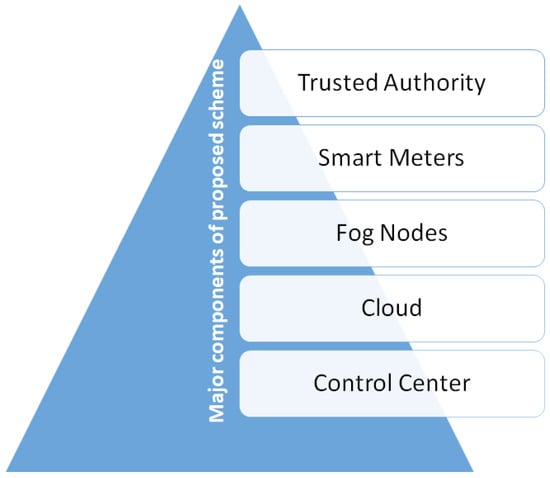
Figure 2.
Major components of the proposed scheme.
3.2. Security Goals
This subsection identifies the various security goals of the proposed scheme (Figure 3).
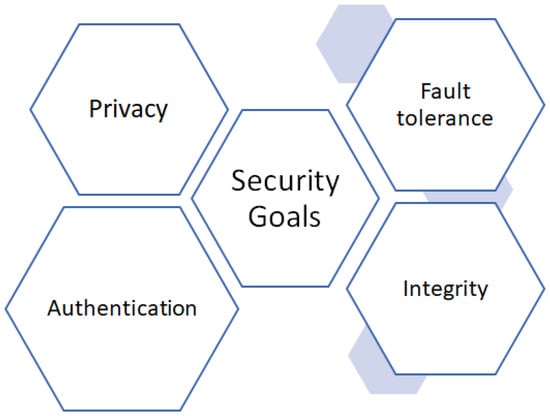
Figure 3.
Security goals of the proposed scheme.
- Privacy: In case data communicated over an unsecured channel are attacked by the attacker, adversary A will still not be capable of accessing the user’s data. There is no possibility for FN to decipher the user’s data so that FN’s security does not get jeopardize affecting the privacy of the user. In addition, CC decrypts data. Only aggregated data are available to CC after decryption; however, there is no means of obtaining data on an individual basis from each SM. As a result, individual privacy must be protected.
- Fault Tolerance: We assume that some SMs will be inactive for a period of time and will not provide FN with their consumption data. Our system being fault-tolerant will enable it to aggregate and decipher SM readings. Previous systems were incapable of solving the issue of fault tolerance leading to communication delays, as a result, the CC permission of TA for missing values was affected and it halts the data aggregation process. Our objective is to keep this delay as short as possible.
- Integrity: The integration of the metering data needs to be maintained, and unauthorized alteration of any type should be detected. If the reading of the meters has been changed, the fog node and control centre should notice it.
- Authentication: FN and CC are responsible for making sure that the data are coming from a trusted and authorized source only as the same secret key is shared with both SM and the associated FN. Similarly, CC validates the source authenticity of each FN’s aggregated data. It is necessary to avoid any fake values being injected by malicious entities that can result in victimizing an innocent user by injecting dummy data.
4. Problem Identification
In existing works, sending huge amounts of data to BS across a point-to-point network can lead to an increase in communication costs. Furthermore, data are rarely compressed, which adds to the overhead. A large number of SMs providing significant amounts of data may cause a sensing bottleneck in an IoT environment. It might be more difficult if the SMs are synchronized to send data in a cyclic pattern. Bypassing the sensing bottleneck requires a selective or green sensing technique. Moreover, SMs in IoT-enabled environment have resource constraints such as restricted power supply, communication bandwidth, transmission speed, and memory storage capacity. By compressing data, the efficiency of the source’s processes can be increased. In an IoT environment, computation often requires less energy than data transfer. Data compression before transmission decreases data size, which can lead to lower SMs energy usage. Existing approaches, such as [15,27], aggregate data without the need for any kind of compression method. These methods employ asymmetric keys, which increase communication costs owing to huge message length, memory requirements, and computation time. For these reasons, the idea of proposing a new scheme capable of sending a huge amount of data in an aggregated manner, as well as securely and efficiently, through the network came to the minds of the authors.
5. Proposed Data Aggregation Scheme for Smart Grid
This section proposes an efficient data aggregation scheme for the SG network to address the challenges that have been discovered. The collection and distribution of sensitive data is a vital task in safe data gathering techniques. Data security should be given top priority in applications that enable SG-IoT for data sharing. Any intermediary can access and modify sensitive data, even if they are delivered efficiently but the confidentiality was not considered. By adopting integrity-protected hierarchical data aggregation and compression, our proposed solution addresses these difficulties. Figure 4 depicts three steps of our work: SM’s local compressed data transmission, FN’s message reception and aggregation and cloud server data extraction.
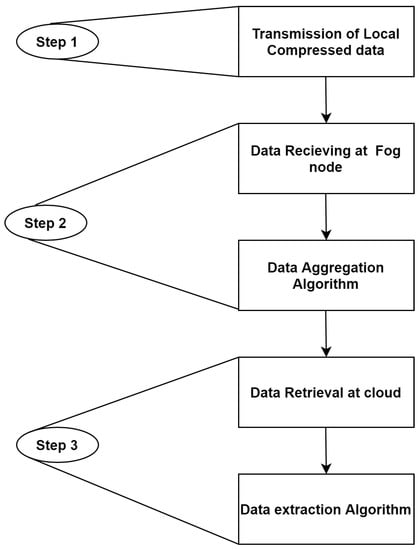
Figure 4.
Various steps involved in the proposed scheme.
In Step 1, local compressed data is sent from each SM to its regional FN. In this case, a method is provided to overcome the mentioned issues by utilizing data compression techniques and a symmetric key scheme in which each SM submits its compressed data to its regional FN. The process of data sharing is initiated by SMs by using pre-loaded keys shared with FNs to encrypt the data and forwards them to the FN. Only those SMs that meet the query request criteria or use synchronization time for transmission are capable of sharing data in this situation.
To begin, the XOR of the message mn of the SMn with the shared symmetric key Keyn,c between the SMn and cloud is taken to generate a ciphertext Cn. Furthermore, hn, the hash function of a ciphertext message is calculated by combining a shared symmetric key and a timestamp. The CD is a compressed version of Cn and hn i.e., CD = compression(Cn||hn). Furthermore, Msgn is a message issued by a SM that is composed of SM’s ID (SMn), timestamp T, and compressed data (CD).
In Step 2, we introduce data receiving and aggregation algorithm at FN, which receives compressed messages Msgn from its regional SMs and concatenates them. The receiving operation and data aggregation at FN is demonstrated in Algorithm 1. The compressed message Msgn is received by FN from all SMs, where n is the SM’s ID. Each Msgn is made up of node ID (SMn), timestamp (T) and CD. After receiving Msgn = (SMn||T ||CD) from SMn, the FN calculates timestamp T. If the condition (T− T) < for Msgn is true, the message is fresh; otherwise, it is rejected. Next, to ensure message integrity for each fresh received Msgn by FNM, it calculates H(Msgn) and compares it with the given hash. If there is no violation of integrity, FN combines all compressed messages received as Agg − Msgm = Agg − Msgm|| Msgn, resulting in Agg − Msgm = (Msgn||Msgn+1||...||Msgn+q) for q messages received at FN. The value of Agg − Msgm is initially null because FN has no data at first. Finally, FNm sends Datam to cloud, computed by performing XOR of Agg − Msgm with the shared symmetric key Keym, c, which is shared between FNm and the cloud. Algorithm 1 is represented in an simple way in flowchart form in Figure 5.
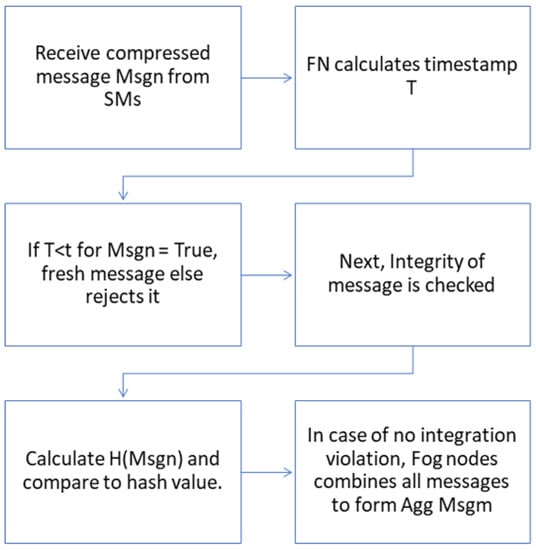
Figure 5.
Flowchart representation of Algorithm 1—Message Aggregation.
| Algorithm 1 Message Aggregation at FN | |
| 1 | Initialize: Agg − Msgm = NULL |
| 2 | Begin: Receive Msgn |
| 3 | Msgn = (SMn) || T || CD) from meter SMn |
| 4 | if T − T < then |
| 5 | if H(Msgn) equals to H(Msgn) then |
| 6 | Agg − Msgm = Agg − Msgm + Msgn |
| 7 | else |
| 8 | Rejects message because of loss of integrity |
| 9 | else if |
| 10 | else |
| 11 | Rejects message because of failure of freshness |
| 12 | end if |
| 13 | End |
In Step 3, we introduce the data extraction algorithm at the cloud, which receives compressed data Datam from all FNs in a sequential order. The data are also decompressed by the cloud before being decrypted individually. The cloud divides the aggregated data by delimiter and extracts each FN’s data. The extraction of aggregated data at the cloud is performed by calculating XOR of Datam with Keym,c. Next, using a loop to extract individual messages Msgn, verify the timestamp and compute the hash function for each plaintext mn using the decompress technique, then recover the original message mn by calculating XOR of the Msgn and Keyn,c. Algorithm 2 explains the data extraction procedure at cloud in detail and its flowchart explanation is shown in Figure 6.
| Algorithm 2 Data Extraction at Cloud | |
| 1 | Begin: Receive Datam |
| 2 | Datam = Agg − Msgm Keym, c |
| 3 | if H(Datam) equals to H(Datam) then |
| 4 | Agg − Msgm = Datam Keym, c |
| 5 | For count = 1 to q |
| 6 | Extract Msgn = (SMn || T || CD) from FN |
| 7 | if T T < then |
| 8 | Extract (cn || hn) using decompress CD |
| 9 | Calculate hn = h(cn || Keyn, c || T) |
| 10 | if hn equals to calculated h’n then |
| 11 | hn = cn Keyn, c |
| 12 | Store in cloud local repository |
| 13 | else |
| 14 | Rejects message because of loss of integrity |
| 15 | endif |
| 16 | else |
| 17 | Rejects message because of failure of freshness |
| 18 | else |
| 19 | Rejects message because of loss of integrity in |
| 20 | Agg − Msgm |
| 21 | endif |
| 22 | End |
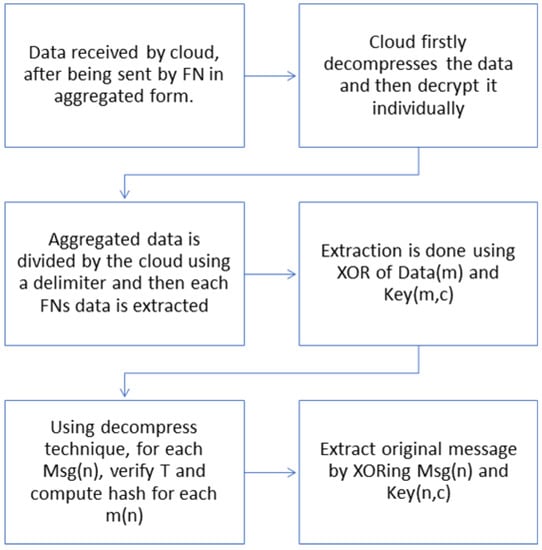
Figure 6.
Flowchart representation of Algorithm 2—Data extraction at the cloud.
6. Results and Discussion
This section discusses the proposed scheme’s performance in comparison with the existing schemes of SPPDA [16] and GCEDA [28] based on parameters such as storage space, communication cost and transmission ratio. The results were validated through extensive simulations, where SMs were deployed within an area of 1200 × 1200 m. This involved FNs and SMs, with each kind of node being set independently by creating relevant classes and functions for transmission, receiving, hashing, encryption, decryption and other associated algorithms. Additionally, to assess the impact of data compression on the system, the number of packets exchanged was considered. Furthermore, energy consumption is retrieved through the use of energy. The proposed scheme was simulated in MATLAB with C++, which includes various C++ files such as nodes configuration, node deployment, message sending and message reception. In addition, some functions were also implemented for data encryption, message decryption and hashing.
6.1. Storage
The impact on storage space in terms of bytes on a single node for different key sizes while considering group size of 5 to 25 nodes is presented in Figure 7. As shown in Figure 7, when there are 15 nodes in a group, the storage required per node is 90, 100 and 150 bytes for 16-bit, 32-bit, and 64-bit key sizes, respectively. Although the storage required for 16-bit key size is minimum among all, there is a chance that the attacker could simply gain access to the information. To add to the security, we have shown how much it costs to manage keys with 32 bits and 64 bits. MScost = (Number of keys · key size) is a formula for calculating memory storage costs. Individual nodes in group communication require modest storage to keep track of fewer keys.
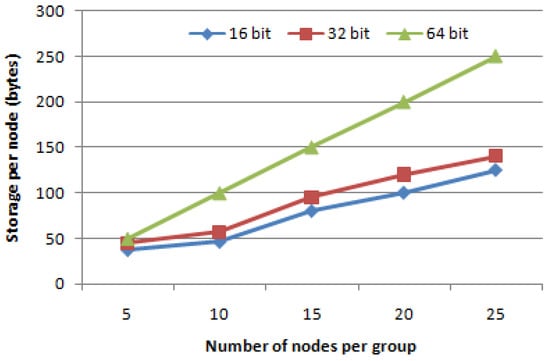
Figure 7.
Comparison of storage cost on single node for variable key size.
Figure 8 illustrates that for a single message with a data size of 150 bytes, the proposed scheme compresses the data to 90 bytes, whereas the data storage for SPPDA and GCEDA is 150 bytes. The results clearly reveal better storage with less memory requirement for the proposed scheme in comparison with existing schemes.
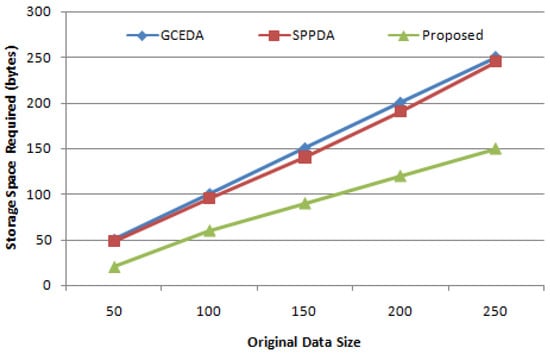
Figure 8.
Comparison of storage cost for data storage of the proposed scheme with GCEDA and SPPDA schemes.
6.2. Communication Cost
In Figure 9, the cost of communicating aggregated data messages via the network is illustrated. Our suggested compressed data strategy offers lower communications costs than the other two current schemes, according to simulation findings. In data transmission, the smaller-sized messages require a smaller communication cost in an IoT-enabled WSN compared with large-sized messages. Therefore, the result of our proposed scheme shows that when all fog nodes communicate, our scheme requires only 10,000 bytes of data in aggregated form, whereas SPPDA and GCEDA require 11,400 and 10,000 bytes, respectively. As messages must be exchanged across numerous pathways to reach FN, SPPDA requires additional resources. On the other hand, the proposed scheme exchange only 5200 bytes of aggregated data which is almost half of the original data. The results prove reduced communication cost to a great extent for our proposed scheme.
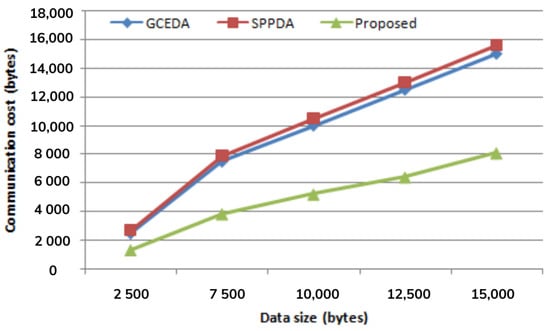
Figure 9.
Comparison of message communication cost of the proposed scheme with GCEDA and SPPDA schemes.
6.3. Transmission Cost
The transmission ratio (Transr) is the ratio of number of packets received x to number of packets sent Y. Figure 10 shows transmission ratios for GCEDA, SPPDA and proposed scheme are 0.835, 0.729, and 0.713, respectively, when 65 messages are sent. A better transmission ratio was recorded for the proposed scheme in comparison with existing schemes.
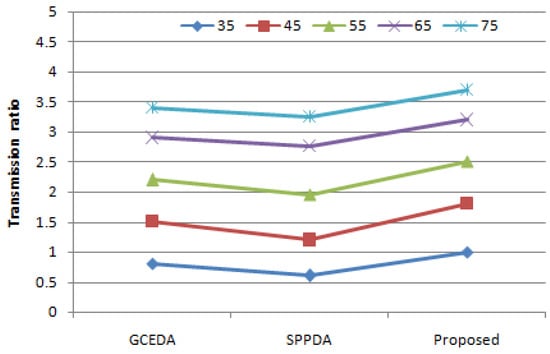
Figure 10.
Comparison of transmission ratio of the proposed scheme with GCEDA and SPPDA with varying messages.
7. Conclusions and Future Scope
This research discusses the framework for secure data aggregation using a data compression mechanism in an IoT-based SG environment. The main characteristics of our proposed method and implementation are: Manipulation of our innovative fog-enabled technique that we proposed. It provides secure data transmission from SMs to FN, which then sends aggregated data to the cloud server. It receives data from various SMs and prepares an aggregated message using the message aggregation algorithm at FN, which is proposed in our work. Compression is also used by SM to minimize data size and communication energy usage. The data extraction algorithm which is also proposed in this paper is further used by the cloud server to extract data from each FN initially, and then, second-level splitting is used to collect each SM’s data. We conducted extensive simulations in MATLAB to confirm our findings. The results revealed outstanding performance of the proposed strategy in comparison with existing GCEDA and SPPDA methods for different performance parameters such as storage space—2 times; transmission cost—1.4 times and 1.10 times; communication cost—1.15 and 1.10 times, respectively, making them efficient schemes for communication in a smart grid environment. The proposed work did not discuss any kind of attack on the SG-IoT system. In future, it is possible to study how the proposed scheme can provide security against cyber attacks which are on rise, while still maintaining the viability of the performance factors. The aggregated data need to be secure from any such attack to protect the users’ security. For these techniques, such as the fusion-based defence technique, modifying parameters of the keys, auditing logs and others or some combination of these should be considered. Classification of attacks is not performed in this work but is a possible task for future work.
Author Contributions
Conceptualization, S., S.R. and A.S.; methodology, R.A. and A.S.; software, S.R. and S.; validation, A.S. and D.S.M.H.; resources, R.A. and D.S.M.H.; writing—original draft preparation, S. and S.R.; writing—review and editing, A.S. and R.A.; supervision, R.A., D.S.M.H. and A.S.; All authors have read and agreed to the published version of the manuscript.
Funding
The article funded by Deputyship for Research & Innovation, Ministry of Education in Saudi Arabia for funding this research work through the project number RI-44-0029.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
No data is associated with this.
Acknowledgments
The authors extend their appreciation to the Deputyship for Research & Innovation, Ministry of Education in Saudi Arabia for funding this research work through the project number RI-44-0029.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Sayghe, A.; Hu, Y.; Zografopoulos, I.; Liu, X.; Dutta, R.G.; Jin, Y.; Konstantinou, C. Survey of machine learning methods for detecting false data injection attacks in power systems. IET Smart Grid 2020, 3, 581–595. [Google Scholar] [CrossRef]
- Prasanna Srinivasan, V.; Balasubadra, K.; Saravanan, K.; Arjun, V.S.; Malarkodi, S. Multi Label Deep Learning classification approach for False Data Injection Attacks in Smart Grid. KSII Trans. Internet Inf. Syst. 2021, 15, 2168–2187. [Google Scholar] [CrossRef]
- Ganjkhani, M.; Fallah, S.N.; Badakhshan, S.; Shamshirband, S.; Chau, K.W. A Novel Detection Algorithm to Identify False Data Injection Attacks on Power System State Estimation. Energies 2019, 12, 2209. [Google Scholar] [CrossRef]
- Li, B.; Lu, R.; Choo, K.K.R.; Wang, W.; Luo, S. On reliability analysis of smart grids under topology attacks: A stochastic petri net approach. ACM Trans. Cyber-Phys. Syst. 2018, 3, 1–25. [Google Scholar] [CrossRef]
- Dileep, G. A survey on smart grid technologies and applications. Renew. Energy 2020, 146, 2589–2625. [Google Scholar] [CrossRef]
- Kumar, P.; Lin, Y.; Bai, G.; Paverd, A.; Dong, J.S.; Martin, A. Smart grid metering networks: A survey on security, privacy and open research issues. IEEE Commun. Surv. Tutor. 2019, 21, 2886–2927. [Google Scholar] [CrossRef]
- Ganguly, P.; Nasipuri, M.; Dutta, S. Challenges of the existing security measures deployed in the smart grid framework. In Proceedings of the 2019 IEEE 7th International Conference on Smart Energy Grid Engineering (SEGE), Oshawa, ON, Canada, 12–14 August 2019; pp. 1–5. [Google Scholar]
- Wood, G.; Newborough, M. Dynamic energy-consumption indicators for domestic appliances: Environment, behaviour and design. Energy Build. 2003, 35, 821–841. [Google Scholar] [CrossRef]
- Luo, X.; Zhang, D.; Yang, L.T.; Liu, J.; Chang, X.; Ning, H. A kernel machine-based secure data sensing and fusion scheme in wireless sensor networks for the cyber-physical systems. Future Gener. Comput. Syst. 2016, 61, 85–96. [Google Scholar] [CrossRef]
- Lyu, L.; Nandakumar, K.; Rubinstein, B.; Jin, J.; Bedo, J.; Palaniswami, M. PPFA: Privacy preserving fog-enabled aggregation in smart grid. IEEE Trans. Ind. Inform. 2018, 14, 3733–3744. [Google Scholar] [CrossRef]
- Wang, H.; Wang, Z.; Domingo-Ferrer, J. Anonymous and secure aggregation scheme in fog- based public cloud computing. Future Gener. Comput. Syst. 2018, 78, 712–719. [Google Scholar] [CrossRef]
- Liu, N.J.; Weng, J.; Yang, A.; Chen, Y.; Lin, X. Enabling efficient and privacy-preserving aggregation communication and function query for fog computing-based smart grid. IEEE Trans. Smart Grid 2019, 11, 247–257. [Google Scholar] [CrossRef]
- Guan, Z.; Zhang, Y.; Wu, L.; Wu, J.; Li, J.; Ma, Y.; Hu, J. Appa: An anonymous and privacy preserving data aggregation scheme for fog-enhanced IoT. J. Netw. Comput. Appl. 2019, 125, 82–92. [Google Scholar] [CrossRef]
- Kishor, A.; Chakraborty, C.; Jeberson, W. A Novel Fog Computing Approach for Minimization of Latency in Healthcare using Machine Learning. Int. J. Interact. Multimed. Artif. Intell. 2021, 6, 7–17. [Google Scholar] [CrossRef]
- Han, S.; Zhao, S.; Li, Q.; Ju, C.H. Privacy-preserving and multi functional health data aggregation with fault tolerance. IEEE Trans. Inf. Forensics Secur. 2015, 11, 1940–1955. [Google Scholar] [CrossRef]
- Zhang, C.; Li, C.; Zhang, J. A secure privacy-preserving data aggregation model in wearable wireless sensor networks. J. Electr. Comput. Eng. 2015, 2015. [Google Scholar] [CrossRef]
- Patel, P.D.; Lapsiwala, P.B.; Kshirsagar, R.V. Data aggregation in wireless sensor network. Int. J. Manag. IT Eng. 2012, 2, 457–472. [Google Scholar]
- Fasolo, E.; Rossi, M.; Widmer, J.; Zorzi, M. In-network aggregation techniques for wireless sensor networks: A survey. IEEE Wirel. Commun. 2007, 14, 70–87. [Google Scholar] [CrossRef]
- Othman, S.; Trad, A.; Youssef, H.; Alzaid, H. Secure data aggregation with mac authentication in wireless sensor networks. In 12th IEEE International Conference on Trust, Security and Privacy in Computing and Communications; IEEE: Manhattan, NY, USA, 2013; pp. 188–195. [Google Scholar]
- Berjón, R.; Mateos, M.; Beato, M.E.; Fermoso García, A. An Event Mesh for Event Driven IoT Applications. Int. J. Interact. Multimed. Artif. Intell. 2022, 7, 54–59. [Google Scholar] [CrossRef]
- Zhu, X.; Deng, H. A Security Situation Awareness Approach for IoT Software Chain Based on Markov Game Model. Int. J. Interact. Multimed. Artif. Intell. 2022, 7, 59–65. [Google Scholar] [CrossRef]
- Kaur, N.; Mittal, A. Fog computing serverless architecture for real time unpredictable traffic. In IOP Conference Series: Materials Science and Engineering; IOP Publishing: Bristol, UK, 2021; Volume 1022, p. 012026. [Google Scholar]
- Kashyap, V.; Kumar, A. Load balancing techniques for fog computing environment: Comparison, taxonomy, open issues, and challenges. Concurr. Comput. Pract. Exp. 2022, 34, e7183. [Google Scholar] [CrossRef]
- Lin, X.; Lu, R.; Shen, X. Mdpa: Multidimensional privacy-preserving aggregation scheme for wireless sensor networks. Wirel. Commun. Mob. Comput. 2010, 10, 843–856. [Google Scholar] [CrossRef]
- Lalos, A.S.; Antonopoulos, A.; Kartsakli, E.; Di Renzo, M.; Tennina, S.; Alonso, L.; Verikoukis, C. Rlnc-aided cooperative compressed sensing for energy efficient vital signal telemonitoring. IEEE Trans. Wirel. Commun. 2015, 14, 3685–3699. [Google Scholar] [CrossRef]
- Mahmud, R.; Ramamohanarao, K.; Buyya, R. Application management in fog computing environments: A taxonomy, review and future directions. ACM Comput. Surv. (CSUR) 2020, 53, 1–43. [Google Scholar] [CrossRef]
- Gelogo, Y.E.; Kim, C.H. A design of secure e-health data management system. J. Secur. Eng. 2015, 12, 181–190. [Google Scholar] [CrossRef]
- Mantri, D.; Prasad, N.R.; Prasad, R. Grouping of clusters for efficient data aggregation (GCEDA) in wireless sensor network. In Proceedings of the 2013 3rd IEEE International Advance Computing Conference (IACC), Ghaziabad, India, 22–23 February 2013; pp. 132–137. [Google Scholar]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).