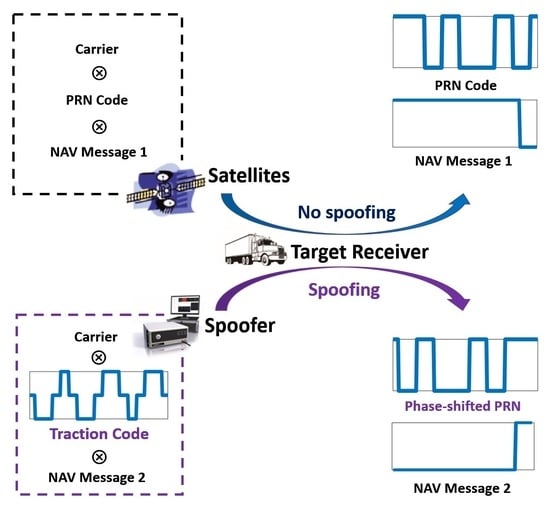
2.1. Conventional GNSS Traction Spoofing
The conventional traction process of spoofing can be divided into three steps:
Step 1: Signal reception. The receiving module of the spoofer receives a genuine signal, detects the location and speed of the target, and estimates the genuine signal’s key parameters.
Step 2: Determine the traction scheme. The parameters of the spoofing signal are set such that the correlation peak of the spoofing signal arriving at the target receiver aligns gradually with the actual peak. In a conventional traction strategy, the correlation peak envelope of the composite signal is distorted, as shown in
Figure 2.
Step 3: Traction spoofing. The spoofing signal is generated to dominate the tracking loop and gradually enlarge the code phase difference to generate a pseudo-distance error, which eventually controls the target.
The correlation result between the local and authentication signals is defined as
, and thatbetween the local and superimposed signals is defined as
. If the correlation function between the spoofing signal and local replica is
, then the distortion correlation peak envelope of the composite signal is as illustrated in
Figure 2.
In the first step, the detection of the antenna position and speed of the spoofing target, power level, channel conditions, and other information is not within the scope of this study, assuming that the spoofer has obtained specific information. The content discussed in this study is the setting and generation module of the spoofing signal.
The discussion in this paper is based on a Binary Phase Shift Keying (BPSK) signal system. First, we can model the genuine signal as:
Similarly, the spoofing signal can be expressed as
where the subscripts a and s represent the genuine and spoofing signals, respectively. In addition,
,
,
,
and
denote the satellite signal power, navigation message, pseudo code, Doppler shift, and initial carrier phase, respectively.
The traction modes in the latter two steps can be divided into synchronous and asynchronous traction according to the accuracy of the parameter estimation [
10].
- (1)
Synchronous traction
The diagram of synchronous traction is shown in
Figure 3.
T1: At the beginning of traction, the spoofing code phase (Doppler) is aligned with the genuine code phase (Doppler).
T2: Increase the power of spoofing signals.
T3: Drag the correlation peak away from the original tracking point.
T4: Keep the power consistent with the genuine signal.
This method requires high measurement accuracy in the first step and is difficult to achieve in an actual scenario.
- (2)
Asynchronous traction
A diagram of asynchronous traction is shown in
Figure 4. Unlike synchronous traction, asynchronous traction does not require a spoofer to determine the exact parameters of an authentication signal. This traction mode directly generates a higher power correlation peak to control the loop, which is more suitable for application in actual scenarios.
Control of the distance velocity of the correlated peaks is defined as the traction code rate
. In the third step of the spoofing traction process, according to whether the spoofing signal maintains the code and carrier phase consistency, conventional traction strategies can be divided into two types [
11]:
Strategy 1 Adjust the code phase only
The code and carrier phase consistencies are broken, and only the code rate is altered.
Strategy 2 Maintain code-carrier coherence
If the spoofing signal maintains code-carrier coherence, we obtain
where
and
represent the nominal carrier frequency and code rate, respectively.
The deception process of the spoofer is illustratedin
Figure 5. The first light-grey area is the setting module of the spoofing signal, and the lower light-grey area is the generation module of the spoofing signal.
In conventional traction strategies, although the Pseudo-Random Noise (PRN) code
used forspoofing is the same as the genuine signal, there is a designed phase difference
:
where
After determining the traction speed , the phase difference can be obtained from Equation (6). Then can be obtained from Equation (5).
The distortion in
Figure 2 is often the root cause of TOA and power detection; hence, traction strategies that can avoid correlation peak superposition are considered. In this case, replacing the code of the original system may be a novel idea, as discussed in the next section.
2.3. Methods of Simulation and Experiment
2.3.1. Theoretical Model of Received Signal
According to the signal model in
Section 2.1, the composite signal r(t) is demodulated by the local receiver as follows:
where
is the code phase difference between the genuine and local signals, and the same is true for parameters
,
,
,
,
and other parameters.
Coherent integration of
is performed to obtain the prompt correlation values:
are integrated and dumped to produce the prompt correlation results of spoofing signals:
Given and , we can obtain and according to Equation (8).
Strategy 1
Assuming that the amplitude ratio between the spoofing and genuine signals is
, the correlation results can be simplified as
The same is true for and .
Define
as the traction speed, then
Then , , the early and late correlation results can be derived.
When the carrier loop is in a steady state, the received signal power is not transferred from the in-phase components to quadrature components. The phase discriminator of the code tracking loop processes the early and late correlation results, and the output is
where
,
.
Local code Doppler
is obtained after the filter of the code loop processing
:
Strategy 2
If the spoofing signal maintains the code-carrier coherence, the frequency change in the spoofing signal directly influences the local carrier generation, and the received signal power is transferred to the quadrature components. The prompt correlation amplitude is expressed as follows:
The output of the phase discriminator of the code tracking loop can be expressed as:
where the forms of the early and late correlation amplitudes are the same as those of the prompt correlation amplitude; only the function R(τ) is replaced by
or
.
The output of the phase discriminator of the carrier loop is typically calculated using a two-quadrant arctangent function:
Local carrier Doppler
is obtained after the filter of carrier loop processing
:
Proposed Strategy Spoofing traction strategy based on the generation of traction code
The correlation results can be stable throughout the traction process, and the prompt correlation result
is always
Similarly, the forms of the early and late correlation results are the same as those of the prompt correlation results. Only functions are replaced by and .
The ideal output of the phase discriminator of the code loop can be obtained:
2.3.2. Simulation and Conditions
Considering synchronous traction with a more hidden spoofing effect as an example, simulations were performed for three traction strategies according to the theoretical model of the received signal in
Section 2.3.1. Because the simulation does not require mass data processing at a high sampling rate, it can quickly test traction success under a certain strategy. For the 20-s data, the simulation of Strategy 1 took less than 1 s, and the simulation of Strategy 2 took less than 2 s.
Spoofing was selected to enter at 1 s. Traction duration was determined by
and the tracking-loop structure. Because the carrier loop is only related to the prompt correlation value, when
and
are 1 chip, the two peaks have exited each other’s prompt tracking point, whereas the code loop needs to wait for the other correlation peak to exit the early or late tracking point. If the traction duration of the carrier loop is defined as
and that of the code loop is defined as
, then
In other words, according to the structural characteristics of the carrier and code loops, the traction duration should be at least .
The maximum spoofing power of conventional spoofing signals is equal to the genuine signal power. The correlator spacing at the receiver was set as the typical value for satellite navigation receiver applications, i.e., D = 2d = 1. The spoofing signal has the same initial carrier and code phases as the genuine signal when added.
The first set of simulations (Nos. 1, 3, and 5) was used to directly compare the theoretical deception effects of the strategies.
The Simulation conditions are presented in
Table 1. When implementing a traction strategy to successfully implement spoofing traction, the selection of traction speed
follows certain principles. According to the code loop structure, the code phase offset within each coherence integration should not exceed 0.5 chips [
12], that is the traction speed
should not be too fast. However, owing to the loose requirements, spoofing may fail even if the conditions are met.
When the traction strategy is determined, the range of traction speed that can make traction successful is determined. Therefore, the theoretical value range of the traction speeds of the three strategies can be determined via another set of traversal simulations (Nos. 2, 4, and 6).
2.3.3. Spoofing Experiment and Scenario
To verify the applicability of the proposed strategy in actual environments, effective intermediate-frequency spoofing data were generated based on the signal generation software, and noise was added to the composite signal. We then used a software receiver to examine the effects of the different spoofing traction strategies. No. 33 satellite signal was selected. The intermediate frequency was , sampling rate was and carrier-to-noise ratio was . Three traction strategies were simulated under these conditions.
However, to simulate the change in the signal strength caused by different noise environments and satellite altitude angle changes, was set to , and , respectively. Owing to the particularity of spoofing, we expected the received results to be stably close to those of the genuine signal. Therefore, RMSE statistics were conducted on the results of the three traction strategies to observe the performance of the proposed strategy under different . These statistics were compared with the genuine results.
A spoofing scenario of was used to simulate the power enhancement in special scenarios, such as the battlefield. To simulate narrow correlators and pulse-aperture correlators, spoofing scenarios with narrow correlation intervals () were added.
The designed spoofing scenarios are presented in
Table 2.
2.3.4. Data Processing
Whether in the simulation or experiment, the local code phase is not directly known, and it must be obtained using the following formula:
where
is the initial code phase obtained from acquisition. The phase difference diagram can be obtained by subtracting
from
and
, respectively.
Once we obtain the tracking results, we must determine whether the spoofing traction was successful. For spoofing, whose frequency is locked to the genuine signal, we want
to be 0 to demonstrate that the code loop traction is successful, and for spoofing that maintains the code-carrier coherence, we also want
to be 0 to demonstrate that the carrier loop traction is successful. These results can be expressed using the following formulas:
If (or ) is less than 0, traction succeeds; otherwise, traction fails.
Given the maximum traction speed
for a given strategy, the shortest time required for deceptive traction can be calculated using the following formula:
Because there are several detection methods included in TOA and power detection, this study attempts to use a simple statistical analysis method and the SQM method as examples to verify the detection quantity. If we perform a statistical analysis on observation
, the RMSE statistic is:
where
are the fitting values of the genuine signal observations. To reflect the influence of the spoofing signals of each strategy on the RMSE, the RMSE values are calculated as follows:
where
represents the RMSE statistic of the genuine signal observations.
In the SQM technique, we used a Ratio Test metric to identify correlation distortions. The Ratio Test metric is:
where
, L, and P denote early, late, and prompt correlator outputs over the in-phase branch, respectively.
To observe fluctuations, we uniformly subtracted the ideal value of metric 1/2 from the metric when plotting.