Vehicular Communications Utility in Road Safety Applications: A Step toward Self-Aware Intelligent Traffic Systems
Abstract
1. Introduction
2. Issues and Solutions Addressed in Vehicular Communications
3. Vehicular Communications and Proposed Solutions

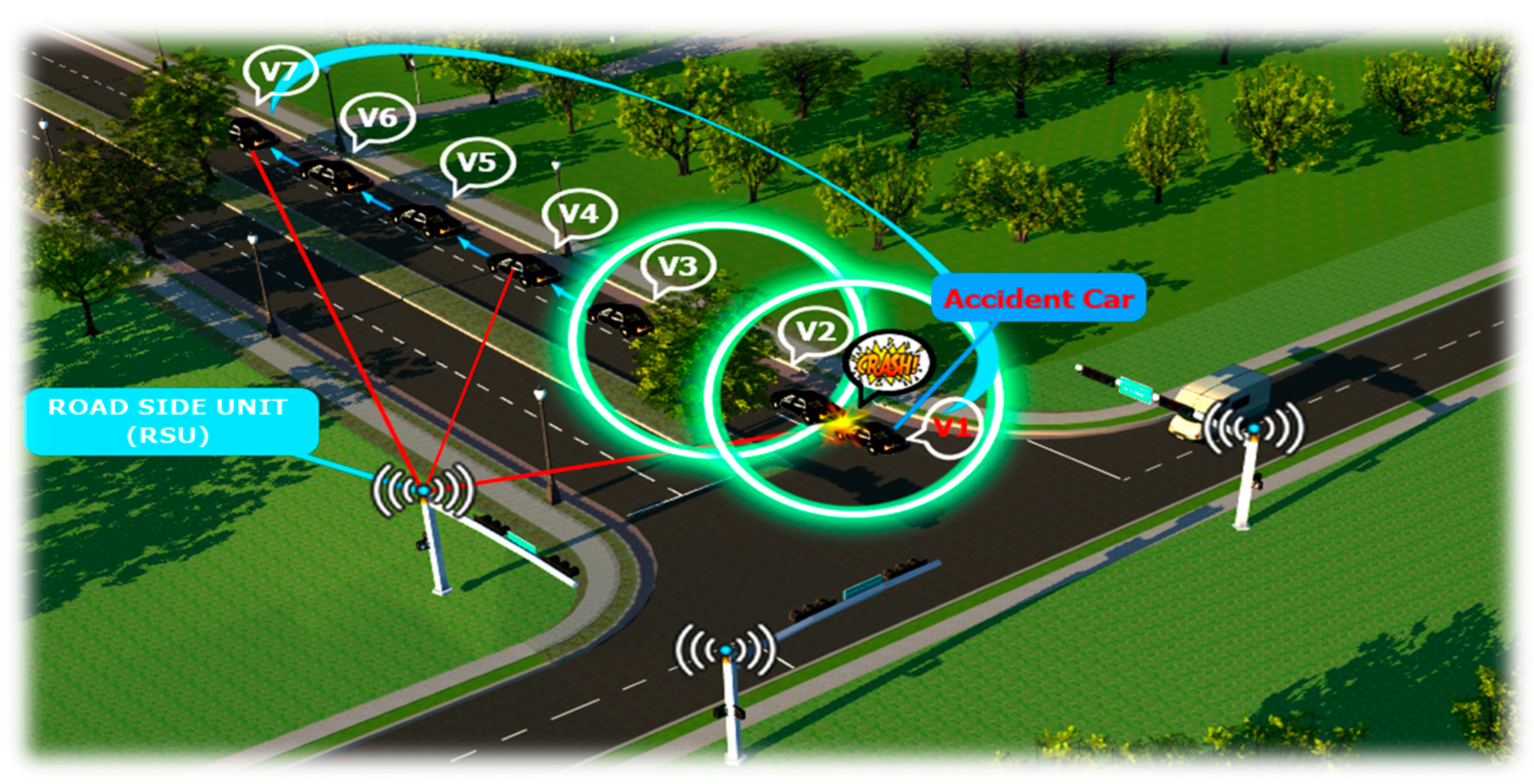
3.1. Receiving the Warning Message Confirmed by the Transceiver in V2R or R2V Communication Mode
- ⮚
- When the vehicle receives, it performs a verification of the source ID and the advertising message but does not send the message back to the roadside unit in order to reduce overhead in the network.
- ⮚
- When the receiving vehicle does not play the role of the source vehicle but is positioned in front of one that is the source, it has an obligation to avoid and ignore the message.
- ⮚
- When the vehicle acting as a receiver is positioned behind the source vehicle but has received warning messages that are identified with the same event ID from the V2V communication network, it must ignore the message.
- ⮚
- When the vehicle with the receiving role is positioned behind a source vehicle and does not receive the event ID, the transmission of procedures before the event and the prevention of a collision are performed, all the while waiting for confirmation of the warning message and event ID from the rear platoon.
- (a)
- If it receives a warning message containing the same event ID, then the process of retransmitting the warning message containing the event are stopped. This process facilitates fluid communication and also reduces costs.
- (b)
- Otherwise, instances of periodic transmission of the message containing the warning characteristics are created until a warning message is returned containing the event ID from the vehicles located in the rear.
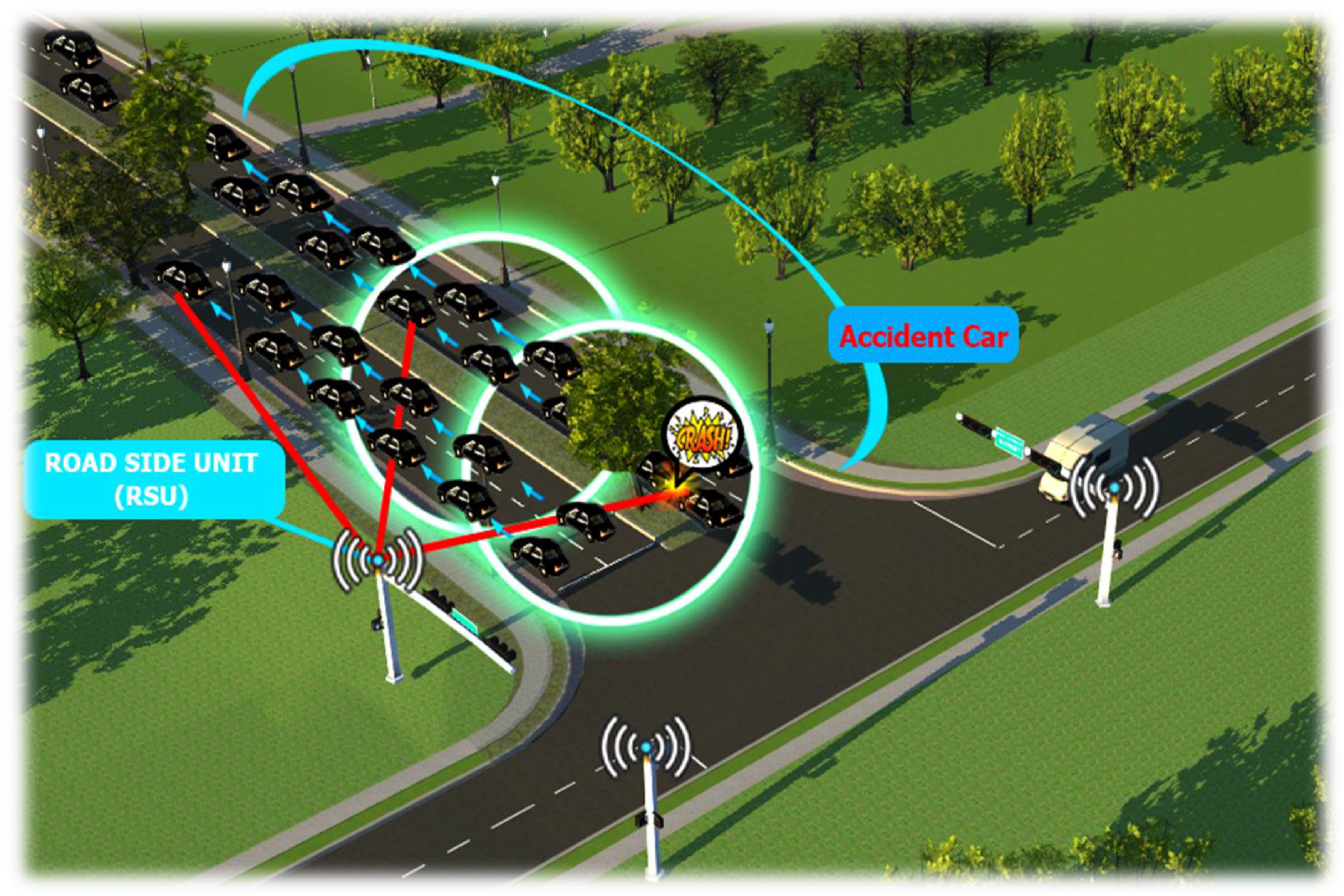
3.2. How to Receive Warning Messages from the Receiver That Processes the Information in the V2V Communication Module
- ⮚
- When the receiving vehicle is located in front of the vehicle broadcasting, it no longer has to retransmit the warning message regarding the event with the same ID. The aim is to reduce the number of messages broadcast on the network.
- ⮚
- When the receiving vehicle is positioned behind the broadcasting vehicle and the message has been reconditioned after, it must ignore the message.
- ⮚
- When the receiving vehicle is positioned behind the vehicle dedicated to broadcast and it receives the warning message as the first factor, it must perform the necessary measures and procedures to avoid a collision. At the same time, it has the role of verifying the validity of the message and whether an event with the same ID is not received from the roadside unit. If the information is not confirmed, it periodically sends the warning message to the roadside unit to obtain a warning message with the event ID. In parallel, the receiving vehicle has the quality of waiting for a random amount of time to filter the warning messages that have a similar event ID from the vehicles in the rest of the platoon.
- (a)
- If such a message is received, the vehicle has the obligation to stop sending it regarding the same event. Commonly, again this method helps to reduce costs.
- (b)
- If such a message is not received, the vehicle has the obligation to periodically send a warning message until an event ID is received from the vehicles behind the receiver.
4. Theory Principles and Simulation Results
4.1. Introduction to Theory Principles

- (1)
- signal-to-noise ratio (SNR) analyzed for a sample;
- (2)
- bit-analysis-type ratio for the sectional-type density of the noise power (Eb/); and
- (3)
- power-to-noise symbol-type ratio for spectral density power (Es/).
4.2. Practical Scenarios and Simulations Results
- (a)
- Illustration of the behavioral scheme of the receiving vehicles in the case of the V2R communication protocol, where the source vehicle sends warning messages to the RSU, waiting for the return of the messages with the event ID from the roadside unit;
- (b)
- Illustration of the behavioral scheme of the receiving vehicles in the case of the V2V communication protocol, where the vehicles periodically send messages to other cars in nearby areas until the event ID is returned from the rear vehicles;










5. Discussion

6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Abbreviations
| VANET | Vehicular ad hoc network |
| MC | Multi-channel |
| V2V | Vehicle-to-vehicle |
| V2R | Vehicle-to-road |
| R2V | Road-to-vehicle |
| ITS | Intelligent transportation system |
| DSRC | Dedicated short-range communication |
| ASTM | American Society for Testing and Materials |
| OFDM | Orthogonal frequency-division multiplexing |
| CSMA/CA | Carrier/sense multiple access with collision avoidance |
| MAC | Medium access control |
| TDMA | Time-division multiple access |
| AODV | Ad hoc distance vector |
| ID | Identifier |
| CFP | Contention-dree period |
| CP | Containment period |
| WAVE | Wireless access in the average vehicle |
| BSSID | Basic Service Set Identification |
| RSU | Roadside unit |
| GPS | Global Positioning System |
| PHY | Physical layer |
| SNR | Signal-to-noise ratio |
| V2X | Vehicle-to-everything |
| VLC | Visible light communication |
| V2I | Vehicle-to-infrastructure |
| AWGN | Additive white Gaussian noise |
References
- Belokurov, V.; Spodarev, R.; Belokurov, S. Determining Passenger Traffic as Important Factor in Urban Public Transport System. Transp. Res. Procedia 2020, 50, 52–58. [Google Scholar] [CrossRef]
- Enoch, M.P.; Cross, R.; Potter, N.; Davidson, C.; Taylor, S.; Brown, R.; Huang, H.; Parons, J.; Tuker, S.; Wynne, E.; et al. Future Local Passenger Transport System Scenarios and Implications for Policy and Practice. Transp. Policy 2020, 90, 52–67. [Google Scholar] [CrossRef]
- Pahs, J.; Dulebenets, M.A.; Kavoosi, M.; Abioye, O.F.; Theopilus, O.; Wang, H.; Kampmann, R.; Guo, W. Holistic Tatical-level Planning in Liner Shipping: An Exact Optimization Approach. J. Shipp. Trade 2020, 5, 1–35. [Google Scholar]
- Albayrak, M.B.K.; Özcan, I.C.; Can, R.; Dobruszkes, F. The Determinants of Air Passenger Traffic at Turkish Airports. J. Air Transp. Manag. 2020, 86, 101818. [Google Scholar] [CrossRef]
- Sheet, F. 358—Road Traffic Injuries; World Health Organization: Geneva, Switzerland, 2016. [Google Scholar]
- Global Status Report on Road Safety 2018; World Health Organization: Geneva, Switzerland, 2018.
- Kenney, J.B. Dedicated Short-range Communications (DSRC) Standards in the United States. Proc. IEEE 2011, 99, 1162–1182. [Google Scholar] [CrossRef]
- Ahangar, M.N.; Ahmed, Q.Z.; Khan, F.A.; Hafeez, M. A Survey of Autonomous Vehicles: Enabling Communication Technologies and Challenges. Sensors 2021, 21, 706. [Google Scholar] [CrossRef] [PubMed]
- Cho, S. SINR-Based MCS Level Adaptation in CSMA/CA Wireless Networks to Embrace IoT Devices. Symmetry 2017, 9, 236. [Google Scholar] [CrossRef]
- Zadobrischi, E.; Cosovanu, L.; Avătămăniţei, S.; Căilean, A. Complementary Radiofrequency and Visible Light Systems for Indoor and Vehicular Communications. In Proceedings of the 23rd International Conference on System Theory, Control and Computing (ICSTCC 2019), Sinaia, Romania, 9–11 October 2019; pp. 419–423. [Google Scholar]
- Liang, C.N.; Chen, B.C. A study of DSRC jammer in vehicle safety application testbed. In Proceedings of the 2012 12th International Conference on ITS Telecommunications, Taipei, Taiwan, 5–8 November 2012; pp. 216–219. [Google Scholar]
- Wu, X.; Subramanian, S.; Guha, R.; White, R.G.; Li, J.; Lu, K.W.; Zhang, T. Vehicular Communications Using DSRC: Challenges, Enhancements, and Evolution. IEEE J. Sel. Areas Commun. 2013, 31, 399–408. [Google Scholar]
- Ligo, A.K.; Peha, J.M.; Ferreira, P.; Barros, J. Throughput and Economics of DSRC-Based Internet of Vehicles. IEEE Access 2018, 6, 7276–7290. [Google Scholar] [CrossRef]
- Yoshioka, S.; Inoue, Y.; Suyama, S.; Kishiyama, Y.; Okumura, Y.; Kepler, J.; Cudak, M. Field Experimental Evaluation of Beamtracking and Latency Performance for 5G mmWave Radio Access in Outdoor Mobile Environment. In Proceedings of the IEEE 27th Annual International Symposium on Personal, Indoor, and Mobile Radio Communications (PIMRC 2016), Valencia, Spain, 4–8 September 2016; pp. 1–6. [Google Scholar]
- Safety Communications Project Task 3 Final Report; Technical Report DOTHS 809 859; CAMP Vehicle Safety Communication Consortium: Farmington, MI, USA, 2005.
- Koziol, M. MWC Barcelona 2019: On the Road to Self-Driving Cars, 5G Will Make Us Better Drivers; IEEE Spectrum Press: New York, NY, USA, 2019. [Google Scholar]
- Liang, Z.; Wakahara, Y. Real-time Urban Traffic Amount Prediction Models for Dynamic Route Guidance Systems. EURASIP J. Wirel. Commun. Netw. 2014, 2014, 85. [Google Scholar] [CrossRef]
- Lin, L.; Li, W.; Peeta, S. Efficient Data Collection and Accurate Travel Time Estimation in a Connected Vehicle Environment Via Real-Time Compressive Sensing. J. Big Data Anal. Transp. 2019, 1, 95–107. [Google Scholar] [CrossRef]
- Miao, L.; Virtusio, J.J.; Hua, K.-L. PC5-Based Cellular-V2X Evolution and Deployment. Sensors 2021, 21, 843. [Google Scholar] [CrossRef] [PubMed]
- Huch, S.; Ongel, A.; Betz, J.; Lienkamp, M. Multi-Task End-to-End Self-Driving Architecture for CAV Platoons. Sensors 2021, 21, 1093. [Google Scholar] [CrossRef]
- Papaioannou, P.; Papadopoulos, E.; Nikolaidou, A.; Politis, I.; Basbas, S.; Kountouri, E. Dilemma Zone: Modeling Drivers’ Decision at Signalized Intersections against Aggressiveness and Other Factors Using UAV Technology. Safety 2021, 7, 11. [Google Scholar] [CrossRef]
- Lenkutis, T.; Čerškus, A.; Šešok, N.; Dzedzickis, A.; Bučinskas, V. Road Surface Profile Synthesis: Assessment of Suitability for Simulation. Symmetry 2021, 13, 68. [Google Scholar] [CrossRef]
- Kulin, M.; Kazaz, T.; De Poorter, E.; Moerman, I. A Survey on Machine Learning-Based Performance Improvement of Wireless Networks: PHY, MAC and Network Layer. Electronics 2021, 10, 318. [Google Scholar] [CrossRef]
- Elsas, R.; Hoebeke, J.; Van Leemput, D.; Shahid, A.; Daneels, G.; Famaey, J.; De Poorter, E. Intra-Network Interference Robustness: An Empirical Evaluation of IEEE 802.15.4-2015 SUN-OFDM. Electronics 2020, 9, 1691. [Google Scholar] [CrossRef]
- Mrozik, M.; Merkisz-Guranowska, A. Environmental Assessment of the Vehicle Operation Process. Energies 2021, 14, 76. [Google Scholar] [CrossRef]
- Haque, K.F.; Abdelgawad, A.; Yanambaka, V.P.; Yelamarthi, K. LoRa Architecture for V2X Communication: An Experimental Evaluation with Vehicles on the Move. Sensors 2020, 20, 6876. [Google Scholar] [CrossRef] [PubMed]
- Barthelemy, M. Revisiting urban economics for understanding urban data. In Theories and Models of Urbanization; Springer: Cham, Switzerland, 2020; pp. 121–131. [Google Scholar]
- Košťál, K.; Bencel, R.; Ries, M.; Trúchly, P.; Kotuliak, I. High Performance SDN WLAN Architecture. Sensors 2019, 19, 1880. [Google Scholar] [CrossRef] [PubMed]
- Demba, A.; Möller, D.P.F. Vehicle-to-Vehicle Communication Technology. In Proceedings of the 2018 IEEE International Conference on Electro/Information Technology (EIT), Rochester, MI, USA, 3–5 May 2018; pp. 0459–0464. [Google Scholar]
- Nafi, S.; Khan, R.H.; Khan, J.Y.; Gregory, M. A Predictive Road Traffic Management System Based on Vehicular ad-hoc Network. In Proceedings of the Australasian Telecommunication Networks and Applications Conference (ATNAC 2014), Southbank, VIC, Australia, 26–28 November 2014; pp. 135–140. [Google Scholar]
- Gupta, S.K.; Khan, J.Y.; Ngo, D.T. Cluster-based D2D Architecture for Safety Services in Vehicular ad hoc Networks. In Proceedings of the 2018 IEEE Wireless Communications and Networking Conference Workshops (WCNCW), Barcelona, Spain, 15–18 April 2018; pp. 43–48. [Google Scholar]
- Hanggoro, A.; Sari, R.F. Performance Evaluation of the Manhattan Mobility Model in Vehicular ad-hoc Networks for High Mobility Vehicle. In Proceedings of the 2013 IEEE International Conference on Communication, Networks and Satellite (COMNETSAT), Yogyakarta, Indonesia, 3–4 December 2013; pp. 31–36. [Google Scholar]
- Nafi, N.S.; Hasan, M.K.; Abdallah, A.H. Traffic Flow Model for Vehicular Network. In Proceedings of the 2012 International Conference on Computer and Communication Engineering (ICCCE), Kuala Lumpur, Malaysia, 12–14 June 2012; pp. 738–743. [Google Scholar]
- Nafi, N.S.; Khan, J.Y. A VANET based Intelligent Road Traffic Signalling System. In Proceedings of the Australasian Telecommunication Networks and Applications Conference (ATNAC) 2012, Brisbane, QLD, Australia, 7–9 November 2012; pp. 1–6. [Google Scholar]
- Tsouri, G.R.; Wagner, D.M. Threshold Constraints on Symmetric Key Extraction from Rician Fading Estimates. IEEE Trans. Mob. Comput. 2013, 12, 2496–2506. [Google Scholar] [CrossRef]
- Zogas, D.A.; Karagiannidis, G.K. Infinite-series Representations Associated with the Bivariate Rician Distribution and Their Applications. IEEE Trans. Commun. 2005, 53, 1790–1794. [Google Scholar] [CrossRef]
- Hanafi, E.; Martin, P.A.; Smith, P.J.; Coulson, A.J. Quickest Spectrum Sensing With Multiple Antennas in Rician and Correlated Rayleigh Channels. IEEE Commun. Lett. 2014, 18, 1455–1458. [Google Scholar] [CrossRef]
- Le, K.N. On Selection Combiner Output Multivariate Distributions in Correlated Generalized-Rician Fading. IEEE Commun. Lett. 2017, 21, 242–245. [Google Scholar] [CrossRef]
- Fan, W.; Kyösti, P.; Hentilä, L.; Nielsen, J.Ø.; Pedersen, G.F. Rician Channel Modeling for Multiprobe Anechoic Chamber Setups. IEEE Antennas Wirel. Propag. Lett. 2014, 13, 1761–1764. [Google Scholar] [CrossRef]
- Jiang, R.; Wu, Q.; Zhu, Z. Full Velocity Difference Model for a Car-following Theory. Phys. Rev. E 2001, 64, 017101: 1–017101: 4. [Google Scholar] [CrossRef] [PubMed]
- Choi, B.; Jung, D.; Lim, H. Interframe Spacing Adaptation Method for IEEE 802.11 WLANs Coexisting with IEEE 802.16 Networks. In Proceedings of the 2011 IEEE 36th Conference on Local Computer Networks, Bonn, Germany, 4–7 October 2011; pp. 299–302. [Google Scholar]
- Abbasi, I.A.; Shahid Khan, A. A Review of Vehicle to Vehicle Communication Protocols for VANETs in the Urban Environment. Future Internet 2018, 10, 14. [Google Scholar] [CrossRef]
- Maitipe, B.R.; Ibrahim, U.; Hayee, M.I.; Kwon, E. Vehicle-to-Infrastructure and Vehicle-to-Vehicle Information System in Work Zones: Dedicated Short-Range Communications. Transp. Res. Rec. 2012, 2324, 125–132. [Google Scholar] [CrossRef]
- Li, T.; Hui, F.; Liu, C.; Zhao, X.; Khattak, A.J. Analysis of V2V Messages for Car-Following Behavior with the Traffic Jerk Effect. J. Adv. Transp. 2020, 2020, 11. [Google Scholar] [CrossRef]
- Huang, L.; Yao, J.; Wu, W.; Yang, X. Feasibility Analysis of Vehicle-to-vehicle Communication on Suburban Road. Promet-Traffic Transp. 2013, 25, 483–493. [Google Scholar] [CrossRef]
- Haferkamp, M.; Al-Askary, M.; Dorn, D.; Sliwa, B.; Habel, L.; Schreckenberg, M.; Wietfeld, C. Radio-based Traffic Flow Detection and Vehicle Classification for Future Smart Cities. In Proceedings of the 2017 IEEE 85th Vehicular Technology Conference (VTC Spring), Sydney, NSW, Australia, 4–7 June 2017; pp. 1–5. [Google Scholar]
- Zadobrischi, E.; Cosovanu, L.-M.; Dimian, M. Traffic Flow Density Model and Dynamic Traffic Congestion Model Simulation Based on Practice Case with Vehicle Network and System Traffic Intelligent Communication. Symmetry 2020, 12, 1172. [Google Scholar] [CrossRef]
- Zadobrischi, E.; Avătămănitei, S.; Căilean, A.; Dimian, M.; Negru, M. Toward a Hybrid Vehicle Communication Platform Based on VLC and DSRC Technologies. In Proceedings of the 2019 IEEE 15th International Conference on Intelligent Computer Communication and Processing (ICCP), Cluj-Napoca, Romania, 5–7 September 2019; pp. 103–107. [Google Scholar]
- Wu, D.; Zhang, W.; Tang, L.; Zhang, C. A New Integrated Scheme for Urban Road Traffic Flood Control Using Liquid Air Spray/Vaporization Technology. Sustainability 2020, 12, 2733. [Google Scholar] [CrossRef]
- Shrestha, R.; Nam, S.Y.; Bajracharya, R.; Kim, S. Evolution of V2X Communication and Integration of Blockchain for Security Enhancements. Electronics 2020, 9, 1338. [Google Scholar] [CrossRef]
- Cailean, A.; Cagneau, B.; Chassagne, L.; Popa, V.; Dimian, M. A Survey on the Usage of DSRC and VLC in Communication-based 1112 Vehicle Safety Applications. In Proceedings of the IEEE 21st Symposium on Communications and Vehicular Technology in the 1113 Benelux (SCVT), Delft, The Netherlands, 10 November 2014; pp. 69–74. [Google Scholar]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zadobrischi, E.; Dimian, M. Vehicular Communications Utility in Road Safety Applications: A Step toward Self-Aware Intelligent Traffic Systems. Symmetry 2021, 13, 438. https://doi.org/10.3390/sym13030438
Zadobrischi E, Dimian M. Vehicular Communications Utility in Road Safety Applications: A Step toward Self-Aware Intelligent Traffic Systems. Symmetry. 2021; 13(3):438. https://doi.org/10.3390/sym13030438
Chicago/Turabian StyleZadobrischi, Eduard, and Mihai Dimian. 2021. "Vehicular Communications Utility in Road Safety Applications: A Step toward Self-Aware Intelligent Traffic Systems" Symmetry 13, no. 3: 438. https://doi.org/10.3390/sym13030438
APA StyleZadobrischi, E., & Dimian, M. (2021). Vehicular Communications Utility in Road Safety Applications: A Step toward Self-Aware Intelligent Traffic Systems. Symmetry, 13(3), 438. https://doi.org/10.3390/sym13030438






