1. Introduction
After the landmark announcement of IBM’s new quantum computer, which managed to successfully break the 100-qubit barrier [
1], it appears that we have moved closer than originally anticipated to the realization of practical quantum computation and the definitive transition from the digital era to the quantum era. However, such rapid technological advancements also herald some rather serious issues with our current infrastructure—issues that can pose significant threats to our information security. After the publication of one of the most famous papers in the field of quantum computing by Peter Shor in 1994 [
2], which proposed an algorithm that can solve the integer factorization problem in polynomial time, and is thus theoretically able to break any cryptosystem based on the aforementioned problem, it was made apparent that, if quantum computers become a reality, then the existing digital security protocols must be replaced with ones that can withstand attacks from a quantum computer.
Fortunately, after recognizing the potential vulnerability of the current infrastructure, the scientific community came up with an explosion of proposals in the field of quantum cryptography, which resulted in a profound increase of the maturity of the field. Quantum cryptography in its present state can be broken down into two main branches. The first branch is referred to as post-quantum cryptography or quantum-resistant cryptography, and it relies on the development of cryptographic protocols that are based on the complexity of certain mathematical problems. It is believed, but not yet proven, that the aforementioned problems can not be solved in polynomial time even with a quantum computer. The second branch of the field, known as quantum cryptography, strives to create secure cryptosystems based on the clever implementation of certain properties of quantum mechanics, such as entanglement and superposition of quantum states, the non-locality principle, the no-cloning theorem, etc. This branch of quantum cryptography, which this paper is part of, was originally created by proposing two novel solutions to the fundamental problem of key distribution. The historic works of Bennett and Brassard for the BB84 QKD protocol [
3], and Ekert for the E91 QKD protocol [
4], were instrumental, as they established the two main methods of sharing information between two or more players utilizing the power of quantum mechanics, known as the prepare-and-measure and the entanglement-based methods, upon which every quantum cryptographic protocol is based on.
After these two protocols, a rapid expansion of the sub-field of quantum key distribution ensued that resulted in multiple attempts on transitioning other sub-fields of cryptography into their quantum counterparts. One of the numerous sub-fields of cryptography which can be improved with the use of quantum mechanics, in order to enhance its security and efficiency against a quantum computer, is the field of secret sharing, which can be described as a clandestine game between three or more individual players that are located in two different geographical locations and are unable to communicate in person. For the sake of simplicity, we shall initially describe the simplest version of the game, involving only three players. However, the game can be scaled up to as many players as we want. Therefore, we start by dividing the three players into two groups. The first group consists of the dealer or spymaster, which is a single person, and, for this game, we shall give this honor to Alice, who is located in Athens. The second group consists of her secret agents, the rest of the players—in this case Bob and Charlie, who are located in Corfu. In this game, the spymaster Alice wants to send a set of secret instructions to her agents for them to act upon. However, Alice is not certain that she can trust both of her agents because she suspects that one of them, but not both, is a double agent and is working for the enemy, with the goal of foiling her plans. However, she knows that, if both of her agents partake in the mission together, the agent who is loyal to Alice will prevent the double agent from causing any damage. Furthermore, aside from the possible double agent who wants to sabotage the mission, Alice must also take precautions to assure the confidentiality of the mission from possible eavesdroppers, which for the sake of the game will be referred to as Eve. Therefore, Alice must somehow find a way to make both her agents act on her behalf, and, at the same time, prevent both the dishonest agent and Eve from tempering with the mission.
This elaborate game may at first sight seem a little redundant or even superfluous, yet the field of secret sharing has been proven vital for a certain type of problems with multiple real world uses, as for example, to guarantee that a single individual or a small group of the involved party can not access a valuable shared resource, such as a shared bank account. This means that, in order to take any action, all involved members must act in concert. As a consequence, this requirement makes it considerably more difficult for any individual who wants to have unauthorized access to secret information or to perform an unauthorized action, to achieve her purpose. Practically, this implies that the only way for a malicious player to perform any action is to convince every single member to go along.
The pioneering works of Hillery et al. [
5] and Cleve et al. [
6], which proved that secret sharing can be achieved with the use of quantum mechanics, paved the way for the creation of a new field with the name of Quantum Secret Sharing (QSS for short). Since then, there has been extensive progress in this field, with a plethora of proposals actively continuing the research to this day [
7,
8,
9,
10,
11,
12,
13,
14]. Multiple research groups have devised protocols demonstrating the viability of QSS (see, for instance, [
15,
16,
17]). More recently, elaborate proof-of-concept experimental demonstrations of novel and effective protocols applicable to real world scenarios have been introduced by the researchers in [
18,
19,
20,
21]. Another line of research attempted to extend the capabilities of the field by proposing non-binary protocols that rely on the use of qudits rather than qubits [
22,
23].
With this rapid advancement of the field, one may also observe some notable efforts towards the application of Grover’s algorithm [
24], which is one of the most famous algorithms of all time, as a QSS protocol [
25,
26,
27]. In the same vein, it has also been shown by multiple proposals that well-known quantum algorithms, such as the Deutsch-Josza, the Bernstein-Vazirani and Simon’s algorithms can be utilized in implementing viable QKD protocols [
28,
29,
30,
31]. This decade promises to be the Quantum Decade that will, hopefully, transform every aspect of the industry and the society for the better. Technologically, we are fast approaching the era of the quantum-centric supercomputer [
32]. The quantum-centric supercomputer will combine quantum and classical processors, quantum and classical communication networks into a harmonious quantum ecosystem that will elevate our computing capabilities to new undreamed-of heights. Every quantum practitioner knows that building a quantum computer capable of practical impact involves millions of qubits. Hence, the problem of scaling the current, modest in terms of qubits, quantum processors is of paramount importance. One way to cleverly bypassing the problem of scaling the number of qubits of a single quantum processor is by linking multiple such processors together into a modular quantum system capable of scaling without limitations. In view of this current trend, we advocate the utility and efficiency of using quantum algorithms as cryptographic protocols, either by modifying established quantum algorithms, or by building new ones based on some fundamental concepts of other algorithms. We believe that this approach will prove beneficial for achieving effective security between multiple quantum computers, by simply exchanging information and processing it using gates, without the need of extra equipment [
33].
In this paper, we propose a new QSS protocol in the form of a quantum game, which we hope will make its presentation simple and pedagogical, thanks to the inherent ability of game theory to present complex and challenging problems in a more innate and comprehensive way. As a consequence, quantum games have gained prominence as a useful paradigm of the quantum world and have been used to tackle important problems. A typical example in this area is the quantum game of coin tossing and its application to cryptographic protocols (see [
3] and the more recent [
34]). The beginning of this field can be traced back to two landmark papers from 1999: Meyer’s PQ penny flip game [
35] and the Eisert–Wilkens–Lewenstein scheme [
36]. Numerous works that were inspired from the PQ penny flip game have appeared in the literature and some recent results are given in [
37,
38,
39]. The Eisert–Wilkens–Lewenstein scheme was successfully employed in the study of quantum versions of well-known classical games, such as the famous Prisoners’ Dilemma, where the quantum strategies outperformed the classical strategy [
36], and to quantum extensions of the classical repeated Prisoners’ Dilemma strategies [
40]. Winning strategies for abstract quantum games can also be encoded as infinite words accepted by quantum automata, as demonstrated in [
41]. Quantum games have even been used in [
42] as a metaphor for the operation of a hypothetical quantum parliament.
1.1. Contribution
As a result of our approach, in this paper, we propose the novel Symmetric Extensible Quantum Secret Sharing protocol, which we designate by SEQSS, where n represents the number of participating players. The final result is an entanglement-based protocol that relies on the use of maximally entangled GHZ tuples, evenly distributed among the players, in order to allow our spymaster Alice to securely share the secret message with her agents, by implementing a unitary transform . As the name suggests, it exhibits symmetry, since all agents are treated indiscriminately, utilizing identical quantum circuits. It offers uncompromising security, making it virtually impossible for a malicious eavesdropper or a rogue double agent to disrupt its successful execution, due to the fact that only the spymaster performs all the steps in the protocol, while the rest of the agents will only have to apply Hadamard gates and measure their registers, rendering them unable to tamper with the protocol. Additionally, we provide a rigorous mathematical analysis of what will happen, if Eve or a rogue agent decides to implement their own unitary function . After the completion of the quantum part of the protocol, it is mandatory for the spymaster to publicly communicate her final measurement to her agents, since without this information the agents will not be able to discover the secret message, even if they combine together all their individual data. However, this can be considered as an added advantage, which can be further illustrated as a clandestine mission with Alice as the spymaster and the rest of her agents acting on her behalf. In this mission, Alice has created a detailed plan, outlining all possible scenarios of the mission, and she has broken down her plan into multiple secret messages, i.e., s, s, … At the beginning of the mission, Alice and her agents complete the quantum part of the protocol multiple times, in order for everyone to have a piece of every single secret message that might be used. At a later moment, Alice can decide if, or when she wants to broadcast some of her measurements based on the real-time feedback from her agents. For example, she will broadcast her piece of information to start the mission, and then, based on how the mission progresses, she will only broadcast in real time only those secret messages that are relevant to unfolding scenario of the mission. This strategy provides her with the ability to hide from her agents and the enemy possible critical information. Furthermore, since she can broadcast her pieces of the secret message on a public channel, after the completion of the quantum part, Alice and her agents can use whatever communication method they deem suitable for the mission.
1.2. Organization
This paper is organized as follows:
Section 1 gives an introduction to the subject along with some relevant references.
Section 2 provides a brief introduction about the GHZ states and the principle of entanglement, a vital tool used in the formulation of the proposed protocol.
Section 3 showcases the Symmetric Extensible QSS protocol twice, once in its simplest form, which is restricted to only three players and once in its general form, which is played by
n players.
Section 4 gives a brief security analysis on a certain number of known attack strategies that Eve can employ in order to compromise the security of the protocol and acquire confidential information about the secret message that Alice wants to share. Finally,
Section 5 discusses the operation and advantages of the proposed protocol.
2. Background on GHZ States
Quantum entanglement can be described mathematically as the linear combination of two or more product states. This unique phenomenon is universally considered as one of the fundamental principles of quantum mechanics and is the basis of many fascinating proposals, one of which is the achievement of quantum teleportation. Moreover, entanglement-based techniques have been proven indispensable in the field of quantum secret sharing and quantum cryptography in general. In this paper, for the realization of our QSS protocol, we will heavily rely on the utilization of maximally entangled pairs of three or more qubits, which are commonly known as GHZ states. Therefore, we believe that the following subsection, in which we give a brief explanation on the nature of GHZ states, will facilitate the understanding of the proposed protocol.
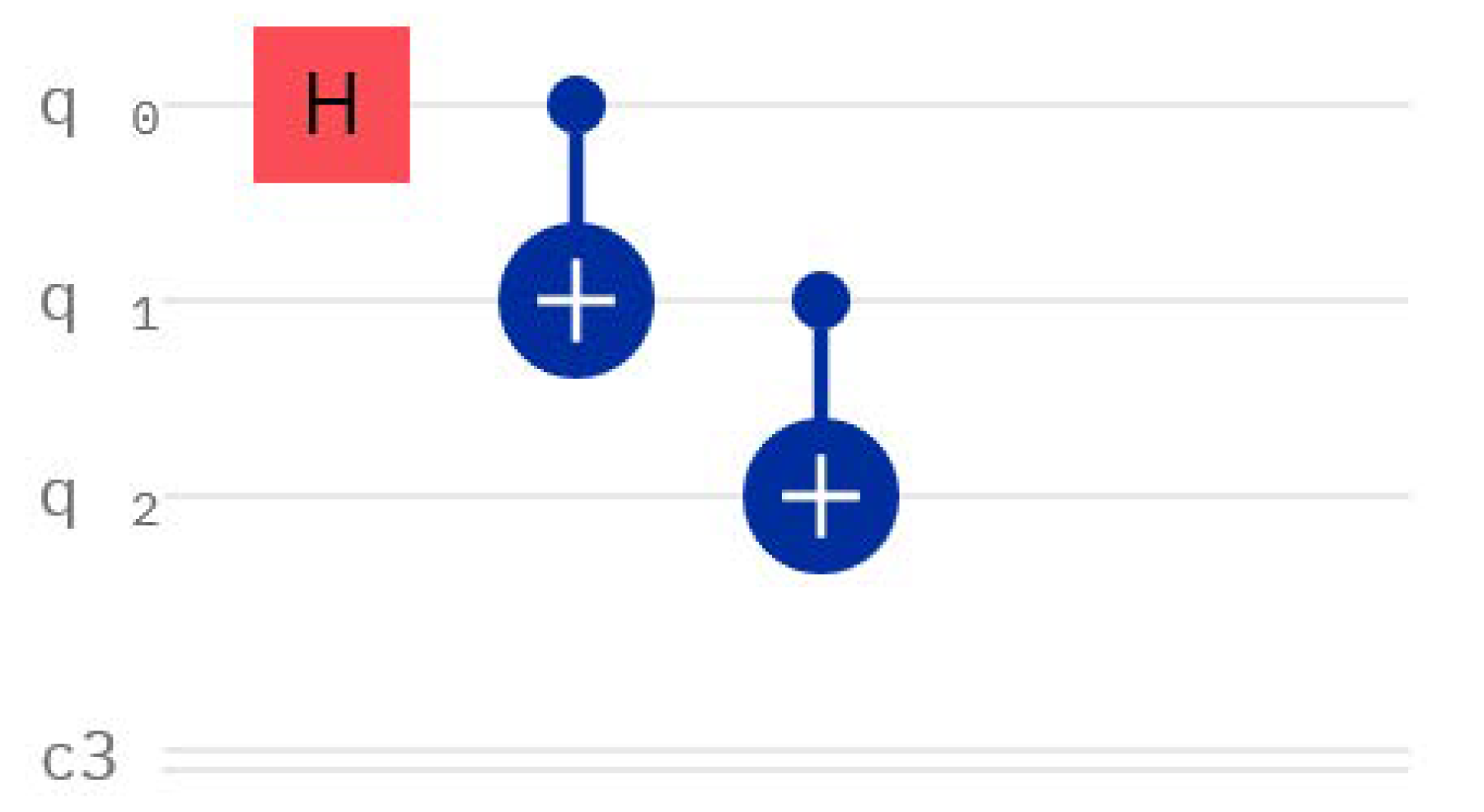
From the perspective of quantum computing, a GHZ state can be produced by a circuit with three or more qubits, upon which a Hadamard gate is applied to the first qubit, then a CNOT gate is applied to the first and second qubits, and subsequently a CNOT to the second and third qubits, and so on until we reach the last qubit. A possible quantum circuit for preparing three qubits in the GHZ state is shown in
Figure 1.
Figure 2 gives the state vector description of the corresponding GHZ state. These figures were also obtained from the IBM Quantum Composer [
43].
Generalizing the same reasoning as in the case of the 3 qubit GHZ state shown in
Figure 1, the mathematical representation of a composite system consisting of
n single qubit subsystems all entangled in the GHZ state, denoted by
, goes as follows:
The above setting can be generalized to the case where a composite system consists of
n subsystems, say
n quantum registers
, each of them having
m qubits, and the corresponding qubits of all the
n registers are entangled in the
state. The state of the composite system, denoted by
, is described by the formula below:
The proof for this formula is rather straightforward. If we take the entangled state
, as shown in (
1) twice, the resulting tensor product can be portrayed as
Following this pattern, we can successfully derive the general Formula (
2) with induction and thus complete the proof.
3. The Symmetric Extensible QSS Protocol
In this section, we thoroughly analyze the proposed Symmetric Extensible QSS (for short SEQSS) protocol in great detail. All of Alice’s agents employ identical quantum circuits, hence the term symmetric. Due to the nature of the game, the least number of agents Alice can deploy is two, e.g., agents Bob and Charlie, but their number can seamlessly increase to accommodate as many as necessary, which explains the term extensible. We begin our analysis with the simplest version, which is a demonstration of the protocol restricted to only three players, designated by SEQSS, while later on we transition to the general version that consists of n agents and is aptly designated as SEQSS.
3.1. The 3-Player SEQSS3 Protocol
Let us begin by showcasing the protocol as a game between three players divided into two groups, exactly as we outlined in
Section 1. Thus, we will have Alice being the first group and playing the role of the spymaster, tasked with sharing the secret instructions denoted by
to her agents, and Bob and Charlie comprising the second group and playing the role of said secret agents, who are spatially separated form Alice, but they are both located in the same region of space. The game will start by having all three players share
m triplets of maximally entangled qubits. Each triplet is in the
state and Alice, Bob and Charlie possess the qubit
,
and
, respectively, of the triplet. At this point, it is important to state that there are no limitations on which player will create the GHZ triplets in the first place. The states can be created and distributed accordingly by either Alice, her agents, or even by a third party source, e.g., a satellite [
44]. The goal of the current game is for Alice to successfully share her secret message
with her agents Bob and Charlie. However, the secret message
, should not be readable by her agents individually. They must both combine their results in order to be able to read it. This task can be successfully accomplished by performing the steps shown below visually in
Figure 3 in the form of a quantum circuit.
Furthermore, we point out that each of our three protagonists has a private quantum circuit and the three quantum circuits are similar, in the sense that they all contain an Input Register consisting of
m qubits. Bob and Charlie’s circuits are virtually identical, whereas Alice’s circuit differs because it also contains an Output Register consisting of a single qubit, a Hadamard gate acting on the Output Register and the unitary transform
, which acts on both her Input and Output Registers. The corresponding qubits in Alice’s, Bob’s and Charlie’s Input Registers constitute a triplet entangled in the
state.
Table 1 explains the abbreviations that are used in the quantum circuit depicted in
Figure 3.
To describe the resulting composite system, we invoke Formula (
2) setting
. Following the steps of the circuit shown above, we can examine the phases of the algorithm more closely, starting with the initial state
of the system:
As expected,
,
and
correspond to Alice’s, Bob’s and Charlie’s Input Registers, respectively, representing each player’s part of the GHZ states. Likewise,
represents Alice’s Output Register. During our analysis, the subscripts
A,
B and
C will be consistently used to designate the registers belonging to Alice, Bob and Charlie, respectively. We also emphasize that for consistency we use the Qiskit [
45] convention of ordering qubits, where the most significant qubit is the bottom qubit and the least significant qubit is the top qubit.
Continuing to the next phase, Alice effectively initiates the protocol by applying the Hadamard transform to her Output Register. In view of the fact that
, this produces the ensuing state
This will allow Alice to apply her function
on her registers by using the standard scheme:
Consequently, the next state becomes
At this point, we emphasize that Alice’s function is
where
is the secret message chosen by Alice. Refs. (7) and (8) can be written as
Subsequently, Alice, Bob and Charlie apply the
m-fold Hadamard transform to their Input Registers, driving the system into the next state
We can observe now that, when
then
, the expression
becomes
. As a result, the sum
=
. Whenever
, the sum is just 0 because, for exactly half of the inputs
, the exponent will be 0 and, for the remaining half, the exponent will be 1. Hence, one may write that
Utilizing Equation (12), and ignoring for a moment Alice’s Output Register, which is at state
, the following three equivalent and symmetric forms can be derived:
By combining (10) with (13)–(15), state
can be more succinctly written as:
where the states of the three players’ Input Registers are always correlated as expressed by the following fundamental property:
Finally, Alice, Bob and Charlie measure their GHZ states in their Input Registers obtaining
and thus successfully completing the quantum part of the protocol.
We may easily observe that the contents of each of the three Input Registers appear random to Alice, Bob and Charlie, but are, when viewed as a composite system, correlated by the fundamental property (17) of the SEQSS protocol. We now recall that Bob and Charlie are in the same region of space. This implies that they can securely exchange information without using any classical or quantum communication channel. A critical remark is that, even if Bob and Charlie combine their measurements and , they still will not be able to retrieve Alice’s secret , unless, of course, it happens that . This last event can happen with probability , which is virtually negligible for large values of m. Bob and Charlie still need a crucial ingredient from Alice, namely the contents of Alice’s Input Register. Hence, we can conclude the protocol by having Alice share her measurement with anyone of her agents via a public channel. She can choose either Bob or Charlie without affecting the protocol. Finally, Bob and Charlie, being in possession of , can combine their measurements and obtain the secret message , according to (17).
The part where Alice must share her measurement with her agents after the quantum part of the protocol, can be seen as an advantage, due to the fact that Alice and her agents may perform the quantum part of the protocol at a given time and then have Alice, as the spymaster, determine when will be the right time for her agents to unlock the secret message, by deciding when to broadcast her measurement.
Figure 4 provides a mnemonic visualization of the spatial positions of Alice, Bob and Charlie in the SEQSS
protocol, as well as the operation of the quantum and the classical channel.
3.2. The n-Player SEQSSn Protocol
Now that we have presented the simplest version of the protocol, we can move on to the general version, which can be described as an obvious extension of the SEQSS
game, where now Alice’s agents are not only two but
, namely Agent
, …, Agent
. The quantum circuit implementing the SEQSS
protocol is depicted in the next
Figure 5. As before, Alice is spatially separated from her
agents, which are all located in the same region of space. Additionally, we point out that each of the
n players has their own quantum circuit and that the
n quantum circuits are similar, since they all contain an Input Register consisting of
m qubits. All the
Alice’s secret agents have identical circuits. Alice’s circuit differs because it also contains an Output Register, consisting of a single qubit, upon which a Hadamard gate acts, and the unitary transform
acting on both her Input and Output Registers. The corresponding qubits in the Input Registers used by Alice and her
secret agents constitute an
n-tuple entangled in the
state.
Table 2 explains the abbreviations that are used in the quantum circuit depicted in
Figure 5.
Once again, following the steps of the circuit shown in
Figure 5, we can examine the steps of the algorithm more closely, by starting with the initial state of the system
As before,
gives the state of Alice’s Input Register,
, represent the states of the Input Registers of the
agents, and
is the state of Alice’s Output Register. In our subsequent analysis, the subscripts
A,
are consistently used to designate the registers belonging to Alice and Agent
, …, Agent
, respectively. Thus, we may move on to the next phase, by having Alice initiate the protocol, via the application of the Hadamard transform to her Output Register, which produces the ensuing state
Akin to the previous version, this will allow Alice to apply her function given by (8) on her registers and lead to the next state, which is
Afterwards, Alice and all her secret agents apply the
m-fold Hadamard transformation to their Input Registers, driving the system into the next state
The crucial observation now is that, if
then
, the expression
becomes
. As a result, the sum
=
. Whenever
, the sum is just 0 because for exactly half of the inputs
the exponent will be 0 and for the remaining half the exponent will be 1. Therefore, we derive that
Equation (24) leads to the following
n equivalent and symmetric formulations:
By combining (22) with (25)–(27), we can write state
in a compact way as
where the states of all the
n players’ Input Registers are always correlated as dictated by the fundamental property
Finally, Alice and her secret agents Agent
, …, Agent
measure their GHZ states in their Input Registers obtaining
which completes the quantum part of the SEQSS
protocol.
In this most general case, we encounter the same motif we saw in the case of the three players. In particular, although the contents of each of the n Input Registers appear random to Alice and her secret agents, when viewed as a composite system, they are correlated by the fundamental property (29) of the SEQSS protocol. The fact that all of Alice’s agents are in the same geographical region implies that they can securely exchange information without using any classical or quantum communication channel. However, even if all the secret agents combine their measurements , they will still not be able to retrieve Alice’s secret , unless, of course, it happens that . This last event can happen with probability , which tends to zero as m increases. Alice’s agents lack a crucial ingredient from Alice, namely the contents of Alice’s Input Register. Hence, we can conclude the protocol by having Alice share her measurement with anyone of her agents via a public channel. She can choose either one of them without affecting the protocol. Finally, the secret agents, being in possession of , can combine their measurements and obtain the secret message , according to (29).
Let us again stress that Alice may share her measurement with anyone of her agents. This is undoubtedly an important advantage of the protocol, due to the fact that Alice and her agents may perform the quantum part of the protocol at a given time and then have Alice, as the spymaster, determine when will be the right time for her agents to unlock the secret message, by deciding when to broadcast her measurement. Furthermore, the broadcast of Alice’s measurement via a public channel, will not hinder the security of the protocol because, even if Eve is present, she will still need the rest of the measurements, in order to retrieve the secret message .
Figure 6 presents a mnemonic representation of the SEQSS
protocol, together with the operation of the quantum and classical channels.
4. Security Analysis of the Protocol
In this section, we provide a brief security analysis of the SEQSS protocol, against certain known types of attacks that Eve can employ, in an attempt to acquire vital information and break the confidentiality of the protocol. The SEQSS protocol is an entanglement-based protocol, which allows Alice to secretly transmit information to her agents with the use of entangled GHZ qubits. Therefore, the security of our protocol can be assured by a plethora of well-established phenomena, namely, the monogamy of entangled particles, the no cloning theorem and non-locality. Furthermore, it is important to state that Eve’s goal here is only to acquire the measurements of the secret agents. This is because, during the final stage of the protocol, Alice will publicly share her measurement with her secret agents, in order for them to unlock the secret message. Now, in order to further establish the security of the protocol, we will consider the following attack strategies.
4.1. Measure and Resend Attack
In this attack, Eve’s strategy is to intercept the GHZ tuples during their transmission from the source to the players, measure them and then resend them back to the players. In this attack, Eve will not acquire any information, due to the fact that the GHZ tuples during the transmission phase will not be carrying any information—thus rendering this strategy ineffective against the protocol.
4.2. Intercept and Resend Attack
This is one of the oldest strategies for Eve to gain any valuable information from the protocol and the way this strategy works is by having Eve intercept the transmitted GHZ tuples, then measure them in the computational basis with the goal of gaining valuable information and, finally, send the new cloned GHZ qubits to the players. As we mentioned above, Eve will not gain any information, simply because the GHZ tuples at the transmission phase do not contain any information about the secret message. Additionally, the no cloning theorem prohibits the ability to create clones of the intercepted qubits without destroying them.
4.3. Entangle and Measure Attack
In this attack, Eve’s strategy is to intercept the transmitted GHZ qubits that are heading to the secret agents. Only now, instead of measuring them, as we saw above, she will entangle them with her ancilla state, prepared in some state
determined by Eve, by performing a unitary operation
U on the composite system and then send the GHZ qubits to the secret agents. Finally, Eve will wait for the protocol to complete and then measure her qubits in order to acquire useful information about the secret message. In order to analyze this attack, we consider the worst case scenario, wherein Eve is already in an advantageous position, by assuming that, instead of intercepting the GHZ states, she will be the one who will create them, along with an extra tuple for herself and distribute them to the rest of the players. Therefore, rather than having
states for the
n players, we will have
states for the
n players plus Eve. Furthermore, we will assume that, in this scenario, Eve can also perform her own unitary transform
just like Alice. Thus, we begin our scenario in the initial state
of the system:
Starting in a similar fashion as the
protocol presented in the previous section,
and
represent Alice’s Input and Output Registers, respectively,
, represent the states of the Input Registers of the
agents, and
and
represent Eve’s Input and Output Registers respectively. As before, the subscripts
will consistently be used to designate the registers belonging to Alice, her Agents, and Eve respectively. Thus, we proceed to the next phase, by having Alice and Eve initiate the protocol by having both apply the Hadamard transform to their Output Registers, which will produce the following state:
Next, Alice and Eve will have the ability to apply their functions given by (8) on their registers. In this scenario,
and
represent Alice’s secret message and Eve’s input string, respectively, that leads to the next state, which is
Afterwards, everyone can apply the
m-fold Hadamard transformation to their Input Registers, driving the system into the next state
Again, the crucial observation now is that, if
then
, the expression
becomes
. As a result, the sum
=
. Whenever
, the sum is just 0 because, for exactly half of the inputs
, the exponent will be 0 and for the remaining half the exponent will be 1. Therefore, we derive that
Equation (36) leads to the following
n equivalent and symmetric formulations.
By combining (34) with (37)–(39), we can write state
in a compact way as
where the states of all the
n players’ plus Eve’s Input Registers are always correlated as dictated by the fundamental property
Finally, Alice, her secret agents Agent
, …, Agent
and Eve can measure their GHZ states in their Input Registers obtaining
From the above procedure, we can make several important observations about Eve’s measurement. Starting with (37)–(39), from which it is easy to see that Eve will measure , which in fact is Alice’s message XORed with Eve’s input string and the random variables measured by the agents. Therefore, even if Eve manages to take part in the procedure, she will not be able to acquire any useful information about the secret message . Additionally, after the completion of the quantum part of the protocol, when the players will try to combine their measurements, in order to unlock the secret message, they will realize that they are not able to unlock the secret message because they will still need Eve’s measurement. Hence, in that case, they will be alerted about the fact that Eve tempered with the procedure.
4.4. Blinding Attack
In this attack, Eve’s strategy is not to intercept the transmitted GHZ qubits, but actually block them entirely from ever reaching the intended players and then create her own GHZ qubits and transmit these to the players. Of course, it is clear that this strategy only works if the players rely on a third party for the creating and distribution of the GHZ states. However, even if that is the case, Eve will not be able to acquire any information by having her own qubits entangled in the system, due to the fact that, in our protocol, she will be considered as an extra player and she will still need the measurements of the other players, in order to unlock the secret message.