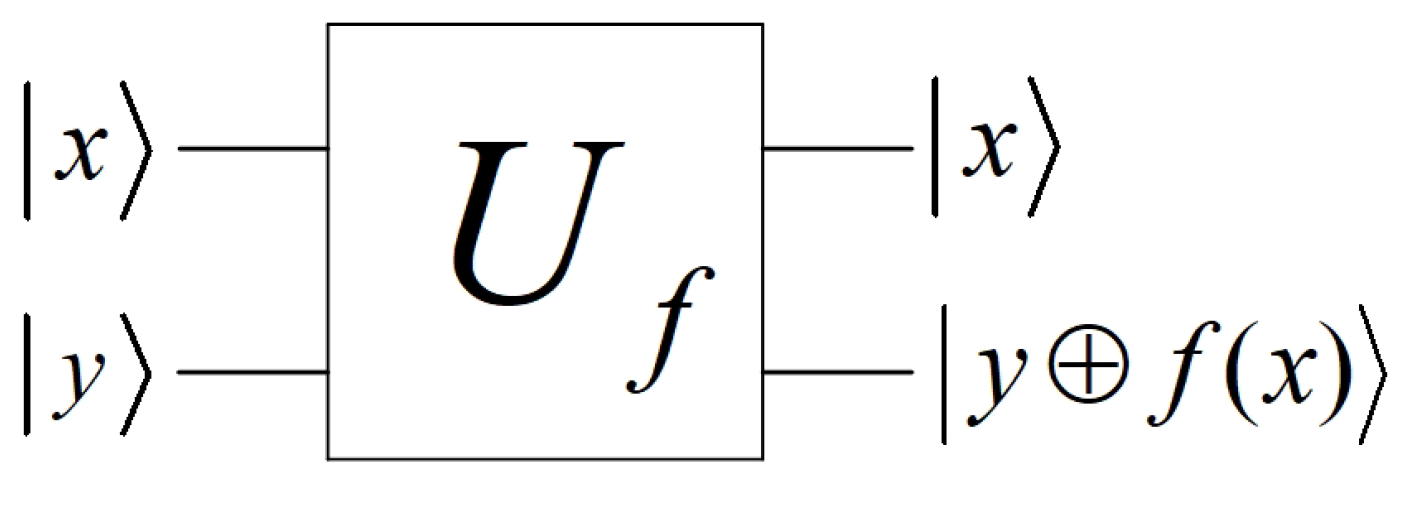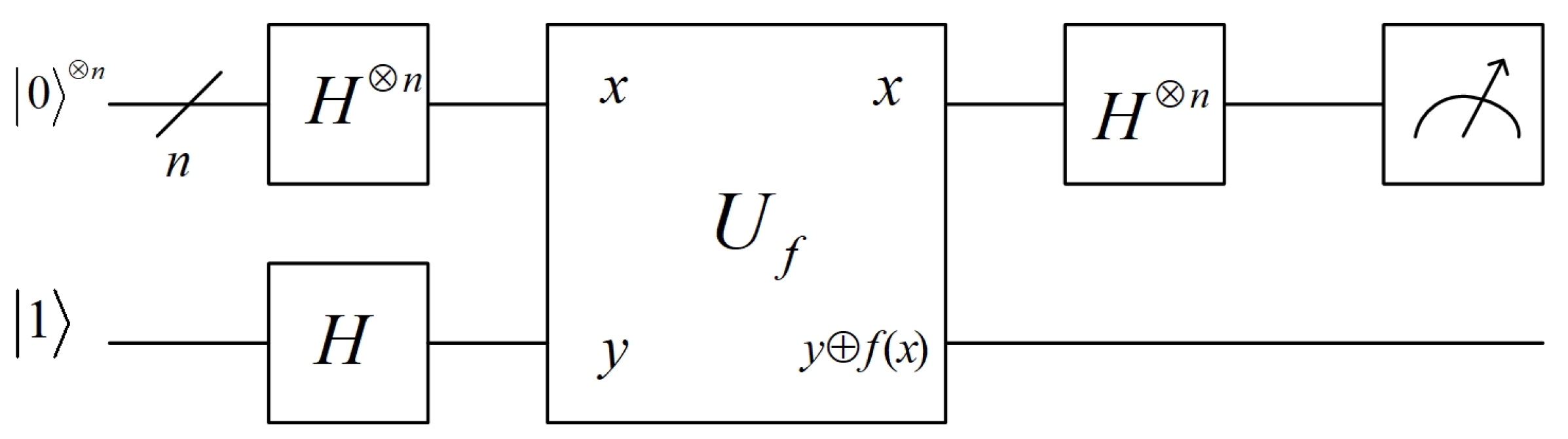Abstract
In order to design quantum-safe block ciphers, it is crucial to investigate the application of quantum algorithms to cryptographic analysis tools. In this study, we use the Bernstein–Vazirani algorithm to enhance truncated differential cryptanalysis and boomerang cryptanalysis. We first propose a quantum algorithm for finding truncated differentials, then rigorously prove that the output truncated differentials must have high differential probability for the vast majority of keys in the key space. Subsequently, based on this algorithm, we design a quantum algorithm for finding boomerang distinguishers. The quantum circuits of the two proposed quantum algorithms contain only polynomial quantum gates and qubits. Compared with classical tools for searching truncated differentials or boomerang distinguishers, the proposed algorithms can maintain the polynomial complexity while fully considering the impact of S-boxes and key scheduling.
Keywords:
quantum information; quantum cryptanalysis; symmetric cryptography; differential attack; boomerang attack PACS:
03.67.-a; 03.67.Dd
1. Introduction
Recently, research on quantum computers has continuously made new progress worldwide. Many scientists, companies and research institutions are committed to utilizing various quantum systems to develop quantum computers. It is foreseen that the successful development of quantum computers will have a profound impact in many fields. Cryptography is one such field.
The two most promising physical implementation schemes for quantum computers are trapped-ion [1] and superconducting circuit [2]. Ion-trap quantum computers have the advantage of great qubit connectivity and small decoherence, while superconducting quantum computers have the advantage of high designability and scalability. In recent years, investigations on ion-trap quantum computers have made great progress [3,4], especially in the improvement of high-fidelity gate [5]. The study of superconducting quantum computers has also made remarkable progress [6,7,8]. Google’s Sycamore quantum computer and IBM’s Eagle quantum computer are both based on superconductivity [9,10]. The power of quantum computers in information processing stems from the novel properties of quantum information that differ from those of classical information. Quantum computers possess the natural feature of parallel computing. When an n-qubit quantum computer processes data, operators actually operate on data states simultaneously. This parallelism may make some problems uncomputable in electronic computers become computable in quantum computers, such as factoring large integers, which is a difficult problem that many public key algorithms are built upon, but may be solved on quantum computers by running Shor’s algorithm [11].
The threats posed by quantum computing to symmetric algorithms have also received considerable attention. The most typical example is Grover’s algorithm [12], which requires only complexity to search an unordered database with M elements, while complexity is required in classical computing. Another important algorithm used to attack symmetric schemes is Simon’s algorithm [13]. It was first used for attacking Feistel ciphers [14,15,16] and EM schemes [14,16]. It was then combined with Grover’s algorithm for extracting the keys of ciphers with FX, Feistel and generalized Feistel structures [17,18,19]. For SPN ciphers, Jaques et al. investigated cryptanalysis of the AES algorithm using Grover’s algorithm [20]. Zhang utilized quantum algorithms to attack generalized Feistel ciphers [21]. Xiang introduced a method for constructing periodic functions and used it to attack LBlock cipher [22]. In addition to the aforementioned quantum algorithms, the Bernstein–Vazirani (BV) algorithm [23] was recently utilized in cryptanalysis [24,25,26,27].
In addition to specific attack strategies, cryptanalytic tools are also crucial for evaluating the security of cryptosystems. In this field, quantum algorithms were first used for differential cryptanalysis [25,28,29] and then for linear cryptanalysis [26,29,30]. Subsequently, quantum collision attacks on hash functions were studied [31,32]. Denisenko analyzed the complexity of quantum differential attack based on the quantum search algorithm [33]. Hosoyamada used quantum algorithms to speed-up classical multidimensional linear attack [34]. Xu et el. applied quantum search algorithm to differential meet-in-the-middle attack [35]. Quantum attacks under this model were also proposed [36,37,38]. Zhang proposed a quantum attack under quantum-related key model against the Sum of Even–Mansour construction [39]. Wu and Feng used BV algorithm to search for related-key differentials and recover key based on quantum counting algorithm [40]. These attacks showcased the superiority of quantum cryptanalytic tools over traditional cryptanalytic tools.
Many quantum attacks on block ciphers are too large in scale to be implemented or even simulated. However, researchers may be able to simulate a small part of the whole quantum attacks. For example, Zhou et al. simulated the quantum circuit of S-boxes instead of the whole cipher when studying the quantum circuit of AES [41]. Qiskit SDK is a powerful open-source tool for the simulations of quantum algorithms. Many small-scale quantum algorithms have been simulated using Qiskit [42,43,44]. LIGHTER-R is another useful tool proposed by Dasu, which can be used to design quantum circuits of Boolean functions [45].
Contributions. In this study, we explore the applications of the Bernstein–Vazirani algorithm to two variants of differential attacks: truncated differential and boomerang attacks. First, we design a quantum algorithm for searching truncated differentials that have a high probability for a large proportion of keys in the key space. Subsequently, based on this algorithm, we construct another quantum algorithm for searching for boomerang distinguishers. We demonstrate the correctness of both quantum algorithms using rigorous proofs. Both quantum algorithms request only polynomial quantum gates and qubits and have the following advantages:
- Quantum adversaries are able to perform the proposed attacks in model. Namely, there is no need for quantum queries. Compared to many proposed quantum attack algorithms [14,15,16,18,19,46] that require quantum queries, our algorithms are easier to implement.
- Classical cryptanalytic tools for finding truncated differentials with high probability or boomerang distinguishers usually cannot concern all of the details of the involved S-boxes when they are not at a small-scale. The classical tools can only search for truncated differentials or boomerang distinguishers of extremely few rounds when the S-boxes have an 8-bit scale, which is very common in block ciphers. By comparison, our quantum algorithms fully utilize the superiority of quantum computing to improve this issue. They entirely characterized the S-boxes through the accurate implementation of the unitary operator of the block ciphers.
- Classical truncated differential attacks do not involve the key scheduling under the single-key attack model, but our algorithms incorporate the key scheduling into the quantum circuits and thus fully reflect its impact to the differential propagation.
Related works. Paul et al. combined classical boomerang attack with Grover’s algorithm to quantize the traditional boomerang attack [47]. Zhou et al. improved this quantum attack strategy by allowing the retrieval of subkeys from both sides of block ciphers [48]. Boomerang attack includes two stages. The first stage is to find boomerang distinguishers and the second stage is to recover the key using the found distinguishers. The works in [47,48] only focused on the second stage. Both of them studied the use of quantum algorithms for accelerating the retrieval of key. Our work focuses on the first stage and studies the use of quantum algorithms for finding boomerang distinguishers.
2. Preliminaries
The main notations and their definitions are presented in Table 1.

Table 1.
Notations.
2.1. Differential
Throughout this study, denotes a block cipher, where is the master key. denotes the r-round iteration of . Here , denote the round keys generated from k according to the key scheduling.
Suppose x and are two plaintexts, and , . We call an output difference and an input difference. is defined as a differential of . The probability of differential is defined as
If this value is equal to p, we call a p-probability differential of .
Differential attack was proposed in 1991 and is one of the most commonly used cryptanalysis methods [49]. It utilizes a high-probability differential to break block ciphers. Let be the t-round iteration of , where . is a reduced cipher of . In differential attacks the adversaries first search for a differential of having high probability, then use this differential to screen out the right subkey involved in the last rounds of .
Variants of differential cryptanalysis have been proposed, including impossible differential attacks [50], truncated differential attacks [51] and boomerang attacks [52]. These attacks all utilize the no-random statistical properties of the ciphertext differences when specifying the plaintext differences.
Inspired by the concept of differential of block ciphers, we define the differential of Boolean functions. Let be a set containing all Boolean functions that map u bits to v bits, where are arbitrary positive integers. For any and , let and . We call an output difference and an input difference. is defined as a differential of f. The probability of differential is defined as
If this value is equal to p, we call a p-probability differential of f. Especially, for any function f in , we define two sets
Let . The vectors in are called complete differentials of f. For any vector (), is obviously a 1-probability differential. For any , cannot form a 1-probability differential of f as an input difference.
2.2. Quantum Computing
In quantum computing theory, information is stored in qubits. A qubit can be realized by any two-level quantum system, such as polarized photons. It is an analogue of a classical bit, but besides the states and , it can also be in a state that is a linear combination of and :
where and can be any complex numbers that satisfy . It is usually called a superposition state. Multiple qubits are combined via tensor product. Suppose the first qubit is in the state , the second qubit is in the state , then the system of these two qubits is in the state
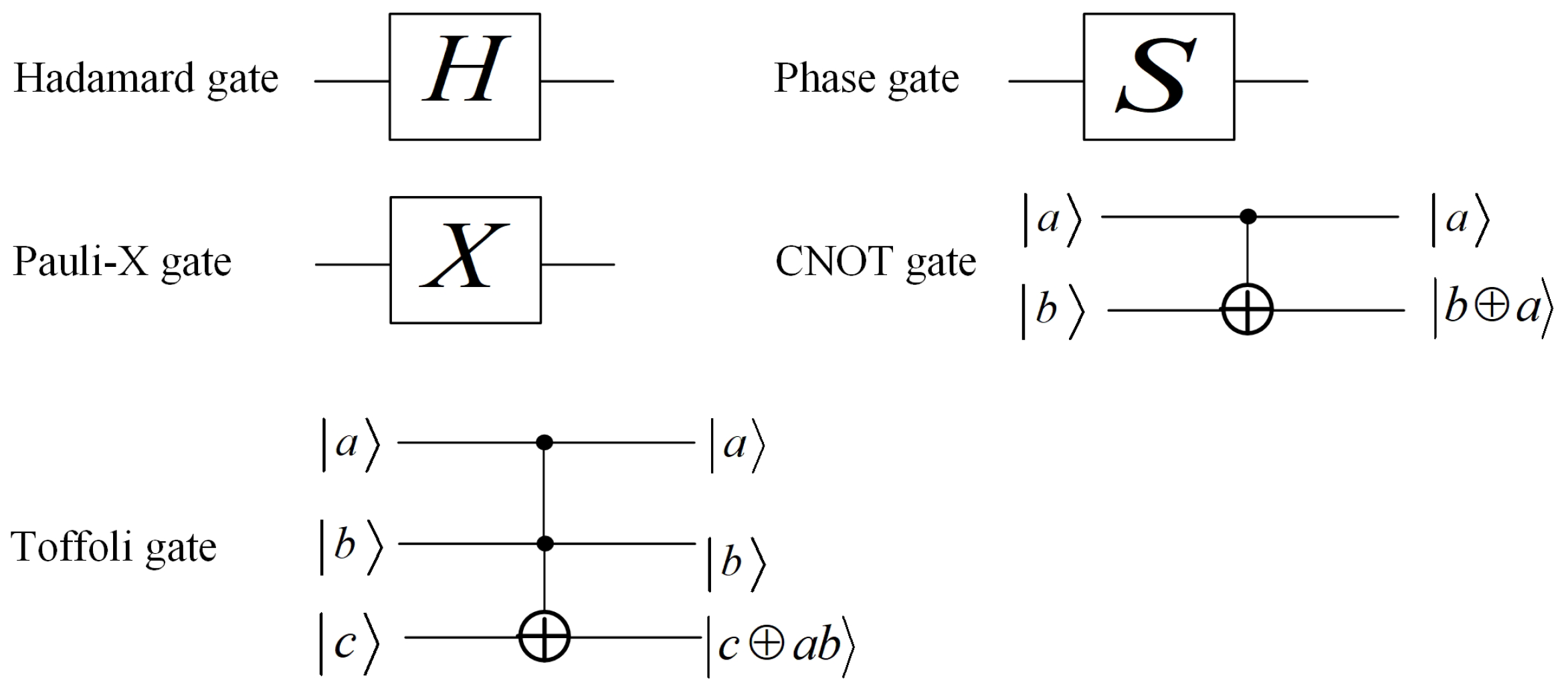
Classical bits can be manipulated by logic gates such as NAND and AND gates. Similarly, qubits are manipulated by quantum gates. Common quantum gates include Pauli-X gate (X gate), Phase gate (S gate), Hadamard gate (H gate), Controlled-NOT gate ( gate) and Toffoli gate. These gates act according to following rules:
These quantum gates are represented in quantum circuits as in Figure 1. A collection of quantum gates interlinked by quantum wires is called a quantum circuit.
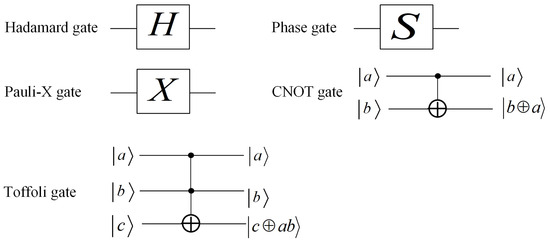
Figure 1.
The notation of common quantum gates.
Define . is the tensor product of n Hadamard gates and
The states , are all called computational basis states. Applying quantum gate on a initial state yields a superposition of all computational basis states.
For any , a quantum circuit realizes f is equivalent to realizing the following operator
can be integrated into quantum circuits as presented in Figure 2.
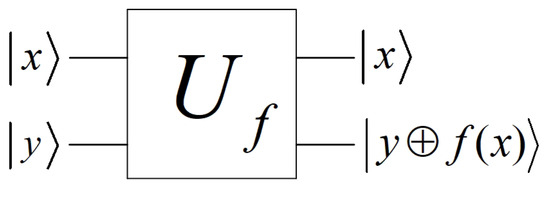
Figure 2.
Quantum gate .
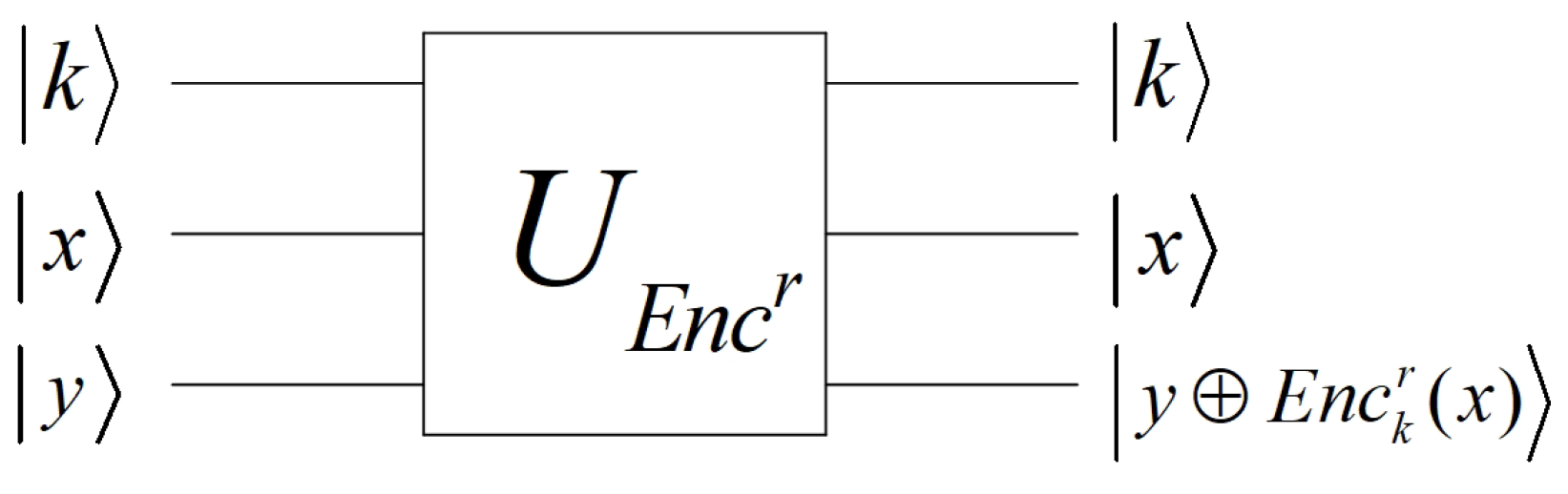
When quantum state is measured on the computational basis states, the probability of outputting x is equal to . If , the output is definitely not x. Any block cipher can be efficiently realized using a quantum circuit. Namely, there is a quantum circuit with polynomial-complexity taking a state of plaintexts and master keys as input, and outputting the corresponding ciphertexts, realizing the unitary operator
All quantum circuits can be realized using only the gates in some universal gate set [53], such as . Thus, can be realized using a quantum circuit containing only polynomial universal gates. Let the total amount of quantum universal gates in this circuit be . can be integrated into the quantum circuits as shown in Figure 3.
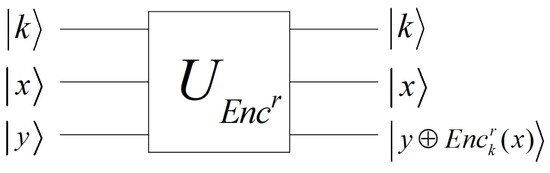
Figure 3.
Quantum gate .
Two models have been proposed to describe quantum adversaries: the and models [54,55,56]. adversaries can perform local quantum operations but can merely make queries classically to the cryptography primitives. In addition to classical queries and local quantum operations, adversaries can also query the quantum oracles of the cryptography primitives. model is more demanding because it is difficult to achieve the quantum oracles of cryptography primitives in practice.
2.3. Bernstein–Vazirani Algorithm
Bernstein–Vazirani (BV) algorithm [23] was designed to solve the problem: being a secret vector, with a quantum circuit of function , how to obtain the value of s. BV algorithm runs as follows:
- 1.
- Implement Hadamard transform on , giving
- 2.
- Using the quantum circuit of f to get
- 3.
- Discarding the unentangled last qubit, perform Hadamard operator on the remaining qubits, gettingSince , we haveTherefore, measuring gives the value of s.
For any function in , the Walsh transform is defined as the function
Equation (1) shows that, if BV algorithm is run on a general function , the final quantum state without measured will be
where is the Walsh transform of f. When this state is measured, the probability of being output is . Thus, BV algorithm running on f must output y such that .
Figure 4 shows the circuit of BV algorithm. BV algorithm needs totally universal gates. The corresponding quantum circuit requires qubits.
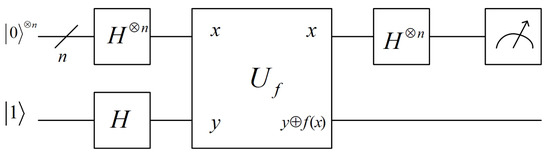
Figure 4.
Quantum circuit of BV algorithm.
Utilizing the fact that BV algorithm always outputs the vectors in the support set of the Walsh transform, Li et al. constructed a quantum algorithm used for finding differentials with high probability [57].
For any , let
It is easy to verified that . This parameter is the maximum differential probability of f except for the probability-1 differentials. The authors of [25,57] proved the following theorems that illustrate the soundness of the aforementioned algorithm.
Theorem 1
([57]). If Algorithm 1 outputs two sets and when applied to a function , then for any (), any ϵ satisfying , it holds that
| Algorithm 1 Quantum algorithm for finding high-probability differentials. |
Input:the quantum circuit realizing , a polynomial of n. Output: a differential of function f.
|
Theorem 2
([25]). Suppose and there is a constant such that . If Algorithm 1 outputs two sets and when applied to f with , then for any vector (), we have
Theorem 1 demonstrates that, for any vector (), the differential probability of to f is greater than with a probability greater .
3. Quantum Truncated Differential Attack
Knudsen introduced the truncated differential attack in 1994 [51]. This cryptanalytic method has been widely applied to attack symmetric ciphers [58,59]. In the initial version of differential attacks, the adversaries utilize full differences of plaintexts and ciphertexts, whereas in truncated differential attacks the adversaries consider differences partially determined. The adversaries only predict some bits of the differentials rather than the entire differentials.
We still consider the block cipher with the key space . A truncated differential of is a pair of vectors such that , where ∗ denotes an undetermined bit. Let , , , . then . The bits of () that take the value of zero or one are defined as predicted bits, whereas those with a value of ∗ are defined as unpredicted bits.
A truncated difference is equivalent to a set of complete differences. Define
then truncated differences and are equivalent to and , respectively. If a complete input difference is in , that is, for all , such that , we say that matches the truncated difference , and this case is denoted as ∼. Similarly, ∼ implies that matches the truncated difference .
Conditional probability
is defined as the probability of . If p is equal to the probability of , we call a p-probability truncated differential of .
Let () be a reduced cipher of . In a truncated differential attack, the adversaries first search for a truncated differential of that has a high probability and then use this truncated differential, denoted as , to recover the subkeys involved in the last rounds. In detail, the adversaries fix the plaintext difference and then use pairs of plaintexts, whose differences match , to make encryption queries and obtain pairs of corresponding ciphertexts. Subsequently, for each possible candidate subkey of the last rounds, the adversaries use it to decrypt rounds to obtain M output differences of , in the meantime calculate the amount of the differences that match . Finally, the right subkey is the subkey having the maximum count.
The amount of plaintext pairs required in such a counting scheme and the success probability of obtaining the right key are determined by the ratio of signal to noise [49], and its definition is
where L denotes the total amount of possible subkeys involved in the last rounds, p denotes the probability of , denotes the average count that every plaintext pair contributes and denotes the proportion of pairs not discarded in the preprocessing procedure. We do not consider any pre-discarding processes, therefore we set . A truncated differential attack succeeds only when . Thus, the adversaries should use a truncated differential that makes the ratio of signal to noise greater than one. The greater is, the easier it is to single out the right subkey.
In the following, we propose a quantum algorithm used for finding truncated differentials. In a classical truncated differential attack, because the adversaries do not know the value of k of the reduced cipher , they must find a truncated differential whose probability is high regardless of the value of the key k. Therefore, our quantum algorithm is designed to search for truncated differentials that have high probability for a large proportion of keys in . Specifically, by choosing a polynomial , the adversaries can force our quantum algorithm to output truncated differentials that have a high probability for more than proportion of keys in . We present the algorithm and analyze its effectiveness and complexity.
3.1. Finding Truncated Differentials via BV Algorithm
Given a reduced block cipher , let , . That is, denotes the j-th component function of . An intuitive method for finding high-probability truncated differentials is to implement Algorithm 1 on every . If Algorithm 1 finds differentials of several component functions that all have high probability and have a common input difference, then we can derive a truncated differential of that has high probability. However, running Algorithm 1 on requires quantum queries of . It is impossible to achieve this even under model because is a reduced cipher instead of the complete cipher . In the original differential attack, the adversaries are also not able to query the reduced version. They thus analyzed the detailed constructions of the cipher and searched for truncated differentials whose probabilities were high regardless of the value the key took. Inspired by this idea, we consider searching for the truncated differentials with a high probability for most keys.
Since all constructions of the cipher , except for the private key k, are public, the function
take the key as the input and is known and determined to the adversaries. Thus, the adversaries have access to the quantum circuit of the unitary operator
Let be the amount of quantum universal gates in this circuit. The adversaries also have the quantum circuit of every component function
The corresponding amount of gates is (, n). The adversaries have the quantum circuits of ’s. Therefore, they can run Algorithm 1 on ’s without quantum queries. The adversaries can run Algorithm 1 to obtain the differentials of high probability of every , then by taking a common input difference of part component functions as the input difference, they can obtain a truncated differential having high probability. According to this idea, we propose Algorithm 2 for finding truncated differentials of block ciphers.
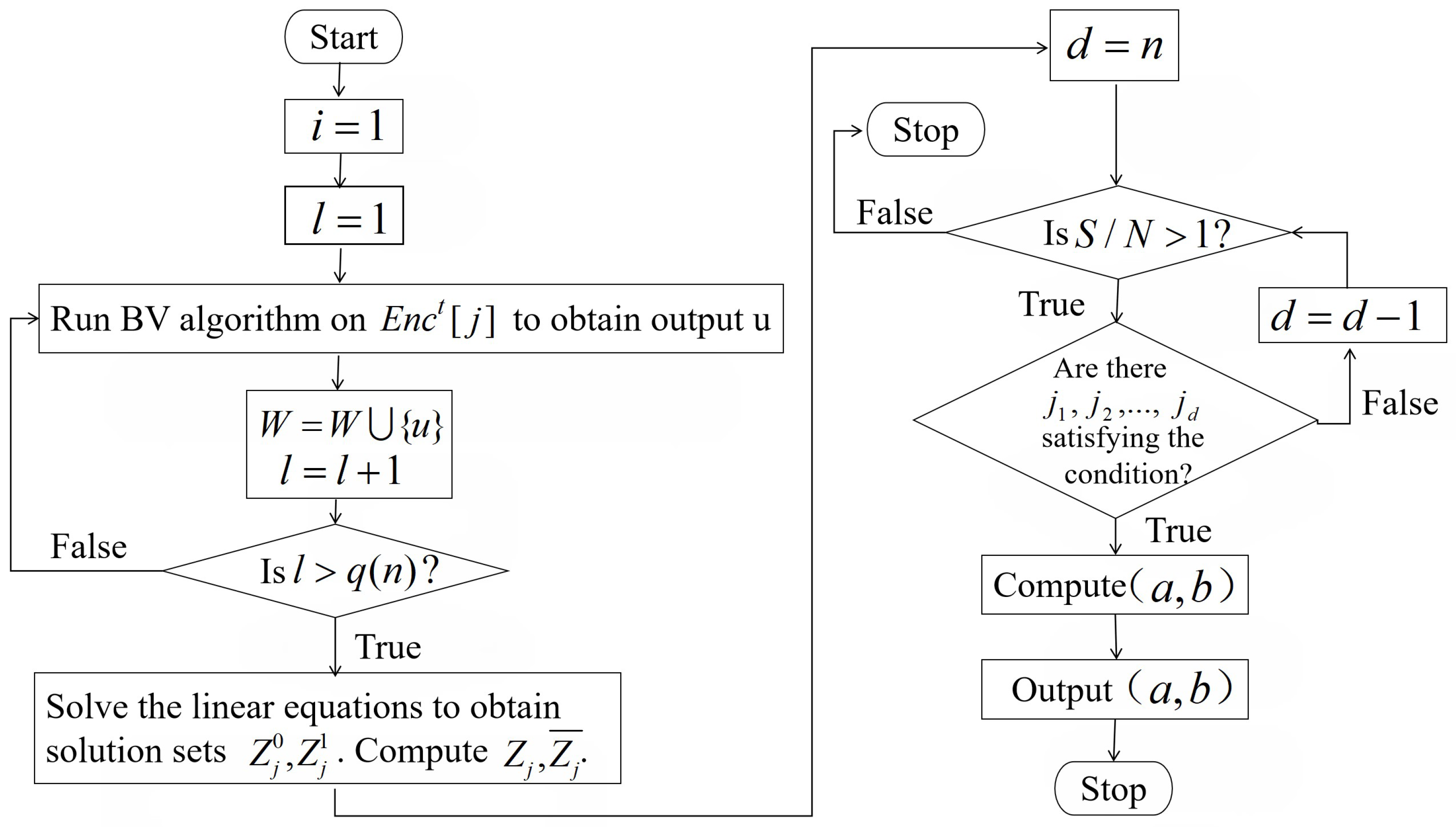
The flowchart of Algorithm 2 is presented in Figure 5. Steps 1–18 of Algorithm 2 are used to determine the high-probability differentials of for every , n. The purpose of steps 19–26 is to choose a difference which is a common input difference of as many as possible. Algorithm 2 outputs a truncated differential of . The symbol “∗” in b means that the corresponding bits are unpredicted. In a quantum truncated differential attack, the adversaries first choose a polynomial and a constant (), then implement Algorithm 2 to get an output . According to Theorem 3 which is proven in Section 3.2, the differential probability of is greater than for more than proportion of keys in with an overwhelming probability.
| Algorithm 2 Quantum algorithm for finding high-probability truncated differentials |
|
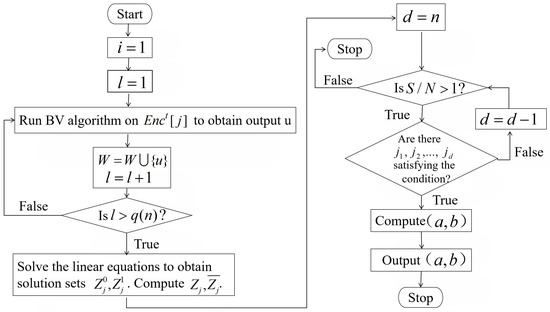
Figure 5.
The flowchart of Algorithm 2.
To implement steps 21-22, the adversaries traverse the variables , in sequence. For , , , , ⋯, , n, Algorithm 2 needs to compute the intersection of the sets , . If the intersection contains nonzero vectors, Algorithm 2 randomly chooses a nonzero vector and outputs it.
In order to demonstrate the feasibility of the output truncated differential , it is necessary to compute the ratio of signal to noise . To this end, we first calculate the parameter , which is equal to the average count that every plaintext pair contributes. There are d bits of the difference b predicted, therefore a total of output differences matching the truncated difference b. In the counting process, the ciphertexts of a fixed pair of plaintexts are decrypted using L candidate subkeys. The resulting L output differences can be viewed as random vectors. Therefore, every plaintext pair contributes
counts on average. Then
This value is greater than one because of the condition in the step 14 of Algorithm 2. After obtaining the output , the adversaries can utilize it to find the right subkey involved in the last rounds, similar to the traditional truncated differential attack. This attack should work for at least proportion of keys in . Even if “No” is output, the adversaries can adjust the polynomial and to increase the success probability.
3.2. Analysis of Algorithm 2
We analyze the correctness and efficiency of Algorithm 2. Theorem 3 indicates the correctness of Algorithm 2.
Theorem 3.
Suppose Algorithm 2 outputs , then with an overwhelming probability, there is a subset satisfying that , and for every key ,
That is, the differential probability of is greater than σ for more than proportion of keys in .
Proof.
b has d predicted bits, whose subscripts are , . Appending m zeros after the vector a gives an -bit vector , . Since , , it holds that
The -bit vector can be viewed as the output of Algorithm 2 when it is applied to for all . From Theorem 1, the probability that
holds is greater than . If the above inequality holds, then the number of z that satisfies
for both and is greater than . Likewise, the number of z satisfying Equation (3) for all is greater than . By induction, the number of z that satisfies Equation (3) for all is more than . Therefore, the probability that
holds is greater than , which is equivalent to
Let
Equation (4) indicates that . Here is the statistical expectation of and the variable k follows the uniform distribution of . Therefore, when Equation (4) holds, we have
for any polynomial . This is because, if not, then , which means
This leads to a contradiction. Thus, as long as Equation (4) holds, the proportion of the keys satisfying in must be greater than . Let S be a set of all such keys. We have , and for every ,
Let . Since , the probability that Equation (4) holds is larger than . Therefore, with an overwhelming probability, there is a subset satisfying that , and for every ,
which means that the differential probability of is greater than for more than proportion of keys in □
When implementing a truncated differential attack, the adversaries first choose a polynomial and a parameter , then run Algorithm 2 to get . The polynomial is used to characterize the expected proportion of keys under which has high probability. The parameter is used characterize the expected differential probability. According to Theorem 3, with an overwhelming probability, for at least proportion of keys in the probability of is greater than . Then the adversaries can use to determine the subkey of the last rounds as in a traditional truncated differential attack. This attack works for at least the proportion of keys in . The amount of plaintext pairs required in the counting process is determined by the value of . Based on experimental observations, about 20 to 40 appearances of right plaintext pairs are enough [49]. Therefore, about plaintext pairs are sufficient.
For analyzing the complexity, we first calculate the amounts of universal gates and qubits required and then estimate the complexity of the classical computing involved.
In Algorithm 2, BV algorithm is performed on each for times (, ). Every call requires the execution of Hadamard gates and one quantum circuit of . Thus, each call requires quantum universal gates. The total number of Hadamard gates required for Algorithm 2 is
Since it holds that
the total number of times Algorithm 2 needs to execute the quantum circuit of is . In summary, Algorithm 2 requires
universal gates in total. This number is a polynomial of n and m.
Classical computing part is to solve the linear system for each , n and . The adversaries need to solve a total of systems, and every system has equations and n unknowns. Therefore, the classical complexity of this part is . Applying BV algorithm to every requires qubits. Thus, Algorithm 2 requires
qubits in total.
The parameters involved in Algorithm 2 include the constant , polynomial , blocksize n and key length m. For the convenience of parameter analysis, we list the quantum resources required for Algorithm 2 in Table 2, then analyze the influence of these parameters on the complexity of Algorithm 2.

Table 2.
Quantum resources required for Algorithm 2.
The parameter is chosen by the adversary and satisfies . is the lower bound of the probability of truncated differentials desired by the adversary. Since truncated differentials have at least one predicted bit, the probability of any truncated differential of a random permutation is no more than . Taking is sufficient to ensure that the truncated differential output by Algorithm 2 is an effective differential. When more than one bit is predicted, the value of can take a smaller value. Therefore, the coefficient in Table 2 usually can be seen as a small constant.
The parameter is a polynomial chosen by the adversary. It characterizes the expected proportion of keys under which the output differential has high probability. The larger the value of , the more keys are feasible for the attack, but at the same time, the complexity also increases. The adversary can choose based on the expected key proportion and acceptable complexity. Especially, can be chosen as a constant , then the number of Hadamard gates is . The number of times needs to be executed quantumly is and the number of qubits is . Here we omit m because usually .
The values of parameters depend on which block cipher is attacked. For common non-lightweight block ciphers, the value of the blocksize n is generally between 128 and 256, the value of the key length m is generally between 128 and 256. For common lightweight block ciphers, the value of the blocksize n is generally between 32 and 128, the value of the key length m is generally between 64 and 256. We take , as an example and list the values of these parameters of several block ciphers and the corresponding complexity of Algorithm 2 in Table 3.

Table 3.
Quantum complexity of Algorithm 2 on specific block ciphers 1.
At present, the largest quantum chip is released by IBM, supporting over 1000-plus qubits [60]. IBM quantum platform supports the quantum circuits of 100-plus qubits. According to Table 3, it is unfeasible to completely implement or simulate Algorithm 2 on a block cipher.
3.3. Simulation
In this subsection, we simulate Algorithm 2 acting on a simple Boolean function. This demonstrates the practicality and correctness of Algorithm 2. Specifically, we choose a Boolean function , whose truth table in presented in Table 4. Let . To simulate Algorithm 2 with Qiskit, we need to construct the quantum circuit of each component function (), then apply BV algorithm on each to find high-probability differentials of . Using LIGHTER-R tool or manual deduction it is easy to obtain the construction of quantum circuits of all component functions . The code of the simulation is presented on GitHub [61].

Table 4.
Truth table of F.
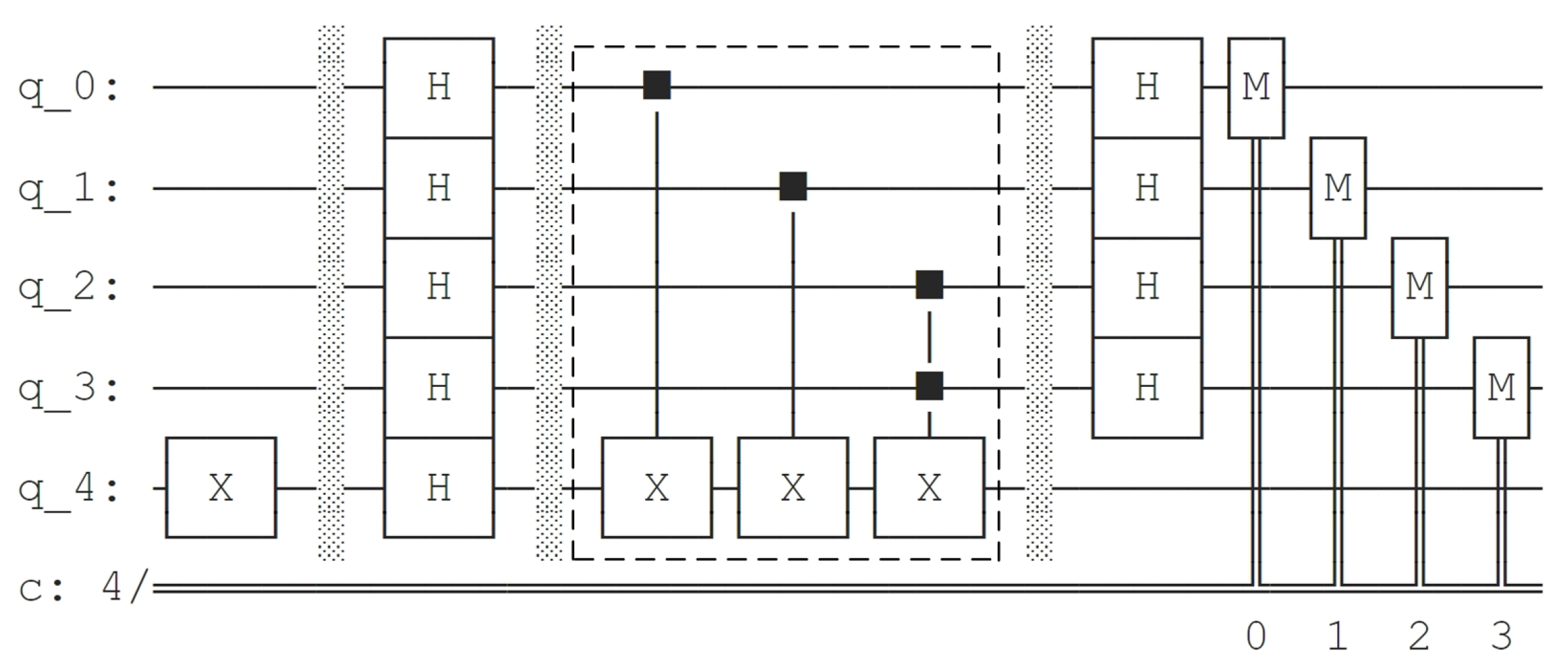
After constructing the quantum circuit of on Qiskit, we use the draw method to generate the quantum circuit diagram of BV algorithm acted on . The circuit diagram is shown in Figure 6. The symbol M denotes the measurement on the computational basis states. We add a dotted box to mark the part of quantum circuit implementing .
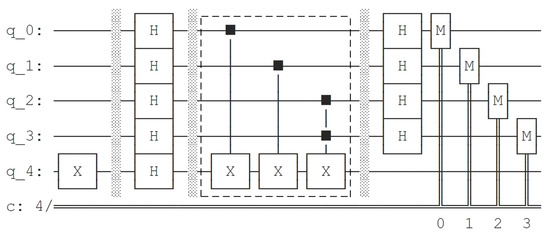
Figure 6.
Quantum circuit diagram of BV algorithm acted on generated by Qiskit.
The measurement results simulated by Qiskit are shown in Figure 7. They only take four values: 1100, 1110, 1101 and 1111. Then solving the equation
gives a fundamental solution system: . The solution set of the above equation is . The solution set of the equation
is . According to step 9 of Algorithm 2, we let .
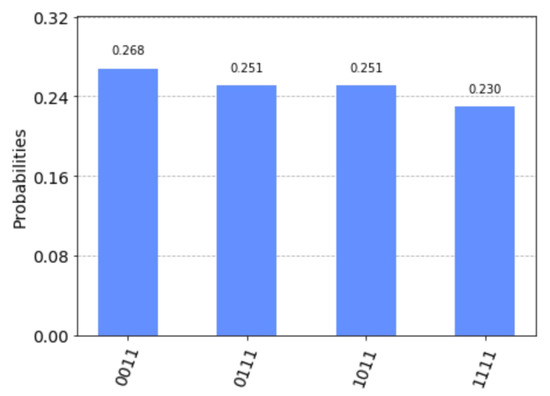
Figure 7.
Measurement results on simulated by Qiskit.
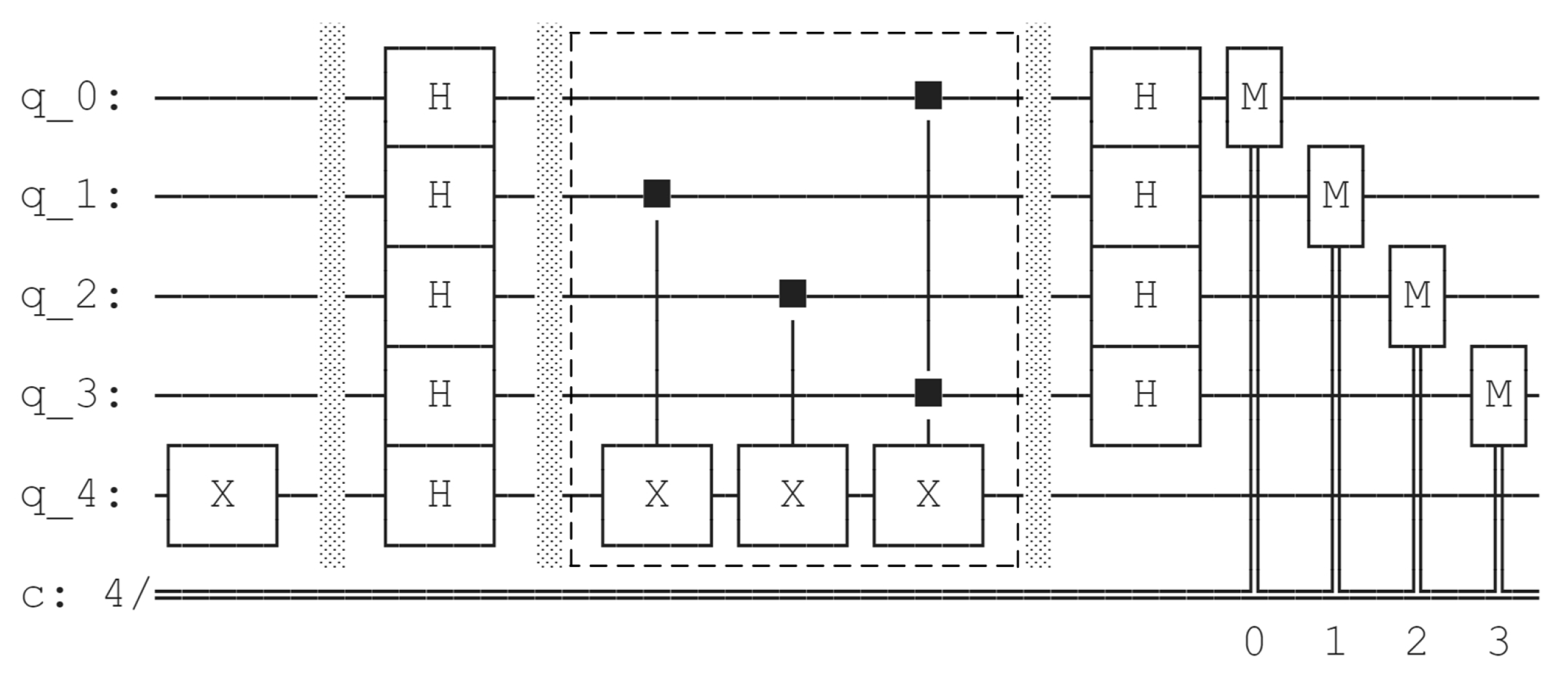
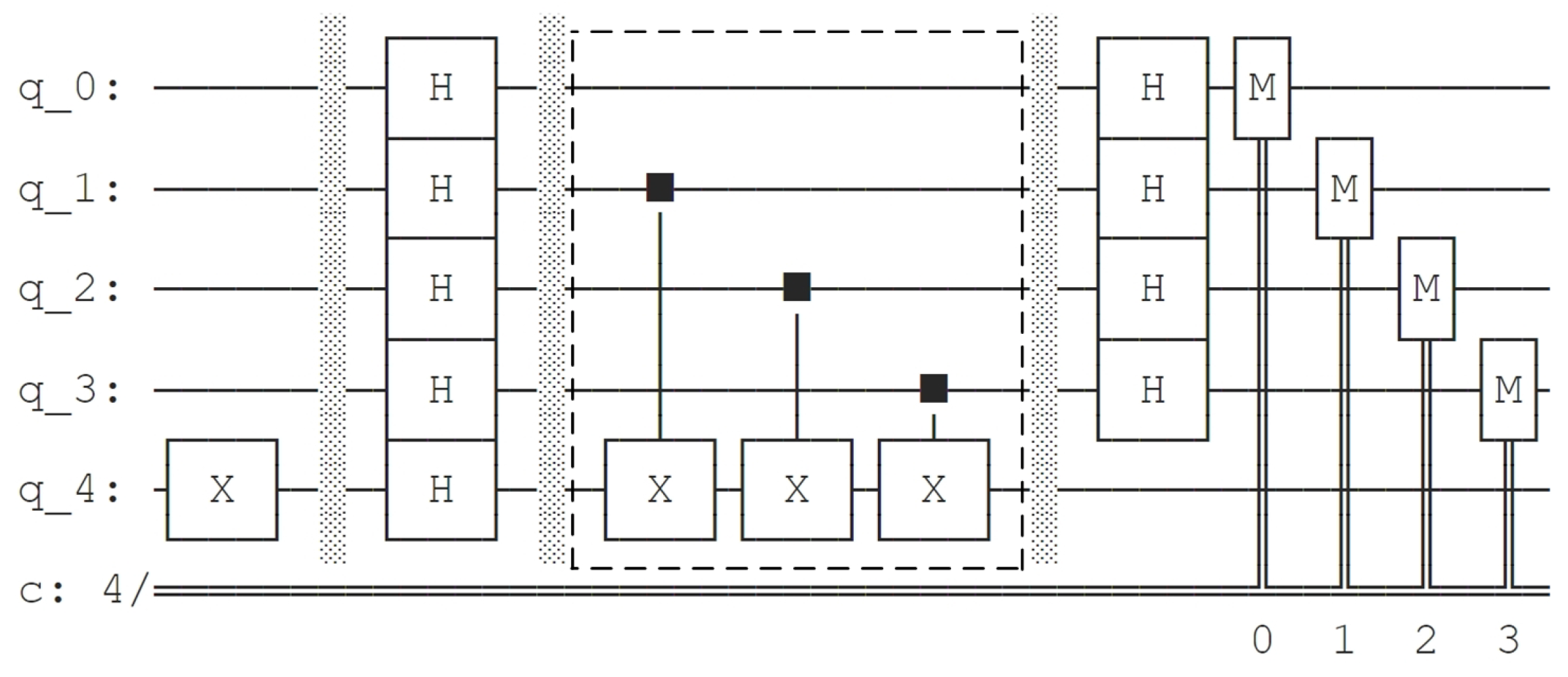
By employing a similar method, we construct the quantum circuit of on Qiskit and use the draw method to generate the quantum circuit diagram of BV algorithm acted on . The circuit diagram is shown in Figure 8. We add a dotted box to mark the part of quantum circuit implementing .
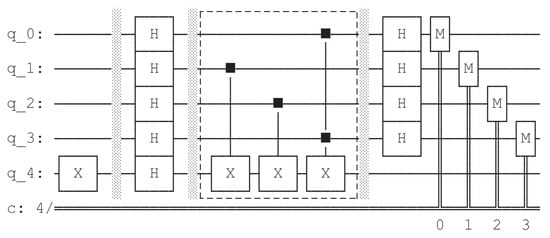
Figure 8.
Quantum circuit diagram of BV algorithm acted on generated by Qiskit.
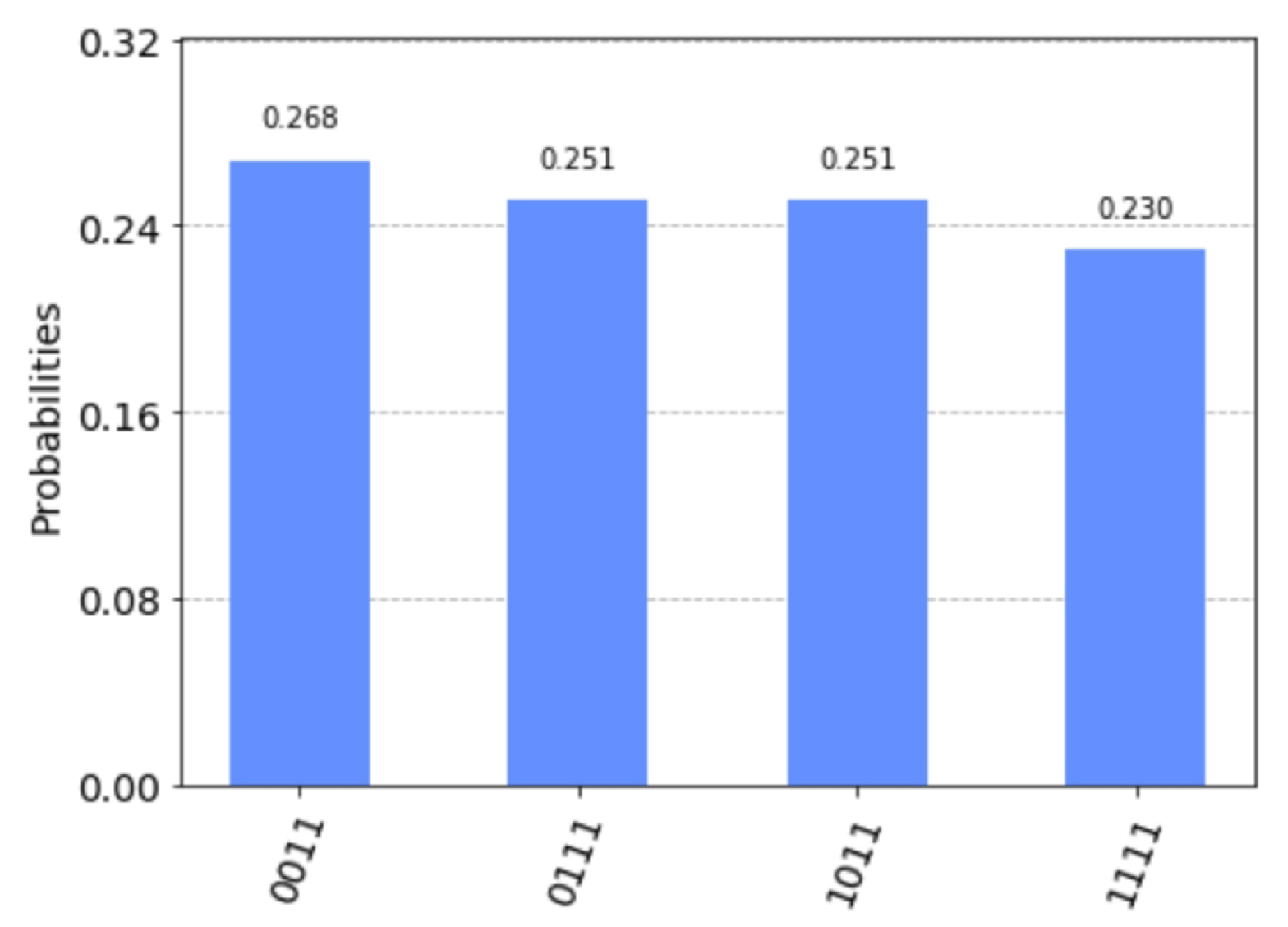
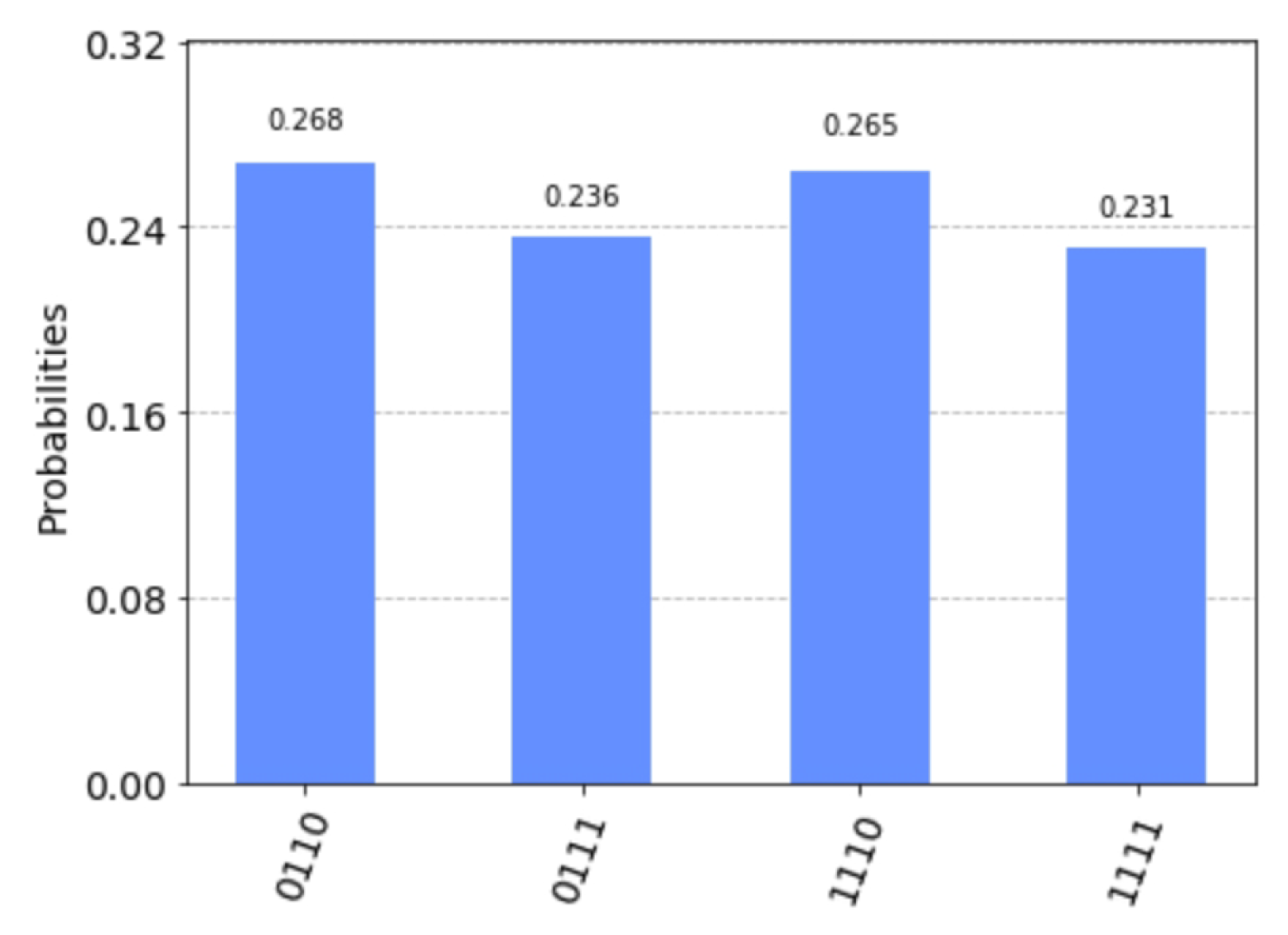
The measurement results simulated by Qiskit are shown in Figure 9. They only take four values: 0110, 1110, 0111 and 1111. Solving the equation
gives a fundamental solution system: . The solution set of the above equation is . The solution set of the equation
is . According to step 9 of Algorithm 2, we let .
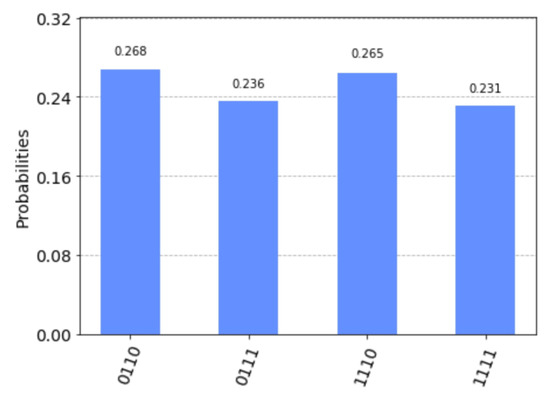
Figure 9.
Measurement results on simulated by Qiskit.
Similarly, we construct the quantum circuit of on Qiskit and use the draw method to generate the quantum circuit diagram of BV algorithm acted on . The circuit diagram is shown in Figure 10. We add a dotted box to mark the part of quantum circuit implementing .
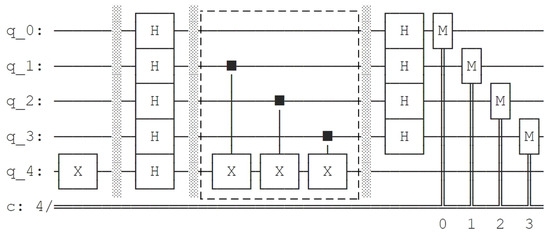
Figure 10.
Quantum circuit diagram of BV algorithm acted on generated by Qiskit.
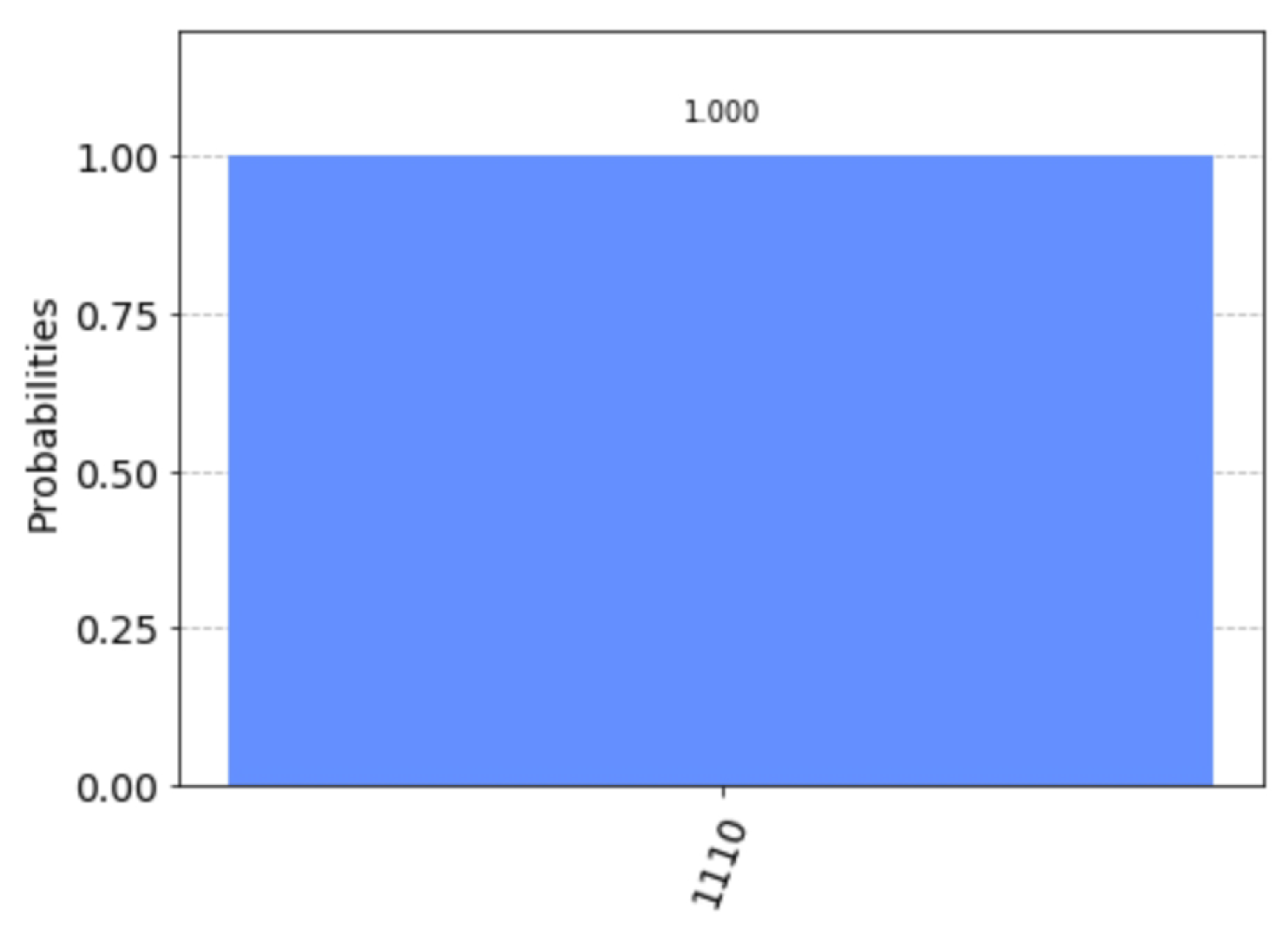
The measurement results simulated by Qiskit are shown in Figure 11. They only take one value: 0111. Solving the equation gives a fundamental solution system: . The solution set of this equation is . The solution set of the equation is . According to step 9 of Algorithm 2, we let
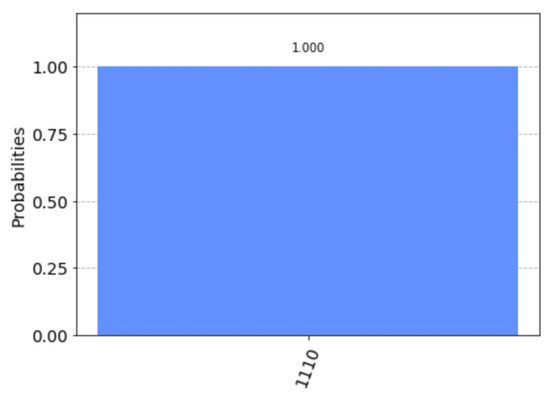
Figure 11.
Measurement results on simulated by Qiskit.
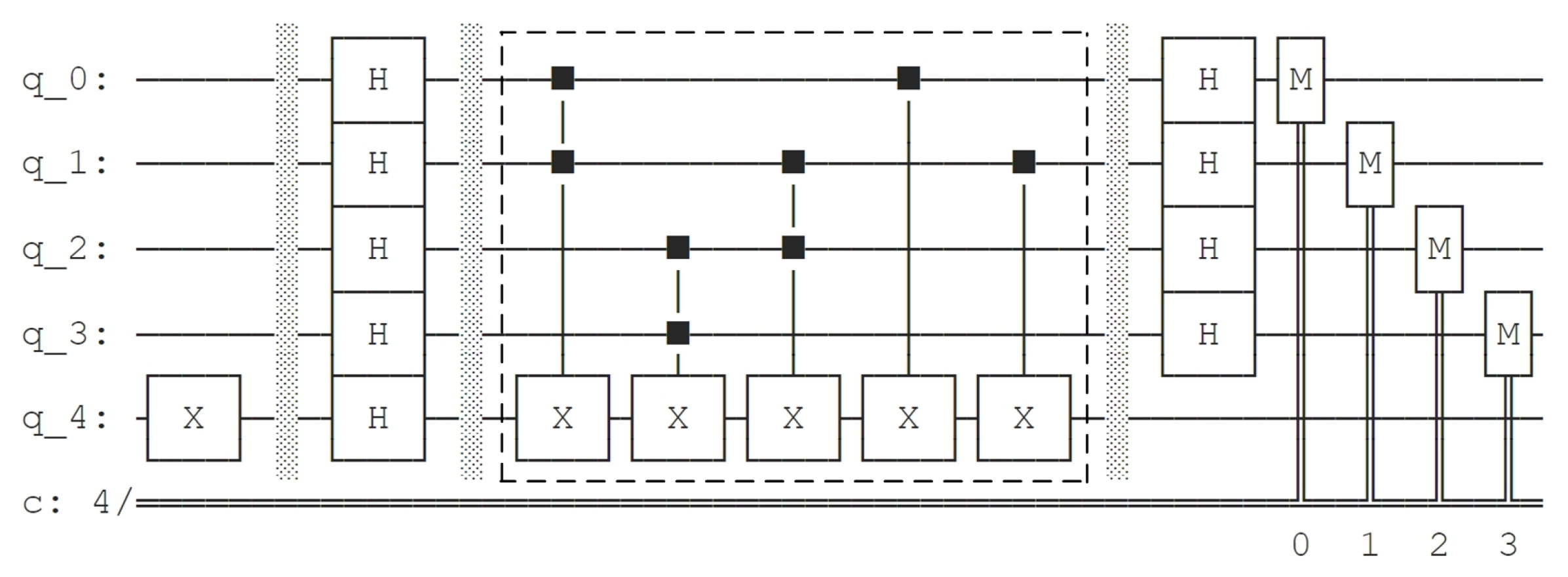
Then we construct the quantum circuit of on Qiskit and use the draw method to generate the quantum circuit diagram of BV algorithm acted on . The circuit diagram is shown in Figure 12. We add a dotted box to mark the part of quantum circuit implementing .
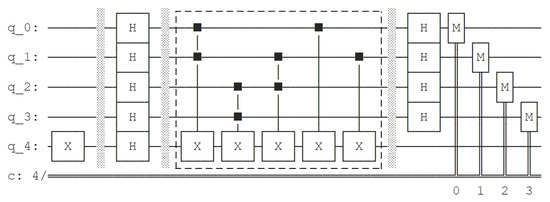
Figure 12.
Quantum circuit diagram of BV algorithm acted on generated by Qiskit.
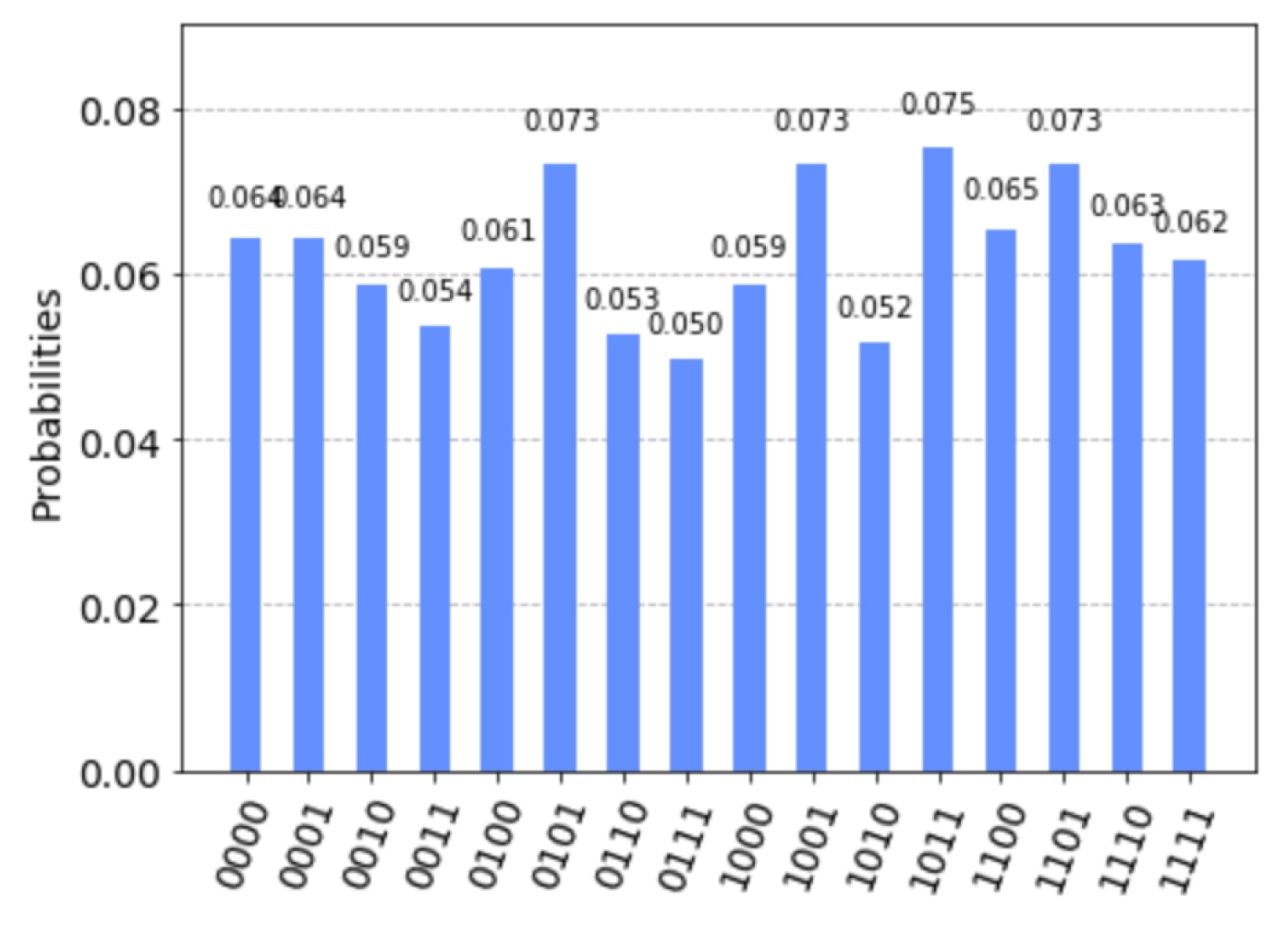
The measurement results simulated by Qiskit are shown in Figure 13. All vectors in appear in the measurement results. The system of linear equations has only one solution . The solution set of the system of linear equations is the empty set, that is, . According to step 9 of Algorithm 2, we let
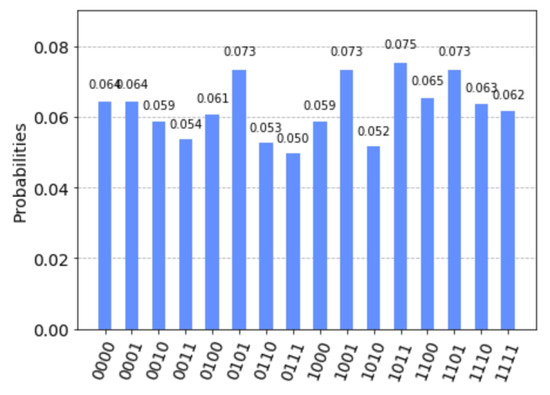
Figure 13.
Measurement results on simulated by Qiskit.
Since , and , Algorithm 2 chooses and let , then output . It is easy to verify that ∼b holds for all . The probability of the truncated differential is one. This indicates that Algorithm 2 can indeed find high-probability truncated differentials.
4. Quantum Boomerang Attack
4.1. Quantum Algorithm for Finding Boomerang Distinguisher
Since its proposal in 1999, the boomerang attack [52] has been widely used as a cryptanalysis method. The principle of boomerang cryptanalysis is to connect two differential paths having a high probability such that the adversaries can attack more rounds. This attack was proposed because, when constructing the differential characteristics of block ciphers, the probability of the differential rapidly decreases as the round number increases. It works in cases where it is difficult to find a -round differential characteristic of some block ciphers that has high probability, while it is possible to find -round and -round differential characteristics having high probability.
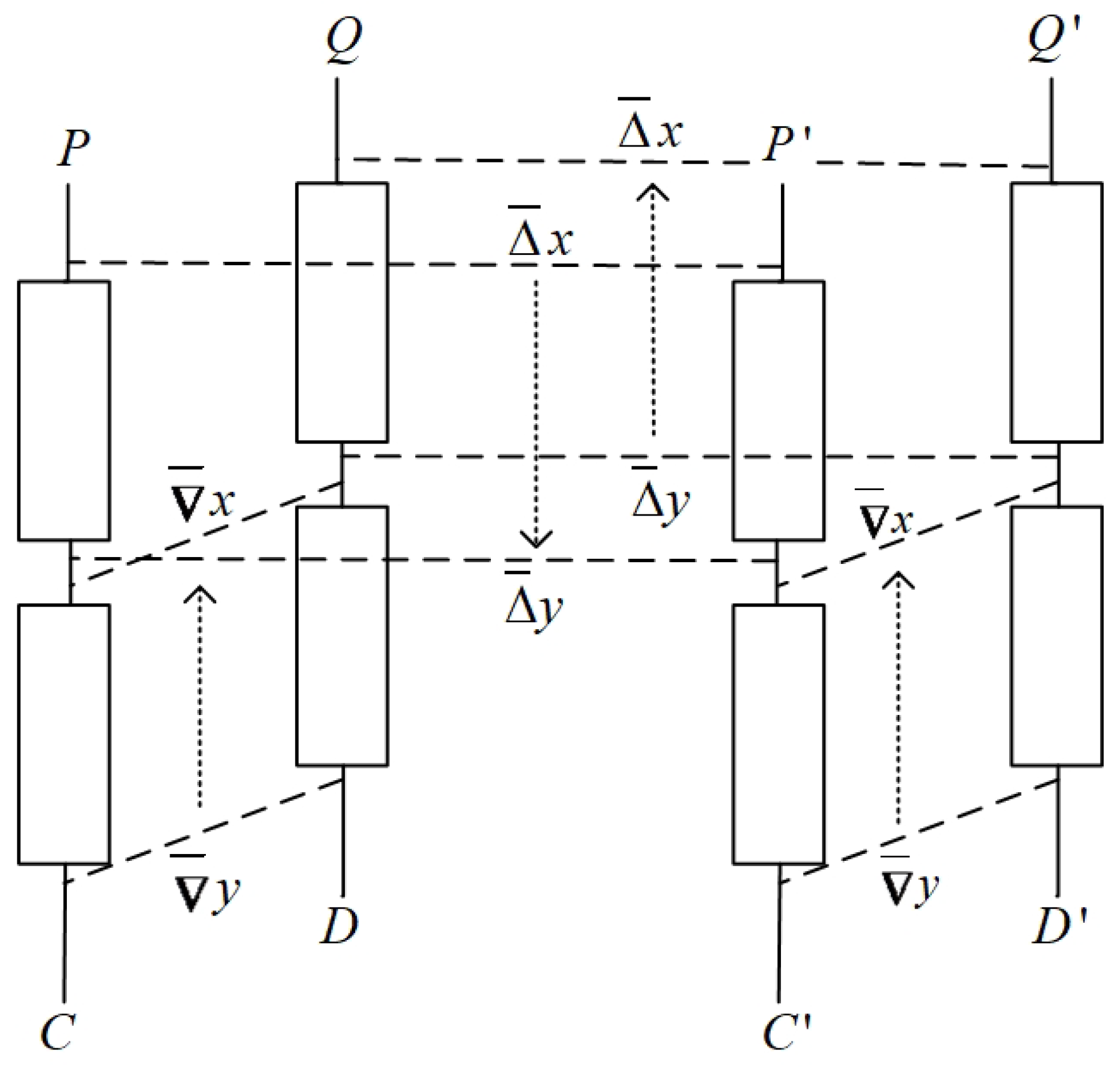
Suppose , where , has a -probability truncated differential and the inverse function of has a -probability truncated differential . As shown in Figure 14, are four plaintexts and the corresponding ciphertexts under are , respectively. are said to satisfy the differential of , if ∼ and ∼. If both and satisfy the differential of , and both and satisfy the differential of , then is called a right quadruple. Such two differentials are called a boomerang distinguisher of . Quadruples can be generated via the following method:
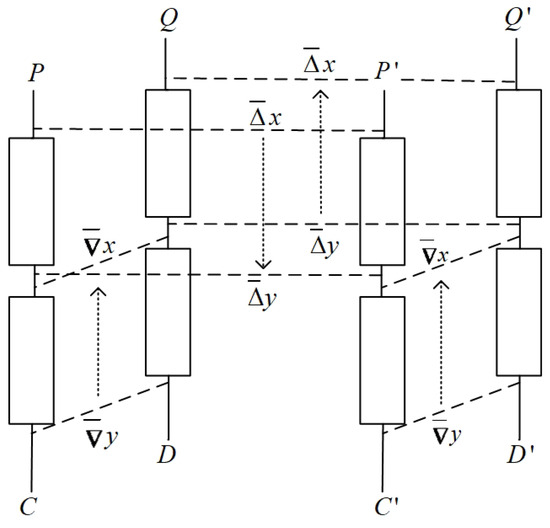
Figure 14.
Boomerang attack.
- 1.
- Choose two plaintexts satisfying ∼ and denote the corresponding ciphertexts as .
- 2.
- Compute and , and decrypt to obtain the corresponding plaintexts .
- 3.
- Test whether it holds that ∼.
The probability that satisfies differential is . The probability of satisfying the differential is . The probability of satisfying the differential is also . Under these three conditions, it naturally holds that ∼, so that the probability of ∼ is . In summary, the probability of a quadruple generated by the above method being a right quadruple is . For a random permutation, this probability is , where d is the number of determined bits of . If , then the block cipher can be distinguished from a random permutation through data analysis. A boomerang distinguisher can be used to search for the subkey involved in the last several rounds of the attacked block cipher.
The key to a boomerang attack is to find the boomerang distinguisher, namely, a -round truncated differential of and a -round truncated differential of that have a high probability. Thus, the essence of boomerang attack is to find two truncated differentials that have a high probability, which can be achieved using Algorithm 2. According to these analysis, we propose Algorithm 3 for finding boomerang distinguishers.
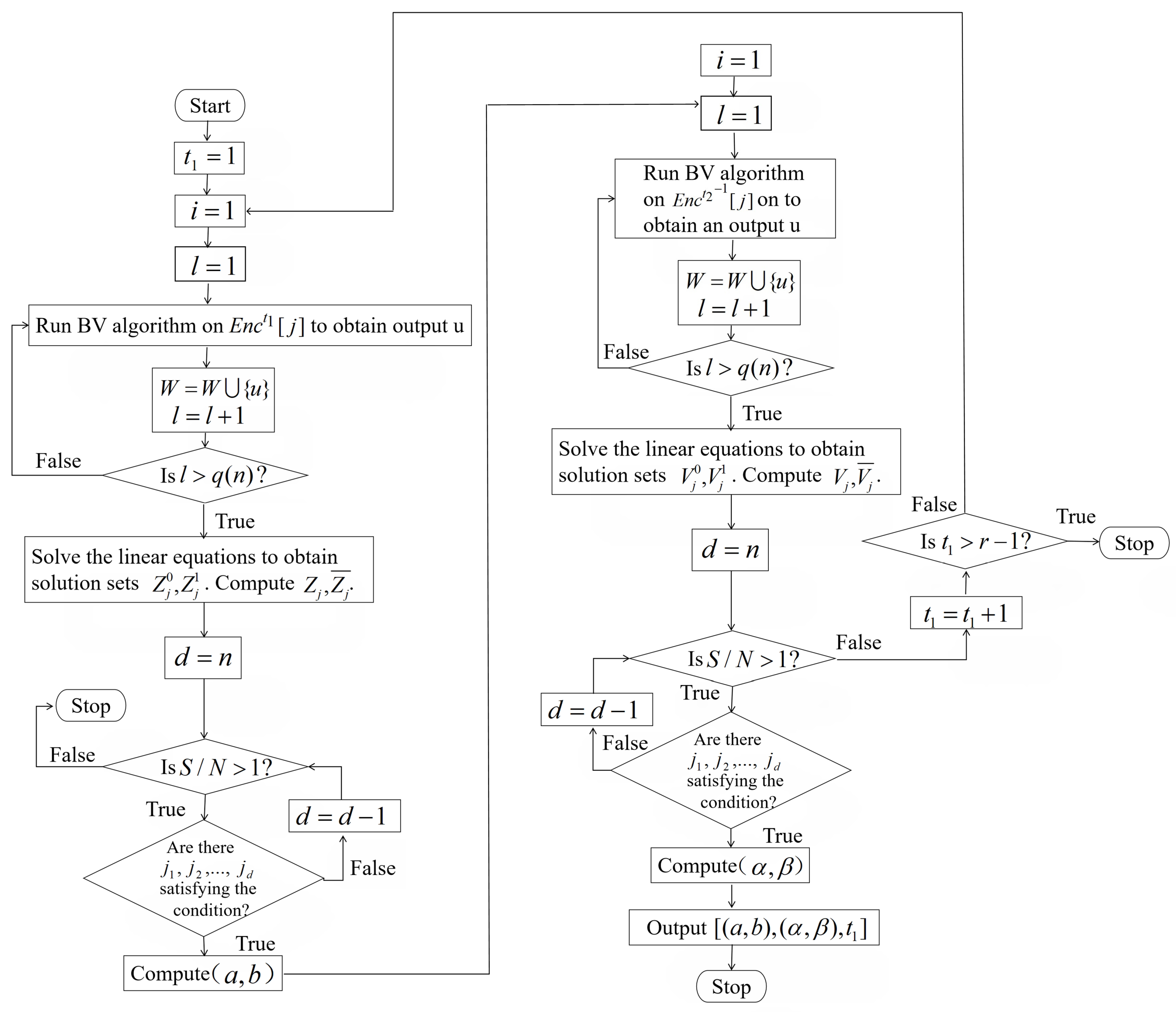
Steps 4–22 of Algorithm 3 are used to find a truncated differential of . The probability of is larger than for at least proportion of keys in . Steps 26–43 are used to find a truncated differential of . The probability of is also larger than for at least proportion of keys in . Steps 23–25 are to determine whether the truncated differential of has been found. If , no satisfied truncated differential of is found, then break out of the current loop and try the next . If and are successfully found, these two differentials form a boomerang distinguisher of . The probability of the corresponding quadruple is for more than proportion of keys in . The flowchart of Algorithm 3 is presented in Figure 15.
| Algorithm 3 Quantum algorithm for finding boomerang distinguishers. |
|
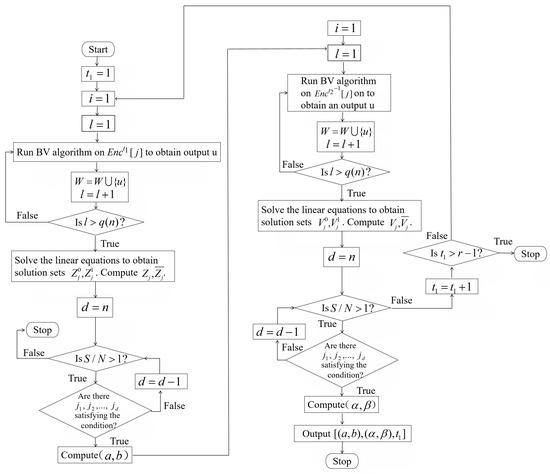
Figure 15.
The flowchart of Algorithm 3.
4.2. Analysis of Algorithm 3
The process of Algorithm 3 is actually to call Algorithm 2 on and , respectively, for all ⋯, n and . Therefore, the total number of Hadamard gates required for Algorithm 3 is
Since it holds that
the total number of times Algorithm 3 needs to execute the quantum circuit of is . This number is a polynomial of n and m. In summary, Algorithm 3 requires
universal gates in total.
Algorithm 3 calls Algorithm 2 on and , respectively, for all , and . Thus, Algorithm 3 requires
qubits in total.
The parameters involved in Algorithm 3 include the constant , polynomial , blocksize n, number of rounds r and key length m. For the convenience of parameter analysis, we list the numbers of quantum resources required for Algorithm 3 in Table 5, then analyze the influence of parameters on the complexity of Algorithm 3.

Table 5.
Quantum resources required for Algorithm 3.
Similar to Algorithm 2, the parameters of Algorithm 3 are chosen by the adversary. is the lower bound of the probability of boomerang distinguishers desired by the adversary. Since the probability of any boomerang distinguisher of a random permutation is no more than , taking is sufficient to ensure that the boomerang distinguisher output by Algorithm 3 is an effective distinguisher.
The parameter is a polynomial chosen by the adversary. It characterizes the expected proportion of keys under which the output boomerang distinguisher has high probability. Specifically, can be chosen as a constant , then the number of Hadamard gates is , the number of times needs to be executed quantumly is and the number of qubits is . Here, we omit m because usually .
The values of parameters depend on which block cipher is attacked. For common non-lightweight block ciphers, the value of the blocksize n is generally between 128 and 256, the value of the round number r is generally between 10 and 40 and the value of the key length m is generally between 128 and 256. For common lightweight block ciphers, the value of the blocksize n is generally between 32 and 128, the value of the round number r is generally between 32 and 80 and the value of the key length m is generally between 64 and 256. We take , as an example and list the values of these parameters of several common block ciphers and the corresponding complexity of Algorithm 3 in Table 6.

Table 6.
Quantum complexity of Algorithm 3 on specific block ciphers 1.
Since IBM quantum platform only supports operations of 100-plus qubits, according to Table 6, it is unfeasible to completely implement or simulate Algorithm 3 on a block cipher.
5. Results
We apply BV algorithm to truncated differential cryptanalysis and boomerang cryptanalysis and propose two quantum algorithms for finding high-probability truncated differentials and boomerang distinguishers, respectively.
For truncated differential cryptanalysis, we propose Algorithm 2 for finding truncated differentials that have high probability. Given the quantum circuit of a block cipher , Algorithm 2 takes the key as a part of the input and repeats running BV algorithm on each component function of to find truncated differentials of each , then obtains a truncated differential of by searching for a common input difference of as many component functions as possible. When executing Algorithm 2, the adversary first chooses parameters and , Algorithm 2 is then run to obtain a truncated differential. We use quantum information theory and probability theory to rigorously prove that the probability of the truncated differential output by Algorithm 2 must be greater than for more than proportion of keys in . Algorithm 2 can be run by Q1 quantum adversaries and the complexity is at polynomial level. We take as an example and list numbers of universal gates and qubits of Algorithm 2 under different values of in Table 7. The values in Table 7 are obtained according to Equations (5) and (6).

Table 7.
Quantum complexity of Algorithm 2 under .
For boomerang cryptanalysis, we propose Algorithm 3 for finding boomerang distinguishers. Given the quantum circuit of a block cipher , Algorithm 3 traverses the value of from 1 to and calls Algorithm 2 to find the truncated differentials of and , respectively, where . When executing Algorithm 3, the adversary also needs to choose parameters and , then runs Algorithm 3 to obtain a boomerang distinguisher of . The probability of generating a right quadruple of this boomerang distinguisher is greater than for more than proportion of keys in . Algorithm 3 can be run by Q1 quantum adversaries and the complexity is at polynomial level. We take as an example, and list number of universal gates and qubits of Algorithm 3 under different values of in Table 8. The values in Table 8 are obtained according to Equations (7) and (8).

Table 8.
Quantum complexity of Algorithm 3 under .
6. Conclusions
In this study, we further explored the superior computing power of quantum algorithms when applied to the field of cryptanalysis. We used BV algorithm to enhance two variants of differential cryptanalysis: truncated differential cryptanalysis and boomerang cryptanalysis. We constructed two quantum algorithms that can find truncated differentials and boomerang distinguishers of block ciphers. We prove with an overwhelming probability, that the truncated differentials or boomerang distinguishers found by our algorithms have a high probability for the most keys in the key space.
The complexity of our algorithms is at the polynomial level and adversaries can realize them in Q1 model. Compared to many proposed quantum attack algorithms [14,15,16,18,19,46] which demand quantum queries, our algorithms are more practical for realization. Classical automatic tools for searching truncated differentials with high probability or boomerang distinguishers were unable to consider all the details of S-boxes when the S-boxes were not small-scale. For example, in the case of the widely used 8-bit S-boxes, the classical searching tools can only work for extremely few rounds. In comparison, our algorithms fully utilize the strengths of quantum computing to compensate for this shortcoming. Their quantum circuits strictly compute the S-boxes when performing the operator and only have polynomial quantum gates. Moreover, classical truncated differential and boomerang attacks are unable to consider the influence of key scheduling in the attack model of single-key, but the proposed algorithms incorporate the key scheduling into the operator and thus fully consider the impact of the key scheduling. We believe the study of quantum cryptanalysis is crucial for the design of quantum-secure cryptosystems in order to prepare for the arrival of quantum computers.
For further research, reducing the quantum complexity of the proposed algorithms is a meaningful direction. It would also be interesting to explore the possible applications of quantum algorithms in other cryptanalytic tools such as integral and algebraic attacks. Quantum key distribution technique uses quantum systems to generate and distribute keys. The quantum algorithms proposed in this paper are used to attack traditional block ciphers that encrypt classical information. Investigating a combination of the proposed algorithms with quantum key distribution technique may be an interesting research direction.
Author Contributions
Conceptualization, H.X. and L.Y.; Formal analysis, H.X.; Funding acquisition, H.X.; Investigation, H.X.; Methodology, H.X.; Validation, H.X. and L.Y.; Visualization, H.X.; Writing—original draft, H.X.; Writing—review and editing, H.X. and L.Y. All authors have read and agreed to the published version of the manuscript.
Funding
This research was supported by the Beijing Natural Science Foundation (no.4234084) and Open Research Fund of Key Laboratory of Cryptography of Zhejiang Province (no.ZCL21012).
Data Availability Statement
The original contributions presented in the study are included in the article, further inquiries can be directed to the corresponding author.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Cirac, J.I.; Zoller, P. Quantum computations with cold trapped ions. Phys. Rev. Lett. 1995, 74, 4091–4094. [Google Scholar] [CrossRef] [PubMed]
- Wendin, G. Quantum information processing with superconducting circuits: A review. Rep. Prog. Phys. 2017, 80, 106001. [Google Scholar] [CrossRef]
- Malinowski, M.; Allcock, D.T.C.; Ballance, C.J. How to wire a 1000-qubit trapped-ion quantum computer. PRX Quantum 2023, 4, 040313. [Google Scholar] [CrossRef]
- Jain, S.; Sägesser, T.; Hrmo, P.; Torkzaban, C.; Stadler, M.; Oswald, R.; Axline, C.; Bautista-Salvador, A.; Ospelkaus, C.; Kienzler, D.; et al. Penning micro-trap for quantum computing. Nature 2024, 627, 510–514. [Google Scholar] [CrossRef]
- Leung, P.H.; Landsman, K.A.; Figgatt, C.; Linke, N.M.; Monroe, C.; Brown, K.R. Robust 2-qubit gates in a linear ion crystal using a frequency-modulated driving force. Phys. Rev. Lett. 2018, 120, 020501. [Google Scholar] [CrossRef]
- Bao, Z.; Li, Y.; Wang, Z.; Wang, J.; Yang, J.; Xiong, H.; Song, Y.; Wu, Y.; Zhang, H.; Duan, L. A cryogenic on-chip microwave pulse generator for large-scale superconducting quantum computing. Nat. Commun. 2024, 15, 5958. [Google Scholar] [CrossRef] [PubMed]
- Zhang, Y.; Ge, Y.Q.; Liu, Y. Simulation of Kitaev chain using one-dimensional chain of superconducting qubits and environmental effects on topological states. J. Appl. Phys. 2024, 136, 064401. [Google Scholar] [CrossRef]
- Aumentado, J.; Catelani, G.; Serniak, K. Quasiparticle poisoning in superconducting quantum computers. Phys. Today 2023, 76, 34–39. [Google Scholar] [CrossRef]
- Arute, F.; Arya, K.; Babbush, R.; Bacon, D.; Bardin, J.C.; Barends, R.; Biswas, R.; Boixo, S.; Brandao, F.G.S.L.; Buell, D.A.; et al. Quantum supremacy using a programmable superconducting processor. Nature 2019, 574, 505–510. [Google Scholar] [CrossRef] [PubMed]
- Edman, B.T. A Hardware-Focused Tour of IBM’s 127-Qubit Eagle Processor. Vanderbilt Undergrad. Res. J. 2024, 14, 21–30. [Google Scholar]
- Shor, P.W. Algorithms for quantum computation: Discrete logarithms and factoring. In Proceedings of the 35th Annual Symposium on Foundations of Computer Science, Santa Fe, NM, USA, 20–22 November 1994; pp. 124–134. [Google Scholar]
- Grover, L.K. A fast quantum mechanical algorithm for database search. In Proceedings of the Twenty-Eighth Annual ACM Symposium on Theory of Computing, Philadelphia, PA, USA, 22–24 May 1996; pp. 212–219. [Google Scholar]
- Simon, D.R. On the power of quantum computation. SIAM J. Comput. 1997, 10, 1474–1483. [Google Scholar] [CrossRef]
- Kuwakado, H.; Morii, M. Quantum distinguisher between the 3-round Feistel cipher and the random permutation. In Proceedings of the IEEE International Symposium on Information Theory, Austin, TX, USA, 13–18 June 2010; pp. 2682–2685. [Google Scholar]
- Santoli, T.; Schaffner, C. Using Simon’s algorithm to attack symmetric-key cryptographic primitives. Quantum Inf. Comput. 2017, 17, 65–78. [Google Scholar] [CrossRef]
- Kaplan, M.; Leurent, G.; Leverrier, A.; Naya-Plasencia, M. Breaking symmetric cryptosystems using quantum period finding. In Proceedings of the CRYPTO’16: 36th Annual International Cryptology Conference, Santa Barbara, CA, USA, 14–18 August 2016; pp. 207–237. [Google Scholar]
- Leander, G.; May, A. Grover Meets Simon–Quantumly Attacking the FX-construction. In Proceedings of the ASIACRYPT’17: 23rd International Conference on the Theory and Applications of Cryptology and Information Security, Hong Kong, China, 3–7 December 2017; pp. 161–178. [Google Scholar]
- Dong, X.; Wang, X. Quantum key-recovery attack on Feistel structures. Sci. China Inf. Sci. 2018, 10, 240–246. [Google Scholar] [CrossRef]
- Dong, X.; Wang, X. Quantum cryptanalysis on some generalized Feistel schemes. Sci. China Inf. Sci. 2019, 62, 22501:1–22501:12. [Google Scholar] [CrossRef]
- Jaques, S.; Naehrig, M.; Roetteler, M.; Virdia, F. Implementing Grover Oracles for Quantum Key Search on AES and LowMC. In Proceedings of the EUROCRYPT’20: 39th Annual International Conference on the Theory and Applications of Cryptographic Techniques, Zagreb, Croatia, 10–14 May 2020; pp. 280–310. [Google Scholar]
- Zhang, Z.; Wu, W.; Sui, H.; Wang, B. Quantum attacks on type-3 generalized Feistel scheme and unbalanced Feistel scheme with expanding functions. Chin. J. Electron. 2023, 32, 209–216. [Google Scholar] [CrossRef]
- Xiang, Z.; Wang, X.; Yu, B.; Sun, B.; Zhang, S.; Zeng, X.; Shen, X.; Li, N. Links between Quantum Distinguishers Based on Simon’s Algorithm and Truncated Differentials. IACR Trans. Symmetric Cryptol. 2024, 2024, 296–321. [Google Scholar] [CrossRef]
- Bernstein, E.; Vazirani, U. Quantum complexity theory. SIAM J. Comput. 1997, 26, 1411–1473. [Google Scholar] [CrossRef]
- Li, H.; Yang, L. Quantum differential cryptanalysis to the block ciphers. In Proceedings of the International Conference on Applications and Techniques in Information Security, Beijing, China, 4–6 November 2015; pp. 44–51. [Google Scholar]
- Xie, H.; Yang, L. Using Bernstein-Vazirani algorithm to attack block ciphers. Des. Codes Cryptogr. 2019, 86, 1161–1182. [Google Scholar] [CrossRef]
- Chen, H.; Li, Y.; Abla, P.; Li, Z.; Jiao, L.; Wang, M. Quantum Algorithm for Finding Impossible Differentials and Zero-Correlation Linear Hulls of Symmetric Ciphers. In Proceedings of the Australasian Conference on Information Security and Privacy, Brisbane, Australia, 5–7 July 2023; pp. 431–451. [Google Scholar]
- Zhou, B.M.; Yuan, Z. Quantum Attacks without Superposition Queries: The Offline Bernstein-Vazirani Meets Grover Algorithm. In Proceedings of the 2nd International Conference on Computing, Communication, Perception and Quantum Technology, Xiamen, China, 4–7 August 2023; pp. 68–71. [Google Scholar]
- Zhou, Q.; Lu, S.; Zhang, Z.; Sun, J. Quantum differential cryptanalysis. Quantum Inf. Process. 2015, 14, 2101–2109. [Google Scholar] [CrossRef]
- Kaplan, M.; Leurent, G.; Leverrier, A.; Naya-Plasencia, M. Quantum differential and linear cryptanalysis. IACR Trans. Symmetric Cryptol. 2016, 2016, 71–94. [Google Scholar] [CrossRef]
- Shi, R.; Xie, H.; Feng, H.; Yuan, F.; Liu, B. Quantum zero correlation linear cryptanalysis. Quantum Inf. Process. 2022, 21, 293. [Google Scholar] [CrossRef]
- Hosoyamada, A.; Sasaki, Y. Finding Hash Collisions with Quantum Computers by Using Differential Trails with Smaller Probability than Birthday Bound. In Proceedings of the EUROCRYPT’20: 39th Annual International Conference on the Theory and Applications of Cryptographic Techniques, Zagreb, Croatia, 10–14 May 2020; pp. 249–279. [Google Scholar]
- Dong, X.; Sun, S.; Shi, D.; Gao, F.; Wang, X.; Hu, L. Quantum Collision Attacks on AES-Like Hashing with Low Quantum Random Access Memories. In Proceedings of the ASIACRYPT’20: International Conference on the Theory and Application of Cryptology and Information Security, Daejeon, Republic of Korea, 7–11 November 2020; pp. 727–757. [Google Scholar]
- Denisenko, D. Quantum differential cryptanalysis. J. Comput. Virol. Hacking Tech. 2022, 18, 3–10. [Google Scholar] [CrossRef]
- Hosoyamada, A. Quantum Speed-Up for Multidimensional (Zero Correlation) Linear Distinguishers. In Proceedings of the 29th International Conference on the Theory and Application of Cryptology and Information Security, Guangzhou, China, 4–8 December 2023; pp. 311–345. [Google Scholar]
- Xu, Y.S.; Cai, B.B.; Yuan, Z.; Qin, S.J.; Gao, F.; Wen, Q.Y. Quantum Differential Meet-In-The-Middle Attack and Some Applications to Lightweight Ciphers. Adv. Quantum Technol. 2024, 2400157. [Google Scholar] [CrossRef]
- Roetteler, M.; Steinwandt, R. A note on quantum related-key attacks. Inf. Process. Lett. 2015, 115, 40–44. [Google Scholar] [CrossRef]
- Hosoyamada, A.; Aoki, K. On quantum related-key attacks on iterated Even-Mansour ciphers. IEICE Trans. Fundam. Electron. Commun. Comput. Sci. 2019, 102, 27–34. [Google Scholar] [CrossRef]
- Xie, H.; Yang, L. A quantum related-key attack based on the Bernstein-Vazirani algorithm. Quantum Inf. Process. 2020, 19, 240. [Google Scholar] [CrossRef]
- Zhang, P. Quantum Related-Key Attack Based on Simon’s Algorithm and Its Applications. Symmetry 2023, 15, 972. [Google Scholar] [CrossRef]
- Wu, H.; Feng, X. Quantum related-key differential cryptanalysis. Quantum Inf. Process. 2024, 23, 269. [Google Scholar] [CrossRef]
- Zou, J.; Wei, Z.; Sun, S.; Liu, X.; Wu, W. Quantum circuit implementations of AES with fewer qubits. In Proceedings of the 26th International Conference on the Theory and Application of Cryptology and Information Security, Daejeon, Republic of Korea, 7–11 December 2020; pp. 697–726. [Google Scholar]
- Kanazawa, N.; Egger, D.J.; Ben-Haim, Y.; Zhang, H.; Shanks, W.E.; Aleksandrowicz, G.; Wood, C.J. Qiskit experiments: A python package to characterize and calibrate quantum computers. J. Open Source Softw. 2023, 8, 5329. [Google Scholar] [CrossRef]
- Tudorache, A.G. Graph Generation for Quantum States Using Qiskit and Its Application for Quantum Neural Networks. Mathematics 2023, 11, 1484. [Google Scholar] [CrossRef]
- Khaleel, F.A.; Tawfeeq, S.K. Implementation of a modified noise-free and noisy multistage quantum cryptography protocol using QISKIT. Quantum Stud. Math. Found. 2024, 1–12. [Google Scholar] [CrossRef]
- Dasu, V.A.; Baksi, A.; Sarkar, S.; Chattopadhyay, A. Lighter-r: Optimized reversible circuit implementation for sboxes. In Proceedings of the 32nd IEEE International System-on-Chip Conference (SOCC), Singapore, 3–6 September 2019; pp. 260–265. [Google Scholar]
- Kuwakado, H.; Morii, M. Security on the quantum-type Even-Mansour cipher. In Proceedings of the 2012 International Symposium on Information Theory and Its Applications, Honolulu, HI, USA, 28–31 October; pp. 312–316.
- Frixons, P.; Naya-Plasencia, M.; Schrottenloher, A. Quantum boomerang attacks and some applications. In Proceedings of the 28th International Conference on Selected Areas in Cryptography, Virtual Event, 29 September–1 October 2021; pp. 332–352. [Google Scholar]
- Zou, H.; Zou, J.; Luo, Y. New results on quantum boomerang attacks. Quantum Inf. Process. 2023, 22, 171. [Google Scholar] [CrossRef]
- Biham, E.; Shamir, A. Differential cryptanalysis of DES-like cryptosystems. J. Cryptol. 1991, 4, 3–72. [Google Scholar] [CrossRef]
- Biham, E.; Biryukov, A.; Shamir, A. Cryptanalysis of Skipjack reduced to 31 rounds using impossible differentials. In Proceedings of the International Conference on the Theory and Applications of Cryptographic Techniques, Prague, Czech Republic, 2–6 May 1999; pp. 12–23. [Google Scholar]
- Knudsen, L.R. Truncated and higher order differentials. In Fast Software Encryption: Second International Workshop Leuven, Belgium, December 14–16, 1994 Proceedings 2; Springer: Berlin/Heidelberg, Germany, 1994; pp. 196–211. [Google Scholar]
- Wagner, D. The boomerang attack. In Fast Software Encryption: 6th International Workshop, FSE’99 Rome, Italy, March 24-26, 1999 Proceedings; Springer: Berlin/Heidelberg, Germany, 1999; pp. 156–170. [Google Scholar]
- Nielsen, M.; Chuang, I. Quantum Computation and Quantum Information, 1st ed.; Cambridge University Press: Cambridge, UK, 2000. [Google Scholar]
- Damgård, I.; Funder, J.; Nielsen, J.B.; Salvail, L. Superposition attacks on cryptographic protocols. In Proceedings of the International Conference on Information Theoretic Security, Cham, Switzerland, 28–30 November 2013; pp. 142–161. [Google Scholar]
- Boneh, D.; Zhandry, M. Secure signatures and chosen ciphertext security in a quantum computing world. In Proceedings of the CRYPTO’13: 33rd Annual Cryptology Conference, Santa Barbara, CA, USA, 18–22 August 2013; pp. 361–379. [Google Scholar]
- Gagliardoni, T.; Hlsing, A.; Schaffner, C. Semantic security and indistinguishability in the quantum world. In Proceedings of the CRYPTO’16: 36th Annual International Cryptology Conference, Santa Barbara, CA, USA, 14–18 August 2016; pp. 60–89. [Google Scholar]
- Li, H.; Yang, L. A quantum algorithm to approximate the linear structures of Boolean functions. Math. Struct. Comput. Sci 2018, 28, 1–13. [Google Scholar] [CrossRef]
- Knudsen, L.R.; Berson, T.A. Truncated differentials of SAFER. In Fast Software Encryption: Third International Workshop Cambridge, UK, February 21–23 1996 Proceedings 3; Springer: Berlin/Heidelberg, Germany, 1996; pp. 15–26. [Google Scholar]
- Knudsen, L.R.; Robshaw, M.J. Truncated differentials and Skipjack. In Proceedings of the CRYPTO’99: 19th Annual International Cryptology Conference, Santa Barbara, CA, USA, 15–19 August 1999; pp. 165–180. [Google Scholar]
- Davide, C. IBM releases first-ever 1,000-qubit quantum chip. Nature 2023, 624, 238. [Google Scholar]
- Simulation-with-Qiskit. Available online: https://github.com/huiqinxie/Simulation-with-Qiskit (accessed on 22 August 2024).
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).