Mobile Personal Multi-Access Edge Computing Architecture Composed of Individual User Devices
Abstract
:1. Introduction
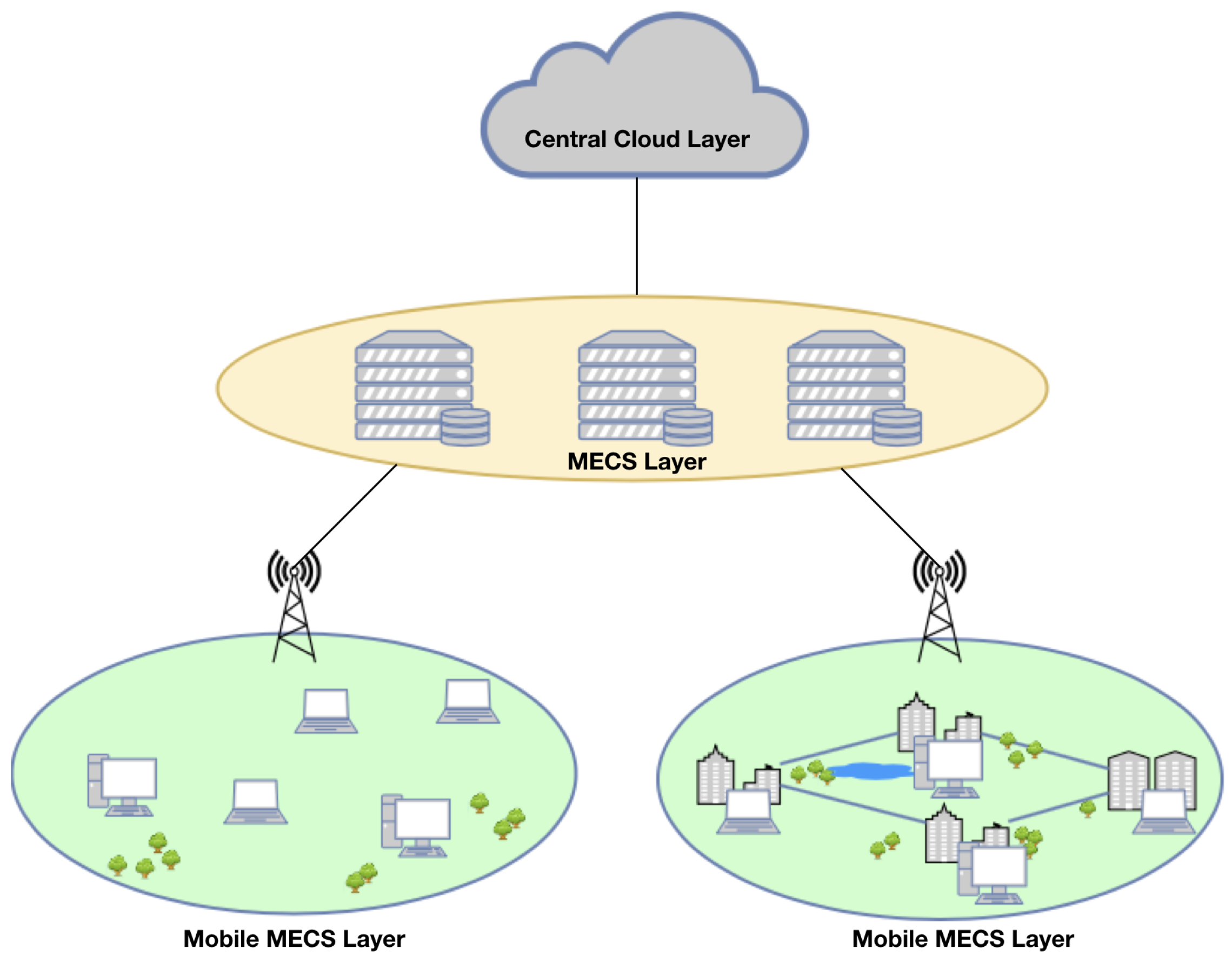
2. Proposed Mobile Personal Multi-Access Edge Computing Architecture
2.1. Components to Utilize Mobile Device as MECS
2.2. Working Distribution and Merging Process
2.3. Detailed Operation Process of the Proposed Scheme
3. Performance Evaluation
3.1. Service Delivery Time for the Number of mMECS
3.2. Average Service Time Due to the Movement of the Mobile User
4. Conclusions
Author Contributions
Funding
Conflicts of Interest
Abbreviations
| MEC | Multi-Access Edge Computing |
| MECS | Multi-Access Edge Computing Server |
| VR | Virtual Reality |
| AR | Augmented Reality |
| GCP | Google Cloud Platform |
| EC2 | Amazon Elastic Compute Cloud |
| IaaS | Infrastructure as a Service |
| PaaS | Platform as a Service |
| SaaS | Software as a Service |
| 5G | Fifth Generation |
| URLLC | Ultra-Reliable and Low-Latency Communication |
| ETSI | European Telecommunications Standard Institute |
| RAN | Radio Access Network |
| mMECS | mobile MECS |
| mNR | mobile Node Registration |
| mMT | mMECS Management Table |
| TOR | Task Offloading Request |
| mSR | mobile Service Request |
| mSRA | mSR Acknowledgement |
| MIPS | Million Instructions Per Second |
| ML | Machine Learning |
References
- Liu, Q.; Huang, S.; Opadere, J.; Han, T. An edge network orchestrator for mobile augmented reality. In Proceedings of the IEEE INFOCOM 2018-IEEE Conference on Computer Communications, Honolulu, HI, USA, 15–19 April 2018; pp. 756–764. [Google Scholar]
- Sukhmani, S.; Sadeghi, M.; Erol-Kantarci, M.; El Saddik, A. Edge Caching and Computing in 5G for Mobile AR/VR and Tactile Internet. IEEE Multimed. 2018, 26, 21–30. [Google Scholar] [CrossRef]
- Qiao, X.; Ren, P.; Dustdar, S.; Liu, L.; Ma, H.; Chen, J. Web AR: A Promising Future for Mobile Augmented Reality—State of the Art, Challenges, and Insights. Proc. IEEE 2019, 107, 651–666. [Google Scholar] [CrossRef]
- Yang, X.; Chen, Z.; Li, K.; Sun, Y.; Liu, N.; Xie, W.; Zhao, Y. Communication-constrained mobile edge computing systems for wireless virtual reality: Scheduling and tradeoff. IEEE Access 2018, 6, 16665–16677. [Google Scholar] [CrossRef]
- Elbamby, M.S.; Perfecto, C.; Bennis, M.; Doppler, K. Toward low-latency and ultra-reliable virtual reality. IEEE Netw. 2018, 32, 78–84. [Google Scholar] [CrossRef] [Green Version]
- Lee, J.; Kim, D.; Lee, J. Mobile Edge Computing Based Immersive Virtual Reality Streaming Scheme. Comput. Inform. 2020, 38, 1131–1148. [Google Scholar] [CrossRef]
- Wang, S.; Xu, J.; Zhang, N.; Liu, Y. A survey on service migration in mobile edge computing. IEEE Access 2018, 6, 23511–23528. [Google Scholar] [CrossRef]
- Hao, Z.; Yi, S.; Chen, Z.; Li, Q. Nomad: An Efficient Consensus Approach for Latency-Sensitive Edge-Cloud Applications. In Proceedings of the IEEE INFOCOM 2019, Paris, France, 29 April–2 May 2019; pp. 2539–2547. [Google Scholar]
- Palmarini, R.; Erkoyuncu, J.A.; Roy, R.; Torabmostaedi, H. A systematic review of augmented reality applications in maintenance. Robot. Comput. Integr. Manuf. 2018, 49, 215–228. [Google Scholar] [CrossRef] [Green Version]
- Li, S.; Xu, L.D.; Zhao, S. 5G Internet of Things: A survey. J. Ind. Inf. Integr. 2018, 10, 1–9. [Google Scholar] [CrossRef]
- Chen, M.H.; Dong, M.; Liang, B. Resource sharing of a computing access point for multi-user mobile cloud offloading with delay constraints. IEEE Trans. Mob. Comput. 2018, 17, 2868–2881. [Google Scholar] [CrossRef] [Green Version]
- Zhou, B.; Dastjerdi, A.V.; Calheiros, R.N.; Buyya, R. An online algorithm for task offloading in heterogeneous mobile clouds. ACM Trans Internet Technol. (TOIT) 2018, 18, 23. [Google Scholar]
- Challita, S.; Zalila, F.; Gourdin, C.; Merle, P. A Precise Model for Google Cloud Platform. In Proceedings of the 2018 IEEE International Conference on Cloud Engineering (IC2E), Orlando, FL, USA, 17–20 April 2018; Volume 10, pp. 177–183. [Google Scholar]
- Ostermann, S.; Iosup, A.; Yigitbasi, N.; Prodan, R.; Fahringer, T.; Epema, D. A performance analysis of EC2 cloud computing services for scientific computing. In Proceedings of the International Conference on Cloud Computing, Munich, Germany, 19–21 October 2009; pp. 115–131. [Google Scholar]
- Langmead, B.; Nellore, A. Cloud computing for genomic data analysis and collaboration. Nat. Rev. Genet. 2018, 19, 208. [Google Scholar] [CrossRef] [PubMed]
- Jacobson, V.; Smetters, D.K.; Thornton, J.D.; Plass, M.F.; Briggs, N.H.; Braynard, R.L. Networking named content. In Proceedings of the 5th International Conference on Emerging Networking Experiments and Technologies, Rome, Italy, 1–4 December 2009; pp. 1–12. [Google Scholar]
- Lee, J.; Lee, J. Efficient Mobile Content-Centric Networking Using Fast Duplicate Name Prefix Detection Mechanism. Contemp. Eng. Sci. 2014, 7, 1345–1353. [Google Scholar] [CrossRef] [Green Version]
- Rosário, D.; Schimuneck, M.; Camargo, J.; Nobre, J.; Both, C.; Rochol, J.; Gerla, M.T. Service migration from cloud to multi-tier fog nodes for multimedia dissemination with QoE support. Sensors 2018, 18, 329. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Lee, J.; Lee, J. Pre-allocated duplicate name prefix detection mechanism using naming-pool in mobile content-centric network. In Proceedings of the 2015 Seventh International Conference on Ubiquitous and Future Networks, Sapporo, Japan, 7–10 July 2015; pp. 115–117. [Google Scholar]
- Li, H.; Shou, G.; Hu, Y.; Guo, Z. Mobile edge computing: Progress and challenges. In Proceedings of the 2016 4th IEEE International Conference on Mobile Cloud Computing, Services, and Engineering (MobileCloud), Services, Oxford, UK, 29 March–1 April 2016. [Google Scholar]
- Bonomi, F.; Milito, R.; Zhu, J.; Addepalli, S. Fog computing and its role in the internet of things. In Proceedings of the First Edition of the MCC Workshop on Mobile Cloud Computing, Helsinki, Finland, 17 August 2012; pp. 13–16. [Google Scholar]
- Trakadas, P.; Nomikos, N.; Michailidis, E.T.; Zahariadis, T.; Facca, F.M.; Breitgand, D.; Rizou, S.; Masip, X.; Gkonis, P. Hybrid Clouds for Data-Intensive, 5G-Enabled IoT Applications: An Overview, Key Issues and Relevant Architecture. Sensors 2019, 19, 3591. [Google Scholar] [CrossRef] [Green Version]
- Mach, P.; Becvar, Z. Mobile edge computing: A survey on architecture and computation offloading. IEEE Internet Things J. 2018, 5, 450–465. [Google Scholar] [CrossRef] [Green Version]
- Lee, J.; Kim, D.; Lee, J. ZONE-Based Multi-Access Edge Computing Scheme for User Device Mobility Management. Appl. Sci. 2019, 9, 2308. [Google Scholar] [CrossRef] [Green Version]
- Zuo, C.; Shao, J.; Wei, G.; Xie, M.; Ji, M. CCA-secure ABE with outsourced decryption for fog computing. Future Gener. Comput. Syst. 2018, 78, 730–738. [Google Scholar] [CrossRef]
- Mahmud, R.; Kotagiri, R.; Buyya, R. Fog computing: A taxonomy, survey and future directions. In Internet of Everything; Springer: Singapore, 2018; pp. 103–130. [Google Scholar]
- Bitam, S.; Zeadally, S.; Mellouk, A. Fog computing job scheduling optimization based on bees swarm. Enterp. Inf. Syst. 2018, 12, 373–397. [Google Scholar] [CrossRef]
- Hu, Y.C.; Patel, M.; Sabella, D.; Sprecher, N.; Young, V. Mobile Edge Computing—A Key Technology towards 5G; ETSI White Paper; European Telecommunications Standards Institute: Valbonne, France, 2015; Volume 11, pp. 1–16. [Google Scholar]
- Aloqaily, M.; Al Ridhawi, I.; Salameh, H.B.; Jararweh, Y. Data and service management in densely crowded environments: Challenges, opportunities, and recent developments. IEEE Commun. Mag. 2019, 57, 81–87. [Google Scholar] [CrossRef]
- Lee, J.; Lee, J. Mobile Edge Computing based Charging Infrastructure considering Electric Vehicle Charging Efficiency. J. Korea Acad. Ind. Coop. Soc. 2017, 18, 669–674. [Google Scholar]
- Balasubramanian, V.; Aloqaily, M.; Zaman, F.; Jararweh, Y. Exploring Computing at the Edge: A Multi-Interface System Architecture Enabled Mobile Device Cloud. In Proceedings of the IEEE 7th International Conference on Cloud Networking (CloudNet), Tokyo, Japan, 22–24 October 2018; pp. 1–4. [Google Scholar]
- Wo, H.; Sun, Y.; Wolter, K. Energy-Efficient Decision Making for Mobile Cloud Offloading. IEEE Trans. Cloud Comput. 2020, 8, 570–584. [Google Scholar]
- Chu, S.; Fang, Z.; Song, S.; Zhang, Z.; Gao, C. Efficient Multi-Channel Computation Offloading for Mobile Edge Computing: A Game-Theoretic Approach. IEEE Trans. Cloud Comput. 2020, 8, 1. [Google Scholar] [CrossRef]
- Joyee, S.; Ruj, S. Efficient Decentralized Attribute Based Access Control for Mobile Clouds. IEEE Trans. Cloud Comput. 2017, 8, 124–137. [Google Scholar]
- Sonmez, C.; Ozgovde, A.; Ersoy, C. EdgeCloudSim: An environment for performance evaluation of edge computing systems. Trans. Emerg. Telecommun. Technol. 2018, 29, e3493. [Google Scholar] [CrossRef]
- Calheiros, R.N.; Ranjan, R.; Beloglazov, A.; De Rose, C.A.; Buyya, R. CloudSim: A Toolkit for Modeling and Simulation of Cloud Computing Environments and Evaluation of Resource Provisioning Algorithms. Softw. Pract. Exper. 2011, 41, 23–50. [Google Scholar] [CrossRef]
- Lee, J.; Lee, J. Hierarchical Mobile Edge Computing Architecture Based on Context Awareness. Appl. Sci. 2018, 8, 1160. [Google Scholar] [CrossRef] [Green Version]
- Lee, J.; Lee, J. Preallocated duplicate name prefix detection mechanism using naming pool in CCN based mobile IoT networks. Mob. Inf. Syst. 2016, 2016. [Google Scholar] [CrossRef]
- Pakusch, C.; Stevens, G.; Boden, A.; Bossauer, P. Unintended Effects of Autonomous Driving: A Study on Mobility Preferences in the Future. Sustainability 2018, 10, 2404. [Google Scholar] [CrossRef] [Green Version]
- Wu, R.; Luo, G.; Yang, Q.; Shao, J. Learning individual moving preference and social interaction for location prediction. IEEE Access 2018, 6, 10675–10687. [Google Scholar] [CrossRef]
- Bhimani, J.; Yang, Z.; Mi, N.; Yang, J.; Xu, Q.; Awasthi, M.; Balakrishnan, V. Docker container scheduler for I/O intensive applications running on NVMe SSDs. IEEE Trans. Multi Scale Comput. Syst. 2018, 4, 313–326. [Google Scholar] [CrossRef]
- Merkel, D. Docker: Lightweight linux containers for consistent development and deployment. Linux J. 2014, 239, 2. [Google Scholar]
- Felter, W.; Ferreira, A.; Rajamony, R.; Rubio, J. An updated performance comparison of virtual machines and linux containers. In Proceedings of the 2015 IEEE International Symposium on Performance Analysis of Systems and Software (ISPASS), Philadelphia, PA, USA, 29–31 March 2015; pp. 171–172. [Google Scholar]












| Component | Description |
|---|---|
| Access MECS | Creates the segment information of the task requested from the service requestor. |
| mMECS | Performs task offloading based on the segment information. |
| Service Requester | Serve task offloading requests to the access MECS. |
| Component | Description |
|---|---|
| User Mobility Model | Nomadic Mobility Model |
| Number of Mobile User | 50–200 |
| Number of Mobile Preference Level | 3 |
| Probability of Selecting a Mobile Preference Level | Equal (1/3) |
| Number of access MECS per Place | 1 |
| VM Processor Speed (MIPS) per access MECS | 955 |
| Processor Speed (MIPS) per mMECS | 19 |
| WLAN Bandwidth (Mbps) | 300 |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Lee, J.; Kim, J.-W.; Lee, J. Mobile Personal Multi-Access Edge Computing Architecture Composed of Individual User Devices. Appl. Sci. 2020, 10, 4643. https://doi.org/10.3390/app10134643
Lee J, Kim J-W, Lee J. Mobile Personal Multi-Access Edge Computing Architecture Composed of Individual User Devices. Applied Sciences. 2020; 10(13):4643. https://doi.org/10.3390/app10134643
Chicago/Turabian StyleLee, Juyong, Jeong-Weon Kim, and Jihoon Lee. 2020. "Mobile Personal Multi-Access Edge Computing Architecture Composed of Individual User Devices" Applied Sciences 10, no. 13: 4643. https://doi.org/10.3390/app10134643
APA StyleLee, J., Kim, J.-W., & Lee, J. (2020). Mobile Personal Multi-Access Edge Computing Architecture Composed of Individual User Devices. Applied Sciences, 10(13), 4643. https://doi.org/10.3390/app10134643






