Practical I-Voting on Stellar Blockchain
Abstract
:1. Introduction
- Immutability: No one can change the vote after it was made.
- Verifiability: Everyone should be able to verify if his or her vote has been counted correctly.
- Scalability: The system should be able to handle large scale elections, both in terms of votes per second and voting costs.
- Authorization: Only authorized voters can vote, and no one can vote more than once.
- Privacy: Relation between voter and his vote must be kept in secret. Each voter must be sure about its vote privacy.
- Coercion resistance: It should be illegal to sell or exchange votes.
- Fairness: No partial results are available until the end of the election.
- It describes the i-voting system based on the Stellar blockchain network and its limited smart contract capabilities.
- It describes the practical aspect of blockchain i-voting where a user is completely abstracted from blockchain technology used underneath; thus, no knowledge of wallets and key pairs are needed.
- It describes the implementation of a blind signature over ed25519 to achieve voter privacy.
- It describes a method of weighted votes, based on, e.g., company shares.
2. Blockchain Technology for I-Voting
2.1. Blockchain Based I-Voting Systems
- Keys distribution;
- Casting a vote and creating a confirmation;
- Decryption of votes;
- Verification and audit of voting.
- Registration/preparation;
- Invitation;
- Voting;
- Tally/audit.
2.2. Stellar Consensus Protocol
3. System Proposition
- Immutability is a core property of blockchain technology.
- Trustless result counting is made possible thanks to public Blockchain that allows everyone to query any account data, especially all transactions sent to the ballot-box account.
- Verifiability is guaranteed by the fact that transaction is sent directly to the Stellar blockchain; in response, we receive the transaction hash, which allows us to keep track of our transaction.
- Coercion resistance is achieved by blockchain transparency. Each vote-token transaction can be easily tracked down. If the vote-token does not go directly to the ballot-box account, it is invalidated––similarly how ballot-paper must not leave the polling station.
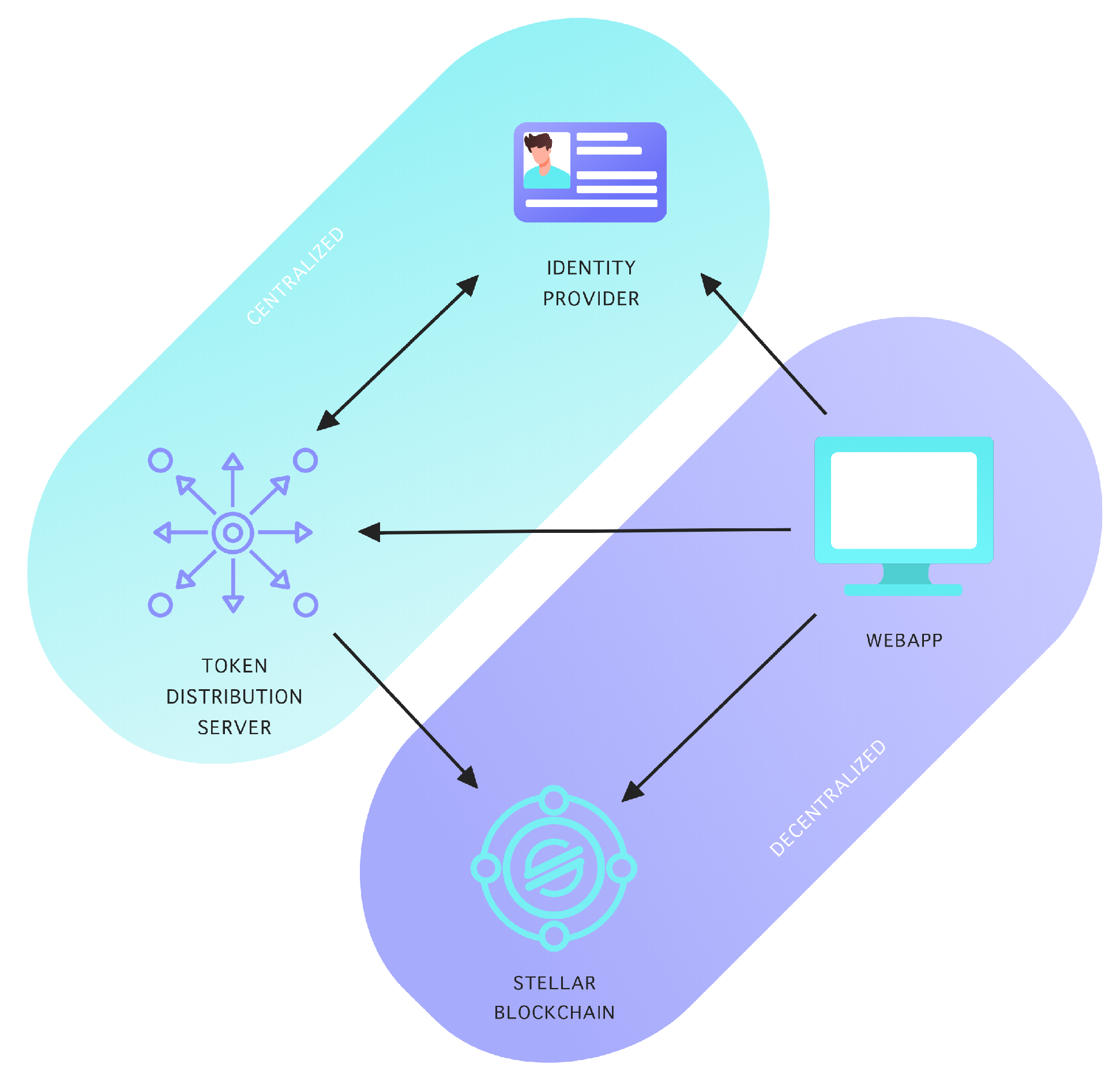
3.1. Architecture of I-Voting on Stellar Platform
3.2. Ballot Encoding
3.3. Encryption
3.4. Privacy
- Bob generate random nonce number k in the range , computeand sends r to Alice.
- Alice picks two random numbers a and b in the range , use them to compute challenge number eand sends e to Bob
- Bob perform signand sends s to Alice
- Alice computesThe pair is a valid signature on transaction M.
- Alice prepares a message.
- Place it into the envelope along with carbon paper.
- Bob signs the envelope.
- Alice takes a signed message from the envelope.
3.5. Final Voting Protocol and Elections
- User proofs its identity to Identity Provider using one of the possible methods, e.g., email/password, one-time code, email confirmation, OAuth2/OpenID.
- Identity Provider issue certificate that is later presented to the election commission (TDS) proving user identity.
- User writes a random number (authorization token) on paper and puts it into the envelope with carbon paper.
- User shows the certificate and the envelope with the authorization token (random number) to the election commission (TDS). The certificate allows the election commission to identify the user.
- The election commission (TDS) validates the certificate and checks if the user has not already issued a ballot paper. Sign the envelope, and so the authorization token through the carbon paper.
- User put off the authorization token from the envelope.
- User waits a random amount of time outside the election local.
- User put the mask on his face and goes back to the election local––this time as Anonymous. The Anonymous shows the signed authorization token to the election commission (TDS) and redeem it for ballot-paper.
- Anonymous mark the candidate on the ballot paper.
- Anonymous throws the ballot paper into the ballot box.
- Create an issuer, distributor, ballot-box accounts.
- Create separate channel account for each voter.
- Issue specified number of voting tokens.
- Lockout the issuer account from issuing new tokens.
- Prepare a set of candidates consisting of candidate names and candidate codes.
- Generate key pair for blind signature.
- Generate key pair for encrypt/decrypt transaction memo fields during/after the election period.
- Optionally split the decryption key among trusted parties (e.g., candidates), so the decryption is possible only if they reveal the secret parts altogether.
3.6. Securing Client App
- Total number of possible vote tokens (number of eligible voters);
- Issuer, distributor, and ballot-box public keys;
- Set of candidates;
- Encryption key, allowing to encrypt the ballot-box.
3.7. Weighted Votes
- The first one is the simplest. Instead of sending one vote token for each voter, we can send him multiple vote tokens. That way, the counting method does not change. The downside is that we lose the information about the number of voters in the elections since the number of vote tokens does not equal the number of eligible voters.
- Second one is to send vote tokens along with additional vote weight tokens that could represent the weight of such vote. The counting method would require an additional query of Stellar account assets (tokens), but we do not lose track of the number of vote tokens.
- Third one assumes that the voter already possesses the Stellar account with the tokens representing the vote’s weight. That way, the voter can specify the account he wants to receive the vote token, instead of generating a new temporal account.
4. Results
4.1. Scalability
4.2. Transaction Fees
4.3. Fully Decentralized Blockchain Application
5. Discussion and Future Works
6. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Schneier, B. Applied Cryptography, 2nd ed.; Protocols, Algorithms, and Source Code in C; John Wiley & Sons, Inc.: Hoboken, NJ, USA, 2007; Chapter 23.9; p. 5.3. [Google Scholar]
- Sadia, K.; Masuduzzaman, M.; Paul, R.K.; Islam, A. Blockchain Based Secured E-voting by Using the Assistance of Smart Contract. arXiv 2019, arXiv:1910.13635. [Google Scholar]
- Hjálmarsson, F.Þ.; Hreiðarsson, G.K.; Hamdaqa, M.; Hjálmtỳsson, G. Blockchain-based e-voting system. In Proceedings of the 2018 IEEE 11th International Conference on Cloud Computing (CLOUD), San Francisco, CA, USA, 2–7 July 2018; pp. 983–986. [Google Scholar]
- Ayed, A.B. A conceptual secure blockchain-based electronic voting system. Int. J. Netw. Secur. Its Appl. 2017, 9, 1–9. [Google Scholar]
- Vo-Cao-Thuy, L.; Cao-Minh, K.; Dang-Le-Bao, C.; Nguyen, T.A. Votereum: An Ethereum-Based E-Voting System. In Proceedings of the 2019 IEEE-RIVF International Conference on Computing and Communication Technologies (RIVF), Danang, Vietnam, 20–22 March 2019; pp. 1–6. [Google Scholar]
- Qadah, G.Z. Requirements, design and implementation of an e-voting system. In Proceedings of the IADIS International Conference on Applied Computing, Algarve, Portugal, 22–25 February 2005; pp. 405–409. [Google Scholar]
- Zhang, Q.; Xu, B.; Jing, H.; Zheng, Z. Ques-Chain: An Ethereum Based E-Voting System. arXiv 2019, arXiv:1905.05041. [Google Scholar]
- Adida, B. Helios: Web-based Open-Audit Voting. Usenix Secur. Symp. 2008, 17, 335–348. [Google Scholar]
- Mazieres, D. The stellar consensus protocol: A federated model for internet-level consensus. Stellar Dev. Found. 2015, 32. Available online: http://citeseerx.ist.psu.edu/viewdoc/download?doi=10.1.1.696.93&=&rep=rep1&=&type=pdf (accessed on 15 July 2020).
- Nakamoto, S. Bitcoin Whitepaper. 2008. Available online: https://bitcoin.org/bitcoin (accessed on 15 July 2020).
- Buterin, V. Ethereum white paper. Github Repos. 2013, 1, 22–23. [Google Scholar]
- Gaudry, P.; Golovnev, A. Breaking the encryption scheme of the Moscow Internet voting system. arXiv 2019, arXiv:cs.CR/1908.05127. [Google Scholar]
- Polys Online Voting System—Whitepaper. Available online: https://polys.me/assets/docs/Polys_whitepaper.pdf. (accessed on 15 July 2020).
- Moore, L.; Sawhney, N. Under the hood: The West Virginia Mobile Voting Pilot (2019). 2019. Available online: https://sos.wv.gov/FormSearch/Elections/Informational/West-Virginia-Mobile-Voting-White-Paper-NASS-Submission.pdf (accessed on 12 October 2020).
- Specter, M.A.; Koppel, J.; Weitnzer, D. The Ballot Is Busted Before the Blockchain: A Security Analysis of Voatz, the First Internet Voting Application Used in US Federal Elections. 2020. Available online: https://internetpolicy.mit.edu/wp-content/uploads/2020/02/SecurityAnalysisOfVoatz_Public.pdf (accessed on 15 July 2020).
- TIVI Online Voting System. Available online: https://tivi.io (accessed on 28 July 2020).
- Krips, K.; Kubjas, I.; Willemson, J. An Internet Voting Protocol with Distributed Verification Receipt Generation. In Proceedings of the E-Vote-ID 2018, Bregenz, Austria, 2–5 October 2018; p. 128. [Google Scholar]
- Tarasov, P.; Tewari, H. The Future of E-VOTING. IADIS Int. J. Comput. Sci. Inf. Syst. 2017, 12, 148–165. [Google Scholar]
- Khan, K.M.; Arshad, J.; Khan, M.M. Secure digital voting system based on blockchain technology. Int. J. Electron. Gov. Res. (IJEGR) 2018, 14, 53–62. [Google Scholar] [CrossRef]
- Hsiao, J.H.; Tso, R.; Chen, C.M.; Wu, M.E. Decentralized E-voting systems based on the blockchain technology. In Advances in Computer Science and Ubiquitous Computing; Springer: Berlin/Heidelberg, Germany, 2017; pp. 305–309. [Google Scholar]
- Jefferson, D. The Myth of “Secure” Blockchain Voting. Verified Voting. Available online: https://verifiedvoting.org/the-myth-of-secure-blockchain-voting/ (accessed on 12 October 2020).
- Lamport, L.; Shostak, R.; Pease, M. The Byzantine generals problem. In Concurrency: The Works of Leslie Lamport; ACM: New York, NY, USA, 2019; pp. 203–226. [Google Scholar]
- Lamport, L. The part-time parliament. In Concurrency: The Works of Leslie Lamport; ACM: New York, NY, USA, 2019; pp. 277–317. [Google Scholar]
- Lamport, L. Paxos made simple. ACM Sigact News 2001, 32, 18–25. [Google Scholar]
- Ongaro, D.; Ousterhout, J. In search of an understandable consensus algorithm. In Proceedings of the 2014 USENIX Annual Technical Conference (USENIX ATC 14), Philadelphia, PA, USA, 19–20 June 2014; pp. 305–319. [Google Scholar]
- Castro, M.; Liskov, B. Practical Byzantine fault tolerance. OSDI 1999, 99, 173–186. [Google Scholar]
- King, S.; Nadal, S. Ppcoin: Peer-to-peer crypto-currency with proof-of-stake. Self-Publ. Pap. August 2012, 19, 1. [Google Scholar]
- whitepaperSLM.pdf. Available online: https://slimcoin.info/whitepaperSLM.pdf (accessed on 28 August 2020).
- NEM_techRef.pdf. Available online: https://nemplatform.com/wp-content/uploads/2020/05/NEM_techRef.pdf (accessed on 28 August 2020).
- Kim, M.; Kwon, Y.; Kim, Y. Is Stellar as secure as you think? In Proceedings of the 2019 IEEE European Symposium on Security and Privacy Workshops (EuroS&PW), Stockholm, Sweden, 17–19 June 2019; pp. 377–385. [Google Scholar]
- Safety vs. Liveness in the Stellar Network. Available online: https://www.scs.stanford.edu/~dm/blog/safety-vs-liveness.html (accessed on 7 July 2020).
- Why Quorums Matter and How Stellar Approaches Them—Developers Blog. Available online: https://www.stellar.org/developers-blog/why-quorums-matter-and-how-stellar-approaches-them (accessed on 12 October 2020).
- Lachowski, L. Complexity of the quorum intersection property of the Federated Byzantine Agreement System. arXiv 2019, arXiv:1902.06493. [Google Scholar]
- Fischer, M.J.; Lynch, N.A.; Paterson, M.S. Impossibility of distributed consensus with one faulty process. J. ACM 1985, 32, 374–382. [Google Scholar]
- Sayeed, S.; Marco-Gisbert, H. Assessing blockchain consensus and security mechanisms against the 51% attack. Appl. Sci. 2019, 9, 1788. [Google Scholar] [CrossRef] [Green Version]
- Li, X.; Wu, X.; Pei, X.; Yao, Z. Tokenization: Open Asset Protocol on Blockchain. In Proceedings of the 2019 IEEE 2nd International Conference on Information and Computer Technologies (ICICT), Kahului, HI, USA, 14–17 March 2019; pp. 204–209. [Google Scholar]
- Personal Tokens. Available online: https://www.personaltokens.io/ (accessed on 18 June 2020).
- Analysis of the DAO Exploit. Available online: https://hackingdistributed.com/2016/06/18/analysis-of-the-dao-exploit/ (accessed on 3 June 2020).
- Balinski, M.; Laraki, R. Majority Judgment: Measuring, Ranking, and Electing; MIT Press: Cambridge, MA, USA, 2011. [Google Scholar]
- Shamir, A. How to share a secret. Commun. ACM 1979, 22, 612–613. [Google Scholar] [CrossRef]
- Van Saberhagen, N. CryptoNote v 2.0. 2013. Available online: https://decred.org/research/saberhagen2013.pdf. (accessed on 12 October 2020).
- Sasson, E.B.; Chiesa, A.; Garman, C.; Green, M.; Miers, I.; Tromer, E.; Virza, M. Zerocash: Decentralized anonymous payments from bitcoin. In Proceedings of the 2014 IEEE Symposium on Security and Privacy, San Jose, CA, USA, 18–21 May 2014; pp. 459–474. [Google Scholar]
- CoinJoin: Bitcoin Privacy for the Real World. Available online: https://bitcointalk.org/?topic=279249 (accessed on 11 July 2020).
- Brassard, G.; Crépeau, C.; Robert, J.M. All-or-nothing disclosure of secrets. In Conference on the Theory and Application of Cryptographic Techniques; Springer: Berlin/Heidelberg, Germany, 1986; pp. 234–238. [Google Scholar]
- Salomaa, A.; Santean, L. Secret selling of secrets with several buyers. Bull. EATCS 1990, 42, 178–186. [Google Scholar]
- Chaum, D. Blind Signatures for Untraceable Payments. In Advances in Cryptology; Chaum, D., Rivest, R.L., Sherman, A.T., Eds.; Springer: Boston, MA, USA, 1983; pp. 199–203. [Google Scholar]
- Channels—Stellar Documentation. Available online: https://developers.stellar.org/docs/glossary/payment-channels/ (accessed on 13 July 2020).
- Securing Web-Based Projects—Stellar Documentation. Available online: https://developers.stellar.org/docs/tutorials/securing-projects/ (accessed on 8 August 2020).
- Benet, J. Ipfs-content addressed, versioned, p2p file system. arXiv 2014, arXiv:1407.3561. [Google Scholar]
- Protocol 11 Improvements-SDF Blog. Available online: https://www.stellar.org/blog/protocol-11-improvements-stellar (accessed on 31 July 2020).
- Stellar Network Dashboard. Available online: https://dashboard.stellar.org/ (accessed on 31 July 2020).
- Lightning on Stellar: Technical Spec and Roadmap-Developers Blog. Available online: https://www.stellar.org/developers-blog/lightning-on-stellar-roadmap (accessed on 31 July 2020).
- Interstellar/Starlight: Payment Channels on Stellar. Available online: https://github.com/interstellar/starlight (accessed on 12 October 2020).
- Poon, J.; Dryja, T. The Bitcoin Lightning Network: Scalable Off-Chain Instant Payments. Version 0.5.9.2. 14 January 2016. Available online: https://nakamotoinstitute.org/research/lightning-network/ (accessed on 12 October 2020).
- Stellar Community Fund. Available online: https://www.stellar.org/community-fund (accessed on 10 July 2020).
- Stellar Community Fund: Round 4 Results|by Tyler van der Hoeven|Stellar Community|Medium. Available online: https://medium.com/stellar-community/stellar-community-fund-round-4-results-b3ed5f6acbe1 (accessed on 30 August 2020).



Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Barański, S.; Szymański, J.; Sobecki, A.; Gil, D.; Mora, H. Practical I-Voting on Stellar Blockchain. Appl. Sci. 2020, 10, 7606. https://doi.org/10.3390/app10217606
Barański S, Szymański J, Sobecki A, Gil D, Mora H. Practical I-Voting on Stellar Blockchain. Applied Sciences. 2020; 10(21):7606. https://doi.org/10.3390/app10217606
Chicago/Turabian StyleBarański, Stanisław, Julian Szymański, Andrzej Sobecki, David Gil, and Higinio Mora. 2020. "Practical I-Voting on Stellar Blockchain" Applied Sciences 10, no. 21: 7606. https://doi.org/10.3390/app10217606
APA StyleBarański, S., Szymański, J., Sobecki, A., Gil, D., & Mora, H. (2020). Practical I-Voting on Stellar Blockchain. Applied Sciences, 10(21), 7606. https://doi.org/10.3390/app10217606





