A Search Efficient Privacy-Preserving Location-Sharing Scheme in Mobile Online Social Networks
Abstract
1. Introduction
- (1)
- We create a new approach named associated grids to improve the efficiency of location-sharing systems. Based on the grid structure and a user’s query distance, we can find out the smallest set of grid cells (i.e., the associated grids) that cover the user’s query distance. By using the approach, our scheme can filter out the locations of the user’s friends that are not in the associated grids, which can reduce the burden of distance calculation and comparison on the location server.
- (2)
- We propose a new user-defined access control policy to meet users’ flexible privacy-preserving requirements. For some specific geofences or sensitive areas that users do not want to share with their friends, users can use the access control policy to prevent the leakage of privacy in social networks. Compared with paper [10], our solution can provide a more flexible privacy-preserving way, rather than simply preventing users from sharing locations with their friends.
- (3)
- Extensive simulations are implemented to explore the relationship between different solutions and parameters, as well as the performance of our scheme (i.e., SELS).
2. Related Work
3. Preliminaries
3.1. Grid Structure
3.2. Associated Grids
- (1)
- Based on the grid cell which base station B locates in, the four coordinates (i.e., upper-left, lower-left, upper-right, and lower-right) of can be found.
- (2)
- Four circles can be formed by taking the user’s query distance l as the radius and four coordinates (i.e., upper-left, lower-left, upper-right, and lower-right) of as the center.
- (3)
- The grid cellsthat cover the above four circles can be figured out. Then these grid cells are named the associated grids of the user. Figure 1b shows the associated grids (i.e., green grid cells) when the user’s query distance is 2 km.
3.3. RSA Signature Scheme
- (1)
- is a key pair generation algorithm. Firstly, select two large prime numbers p and q. Then, compute and choose e so as to and , where and is the greatest common divisor. Finally, compute and then is defined as the public key and is defined as the private key.
- (2)
- is a signing algorithm. Suppose M is the message to be signed, then the ciphertext is the signature that will be sent and used for verification.
- (3)
- is a verification algorithm. Given a signature C, if the decrypted is the same as the original message M, then the C can be accepted as a valid signature.
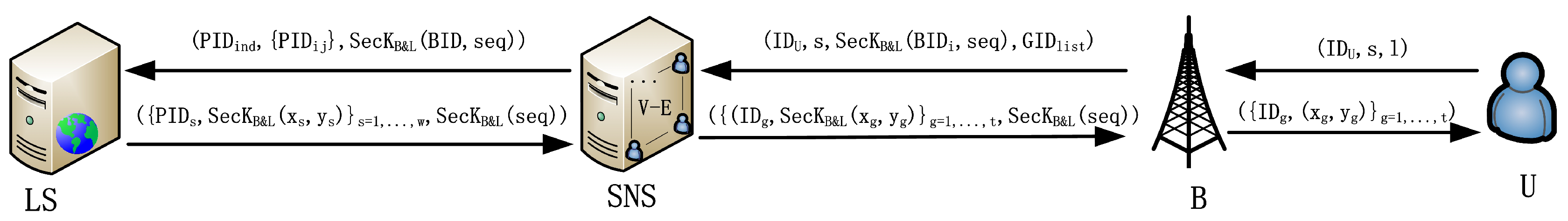
4. System Architecture and Security Model
4.1. Architecture
- (1)
- The entity of users, with mobile terminals, can send a request for location-sharing with nearby friends or strangers. Within a specified query distance, an issuing user can know nearby friends or strangers’ locations if some pre-set access control policies are satisfied. Users can communicate with base stations and online social network server directly via their mobile devices. One user only has a unique identity in the online social network server.
- (2)
- Base station (B) is an entity that has a certain computation and acts as a connecting thread. Users can communicate with servers through base stations.
- (3)
- The social network server () is an entity that stores users’ social network topology, in the form of social network graph . V is a set of vertices which represent users’ identities and E is a set of edges that indicate the friends’ relationships. If two vertices are connected by an edge, the two corresponding users have a social relationship (i.e., they are friends). In addition, the social network server is also responsible for user registration and provides social network services based on the requirements of users’ queries.
- (4)
- The location server () is an entity that stores the location information of users and dummies. In addition, it also takes charge of providing location-related services such as computing and comparing the Euclidean distance of two locations based on their coordinates.
4.2. Security Model
4.3. Security Goals
5. Search Efficient Privacy-Preserving Location-Sharing (SELS) Scheme
- (1)
- B generates a new mapping relationship ) between grid cells’ identifiers and their fake-IDs. Then, the new fake-ID set (i.e., ) is encrypted with the secret key and sent to .
- (2)
- uses the random number generator [25] to generate a new . Then, the new and identifier of each user are encrypted with the secret key and sent to B.
- (3)
- To prevent the users who are no longer friends from getting messages, updates the session key for each user based on social network graphs.
- (1)
- When user U updates his/her location, U needs to submit a message in the form of to B. is the U’s current location and is the encrypted location information with . is the grid cell access control policy, which means the current grid cell is accessible/inaccessible (i.e., U allows or forbids the current grid cell where U locates can be searched by the location-sharing requests of his/her friends). When getting the message, B will record the access control policy in the form of in the database. Note that A is the default state and F means only the current grid cell can not be searched by the location-sharing request of his/her friends (i.e., the current grid cell is a sensitive area that U does not want his/her friends to know). However, if U is no longer in this grid cell, U can be searched by the location-sharing requests of his/her friends.
- (2)
- If A is included in U’s submitted message, B will send a message in the form of to , where is the fake-ID of the grid cell where B locates. For example, if U offers update information through base station which locates in , then will send to . After receiving the update information, will reply a message to B which then forwards to U. If U’s submitted message includes F, B will do nothing.
- (3)
- B sends a message in the form of to , where is the pseudo-ID set of U and is a random string to imitate the encrypted location. Herein, suppose that in the last mapping relationship update, then represents the real information of U, and indicates the dummies of U. Then stores the information in its database and sends a response in the form of to B which then forwards to U.
- (1)
- U needs to submit a query in the form of to B, where f means this query is a request for querying friends’ locations and l indicates the specified query distance such as 2 km.
- (2)
- When receiving U’s query, B first figures out the associated grids of U (see Section 3.2) based on U’s query distance l, and form a list which contains the fake-ID set of the associated grids. The purpose of finding out the list is to help filter out U’s friends that are not in the associated grids. Then, B encrypts its identifier and with to form , where is a sequence number to resist the replay attack. Finally, B sends the message to .
- (3)
- According to U’s social network graph and users’ location update information, finds out the U’s friends who are in (i.e., seeking out U’s friends whose locations are in ). Suppose that there are m users meeting the above condition, where and n is the total number of U’s friends. Then will collect these users’ to form a set , where and . The purpose of forming is to perturb the identity information of U’s friends. Finally, sends a query in the form of to , where represents the real pseudo-ID of U.
- (4)
- After getting of the query from , runs the distance comparison function , where is a function to compute Euclidean distance and is the coordinates of . represents the corresponding coordinates of pseudo-IDs in , where . Suppose that there are w s satisfying the distance comparison function, then collects these w s to form a set and finds the corresponding , where and . Finally, replies a message in the form of to .
- (5)
- Upon receiving , recovers the real identifiers from to form a result set (i.e., the friends’ real identifiers of U) based on the s of U’ friends. The purpose of forming is to filter out dummies of U’s friends. Suppose that there are t users’ s recovered from the result set, then sends a message in the form of to B. Note that if , will send ⌀ to B.
- (6)
- Upon the reception of the response from , B first checks the sequence number and then decrypts to obtain . Finally, B replies the result in form of to user U.
- (7)
- After obtaining , U uses session key to decrypt the corresponding coordinates of his/her friends.
- (1)
- U needs to submit a query in the form of to B, where s means this query is a request for querying strangers’ locations and l indicates the specified query distance such as 2 km.
- (2)
- After receiving U’s query, B figures out the associated grids based on U’s query distance l, and forms a list . Then, B sends the message to .
- (3)
- Based on and U’s social network graph, first eliminates the users who have friendship with U. Then, will randomly collect a certain number of users’ to form a set , where , , and is a number of randomly selected users. Finally, sends a query in the form of to , where represents the real pseudo-ID of U.
- (4)
- When receiving of the query from , runs the distance comparison function . indicates the corresponding coordinates of pseudo-IDs in , where . Suppose that there are w s satisfying the distance comparison function, then collects these w s to form a set and finds the corresponding , where and . Finally, replies a message in the form of to .
- (5)
- Upon receiving , recovers the real identifiers from to form a result set (i.e., the users’ real identifiers) based on users’ s. Suppose that there are t users’ s recovered from the result set, then sends to B.
- (6)
- After getting the response from , B first checks the sequence number and then decrypts to obtain . Finally, B replies the result in the form of to user U.
6. Discussion
6.1. Efficiency Analysis
6.2. Security Analysis
7. Simulation and Results
7.1. Simulation Setup
- (1)
- Under the condition of querying friends’ locations, ten locations are randomly selected as the initial locations of an issuing user. The total number of users n is set to be 1000 and the users are randomly distributed throughout the grid structure. The number of pseudo-IDs for each user k and the query distance l of the issuing user are set as 10 and 5 km, respectively. The number range of friends for each user f changes from 50 to 90. We execute 100 times and then calculate the average number of effective users and the average time cost under different f. The above settings are named scenario-1, which is used to explore the effect caused by f.
- (2)
- Under the condition of querying friends’ locations, ten locations are randomly selected as the initial locations of an issuing user. The total number of users n is set to be 1000 and the users are randomly distributed throughout the grid structure. The number of pseudo-IDs for each user k and the number of friends for each user f are set as 10 and 50, respectively. The query distance l of the issuing user changes from 1 km to 5 km. We execute 100 times and then calculate the average number of effective users and the average time cost under different l. The above settings are named scenario-2, which is used to research the effect caused by l.
- (3)
- Under the condition of querying friends’ locations, ten locations are randomly selected as the initial locations of an issuing user. The total number of users n is set to be 1000 and the users are randomly distributed throughout the grid structure. The query distance l of the issuing user and the number of friends for each user f are set as 5 km and 50, respectively. The number of pseudo-IDs for each user k changes from 10 to 30. We execute 100 times and then calculate the average number of effective users and the average time cost under different k. The above settings are named scenario-3, which is used to study the effect caused by k.
- (4)
- Under the condition of querying friends’ locations, ten locations are randomly selected as the initial locations of an issuing user. The total number of users n changes from 1000 to 2500 and the users are randomly distributed throughout the grid structure. The query distance of the issuing user l, the number of pseudo-IDs for each user k, and the number of friends for each user f are set as 5 km, 10, and 50, respectively. We execute 100 times and then calculate the average number of effective users and the average time cost under different k. The above settings are named scenario-4, which is used to research the effect caused by n.
7.2. Simulation Results
8. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Vijayakumar, P.; Obaidat, M.S.; Azees, M.; Islam, S.K.H.; Kumar, N. Efficient and Secure Anonymous Authentication With Location Privacy for IoT-Based WBANs. IEEE Trans. Ind. Inform. 2020, 16, 2603–2611. [Google Scholar] [CrossRef]
- Sun, G.; Chang, V.; Ramachandran, M.; Sun, Z.; Li, G.; Yu, H.; Liao, D. Efficient location privacy algorithm for Internet of Things (IoT) services and applications. J. Netw. Comput. Appl. 2017, 89, 3–13. [Google Scholar] [CrossRef]
- Yang, G.; Luo, S.; Zhu, H.; Xin, Y.; Li, M.; Wang, Y. An Efficient Approach for LBS Privacy Preservation in Mobile Social Networks. Appl. Sci. 2019, 9, 316. [Google Scholar] [CrossRef]
- Yang, G.; Luo, S.; Zhu, H.; Xin, Y.; Xiao, K.; Chen, Y.; Li, M.; Wang, Y. A Mechanism to Improve Effectiveness and Privacy Preservation for Review Publication in LBS. IEEE Access 2019, 7, 156659–156674. [Google Scholar] [CrossRef]
- Xiaoying, S.; Zhenhai, Y.; Qiming, F.; Quan, Z. A Visual Analysis Approach for Inferring Personal Job and Housing Locations Based on Public Bicycle Data. Int. J. Geo Inf. 2017, 6, 205. [Google Scholar]
- Wei, W.; Xu, F.; Li, Q. MobiShare: Flexible privacy-preserving location sharing in mobile online social networks. In Proceedings of the 2012 Proceedings IEEE Infocom, Orlando, FL, USA, 25–30 March 2012; pp. 2616–2620. [Google Scholar]
- Li, J.; Li, J.; Chen, X.; Liu, Z.; Jia, C. MobiShare+: Security Improved System for Location Sharing in Mobile Online Social Networks. J. Internet Serv. Inf. Secur. 2014, 4, 25–36. [Google Scholar]
- Liu, Z.; Luo, D.; Li, J.; Chen, X.; Chunfu, J. N-Mobishare: New privacy-preserving location-sharing system for mobile online social networks. Int. J. Comput. Math. 2016, 93, 384–400. [Google Scholar] [CrossRef]
- Shen, N.; Yuan, K.; Yang, J.; Jia, C. B-Mobishare: Privacy-Preserving Location Sharing Mechanism in Mobile Online Social Networks. Comput. Stand. Interfaces 2016, 44, 102–109. [Google Scholar] [CrossRef]
- Sun, G.; Xie, Y.; Liao, D.; Hongfang, Y.; Chang, V. User-Defined Privacy Location-Sharing System in Mobile Online Social Networks. J. Netw. Comput. Appl. 2017, 86, 34–45. [Google Scholar] [CrossRef]
- Li, J.; Yan, H.; Liu, Z.; Chen, X.; Huang, X.; Wong, D. Location-Sharing Systems With Enhanced Privacy in Mobile Online Social Networks. IEEE Syst. J. 2017, 11, 439–448. [Google Scholar] [CrossRef]
- Li, J.; Yan, H.; Liu, Z.; Chen, X.; Huang, X.; Wong, D. CenLocShare: A centralized privacy-preserving location-sharing system for mobile online social networks. Future Gener. Comput. Syst 2018, 86, 863–972. [Google Scholar]
- Liu, J.; Fu, L.; Wang, X.; Tang, F.; Chen, G. Joint Recommendations in Multilayer Mobile Social Networks. IEEE Trans. Mob. Comput. 2020, 19, 2358–2373. [Google Scholar] [CrossRef]
- Lai, I.K.W.; Liu, Y. The Effects of Content Likeability, Content Credibility, and Social Media Engagement on Users’ Acceptance of Product Placement in Mobile Social Networks. J. Theor. Appl. Electron. Commer. Res. 2020, 15, 1–19. [Google Scholar] [CrossRef]
- Erdemir, E.; Dragotti, P.L.; Gunduz, D. Privacy-Aware Location Sharing with Deep Reinforcement Learning. IEEE Trans. Inf. Forensics Secur. 2019, 16, 1–6. [Google Scholar]
- Sweeney, L. k-anonymity: A model for protecting privacy. Int. J. Uncertain. Fuzziness Knowl. Based Syst. 2002, 10, 557–570. [Google Scholar] [CrossRef]
- Wu, Z.; Li, G.; Shen, S.; Lian, X.; Chen, E.; Xu, G. Constructing dummy query sequences to protect location privacy and query privacy in location-based services. World Wide Web Internet Web Inf. Syst. 2020. [Google Scholar] [CrossRef]
- Cui, N.; Yang, X.; Wang, B. A Novel Spatial Cloaking Scheme Using Hierarchical Hilbert Curve for Location-Based Services. In Proceedings of the 17th International Conference on Web-Age Information Management (WAIM), Nanchang, China, 3–5 June 2016; pp. 15–27. [Google Scholar]
- Son, J.; Kim, D.; Tashakkori, R.; Tokutaz, A.; Ohx, H. A New Mobile Online Social Network Based Location Sharing with Enhanced Privacy Protection. In Proceedings of the 25th IEEE International Conference on Computer Communications and Networks (ICCCN), Waikoloa, HI, USA, 1–4 August 2016; pp. 59–68. [Google Scholar]
- Olteanu, A.M.; Humbert, M.; Huguenin, K.; Hubaux, J.P. The (Co-)Location Sharing Game. Proc. Priv. Enhancing Technol. 2019, 2019, 5–25. [Google Scholar] [CrossRef][Green Version]
- Lin, T.L.; Chang, H.Y.; Li, S.L. A Location Privacy Attack Based on the Location Sharing Mechanism with Erroneous Distance in Geosocial Networks. Sensors 2020, 20, 918. [Google Scholar] [CrossRef]
- Xu, C.; Xie, X.; Zhu, L.; Sharif, K.; Guizani, M. PPLS: A privacy-preserving location-sharing scheme in mobile online social networks. China Inf. Sci. 2020, 63, 56–68. [Google Scholar] [CrossRef]
- Zhang, S.; Choo, K.K.R.; Liu, Q.; Wang, G. Enhancing privacy through uniform grid and caching in location-based services. Future Gener. Comput. Syst. 2018, 86, 881–892. [Google Scholar] [CrossRef]
- Lu, R.; Lin, X.; Shi, Z.; Shao, J. PLAM: A Privacy-Preserving Framework for Local-Area Mobile Social Networks. In Proceedings of the 33rd IEEE Annual Conference on Computer Communications (IEEE INFOCOM), Toronto, QN, Canada, 27 April–2 May 2014; pp. 763–771. [Google Scholar]
- Sunar, B.; Martin, W.J.; Stinson, D.R. A provably secure true random number generator with built-in tolerance to active attacks. IEEE Trans. Comput. 2007, 56, 109–119. [Google Scholar] [CrossRef]










| Notation | Description |
|---|---|
| A user’s identifier. | |
| A user’s pseudo-identifier (pseudo-ID). | |
| A grid cell’s identifier. | |
| A grid cell’s fake-identifier (fake-ID). | |
| A base station’s identifier. | |
| A location coordinate. | |
| Threshold distance for friends. | |
| Threshold distance for strangers. | |
| The distance comparison function to compute Euclidean distance from i to j. | |
| l | A user’s query distance. |
| A time-stamp. | |
| Location server’s secret key, shared with base stations. | |
| Social network server’s secret key, shared with base stations. | |
| A user’s session key, shared with all his friends. | |
| A sequence number, generated by base stations. |
| Scheme | Time Complexity |
|---|---|
| MobiShare [6] | |
| UDPLS [10] | |
| MLS [11] | |
| CenLocShare [12] | |
| SELS (Our scheme) |
| Item | Attribute | Specification |
|---|---|---|
| n | Variate | 1000–2500 |
| k | Variate | 10–30 |
| Constant | 20 × 20, 1 km × 1 km | |
| Constant | 5 km | |
| l | Variate | 1–5 km |
| f | Variate | 50–90 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Yang, G.; Luo, S.; Xin, Y.; Zhu, H.; Wang, J.; Li, M.; Wang, Y. A Search Efficient Privacy-Preserving Location-Sharing Scheme in Mobile Online Social Networks. Appl. Sci. 2020, 10, 8402. https://doi.org/10.3390/app10238402
Yang G, Luo S, Xin Y, Zhu H, Wang J, Li M, Wang Y. A Search Efficient Privacy-Preserving Location-Sharing Scheme in Mobile Online Social Networks. Applied Sciences. 2020; 10(23):8402. https://doi.org/10.3390/app10238402
Chicago/Turabian StyleYang, Guangcan, Shoushan Luo, Yang Xin, Hongliang Zhu, Jingkai Wang, Mingzhen Li, and Yunfeng Wang. 2020. "A Search Efficient Privacy-Preserving Location-Sharing Scheme in Mobile Online Social Networks" Applied Sciences 10, no. 23: 8402. https://doi.org/10.3390/app10238402
APA StyleYang, G., Luo, S., Xin, Y., Zhu, H., Wang, J., Li, M., & Wang, Y. (2020). A Search Efficient Privacy-Preserving Location-Sharing Scheme in Mobile Online Social Networks. Applied Sciences, 10(23), 8402. https://doi.org/10.3390/app10238402







