SENTINEL: A Secure and Efficient Authentication Framework for Unmanned Aerial Vehicles
Abstract
:1. Introduction
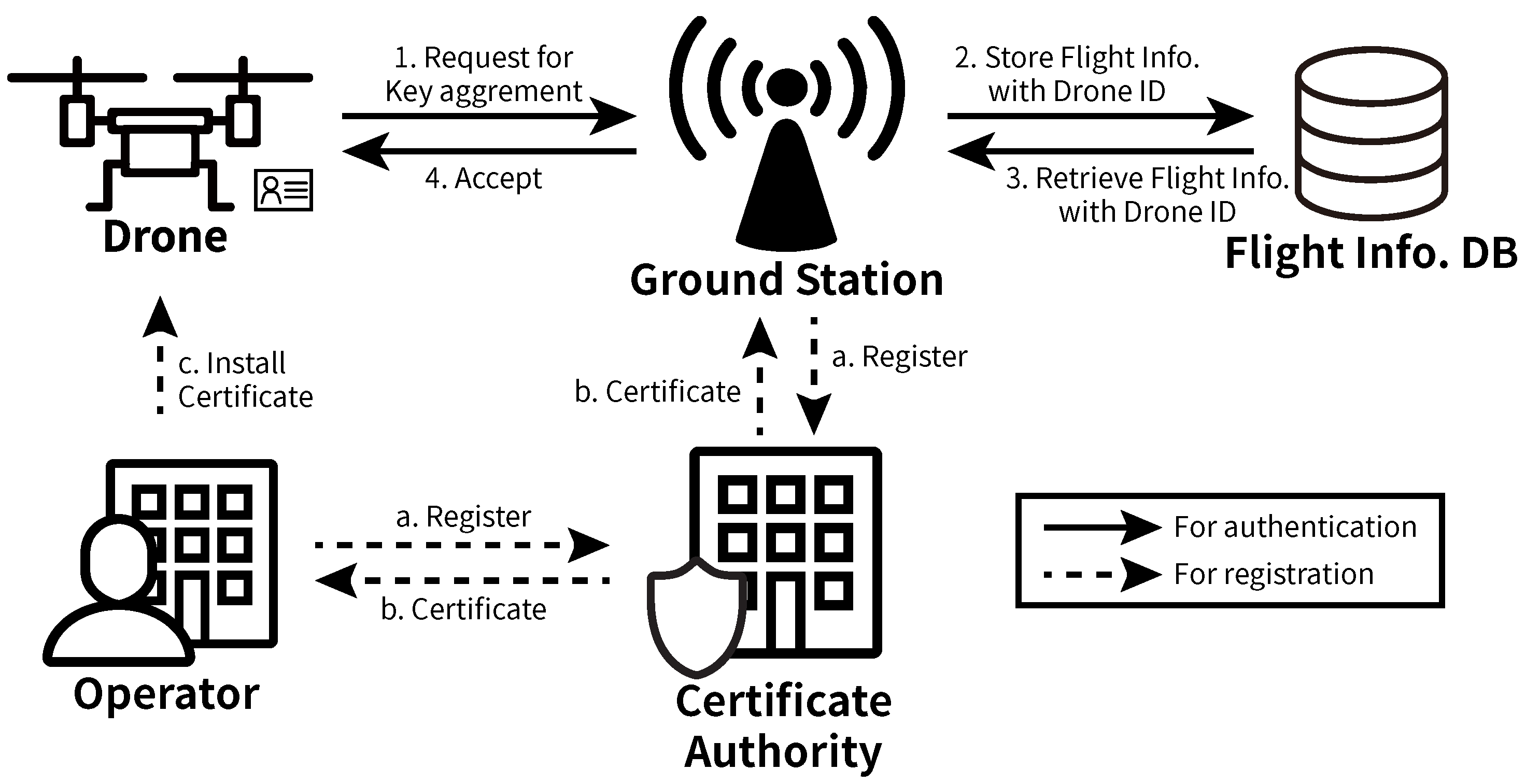
- We propose SENTINEL (Secure and Efficient autheNTIcation for uNmanned aErial vehicLes) to provide mutual authentication between drones and ground stations. SENTINEL initially generates a flight session key for a drone having a flight plan and registers the flight session key and its flight plan into a centralized database that can be accessed by all ground stations. The registered flight session key is used to authenticate the drone by ground stations as the MAC key while it is flying (see Section 4 and Section 5).
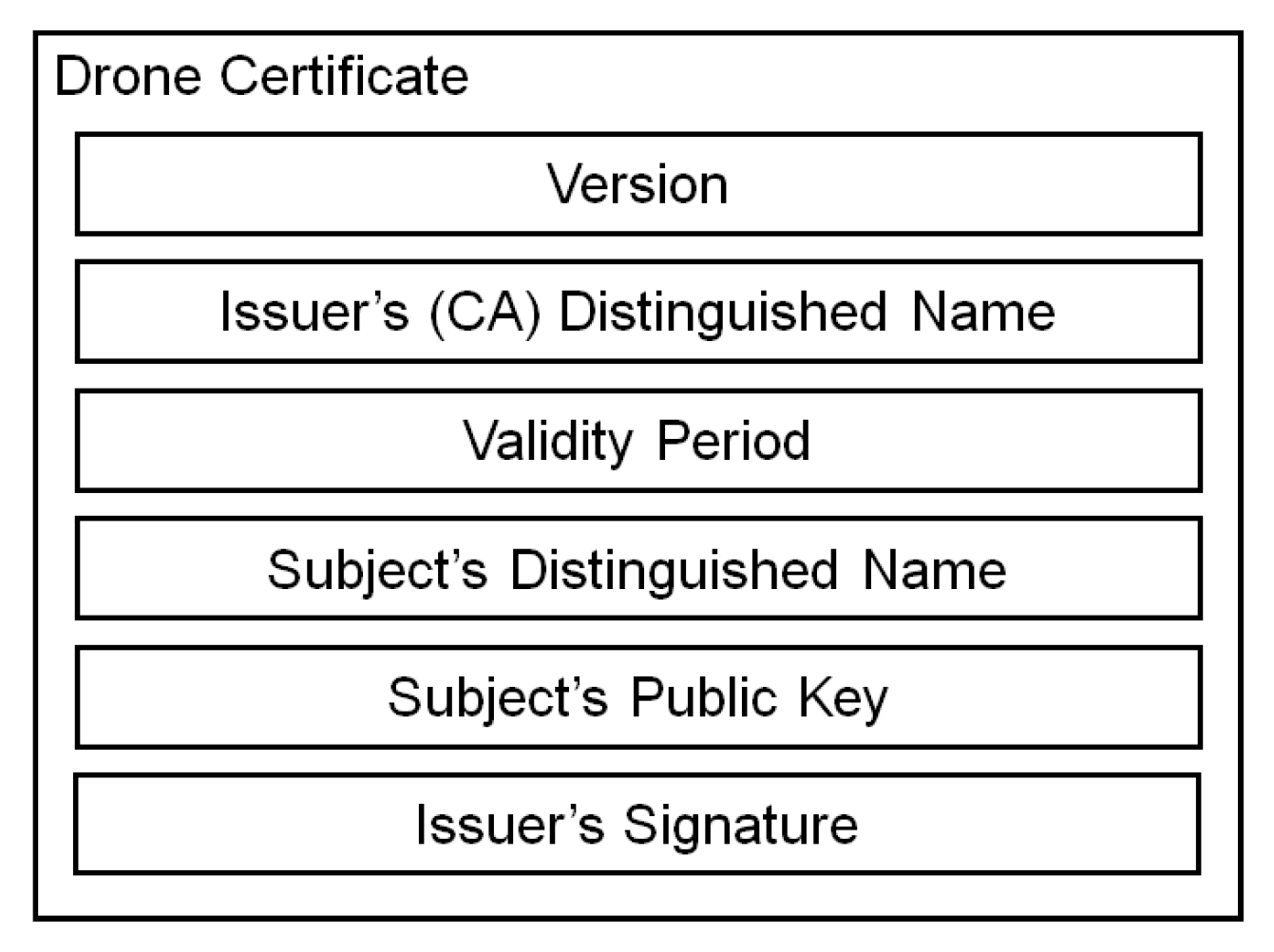
- We designed a lightweight certificate format that is suitable for IoD environments. Compared to the conventional X.509 v3 certificate, the proposed certificate is designed to contain only minimal information required to build public key infrastructure in IoD environments. To further reduce the size of certificates, we adopt a binary format in the proposed certificate, instead of a human-readable text format adopted in X.509 v3 certificates. Our results show that the size of the proposed certificate was about 3.7 times smaller than the size of a typical X.509 v3 certificate (see Section 6).
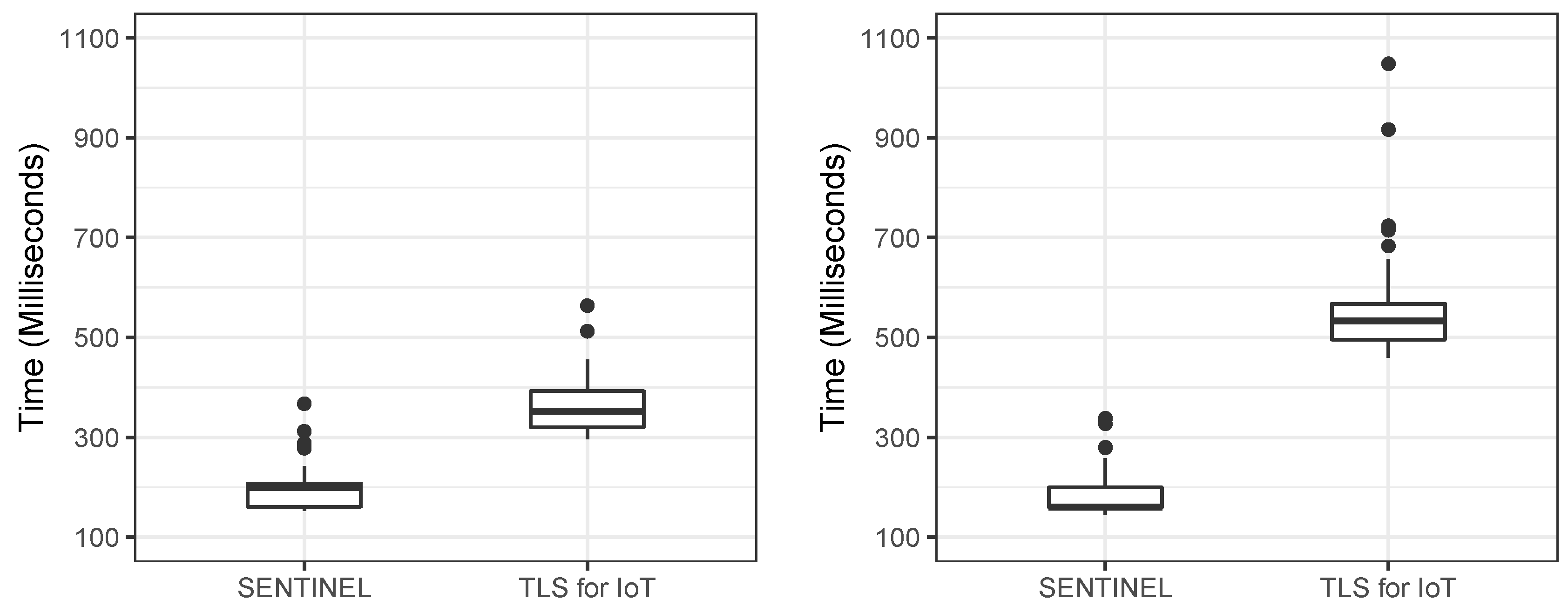
- We implement a prototype of SENTINEL to show its feasibility and efficiency. Our results demonstrate that the execution time of the authentication protocol in SENTINEL is 3.1 times faster than the “TLS for IoT” protocol on average (see Section 7). We also formally verify the security of SENTINEL using ProVeif, which is a formal verification tool (see Section 8).
2. Related Work
2.1. Security and Privacy in IoD
2.2. Authentication among Drones, Ground Stations, and Other Parties
2.3. Authentication between Users and Drones
3. Background
3.1. Terminology and Notations
- Drone is an entity (known as an unmanned aerial vehicle, UAV) designed to be flown either through remote or autonomous controls using embedded software and sensors. In this paper, a drone is recognized as authorized one when a ground station successfully verifies the authenticity of the drone.
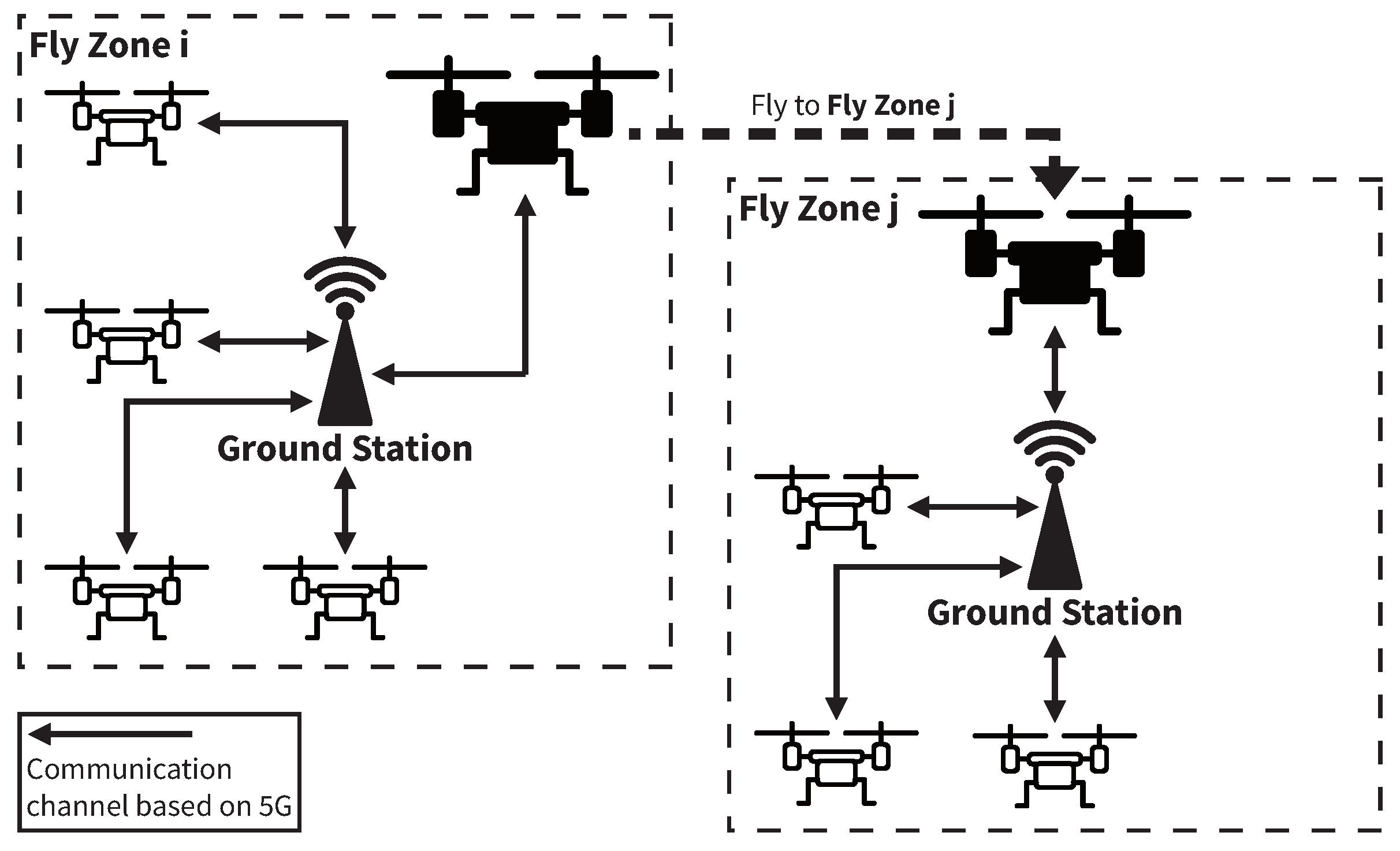
- Ground station is an entity that allows drones to communicate with other drones using a 5G network and has the role of tracking the locations of (authorized) drones during their flight.
- Certificate authority (CA) is an entity which performs two roles. The first role is to issue a certificate to drones and ground stations. Another role is to confirm whether the certificate is revoked by comparing the certificate with the certificate revocation list.
- Operator is a person or a company that wants to control a drone. It requests a certificate for her drone to CA. After having the certificate, it has to install the certificate on the drone. We assume that each drone has a unique certificate issued by a legitimate CA.
3.2. Threat Model
- The attacker can eavesdrop on a public channel. That is, the attacker can steal or drop the message between drones and ground stations.
- The attacker can also send any messages to drones and ground stations.
4. Overview of SENTINEL
5. Security Protocols in SENTINEL
5.1. Mutual Authentication and Key Agreement Protocol
- 1.
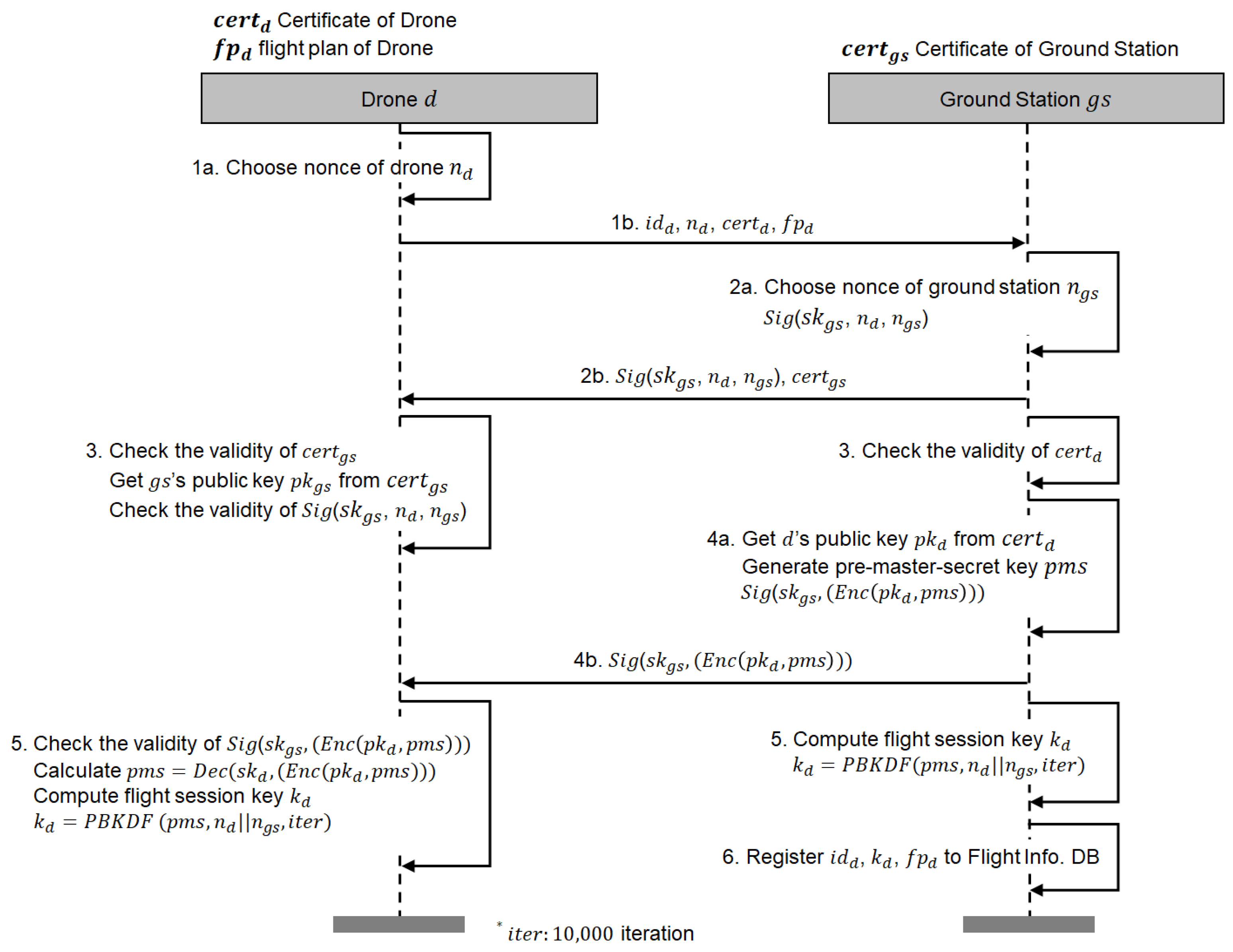
- When a drone d tries to start a flight, d first chooses a random nonce using a cryptographically secure pseudorandom function, and sends the message including drone’s identity , , drone’s certificate , and drone’s flight plan to a predesignated ground station .
- 2.
- On receiving the message from d, also chooses its random nonce . Then, signs “ and ” with the ground station’s private key . We use to represent the signed message of “ and ” with . sends the message including the signed value and the ground station’s certificate .
- 3.
- After sending the messages, checks the validity of received from d. At the same time, d also checks the validity of . Then, d extracts the ground station’s public key from to check the validity of . As a result, d has a valid which will be used for generating the flight session key.
- 4.
- extracts the public key of from . After extracting , generates a pre-master-secret key using a cryptographically secure pseudorandom function and then encrypts with , which resulted in . Then, signs with and sends to d.
- 5.
- As for the last step, concatenates and denoted as . Here, random nonces are used to prevent replay attacks. Then, computes a flight session key using a key derivation functions (e.g., PBKDF2 [26] with 10,000 iteration) with and together. At the side of the drone, d first checks the validity of with . If the signature is valid, then d decrypts with its private key . Finally, d also computes the flight session key using a key derivation function with and , which is the exactly same as the key generation by .
- 6.
- After completing the generation of the flight session key , registers the drone d’s identity , flight session key and flight plan to the flight information database.
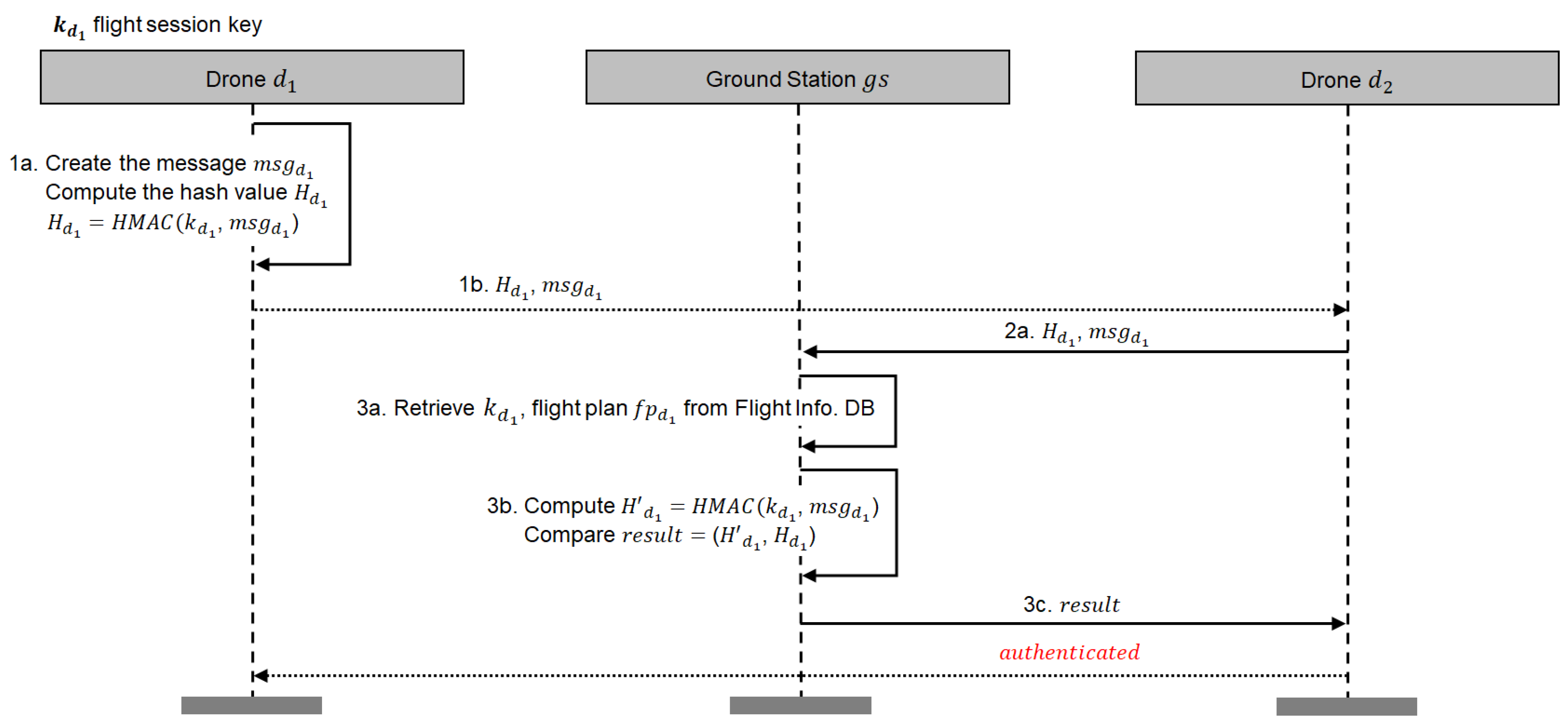
5.2. Drone Authentication Protocol
- 1.
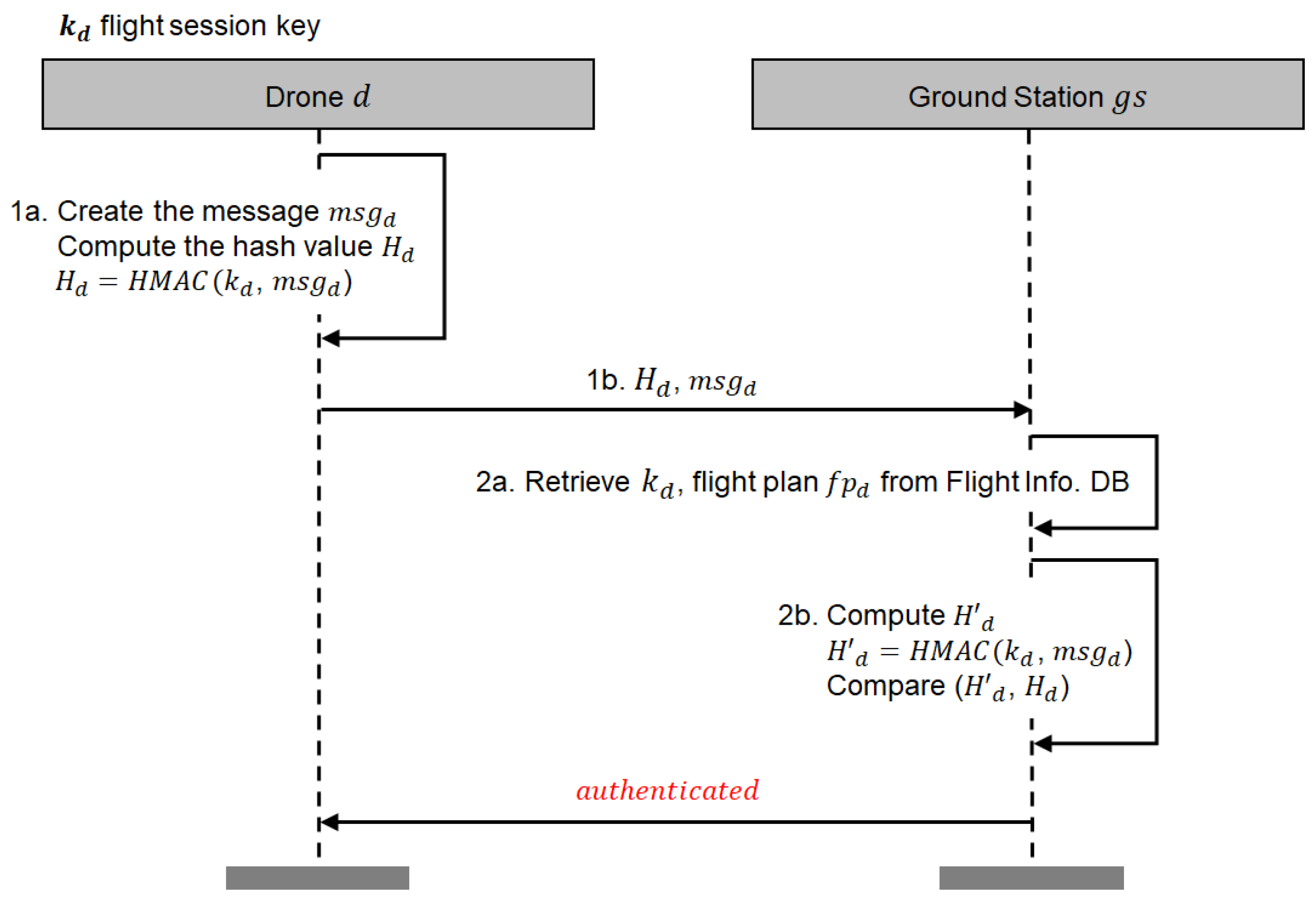
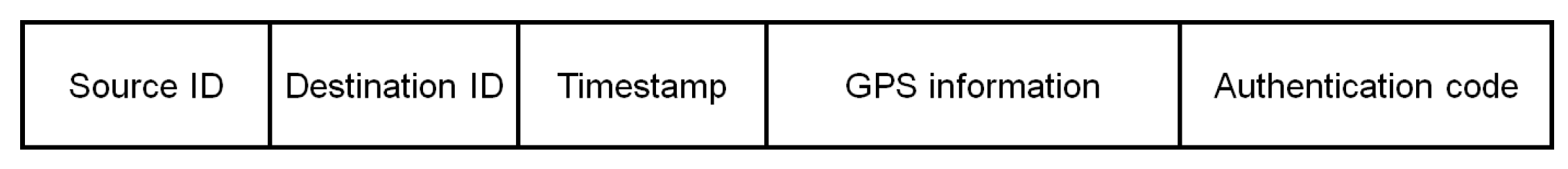
- The drone d creates a message that contains the information about the drone d’s (GPS) location and timestamp. The message also contains the drone d’s identifier as the message sender’s identifier (‘Source ID’) and the ground station’s identifier as the message recipient’s identifier (‘Destination ID’) in order to prevent replay attacks and man-in-the-middle attacks. Then, d computes the authentication code using a HMAC (hash-based message authentication code function) with and and sends with the original message to a ground station .
- 2.
- On receiving the message from the drone d, the ground station fetches the drone d’s record with from the flight information database and extracts the flight session key from the record. For verifying the validity of the received , computes using received message and the retrieved flight session key . After computing , compares with the received authentication code . If , believes that is not compromised and the drone d holds the flight session key . After verifying the authentication code, makes a decision on whether or not to allow the drone d’s flight entering its fly zone by checking whether this fly zone is contained in d’s flight plan.
- Source ID. This field represents the message sender’s identity (i.e., the drone d’s identity). The sender’s identity can be used with the recipient’s identifier to prevent man-in-the-middle attacks. In our prototype implementation, the size of this field is 4 bytes.
- Destination ID. This field represents the message recipient’s identity. In the proposed protocol, the message recipient can be either a ground station or another drone. In our prototype implementation, the size of this field is 4 bytes.
- Timestamp. This field represents the time when the message was created. The timestamp can be used to ensure the freshness of messages. In our prototype implementation, the size of this field is 8 bytes.
- GPS information. This field represents the drone’s current location information based on the GPS signal. This information can be used to trace the drone’s location. In our prototype implementation, the size of this field is 24 bytes.
- Authentication code. This field represents the authentication code computed as . The authentication code is used to ensure message authenticity and integrity.
- 1.
- The drone creates a message that contains the information about the drone ’s (GPS) location and timestamp. The message also contains the drone ’s identifier as the message sender’s identifier (‘Source ID’) and the other drone ’s identifier as the message recipient’s identifier (‘Destination ID’). Then, computes the authentication code using a HMAC (hash-based message authentication code function) with and and sends with the original message to the drone .
- 2.
- On receiving the message from the drone , the drone relays the message to a ground station .
- 3.
- On receiving the message from the drone , the ground station fetches the drone ’s record with from the flight information database and extracts the flight session key from the record. For verifying the validity of the received , computes using received message and the retrieved flight session key . After computing , compares with the received authentication code . If , believes that is not compromised and the drone holds the flight session key . After verifying the authentication code, makes a decision on whether or not to allow the drone ’s flight entering its fly zone by checking whether this fly zone is contained in ’s flight plan. The ground station sends this result to the drone .
6. Digital Certificate for SENTINEL
- Version. This field represents a version of the certificate, which may be changed when the certificate is updated. We set the size of this field to 1 byte.
- Issuer’s (CA) Distinguished Name. This field specifies the issuer’s distinguished name. The size of this field is 2 bytes.
- Validity Period. This field specifies the period for which the certificate is valid. This certificate can no longer be used after being expired. We set the size of this field to 16 bytes.
- Subject’s Distinguished Name. This field specifies the distinguished name of the subject, such as a drone’s identifier and a ground station’s identifier. The size of this field is 4 bytes.
- Subject’s Public key. This field contains the subject’s public key, and the length of the public key can be approximately 91 bytes. Unlike conventional X.509 v3 certificates, this field does not specify the type of a public key algorithm compatible with the public key because we assume a fixed algorithm. For drones, we recommend using ECDSA [28] to reduce their computational overhead.
- Issuer’s Signature. This field contains the issuer’s signature on this certificate, which will be used by recipients to verify the validity of this certificate. The size of this field is approximately 70 bytes.
7. Experiments
7.1. Implementation
7.2. Evaluation—Lightweight Digital Certificate
7.3. Evaluation—Mutual Authentication and Key Agreement Protocol
7.4. Evaluation—Drone Authentication Protocol
8. Security Analysis
8.1. Formal Security Analysis Using ProVerif
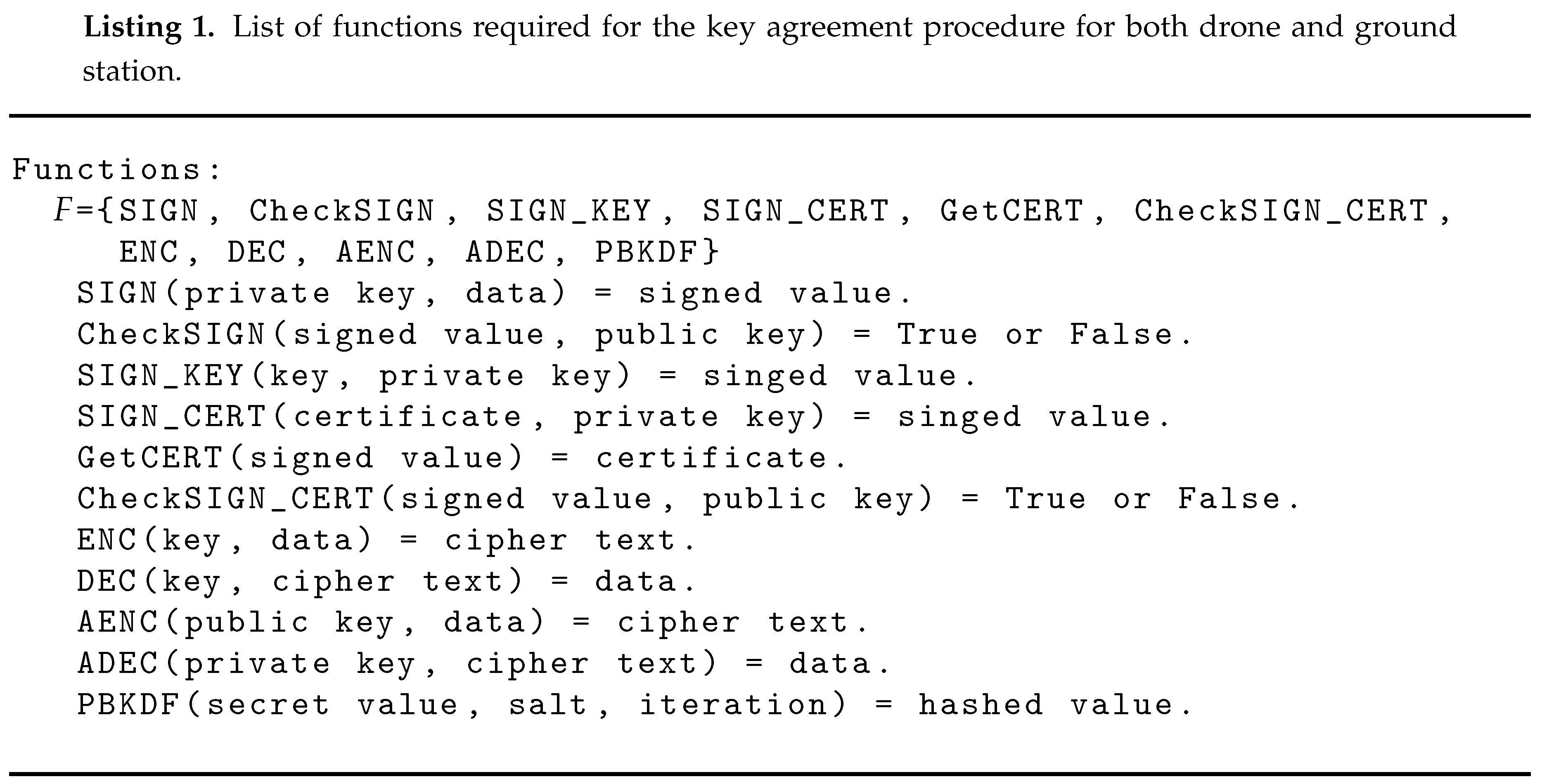
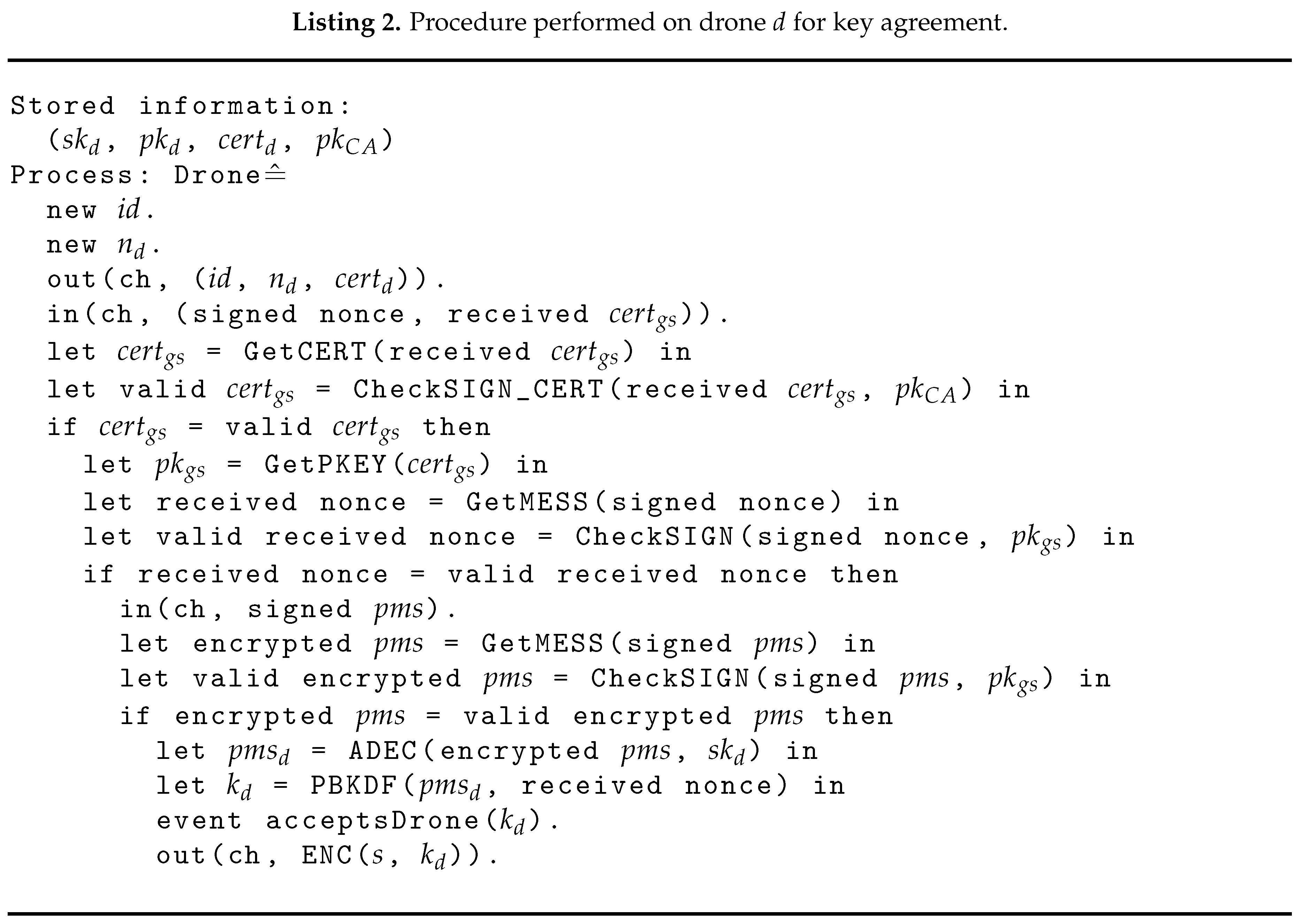
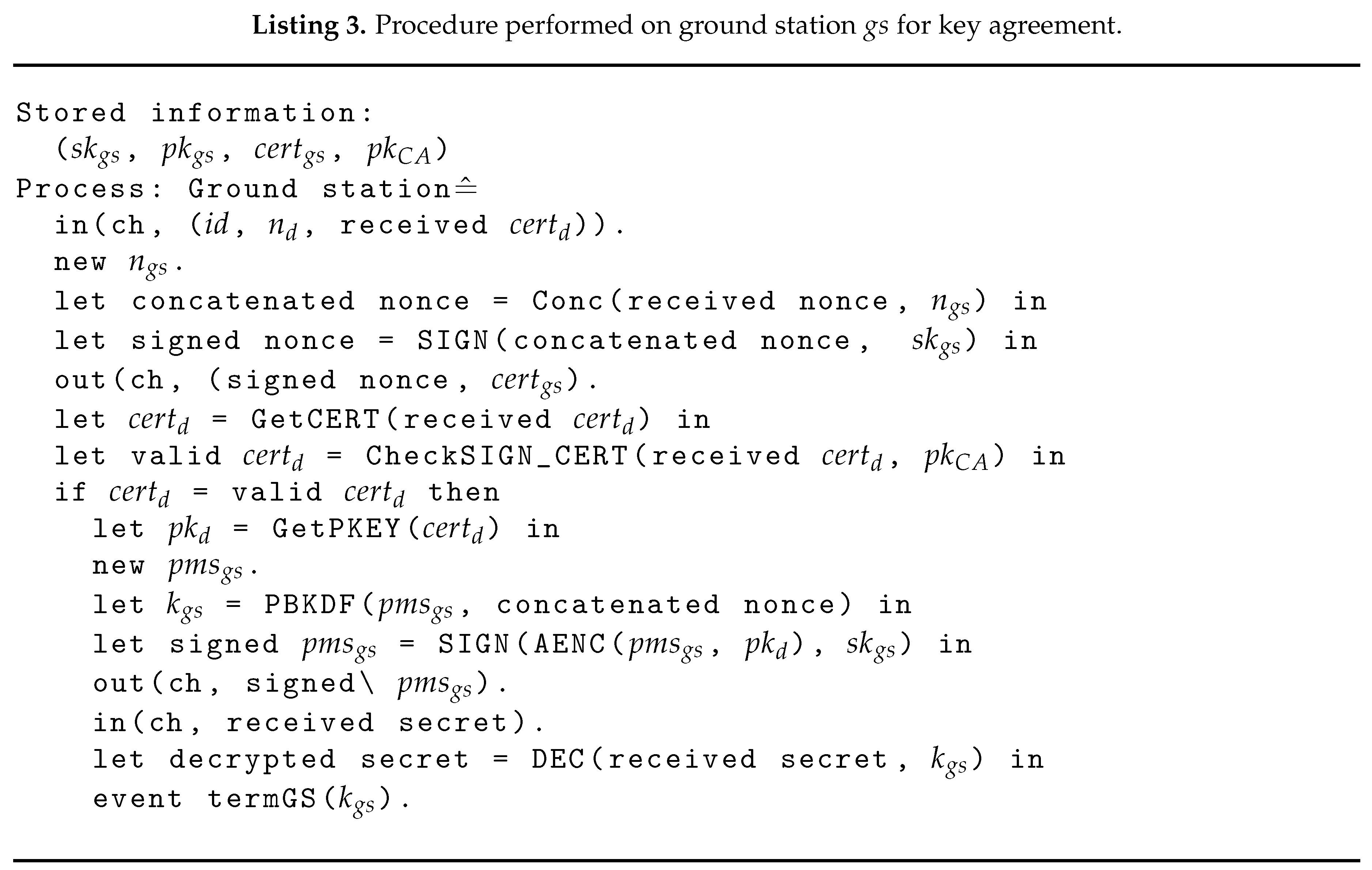
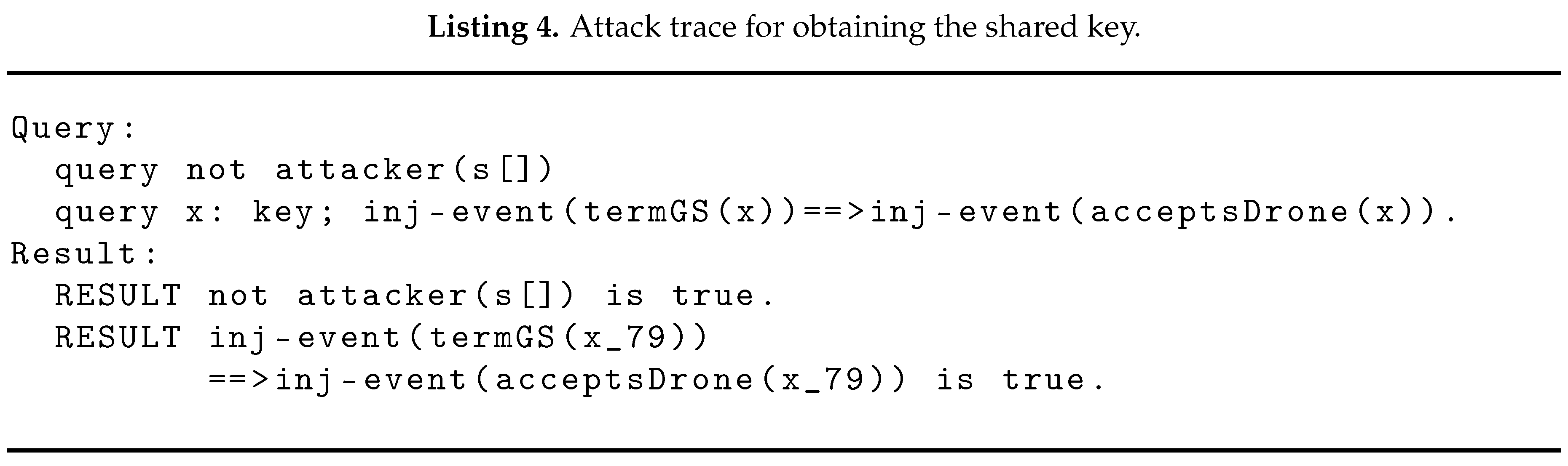
8.2. Informal Security Analysis
- Mutual authentication. Both the drone and the ground station have certificates issued by CA. During the key agreement process, both entities exchange their certificates and check the validity of the certificates. Consequently, the drone and the ground station authenticate each other if their certificates are valid.
- Pseudonymity. During the authentication process, the drone sends a message that contains its identity in SENTINEL. For preserving the privacy of the drone, a pseudonym can be used instead of the real identity of the drone. In this way, the ground station can still check if the drone has been authorized for its flight without exposing the drone’s real identity.
- Revocability. As mentioned in Section 5, both the drone and the ground station can check whether the opposing party’s certificate is revoked using a certificate validation service such as an online certificate status protocol (OCSP).
- Session key agreement. The drone and the ground station perform the key agreement process to make a flight session key (see Figure 3).
- Man-in-the middle attack. Under the mutual authentication, SENTINEL guarantees to resist against man-in-the-middle attacks. Both the drone and ground station validate each other using the certificate.
- Replay attack. The timestamp is contained in the message for authentication that represents the time to create the message. With the timestamp, the message cannot be reused because the ground station can check the freshness of the message.
- Impersonation attack. A malicious drone can try to impersonate a legitimate drone d using and . Although the malicious drone uses and , it is not possible to obtain the pre-master-secret key without the drone d’s private key.
- Known session key attack. Flight session keys are always newly created with random parameters such as , , and . Therefore, it is not possible to succeed with a known session key attack.
9. Conclusions
Supplementary Materials
Author Contributions
Funding
Conflicts of Interest
Abbreviations
| ASN.1 | Abstract syntax notation one |
| CA | Certificate authority |
| CSPRNG | Cryptographically secure pseudorandom number generator |
| DER | Distinguished encoding rules |
| ECDSA | Elliptic curve digital signature algorithm |
| GS | Ground station |
| HMAC | Hash-based message authentication code |
| IoD | Internet of drones |
| IoT | Internet of things |
| LTE | Long-term evolution |
| MAC | Message authentication code |
| OCF | Open connectivity foundation |
| OCSP | Online certificate status protocol |
| PBKDF | Password-based key derivation function |
| PIN | Personal identification number |
| PKI | Public key infrastructure |
| SHA | Secure hash algorithm |
| TLS | Transport layer security |
| UAV | Unmanned aerial vehicle |
References
- Symington, S. Amazon.com Has Officially Begun Drone Delivery. Available online: https://www.fool.com/investing/2016/12/20/amazoncom-has-officially-begun-drone-delivery.aspx (accessed on 18 March 2020).
- Gang, J. Drone Use in the Entertainment Industry and Beyond. Available online: https://thebottomline.as.ucsb.edu/2018/09/drone-use-in-the-entertainment-industry-and-beyond (accessed on 18 March 2020).
- Shear, M.D.; Schmidt, M.S. White House Drone Crash Described as a U.S. Worker’s Drunken Lark. Available online: https://www.nytimes.com/2015/01/28/us/white-house-drone.html (accessed on 18 March 2020).
- Wazid, M.; Das, A.K.; Kumar, N.; Vasilakos, A.V.; Rodrigues, J.J. Design and analysis of secure lightweight remote user authentication and key agreement scheme in Internet of drones deployment. IEEE Internet Things J. 2018, 6, 3572–3584. [Google Scholar] [CrossRef]
- Srinivas, J.; Das, A.K.; Kumar, N.; Rodrigues, J.J. TCALAS: Temporal Credential-Based Anonymous Lightweight Authentication Scheme for Internet of Drones Environment. IEEE Trans. Veh. Technol. 2019, 68, 6903–6916. [Google Scholar] [CrossRef]
- Zhang, Y.; He, D.; Li, L.; Chen, B. A lightweight authentication and key agreement scheme for internet of drones. Comput. Commun. 2020, 154, 455–464. [Google Scholar] [CrossRef]
- Lloyd, B.; Simpson, W. PPP Authentication Protocols. RFC 1334. 1992. Available online: https://tools.ietf.org/html/rfc1334/ (accessed on 27 March 2020).
- Simpson, W. PPP Challenge Handshake Authentication Protocol (CHAP). RFC 1994. 1996. Available online: https://tools.ietf.org/html/rfc1994/ (accessed on 27 March 2020).
- Aboba, B.; Blunk, L.; Vollbrecht, J.; Carlson, J.; Levkowetz, H.E. Extensible Authentication Protocol (EAP). RFC 3748. 2004. Available online: https://www.hjp.at/doc/rfc/rfc3748.html (accessed on 27 March 2020).
- The OCF Security Specification. 2020. Available online: https://openconnectivity.org/developer/specifications/ (accessed on 27 March 2020).
- IoTivity Wiki. Available online: https://iotivity.org/ (accessed on 27 March 2020).
- Sciancalepore, S.; Capossele, A.; Piro, G.; Boggia, G.; Bianchi, G. Key Management Protocol with Implicit Certificates for IoT Systems. In Proceedings of the Workshop on IoT Challenges in Mobile and Industrial Systems, Florence, Italy, 18 May 2015. [Google Scholar]
- Porambage, P.; Schmitt, C.; Kumar, P.; Gurtov, A.; Ylianttila, M. Two-phase authentication protocol for wireless sensor networks in distributed IoT applications. In Proceedings of the IEEE Conference on Wireless Communications and Networking, Istanbul, Turkey, 6–9 April 2014. [Google Scholar]
- Housley, R.; Ford, W.; Polk, W.; Solo, D. Internet X.509 Public Key Infrastructure Certificate and CRL Profile. RFC 2459. 1999. Available online: https://rfc-editor.org/rfc/rfc2459.txt (accessed on 27 March 2020).
- Kwon, H.; Raza, S.; Ko, J. POSTER: On Compressing PKI Certificates for Resource Limited Internet of Things Devices. In Proceedings of the 2018 on Asia Conference on Computer and Communications Security, Incheon, Korea, 4–8 June 2018. [Google Scholar]
- Gharibi, M.; Boutaba, R.; Waslander, S.L. Internet of Drones. IEEE Access 2016, 4, 1148–1162. [Google Scholar] [CrossRef]
- Lin, C.; He, D.; Kumar, N.; Choo, K.K.R.; Vinel, A.; Huang, X. Security and Privacy for the Internet of Drones: Challenges and Solutions. IEEE Commun. Mag. 2018, 56, 64–69. [Google Scholar] [CrossRef]
- Ni, J.; Lin, X.; Zhang, K.; Shen, X. Privacy-preserving real-time navigation system using vehicular crowdsourcing. In Proceedings of the 2016 IEEE 84th Vehicular Technology Conference (VTC-Fall), Montréal, QC, Canada, 18–21 September 2016; pp. 1–5. [Google Scholar]
- Tian, Y.; Yuan, J.; Song, H. Efficient privacy-preserving authentication framework for edge-assisted Internet of Drones. J. Inf. Secur. Appl. 2019, 48, 102354. [Google Scholar] [CrossRef]
- Greenpeace Crashes Superman-Shaped Drone into French Nuclear Plant. 2018. Available online: https://www.reuters.com/article/us-france-nuclear-greenpeace/greenpeace-crashes-superman-shaped-drone-into-french-nuclear-plant-idUSKBN1JT1JM (accessed on 28 March 2020).
- Gatwick Airport Drone Incident. 2018. Available online: https://en.wikipedia.org/wiki/Gatwick_Airport_drone_incident (accessed on 28 March 2020).
- Drone Filmed People’s Pin Codes at Co Antrim ATM. 2016. Available online: https://www.belfasttelegraph.co.uk/news/northern-ireland/drone-filmed-peoples-pin-codes-at-co-antrim-atm-34945847.html (accessed on 28 March 2020).
- Won, J.; Seo, S.; Bertino, E. Certificateless cryptographic protocols for efficient drone-based smart city applications. IEEE Access 2017, 5, 3721–3749. [Google Scholar] [CrossRef]
- Chen, C.L.; Deng, Y.Y.; Weng, W.; Chen, C.H.; Chiu, Y.J.; Wu, C.M. A traceable and privacy-preserving authentication for UAV communication control system. Electronics 2020, 9, 62. [Google Scholar] [CrossRef] [Green Version]
- Dolev, D.; Yao, A. On the security of public key protocols. IEEE Trans. Inf. Theory 1983, 29, 198–208. [Google Scholar] [CrossRef]
- Kaliski, B. PKCS# 5: Password-Based Cryptography Specification Version 2.0; RFC 2898; RSA Laboratories: Bedford, MA, USA, 2000; Available online: https://tools.ietf.org/html/rfc2898/ (accessed on 30 June 2019).
- Berges, P.M. Exploring the Vulnerabilities of Traffic Collision Avoidance Systems (TCAS) Through Software Defined Radio (SDR) Exploitation. Ph.D. Thesis, Virginia Tech, Blacksburg, VA, USA, 2019. [Google Scholar]
- Johnson, D.; Menezes, A.; Vanstone, S. The Elliptic Curve Digital Signature Algorithm (ECDSA). Int. J. Inf. Secur. 2001, 1, 36–63. [Google Scholar] [CrossRef]
- Suárez-Albela, M.; Fernández-Caramés, T.M.; Fraga-Lamas, P.; Castedo, L. A Practical Performance Comparison of ECC and RSA for Resource-Constrained IoT Devices. In Proceedings of the Global Internet of Things Summit, Bilbao, Spain, 4–7 June 2018. [Google Scholar]
- Blanchet, B. Automatic verification of correspondences for security protocols. J. Comput. Secur. 2009, 17, 363–434. [Google Scholar] [CrossRef] [Green Version]
- Bhargavan, K.; Blanchet, B.; Kobeissi, N. Verified Models and Reference Implementations for the TLS 1.3 Standard Candidate. In Proceedings of the IEEE Symposium on Security and Privacy, San Jose, CA, USA, 22–26 May 2017. [Google Scholar]
- Kobeissi, N.; Bhargavan, K.; Blanchet, B. Automated Verification for Secure Messaging Protocols and their Implementations: A Symbolic and Computational Approach. In Proceedings of the IEEE European Symposium on Security and Privacy, Paris, France, 26–28 April 2017. [Google Scholar]
| Notation | Description |
|---|---|
| || | Concatenation operation |
| Identity of drone d | |
| Flight plan for drone d | |
| Nonce of drone d | |
| Nonce of ground station | |
| Certificate of drone d | |
| Certificate of ground station | |
| Private key of drone d | |
| Private key of ground station | |
| Public key of drone d | |
| Public key of ground station | |
| Public key of CA | |
| Signing function | |
| Encryption function | |
| Decryption function | |
| Password-based key derivation function | |
| Pre-Master-Secret key | |
| Flight session key for drone d | |
| Flight session key for ground station | |
| Hash-based message authentication code function | |
| Hash value computed by drone d | |
| Hash value computed by ground station | |
| Message of drone d |
| SENTINEL | X.509 | X.509 (gzip) | |
|---|---|---|---|
| Size (bytes) | 186 | 682 | 654 |
| SENTINEL | TLS for IoT | ||
|---|---|---|---|
| Time (ms) | Avg. | 198.06 | 359.66 |
| Std. | 39.25 | 50.80 | |
| Message size (bytes) | Send | 426 | 708 |
| Receive | 192 | 825 | |
| Total | 618 | 1533 |
| SENTINEL | TLS for IoT | ||
|---|---|---|---|
| Time (ms) | Avg. | 178.57 | 549.75 |
| Std. | 35.07 | 84.27 | |
| Message size (bytes) | Total | 72 | 1644 |
| Security Features | Srinivas et al. [5] | Zhang et al. [6] | Wazid et al. [4] | Won et al. [23] | Tian et al. [19] | Chen et al. [24] | SENTINEL |
|---|---|---|---|---|---|---|---|
| Mutual authentication | ✓ | ✓ | ✓ | ✓ | ✗ | ✓ | ✓ |
| Pseudonymity/Anonymity | ✓ | ✓ | ✓ | ✗ | ✗ | ✓ | ✓ |
| Revocability | ✓ | ✓ | ✓ | ✗ | ✗ | ✗ | ✓ |
| Session key agreement | ✓ | ✓ | ✓ | ✓ | ✗ | ✓ | ✓ |
| Man-in-the middle attack | ✓ | ✓ | ✓ | ✓ | - | ✓ | ✓ |
| Replay attack | ✓ | ✓ | ✓ | - | ✓ | ✓ | ✓ |
| Impersonation attack | ✓ | ✓ | ✓ | - | - | ✓ | ✓ |
| Known session key attack | - | ✓ | - | - | N/A | - | ✓ |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Cho, G.; Cho, J.; Hyun, S.; Kim, H. SENTINEL: A Secure and Efficient Authentication Framework for Unmanned Aerial Vehicles. Appl. Sci. 2020, 10, 3149. https://doi.org/10.3390/app10093149
Cho G, Cho J, Hyun S, Kim H. SENTINEL: A Secure and Efficient Authentication Framework for Unmanned Aerial Vehicles. Applied Sciences. 2020; 10(9):3149. https://doi.org/10.3390/app10093149
Chicago/Turabian StyleCho, Geumhwan, Junsung Cho, Sangwon Hyun, and Hyoungshick Kim. 2020. "SENTINEL: A Secure and Efficient Authentication Framework for Unmanned Aerial Vehicles" Applied Sciences 10, no. 9: 3149. https://doi.org/10.3390/app10093149
APA StyleCho, G., Cho, J., Hyun, S., & Kim, H. (2020). SENTINEL: A Secure and Efficient Authentication Framework for Unmanned Aerial Vehicles. Applied Sciences, 10(9), 3149. https://doi.org/10.3390/app10093149






