Abstract
Population aging is currently a tough problem of many countries. How to utilize modern technologies (including both information and medical technologies) to improve the service quality of health information is an important issue. Personal Health Record (PHR) could be regarded as a kind of health information records of individuals. A ciphertext policy attribute-based encryption (CP-ABE) is a cryptographic primitive for fine-grained access control of outsourced data in clouds. In order to enable patients to effectively store his medical records and PHR data in medical clouds, we propose an improved multi-user CP-ABE scheme with the functionality of keyword search which enables data users to seek for specific ciphertext in the cloud server by using a specific keyword. Additionally, we adopt an independent proxy server in the proposed system architecture to isolate the communication between clients and the cloud server, so as to prevent cloud servers from suffering direct attacks and also reduce the computational loading of cloud servers. Compared with the previous approach, the proposed encryption algorithm takes less running time and the ciphertext length is also relatively short. Moreover, the procedures of re-encryption and pre-decryption only require one exponentiation computation, respectively.
1. Introduction
With the evolution of wireless technology and mobile application devices, mobile commerce and computing have received much attention and sharing data on cloud servers equally becomes more convenient. Nevertheless, several potential security risks like the impersonation attacks and data disclosure should be noted. To protect sensitive data before being uploaded to cloud servers, data encryption is a commonly employed way of preventing the risk of data disclosure, i.e., a data owner encrypts data with his/her own key before uploading data to cloud centers such that only authorized data users could decrypt and recover original messages.
Personal health information is an important factor in the digitization of medical treatment. In addition to the electronic medical records of hospitalization and related surgery, everyone can independently check his/her own health information such as heartbeat, height, blood pressure, blood sugar and diet content. Such health information can be used as a basis for self-health monitoring. Generally speaking, current health information could be classified into personal health record (PHR) [1,2], electronic health record (EHR) [3] and electronic medical record (EMR) [4,5], which are explained as follows.
Person health record (PHR): This record is measured by the personal health sensing equipment. It can be used to measure the wearer’s daily physiological data including everyday diet, exercise habits, heartbeat, blood sugar, medication, doctor’s diagnosis records and other related information. Such health records maintained by the wearer could be provided to the physician for evaluation at the time of consultation. As for the long-term treatment, it can also save unnecessary medical expense.
Electronic health record (EHR): This record contains medical history, medication records, prescription, medication allergies, etc. It can be accessed by specific hospitals with the the patient’s consent, so that medical personnel can easily search the relevant information about the patient. In addition, the record can be updated by patients and medical institutions at any time. With various information, medical staff are able to make more accurate and efficient diagnoses.
Electronic medical record (EMR): Nowadays, the electronic medical records used by medical institutions, the process of patient diagnosis and treatment are all kept in the medical cloud system by the physicians. The access right of the electronic medical records is owned by the physician, meaning that these data could be accessed by hospitals through the medical clouds.
In medical cloud environments, there will be three main roles: a medical data owner, a cloud server and a medical user. The medical data owner will store his/her own health data on the cloud server and then authorize specific users such as patients and medical staffs to access the data. However, since cloud servers are not completely trustworthy, there will be many security misgivings such as data leakage and data loss. When the data are stored in the clouds with the form of ciphertext, it would be difficult to perform the functionality of keyword search. Consequently, a suitable cryptographic mechanism which could deal with the above scenarios is quite important. In this work, we elaborate on the merits of attribute-based encryption mechanisms and come up with a multi-user ciphertext policy attribute-based encryption scheme with the functionality of keyword search for medical cloud systems.
1.1. Related Work
In 1998, Blaze et al. [6] presented the first proxy-re encryption (PRE) in which a semi-trusted agent could obtain one re-encryption key to transform the ciphertext intended for the user A to the ciphertext intended for the user B, so that the user B could decrypt the ciphertext with his/her private key. In order to ensure the confidentiality of the ciphertext during the re-encryption process, the agent should not be capable of learning any information related to encrypted messages. In 2005, Ateniese et al. [7] introduced the PRE mechanism based on bilinear pairings and proved that their scheme could withstand chosen-ciphertext attacks. In 2007, Canetti and Hohenberger [8] addressed a multiple-hop PRE scheme which could also resist the chosen-ciphertext attack. Meanwhile, they proved the security of their mechanism in the standard security proof model. Thinking of identity-based cryptosystems, in 2016, Wang et al. [9] presented two ID-based PRE variants which are suitable for secure data sharing in the cloud. Considering secure cloud storage, in 2018, Zeng and Choo [10] addressed a so-called conditional PRE scheme with efficient computation. Nowadays, the PRE mechanism has many practical applications [6,11,12,13,14,15,16] like the forwarding of e-mails, the distribution of private keys and the management of key escrow.
To further provide the ciphertext with the search function, Boneh et al. [17] introduced the mechanism of public key encryptions with the characteristic of keyword search (PEKS) utilizing the assumption of Decision Diffie–Hellman Problem (DDHP). In their scheme, a data owner can use the public key to encrypt data along with keywords such that data users could request the keyword search on stored ciphertexts and decrypt it. In 2016, Cui et al. [18] realized an expressive PEKS system in prime order groups. Their scheme supports the multi-keyword search using the expressive Boolean formula. They also proved the security of their scheme in the standard model. To date, lots of methods for PEKS have been presented. The PEKS is a security mechanism that is often applied to cloud storage and could be utilized to seek for encrypted data. Unfortunately, the scheme is inherently subject to the attacks of keyword guessing. To solve this security flaw, in 2016, Chen et al. [19] presented a sever-aided public key encryption with a keyword search (SA-PEKS). In their construction, a semi-trust keyword server (KS) will be independent from the storage server and the data user must be authenticated by the KS to obtain credentials. Their scheme is different from the PEKS as users must request the KS to run an authentication protocol for generating a KS-derived keyword in SA-PEKS. Consequently, it is secure against the offline keyword-guessing attacks.
In order to share a ciphertext with many persons, Sahai and Water [20] presented an extension of IBE, called an attribute-based encryption (ABE) scheme. ABE is a promising cryptographic primitive which offers reliable and dynamic data-sharing. The notion of ABE utilizes the attributes of users to match an access policy associated with the ciphertext or the private key. More precisely, the ABE schemes could be classified into two categories, namely Ciphertext-Policy ABE (CP-ABE) [21] and Key-Policy ABE (KP-ABE) [22]. In 2007, Bethencourt et al. [21] introduced the CP-ABE. In a CP-ABE cloud storage system, a data owner encrypts data into ciphertext and then specifies an access policy before storing the ciphertext in the cloud server. The data user’s private key is correlated with a set of attributes based on his/her identity. On the other hand, in a KP-ABE cloud storage system, a data owner’s ciphertext is associated with a set of attributes, while the data user’s private key is correlated with an access policy. In 2017, Lin et al. [23] proposed a collaborative key management mechanism using CP-ABE to share data in clouds. In their scheme, a key authority will be responsible for generating, issuing and storing private keys. Using the attribute group key to perform the private key update, their system could achieve immediate attribute revocation. In 2019, Sethia et al. [24] proposed a constant-size CP-ABE scheme with scalable revocation for resource-constrained IoT devices. They not only successfully implemented the proposed scheme, but also showed that their work is chosen-ciphertext attack (CCA)-secure. In 2020, Zhou et al. [25] proposed a multi-authority CP-ABE access model in multicloud. In particular, they introduced an attribute mapping method to handle both problems of data-sharing security and policy conflict in multicloud storage systems (MCSS).
1.2. Contributions
In this work, the authors aim at the access control and data-sharing of cloud health information. Using attribute-based encryption schemes, we further combine the techniques of ciphertext keyword search, linear secret-sharing and proxy re-encryption. In addition to being applicable to medical cloud systems, the proposed approach could also be applied to the general cloud environments. Specifically, we improve Wang et al.’s system [26] by reducing the ciphertext length and the computational complexity of encryption algorithm, and further introducing the role of proxy server to enhance the communication security. The shorter ciphertext length of our system also benefits the savings of communication overheads. Technically speaking, we combine users’ attribute private keys with the public key of the proxy server, so that a legal trapdoor generated by the data user must be further converted by the proxy server. Besides, the ciphertext sent by the data owner is also re-encrypted by the proxy server before it is stored in the cloud server. Consequently, when a data user requests an encrypted message from the cloud server, this message should be pre-decrypted by the proxy server before it can be correctly recovered by the data user.
2. Preliminaries
We review the operation of bilinear pairings [27,28] and the technique of the linear secret-sharing scheme (LSSS) [29] in this section.
Bilinear Pairing
Let the symbols of G1 and G2 be two multiplicative cyclic groups in which the order is a prime number p and g is the generator of the group G1. A bilinear map is expressed as e: G1 × G1→G2 with the following properties:
- (i)
- Bilinearity:
For all elements g, h ∈ G1 and a, b ∈R Zp, we have e(ga, hb) = e(g, h)ab;
- (ii)
- Non-degeneracy:
Let a generator in the group of G1 be p. Then the value e(p, p) would also be a generator in the group G2;
- (iii)
- Computability:
There is an efficient algorithm to compute e(g, h) for all elements g, h ∈ G1.
Linear Secret Sharing Scheme (LSSS) [29]
Let Ml×n be a matrix with the row number of l and the column number of n, Mi the i-th row of the matrix and a mapping function ρ: {1, 2, …, l}→P which converts a row to a label of party. We say that a secret-sharing scheme П for the access structure 𝔸 over a set of parties P could be denoted as a linear secret-sharing method (LSSS) from Zp. It is also represented as (Ml×n, ρ), which consists of the following two effective algorithms:
- (i)
- Share((Ml×n, ρ), s): The share algorithm takes a secret-sharing value s ∈R Zp as an input, randomly chooses y2, …, yn ∈R Zp and defines v = (s, y2, …, yn). At last, it outputs Ml×n · v as the vectors of l shares. That is, the shared value obtained by the participant ρ(i) is λi = ⟨Ml×n · v⟩;
- (ii)
- Recon((Ml×n, ρ), D): The reconstruction algorithm takes an access set D ∈ 𝔸 as the input. Let I = {i | ρ(i) ∈ D}. It will return a set of constants {μi}i ∈ I fulfilling that Σi∈I μi · λi = s.
3. The Proposed Scheme
We introduce an improved CP-ABE scheme with the functionality of keyword search based on Wang et al.’s construction [26]. In particular, we add a proxy server to the proposed system architecture for protecting the medical cloud server from direct attacks. Although two added algorithms, i.e., Re-Encrypt and Pre-Decrypt, would slightly increase the overall computational costs, we believe that it is a worthy tradeoff to obtain a higher security level.
3.1. System Model
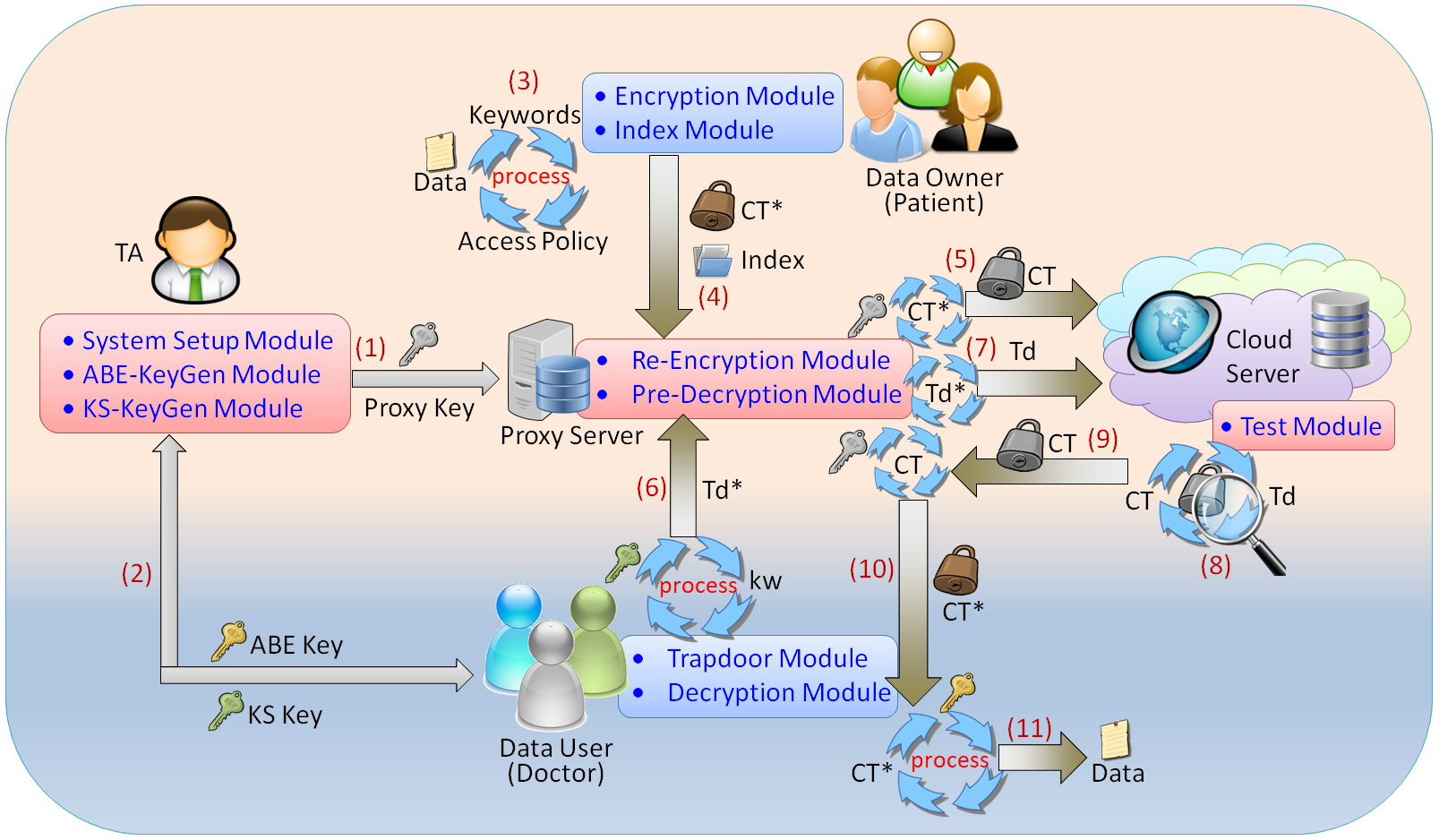
Figure 1 shows the system model of the proposed scheme. There are five main parties in the proposed system: trusted authority (TA), proxy server (PS), medical cloud server (CS), data owner (DO) and the data user (DU).
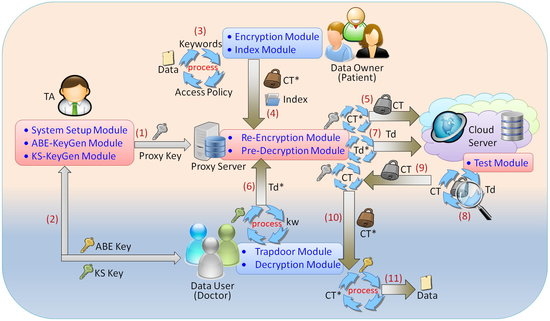
Figure 1.
The architecture and data flow of the proposed system.
Trusted Authority (TA): This would be responsible for the system initialization and generating public parameters, distributing attribute keys (ABE-Keys) and keyword search keys (KS-Keys) associated with DU’s attributes. Moreover, the TA also creates the key pair of proxy servers.
Data Owner (DO): The DO is a patient who defines an access policy for the PHR data or medical records and then encrypts the corresponding keywords into indexes. At last, the DO uploads the ciphertext along with indexes to the cloud.
Cloud Server (CS): The CS provides the services of storage and data retrieval. It will store encrypted data and indexes outsourced by the DO. After receiving requests from data users, it executes search procedures and transmits the matched ciphertext back.
Data User (DU): The DU is a doctor who can access patients’ encrypted data from CS. Specifically, the DU owns the KS-Key and the ABE-key; the former is used to generate trapdoor information while the latter is used to decrypt ciphertexts.
Proxy Server (PS): The PS is an important role between the DO/DU and the CS. The PS is responsible for performing the proxy re-encryption process. After receiving the ciphertext uploaded by the DO, it will execute the re-encryption operation and then transmit the re-encrypted ciphertert to the CS. Similarly, after receiving the ciphertext downloaded by the DU, it will execute pre-decryption process and then return the ciphertext to the DU. Furthermore, when receiving trapdoors of keyword search requests, the PS also modifies it before transmitting it to the CS.
3.2. Algorithms
The proposed system could be divided into ten algorithms stated below.
Setup: Taking as input a security parameter k, the algorithm generates system’s public parameters params and a master secret key msk.
ABE-KeyGen: The attribute key generation algorithm takes as input system parameters params, a master secret key msk, a user’s identity id and the attribute set w. It generates an attribute private key did, w associated with user’s identity id.
KS-KeyGen: The keyword search key generation algorithm takes as input system parameters params, a master secret key msk and a user identity id. It generates a keyword search key qid for id.
Encrypt: The encryption algorithm takes as input system parameters params, an LSSS access structure 𝔸 and a message msg. It generates a ciphertext ct.
Re-Encrypt: The re-encryption algorithm takes as input system parameters params, a ciphertext ct and the private key of PS, say β. It generates a re-encrypted ciphertext ct*.
Index: The index algorithm takes as input system parameters params and a keyword set kw. It produces a secure index IX(kw).
Trapdoor: The trapdoor algorithm takes as input system parameters params, a user’s keyword search key qid, a user’s attribute private key did, w, a keyword set kw and the private key of PS. It generates a trapdoor Tkw corresponding to the keyword set kw.
Test: The test algorithm takes as input system parameters params, a trapdoor Tkw and an index IX(kw). It will return either an intermediate result Qct or 0.
Pre-Decrypt: The pre-decryption algorithm takes as input system parameters params, a re-encrypted ciphertext ct* and the private key of PS, say β. It outputs a ciphertext ct.
Decrypt: The input of this algorithm includes system parameters params, a ciphertext ct with the intermediate data Qct, and the user’s attribute private key did, w. Finally, the algorithm will return an original message msg or an error symbol ⊥.
3.3. Concrete Construction
Based on the previously defined algorithms, the authors will introduce a substantial formation of multi-user CP-ABE scheme with keyword search for medical cloud systems. Table 1 first summarizes several utilized notations. The operation of each algorithm is concretely described as follows.

Table 1.
Symbol notations.
Setup: On inputting a security parameter k, the TA chooses a random numbers d ∈ Zp* as the master secret key, and then generates essential parameters, as shown in Table 1.
ABE-KeyGen: Each DU can request his/her attribute key (ABE-Key) from the TA by sending the correlated identity id and attribute set w. Utilizing the information w and id, the TA first selects t ∈RZp* to derive
K = (gt)d(gd),
L = (gβ)t,
{Kx = H(x)t}x∈w.
Then, TA records (id, gdt) in the user list and the ABE-Key did, w = (K, L, {Kx}) would be returned to the DU through a secure channel.
KS-KeyGen: Each DU could request his/her keyword search key (KS-Key) from the TA by sending the correlated identity id. Utilizing the information id, the TA first checks whether the user’s identity is stored in the user list. Otherwise, the TA will deny this request. Then, DU chooses a random number u ∈ Zp* to compute the following parameter for the TA.
qu = gu
After receiving qu, the TA retrieves gdt from the user list to compute
qid = (gdt)(qud).
The KS-Key qid is sent back to the DU through a secure channel. DU also keeps the chosen random number u for decryption in the future.
Encrypt: When DO wants to encrypt his/her sensitive data msg for uploading to the CS, DO first defines an access policy 𝔸 over a set of parties P who are able to decrypt his/her sensitive data msg. According to LSSS, the secret-sharing scheme for the access policy 𝔸 could be expressed as (Ml×n, ρ) using a random vector v = (s, y2, …, yn) ∈RZp* and a mapping function ρ. Then, DO utilizes the share algorithm of LSSS to obtain l share values λi = ⟨Mi, v⟩ and computes the following parameters:
C = [e(g, g)d]s · (msg),
C’ = gs,
{Ci = gdλiH(ρ(i))−s},
Here, the ciphertext ct is composed of (C, C’, {Ci}).
Index: For creating an index in relation to the keyword set kw, the DO first picks an integer ti ∈R Zp* for each keyword kwi ∈kw, and then computes
{ki = [e(g, g)d]s · e(g, H(kwi))s}kwi ∈ kw,
IX(kw) = {(ti, fi = F(ki, ti))}kwi ∈kw,
Next, the index set IX(kw) along with the corresponding ciphertext ct and the access policy (Ml×n, ρ) are delivered to the PS.
Re-Encrypt: After receiving the ciphertext ct from the DO, the PS first utilizes its private key β to re-encrypt the parameter C in ciphertext as
C* = Cβ.
The re-encrypted ciphertext ct* is formed by (C*, C’, {Ci}). Then the re-encrypted ciphertext ct* along with the access policy (Ml×n, ρ) and index IX(kw) will be stored by the CS.
Trapdoor: The DU can utilize the keyword search key qid to generate a trapdoor for ciphertext search. Let kw be the searched keyword and w the attribute set of DU. First, the DU computes
Tq(kw) = (gH(kw))(qid−u),
L’’ = L−u,
{K’x = Kx−u}x∈w.
Then, the trapdoor T’kw = (Tq(kw), L’’, {K’x}x∈w) and the attribute set w are transferred to the PS. When the PS receives (T’kw, w) from the DU, the PS computes the parameter L’ as
L’ = (L″)β−1.
Then, the modified trapdoor Tkw = (Tq(kw), L’, {K’x}x∈w) and the attribute set w are delivered to the CS.
Test: After receiving (Tkw, w), the CS checks all ciphertext index data (ct*, IX(kw)) and the embedded access policy (Ml×n, ρ). Suppose that w fulfills the access policy (Ml×n, ρ) of some ciphertext ct*. Let {μi}i∈ I be a set of constants outputted by the Recon algorithm of LSSS. Then the CS further computes
and verifies whether IX(kw) satisfies
Qct = Πi ∈ I[e(Ci, L’)e(C’, K’ρ(i))]μi,
kkw = e(C’, Tq(kw))/Qct.
{fi = F(kkw, ti)}fi ∈ IX(kw).
If Equation (18) holds, we know that kw ∈ kw and the CS will transmit (ct*, Qct) to the PS.
We can first derive Equation (16) as follows
Qct = Πi ∈ I[e(Ci, L’)e(C’, K’ρ(i))]μi
= Πi ∈ I[e(gdλiH(ρ(i))−s, gt)e(gs, H(ρ(i))t)]μi/u
= Πi ∈ I[e(gdλi, gt)]μi/u
= e(g, g)dts/u
Then, we further derive Equation (17) as follows
kkw = e(C’, Tq(kw))/Qct
= e(gs, H(kw)qid−u)/e(g, g)dts/u
= e(gs, H(kw)(gdtqud)−u)/e(g, g)dts/u
= e(gs, H(kw)(gdt/ugd))/e(g, g)dts/u
= [e(g, g)d]s · e(g, H(kw))s
Consequently, the correctness of Equation (18) could be easily derived below
F(kkw, ti)
= e (e(g, (gb)sH(kw)(ga)s), ti)
= e(ki, ti)
= fi
Pre-Decrypt: After receiving (ct*, Qct) where ct* = (C*, C’, {Ci}), the PS runs the pre-decryption process by computing
C = (C*)β−1.
The new ciphertext ct = (C, C’, {Ci}) and Qct are transferred to the DU
Decrypt: When the DU receives ct = (C, C’, {Ci}) from the PS, it can utilize its attribute key K to recover
msg = C · Qctu/e(C’, K).
The correctness of Equation (20) could be confirmed below:
C · Qctu/e(C’, K)
= msg · [e(g, g)d]s · e(g, g)dts/e(gs, gdtgd)
= msg · e(g, g)ds + dts/e(g, g)s(dt + d)
=msg
Note that in the practical usage, a data owner (patient) should utilize the system parameters generated by the TA rather than re-initializing the whole system parameters each time. The role of proxy server is semi-trusted, i.e., it might be curious about the received ciphertext, but will not deviate from the predefined process. When receiving an identical ciphertext, the cloud server might overwrite the existing one or just abort current process depending on the predefined rules. We display the pseudo-code of the proposed system in Table 2.

Table 2.
The pseudo-code of the proposed system.
4. Security Proof and Efficiency
We first formally prove that the proposed system is secure against the adaptive chosen-ciphertext attacks (CCA2), assuming the hardness of Decisional Diffie–Hellman Problem (DDHP) in the random oracle model as Theorem 1.
Theorem 1.
The proposed multi-user CP-ABE with keyword search is secure against the adaptive chosen-ciphertext attacks (CCA2) in the random oracle model provided that there is no polynomial-time adversary having a non-negligible advantage to break the intractable DDHP.
Proof.
We will complete this security proofs by showing that if the ciphertext indistinguishability of the proposed system could be broken by a polynomial-time adversary , another DDH distinguisher could also be built by calling as a subroutine. The goal of is to decide whether gc = gab or not by giving a DDHP instance (g, ga, gb, gc). In the following simulation game, the distinguisher is responsible for answering queries submitted by the adversary . □
Setup:
Initially, chooses β ∈ Zp* and computes gβ as the key pair of PS. The public key of TA is set as (gc, e(gc, g)). Then transmits necessary system parameters {p, G1, G2, g, e, H, F, gβ, gc, e(gc, g), Ω, w, Λ} to .
Phase 1:
The adversary will interact with the distinguisher below.
H oracle: When submits an H(x) query, returns with an integer v1 ∈R Zp*. The record (x, v1) is also stored in the H-list.
F oracle: When submits an F(ki, ti) query, responds with an integer v2 ∈R Zp*. The record (ki, ti, v2) is also stored in the F-list.
ABE-KeyGen oracle: When submits an ABE-KeyGen(id, w) query, selects t ∈RZp* to derive K = (gc)t(gc), L = (gβ)t, {Kx = H(x)t}x∈w, and keeps (id, gct) in the user list. Finally, returns the ABE-Key did, w = (K, L, {Kx}).
KS-KeyGen oracle: When submits a KS-KeyGen(id) query, first checks if id is stored in the user list and then retrieves gct to compute qu = gu and qid = (gct)(gcu) where u ∈ Zp*. The value (qid, u) is also returned to as a result.
Encrypt oracle: When submits an Encrypt(𝔸, msg) query, first chooses a random vector v = (s, y2, …, yn) ∈RZp* and computes λi = ⟨Mi, v⟩, C = [e(gc, g)]s · (msg), C’ = gs, {Ci = gcλiH(ρ(i))−s}. The ciphertext ct = (C, C’, {Ci}) is returned to as a result.
Index oracle: When submits an Index(kw) query, chooses ti ∈R Zp* for each keyword kwi ∈kw, and then computes {ki = [e(g, gc)]s · e(g, H(kwi))s}kwi ∈kw and IX(kw) = {(ti, fi = F(ki, ti))}kwi ∈kw. At last, the index set IX(kw) is returned to as a result.
Re-Encrypt oracle: When submits a Re-Encrypt(ct) query, returns ct* = (C*, C’, {Ci}) where C* = Cβ.
Trapdoor oracle: When submits a Trapdoor(id, qid, u, kw, did, w, w) query, runs the Trapdoor algorithm of the proposed system and then returns Tkw = (Tq(kw), L’, {K’x}x∈w) to .
Test oracle: When submits a Test(Tkw, w) query, runs the Test algorithm of the proposed system and then returns the result to .
Pre-Decrypt oracle: When submits a Pre-Decrypt(ct*, Qct) query, runs the Pre-Decrypt algorithm of the proposed system and then returns ct = (C, C’, {Ci}) & Qct to .
Decrypt oracle: When submits a Decrypt(id, ct*, Qct) query, first find out the ABE-Key did, w from previous history of ABE-KeyGen queries and then runs the Decrypt algorithm. Then the recovered msg is returned to .
Challenge:
The adversary would deliver two messages, (msg0, msg1) of the same length and an access policy 𝔸. Next, decides mλ using an internal flipped coin λ ← {0, 1} and generates a corresponding ciphertext ct‘ according to the steps of previous Encrypt queries except that C = [e(ga, gb)]s · (msgλ). The ciphertext ct‘ is the target challenge for .
Phase 2:
The adversary could make new queries, such as those mentioned in Phase 1. However, it is not allowed to directly make a Decrypt query on the challenged ciphertext. At the end of this game, has to output a bit λ’. If λ’ = λ, we say that wins this game.
Analysis of the game:
In the above simulation game, responds to each query made by with an indistinguisbable response without termination. Therefore, we could claim that if the adversary has the non-negligible advantage ε to break the ciphertext indistinguishability of the proposed scheme, the distinguisher also has the non-negligible advantage ε to solve the given DDHP instance. Precisely specking, when λ’ = λ, we could know that gc = gab. Otherwise, gc ≠ gab.
Q.E.D.
Considering potential data risks in medical cloud systems, the authors analyze the essential security requirements with respect to the constructed system as follows.
- (1)
- User-controlled access control
In our system, the encryption process uses an attribute-based encryption mechanism. That is, the DO can formulate a corresponding access structure for his/her ciphertext and authorize it to a specific DU through the access structure. In other words, when the DU wants to access the ciphertext stored in the cloud, the attribute set corresponding to the DU’s private key must satisfy the access structure of desired ciphertext. Therefore, the proposed system has the characteristic of user-controlled access control.
- (2)
- Multi-user sharing
Cloud data sharing mechanisms could be categorized into two types, i.e., single-user and multi-user. Traditionally, it is not secure to achieve multi-user data sharing by using the technique of private key sharing. In our system, the idea of multi-user sharing is realized by utilizing the technique of linear secret-sharing (LSSS) which randomly chooses a secret-sharing value s through the Share algorithm to achieve multi-user sharing and avoid the risk of private key leakage.
- (3)
- Confidentiality of ciphertexts
According to the proposed Encrypt algorithm, the ciphertext ct generated by the DO includes parameters (C, C’, {Ci}). However, only the parameter C is related to the plaintext msg. Since C = msg · e (ga, gs). Without the secret-sharing value s randomly chosen by the DO, any malicious attacker can only derive the original plaintext msg by guessing the correct s, and the success probability is only (p − 1)−1, which is negligible.
- (4)
- Confidentiality of searched keywords
In the proposed trapdoor algorithm, the keywords sent by the DU will be encrypted by the PS, which utilizes the DU’s KS-Key and an integer u chosen at random. Therefore, only the parameter Tq(kw) of the trapdoor contains the plaintext information of the keyword kw searched by the DU. When the PS re-encrypts the parameter L’’ of the trapdoor with its private key β, it learns nothing about the keyword searched by the DU. Moreover, a malicious TA only knows the KS-Key of the DU. Even if it colludes with the PS, they cannot successfully derive the keyword kw due to the unknown random number u chosen by the DU.
- (5)
- Unforgeability of trapdoors
A legitimate trapdoor T’kw generated by the DU includes (Tq(kw), L’, {K’x}x∈ w), in which the parameter Tq(kw) is generated by the KS-Key, the parameters L’ and {K’x}x∈ w are both generated using a random number correlated to the KS-Key. In addition, the re-encrypted trapdoor created by the PS is Tkw = (Tq(kw), L’, {K’x}x∈ w), in which the parameter L’ is computed with the PS’s private key β. Therefore, without all of the above-mentioned information, no attackers could forge a legitimate trapdoor.
- (6)
- Resistance to malicious cloud servers
Uploading sensitive data to the cloud server is risky. If the CS’s behavior is malicious, the encrypted data and keywords uploaded by the user might be viewed. However, according to the proposed Encrypt, Re-Encrypt and Trapdoor algorithms, if a malicious CS lacks the information of correct user keys, the PS’s private key and the utilized random number, it will encounter computational difficulty and fail to make it.
Since the proposed scheme is modified from Wang et al.’s mechanism [26], we will make a comparison of computational complexity. Table 3 shows the computational complexity analysis of the algorithms of the two systems. Note that we only consider the operations of bilinear pairing (Tbp) and exponential (Texp), since they will take more computation time. From this table, it is evident that the Encrypt algorithm of our system is efficient than that of Wang et al.’s work. The ciphertext length of the proposed scheme is also shorter, which could benefit to the reduction in communication overheads and cloud storage space. Although Wang et al.’s system has the lower computational complexity in the algorithm of Trapdoor, their system does not support the functionalities of re-encryption and pre-decryption.

Table 3.
Comparison of computational costs.
To make a practical simulation of the proposed system, we adopt the experimental results of [30] which utilized the hardware of Macbook Pro laptop with a 2.7 GHz Intel Core i5 processor and 8GB RAM. According to their results, shown in Table 4, the approximate running time of a bilinear pairing operation is about 10.243 milliseconds (ms), and that of an exponentiation computation is 1.266 ms.

Table 4.
Approximate execution time of evaluated computation.
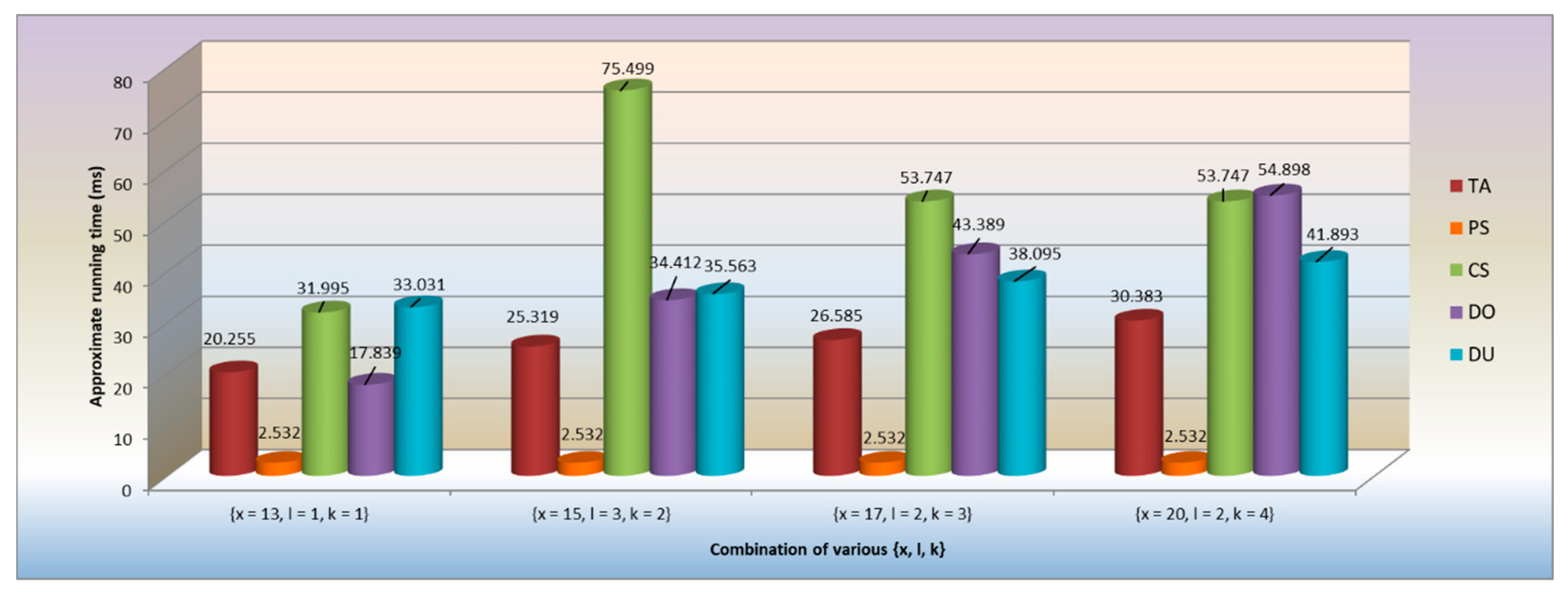
Figure 2 simulates the approximate running time of each participated party with respect to various {x, l, k} combinations. From this figure, we can observe that the running time of the PS remains constant no matter how the combination changes. As for the DU, its running time is mainly affected by the size of attribute sets. The major factor to affect the running time of the CS is the number of shared users, since the CS must spend more time to perform the Test procedure. The TA is responsible for performing the ABE-KeyGen and KS-KeyGen algorithms, i.e., its running time would be affected by the size of attribute sets along with the number of shared users. The latter also affects the execution time of the DO when performing the encryption procedure. In addition, the Index algorithm carried out by the DO would also be influenced by the number of keywords.
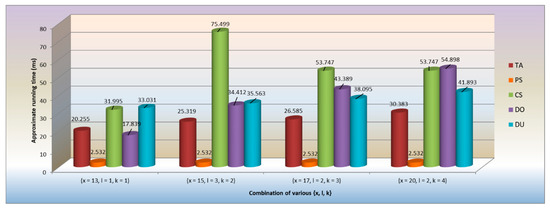
Figure 2.
Comparison of various {x, l, k} combinations.
5. Conclusions
The data-sharing of medical cloud systems is an important issue in the current world. How to ensure the security of health and medical data kept in cloud servers has become the critical topic of many researchers. Using attribute-based encryption mechanisms could obtain one-to-many data-sharing and fine-grained access control. In this work, the authors came up with an efficient multi-user, ciphertext policy attribute-based encryption scheme with keyword search for medical cloud systems. More precisely, we improved Wang et al.’s system by decreasing the computational complexity of Encrypt algorithm and further introduced the role of proxy server to not only release the load of the cloud server, but also protect the cloud server from direct attacks. The Re-Encrypt and Pre-Decrypt processes conducted by the proxy server only take one exponentiation computation. We believe that it would be a worthy tradeoff to obtain a better security level. Compared with Wang et al.’s system, the ciphertext length of our system is also shorter, which aids in the savings of communication costs.
Author Contributions
H.-Y.L. wrote the original draft. Y.-R.J. made the performance evaluation. All authors have read and agreed to the published version of the manuscript.
Funding
This work was supported in part by the Ministry of Science and Technology of Republic of China under the contract number MOST 109-2221-E-019-052.
Conflicts of Interest
The authors declare that they have no conflict of interest.
Ethical Approval
This article does not contain any studies with human participants or animals performed by the author.
References
- Srinivasan, U.; Datta, G.; Hons, M.S.; Hons, B.E. Personal health record (PHR) in a talisman: An approach to providing continuity of care in developing countries using existing social customs. In Proceedings of the 2007 9th International Conference on e-Health Networking, Application and Services, Taipei, Taiwan, 19–22 June 2007; pp. 277–279. [Google Scholar]
- Puustjärvi, J.; Puustjärvi, L. Exploiting personal health records in automating information therapy. In Proceedings of the 2010 Second International Conference on eHealth, Telemedicine, and Social Medicine, St. Maarten, The Netherlands, 10–16 February 2010; pp. 100–105. [Google Scholar]
- Azhagiri, M.; Amrita, R.; Aparna, R.; Jashmitha, B. Secured electronic health record management system. In Proceedings of the 2018 3rd International Conference on Communication and Electronics Systems (ICCES), Coimbatore, India, 15–16 October 2018; pp. 915–919. [Google Scholar]
- Zhu, H.; Hou, M. Research on an electronic medical record system based on the Internet. In Proceedings of the 2018 2nd International Conference on Data Science and Business Analytics (ICDSBA), Changsha, China, 21–23 September 2018; pp. 537–540. [Google Scholar]
- Yang, W.; Chen, J.; Chen, Y. An electronic medical record management system based on smart contracts. In Proceedings of the 2019 Twelfth International Conference on Ubi-Media Computing (Ubi-Media), Bali, Indonesia, 6–9 August 2019; pp. 220–223. [Google Scholar]
- Blaze, M.; Bleumer, G.; Strauss, M. Divertible Protocols and Atomic Proxy Cryptography. In Advances in Cryptology—EUROCRYPT’98; Springer: Berlin/Heidelberg, Germnay, 1998; pp. 127–144. [Google Scholar]
- Ateniese, G.; Fu, K.; Green, M.; Hohenberger, S. Improved proxy re-encryption schemes with applications to secure distributed storage. In Proceedings of the 10th Network and Distributed System Security Symposium (NDSS’05), San Diego, CA, USA, 10–13 February 2005; pp. 29–43. [Google Scholar]
- Canetti, R.; Hohenberger, S. Chosen-ciphertext secure proxy re-encryption. In Proceedings of the 14th ACM Conference on Computer and Communications Security (CCS 2007), Alexandria, VA, USA, 29 October–2 November 2007; pp. 185–194. [Google Scholar]
- Wang, X.A.; Xhafa, F.; Zheng, Z.; Nie, J. Identity based proxy re-encryption scheme (IBPRE+) for secure cloud data sharing. In Proceedings of the 2016 International Conference on Intelligent Networking and Collaborative Systems (INCoS), Ostrava, Czech Republic, 7–9 September 2016; pp. 44–48. [Google Scholar]
- Zeng, P.; Choo, K.R. A new kind of conditional proxy re-encryption for secure cloud storage. IEEE Access 2018, 6, 70017–70024. [Google Scholar] [CrossRef]
- Talmy, A.; Dobzinski, O. Abuse freedom in access control schemes. In Proceedings of the 20th International Conference on Advanced Information Networking and Applications (AINA 2006), Vienna, Austria, 18–20 April 2006; pp. 77–86. [Google Scholar]
- Ateniese, G.; Fu, K.; Green, M.; Hohenberger, S. Improved proxy re-encryption schemes with applications to secure distributed storage. ACM Trans. Inf. Syst. Secur. 2006, 9, 1–30. [Google Scholar] [CrossRef]
- Chiu, Y.P.; Lei, C.L.; Huang, C.Y. Secure multicast using proxy encryption. In Proceedings of the 7th International Conference on Information and Communications Security (ICICS), Beijing, China, 10–13 December 2005; pp. 280–290. [Google Scholar]
- Khurana, H.; Hahm, H.S. Certified mailing lists. In Proceedings of the ACM Symposium on Communication, Information, Computer and Communication Security (ASIACCS’06), Taipei, Taiwan, 21 March 2006; pp. 46–58. [Google Scholar]
- Khurana, H.; Slagell, A.; Bonilla, R. Sels: A secure e-mail list service. In Proceedings of the ACM Symposium on Applied Computing (SAC’05), Santa Fe, NM, USA, 13–17 March 2005; pp. 306–313. [Google Scholar]
- Taban, G.; Cárdenas, A.A.; Gligor, V.D. Towards a secure and interoperable DRM architecture. In Proceedings of the 6th ACM Workshop on Digital Rights Management, Alexandria, VA, USA, 30 October–3 November 2006; pp. 69–78. [Google Scholar]
- Boneh, D.; Crescenzo, G.D.; Ostrovsky, R.; Persiano, G. Public key encryption with keyword search. In Advances in Cryptology—EUROCRYPT 2004; Springer: Berlin/Heidelberg, Germnay, 2004; pp. 506–522. [Google Scholar]
- Cui, X.H.; Wan, Z.; Deng, R.; Wang, G.; Li, Y. Efficient and expressive keyword search over encrypted data in cloud. IEEE Trans. Dependable Secur. Comput. 2016, 15, 409–422. [Google Scholar] [CrossRef]
- Chen, R.; Mu, Y.; Yang, G.; Guo, F.; Huang, X.; Wang, X.; Wang, Y. Server-aided public key encryption with keyword search. IEEE Trans. Inf. Forensics Secur. 2016, 11, 2833–2842. [Google Scholar] [CrossRef]
- Sahai, A.; Waters, B. Fuzzy identity-based encryption. In Advances in Cryptology—EUROCRYPT 2005; Springer: Berlin/Heidelberg, Germany, 2005; pp. 457–473. [Google Scholar]
- Bethencourt, J.; Sahai, A.; Waters, B. Ciphertext-policy attribute based encryption. In Proceedings of the IEEE Symposium on Security and Privacy (SP’07), Berkeley, CA, USA, 20–23 May 2007; pp. 321–334. [Google Scholar]
- Goyal, V.; Pandey, O.; Sahai, A.; Waters, B. Attribute-based encryption for fine-grained access control of encrypted data. In Proceedings of the 12th ACM Conference on Computer and Communications Security (CCS’06), Taipei, Taiwan, 22 March 2006; pp. 89–98. [Google Scholar]
- Lin, G.; Hong, H.; Sun, Z. A collaborative key management protocol in ciphertext policy attribute-based encryption for cloud data sharing. IEEE Access 2017, 5, 9464–9475. [Google Scholar] [CrossRef]
- Sethia, D.; Shakya, A.; Aggarwal, R.; Bhayana, S. Constant size CP-ABE with Scalable revocation for resource-constrained IoT devices. In Proceedings of the 2019 IEEE 10th Annual Ubiquitous Computing, Electronics & Mobile Communication Conference (UEMCON), New York City, NY, USA, 10–12 October 2019; pp. 0951–0957. [Google Scholar]
- Zhou, S.; Chen, G.; Huang, G.; Shi, J.; Kong, T. Research on multi-authority CP-ABE access control model in multicloud. China Commun. 2020, 17, 220–233. [Google Scholar] [CrossRef]
- Wang, C.; Li, W.; Li, Y.; Xu, X. A ciphertext-policy attribute-based encryption scheme supporting keyword search function. In Proceedings of the International Symposium on Cyberspace Safety and Security (CSS 2013), Zhangjiajie, China, 13–15 November 2013; pp. 377–386. [Google Scholar]
- Barreto, P.; Naehrig, M. Pairing-friendly elliptic curves of prime order. In Proceedings of the 12th International Workshop on Selected Areas in Cryptography, Kingston, ON, Canada, 11–12 August 2005; pp. 319–331. [Google Scholar]
- Miller, V. The weil pairing and its efficient calculation. J. Cryptol. 2004, 17, 235–261. [Google Scholar] [CrossRef]
- Zhao, J.; Gao, H. LSSS matrix-based attribute-based encryption on lattices. In Proceedings of the 2017 13th International Conference on Computational Intelligence and Security (CIS), Hong Kong, China, 15–18 December 2017; pp. 253–257. [Google Scholar]
- Agrawal, S.; Chase, M. FAME: FAST attribute-based message encryption. In Proceedings of the 2017 ACM SIGSAC Conference on Computer and Communications Security (CSS’17), Dallas, TX, USA, 30 October–3 November 2017; pp. 665–682. [Google Scholar]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).