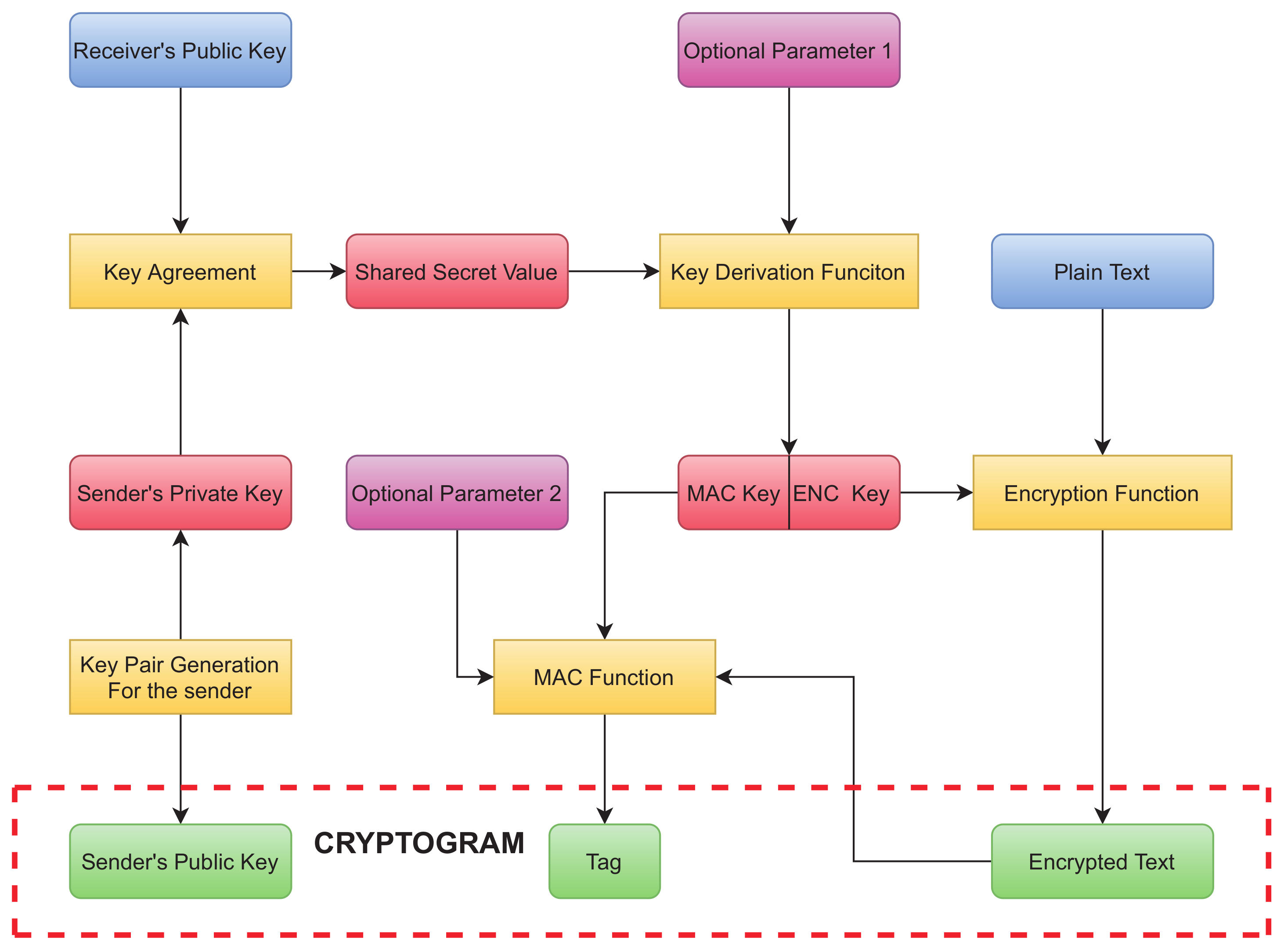
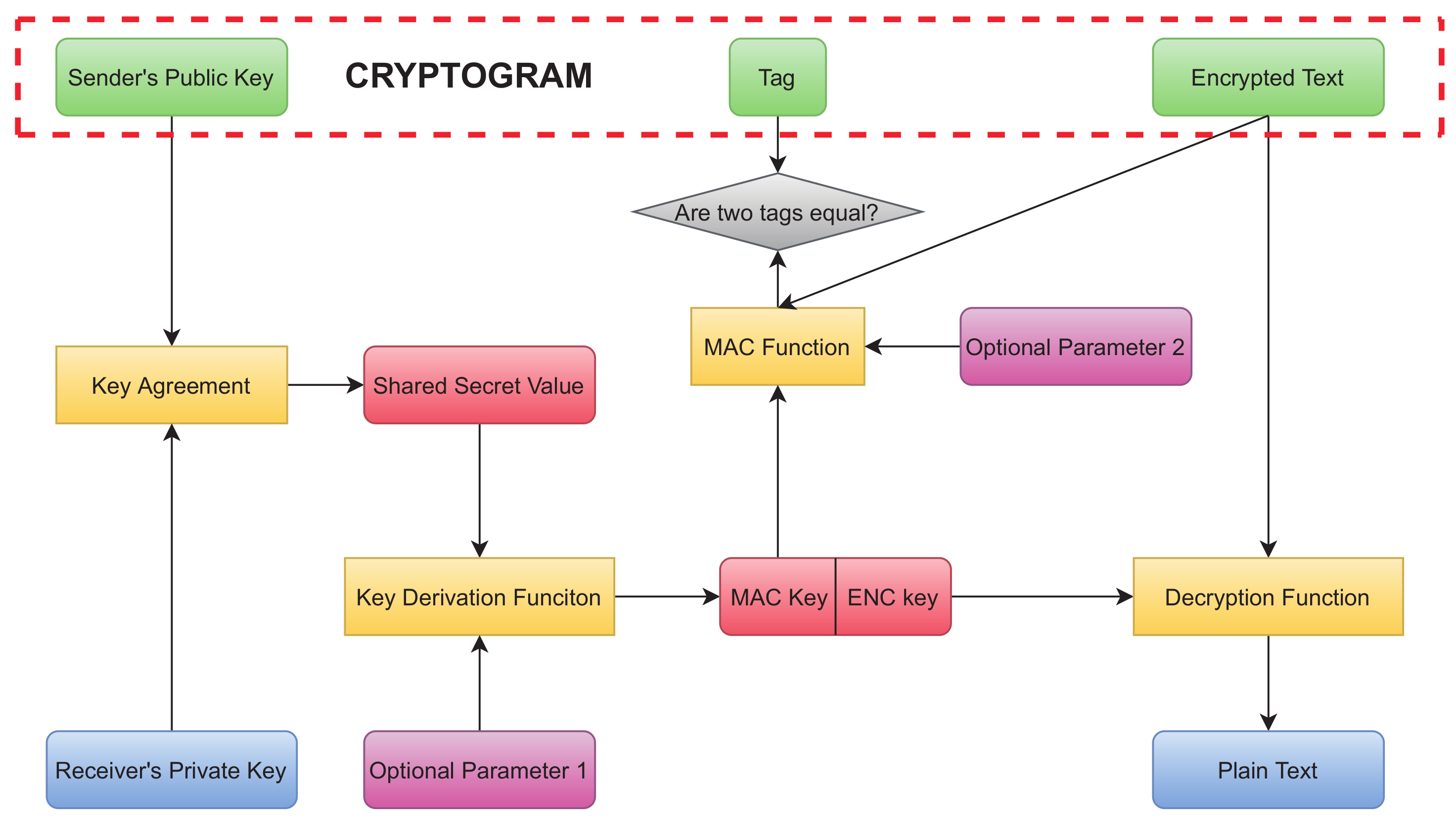
1. Introduction
With the sharp growth in network evolution, the communication of multimedia information (i.e., images, audio, and video) over various networks has been effectively facilitated. However, most of the transmission processes for these contents have been done through an unsecure network, which means there is potential risk for the loss of information or the interception (i.e., illegal copying and distribution) or even malicious tampering of this information [
1,
2]. Therefore, the security of multimedia information, especially in the field of big data and cloud systems, has raised increasing concern [
3,
4]. Traditional encryption methods include the implementation of the data encryption standard (DES) and advance encryption standard (AES) algorithm. Though the methods mentioned above play a vital role in encryption, the inherent features of the image like the strong correlation of pixels and a large amount of information suggest these preliminary technologies are not suitable. On the basis of the sensitivity to initial situations, ergodicity, mixed characteristics, simple analytic description, and high complex behavior of the chaotic system, quantities of schemes based on hyperchaotic systems have been reported from different researchers.
In 1989, Matthew first proposed a scheme which implemented the chaotic system into the encryption for the text [
5]. After Fridrich [
6] firstly applied a chaotic system to the digital picture encryption and divided the procedure of encryption into two main parts in 1998, a diversity of algorithms and methods have been proposed based on the two vital process mentioned above: permutation and diffusion. Some of these methods are based on pixel-level permutation, and the nonequilibrium system with chaos was applied into the encryption by constructing some S-boxes [
7]. Zhang et al. [
8] improved the chaotic map with delay and cascade. Meanwhile, bit-level permutation has been applied to some other algorithms. In [
9], bits of the pixel were segmented into an odd group and an even group, and after that, the chaotic image was calculated by randomly swapping the two groups. A bit-level cyclic shift method was applied in [
10] to enhance the effects of the permutation for the plain image. However, Zhou et al. [
11] mentioned that when adopting nonlinear transformation directly, due to the narrow interval and unrich nonlinear dynamic behavior, some image encryption algorithms based on low-dimensional chaos systems bear security risks. To overcome this vital shortcoming, the hyperchaotic system was designed and realized for image encryption.
Compared with chaotic system, the hyperchaotic system has stronger randomness that is more suitable for image encryption. In [
12], because of the complicated dynamic properties, a four-dimensional (4D) hyperchaotic system was proposed to generate the key stream and control the further rotation and shift for rows and columns of each component of the plain color image. Zhu et al. [
13] used a 2-dimensional compound homogeneous hyperchaotic system (CHHCS) in the process of permutation to obtain good effects. However, by using the chosen-plaintext attack, some encrypted images based on hyperchaotic system could still be successfully converted into the corresponding plain image without any error [
14,
15]. In order to solve this weakness, plaintext was correlated with the chaotic key stream derived from the hyperchaotic sequences when generating the final encryption key stream, which enhanced the security under the chosen-plaintext attack [
16]. However, with the improvement of security, the problem of time efficiency has also been exposed.
Over the last several decades, there has been a sharp increase in the interest in promoting the time efficiency of hyperchaotic image encryption. By using the chaotic shift transform (CST), Liu et al. [
17] combined the processes of permutation and diffusion into one stage, which effectively enhanced the time efficiency. As an important part of the attempt to improve the time efficiency, block shuffling has raised much more attention in recent studies. The author of [
18] presented the algorithm where the image was divided into 4 blocks, and after the replacement according to the pseudorandom sequences derived from the combination chaotic system, these subblocks are combined together. Another scheme proposed in [
19] has divided each color constituent into the same sized blocks with the application of the substitution based on the paired S-box.
Moreover, the consideration of permutation on the bit-level instead of the perspectives of pixel-level has also grown rapidly. To reduce the redundancies implied by the Fridrich’s structure, a novel circular inter- and intrapixel bit-level permutation strategy was mentioned in [
20]. Aqeel-ur-Rehman et al. [
21] proposed a 2-bit-level pixel substitution by using DNA and chaos. However, there are vital flaws for the methods mentioned above: (1) Although the use of block surely reduced the time redundancy, all these referred block sizes are not determined by the property of the image. (2) All the bits of each pixel were treated equally without the consideration of the discrepancy of the quantity of information they respectively contained.
Nevertheless, though these proposed schemes proved to be of high security and efficiency in the process of image encryption, there is one thing they certainly have in common: all these schemes are symmetric. This significant attribute results in one inevitable flaw: the important and sensitive key must be transmitted through a dedicated secure channel to prevent eavesdropping. That means if the key is disclosed, security for further communication is impossible [
22].
In view of the shortcomings above, we propose a novel asymmetric hyperchaotic image encryption scheme based on elliptic curve cryptography (ECC). The author of [
23] illustrated the good time efficiency and security of ECC theoretically, and Rajdeep et al. [
24] made an analysis of various encryption systems, in which ECC shows its excellent characteristics. The advantages of this scheme are as follows: (1) Based on the high security of ECC, sensitive data related to the initial parameters can be transmitted with the cipher image through the public channels. (2) With the application of block-level bit permutation, after the permutation process, because the permutated planes are bit-level planes, the place of the pixels in the image and the values of each pixel are both therefore changed, which means better time efficiency of the encryption with the even better effects. (3) During the diffusion process, the same hyperchaotic sequences used in permutation significantly reduces the complexity of the algorithm and provides better storage efficiency.
The remainder of the paper is arranged as follows. In
Section 2, elliptic curve integrate encrypt scheme (ECIES) for the encryption of the sensitive data is applied and the hyperchaotic system is briefly introduced. In
Section 3, we described this novel asymmetric hyperchaotic image encryption scheme based on ECC in detail, followed by the experimental simulation in
Section 4. Finally, the conclusions are presented in
Section 5.
3. The Asymmetric Hyperchaotic Image Encryption Scheme
In this scheme, we suppose that the sender wants to transmit a confidential image through the public channel to the receiver, and the whole procedure is summarized as follow. First, the sender encrypts the plaintext image using hash value derived from the original image, and the cipher image is obtained through the permutation and diffusion. Then, the received public key from the receiver is used to encrypt the hash value by ECIES, followed by the process of combining it with encrypted images into encrypted packet. After that, the encrypted packet is transferred to the receiver through the public channel. When the receiver gets the encrypted data packet, the decrypted hash value is obtained by the use of the private key and ECIES. Finally, the receiver can use the hash value and the decryption scheme to extract the corresponding plaintext image. The whole process of the scheme is shown in
Figure 3.
As for the encryption algorithm, it can be generally divided into two components: the permutation and the diffusion. For the permutation step, not only has the place of each pixel in the image changed, but with the separation and the combination of the bits in each pixel, the value of each pixel has also changed, which demonstrates the additional effects of diffusion. Moreover, with the consideration of the amount of information that the different bits in the same pixel contain, the corresponding divided bit-level planes have also been parted into the different sized block units for the following step of permutating, making both time efficiency and the strength of security strongly enhanced.
In the process of diffusion, for the advanced utilization ratio of the chaotic sequences, the same sequences applied in permutation are reused. In a two-dimensional image, the method proposed in [
31] is applied to augment the complexity of the correlation between different pixels. It is started from the bottom to the top and from the right to the left, and after a round of diffusion, for each pixel, it is related with two proximal pixels in the downward and rightward direction.
The specific procedure of the algorithm is displayed in
Figure 4, and the part in the green frame is the novel different-sized blocks permutation proposed in this paper.
3.1. The Formation of the Key and the Hyperchaotic Sequences
Before the generation of the hyperchaotic sequences by using the LF-NCHM, the initial values were generated based on the hash value derived from the plaintext image. To ensure security, we used the SHA-256 algorithm to obtain the dynamic hash which is related to the plaintext image, which indicates that even the most trivial alteration would still result in a huge difference for the result. On the basis of the dynamic hash, the initial conditions with extremely strong sensitivity were then determined. After that, these conditions were treated as the input of the LF-NCHM for the construction of the hyperchaotic sequences used in further operations. The specific steps are as follows:
Generate the hash value by using the plaintext image, then split the obtained hash into 32 pieces, like , and each of these pieces contains 8 bits of data related to the plaintext image.
With the application of the formulas shown in (
2), calculate the intermediate values
, and the inputs of the formula are
from Step 1.
Calculate the initial conditions
,
,
, and
in accordance with the
, and the equations applied are displayed in (
3).
In the formula, the , , , and are the initial values given in advance. For the algorithm in this scheme, these conditions are designated here: = 3.1, = 4.4, = 0.3, and = 0.5.
Take the obtained initial values as the input of LF-NCHM to generate the hyperchaotic sequences with the length needed.
3.2. The Permutation Process Based on Different Sized Blocks
In the permutation process, the plaintext image P with the size will firstly be converted into 5 planes on bit-level from the original image with the pixel-level format. The contents of the plane set are a “combined” plane in which all components are the combination of the 1st–4th bit of the pixels in the original image and four planes representing the 5th–8th bit of the pixels, respectively. After converting the image for each content in the set, it would be parted into smaller blocks when it contained more information compared with other planes. More specifically, in this chapter, the plane which is composed of the 8th bit for all the pixels will be divided into blocks, and for the 7th, 6th, and 5th bit, the corresponding plane will be divided with the size of , , and , respectively. For the “combined” plane in the set, because the four bits in this plane contain less information than others in the set, the block size will be to improve the operating speed. Next, the planes are shuffled like the matrixes based on the unit of the blocks divided before, and the distance for shuffling is mainly determined by the hyperchaotic sequences. Finally, combine these 5 permutated planes together and convert into the pixel-level image. Through this novel different sized block permutation, the image experienced both permutation and diffusion simultaneously.
The concrete steps are as follows:
Convert the original plaintext image into 5 different planes, the first plane is the combination of the 1st–4th bits of each pixel in the plaintext image, and the latter 4 planes are made of the corresponding 5th–8th bits respectively. One example for the regulation referred to before is presented in
Figure 5.
Divide these planes into the different sized blocks according to the amount of information that each bit included. In this chapter, the plane of the 8th bit of the plane which contains more information than any other bits in every pixel, so the size of block is
. Based on this consideration, when the length and width of the planes are both the multiples of 16, the 7th, 6th, and 5th plane are divided into the different blocks with the size of
,
, and
, respectively. Otherwise, the planes will be added by zeros. Finally, for the “combined” plane mentioned before, due to it containing the least amount of information,
is the proper block size in order to enhance the time efficiency. The specific process of the division for an example applied with the
size is displayed in
Figure 6.
To ensure the randomness and the relation with the plaintext image, the hyperchaotic sequences generated before are used to determine the distance of the shuffling operation. Firstly, to avoid the insecurity of the over repeated usage of the sequences, the formula (
4) for calculating the shifting displacement is used.
where the indexRow and the indexCol are the numbers of the rows and the columns for the amount of the blocks. The rowChao and colChao are two obtained hyperchaotic sequences, the n means the index of the present column or the row, and the floor(x) obtains the largest integer which is less than or equal to x.
After the value of the migration distance is determined, the shuffling process is as follows: all the rows of the matrix after division will shift in turn, first according to the distance calculated in advance, then the columns will also shift in accordance with their migration distance analogously. An example to interpret the process of shuffling based on the matrix in
Figure 6 is shown in
Figure 7.
Combine all 5 planes after permutation into one pixel-level image PM with the size , which is essentially the inverted process of Step 1 essentially. When it is done, the operation of permutation is finished.
3.3. The Diffusion Process
To reduce the correlation between the neighboring pixels in the image, it is necessary to take the diffusion process. For the diffusion process, there are two major categories: block diffusion and the one based on the pixel-by-pixel mode. For the algorithm proposed in this article, we adopt a one-round operation of the pixel-by-pixel diffusion. The operation is started from the pixel located in the lower right corner of the two-dimensional image, end up with the pixel of the upper left corner of the image. In the whole operation, the spread process is from the botom to the top, and from the right to the left, which means after the present pixel is relevant to its lower and right neighbors. The details of the operation based on [
33] are as follows:
With the generation of the hyperchaotic sequences, the new subsequence for the usage of the diffusion process will be intercepted from one of the obtained sequences. In this article, the chosen sequence for interception is x(i), and a subsequence was intercepted from the x(i). After that, the subsequence x(i) was reshaped into a two-dimensional sequence x(i, j) with the size .
As the input of the diffusion process, the permutated image PM(i, j) was treated through this subprocess: for each pixel in the permutated image, the relation with the right and lower adjacent pixels was built. The final product after the diffusion is the cipher image C(i, j). The specific algorithm is shown in Algorithm 1.
| Algorithm 1 The process of diffusion |
- 1:
fordo - 2:
for do - 3:
if then - 4:
C(i,j) = PM(i,j)⨁floor(x(i,j)×255) - 5:
else if then - 6:
= PM(i,j)⨁C(i,j+1) - 7:
C(i,j) = ⨁floor(x(i,j)×255) - 8:
else if then - 9:
= PM(i,j)⨁C(i+1,j) - 10:
C(i,j) = ⨁floor(x(i,j)×255) - 11:
else - 12:
= PM(i,j)⨁C(i,j+1) - 13:
= ⨁C(i+1,j) - 14:
C(i,j) = ⨁floor(x(i,j)×255) - 15:
end if - 16:
end for - 17:
end for
|
In this part, an example with four pixels was shown to provide the convenience of the comprehension for the method elaborated above.
Figure 8 shows the steps of this operation:
3.4. The Formation of the Encrypted Data Packet
After the encryption process for the plaintext image, the hash value that generates the hyperchaotic system was encrypted through the ECIES, with the public key received from the receiver. The encrypted hash and image were combined together to form an encrypted data packet (PKT) for the final transmission. The presence of the PKT signifies the end of the whole encryption operation.
3.5. Decryption Process
In general, the decryption process of the scheme proposed is basically the reverse of the encryption. The input for the decryption process is the receiver’s private key u and the PKT.
Split the PKT into the encrypted hash and the encrypted image.
Use the private key u to decrypt the encrypted hash.
Use the decrypted hash from the last step to generate the hyperchaotic sequences x(i) and y(i), and reshape the x(i) into the two-dimensional sequence x(i, j).
Take the inverse diffusion process to obtained the permutated-only image PM from the cipher image C and the use of the sequence x(i, j). The concrete process is as follows:
With the combination of two sequences x(i) and y(i), take the reversed operation of the permutation process to obtain five planes which are the divided parts of the original image.
Finally, build them all up into one thing and restore it to the decrypted image P, which size is as the same of the original plaintext image.
Figure 9 reveals the flow chart of the decryption procedure.
5. Conclusions
In this paper, a novel asymmetric hyperchaotic image encryption scheme based on elliptic curve cryptography was proposed. To avoid public channel attacks, in accordance with good speed and security, ECC was used to encrypt sensitive data related with the initial parameters which generated the hyperchaotic sequence.
For the enhancement of time efficiency, in permutation the plain image was firstly divided into five planes according to the amount of information contained in different bits: the combination of the low 4 bits, and the other four planes of high 4 bits. After that, the corresponding rules of block partition were adopted for different planes: smaller sized blocks for the plane contained more information than others. This was followed by the permutation in accordance with the hyperchaotic sequences, where these partied blocks were regarded as the basic units. In the process of diffusion, for the improvement of simplicity of the algorithm, the hyperchaotic sequence used in permutation was applied in diffusion. For the pixels in the two-dimensional plane, we started from the bottom right corner, right to left, bottom to top, and after this procedure, pixels were generally related to the pixels in the previous two directions, which results in more complexity for the correlation.
The experimental results demonstrated that this scheme could resist public channel attacks, statistical analysis attacks, and chosen-plaintext attacks with advantages. According to the data from the analysis of encryption speed (throughput and the number of machine cycles consumed), the scheme performed better speed compared with some bit-level based scheme and showed more security than a various of block shuffling methods. The current version of the algorithm is implemented on the basis of the MATLAB platform, and to improve the time efficiency, the FPGA version will be considered soon for further progress.