Abstract
This paper focuses on electromagnetic information security in communication systems. Classical correlation electromagnetic analysis (CEMA) is known as a powerful way to recover the cryptographic algorithm’s key. In the classical method, only one byte of the key is used while the other bytes are considered as noise, which not only reduces the efficiency but also is a waste of information. In order to take full advantage of useful information, multiple bytes of the key are used. We transform the key into a multidimensional form, and each byte of the key is considered as a dimension. The problem of the right key searching is transformed into the problem of optimizing correlation coefficients of key candidates. The particle swarm optimization (PSO) algorithm is particularly more suited to solve the optimization problems with high dimension and complex structure. In this paper, we applied the PSO algorithm into CEMA to solve multidimensional problems, and we also add a mutation operator to the optimization algorithm to improve the result. Here, we have proposed a multibyte correlation electromagnetic analysis based on particle swarm optimization. We verified our method on a universal test board that is designed for research and development on hardware security. We implemented the Advanced Encryption Standard (AES) cryptographic algorithm on the test board. Experimental results have shown that our method outperforms the classical method; it achieves approximately 13.72% improvement for the corresponding case.
1. Introduction
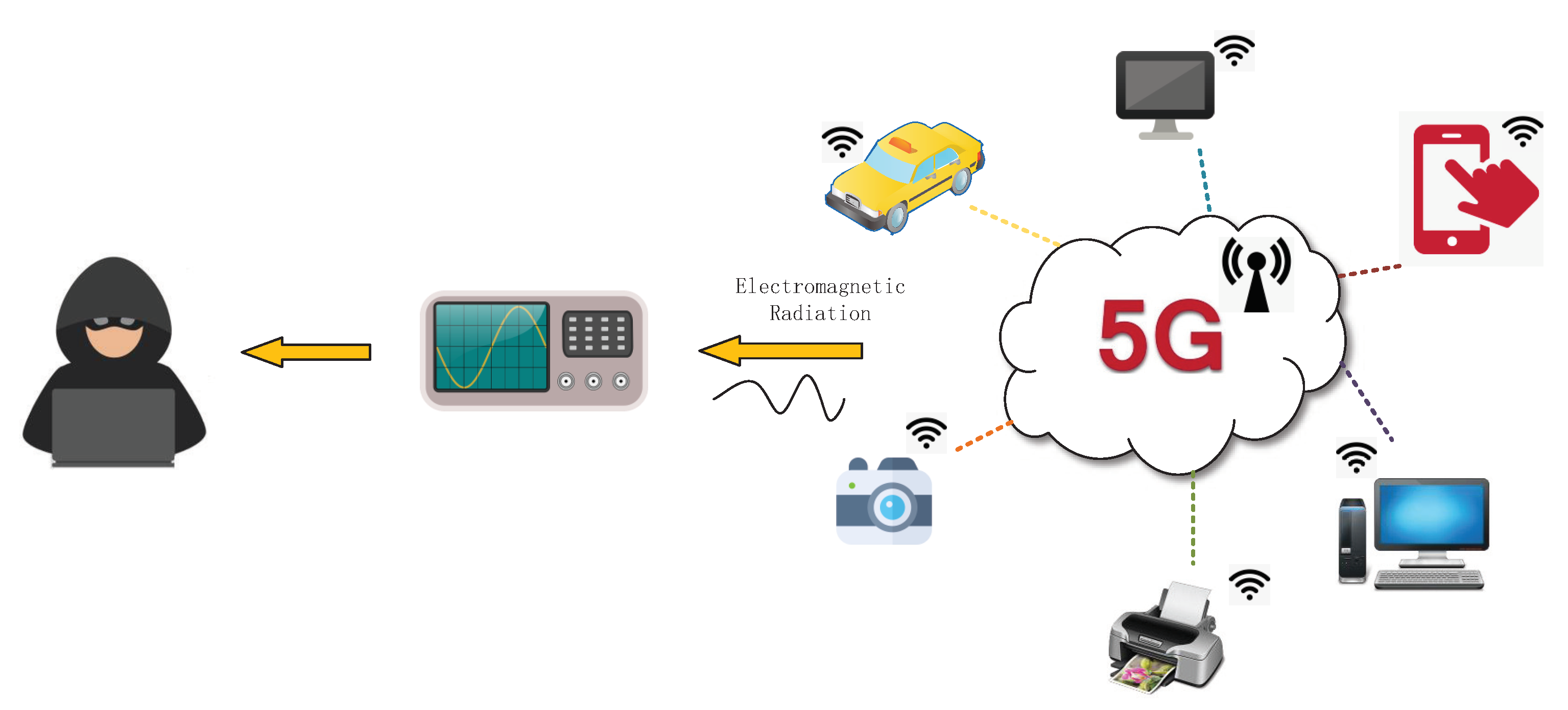
With the rapid development of 5th generation wireless systems (5G), more and more intelligent devices are connected to the Internet. At the same time, information security in communication process is being paid more and more attention. Many modern devices are used in people’s lives, such as mobile phones, personal computers, smart TVs, sensor networks, cryptographic devices, and many other things, just as shown in Figure 1. It is well known that the electromagnetic (EM) signals will be radiated unintentionally when data are processing in these devices. These unintentional electromagnetic radiation could be used to recover the important information, even if they do not exceed the limits of the electromagnetic compatibility (EMC) regulation [1], which poses a threat to the information security. The U.S. National Security Agency has focused on the classified TEMPEST (Telecommunications Electronics Materials Protected from Emanating Spurious Transmissions) program for many years to prevent important information from leaking through this unintentional electromagnetic radiation.
Figure 1.
Information security in communication systems.
One of the most successful techniques for exploiting unintentional electromagnetic radiation is the electromagnetic analysis. A variety of research has been devoted to unintentional electromagnetic radiation in recent years. The screen content was reconstructed by analyzing the unintentional electromagnetic signal from video graphics adapter (VGA) connector when a document or a video was displayed on the liquid-crystal display (LCD) [2]. Remote visualization for screen displays of various mobile devices used in public spaces via electromagnetic waves was reproduced in [3]. The echo state network (ESN) was used to extract the characteristics of the collected electromagnetic signals from a mobile phone and then the support vector machine (SVM) method was used to pattern identifying the characteristics of signals in [4]. The printed image can be easily reconstructed using leaked electromagnetic radiation that came from a laser printer [5]. Leaked electromagnetic radiation from the cable of the USB keyboard was measured by using a field probe and recovery of the data was performed through it [6]. A display image was reconstructed based on the measured time changes in the electromagnetic radiation carrying the signals for drawing the display on touch screen devices such as tablets and smart phones [7]. The electromagnetic radiation signal observation method is also applicable to cryptographic devices. Secret signing keys of Elliptic Curve Digital Signature Algorithm (ECDSA) from iOS devices were extracted fully by unintentional electromagnetic emission [8]. A successful key recovery attack on commercially available contactless Radio Frequency Identification Devices (RFID) based on the Data Encryption Standard (DES) or Triple-DES (3DES) cipher was shown in [9]. All of this research demonstrates that sensitive information can be recovered by unintentional electromagnetic radiation.
In this paper, on the field of electromagnetic information security, we study the threats of information leakage through electromagnetic radiation that can be used to compromise commercial devices and equipment. The rest of the paper is organized as follows. The related works are introduced in Section 2. In Section 3, we introduce the basic knowledge used in our method, including the AES cryptographic algorithm, differential electromagnetic analysis, correlation electromagnetic analysis, and the PSO algorithm. In Section 3, we describe multibyte correlation electromagnetic analysis based on particle swarm optimization in detail. In Section 4, we present our experimental platform and show the experimental results. Finally, we conclude the paper in Section 5.
2. Related Works
Many modern devices are used to implement cryptographic algorithms to protect information in the communication process. Modern cryptographic devices generally remain the secret key in hardware regardless of whether the algorithm is public or not. In order to prevent information from being stolen illegally during network communication, information is generally encrypted before being sent. Cryptographic algorithms or secret keys processed inside cryptographic hardware devices can be inferred by unintentional electromagnetic radiation. Thus, electromagnetic analysis of cryptographic devices has been given more importance in recent years. Non-blinded RSA keys were extracted within seconds using a nonintrusive measurement of electromagnetic emanations from laptop computers [10]. By measuring the target PC’s electromagnetic emanations, the attacker extracted the secret decryption key within seconds, from a target located in an adjacent room across a wall [11]. Attacking the Field Programmable Gate Array (FPGA) implementation of Advanced Encryption Standard (AES) algorithm where all bytes were processed in parallel using differential electromagnetic analysis (DEMA) was shown in [12]. A secret key attack based on correlation electromagnetic analysis (CEMA) was recovered successfully in [13,14,15]. A novel two-stage countermeasure to prevent CEMA was shown in [16]. SVM was used to classify arithmetic operations by electromagnetic leakage in [17]. This way can be considered as a type of template analysis (TA). Simple electromagnetic analysis (SEMA) and DEMA were used to attack DES in a manner to extract information from electromagnetic radiation [18,19]. A multi-objective electromagnetic analysis based on genetic algorithm to recover the AES encryption algorithm’ secret key was proposed in [20]. Non-invasive electromagnetic analysis can be mainly divided into four categories: SEMA, DMEA, CEMA, and TA. For the SEMA method, the attacker deduces the secret key directly by observing the electromagnetic radiation traces. It is effective against asymmetric cryptography implementations in some cases. If the attacker has a strong understanding of the cryptographic device and the implementation of the cryptographic algorithm, only a few traces are needed to recover the secret key. Sometimes, SEMA does not provide enough information to deduce the secret key. Thus, other analytical methods were developed to recover the secret key such as DEMA, CEMA, and TA. Generally, the length of the cryptographic algorithm’s key is very long to ensure security, so the implementations are usually executed in blocks. It is very easy to consider the idea of ‘divide and conquer’, so only a single byte of the key is used when recovering the key. DEMA and CEMA are more complex and effective methods against symmetric cryptography implementation when the SEMA method fails. Additionally, unlike SEMA, DEMA and CEMA require less knowledge about the target device being attacked. TA is considered as the strongest form in an information theoretic sense. The premise of TA is that the attacker must have a copy of the target cryptographic device which may be impossible in some real scenarios. The TA method usually uses a single byte output to create templates. However, the strategy of ‘divide and conquer’ may lose information and efficiency because all bytes of the key contain information. A comparison of single-bit and multi-bit DPA for attacking AES-128 on an ATmega328P was shown in [21]. His work demonstrated that using multi-bit of a key byte can significantly reduce ghost peaks and allow for the recovery of a key with far fewer traces. Multiple bits were applied to linear regression and get a better result in [22]. Their works inspired us to start our research on multiple bytes electromagnetic analysis. In our previous work [23], we have demonstrated that we can use fewer electromagnetic traces by multiple bytes electromagnetic analysis when recovering secret keys. Thus, it is meaningful to explore multiple bytes to recover the key.
In addition, there is very little research that focuses on the PSO optimization algorithm to recover cryptographic devices’ key by electromagnetic radiation. The genetic algorithm has been applied to electromagnetic analysis in [20] to recover the secret key, but the genetic algorithm is a more complicated optimization algorithm. Compared with particle swarm optimization, there are more steps and more parameters in genetic algorithms, such as coding, selection, crossover, and mutation. The PSO algorithm is simplified and effective, which has had great achievements in various fields. A particle swarm optimization (PSO) algorithm was associated with ESN to pre-train some fixed weights values within the network, and experimental results showed obvious enhancement of ESN learning results [24]. An improved PSO algorithm was used to optimize the parameters of least squares support vector machines (LS-SVM) in order to construct an optimal LS-SVM classifier. The improved PSO algorithm can effectively improve the classification accuracy of LS-SVM [25]. An improved PSO called Selectively informed PSO (SIPSO) was used as a leak detection and localization method for liquid pipelines, which was shown to outperform the other global PSO algorithm and local PSO algorithm [26].
In this paper, combining the advantages of multiple bytes of the key and PSO algorithm, we propose a multibyte correlation electromagnetic analysis based on particle swarm optimization to recover the cryptographic devices’ key. The major contributions are summarized as follows:
- (1)
- Multiple bytes of the secret key are used in our method to take full advantage of available information.
- (2)
- We transform the key into multidimensional form, each byte of the key is considered as a dimension. Thus, each point in the coordinate is a key candidate, and we transform the problem of the right key searching into the problem of optimizing correlation coefficients of key candidates.
- (3)
- The PSO algorithm is particularly suited to solve the optimization problems with high dimensions and complex structure, so our method applied the PSO algorithm into the optimization process. In addition, we also add a mutation operator to the PSO algorithm to improve the result.
3. Preliminaries
3.1. Cryptographic Algorithm
AES [27] is a specification for the encryption of electronic data chosen by the National Institute of Standards and Technology (NIST) in 2001. It is based on a design principle known as a substitution–permutation network (SPN), and it is efficient in both software and hardware. AES is a symmetric block ciphers that takes plaintext in blocks of 128 bits and converts them to ciphertext using keys of 128, 192, and 256 bits. The AES-128 encryption algorithm consists of 10 rounds for 128-bit keys. Every round consists of four processing steps, except the last round, which omits the MixColumns step. The four processing steps are as follows:
SubBytes step: The SubBytes step offers the nonlinearity in the cryptographic algorithm. Every byte in the state array is substituted based on rules dictated by a predefined substitution table.
ShiftRows step: The ShiftRows step operates on the rows of the state; it cyclically shifts the bytes in every row by a certain offset except the first row.
MixColumns step: The MixColumns step operates on the column of the state, the four bytes of every column of the state are combined using an invertible linear transformation. The MixColumns function takes four bytes as input and outputs four bytes, where every input byte affects all four output bytes.
AddRoundKey step: In the AddRoundKey step, the subkey is added by combining every byte of the state with the corresponding byte of the subkey using bitwise XOR.
The AES-128 encryption algorithm takes plaintexts in blocks. The plaintexts are masked with a 128-bit fixed key before the first round. After four processing steps are done repeatedly, the plaintexts were converted to ciphertexts. The AES algorithm is considered secure in mathematical proofs, so it is a worldwide standard.
3.2. Particle Swarm Optimization (PSO)
PSO algorithm is a tool for solving optimization problems, which was created by Kennedy and Eberhart [28]. Its inspiration stems from the swarming behavior of birds. The PSO algorithm is a computational way that optimizes a problem by improving a population of candidate solutions, here called particles, and moving these particles around in the search space according to simple mathematical formulae over the particle’s position and velocity. Every particle’s movement is influenced by its local optimal position but is also guided toward the global optimal positions in the search space, which are updated as better positions are found by other particles. This is expected to move the particles’ swarm toward the global optimal solution. At every movement, the solutions are evaluated according to an objective function, which is also called “fitness function”. Generally, the main target is maximizing or minimizing the objective function. The standard PSO algorithm is very simple and easy to implement [29]. For a multidimensional problem of maximizing the objective function, f can be described as
where X is a D-dimensional vector, is the optimal solution after optimization. The ith particle is represented as , the velocity V also is a D-dimensional vector, and ith particle’s velocity is represented as . The particle’s position and velocity are updated by the mathematical Formulae (2) and (3). The new velocity is updated according to the following expression:
where is the ith particle’s velocity in the d dimension; and are the acceleration constants called cognitive coefficients and social coefficients, they are used to balance the displacements of particles toward the local or the global optimal position; and are independent random numbers in the interval (0, 1). The “personal best” of the ith particle indicates the best position obtained so far by that specific particle, is the global best position of the whole swarm. Generally, the value of is limited to the range for controlling roaming of the particle outside the search space.
The new location of ith particle is based on the following equation:
where is the ith particle’s position in the d dimension.
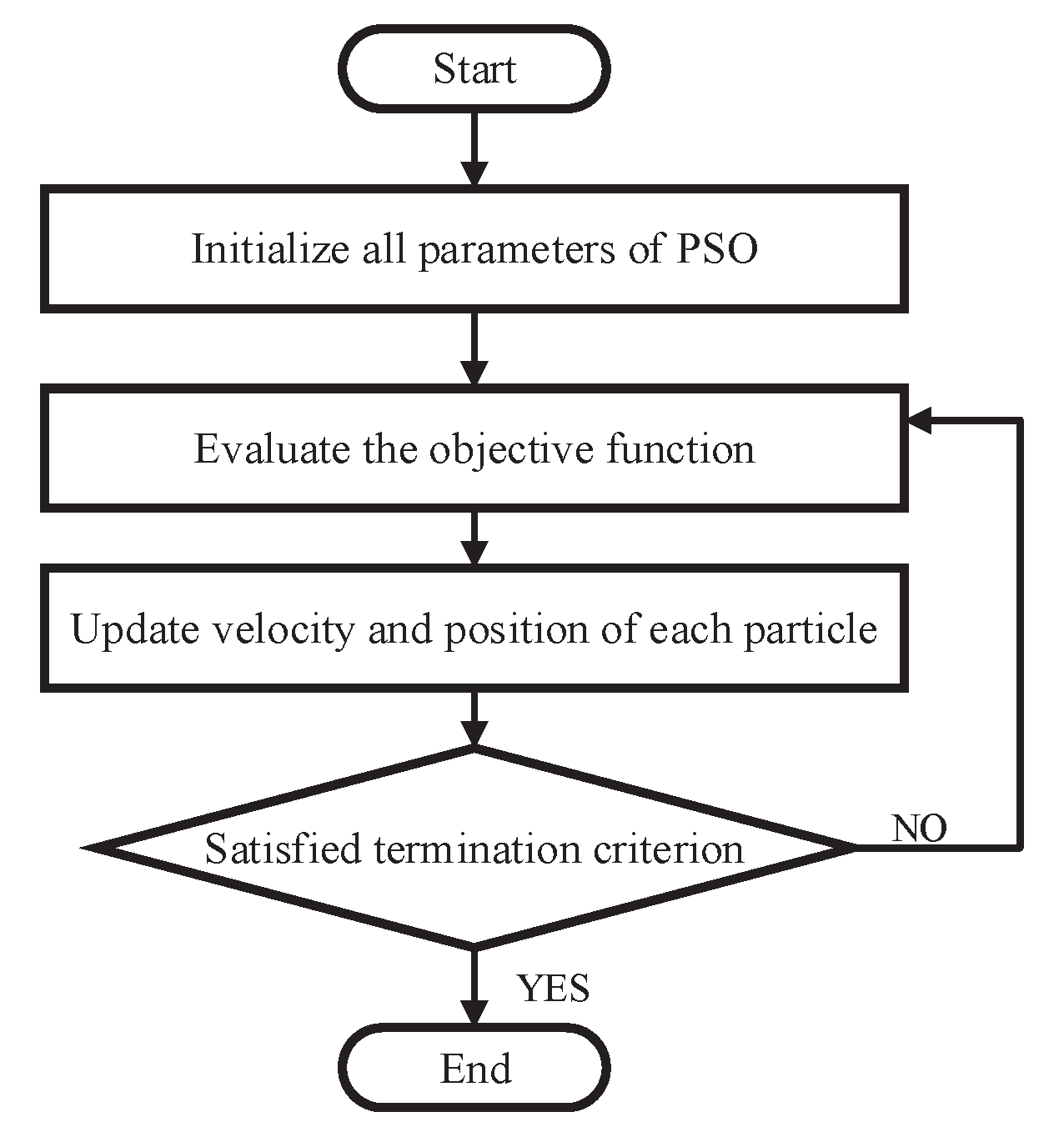
The PSO algorithm will stop when the maximal iterations are reached or the global optimal position of particle in the swarm cannot be improved further after sufficiently many iterations. Therefore, the PSO algorithm has shown its advantages and efficacy in solving complex optimization problems. The basic process of PSO algorithm is shown in Figure 2.
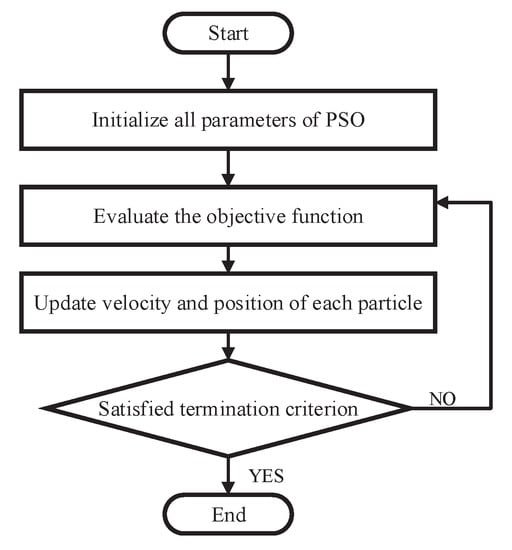
Figure 2.
The basic process of PSO.
3.3. Differential Electromagnetic Analysis (DEMA)
DEMA [30,31] is a classical method in electromagnetic analysis for analyzing electromagnetic consumption to identify data independent correlations. It uses electromagnetic signal traces T to determine whether a key byte guess is correct. The hypothesis is that small variations may be observed in an electromagnetic trace based on the output of the cryptographic algorithm. The main idea of this approach is to partition the electromagnetic traces into two sets, then compute the difference of the average of the two sets. If the two sets are uncorrelated, the difference is close to 0; if the two sets are correlated, the difference is a non-zero value. Given a sufficient number of traces, even tiny correlation can be found, no matter how much noise is in the traces, since the noise will effectively cancel out during the process of averaging. The rule of partition is based on the output of DEMA selection function . The function is defined as computing the b-bit value of the cryptographic algorithm intermediate for ciphertext . The attacker record m ciphertexts (or plaintexts) and m electromagnetic traces. Each trace contains k samples. The attacker computes a k-sample differential trace by finding the difference between the average of the traces for which is 1 and the average of the traces for which is 0. Thus, is the average over of the effect due to the value represented by the selection function on the electromagnetic radiation traces at point j:
where is the ith ciphertext, is the point j in ith electromagnetic traces.
3.4. Correlation Electromagnetic Analysis (CEMA)
CEMA is another classical method which adopts the idea of divide and conquer in electromagnetic analysis. Its main target is to find the correlation between the hypothetical electromagnetic leakage H and the actual electromagnetic leakage traces T of a cryptographic device. In our research, the hypothetical electromagnetic leakage H is assumed to be equal to the predicted subkey intermediate output’s Hamming distance (HD) W. Hamming distance from the current state h to next state s is given as
where represents Hamming weight, ⊕ is exclusive-OR operation. Usually, h and s have a functional relationship
where x is a byte of the key.
Pearson correlation coefficient is applied to predict the correlation between W and T. In a real scenario, a set of N electromagnetic traces T and N associated intermediate output’s Hamming distance W, under the uncorrelated noise assumption, the estimated correlation factor is given by the following formula:
where , is the ith intermediate output’s Hamming distance, the summations are taken over the N traces and the estimation has to be done at every time slot within the electromagnetic traces .
We can guess the key bytes and calculate for every candidate to find the right key. The value of is larger than others when the right key occurs.
4. PSO-Correlation Electromagnetic Analysis (PSO-CEMA)
In this section, we will describe our approach toward multiple bytes of the key and optimization algorithm in detail.
PSO-CEMA transforms the problem of the right key searching into the problem of optimizing correlation coefficients of key candidates. Each byte of the key is considered as a dimension, so each point in the coordinate is a key candidate. Recovering the right key means finding the best point in the multidimensional coordinate.
In order to take full advantage of useful information, all m bytes of the key are used. Hamming distance from the current state to the next state is given as
PSO is a heuristic and extremely simple algorithm that seems to be effective for optimizing a wide range of target functions or fitness functions. Its target is to find the best key point solution from the search space. The PSO algorithm can be summarized as follows:
Given the target function :
Find
where is the PSO’s fitness function or target function, , is the ith intermediate output’s Hamming distance.
The D-dimensional domain is the particle swarm search space which indicates that there are D bytes in a key, . The key is transformed into multidimensional form, . Each byte of the key is considered as a dimension . Thus, every key candidate solution is defined as a particle. The ith key candidate particle is represented as . The movement of follows Equation (3). The velocity for particle i is represented as and the velocity of the key candidate particle is updated in a new way according to the following equation:
where is the inertia weight and its value is non-negative.
Inertia weight plays an important role of balancing the performance of global optimization and local optimization. When is large, the performance of global optimization ability is good, but the performance of local search optimization ability is poor. Considering stronger search ability, inertia weight is modified to have a better convergence speed. The expression of the modified inertia weight is described as follows:
where and are the maximum inertia weight and the minimum inertia weight, is the current iteration number, and is the maximum number of iteration. In order to search the optimal key candidates, the particles move towards the best key point in the search space.
In addition, in order to have a global optimal value, we add a mutation operator to the PSO algorithm. The mutation operator is used to maintain diversity from one iteration of a population to the next. It is analogous to biological mutation. The mutation operator alters one or more position values in the multidimensional coordinate from its initial state. In mutation, the solution may change entirely from the previous solution. Hence, it will come to a better solution by using the mutation operator. The mutation operation will change some particle positions with a mutation probability to avoid local optimum. In our method, for selected particles with lower fitness values, they will change their current positions to other positions randomly to have better fitness values:
The length of cryptographic algorithms’ key is usually very long to ensure the safety. In other words, there are a large number of points in multidimensional coordinates. For example, AES is a symmetric encryption algorithm that can process data using cipher keys with 16 bytes. The range of one byte’s value is from 0 to 255, so there will be points in the multidimensional coordinate. It may need large numbers of initial particles to find the right key in the multidimensional coordinate or it may need large numbers of iterations to get the right key.
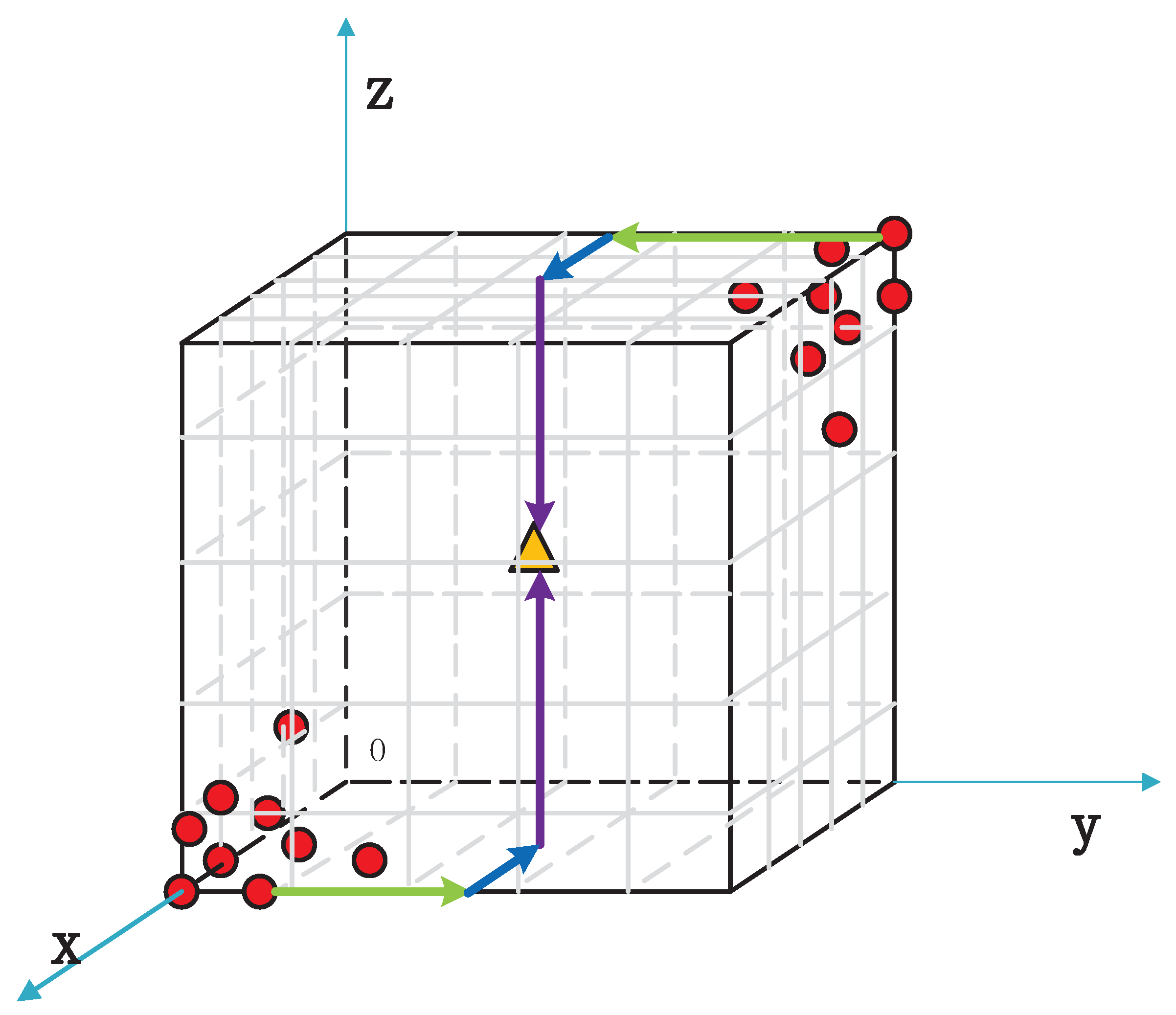
For simplicity, PSO is fixed a directional route to optimize the solution. Taking three-dimensional coordinates, for example, shown in Figure 3, red dots represent the initial particles’ positions, the yellow triangle represents the right key’s position, K(). The particle swarm’s directional route is the y-axis, x-axis, and the z-axis. In other words, particles will firstly find the best point K(0,,0) in K(0,y,0), then find the best point K(,0) in K(0) and then find the right point K() in K() ( are random variables range from 0 to 255). Thus, Hamming distance function in Equation (8) is revised:
where t indicates the current dimension number in a directional route, and m is the number of secret key byte. Here, is set to 0, and it also can be set to other values.
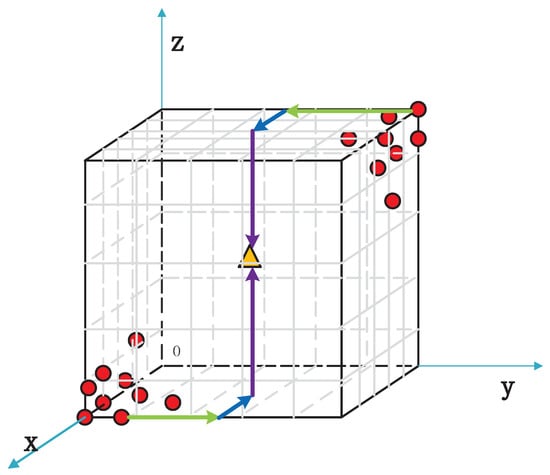
Figure 3.
The basic schematic diagram of the Particle Swarm Optimization—Correlation Electromagnetic Analysis.
PSO-CEMA can be summarized as Algorithm 1.
| Algorithm 1: PSO-CEMA |
 |
5. Experimental Results
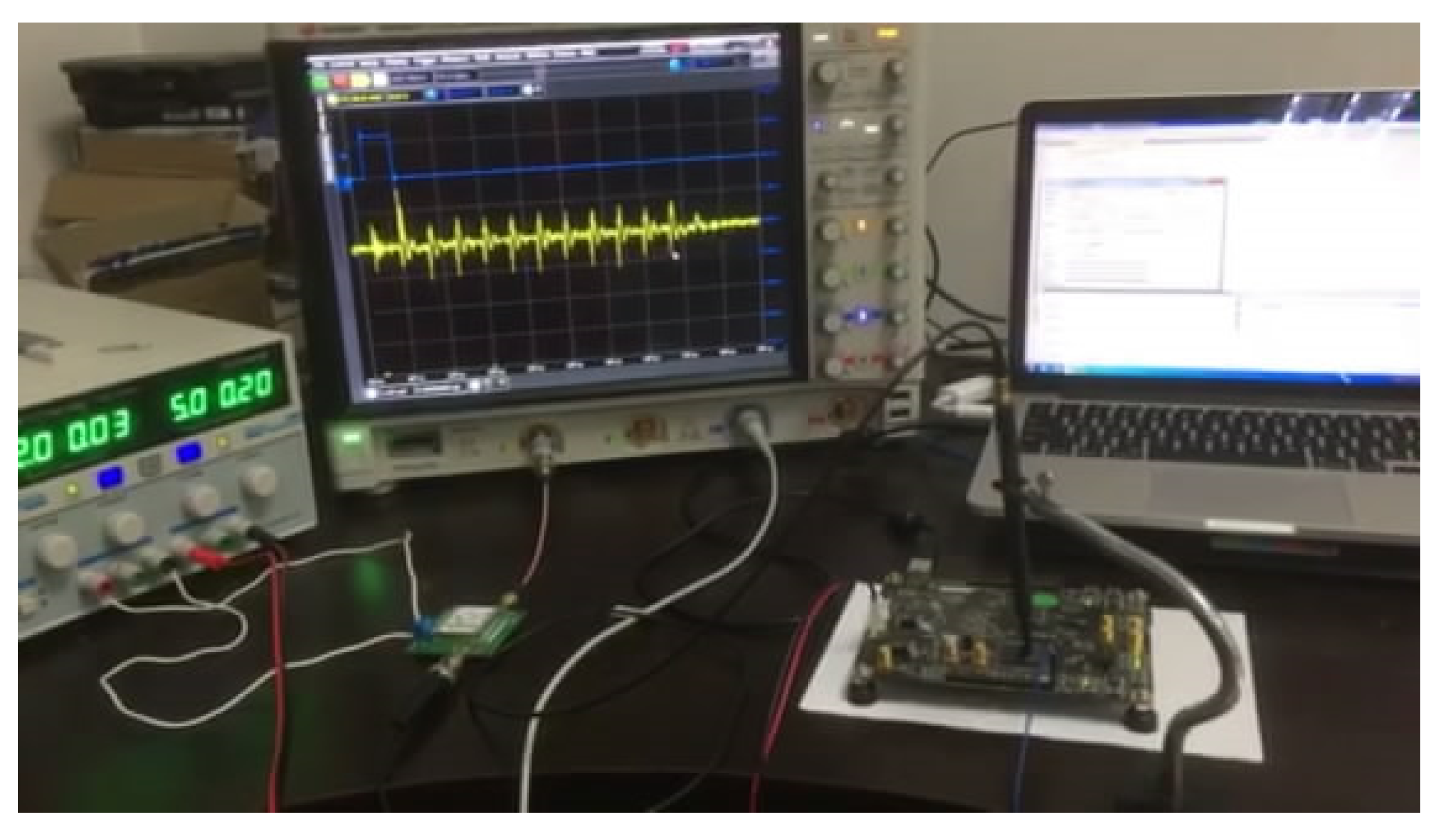
In our experiment, we use the universal test board called Sakura-G, which is designed for research and development on hardware security to standardize the security evaluation method. Experimental platform is shown in Figure 4. We implemented the AES-128 cryptographic algorithm on the Field Programmable Gate Array (Xilinx SPARTAN-6) board with Hamming Distance leakage. The computer sent random messages to the board and the board returned ciphertexts after encryption. The electromagnetic radiation traces corresponding to random messages were measured by an oscilloscope and stored by the computer. The computer also was given an automated setup for data collection and communication. We also used a low noise amplifier to amplify the electromagnetic radiation signal because the original signal was very small.
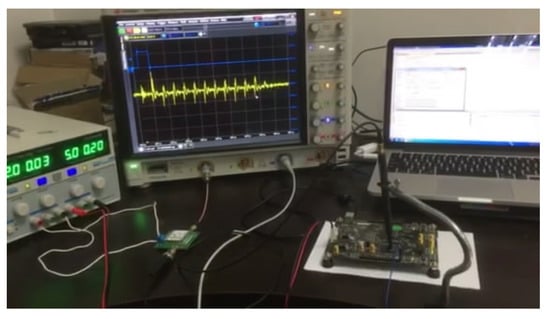
Figure 4.
Experimental platform for Particle Swarm Optimization—Correlation Electromagnetic Analysis.
In our experiment, we focus on the nonlinear SubBytes step of the last round to recover the key. Success rate is known as an effective measure to evaluate the performance. Consequently, we use the success rate to test the performance of different parameters. Success rate is defined as:
where is the successful probability, F is the key recovery function, is the ith byte in the guess key, is the ith byte in the correct key, and m is the byte length of key.
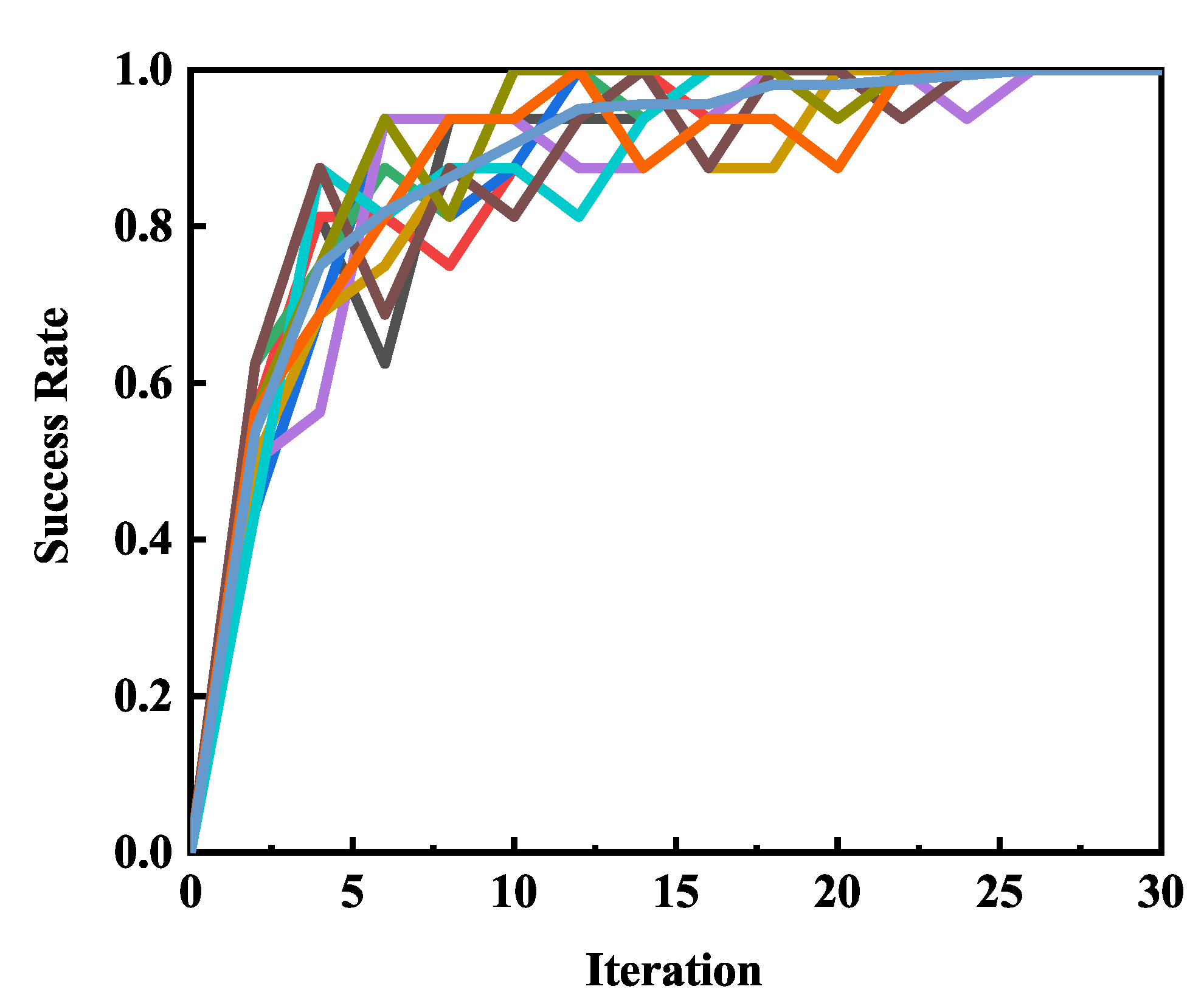
The influence of iteration was studied and experimental results were shown in Figure 5. We perform many experiments to test the influence of iteration on the success rate. When iteration is less than 10, the success rate increased rapidly and then gradually flattened out. When the iteration is 25, we have almost recovered the secret key and reached a stable level. The result shows that, with the increasing of iterations, we achieved a higher success rate. However, if the iteration is very large, it doesn’t provide any further help to recover the secret key.
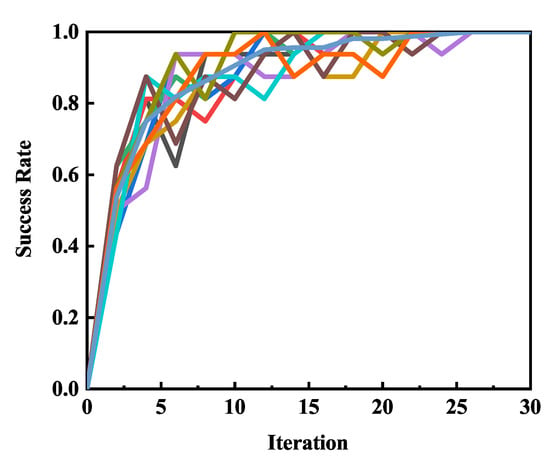
Figure 5.
The relationship between success rate and iterations.
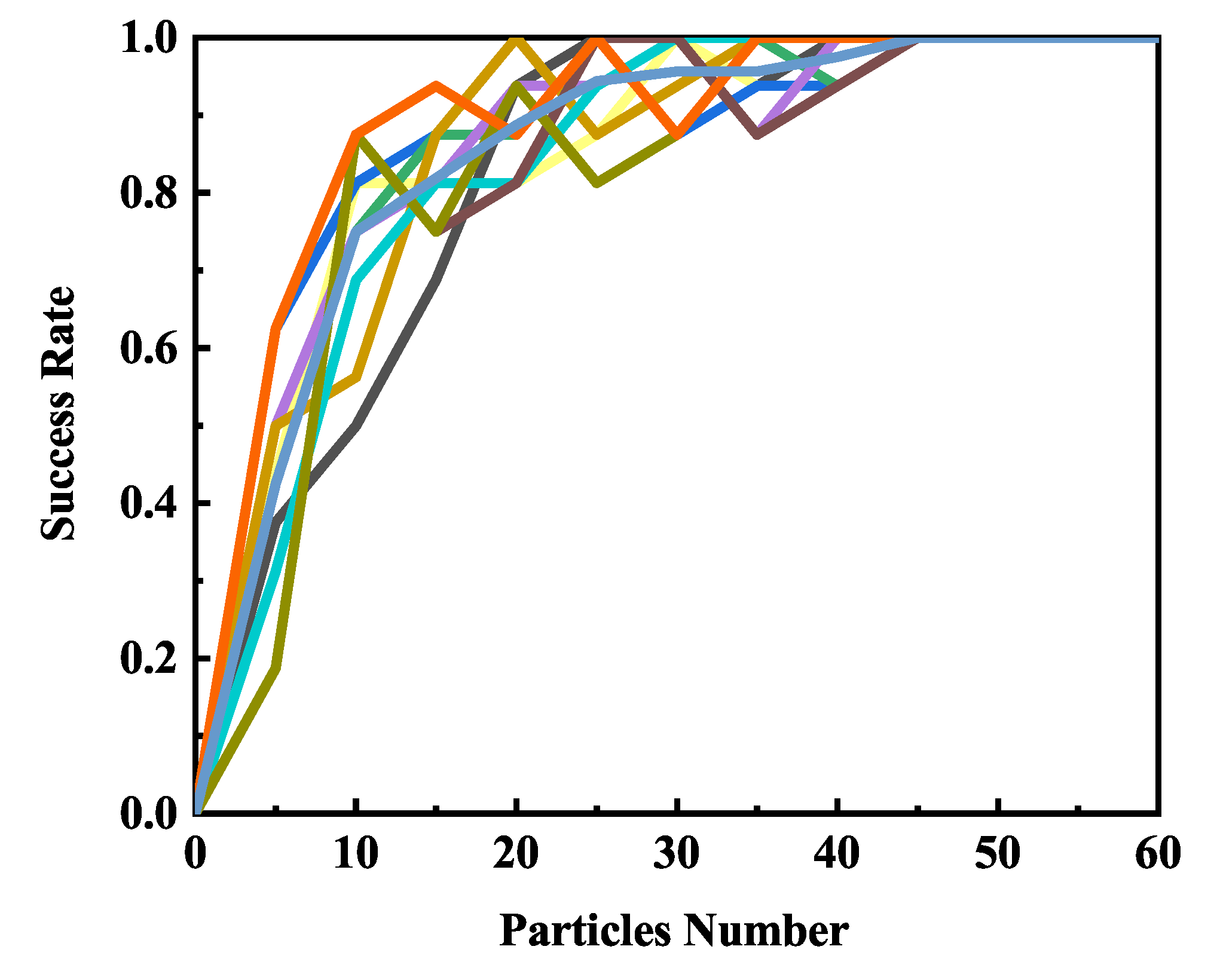
We also tested the influence of initial particles number, and the result was shown in Figure 6. From the figure, we know that, when the number of particles is less than 50, the success rate increases along with the number of particles until recovering the secret key correctly. Thus, we can conclude that iteration and particle number don’t need to be set too large. They will increase computation time if they are very large.
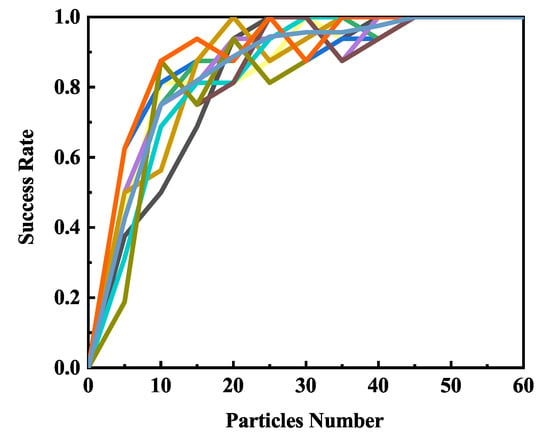
Figure 6.
The relationship between success rate and particle number.
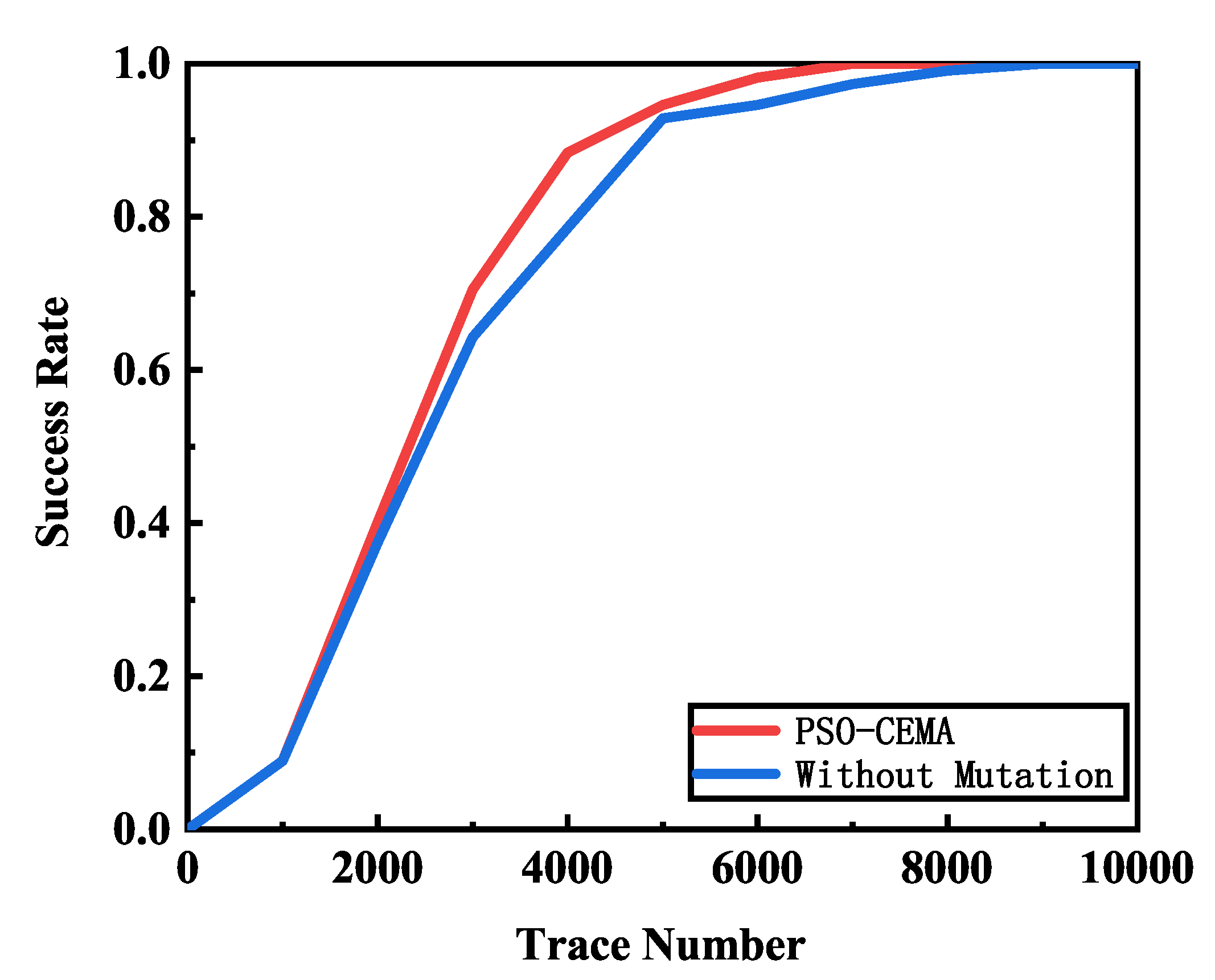
We compare the performance of PSO-CEMA with or without mutation operation in Figure 7. PSO-CEMA can achieve a better performance than PSO-CEMA without mutation. Whilst PSO-CEMA recovers the secret key with a 100% success rate, PSO-CEMA without mutation still needs more than 1000 electromagnetic traces to recover the key correctly.
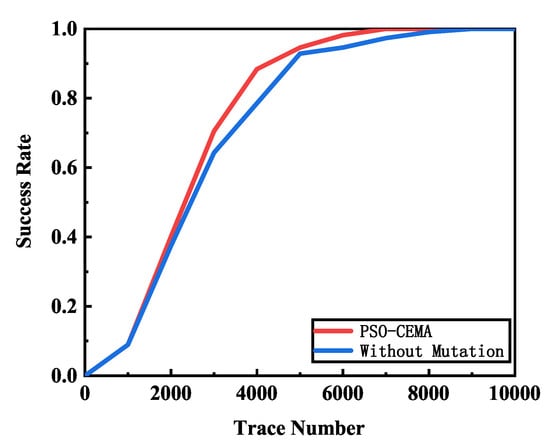
Figure 7.
Success rate comparison of PSO-CEMA with or without mutation operation.
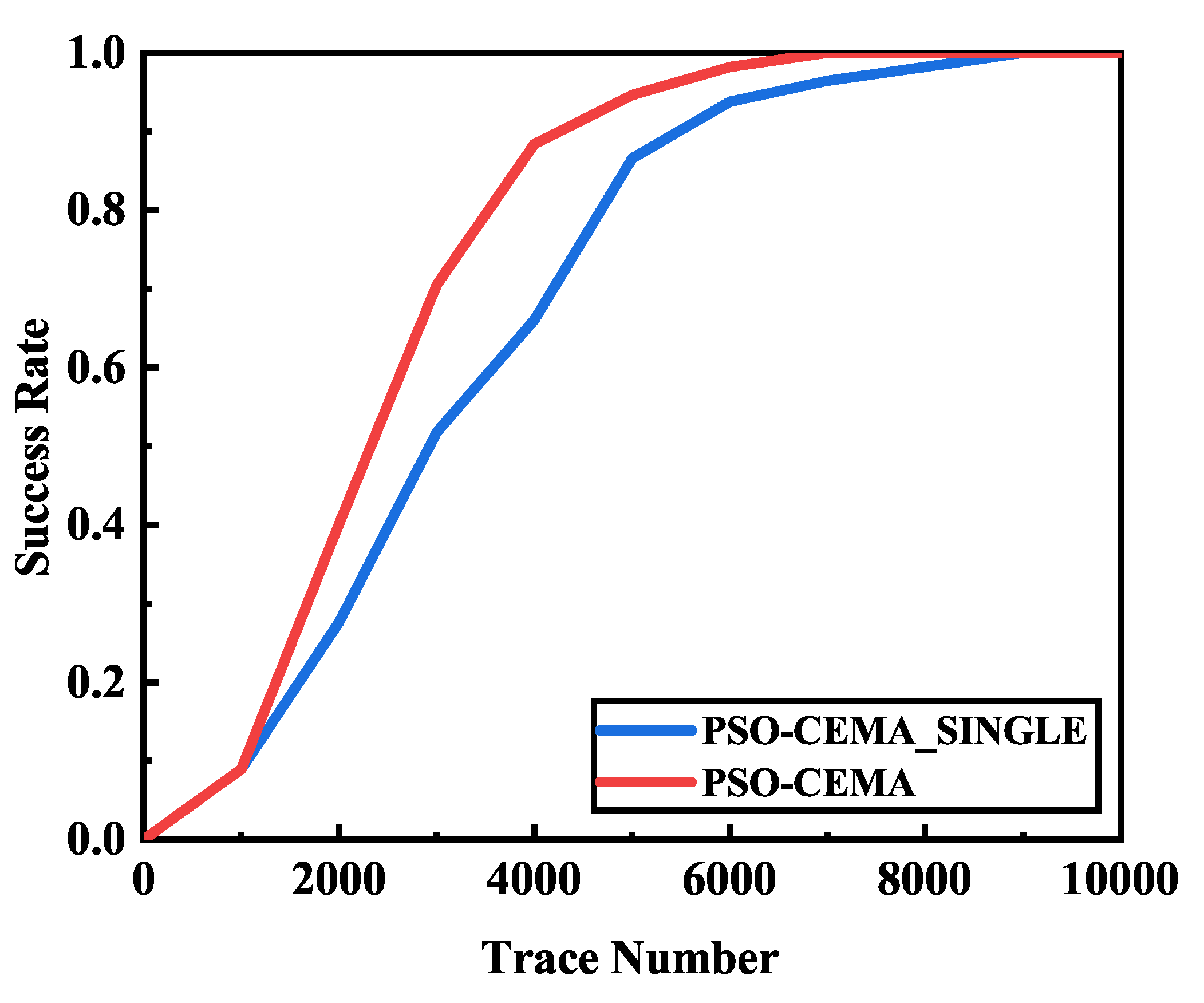
We also compare the performance of single byte and multiple bytes optimized by PSO to verify our method efficiency. The performance is shown in Figure 8. The experimental result shows that the success rate of multiple bytes optimized by PSO is much better than single bytes optimized by PSO. It require approximately 7000 traces for multiple bytes to achieve a 100% success rate. With the same number of electromagnetic traces, the success rate of single byte is approximately 90%. It still needs about 2000 extra traces to achieve a 100% success rate.
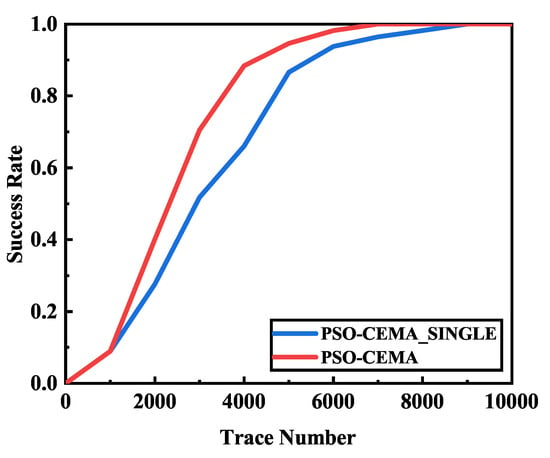
Figure 8.
Success rate comparison of single byte and multiple bytes, the red line is multiple bytes optimized by PSO, and the blue line is a single byte optimized by PSO.
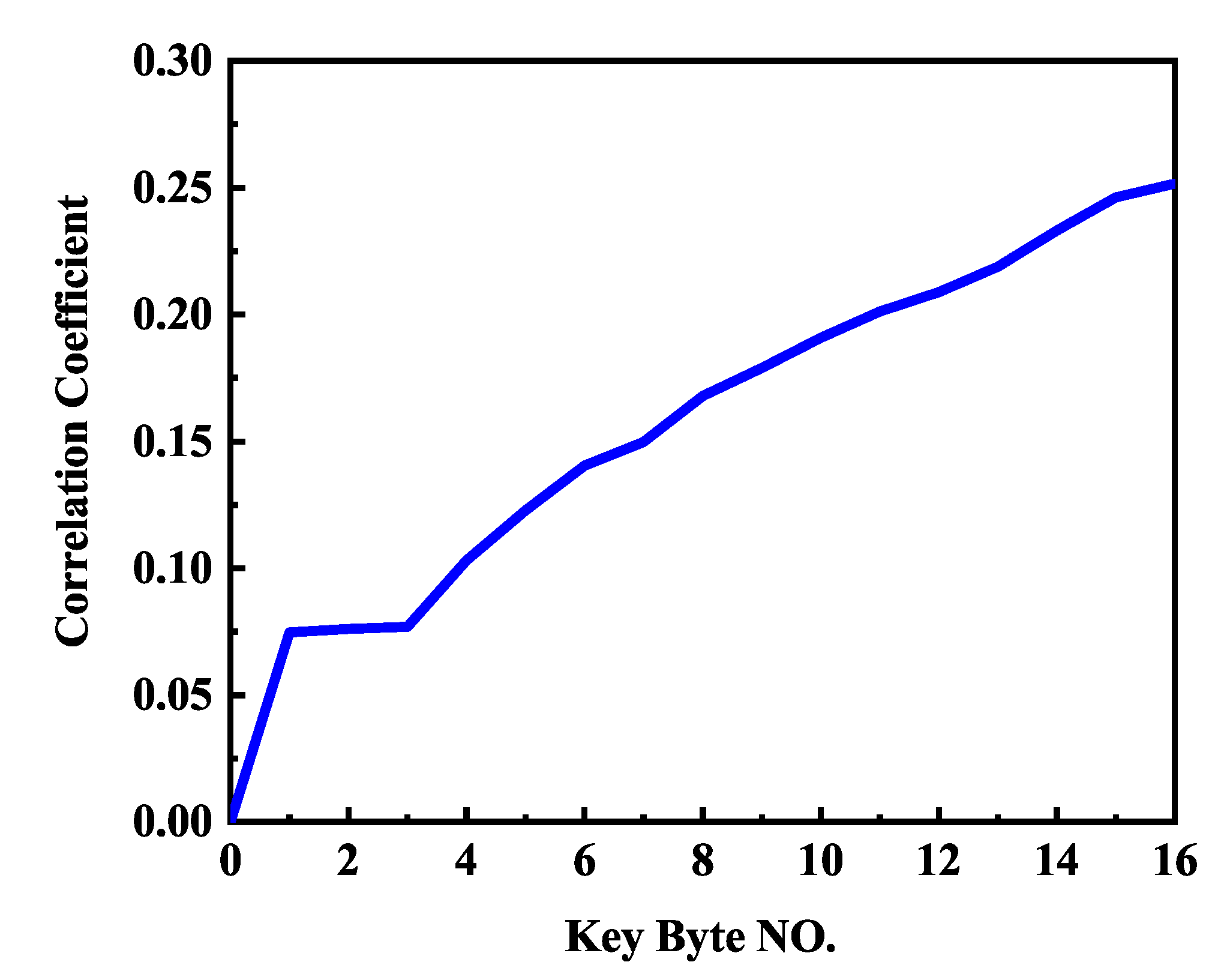
The multibyte key performance is shown in Figure 9. If only a single byte is used, the correlation coefficient is approximately 0.05. If all 16 bytes are used, the correlation coefficient is approximately 0.25. Figure 9 demonstrates that the more bytes we have, the larger the correlation coefficient will be. There is a positive relationship between correlation coefficient and the number of right key bytes. This proves that more useful information is contained in multiple bytes. Thus, it is best if all bytes of the key are used. This also can be deduced by
where SNR is signal-to-noise ratio, is the estimated correlation coefficient. The detailed proof of Equation (15) can be seen in Appendix A. There is a positive correlation between and . The larger the , the larger the . In other words, the more bytes we have, the larger the will be. Thus, it is meaningful to use multiple bytes of the key.
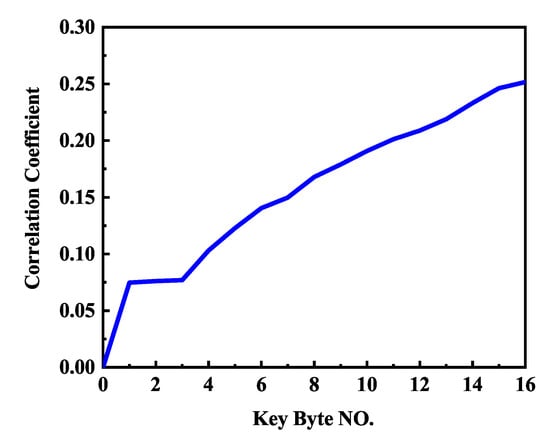
Figure 9.
The relationship between correlation and multiple key bytes.
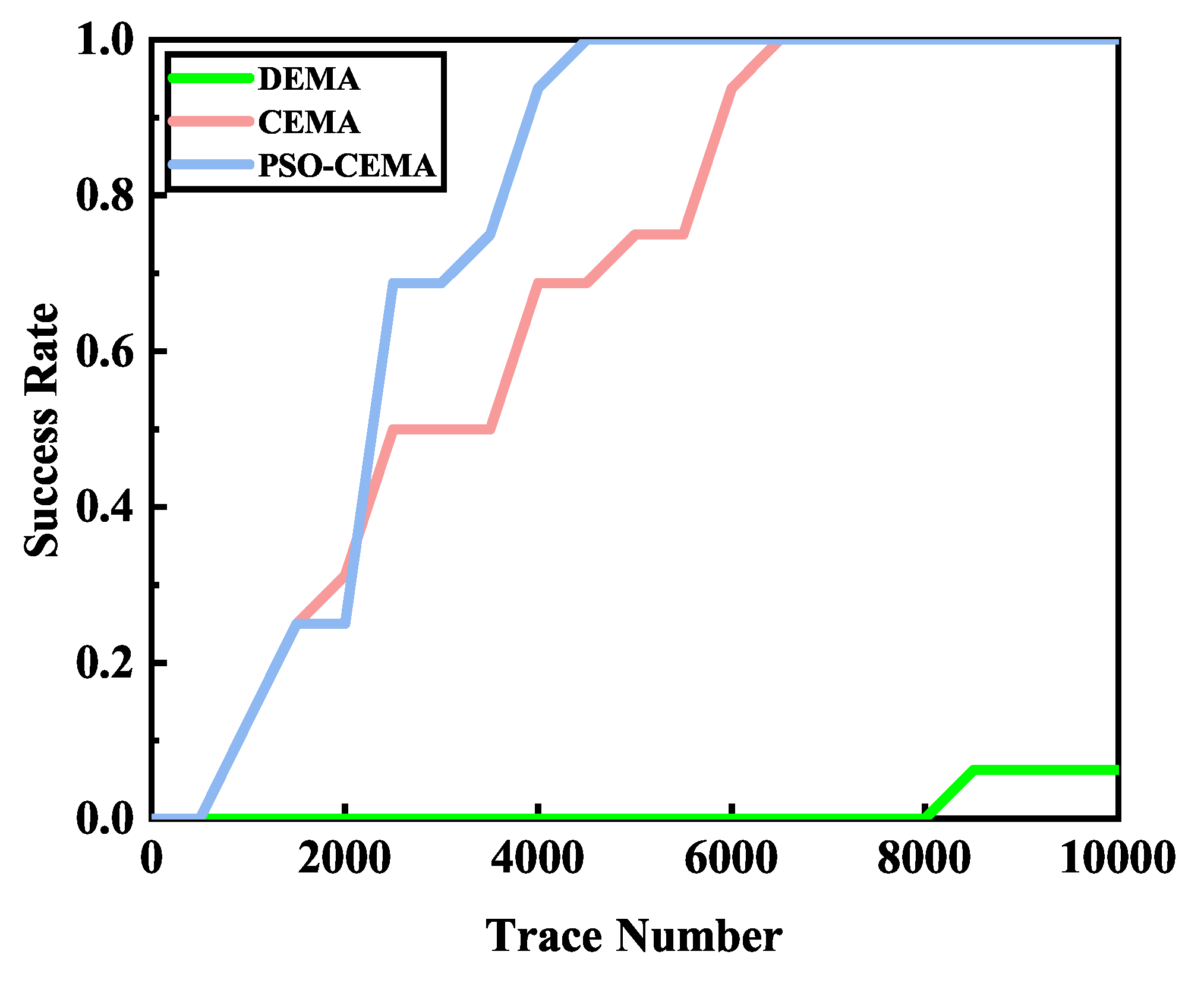
Figure 10 demonstrates the performance of different methods. The performance of PSO-CEMA is best and CEMA is much better than DEMA. For PSO-CEMA, the number of electromagnetic traces is approximately 4500 when the secret key is recovered correctly. With the same number of traces, CEMA’s success rate is approximately 70%, which still needs more traces. When PSO-CEMA and CEMA recover the key correctly, the success rate of DEMA is very low. It still needs a large number of traces if we want to get the right key. The reason is that, in DEMA, only a single bit is used, the other 127 bits are regarded as noise. As a result, little useful information can be used in DEMA. Thus, in the latter, we didn’t take DEMA into account because of its low efficiency.
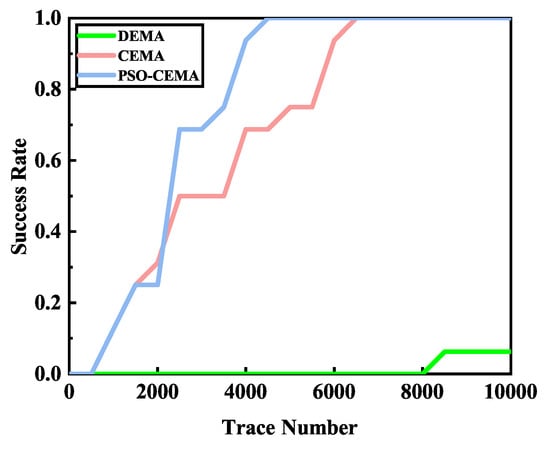
Figure 10.
Success rate of different methods.
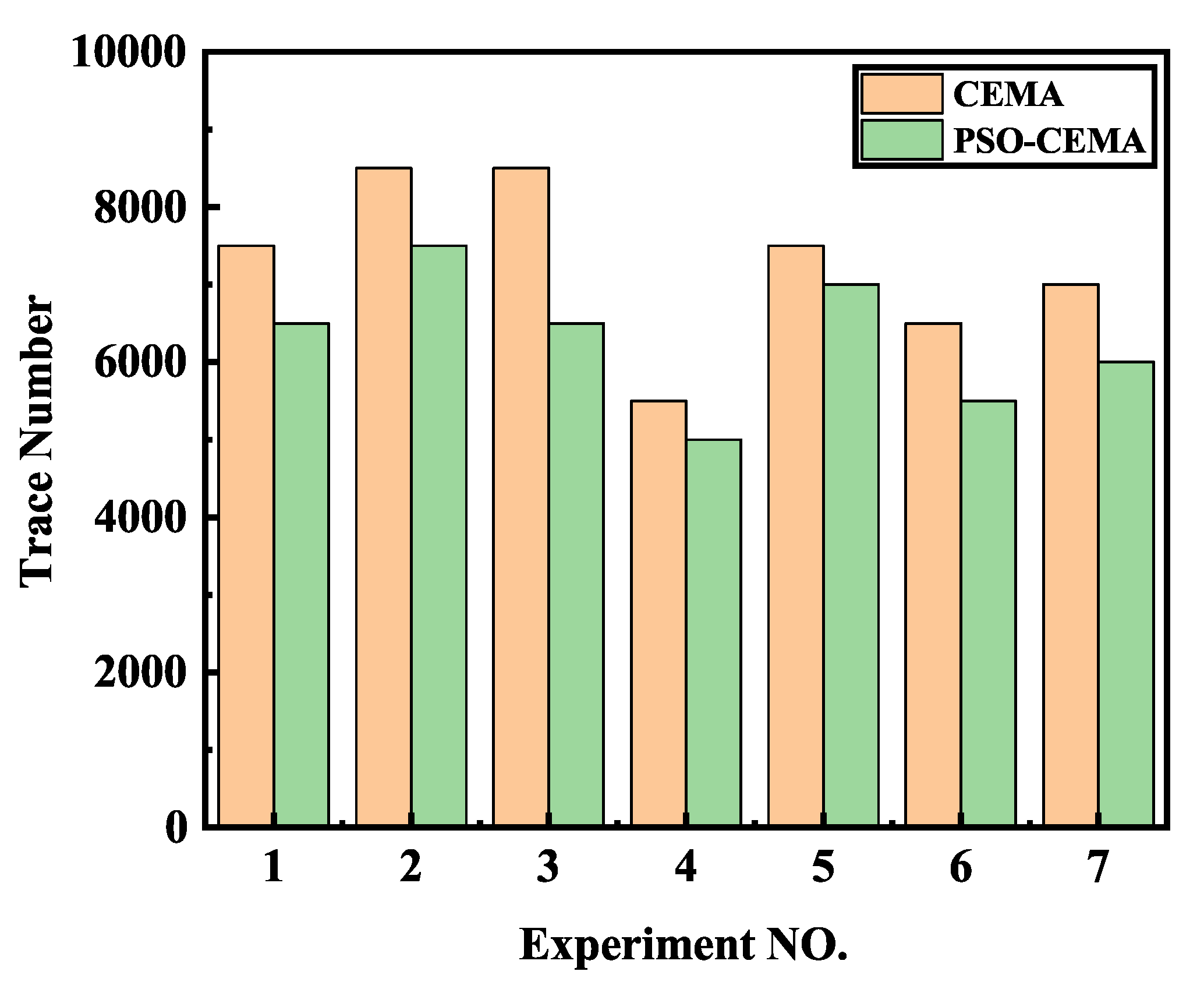
From an attacker aspect, it is better to recover the secret key with less electromagnetic traces. Thus, we used thousands of electromagnetic radiation traces to verify our PSO-CEMA method’s efficiency. In order to highlight the advantage of PSO-CEMA over the existing CEMA method, we compared the total trace number required when the key was recovered correctly with a success rate of 100%. All electromagnetic traces are divided into different sets randomly, and we repeated our method on different sets of electromagnetic traces. The experimental results in Figure 11 show that our method has a better performance. CEMA needs 7286 ± 1075 traces on average while our method needs 6286 ± 859 traces on average, which achieves approximately 13.72% improvement for the corresponding case in CEMA.
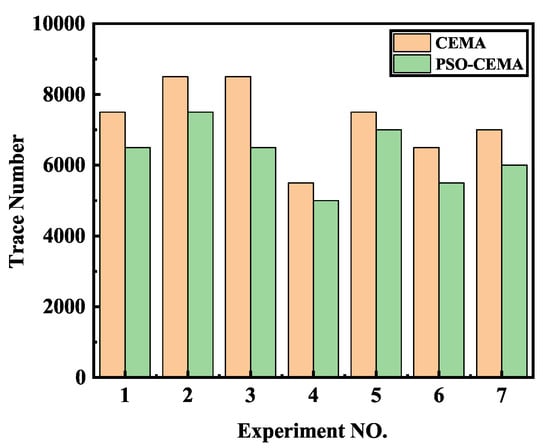
Figure 11.
The minimum number of electromagnetic traces when the right key is recovered.
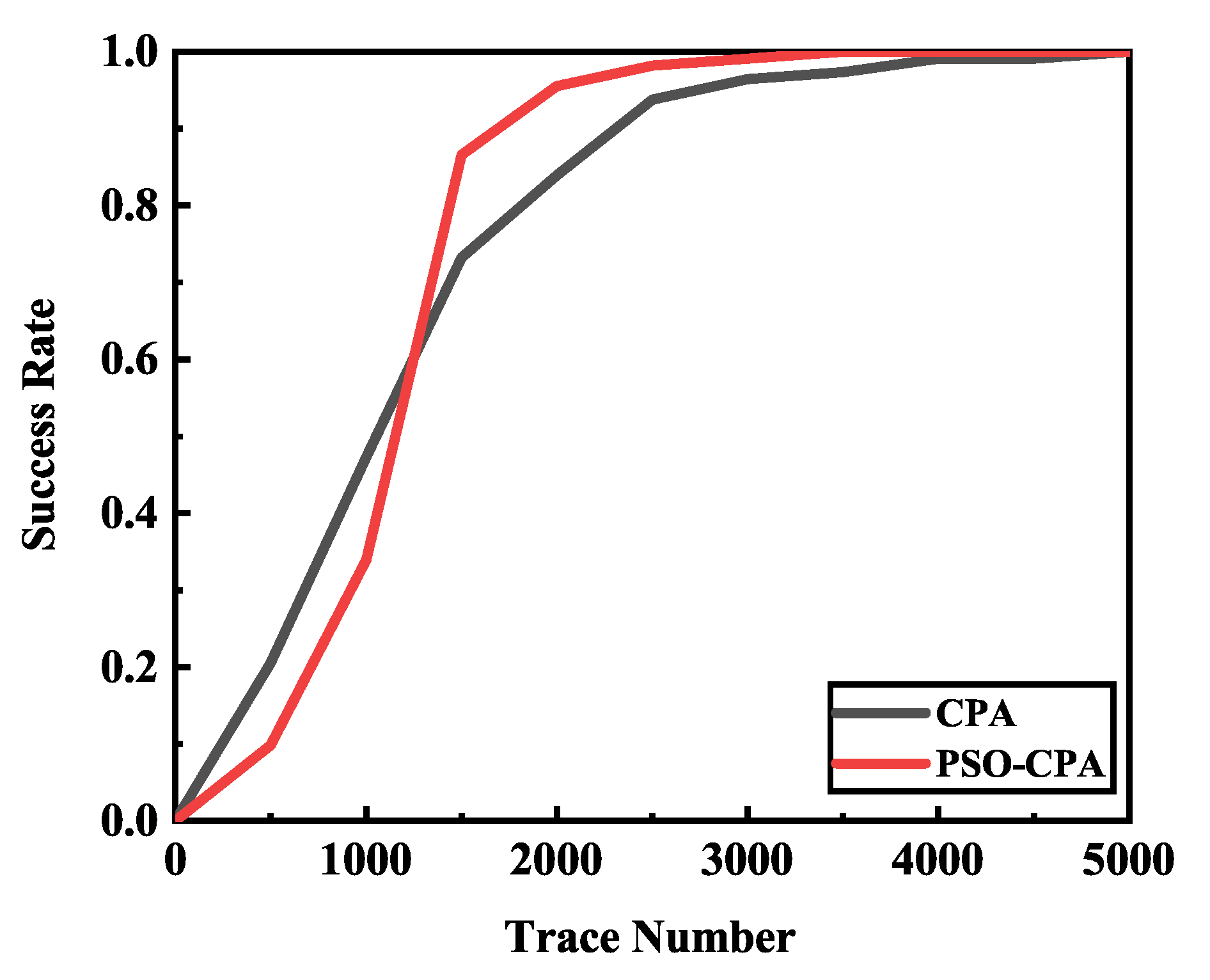
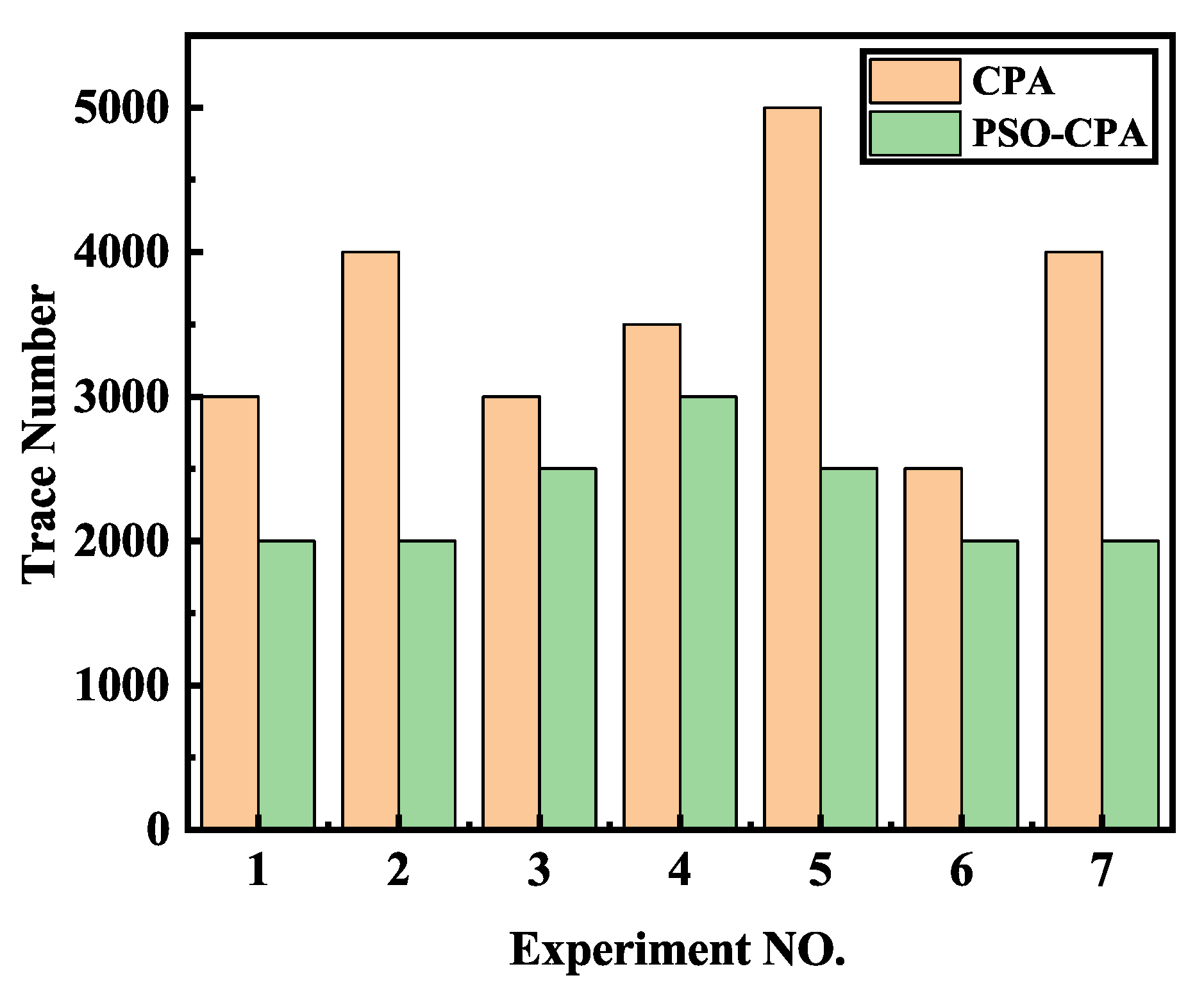
In order to ensure the reproducibility of our method, we applied our method to a public power traces dataset. The experimental results demonstrated a similar conclusion as the previous. Figure 12 shows the success rate of different methods. It can be seen that our method has a better performance than correlation power analysis (CPA). Our method achieves a 100% success rate with about 3500 electromagnetic traces while classical CPA requires about 4500 electromagnetic traces. We also repeated our method on different sets of power traces. All of these traces are also divided into different sets randomly, and we repeated the experiments on these different sets. The total trace number required when the key was recovered correctly is shown in Figure 13. The result showed that our method uses less electromagnetic traces than classical CPA. On average, CPA needs 3571 ± 838 traces while our method only needs 2286 ± 393 traces, which is an improvement of 35.98%. The extra experiments verified our method’s efficiency and reproducibility.
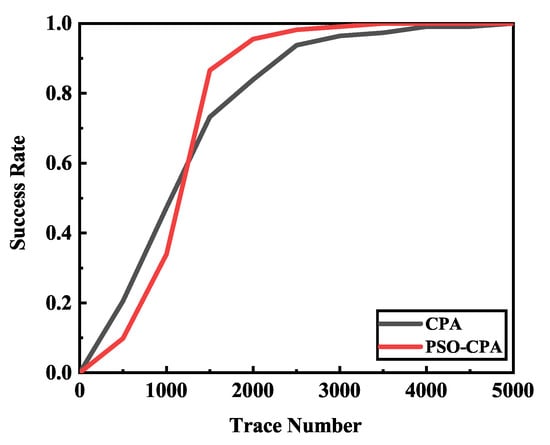
Figure 12.
Success rate of different methods.
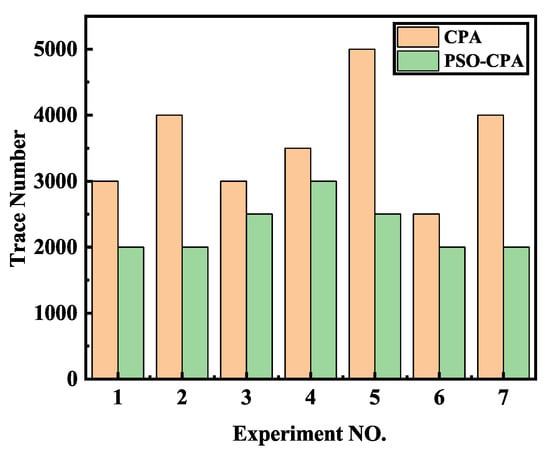
Figure 13.
The minimum number of power traces when the right key is recovered.
6. Conclusions
As can be seen from the above description, electromagnetic analysis can obtain sensitive information in a non-invasive way. In this way, malicious attackers don’t need to have a copy of the cryptographic device or modify the cryptographic device. This is a great threat to modern devices such as computers, mobile phones, and smart cards. In this paper, we focus on electromagnetic radiation security of cryptographic devices in communication systems and propose a multibyte correlation electromagnetic analysis based on PSO algorithm to recover the secret key. The method can be applied to other cryptographic algorithms, if cryptographic algorithms are SPN structures. Our method transformed the key into multidimensional form, so the problem of the right key searching was transformed into the problem of optimizing correlation coefficients of key candidates. In addition, we used multiple bytes to take full advantage of useful information. Experimental results demonstrated that our method outperforms other two classical methods, and, from the results, it can be seen that there is more information contained in multiple bytes.
However, there are some disadvantages in PSO-CEMA. First, we are supposed to set different parameters for different electromagnetic traces—what are the optimal parameters that are still worth exploring. Second, there are many uncorrelated signals in an electromagnetic radiation signal that can be considered as noise. How to reduce these uncorrelated signals is also worth exploring. Third, computational time is longer than classical methods if the initial parameters are too large.
In the future work, we will aim to solve these disadvantages. First of all, filtering work should be considered to have a better electromagnetic radiation signal; then, we will consider an adaptive parameters selection method to get the optimal parameters for different electromagnetic traces. Next, different optimization algorithms will be studied to have a better performance. In addition, other cryptographic algorithms will be studied to verify our method’s efficiency.
Author Contributions
Conceptualization, S.S., H.Z., and L.D.; methodology, S.S. and X.F.; validation, S.S., X.C., and M.S.K.; formal analysis, S.S. and H.Z.; investigation, L.D., X.F., and X.C.; writing—original draft preparation, S.S.; writing—review and editing, H.Z., X.C. and M.S.K.; funding acquisition, H.Z. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by the National Natural Science Foundation of China (62071057), Beijing Natural Science Foundation (3182028), the Fundamental Research Funds for the Central Universities (2019XD17, 2019PTB-001), Aeronautical Science Foundation of China (2019ZG073001), BUPT Excellent Ph.D. Students Foundation (CX2019226), Innovation and Entrepreneurship Project (2020-YC-A144).
Conflicts of Interest
The authors declare no conflict of interest.
Appendix A
In the experiment, the measured electromagnetic radiation traces T contain two parts: the electromagnetic signal part Q and the uncorrelated additive noise part N.
The correlation between H and T is
Theoretically, there is no linear relationship between the hypothetical electromagnetic radiation leakage H and the additive noise N. Both the hypothetical electromagnetic radiation leakage H and electromagnetic signal part Q depend on the data related to cryptographic algorithms. If the correct key is used, . As a result, the values of equal zero and the values of equal one. From Equation (A2), ranges from 0 to 1. Thus,
References
- CISPR. Information Technology Equipment-Radio Disturbance Characteristics-Limits and Methods of Measurement; CISPR: Ispra, Italy, 2006. [Google Scholar]
- Nan, Z.; Lu, Y.; Qiang, C.; Wang, Y. Investigation of Unintentional Video Emanations From a VGA Connector in the Desktop Computers. IEEE Trans. Electromagn. Compat. 2017, 59, 1826–1834. [Google Scholar]
- Hayashi, Y.I.; Homma, N.; Toriumi, Y.; Takaya, K.; Aoki, T. Remote visualization of screen images using a pseudo-antenna that blends into the mobile environment. IEEE Trans. Electromagn. Compat. 2016, 59, 24–33. [Google Scholar] [CrossRef]
- Zhang, C.; Zhang, H.; Luo, J.; Du, Y. Tempest in USB. In Proceedings of the 2017 IEEE 5th International Symposium on Electromagnetic Compatibility (EMC-Beijing), Beijing, China, 28–31 October 2017. [Google Scholar]
- Tosaka, T.; Taira, K.; Yamanaka, Y.; Nishikata, A.; Hattori, M. Feasibility study for reconstruction of information from near field observations of the magnetic field of laser printer. In Proceedings of the International Zurich Symposium on Electromagnetic Compatibility, Singapore, 27 February–3 March 2006. [Google Scholar]
- Sim, D.J.; Lee, H.S.; Yook, J.G.; Sim, K. Measurement and analysis of the compromising electromagnetic emanations from USB keyboard. In Proceedings of the 2016 Asia-Pacific International Symposium on Electromagnetic Compatibility (APEMC), Shenzhen, China, 18–21 May 2016. [Google Scholar]
- Hayashi, Y.I.; Homma, N. Introduction to Electromagnetic Information Security. IEICE Trans. Commun. 2018. [Google Scholar] [CrossRef]
- Genkin, D.; Pachmanov, L.; Pipman, I.; Tromer, E.; Yarom, Y. ECDSA Key Extraction from Mobile Devices via Nonintrusive Physical Side Channels. In Proceedings of the 2016 ACM SIGSAC Conference, Vienna, Austria, 24–28 October 2016. [Google Scholar]
- Kasper, T.; Oswald, D.; Paar, C. EM side-channel attacks on commercial contactless smartcards using low-cost equipment. In International Workshop on Information Security Applications; Springer: Busan, Korea, 2009; pp. 79–93. [Google Scholar]
- Genkin, D.; Pachmanov, L.; Pipman, I.; Tromer, E. Stealing Keys from PCs Using a Radio: Cheap Electromagnetic Attacks on Windowed Exponentiation. In Proceedings of the CHES, Saint-Malo, France, 13–16 September 2015. [Google Scholar]
- Genkin, D.; Pachmanov, L.; Pipman, I.; Tromer, E. ECDH Key-Extraction via Low-Bandwidth Electromagnetic Attacks on PCs. In Proceedings of the Cryptographers’ Track at the RSA Conference, San Francisco, CA, USA, 29 February–4 March 2016. [Google Scholar]
- Carlier, V.; Chabanne, H.; Dottax, E.; Pelletier, H. Electromagnetic side channels of an FPGA implementation of AES. In Cryptology Eprint Archive, Report 2004/145; Citeseer: State College, PA, USA, 2004. [Google Scholar]
- Guo, L.D.; Jie, C.; Liang, Y.; Qiang, Z. Correlation Electromagnetic Analysis for Cryptographic Device. In Proceedings of the 2009 Pacific-Asia Conference on Circuits, Communications and Systems, PACCS 2009, Chengdu, China, 16–17 May 2009. [Google Scholar]
- Hayashi, Y.I.; Homma, N.; Mizuki, T.; Aoki, T.; Sone, H. Efficient Electromagnetic Analysis for Cryptographic Module on the Frequency Domain. Electron. Commun. Jpn. 2016, 99, 24–32. [Google Scholar] [CrossRef]
- Gan, H.; Zhang, H.; Khan, M.S.; Wang, X. An improved differential power analysis against random process interrupts. J. Chin. Inst. Eng. 2019, 42, 127–131. [Google Scholar] [CrossRef]
- Das, D.; Nath, M.; Chatterjee, B.; Ghosh, S.; Sen, S. STELLAR: A Generic EM Side-Channel Attack Protection through Ground-Up Root-cause Analysis. In Proceedings of the HOST, McLean, VA, USA, 6–10 May 2019; pp. 11–20. [Google Scholar]
- Sun, S.; Zhang, H.; Du, Y. The electromagnetic leakage analysis based on arithmetic operation of FPGA. In Proceedings of the 2017 IEEE 5th International Symposium on Electromagnetic Compatibility (EMC-Beijing), Beijing, China, 28–31 October 2017. [Google Scholar]
- Gandolfi, K.; Mourtel, C.; Olivier, F. Electromagnetic Analysis: Concrete Results. In International Workshop on Cryptographic Hardware and Embedded Systems; Springer: Berlin/Heidelberg, Germany, 2001; pp. 251–261. [Google Scholar]
- Rao, J.R.; Rohatgi, P. EMpowering Side-Channel Attacks. IACR Cryptol. EPrint Arch. 2001, 2001, 37. [Google Scholar]
- Sun, S.; Zhang, H.; Dong, L.; Cui, X.; Khan, M.S. A Novel Multi-Objective Electromagnetic Analysis Based on Genetic Algorithm. Sensors 2019, 19, 5542. [Google Scholar] [CrossRef] [PubMed]
- Yonli, M. A Comparison of Single-Bit and Multi-Bit DPA for Attacking AES128 on an ATmega328P. IACR Cryptol. EPrint Arch. 2019, 2019, 899. [Google Scholar]
- Fu, S.; Wang, Z.; Xu, G.; Wei, F.; Wang, A.; Pan, J.; Li, Y.; Zhang, N. Multi-Byte Power Analysis: A Generic Approach Based on Linear Regression. IEEE Access 2018, 6, 67511–67518. [Google Scholar] [CrossRef]
- Sun, S.; Zhang, H.; Wang, Y.; Dong, L.; Li, Q. Multi-Bytes electromagnetic analysis: A novel method to get the key. In Proceedings of the 2019 IEEE 6th International Symposium on Electromagnetic Compatibility (ISEMC), Nanjing, China, 1–4 November 2019; pp. 1–3. [Google Scholar]
- Chouikhi, N.; Ammar, B.; Rokbani, N.; Alimi, A.M. PSO-based analysis of Echo State Network parameters for time series forecasting. Appl. Soft Comput. 2017, 55, 211–225. [Google Scholar] [CrossRef]
- Deng, W.; Yao, R.; Zhao, H.; Yang, X.; Li, G. A novel intelligent diagnosis method using optimal LS-SVM with improved PSO algorithm. Soft Comput. 2019, 23, 2445–2462. [Google Scholar] [CrossRef]
- Zhang, H.; Liang, Y.; Zhang, W.; Xu, N.; Guo, Z.; Wu, G. Improved PSO-based Method for Leak Detection and Localization in Liquid Pipelines. IEEE Trans. Ind. Inform. 2018, 14, 3143–3154. [Google Scholar] [CrossRef]
- Standard, N.F. Announcing the advanced encryption standard (aes). Fed. Inf. Process. Stand. Publ. 2001, 197, 3. [Google Scholar]
- Kennedy, J.; Eberhart, R. Particle Swarm Optimization. In Proceedings of the Icnn95-international Conference on Neural Networks, Perth, Australia, 27 November–1 December 1995. [Google Scholar]
- Shi, Y. A Modified Particle Swarm Optimizer. In Proceedings of the IEEE ICEC Conference, Anchorage, AK, USA, 4–9 May 1998. [Google Scholar]
- Kocher, P.; Jaffe, J.; Jun, B.; Rohatgi, P. Introduction to differential power analysis. J. Cryptogr. Eng. 2011, 1, 5–27. [Google Scholar] [CrossRef]
- Lo, O.; Buchanan, W.J.; Carson, D. Power analysis attacks on the AES-128 S-box using differential power analysis (DPA) and correlation power analysis (CPA). J. Cyber Secur. Technol. 2017, 1, 88–107. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).