Quantum Key Distribution Networks: Challenges and Future Research Issues in Security
Abstract
1. Introduction
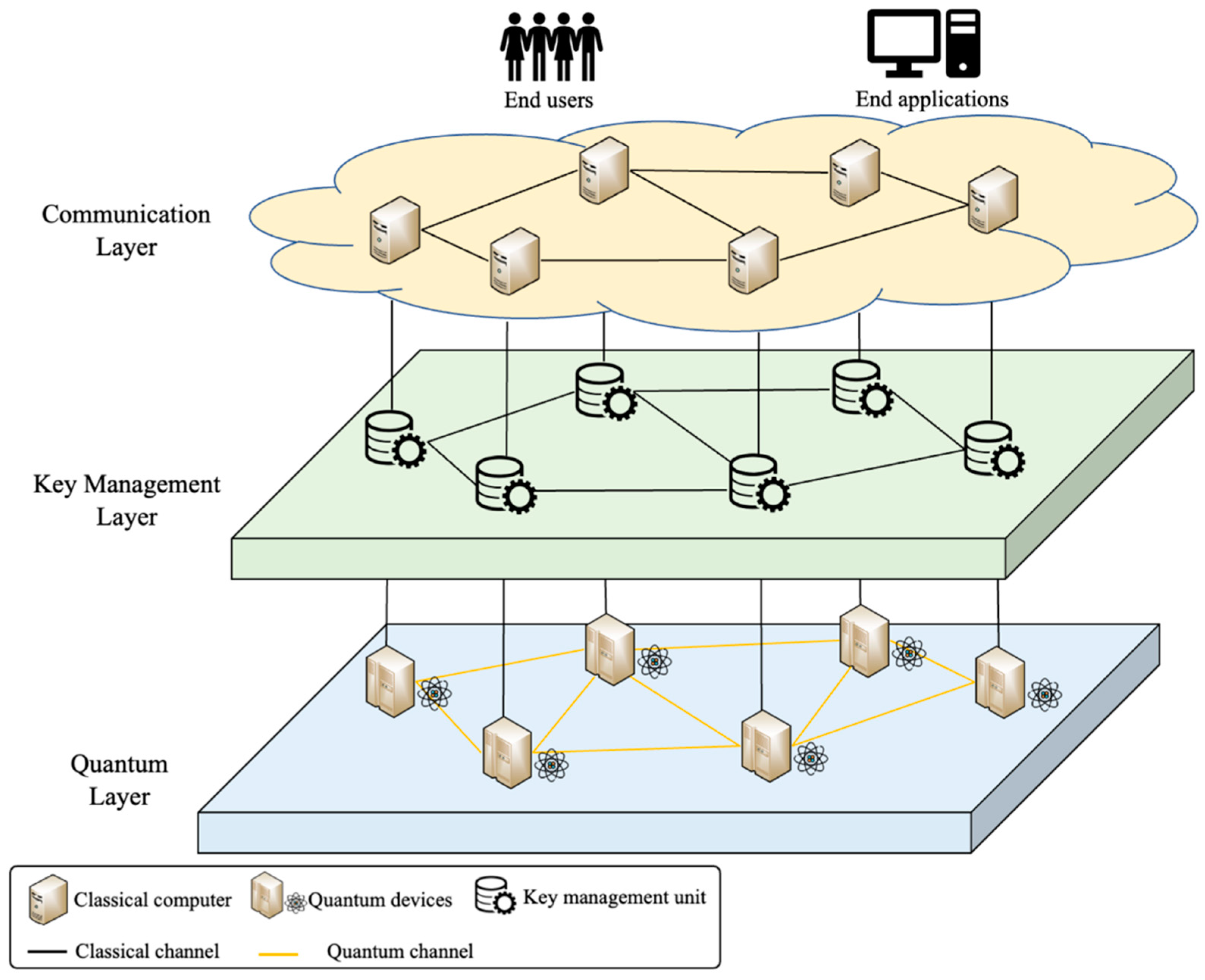
2. Background to Quantum Key Distribution (QKD) Networks
2.1. Quantum Node
2.2. Quantum Link
2.3. QKD Network Type
2.3.1. Active Optical Switch Network
2.3.2. Trusted Node Network
2.3.3. Quantum Repeater Network
3. Key Results of Existing QKD Networks
4. Challenges and Research Issues
- (1)
- Lacking point-to-multipoint (P2M) mechanisms in QKD networks: the key distribution service of the existing QKD network only provides point-to-point (P2P)) key distribution and lacks the P2M mechanism.
- (2)
- Many quantum node resources are consumed by a multiple-path strategy: although a multiple-path strategy can avoid the assumption that all quantum nodes must be trusted, many quantum node resources (e.g., the local keys that are used to help transmit the session key) are consumed to accomplish the multiple-path strategy.
- (3)
- No suitable security interface between the classical end users/applications and the quantum nodes: allowing classical end users/applications to have access to the key distribution service of QKD networks securely within the quantum computing environment is an important issue.
4.1. Lacking the Point-to-Multipoint (P2M) Mechanism in QKD Networks
4.2. Numerous Quantum Node Resources Are Consumed by the Multiple-Path Strategy
4.3. No Suitable Security Interface between the Classical End Users/Applications and Quantum Nodes
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Bennett, C.H.; Brassard, G. Quantum Cryptography: Public Key Distribution and Coin Tossing. In Proceedings of the IEEE International Conference on Computers, Systems and Signal Processing, Bangalore, India, 9–12 December 1984; pp. 175–179. [Google Scholar]
- Shor, P.W.; Preskill, J. Simple Proof of Security of the BB84 Quantum Key Distribution Protocol. Phys. Rev. Lett. 2000, 85, 441–444. [Google Scholar] [CrossRef]
- Gottesman, D.; Hoi-Kwong, L. Proof of security of quantum key distribution with two-way classical communications. IEEE Trans. Inf. Theory 2003, 49, 457–475. [Google Scholar] [CrossRef]
- Tsurumaru, T.; Tamaki, K. Security proof for quantum-key-distribution systems with threshold detectors. Phys. Rev. A 2008, 78, 032302. [Google Scholar] [CrossRef]
- Bennett, C.H.; Brassard, G.; Mermin, N.D. Quantum cryptography without Bell’s theorem. Phys. Rev. Lett. 1992, 68, 557–559. [Google Scholar] [CrossRef] [PubMed]
- Cerf, N.J.; Bourennane, M.; Karlsson, A.; Gisin, N. Security of Quantum Key Distribution Using d-Level Systems. Phys. Rev. Lett. 2002, 88, 127902. [Google Scholar] [CrossRef] [PubMed]
- Long, G.; Liu, X. Theoretically efficient high-capacity quantum-key-distribution scheme. Phys. Rev. A 2002, 65, 032302. [Google Scholar] [CrossRef]
- Grosshans, F.; Van Assche, G.; Wenger, J.; Brouri, R.; Cerf, N.J.; Grangier, P. Quantum key distribution using gaussian-modulated coherent states. Nature 2003, 421, 238. [Google Scholar] [CrossRef]
- Hwang, W.-Y. Quantum Key Distribution with High Loss: Toward Global Secure Communication. Phys. Rev. Lett. 2003, 91, 057901. [Google Scholar] [CrossRef]
- Lo, H.K.; Ma, X.F.; Chen, K. Decoy state quantum key distribution. Phys. Rev. Lett. 2005, 94, 4. [Google Scholar] [CrossRef]
- Hwang, T.; Lee, K.C.; Li, C.M. Provably secure three-party authenticated quantum key distribution protocols. IEEE Trans. Depend. Secur. 2007, 4, 71–80. [Google Scholar] [CrossRef]
- Li, X.H.; Deng, F.G.; Zhou, H.Y. Efficient quantum key distribution over a collective noise channel. Phys. Rev. A 2008, 78, 022321. [Google Scholar] [CrossRef]
- Lo, H.-K.; Curty, M.; Qi, B. Measurement-Device-Independent Quantum Key Distribution. Phys. Rev. Lett. 2012, 108, 130503. [Google Scholar] [CrossRef] [PubMed]
- Yang, C.-W. New Probabilistic Quantum Key Distribution Protocol. Int. J. Theor. Phys. 2018, 57, 3651–3657. [Google Scholar] [CrossRef]
- Boyer, M.; Kenigsberg, D.; Mor, T. Quantum Key Distribution with Classical Bob. Phys. Rev. Lett. 2007, 99, 140501. [Google Scholar] [CrossRef] [PubMed]
- Boyer, M.; Gelles, R.; Kenigsberg, D.; Mor, T. Semiquantum key distribution. Phys. Rev. A 2009, 79, 032341. [Google Scholar] [CrossRef]
- Krawec, W.O. Mediated semiquantum key distribution. Phys. Rev. A 2015, 91, 032323. [Google Scholar] [CrossRef]
- Xu, F.; Qi, B.; Liao, Z.; Lo, H.-K. Long distance measurement-device-independent quantum key distribution with entangled photon sources. Appl. Phys. Lett. 2013, 103, 61101. [Google Scholar] [CrossRef]
- Liu, Y.; Chen, T.Y.; Wang, L.J.; Liang, H.; Shentu, G.L.; Wang, J.; Cui, K.; Yin, H.-L.; Liu, N.-L.; Li, L.; et al. Experimental measurement-device-independent quantum key distribution. Phys. Rev. Lett. 2013, 111, 130502. [Google Scholar] [CrossRef] [PubMed]
- Elliott, C.; Pearson, D.; Troxel, G. Quantum cryptography in practice. In Proceedings of the Conference on Applications, Technologies, Architectures, and Protocols for Computer Communications (SIGCOMM’03), Karlsruhe, Germany, 25–29 August 2003; pp. 227–238. [Google Scholar]
- Elliott, C.; Yeh, H. DARPA Quantum Network Testbed; Technical Report; BBN Technologies Cambridge: New York, NY, USA, 2007; Available online: https://apps.dtic.mil/sti/pdfs/ADA471450.pdf (accessed on 25 March 2021).
- Elliott, C.; Colvin, A.; Pearson, D.; Pikalo, O.; Schlafer, J.; Yeh, H. Current status of the DARPA quantum network. In Quantum Information and Computation III; International Society for Optics and Photonics: Washington, DC, USA, 2005; Volume 5815. [Google Scholar]
- Kollmitzer, C.; Pivk, M. Applied Quantum Cryptography; Springer Science & Business Media: Berlin, Germany, 2010; Volume 797. [Google Scholar]
- Dianati, M.; Alléaume, R.; Gagnaire, M.; Shen, X. Architecture and protocols of the future European quantum key distribution network. Sec. Commun. Netw. 2008, 1, 57–74. [Google Scholar] [CrossRef]
- Peev, M.; Länger, T.; Lorünser, T.; Happe, A.; Maurhart, O.; Poppe, A.; Themel, T. The SECOQC quantum key distribution network in Vienna. New J. Phys. 2009, 11, 75001. [Google Scholar] [CrossRef]
- Masahide Sasaki. Tokyo QKD network and the evolution to secure photonic network. In Proceedings of the Conference on Laser Applications to Photonic Applications (CLEO’11), Baltimore, MD, USA, 1–6 May 2011; OSA: Washington, DC, USA, 2011; Volume 1. [Google Scholar]
- Sarkar, K.; Basavaraju, T.G.; Puttamadappa, C. Ad Hoc Mobile Wireless Networks; CRC Press: Boca Raton, FL, USA, 2008; Volume 1. [Google Scholar]
- Xu, F.; Chen, W.; Wang, S.; Yin, Z.; Zhang, Y.; Liu, Y.; Zhou, Z.; Zhao, Y.; Li, H.; Liu, D.; et al. Field experiment on a robust hierarchical metropolitan quantum cryptography network. Chin. Sci. Bull. 2009, 54, 2991–2997. [Google Scholar] [CrossRef]
- Han, Z.-F.; Xu, F.-X.; Chen, W.; Wang, S.; Yin, Z.-Q.; Zhang, Y.; Liu, Y.; Zhou, Z.; Li, H.-W.; Liu, D.; et al. An application-oriented hierarchical quantum cryptography net- work test bed. In Proceedings of the Optical Fiber Communication Conference, San Diego, CA, USA, 21–25 March 2010. [Google Scholar]
- Wang, S.; Chen, W.; Yin, Z.-Q.; Li, H.-W.; He, D.-Y.; Li, Y.-H.; Zhou, Z.; Song, X.-T.; Li, F.-Y.; Wang, D.; et al. Field and long-term demonstration of a wide area quantum key distribution network. Opt. Express 2014, 22, 21739. [Google Scholar] [CrossRef]
- European Commission. China to Launch World’s First Quantum Communication Network. 2017. Available online: https://cordis.europa.eu/article/id/122516.trending-science-china-to-launch-worlds-first-quantum-communication-network/en (accessed on 3 August 2017).
- ChinaDaily. Quantum Tech to Link Jinan Governments. 2017. Available online: http://www.chinadaily.com.cn/china/2017-07/11/content_30065215.htm (accessed on 11 July 2017).
- Travagnin, M.; Lewis, A. Quantum Key Distribution in Field Implementations. 2019. EUR 29865 EN. Available online: https://op.europa.eu/en/publicationdetail/-/publication/e93e5bf9-efc3-11e9-a32c-01aa75ed71a1/language-en (accessed on 15 October 2019).
- Zhao, Y. The integration of QKD and security services. In Proceedings of the ITU QIT4N Workshop, Shanghai, China, 5–7 June 2019; Available online: https://www.itu.int/en/ITU-T/Workshops-and-Seminars/2019060507/Documents/Yong (accessed on 5 June 2019).
- Wang, S.; Chen, W.; Yin, Z.-Q.; Zhang, Y.; Zhang, T.; Li, H.-W.; Xu, F.-X.; Zhou, Z.; Yang, Y.; Huang, D.-J.; et al. Field test of wavelength-saving quantum key distribution network. Opt. Lett. 2010, 35, 2454–2456. [Google Scholar] [CrossRef]
- Van Meter, R.; Satoh, T.; Ladd, T.D.; Munro, W.J.; Nemoto, K. Path selection for quantum repeater networks. Netw. Sci. 2013, 3, 82–95. [Google Scholar] [CrossRef]
- Tanizawa, Y.; Takahashi, R.; Dixon, A.R. A routing method designed for a Quantum Key Distribution network. In Proceedings of the 2016 Eighth International Conference on Ubiquitous and Future Networks (ICUFN), Vienna, Austria, 5–8 July 2016; pp. 208–214. [Google Scholar]
- Yang, C.; Zhang, H.; Su, J. The QKD network: Model and routing scheme. J. Mod. Opt. 2017, 64, 2350–2362. [Google Scholar] [CrossRef]
- Mehic, M.; Fazio, P.; Rass, S.; Maurhart, O.; Peev, M.; Poppe, A.; Rozhon, J.; Niemiec, M.; Voznak, M. A Novel Approach to Quality-of-Service Provisioning in Trusted Relay Quantum Key Distribution Networks. IEEE/ACM Trans. Netw. 2019, 28, 168–181. [Google Scholar] [CrossRef]
- Hahn, F.; Pappa, A.; Eisert, J. Quantum network routing and local complementation. NPJ Quantum Inf. 2019, 5, 76. [Google Scholar] [CrossRef]
- Amer, O.; Krawec, W.O.; Wang, B. Efficient Routing for Quantum Key Distribution Networks. arXiv 2020, arXiv:2005.12404. [Google Scholar]
- Tang, Z.; Qin, Y.; Jiang, Z.; Krawec, W.O.; Zhang, P. Quantum-Secure Networked Microgrids. In Proceedings of the 2020 IEEE Power & Energy Society General Meeting (PESGM), Washington, DC, USA, 3–6 August 2020; pp. 1–5. [Google Scholar]
- Tang, Z.; Zhang, P.; Krawec, W.O.; Jiang, Z. Programmable Quantum Networked Microgrids. IEEE Trans. Quantum Eng. 2020, 1, 1–13. [Google Scholar] [CrossRef]
- Salvail, L.; Peev, M.; Diamanti, E.; Alléaume, R.; Lütkenhaus, N.; Langer, T. Security of trusted repeater quantum key distribution networks. J. Comput. Secur. 2010, 18, 61–87. [Google Scholar] [CrossRef]
- Tang, Y.L.; Yin, H.L.; Zhao, Q.; Liu, H.; Sun, X.X.; Huang, M.Q.; Zhang, W.-J.; Chen, S.-J.; Zhang, L.; You, L.-X.; et al. Measurement-device-independent quantum key distribution over untrustful metropolitan network. Phys. Rev. X 2016, 6, 011024. [Google Scholar] [CrossRef]
- Tanizawa, Y.; Takahashi, R.; Sato, H.; Dixon, A.R.; Kawamura, S. A Secure Communication Network Infrastructure Based on Quantum Key Distribution Technology. IEICE Trans. Commun. 2016, 99, 1054–1069. [Google Scholar] [CrossRef]
- Fröhlich, B.; Dynes, J.F.; Lucamarini, M.; Sharpe, A.W.; Yuan, Z.; Shields, A.J. A quantum access network. Nature 2013, 501, 69–72. [Google Scholar] [CrossRef] [PubMed]
- Cai, C.; Sun, Y.; Niu, J.; Ji, Y. A Quantum Access Network Suitable for Internetworking Optical Network Units. IEEE Access 2019, 7, 92091–92099. [Google Scholar] [CrossRef]
- Wegman, M.N.; Carter, J. New hash functions and their use in authentication and set equality. J. Comput. Syst. Sci. 1981, 22, 265–279. [Google Scholar] [CrossRef]
- Choi, I.; Young, R.J.; Townsend, P.D. Quantum information to the home. New J. Phys. 2011, 13, 063039. [Google Scholar] [CrossRef]
- Liao, S.-K.; Lin, J.; Ren, J.-G.; Liu, W.-Y.; Qiang, J.; Yin, J.; Li, Y.; Shen, Q.; Zhang, L.; Liang, X.-F.; et al. Space-to-Ground Quantum Key Distribution Using a Small-Sized Payload on Tiangong-2 Space Lab. Chin. Phys. Lett. 2017, 34, 090302. [Google Scholar] [CrossRef]
- Lucamarini, M.; Yuan, Z.L.; Dynes, J.F.; Shields, A.J. Overcoming the rate–distance limit of quantum key distribution without quantum repeaters. Nature 2018, 557, 400–403. [Google Scholar] [CrossRef]
- Minder, M.; Pittaluga, M.; Roberts, G.L.; Lucamarini, M.; Dynes, J.F.; Yuan, Z.L.; Shields, A.J. Experimental quantum key distribution beyond the repeaterless secret key capacity. Nat. Photon. 2019, 13, 334. [Google Scholar] [CrossRef]
- Wang, S.; He, D.-Y.; Yin, Z.-Q.; Lu, F.-Y.; Cui, C.-H.; Chen, W.; Zhou, Z.; Guo, G.-C.; Han, Z.-F. Beating the Fundamental Rate-Distance Limit in a Proof-of-Principle Quantum Key Distribution System. Phys. Rev. X 2019, 9, 021046. [Google Scholar] [CrossRef]
- Liu, Y.; Yu, Z.-W.; Zhang, W.; Guan, J.-Y.; Chen, J.-P.; Zhang, C.; Hu, X.-L.; Li, H.; Jiang, C.; Lin, J.; et al. Experimental Twin-Field Quantum Key Distribution through Sending or Not Sending. Phys. Rev. Lett. 2019, 123, 100505. [Google Scholar] [CrossRef] [PubMed]
- Zhong, X.; Hu, J.; Curty, M.; Qian, L.; Lo, H.-K. Proof-of-Principle Experimental Demonstration of Twin-Field Type Quantum Key Distribution. Phys. Rev. Lett. 2019, 123, 100506. [Google Scholar] [CrossRef] [PubMed]
- Chen, J.-P.; Zhang, C.; Liu, Y.; Jiang, C.; Zhang, W.; Hu, X.-L.; Guan, J.-Y.; Yu, Z.-W.; Xu, H.; Lin, J.; et al. Sending-or-Not-Sending with Independent Lasers: Secure Twin-Field Quantum Key Distribution over 509 km. Phys. Rev. Lett. 2020, 124, 070501. [Google Scholar] [CrossRef] [PubMed]
- Elliott, C. Building the quantum network. New J. Phys. 2002, 4, 46. [Google Scholar] [CrossRef]
- Alléaume, R.; Branciard, C.; Bouda, J.; Debuisschert, T.; Dianati, M.; Gisin, N.; Godfrey, M.; Grangier, P.; Länger, T.; Lütkenhaus, N.; et al. Using quantum key distribution for cryptographic purposes: A survey. Theor. Comput. Sci. 2014, 560, 62–81. [Google Scholar] [CrossRef]
- Hall, M.A.; Altepeter, J.B.; Kumar, P. Ultrafast Switching of Photonic Entanglement. Phys. Rev. Lett. 2011, 106, 053901. [Google Scholar] [CrossRef] [PubMed]
- Lu, J.; Zhou, L.; Kuang, L.-M.; Nori, F. Single-photon router: Coherent control of multichannel scattering for single photons with quantum interferences. Phys. Rev. A 2014, 89, 013805. [Google Scholar] [CrossRef]
- Lemr, K.; Bartkiewicz, K.; Černoch, A.; Soubusta, J. Resource-efficient linear-optical quantum router. Phys. Rev. A 2013, 87, 062333. [Google Scholar] [CrossRef]
- Briegel, H.J.; Dür, W.; Cirac, J.I.; Zoller, P. Quantum repeaters: The role of imperfect local operations in quantum communication. Phys. Rev. Lett. 1998, 81, 5932–5935. [Google Scholar] [CrossRef]
- Bouwmeester, D.; Pan, J.-W.; Mattle, K.; Eibl, M.; Weinfurter, H.; Zeilinger, A. Experimental quantum teleportation. Nature 1997, 390, 575–579. [Google Scholar] [CrossRef]
- Furusawa, A.; Sørensen, J.L.; Braunstein, S.L.; Fuchs, C.A.; Kimble, H.J.; Polzik, E.S. Unconditional Quantum Teleportation. Science 1998, 282, 706–709. [Google Scholar] [CrossRef] [PubMed]
- Pan, J.-W.; Bouwmeester, D.; Weinfurter, H.; Zeilinger, A. Experimental Entanglement Swapping: Entangling Photons That Never Interacted. Phys. Rev. Lett. 1998, 80, 3891. [Google Scholar] [CrossRef]
- RFC 2328—OSPF Version 2. RFC. The Neighborhood of Each Network Node in The Graph Depends on the Network’s Type (Point-To-Point, Broadcast, NBMA Or Point-To-Multipoint) and the Number of Routers Having an Interface to the Network. Available online: https://dl.acm.org/doi/pdf/10.17487/RFC2328 (accessed on 25 March 2021).
- AIT QKD R10 Software. Available online: https://github.com/axdhill/ait-qkd (accessed on 27 June 2016).
- OpenSSL, OpenSSL Project. Available online: onhttps://openssl.org (accessed on 25 March 2021).
- Townsend, P.D. Quantum cryptography on multiuser optical fibre networks. Nature 1997, 385, 47–49. [Google Scholar] [CrossRef]
- Zavitsanos, D.; Ntanos, A.; Giannoulis, G.; Avramopoulos, H. On the QKD Integration in Converged Fiber/Wireless Topologies for Secured, Low-Latency 5G/B5G Fronthaul. Appl. Sci. 2020, 10, 5193. [Google Scholar] [CrossRef]
- Hillery, M.; Bužek, V.; Berthiaume, A. Quantum secret sharing. Phys. Rev. A 1999, 59, 1829. [Google Scholar] [CrossRef]
- Karlsson, A.; Koashi, M.; Imoto, N. Quantum entanglement for secret sharing and secret splitting. Phys. Rev. A 1999, 59, 162. [Google Scholar] [CrossRef]
- Bagherinezhad, S.; Karimipour, V. Quantum secret sharing based on reusable Greenberger-Horne-Zeilinger states as secure carriers. Phys. Rev. A 2003, 67, 044302. [Google Scholar] [CrossRef]
- Guo, G.-P.; Guo, G.-C. Quantum secret sharing without entanglement. Phys. Lett. A 2003, 310, 247–251. [Google Scholar] [CrossRef]
- Liu-Jun, W.; Kai-Yi, Z.; Jia-Yong, W.; Jie, C.; Yong-Hua, Y.; Shi-Biao, T.; Di, Y.; Yan-Lin, T.; Zhen, Z.; Yu, Y.; et al. Experimental Authentication of Quantum Key Distribution with Post-quantum Cryptography. arXiv 2020, arXiv:2009.04662. [Google Scholar]








| Network | DARPA | SECOQC | UQCC | China QKD |
|---|---|---|---|---|
| Project year | 2002–2006 | 2004–2008 | 2010 | 2014–2017 |
| QKD Network type | Active optical switch + Trusted node | Trusted node | Trusted node | Trusted node |
| QKD protocol | BB84 protocol | 5 different QKD protocols | BB84 and BBM92 | BB84 |
| Max. key generating rate | 400 bps over 29 km | 3.1 kbps over 33 km | 304 kpbs over 45 km | 250 kbps over 43 km |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Tsai, C.-W.; Yang, C.-W.; Lin, J.; Chang, Y.-C.; Chang, R.-S. Quantum Key Distribution Networks: Challenges and Future Research Issues in Security. Appl. Sci. 2021, 11, 3767. https://doi.org/10.3390/app11093767
Tsai C-W, Yang C-W, Lin J, Chang Y-C, Chang R-S. Quantum Key Distribution Networks: Challenges and Future Research Issues in Security. Applied Sciences. 2021; 11(9):3767. https://doi.org/10.3390/app11093767
Chicago/Turabian StyleTsai, Chia-Wei, Chun-Wei Yang, Jason Lin, Yao-Chung Chang, and Ruay-Shiung Chang. 2021. "Quantum Key Distribution Networks: Challenges and Future Research Issues in Security" Applied Sciences 11, no. 9: 3767. https://doi.org/10.3390/app11093767
APA StyleTsai, C.-W., Yang, C.-W., Lin, J., Chang, Y.-C., & Chang, R.-S. (2021). Quantum Key Distribution Networks: Challenges and Future Research Issues in Security. Applied Sciences, 11(9), 3767. https://doi.org/10.3390/app11093767









