Evolutionary Game—Theoretic Approach for Analyzing User Privacy Disclosure Behavior in Online Health Communities
Abstract
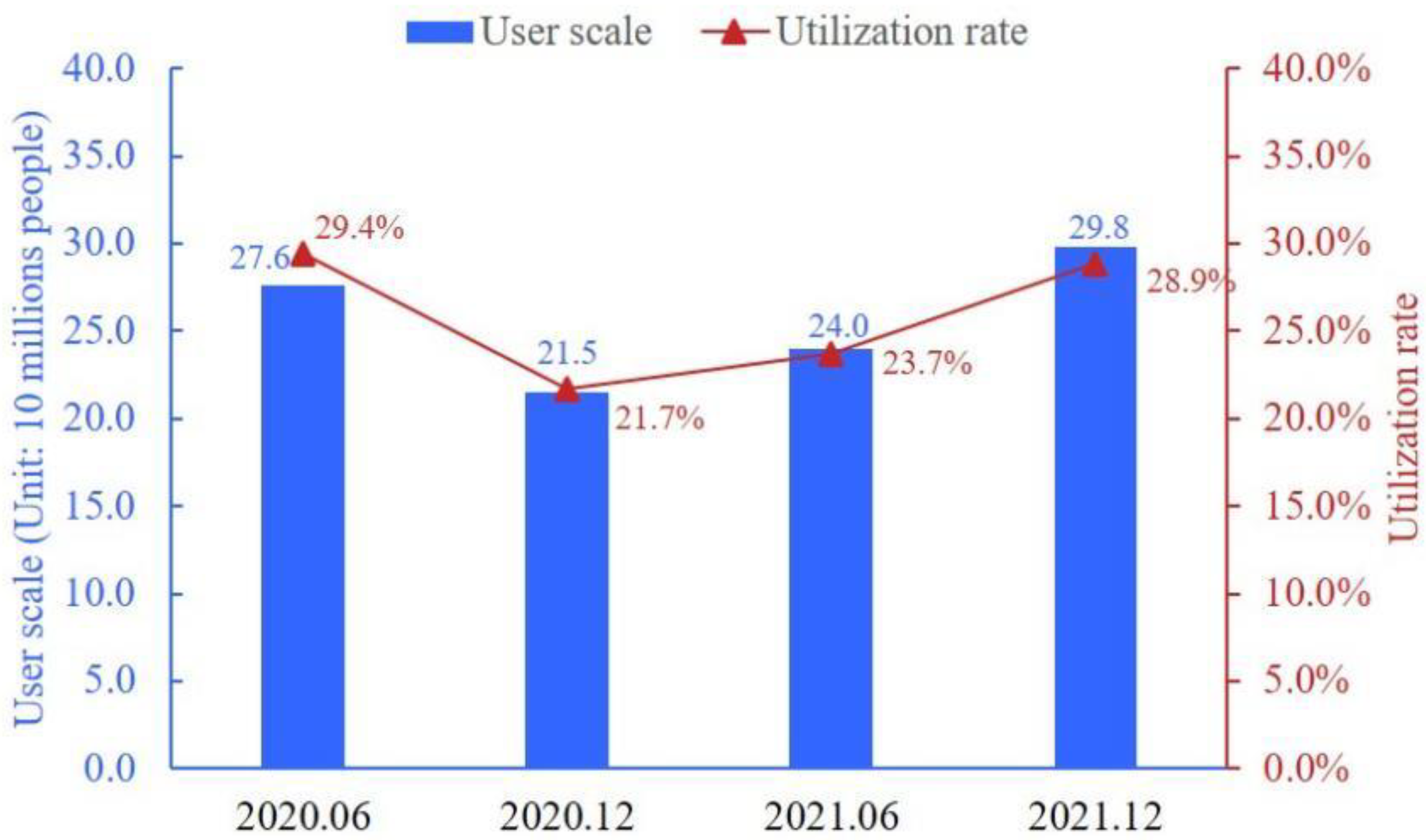
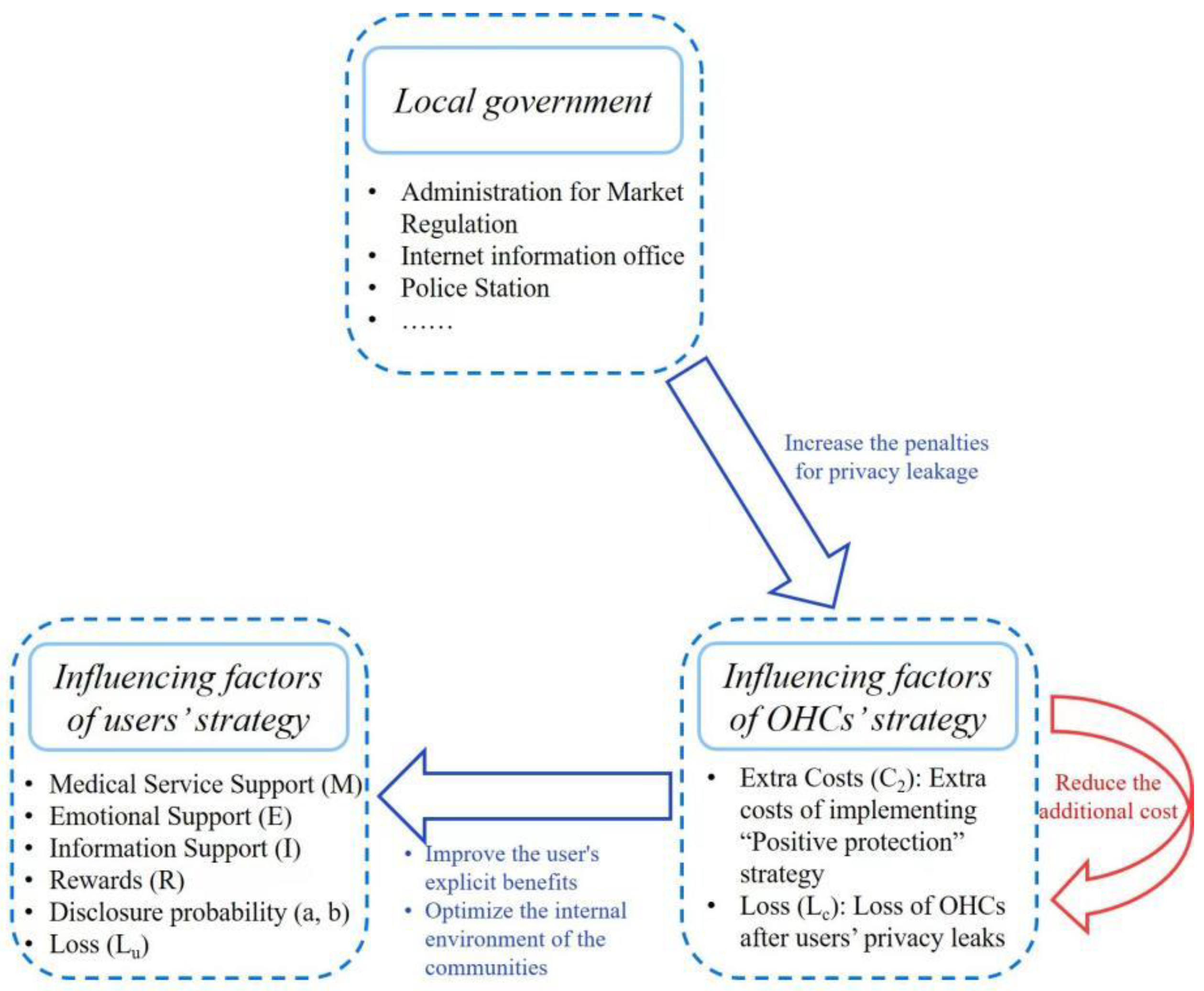
:1. Introduction
2. Literature Review
3. Evolutionary Game Theoretical Model
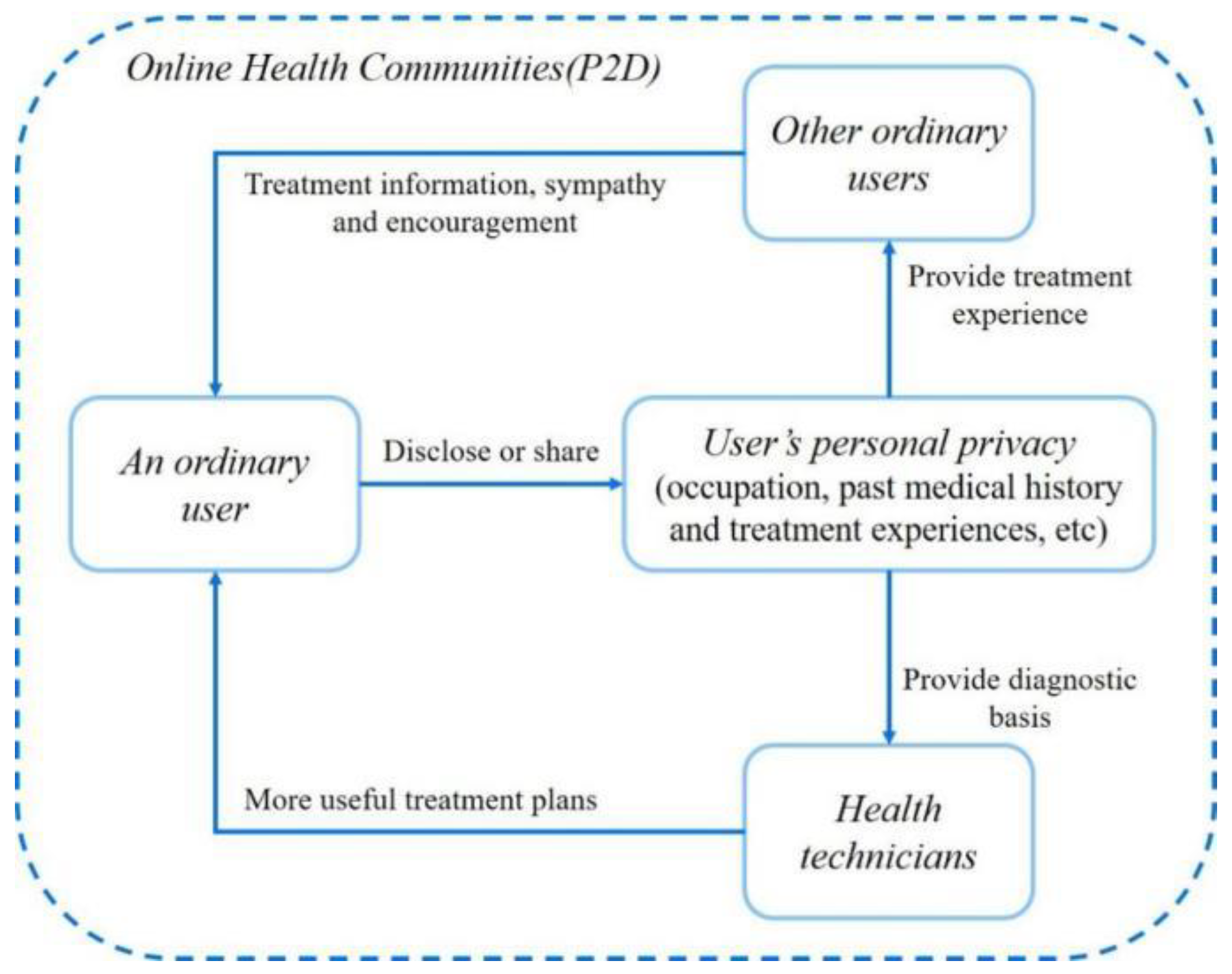
3.1. Problem Description and Model Assumptions
3.2. Model Calculation and Stability Analysis
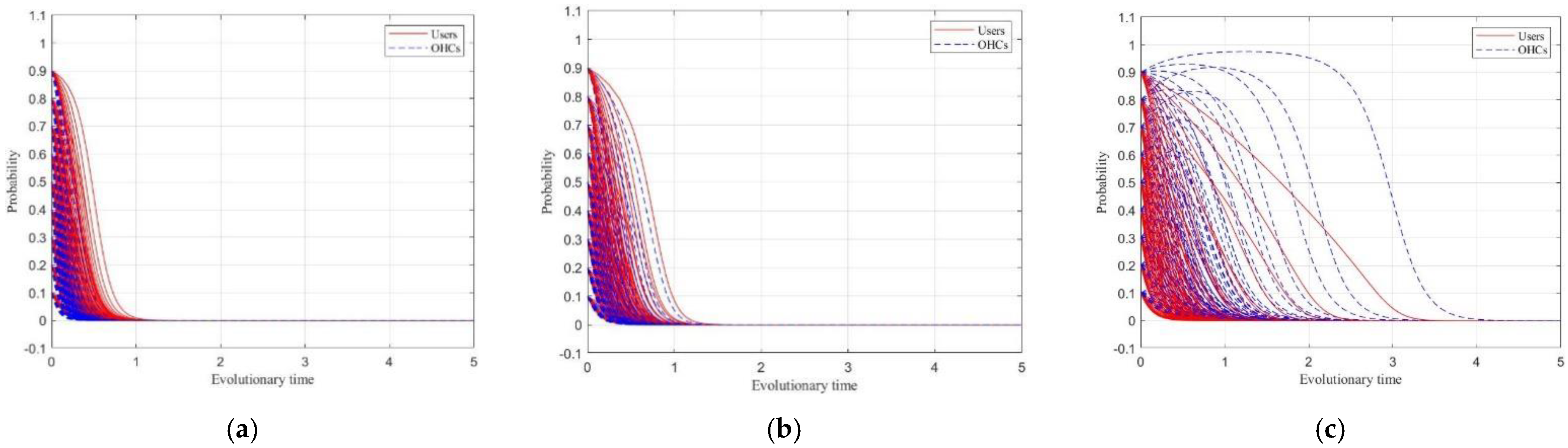
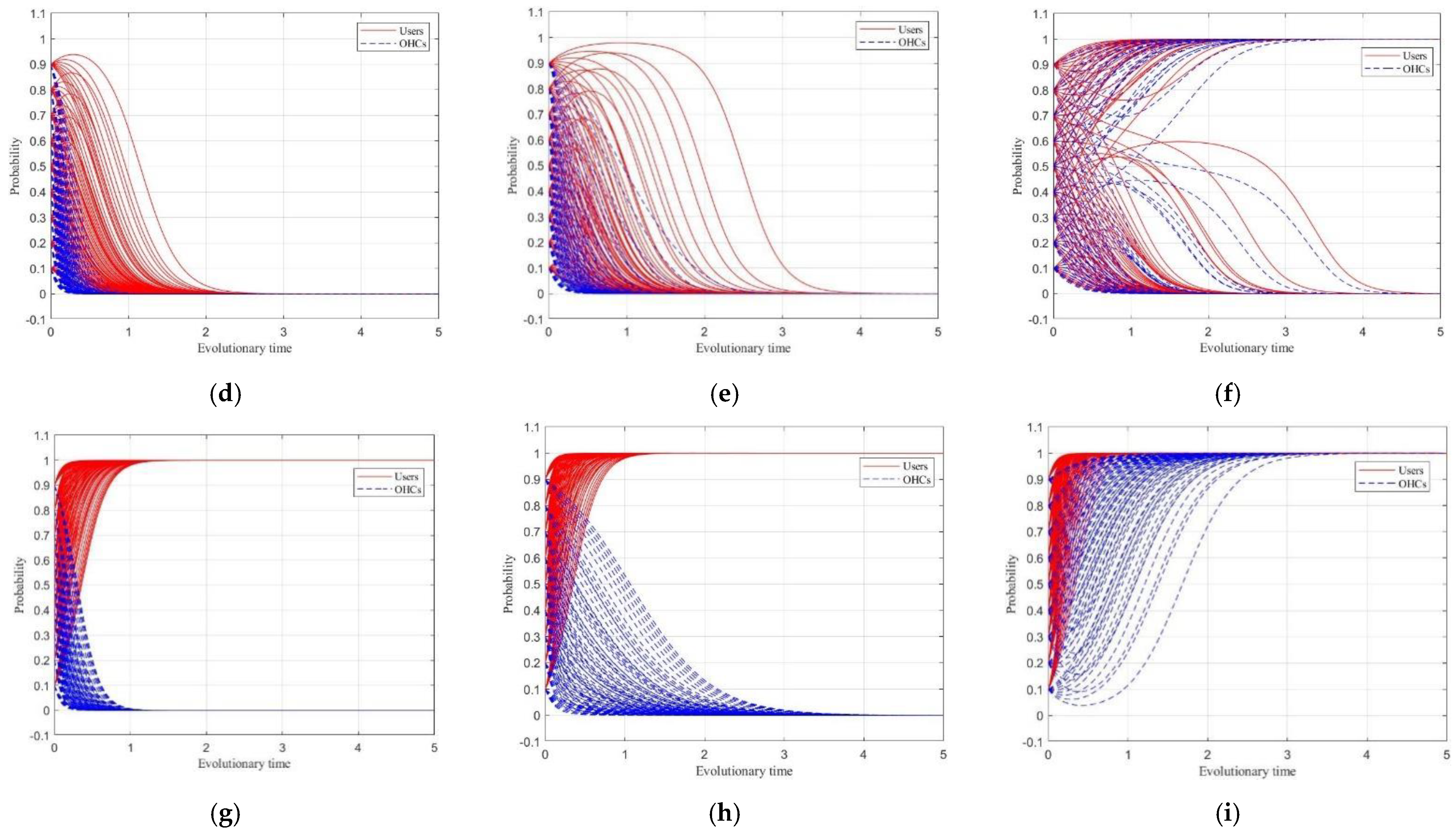
4. Numerical Simulation Experiment
5. Conclusions, Policy Implications, and Future Research
5.1. Conclusions
5.2. Policy Implications
5.3. Future Research
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- National Bureau of Statistics of the People’s Republic of China. Income and Consumption Expenditure of Residents in 2021. Available online: http://www.stats.gov.cn/xxgk/sjfb/zxfb2020/202201/t20220117_1826442.html (accessed on 2 January 2021).
- Yang, H.; Yan, Z.; Jia, L.; Liang, H.G. The impact of team diversity on physician teams’ performance in online health communities. Inform. Process. Manag. 2021, 58, 102421. [Google Scholar] [CrossRef]
- National Bureau of Statistics of the People’s Republic of China. 2021 China Statistical Yearbook; China Statistics Press: Beijing, China, 2021.
- National Bureau of Statistics of the People’s Republic of China. 2020 International Statistical Yearbook; China Statistics Press: Beijing, China, 2021.
- National Bureau of Statistics of the People’s Republic of China. 2021 China Health Statistical Yearbook; Peking Union Medical College Press: Beijing, China, 2021.
- Word Heath Organization. Word Health Statistics 2022: Monitoring Health for the SDGs, Sustainable Development Goals; World Health Organization: Geneva, Switzerland, 2022. [Google Scholar]
- National Bureau of Statistics of the People’s Republic of China. Statistical Bulletin on the Development of Health Care in China in 2020. Available online: http://www.nhc.gov.cn/guihuaxxs/s10743/202107/af8a9c98453c4d9593e07895ae0493c8.shtml (accessed on 5 June 2021).
- Organization for Economic Co-Operation and Development. OECD Health Spending as a Share of GDP, 2005 to 2020 (Estimate). Available online: https://www.oecd.org/els/health-systems/health-expenditure.htm (accessed on 5 June 2021).
- General Office of the State Council of the People’s Republic of China. General Office of the State Council’s Views on Promoting the Development of “Internet Plus Medical Health”. Available online: http://www.gov.cn/zhengce/content/201804/28/content_5286645.htm (accessed on 2 January 2021).
- National Healthcare Security Administration. Guidance from National Healthcare Security Administration on Improving the Price of “Internet Plus” Medical Services and Medical Insurance Payment Policies. Available online: http://www.nhsa.gov.cn/art/2019/8/30/art_37_1707.html (accessed on 2 June 2021).
- Wu, H.; Lu, N.J. Online written consultation, telephone consultation and offline appointment: An examination of the channel effect in online health communities. Int. J. Med. Inform. 2017, 107, 107–119. [Google Scholar] [CrossRef] [PubMed]
- Lei, Y.Q.; Xu, S.H.; Zhou, L.Y. User behaviors and user-generated content in Chinese online health communities: Comparative study. J. Med. Internet Res. 2021, 23, e19183. [Google Scholar] [CrossRef] [PubMed]
- China Internet Network Information Center. Statistics of China’s Internet Development Statistical Report on China’s Internet Development, 48th ed.; China Internet Network Information Center: Beijing, China, 2021; pp. 45–46.
- Zhou, T. Examining users’ knowledge sharing behaviour in online health communities. Data Technol. Appl. 2019, 53, 442–455. [Google Scholar] [CrossRef]
- Zhou, T. Understanding online health community users’ information adoption intention: An elaboration likelihood model perspective. Online Inform. Rev. 2022, 46, 134–146. [Google Scholar] [CrossRef]
- Shamlou, Z.; Saberi, M.K.; Amiri, M.R. Application of theory of planned behavior in identifying factors affecting online health information seeking intention and behavior of women. Aslib J. Inf. Manag. 2022, 74, 727–744. [Google Scholar] [CrossRef]
- Huang, L.; Zhou, J.Y.; Lin, J.C.; Deng, S.L. View analysis of personal information leakage and privacy protection in big data era-based on Q method. Aslib J. Inf. Manag. 2021; ahead of print. [Google Scholar] [CrossRef]
- Naveh, S.; Bronstein, J. Sense making in complex health situations Virtual health communities as sources of information and emotional support. Aslib J. Inf. Manag. 2019, 71, 789–805. [Google Scholar] [CrossRef]
- Zigron, S.; Bronstein, J. “Help is where you find it”: The role of weak ties networks as sources of information and support in virtual health communities. J. Assoc. Inf. Sci. Technol. 2019, 70, 130–139. [Google Scholar] [CrossRef]
- Shao, R.S.; Shi, Z.; Zhang, D. Social Media and Emotional Burnout Regulation During the COVID-19 Pandemic: Multilevel Approach. J. Med. Internet Res. 2021, 23, e27015. [Google Scholar] [CrossRef]
- Sanders, R.; Araujo, T.B.; Vliegenthart, R.; van Eenbergen, M.C.; van Weert, J.; Linn, A.J. Patients’ Convergence of Mass and Interpersonal Communication on an Online Forum: Hybrid Methods Analysis. J. Med. Internet Res. 2020, 22, e18303. [Google Scholar] [CrossRef] [PubMed]
- Peng, Y.X.; Yin, P.P.; Deng, Z.H.; Wang, R.X. Patient-Physician Interaction and Trust in Online Health Community: The Role of Perceived Usefulness of Health Information and Services. Int. J. Envion. Res. Public Health 2020, 17, 139. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Kim, J.; Kim, J.; Collins, C. First impressions in 280 characters or less: Sharing life on Twitter and the mediating role of social presence. Telemat. Inform. 2021, 61, 101596. [Google Scholar] [CrossRef]
- Tang, J.; Akram, U.; Shi, W.J. Why people need privacy? The role of privacy fatigue in app users’ intention to disclose privacy: Based on personality traits. J. Enterp. Inf. Manag. 2021, 34, 1097–1120. [Google Scholar] [CrossRef]
- Mouakket, S. Information self-disclosure on mobile instant messaging applications Uses and gratifications perspective. J. Enterp. Inf. Manag. 2019, 32, 98–117. [Google Scholar] [CrossRef]
- Brandtzaeg, P.B.; Pultier, A.; Moen, G.M. Losing Control to Data-Hungry Apps: A Mixed-Methods Approach to Mobile App Privacy. Soc. Sci. Comput. Rev. 2019, 37, 466–488. [Google Scholar] [CrossRef] [Green Version]
- Wang, W.T.; Ou, W.M.; Chiu, W.C. Autonomous Motivation and Self-Disclosure Intention: An ISS Perspective. J. Organ. End User Comput. 2021, 33, 1–27. [Google Scholar] [CrossRef]
- Lin, C.Y.; Chou, E.Y.; Huang, H.C. They support, so we talk: The effects of other users on self-disclosure on social networking sites. Inf. Technol. People 2021, 34, 1039–1064. [Google Scholar] [CrossRef]
- Liu, Z.L.; Wang, X.Q.; Liu, J. How digital natives make their self-disclosure decisions: A cross-cultural comparison. Inf. Technol. People 2019, 32, 538–558. [Google Scholar] [CrossRef]
- Thompson, N.; Brindley, J. Who are you talking about? Contrasting determinants of online disclosure about self or others. Inf. Technol. People 2021, 34, 999–1017. [Google Scholar] [CrossRef]
- Sun, Y.Q.; Zhang, F.; Feng, Y.F. Do individuals disclose or withhold information following the same logic: A configurational perspective of information disclosure in social media. Aslib J. Inf. Manag. 2022, 74, 710–726. [Google Scholar] [CrossRef]
- Ashuri, T.; Dvir-Gvisman, S.; Halperin, R. Watching Me Watching You: How Observational Learning Affects Self-disclosure on Social Network Sites? J. Comput.-Mediat. Commun. 2018, 23, 34–68. [Google Scholar] [CrossRef] [Green Version]
- Li, K.; Cheng, L.Q.; Teng, C.I. Voluntary sharing and mandatory provision: Private information disclosure on social networking sites. Inform. Process. Manag. 2020, 57, 102128. [Google Scholar] [CrossRef]
- Liu, B.L.; Pavlou, P.A.; Cheng, X.F. Achieving a Balance Between Privacy Protection and Data Collection: A Field Experimental Examination of a Theory-Driven Information Technology Solution. Inf. Syst. Res. 2021, 33, 203–223. [Google Scholar] [CrossRef]
- Gomez-Barroso, J.L. Feel free to use my personal data: An experiment on disclosure behavior when shopping online. Online Inform. Rev. 2021, 45, 537–547. [Google Scholar] [CrossRef]
- Alaqra, A.S.; Fischer-Hubner, S.; Framner, E. Enhancing Privacy Controls for Patients via a Selective Authentic Electronic Health Record Exchange Service: Qualitative Study of Perspectives by Medical Professionals and Patients. J. Med. Internet Res. 2018, 20, e10954. [Google Scholar] [CrossRef]
- Esmaeilzadeh, P. The Impacts of the Perceived Transparency of Privacy Policies and Trust in Providers for Building Trust in Health Information Exchange: Empirical Study. JMIR Med. Inf. 2019, 7, 300–324. [Google Scholar] [CrossRef] [Green Version]
- Robinson, S.C. No exchange, same pain, no gain: Risk-reward of wearable healthcare disclosure of health personally identifiable information for enhanced pain treatment. Health Inform. J. 2019, 25, 1675–1691. [Google Scholar] [CrossRef] [Green Version]
- Zhang, X.; Liu, S.; Chen, X.; Wang, L.; Gao, B.J.; Zhu, Q. Health information privacy concerns, antecedents, and information disclosure intention in online health communities. Inform. Manag.-Amster. 2018, 55, 482–493. [Google Scholar] [CrossRef]
- Wang, X.Y.; Parameswaran, S.; Bagul, D.M.; Kishore, R. Can online social support be detrimental in stigmatized chronic diseases? A quadratic model of the effects of informational and emotional support on self-care behavior of HIV patients. J. Am. Med. Inform. Assn. 2018, 25, 931–944. [Google Scholar] [CrossRef] [Green Version]
- Hur, I.; Cousins, K.C.; Stahl, B.C. A critical perspective of engagement in online health communities. Eur. J. Inform. Syst. 2019, 28, 523–548. [Google Scholar] [CrossRef]
- Zhou, J.J. Factors influencing people’s personal information disclosure behaviors in online health communities: A pilot study. Asia-Pac. J. Public Health 2018, 30, 286–295. [Google Scholar] [CrossRef] [PubMed]
- Fox, G.; van der Werff, L.; Rosati, P.; Endo, P.T.; Lynn, T. Examining the determinants of acceptance and use of mobile contact tracing applications in Brazil: An extended privacy calculus perspective. J. Assoc. Inf. Sci. Technol. 2021, 73, 944–967. [Google Scholar] [CrossRef]
- Shaw, N.; Sergueeva, K. The non-monetary benefits of mobile commerce: Extending UTAUT2 with perceived value. Int. J. Inf. Manag. 2019, 45, 44–55. [Google Scholar] [CrossRef]
- Robillard, J.M.; Feng, T.L.; Sporn, A.B.; Lai, J.A.; Lo, C.; Ta, M.; Nadler, R. Availability, readability, and content of privacy policies and terms of agreements of mental health apps. Internet Interv. 2019, 17, 100243. [Google Scholar] [CrossRef]
- Chen, H.; Chen, H.T. The role of social network sites on the relationship between game users and developers: An evolutionary game analysis of virtual goods. Inf. Technol. Manag. 2021, 22, 67–81. [Google Scholar] [CrossRef]
- Wang, L.; Schuetz, C.G.; Cai, D.H. Choosing Response Strategies in Social Media Crisis Communication: An Evolutionary Game Theory Perspective. Inform. Manag.-Amster. 2021, 58, 103371. [Google Scholar] [CrossRef]
- Zhu, G.; Liu, H.; Feng, M.N. An Evolutionary Game-Theoretic Approach for Assessing Privacy Protection in mHealth Systems. Int. J. Env. Res. Public Health 2018, 15, 2196. [Google Scholar] [CrossRef] [Green Version]
- Friedman, D. On economic applications of evolutionary game theory. J. Evol. Econ. 1998, 8, 15–43. [Google Scholar] [CrossRef] [Green Version]
- Chen, X.H.; Cao, J.; Sanjay, K. Government regulation and enterprise decision in China remanufacturing industry: Evidence from evolutionary game theory. Energ. Ecol. Environ. 2021, 6, 148–159. [Google Scholar] [CrossRef]
- Lv, Y.Q.; Ma, G.J.; Ding, J. Evolutionary Game Analysis of Medical Waste Disposal in China under Different Reward and Penalty Models. Sustainability 2022, 14, 4658. [Google Scholar] [CrossRef]
- Zhu, G.; Liu, H.; Feng, M.N. Sustainability of Information Security Investment in Online Social Networks: An Evolutionary Game-Theoretic Approach. Mathematics 2018, 6, 177. [Google Scholar] [CrossRef] [Green Version]
- Li, M.Y.; Gao, X. Implementation of enterprises’ green technology innovation under market-based environmental regulation: An evolutionary game approach. J. Environ. Manag. 2022, 308, 114750. [Google Scholar] [CrossRef] [PubMed]
- Personal Information Protection Law of the People’s Republic of China. Available online: http://www.npc.gov.cn/npc/c30834/202108/a8c4e3672c74491a80b53a172bb753fe.shtml (accessed on 3 March 2022).


| Notation | Description |
|---|---|
| M | Medical service support obtained by users after disclosing their personal information, |
| E | Emotional support obtained by users after disclosing their personal information, |
| I | Information support obtained by users after disclosing their personal information, |
| Loss of users after their privacy leaks, | |
| Loss of OHCs after users’ privacy leaks, | |
| Rewards from the OHCs after users disclose their personal information, | |
| Costs of implementing the “negative protection” strategy in the OHCs, | |
| Extra costs of implementing the “positive protection” strategy in the OHCs, | |
| B | Benefits of user disclosure of personal information for OHCs influence, |
| a | Probability of users disclosing personal information to medical personnel, |
| b | Probability of users disclosing personal information to other ordinary users, |
| c | Probability of privacy leakage under the “positive protection” strategy, |
| d | Probability of privacy leakage under the “negative protection” strategy, |
| Online Health Communities | |||
|---|---|---|---|
| Positive Protection | Positive Protection | ||
| Users | Disclosure | ||
| Non-disclosure | |||
| Equilibrium Points | ||
|---|---|---|
| D1 (0, 0) | ||
| D2 (1, 0) | ||
| D3 (0, 1) | ||
| D4 (1, 1) | ||
| D5 (x*, y*) | 0 |
| Scenario | Conditions | Determinant | Equilibrium Point | ||||
|---|---|---|---|---|---|---|---|
| (0, 0) | (1, 0) | (0, 1) | (1, 1) | (x*, y*) | |||
| 1 | |||||||
| 0 | |||||||
| Stability | ESS | Saddle point | Saddle point | Unstable point | Center point | ||
| 2 | |||||||
| 0 | |||||||
| Stability | ESS | Saddle point | Saddle point | Unstable point | Center point | ||
| 3 | |||||||
| 0 | |||||||
| Stability | ESS | Unstable point | Saddle point | Saddle point | Center point | ||
| 4 | |||||||
| 0 | |||||||
| Stability | ESS | Saddle point | Unstable point | Saddle point | Center point | ||
| 5 | |||||||
| 0 | |||||||
| Stability | ESS | Saddle point | Unstable point | Saddle point | Center point | ||
| 6 | |||||||
| 0 | |||||||
| Stability | ESS | Unstable point | Unstable point | ESS | Center point | ||
| 7 | |||||||
| 0 | |||||||
| Stability | Saddle point | ESS | Unstable point | Saddle point | Center point | ||
| 8 | |||||||
| 0 | |||||||
| Stability | Saddle point | ESS | Unstable point | Saddle point | Center point | ||
| 9 | |||||||
| 0 | |||||||
| Stability | Saddle point | Saddle point | Unstable point | ESS | Center point | ||
| Scenario | ||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1 | 5 | 2.5 | 1.5 | 1 | 0.6 | 0.4 | 5 | 5 | 20 | 20 | 10 | 15 | 0.3 | 0.7 |
| 2 | 5 | 2.5 | 1.5 | 1 | 0.6 | 0.4 | 5 | 5 | 20 | 20 | 10 | 10 | 0.3 | 0.7 |
| 3 | 5 | 2.5 | 1.5 | 1 | 0.6 | 0.4 | 5 | 5 | 20 | 20 | 10 | 5 | 0.3 | 0.7 |
| 4 | 10 | 5 | 3 | 2 | 0.6 | 0.4 | 10 | 5 | 20 | 20 | 10 | 15 | 0.3 | 0.7 |
| 5 | 10 | 5 | 3 | 2 | 0.6 | 0.4 | 10 | 5 | 20 | 20 | 10 | 10 | 0.3 | 0.7 |
| 6 | 10 | 5 | 3 | 2 | 0.6 | 0.4 | 10 | 5 | 20 | 20 | 10 | 5 | 0.3 | 0.7 |
| 7 | 20 | 10 | 6 | 4 | 0.6 | 0.4 | 20 | 5 | 20 | 20 | 10 | 15 | 0.3 | 0.7 |
| 8 | 20 | 10 | 6 | 4 | 0.6 | 0.4 | 20 | 5 | 20 | 20 | 10 | 10 | 0.3 | 0.7 |
| 9 | 20 | 10 | 6 | 4 | 0.6 | 0.4 | 20 | 5 | 20 | 20 | 10 | 5 | 0.3 | 0.7 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Xu, Z.; Chen, X.; Hong, Y. Evolutionary Game—Theoretic Approach for Analyzing User Privacy Disclosure Behavior in Online Health Communities. Appl. Sci. 2022, 12, 6603. https://doi.org/10.3390/app12136603
Xu Z, Chen X, Hong Y. Evolutionary Game—Theoretic Approach for Analyzing User Privacy Disclosure Behavior in Online Health Communities. Applied Sciences. 2022; 12(13):6603. https://doi.org/10.3390/app12136603
Chicago/Turabian StyleXu, Zhongyang, Xihui Chen, and Yuanxiao Hong. 2022. "Evolutionary Game—Theoretic Approach for Analyzing User Privacy Disclosure Behavior in Online Health Communities" Applied Sciences 12, no. 13: 6603. https://doi.org/10.3390/app12136603







