LogInjector: Detecting Web Application Log Injection Vulnerabilities
Abstract
:1. Introduction
- There are many web interfaces in web applications that interact with users. However, only a few can inject data into the log, so it is challenging to accurately find the log-injectable interfaces.
- The log injection vulnerabilities need to be triggered by accessing the view–logs interface of the web application, and it is difficult to identify the view–logs interface.
- Each web application has a different input-filtering check. It is challenging to pass the application-specific input-filtering checks of the web application and to ensure that the injected data can be executed.
- We systematically studied the web application log injection vulnerabilities for the first time and proposed LogInjector, an effective web application log injection vulnerability-detection method;
- LogInjector can automatically obtain the log storage location, the log-injectable interfaces, and the view–logs interfaces. Based on this information, LogInjector employs dynamic testing based on the feedback-guided mutation to detect log injection vulnerabilities effectively;
- We implemented a prototype of LogInjector and evaluated the effectiveness of LogInjector on 14 web applications. LogInjector detected a total of 16 log injection vulnerabilities, including 6 zero-day vulnerabilities.
2. Background
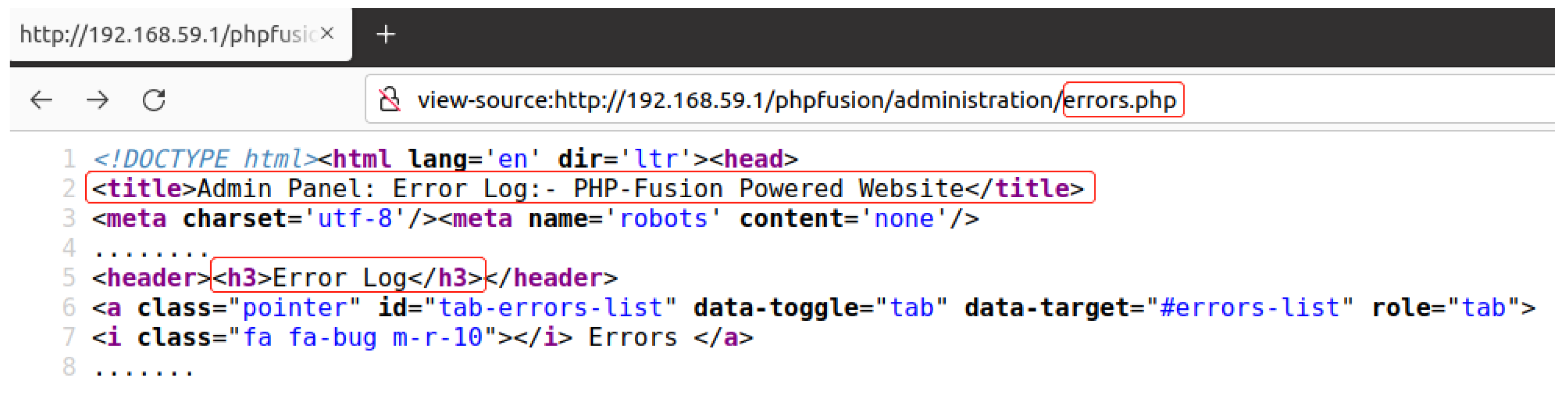
2.1. A Motivating Example
| Listing 1. PHPFusion logs the error message. |
 |
| Listing 2. Display of error log information. |
 |
2.2. Investigating Known Log Injection Vulnerabilities
2.3. Vulnerability Conditions
- (1)
- There is user-controllable input that can be written to the log. A log injection vulnerability must have a user-controlled input source that can write to the log.
- (2)
- It must has a view–logs interface. For the payload injected into the log, it is necessary to access the view–logs interface to execute the payload to trigger the vulnerability.
- (3)
- The injected malicious data can pass the input-filter checks of the web application and retain the execution semantics. A log injection vulnerability exists only if the payload can be stored in the log and the payload can be executed.
3. Related Work
3.1. First-Order Vulnerability Analysis
3.2. Second-Order Vulnerability Analysis
4. Overview
4.1. Finding of Log-Injectable Interfaces
4.2. Identification of View–Logs Interfaces
4.3. Dynamic Testing of Feedback-Guided Mutations
5. Design
5.1. Finding Log-Injectable Interfaces
5.2. Identification of View–Logs Interfaces
- (1)
- The url contains keywords such as log, error;
- (2)
- The HTML <title> tag contains keywords such as log, error;
- (3)
- Tags such as <a>, <h>, and <span> in the HTML of the web page contain keywords such as log, error.
5.3. Dynamic Testing of Feedback-Guided Mutations
5.3.1. Workflow
| Algorithm 1 Dynamic Testing Algorithm Based on Feedback-Guided Mutation. |
|
5.3.2. Initial Inputs
5.3.3. Mutation Operations
5.3.4. Feedback
5.3.5. Vulnerability Verification
6. Evaluation
6.1. Experiment Setup
6.1.1. Experiment Dataset
6.1.2. Test Environment
6.2. Effectiveness
6.2.1. Known Vulnerabilities Verification
6.2.2. Zero-Day Vulnerability Detection
6.3. Comparison with Existing Work
- The input constructed by Black Widow cannot be written to the log;
- The set of test cases injected by Black Widow is limited, and even if the log is written, it does not have execution semantics. The injected data cannot be executed;
- Black Widow injected a payload with code execution semantics, but did not identify the view-logs interface and failed to trigger the vulnerability.
6.4. Discussion
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| DOM | Document Object Model |
| CNVD | China National Vulnerability Database |
| XSS | Cross-site scripting |
| RCE | Remote code execution |
| OWASP | Open Web Application Security Project |
References
- Home—Official Home of the PHPFusion CMS. Available online: https://www.php-fusion.co.uk/ (accessed on 1 June 2022).
- CVE—CVE-2020-17449. Available online: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-17449 (accessed on 1 June 2022).
- Contao Open Source CMS—Contao. Available online: https://contao.org/ (accessed on 1 June 2022).
- Webmin. Available online: https://www.webmin.com/ (accessed on 1 June 2022).
- Log Injection Software Attack|OWASP Foundation. Available online: https://owasp.org/www-community/attacks/Log_Injection (accessed on 1 June 2022).
- Jovanovic, N.; Kruegel, C.; Kirda, E. Static analysis for detecting taint-style vulnerabilities in web applications. J. Comput. Secur. 2010, 18, 861–907. [Google Scholar] [CrossRef] [Green Version]
- Appelt, D.; Nguyen, C.D.; Briand, L.C.; Alshahwan, N. Automated testing for SQL injection vulnerabilities: An input mutation approach. In Proceedings of the 2014 International Symposium on Software Testing and Analysis, San Jose, CA, USA, 21–25 July 2014; pp. 259–269. [Google Scholar]
- Backes, M.; Rieck, K.; Skoruppa, M.; Stock, B.; Yamaguchi, F. Efficient and flexible discovery of php application vulnerabilities. In Proceedings of the 2017 IEEE European Symposium on Security and Privacy (EuroS&P), Paris, France, 26–28 July 2017; pp. 334–349. [Google Scholar]
- Fang, Y.; Li, Y.; Liu, L.; Huang, C. DeepXSS: Cross site scripting detection based on deep learning. In Proceedings of the 2018 International Conference on Computing and Artificial Intelligence, Chengdu, China, 12–14 March 2018; pp. 47–51. [Google Scholar]
- Tang, P.; Qiu, W.; Huang, Z.; Lian, H.; Liu, G. Detection of SQL injection based on artificial neural network. Knowl.-Based Syst. 2020, 190, 105528. [Google Scholar] [CrossRef]
- Van Rooij, O.; Charalambous, M.A.; Kaizer, D.; Papaevripides, M.; Athanasopoulos, E. webFuzz: Grey-Box Fuzzing for Web Applications. In Computer Security—ESORICS 2021; Bertino, E., Shulman, H., Waidner, M., Eds.; Springer International Publishing: Cham, Switzerland, 2021; pp. 152–172. [Google Scholar]
- Erdődi, L.; Sommervoll, Å.Å.; Zennaro, F.M. Simulating SQL injection vulnerability exploitation using Q-learning reinforcement learning agents. J. Inf. Secur. Appl. 2021, 61, 102903. [Google Scholar] [CrossRef]
- Liu, Z.; Fang, Y.; Huang, C.; Xu, Y. GAXSS: Effective Payload Generation Method to Detect XSS Vulnerabilities Based on Genetic Algorithm. Secur. Commun. Netw. 2022, 2022, 2031924. [Google Scholar] [CrossRef]
- Lee, S.; Wi, S.; Son, S. Link: Black-Box Detection of Cross-Site Scripting Vulnerabilities Using Reinforcement Learning. In Proceedings of the ACM Web Conference, Lyon, France, 25–29 April 2022; pp. 743–754. [Google Scholar]
- Zhao, J.; Lu, Y.; Zhu, K.; Chen, Z.; Huang, H. Cefuzz: An Directed Fuzzing Framework for PHP RCE Vulnerability. Electronics 2022, 11, 758. [Google Scholar] [CrossRef]
- Balzarotti, D.; Cova, M.; Felmetsger, V.V.; Vigna, G. Multi-module vulnerability analysis of web-based applications. In Proceedings of the 14th ACM Conference on Computer and Communications Security, Alexandria, VA, USA, 28–31 October 2007; pp. 25–35. [Google Scholar]
- Dahse, J.; Holz, T. Static Detection of Second-Order Vulnerabilities in Web Applications. In Proceedings of the 23rd USENIX Security Symposium (USENIX Security 14), San Diego, CA, USA, 20–22 August 2014; pp. 989–1003. [Google Scholar]
- Olivo, O.; Dillig, I.; Lin, C. Detecting and exploiting second order denial-of-service vulnerabilities in web applications. In Proceedings of the 22nd ACM SIGSAC Conference on Computer and Communications Security, Denver, CO, USA, 12–16 October 2015; pp. 616–628. [Google Scholar]
- Yan, L.; Li, X.; Feng, R.; Feng, Z.; Hu, J. Detection method of the second-order SQL injection in Web applications. In Proceedings of the International Workshop on Structured Object-Oriented Formal Language and Method, Queenstown, New Zealand, 29 October 2013; Springer: Berlin/Heidelberg, Germany, 2013; pp. 154–165. [Google Scholar]
- Suto, L.; San, C. Analyzing the Accuracy and Time Costs of Web Application Security Scanners. Appl. Secur. 2010, 187, 64. [Google Scholar]
- Bau, J.; Bursztein, E.; Gupta, D.; Mitchell, J. State of the art: Automated black-box web application vulnerability testing. In Proceedings of the 2010 IEEE Symposium on Security and Privacy, Oakland, CA, USA, 16–19 May 2010; pp. 332–345. [Google Scholar]
- Vieira, M.; Antunes, N.; Madeira, H. Using web security scanners to detect vulnerabilities in web services. In Proceedings of the IEEE/IFIP International Conference on Dependable Systems & Networks, Lisbon, Portugal, 2 July 2009; pp. 566–571. [Google Scholar]
- Doupé, A.; Cova, M.; Vigna, G. Why Johnny can’t pentest: An analysis of black-box web vulnerability scanners. In Proceedings of the International Conference on Detection of Intrusions and Malware, and Vulnerability Assessment, Bonn, Germany, 8–9 July 2010; Springer: Berlin/Heidelberg, Germany, 2010; pp. 111–131. [Google Scholar]
- Parvez, M.; Zavarsky, P.; Khoury, N. Analysis of effectiveness of black-box web application scanners in detection of stored SQL injection and stored XSS vulnerabilities. In Proceedings of the 2015 10th International Conference for Internet Technology and Secured Transactions (ICITST), London, UK, 14–16 December 2015; pp. 186–191. [Google Scholar]
- MCaLlister, S.; KirDa, E.; Kruegel, C. Leveraging User Interactions for In-Depth Testing of Web Applications. In Proceedings of the International Symposium on Recent Advances in Intrusion Detection, Cambridge, MA, USA, 15–17 September 2008. [Google Scholar]
- Doupé, A.; Cavedon, L.; Kruegel, C.; Vigna, G. Enemy of the State: A {State-Aware}{Black-Box} Web Vulnerability Scanner. In Proceedings of the 21st USENIX Security Symposium (USENIX Security 12), Bellevue, WA, USA, 8–10 August 2012; pp. 523–538. [Google Scholar]
- Duchene, F.; Rawat, S.; Richier, J.L.; Groz, R. KameleonFuzz: Evolutionary fuzzing for black-box XSS detection. In Proceedings of the 4th ACM Conference on Data and Application Security and Privacy, San Antonio, TX, USA, 3–5 March 2014; pp. 37–48. [Google Scholar]
- Steinhauser, A.; Ta, P. Database traffic interception for graybox detection of stored and context-sensitive XSS. Digit. Threat. Res. Pract. 2020, 1, 1–23. [Google Scholar] [CrossRef]
- Eriksson, B.; Pellegrino, G.; Sabelfeld, A. Black Widow: Blackbox Data-driven Web Scanning. In Proceedings of the 2021 IEEE Symposium on Security and Privacy (SP), San Francisco, CA, USA, 24–27 May 2021; pp. 1125–1142. [Google Scholar] [CrossRef]
- Alkhalaf, M.A. Automatic Detection and Repair of Input Validation and Sanitization Bugs; University of California: Santa Barbara, CA, USA, 2014. [Google Scholar]
- Chin, E.; Wagner, D. Efficient character-level taint tracking for Java. In Proceedings of the 2009 ACM Workshop on Secure Web Services, Chicago, IL, USA, 13 November 2009; pp. 3–12. [Google Scholar]
- Bisht, P.; Madhusudan, P.; Venkatakrishnan, V. CANDID: Dynamic candidate evaluations for automatic prevention of SQL injection attacks. ACM Trans. Inf. Syst. Secur. (TISSEC) 2010, 13, 1–39. [Google Scholar] [CrossRef]
- Bulekov, A.; Jahanshahi, R.; Egele, M. Saphire: Sandboxing {PHP} Applications with Tailored System Call Allowlists. In Proceedings of the 30th USENIX Security Symposium (USENIX Security 21), Virtual, CA, USA, 11–13 August 2021; pp. 2881–2898. [Google Scholar]
- Qianlitp/Crawlergo: A Powerful Browser Crawler for Web Vulnerability Scanners. Available online: https://github.com/Qianlitp/crawlergo (accessed on 1 June 2022).
- History API—Web APIs | MDN. Available online: https://developer.mozilla.org/en-US/docs/Web/API/History_API (accessed on 1 June 2022).
- setTimeout()—Web APIs | MDN. Available online: https://developer.mozilla.org/en-US/docs/Web/API/setTimeout (accessed on 1 June 2022).
- html5lib/html5lib-Python: Standards-Compliant Library for Parsing and Serializing HTML Documents and Fragments in Python. Available online: https://github.com/html5lib/html5lib-PYTHON (accessed on 1 June 2022).
- Easy Digital Downloads—Simple eCommerce for Selling Digital Files—WordPress plugin | WordPress.org. Available online: https://wordpress.org/plugins/easy-digital-downloads/ (accessed on 1 June 2022).
- SuiteCRM—Open Source CRM Software Application for Businesses. Available online: https://suitecrm.com/ (accessed on 1 June 2022).
- Zen Cart Support—Zen Cart™—Putting the Dream of Your Own Business within Reach of Anyone! Available online: https://www.zen-cart.com/ (accessed on 1 June 2022).
- Free Shopping Cart Application and Open Source Ecommerce Solution. Available online: https://www.abantecart.com/ (accessed on 1 June 2022).
- Maxsite CMS. Available online: https://max-3000.com/ (accessed on 1 June 2022).
- DSGVO All in one for WP—WordPress Plugin | WordPress.org. Available online: https://wordpress.org/plugins/dsgvo-all-in-one-for-wp/ (accessed on 1 June 2022).
- WP Photo Album Plus—WordPress Plugin | WordPress.org. Available online: https://wordpress.org/plugins/wp-photo-album-plus/ (accessed on 1 June 2022).
- FREE Shopping Cart and Open Source eCommerce Platform—Start Selling Online for Free. Available online: https://www.oscommerce.com/ (accessed on 1 June 2022).
- Better WordPress Google XML Sitemaps (Support Sitemap Index, Multi-Site and Google News)—WordPress Plugin | WordPress.org. Available online: https://wordpress.org/plugins/bwp-google-xml-sitemaps/ (accessed on 1 June 2022).
- CE Phoenix Cart, Free Open Source Shopping Cart | CE Phoenix Cart. Available online: https://phoenixcart.org/ (accessed on 1 June 2022).
- Anagandula, K.; Zavarsky, P. An Analysis of Effectiveness of Black-Box Web Application Scanners in Detection of Stored SQL Injection and Stored XSS Vulnerabilities. In Proceedings of the 2020 3rd International Conference on Data Intelligence and Security (ICDIS), South Padre Island, TX, USA, 24–26 June 2020; pp. 40–48. [Google Scholar]
- Cache Poisoning | OWASP Foundation. Available online: https://owasp.org/www-community/attacks/Cache_Poisoning (accessed on 1 June 2022).
- What is HTTP Request Smuggling? Tutorial & Examples|Web Security Academy. Available online: https://portswigger.net/web-security/request-smuggling (accessed on 1 June 2022).

| Research Focus | Research Articles | Approach | Advantages | Disadvantages |
|---|---|---|---|---|
| First-order vulnerabilities | Jovanovic et al. [6] (2010) | Data flow analysis | Supports alias analysis | High false positives Misses dynamic features |
| Appelt et al. [7] (2014) | Input mutation | Bypasses web application firewalls | Limited mutation operations | |
| Backes et al. [8] (2017) | Code property graph | Detects vulnerabilities based on graph queries | False positives exist Misses dynamic features | |
| Fang et al. [9] (2018) | Deep learning | Extracts the features of XSS payloads | False negatives exist | |
| Tang et al. [10] (2020) | Neural network | Bypasses web application firewalls | Misses context analyses | |
| Van Rooij et al. [11] (2021) | Coverage-based greybox fuzzing | High coverage | Limited mutation operations Only detects reflected XSS | |
| Erdődi et al. [12] (2021) | Reinforcement learning | Supports autonomous penetration testing | Only works with simple CTF challenges | |
| Liu et al. [13] (2022) | Genetic algorithm | Generates effective XSS payloads | Lacks adaptive capability | |
| Lee et al. [14] (2022) | Reinforcement learning | Supports output context analyses | Only detects reflected XSS | |
| Zhao et al. [15] (2022) | Directed fuzzing | Has an effective mutation strategy | Only detects first-order RCE | |
| Second-order vulnerabilities | Balzarotti et al. [16] (2007) | Data flow analysis | Identifies sophisticated multi-module vulnerabilities | Does not support multi-step exploits |
| McAllister et al. [25] (2008) | Black-box dynamic | Explores larger application parts | Does not support inter-state dependency analysis | |
| Doupé et al. [26] (2012) | State-aware black box | Explores more application code | Misses complex workflows and inter-state dependencies | |
| Duchene et al. [27] (2014) | Black box dynamic Genetic algorithm | No false positives | Requires the ability to reset the application | |
| Dahse et al. [17] (2014) | Taint analysis | Models the data flow through persistent data stores | High false positives | |
| Yan et al. [19] (2014) | Combines with static and dynamic analysis | Reduces false positives | Only detects second-order SQLi | |
| Olivo et al. [18] (2015) | Symbolic execution | Supports generating candidate attack vectors | Only detects second-order DoS | |
| Steinhauser et al. [28] (2020) | Graybox dynamic | Intercepts database traffic to identify vulnerabilities | Only detects stored XSS | |
| Eriksson et al. [29] (2021) | Black box data-driven | Supports inter-state dependency analysis | Only detects stored XSS |
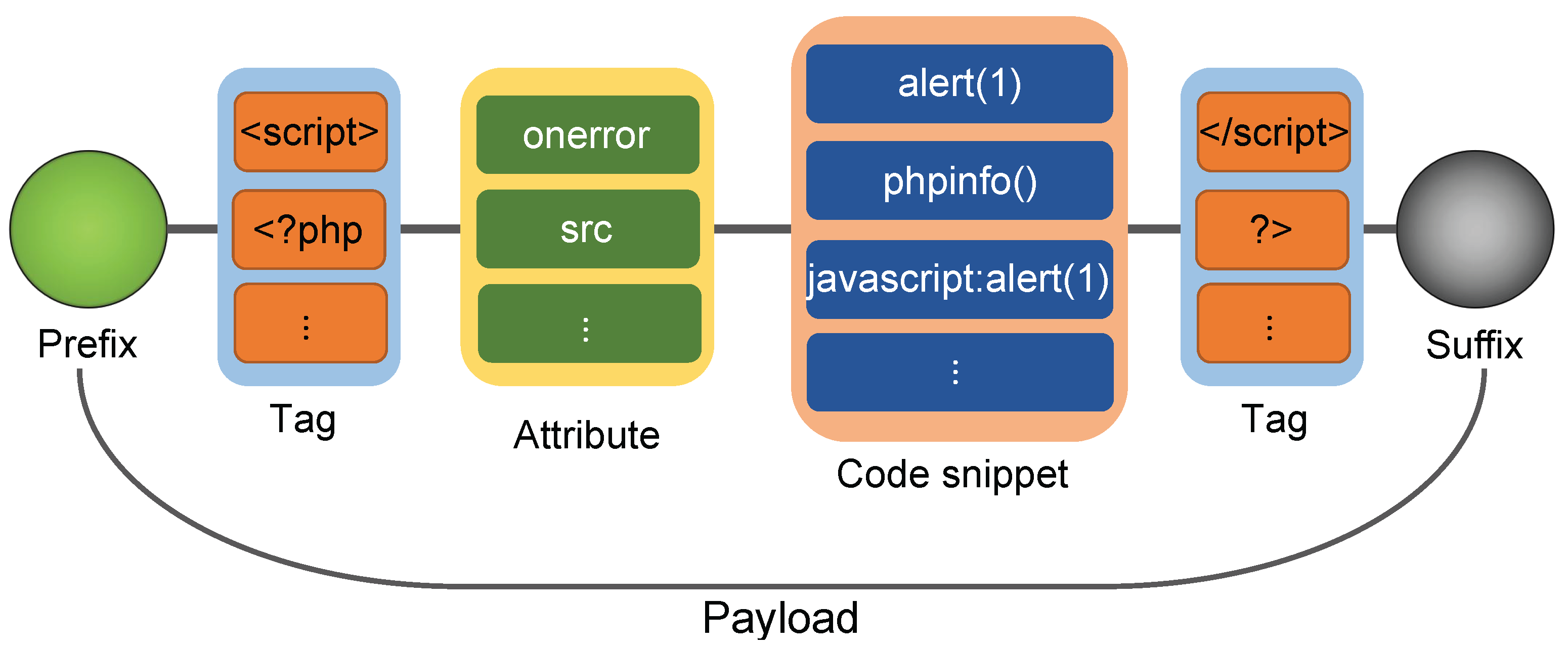
| ID | Initial Inputs | Description |
|---|---|---|
| S1 | <script>alert(1)</script> | Script Tag |
| S2 | <img src=’x’ onerror=alert(1)> | Event Attributes |
| S3 | javascript:alert(1) | Javascript Pseudo Protocol |
| S4 | <link rel=import src=’http://attack.js’> | Remote js file |
| S5 | <?php phpinfo();?> | PHP Tag |
| ID | Description | Score |
|---|---|---|
| F1 | Whether the tag is injected into the log | 0–1 |
| F2 | Whether the attribute is injected into the log | 0–1 |
| F3 | Whether the code snippet is injected into the log | 0–1 |
| F4 | String similarity between the payload and the content injected in the log | [0,1] |
| F5 | Whether the tag is injected into HTML | 0–1 |
| F6 | Whether the attribute is injected into HTML | 0–1 |
| F7 | Whether the code snippet is injected into HTML | 0–1 |
| F8 | String similarity between payload and the corresponding content in the HTML | [0–1] |
| ID | Web Application | Version | ID | Web Application | Version |
|---|---|---|---|---|---|
| 1 | Contao [3] | 4.9.5 | 8 | easy-digital-downloads [38] | 2.11.5 |
| 2 | SuiteCRM [39] | 7.11.19 | 9 | ZenCart [40] | 1.5.5e |
| 3 | webmin [4] | 1.941 | 10 | AbanteCart [41] | 1.3.2 |
| 4 | PHPFusion [1] | 9.03.20 | 11 | MaxSite CMS [42] | v108 |
| 5 | DSGVO All in one for WP [43] | 3.9 | 12 | SuiteCRM [39] | 7.11.23 |
| 6 | WP Photo Album Plus [44] | 8.0.9 | 13 | osCommerce [45] | 2.3.4.1 |
| 7 | BWP Google XML Sitemaps [46] | 1.4.1 | 14 | CE Phoenix [47] | 1.0.8.14 |
| Web Application | Detectable by LogInjector | Vulnerability Type | VUL-ID |
|---|---|---|---|
| Contao 4.9.5 | Yes | XSS | CVE-2021-35210 |
| SuiteCRM 7.11.19 | Yes | RCE | CVE-2021-42840 |
| webmin 1.941 | Yes | XSS | CVE-2020-8820 |
| Yes | XSS | CVE-2020-8821 | |
| PHPFusion 9.03.20 | Yes | XSS | CVE-2020-17449 |
| ZenCart 1.5.5e | Yes | RCE | CVE-2017-11675 |
| DSGVO All in one for WP 3.9 | Yes | XSS | CVE-2021-24294 |
| WP Photo Album Plus 8.0.9 | Yes | XSS | CVE-2021-25115 |
| BWP Google XML Sitemaps 1.4.1 | Yes | XSS | CVE-2022-0230 |
| Easy-digital-downloads 2.11.5 | Yes | XSS | CVE-2022-0706 |
| Web Application | Detectable by LogInjector | Vulnerability Type | VUL-ID |
|---|---|---|---|
| PHPFusion 9.03.20 | Yes | XSS | CNVD-2022-48580 |
| AbanteCart 1.3.2 | Yes | RCE | CNVD-2022-48600 |
| MaxSite CMS v108 | Yes | RCE | CNVD-2022-51198 |
| SuiteCRM 7.11.23 | Yes | RCE | CNVD-2022-51165 |
| osCommerce 2.3.4.1 | Yes | RCE | CNVD-2022-48592 |
| CE Phoenix 1.0.8.14 | Yes | RCE | CNVD-2022-48597 |
| Vulnerability Type | VUL-ID | Web Application | LogInjector | Black Widow |
|---|---|---|---|---|
| XSS | CVE-2021-35210 | Contao 4.9.5 | ✓ | ✗ |
| CVE-2020-8820 | webmin 1.941 | ✓ | ✗ | |
| CVE-2020-8821 | ✓ | ✗ | ||
| CVE-2021-24294 | DSGVO All in one for WP 3.9 | ✓ | ✓ | |
| CVE-2021-25115 | WP Photo Album Plus 8.0.9 | ✓ | ✗ | |
| CVE-2022-0230 | BWP Google XML Sitemaps 1.4.1 | ✓ | ✓ | |
| CVE-2022-0706 | easy-digital-downloads 2.11.5 | ✓ | ✓ | |
| CVE-2020-17449 | PHPFusion 9.03.20 | ✓ | ✗ | |
| CNVD-2022-48580 | ✓ | ✗ | ||
| RCE | CVE-2017-11675 | ZenCart 1.5.5e | ✓ | ✗ |
| CVE-2021-42840 | SuiteCRM 7.11.19 | ✓ | ✗ | |
| CNVD-2022-51165 | SuiteCRM 7.11.23 | ✓ | ✗ | |
| CNVD-2022-51198 | MaxSite CMS v108 | ✓ | ✗ | |
| CNVD-2022-48600 | AbanteCart 1.3.2 | ✓ | ✗ | |
| CNVD-2022-48592 | osCommerce 2.3.4.1 | ✓ | ✗ | |
| CNVD-2022-48597 | CE Phoenix 1.0.8.14 | ✓ | ✗ |
| Reason | Web Application | Vul-ID |
|---|---|---|
| Reason-1 | PHPFusion 9.03.20 | CVE-2020-17449 |
| CNVD-2022-48580 | ||
| Reason-2 | WP Photo Album Plus | CVE-2021-25115 |
| Webmin 1.941 | CVE-2020-8820 | |
| CVE-2020-8821 | ||
| Reason-3 | Contao 4.9.15 | CVE-2021-35210 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Pan, Z.; Chen, Y.; Chen, Y.; Shen, Y.; Li, Y. LogInjector: Detecting Web Application Log Injection Vulnerabilities. Appl. Sci. 2022, 12, 7681. https://doi.org/10.3390/app12157681
Pan Z, Chen Y, Chen Y, Shen Y, Li Y. LogInjector: Detecting Web Application Log Injection Vulnerabilities. Applied Sciences. 2022; 12(15):7681. https://doi.org/10.3390/app12157681
Chicago/Turabian StylePan, Zulie, Yu Chen, Yuanchao Chen, Yi Shen, and Yang Li. 2022. "LogInjector: Detecting Web Application Log Injection Vulnerabilities" Applied Sciences 12, no. 15: 7681. https://doi.org/10.3390/app12157681
APA StylePan, Z., Chen, Y., Chen, Y., Shen, Y., & Li, Y. (2022). LogInjector: Detecting Web Application Log Injection Vulnerabilities. Applied Sciences, 12(15), 7681. https://doi.org/10.3390/app12157681






