Development of Security Rules and Mechanisms to Protect Data from Assaults
Abstract
:1. Introduction
1.1. Cryptography
1.2. Classification of Cryptography
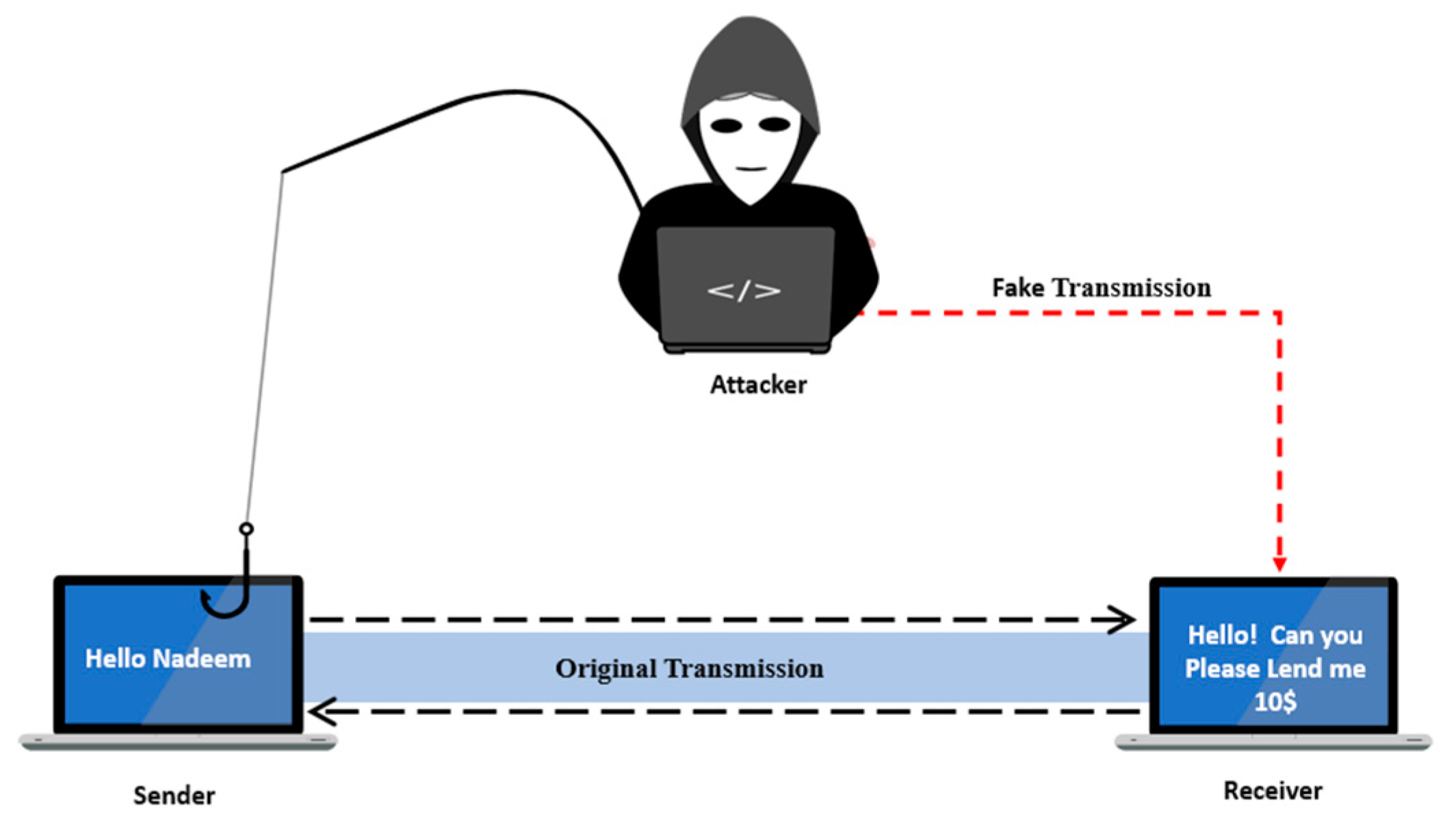
1.3. Problem Formulation
Proposed Paper Solution
2. Literature Review
3. Proposed Algorithm
3.1. Work Overflow
3.2. Data Encryption Process
3.2.1. Bit Reversing
3.2.2. Salting
3.2.3. Caesar Cipher Algorithm
3.2.4. Cipher Matrix Algorithm
| Algorithm 1: Encryption. |
| Input: Plain text Output: Cipher text |
|
3.3. Cipher XORation
3.4. Data Decryption Process
| Algorithm 2: Decryption. |
| Input: Cipher text Output: Plain text |
|
4. Experimental Flow
4.1. Encryption Algorithm
4.2. Decryption Algorithm
5. Testing
5.1. Various Testing Results
5.2. Time and Space Complexity
5.3. Cryptanalysis
6. Comparative Analysis
Novelty of Proposed Work
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Liu, L.; Wang, P.; Lin, J.; Liu, L. Intrusion detection of imbalanced network traffic based on machine learning and deep learning. IEEE Access 2021, 9, 7550–7563. [Google Scholar] [CrossRef]
- Islam, M.M.; Hasan, M.Z.; Shaon, R.A. A Novel Approach for ClientSide Encryption in Cloud Computing. In Proceedings of the International Conference on Electrical, Computer and Communication Engineering (ECCE), Cox’s Bazar, Bangladesh, 7–9 February 2019; pp. 1–6. [Google Scholar]
- Nadeem, M.; Arshad, A.; Riaz, S.; Zahra, S.; Rashid, M.; Band, S.S.; Mosavi, A. Preventing Cloud Network from Spamming Attacks Using Cloudflare and KNN. Comput. Mater. Contin. 2023, 74, 2641–2659. [Google Scholar] [CrossRef]
- Wu, K.; Chen, Z.; Li, W. A Novel Intrusion Detection Model for a Massive Network Using Convolutional Neural Networks. IEEE Access 2018, 6, 50850–50859. [Google Scholar] [CrossRef]
- Hasan, M.; Ariffin, N.; Sani, N. A review of cryptographic impact in cybersecurity on smart grid: Threat, challenges and countermeasures. J. Theor. Appl. Inf. Technol. 2021, 99, 2458–2472. [Google Scholar]
- Hu, Q.; Du, B.; Markantonakis, K.; Hancke, G.P. A Session Hijacking Attack Against a Device-Assisted Physical-Layer Key Agreement. IEEE Trans. Ind. Inform. 2019, 16, 691–702. [Google Scholar] [CrossRef]
- Nirmala, A.P.; Sundaram, B.M.; Prema, R. An Analysis on Security Threats in Cloud Computing. Int. J. Inf. Comput. Sci. 2019, 6, 2138–2153. [Google Scholar]
- Sivan, R.; Zukarnain, Z. Security and Privacy in Cloud-Based E-Health System. Symmetry 2021, 13, 742. [Google Scholar] [CrossRef]
- Al-Shabi, M. A Survey on Symmetric and Asymmetric Cryptography Algorithms in information Security. Int. J. Sci. Res. Publ. 2019, 9, 576–589. [Google Scholar] [CrossRef]
- Mihailescu, M.I.; Nita, S.L. A Searchable Encryption Scheme with Biometric Authentication and Authorization for Cloud Environments. Cryptography 2022, 6, 8. [Google Scholar] [CrossRef]
- MNadeem, M.; Arshad, A.; Riaz, S.; Band, S.S.; Mosavi, A. Intercept the Cloud Network From Brute Force and DDoS Attacks via Intrusion Detection and Prevention System. IEEE Access 2021, 9, 152300–152309. [Google Scholar] [CrossRef]
- Nahar, K.; Chakraborty, P. A Modified Version of Vigenere Cipher using 95 95 Table. Int. J. Eng. Adv. Technol. 2020, 9, 1144–1148. [Google Scholar] [CrossRef]
- Xu, Z.; Xu, C.; Xu, J.; Meng, X. A computationally efficient authentication and key agreement scheme for multi-server switching in WBAN. Int. J. Sens. Netw. 2021, 35, 143–160. [Google Scholar] [CrossRef]
- Nadeem, M.; Arshad, A.; Riaz, S.; Zahra, S.W.; Dutta, A.K.; Al Moteri, M.; Almotairi, S. An Efficient Technique to Prevent Data Misuse with Matrix Cipher Encryption Algorithms. Comput. Mater. Contin. 2022, 74, 4059–4079. [Google Scholar] [CrossRef]
- Gu, K.; Yang, L.; Yin, B. Location Data Record Privacy Protection based on Differential Privacy Mechanism. Inf. Technol. Control. 2018, 47, 639–654. [Google Scholar] [CrossRef] [Green Version]
- Ahmad, S.A.; Garko, A.B. Hybrid Cryptography Algorithms in Cloud Computing: A Review. In Proceedings of the 15th International Conference on Electronics, Computer and Computation (ICECCO), Abuja, Nigeria, 10–12 December 2019; pp. 1–6. [Google Scholar]
- Min, E.; Long, J.; Liu, Q.; Cui, J.; Chen, W. TR-IDS: Anomaly-Based Intrusion Detection through Text-Convolutional Neural Network and Random Forest. Secur. Commun. Netw. 2018, 2018, 1–9. [Google Scholar] [CrossRef] [Green Version]
- Bhavana, V.; Banushree, J.; Bhumika, D.; Chaitanya, B. A Crypto System Using Vigenere and Po-Lybius Cipher. Int. J. Eng. Appl. Sci. Technol. 2021, 6, 39–42. [Google Scholar] [CrossRef]
- Nadeem, M.; Arshad, A.; Riaz, S.; Zahra, S.W.; Dutta, A.K.; Almotairi, S. Preventing the Cloud Networks through Semi-Supervised Clustering from Both Sides Attacks. Appl. Sci. 2022, 12, 7701. [Google Scholar] [CrossRef]
- Biswas, C.; Gupta, U.D.; Haque, M.M. An Efficient Algorithm for Confidentiality, Integrity and Authentication Using Hybrid Cryptography and Steganography. In Proceedings of the International Conference on Electrical, Computer and Communication Engineering, Cox’s Bazar, Bangladesh, 7–9 February 2019; pp. 1–5. [Google Scholar]
- Nadeem, M.; Arshad, A.; Riaz, S.; Zahra, S.W.; Band, S.S.; Mosavi, A. Two Layer Symmetric Cryptography Algorithm for Protecting Data from Attacks. Comput. Mater. Contin. 2022, 74, 2625–2640. [Google Scholar] [CrossRef]
- Ahmed, W.; Rasool, A.; Javed, A.R.; Baker, T.; Jalil, Z. Cyber Security in IoT-Based Cloud Computing: A Comprehensive Survey. Electronics 2022, 11, 16. [Google Scholar] [CrossRef]
- Khraisat, A.; Gondal, I.; Vamplew, P.; Kamruzzaman, J. Survey of intrusion detection systems: Techniques, datasets and challenges. Cybersecurity 2019, 2, 1–22. [Google Scholar] [CrossRef] [Green Version]
- Liu, S.; Wu, J.; Long, C. IoT Meets Blockchain: Parallel Distributed Architecture for Data Storage and Sharing. In Proceedings of the 2018 IEEE International Conference on Internet of Things (iThings) and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom) and IEEE Smart Data (SmartData), Halifax, NS, Canada, 30 July–3 August 2018; pp. 1355–1360. [Google Scholar]
- Tan, C.; Arada, G.; Abad, A.; Magsino, E. A Hybrid Encryption and Decryption Algorithm using Caesar and Vigenère Cipher. J. Phys. Conf. Ser. 2021, 1997, 012021. [Google Scholar] [CrossRef]
- Danasingh, A.A. Performance Analysis of Data Encryption Algorithms for Secure Data Transmission. Int. J. Sci. Adv. Res. Technol. 2016, 2, 388–390. [Google Scholar]
- Zaru, A.; Khan, M. General summary of cryptography. Int. J. Eng. Res. Appl. 2018, 8, 68–71. [Google Scholar]
- Rao, Y.S.; Keshri, A.K.; Mishra, B.K.; Panda, T.C. Distributed denial of service attack on targeted resources in a computer network for critical infrastructure: A differential e-epidemic model. Phys. A Stat. Mech. Its Appl. 2020, 540, 123240. [Google Scholar] [CrossRef]
- Taha, A.A.; AbdElminaam, D.S.; Hosny, K.M. NHCA: Developing New Hybrid Cryptography Algorithm for Cloud Computing Environment. Int. J. Adv. Comput. Sci. Appl. 2017, 8. [Google Scholar] [CrossRef] [Green Version]
- Shivam, V. Design of Hybrid Cryptography system using vigenere cipher and Polybius cipher. In Proceedings of the International Conference on Computational Performance Evaluation (ComPE), Shillong, India, 2–4 July 2020. [Google Scholar]
- Nisha, S.; Farik, M. RSA Public Key Cryptography Algorithm—A Review. Int. J. Sci. Technol. Res. 2017, 6, 187–191. [Google Scholar]
- Chaabouni, N.; Mosbah, M.; Zemmari, A.; Sauvignac, C.; Faruki, P. Network intrusion detection for IoT security based on learning techniques. IEEE Commun. Surv. Tutor. 2019, 21, 2671–2701. [Google Scholar] [CrossRef]
- Carlo, A.J.; Jhone, D.A. Caesar Cipher with Goldbach Code Compression for Efficient Cryptography. Int. J. Emerg. Trends Eng. Res. 2020, 8, 2992–2998. [Google Scholar]
- Md, H. Enhancing the Security of Caesar Cipher Algorithm by Designing a Hybrid Cryptography System. Int. J. Comput. Appl. 2021, 183, 55–57. [Google Scholar]
- Ziadan, Q.; Noor, H. Combining caesar cipher and hill cipher in the generating encryption key on the vigenere cipher algorithm. J. Phys. Conf. Ser. 2021, 1918, 042009. [Google Scholar]
- Md, M.; Ashiq, M.M. Client-side Cryptography Based Security for Cloud Computing System. In Proceedings of the International Conference on Artificial Intelligence and Smart Systems (ICAIS), Tamil Nadu, India, 25–27 March 2021; p. 641105. [Google Scholar]
- Serdano, A.; Zarlis, M.; Nababan, E.B. Performance of Combining Hill Cipher Algorithm and Caesar Cipher Algorithm in Text Security. In Proceedings of the International Conference on Artificial Intelligence and Mechatronics Systems (AIMS), Bandung, Indonesia, 28–30 April 2021; pp. 1–5. [Google Scholar]
- Varun, S.; Shrikant, M. A New Modified Algorithm Based on Caesar Cipher Cryptography for Hindi Vernacular Language; Symbiosis Institute of Computer Studies and Research: Pune, India, 2022. [Google Scholar]
- Hammad, R.; Latif, K.A.; Amrullah, A.Z.; Hairani; Subki, A.; Irfan, P.; Zulfikri, M.; Azhar, L.Z.; Innuddin, M.; Marzuki, K. Implementation of combined steganography and cryptography vigenere cipher, caesar cipher and converting periodic tables for securing secret message. J. Phys. Conf. Ser. 2022, 2279, 012006. [Google Scholar] [CrossRef]
- Nadeem, M.; Arshad, A.; Riaz, S.; Zahra, S.W.; Dutta, A.K.; Alruban, A.; Almutairi, B.; Almotairi, S. Two-Layer Security Algorithms to Prevent Attacks on Data in Cyberspace. Appl. Sci. 2022, 12, 9736. [Google Scholar] [CrossRef]















































| Reference | Year | Proposed Work |
|---|---|---|
| [33] | 2020 | Implemented the Goldbach algorithm on the Caesar cipher algorithm to enhance the functionality of the Caesar cipher algorithm. |
| [25] | 2021 | Surveyed various Vigenère cipher and Caesar cipher papers and collected their best techniques. After that, developed a hybrid algorithm to secure the data from attacks. |
| [34] | 2021 | Combined efficient techniques of Caesar cipher, Playfair, and stream cipher algorithm and developed an advanced encryption algorithm to improve the security of the Caesar cipher algorithm. |
| [35] | 2021 | Identified the weakness of the Vigenère cipher algorithm and discussed that the key used in the Vigenère cipher could be obtained with the help of the Kasiski test. The best Caesar cipher and Hill cipher algorithm techniques were used to solve this problem. |
| [36] | 2021 | Surveyed various papers, collected different techniques, and then developed an algorithm to prevent cloud data from man-in-the-middle attacks. |
| [37] | 2021 | An algorithm was developed to protect text data from cryptanalysis, in which Hill cipher and Caesar cipher algorithms were used. |
| [38] | 2022 | Collected various Caesar cipher techniques to protect data from man-in-the-middle attacks. After that, developed an algorithm that identified how data can be protected from attackers using the Caesar cipher algorithm. |
| [39] | 2022 | Combined Caesar cipher and Vigenère cipher algorithms to encrypt the data. After that, discussed that steganography is a way to hide all pieces of information and discussed that this method can produce more difficult-to-crack encryption. |
| [40] | 2022 | The two-layer algorithm was developed to protect the cloud data. In the first layer, the proposed algorithm was implemented on plain text, and a static key was generated. In layer two, the Vigenère cipher algorithm was implemented on the layer 1 result, and a ciphertext was obtained. |
| Testing | Plain Text | Plain-Text Length (P) | Encoded Text | Key | Cipher Text | Cipher Text Length (C) | Length Difference (L) = C − P |
|---|---|---|---|---|---|---|---|
| 1 | N@deem_9$3 | 10 | ╬ñ█Bm¼meBi|( | S7_45j | ØôävXã>RØ]IB | 12 | 2 |
| 2 | WR!tten_by-@Li | 14 | mºD/ÝHú{ogþÝ°B~¿ | Su$k!8 | >‗`D╠p¬.Kƪã└Ƞ+îå | 16 | 2 |
| 3 | $tuD!O$0ne | 10 | mÜ├e”[eMuÞuÞ|H | WJ&56h | :ðÕPÌ32℘S¦CÇ+¤ | 14 | 4 |
| 4 | @uth0r_is_Z@hra | 15 | kÚfÕ•Dߥñy┼µ¸jUs | Waj!h@ | <êƮ─ÆℑÂ▀╬X¡ªáƻ?R | 16 | 1 |
| 5 | W@jia_12 | 8 | Ã█ó█mi3ap© | N@d50! | ëøãµ]H}!Ìì | 10 | 2 |
| Sr# | Plain Text Length | Encoding Time (s) | Encode Text Length | Key Length | Ciphertext Length | Ciphertext Time (s) | Plain Text Memory Allocation | Cipher Text Memory Allocation |
|---|---|---|---|---|---|---|---|---|
| 1 | 10 | 104.21 | 12 | 6 | 12 | 25.33 | 12.4 KB | 13.4 KB |
| 2 | 14 | 113.43 | 16 | 6 | 16 | 32.27 | 13.9KB | 14.7 KB |
| 3 | 10 | 107.21 | 14 | 6 | 14 | 28.45 | 11.7 KB | 12.5 KB |
| 4 | 15 | 115.37 | 16 | 6 | 16 | 33.15 | 16.9 KB | 18.2 KB |
| 5 | 8 | 93.29 | 10 | 6 | 10 | 21.52 | 10.8 KB | 11.6 KB |
| Sr# | Ciphertext Length | Key Length | Decryption Time (s) | Cipher Text Memory Allocation | Plain Text Memory Allocation |
|---|---|---|---|---|---|
| 1 | 12 | 6 | 96.34 | 13.4 KB | 12.3 KB |
| 2 | 16 | 6 | 102.42 | 14.7 KB | 12.8KB |
| 3 | 14 | 6 | 99.12 | 12.5 KB | 11.9 KB |
| 4 | 16 | 6 | 103.29 | 18.2 KB | 15.4 KB |
| 5 | 10 | 6 | 92.54 | 11.6 KB | 10.9 KB |
| Sr# | Plain Text | Text Length (T) | Ciphertext Length (C) | Length Equalization (T, C) | Key Snatching Algorithm | Key Identification |
|---|---|---|---|---|---|---|
| 1 | N@deem_9$3 | 10 | 12 | T ≠ C | No | No |
| 2 | WR!tten_by-@Li | 14 | 16 | T ≠ C | No | No |
| 3 | $tuD!O$0ne | 10 | 14 | T ≠ C | No | No |
| 4 | @uth0r_is_Z@hra | 15 | 16 | T ≠ C | No | No |
| 5 | W@jia_12 | 8 | 10 | T ≠ C | No | No |
| Sr# | 1 | 2 | 3 | 4 | 5 | Proposed Work |
|---|---|---|---|---|---|---|
| Reference No. | [33] | [25] | [34] | [35] | [38] | |
| Year | 2020 | 2021 | 2021 | 2021 | 2022 | |
| Proposed Algorithm | Implemented Caesar cipher results on the Goldbach algorithm | Implemented Caesar cipher results on the Vigenère cipher algorithm | Implemented Caesar cipher, Playfair, and stream cipher algorithm on plain text | Implemented Caesar cipher and Hill cipher algorithm on key | Random shift key-generation algorithm | Caesar cipher encryption algorithm, cipher matrix algorithm |
| Novelty | Multiple times encoded Caesar cipher results by the Goldbach algorithm | implemented the best techniques of Caesar cipher and Vigenère cipher | Each algorithm is encrypted with a static key | The key was secured using two algorithms | Shifted each character’s values according to each decimal value | Provided data security in three different ways. |
| Research Gaps | Obtained Caesar cipher results were encoded iteratively | Used existing techniques of Caesar cipher and Vigenère cipher | No latest technique has been introduced | Key was obtained by substituting the results of one algorithm to another. | Characters shifted according to a key decimal value | Identified all gaps |
| Proposed Paper Solution | Enhanced data security by salting and bit reversing | Applied the number of time shifting by Caesar cipher | Developed cipher matrix algorithm | Applied key on cipher matrix text for text security | Applied different rules on each algorithm phase | The proposed paper addressed all existing gaps |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zahra, S.W.; Arshad, A.; Nadeem, M.; Riaz, S.; Dutta, A.K.; Alzaid, Z.; Alabdan, R.; Almutairi, B.; Almotairi, S. Development of Security Rules and Mechanisms to Protect Data from Assaults. Appl. Sci. 2022, 12, 12578. https://doi.org/10.3390/app122412578
Zahra SW, Arshad A, Nadeem M, Riaz S, Dutta AK, Alzaid Z, Alabdan R, Almutairi B, Almotairi S. Development of Security Rules and Mechanisms to Protect Data from Assaults. Applied Sciences. 2022; 12(24):12578. https://doi.org/10.3390/app122412578
Chicago/Turabian StyleZahra, Syeda Wajiha, Ali Arshad, Muhammad Nadeem, Saman Riaz, Ashit Kumar Dutta, Zaid Alzaid, Rana Alabdan, Badr Almutairi, and Sultan Almotairi. 2022. "Development of Security Rules and Mechanisms to Protect Data from Assaults" Applied Sciences 12, no. 24: 12578. https://doi.org/10.3390/app122412578
APA StyleZahra, S. W., Arshad, A., Nadeem, M., Riaz, S., Dutta, A. K., Alzaid, Z., Alabdan, R., Almutairi, B., & Almotairi, S. (2022). Development of Security Rules and Mechanisms to Protect Data from Assaults. Applied Sciences, 12(24), 12578. https://doi.org/10.3390/app122412578






